6. Interoperability
With Liming Zhu
The early bird (A) arrives and catches worm (B), pulling string (C) and shooting off pistol (D). Bullet (E) bursts balloon (F), dropping brick (G) on bulb (H) of atomizer (I) and shooting perfume (J) on sponge (K). As sponge gains in weight, it lowers itself and pulls string (L), raising end of board (M). Cannon ball (N) drops on nose of sleeping gentleman. String tied to cannon ball releases cork (O) of vacuum bottle (P) and ice water falls on sleeper’s face to assist the cannon ball in its good work.
—Rube Goldberg, instructions for “a simple alarm clock”
Interoperability is about the degree to which two or more systems can usefully exchange meaningful information via interfaces in a particular context. The definition includes not only having the ability to exchange data (syntactic interoperability) but also having the ability to correctly interpret the data being exchanged (semantic interoperability). A system cannot be interoperable in isolation. Any discussion of a system’s interoperability needs to identify with whom, with what, and under what circumstances—hence, the need to include the context.
Interoperability is affected by the systems expected to interoperate. If we already know the interfaces of external systems with which our system will interoperate, then we can design that knowledge into the system. Or we can design our system to interoperate in a more generic fashion, so that the identity and the services that another system provides can be bound later in the life cycle, at build time or runtime.
Like all quality attributes, interoperability is not a yes-or-no proposition but has shades of meaning. There are several characterizing frameworks for interoperability, all of which seem to define five levels of interoperability “maturity” (see the “For Further Reading” section at the end of this chapter for a pointer). The lowest level signifies systems that do not share data at all, or do not do so with any success. The highest level signifies systems that work together seamlessly, never make any mistakes interpreting each other’s communications, and share the same underlying semantic model of the world in which they work.
Here are some of the reasons you might want systems to interoperate:
• Your system provides a service to be used by a collection of unknown systems. These systems need to interoperate with your system even though you may know nothing about them. An example is a service such as Google Maps.
• You are constructing capabilities from existing systems. For example, one of the existing systems is responsible for sensing its environment, another one is responsible for processing the raw data, a third is responsible for interpreting the data, and a final one is responsible for producing and distributing a representation of what was sensed. An example is a traffic sensing system where the input comes from individual vehicles, the raw data is processed into common units of measurement, is interpreted and fused, and traffic congestion information is broadcast.
These examples highlight two important aspects of interoperability:
1. Discovery. The consumer of a service must discover (possibly at runtime, possibly prior to runtime) the location, identity, and the interface of the service.
2. Handling of the response. There are three distinct possibilities:
• The service reports back to the requester with the response.
• The service sends its response on to another system.
• The service broadcasts its response to any interested parties.
These elements, discovery and disposition of response, along with management of interfaces, govern our discussion of scenarios and tactics for interoperability.
6.1. Interoperability General Scenario
The following are the portions of an interoperability general scenario:
• Source of stimulus. A system initiates a request to interoperate with another system.
• Stimulus. A request to exchange information among system(s).
• Artifacts. The systems that wish to interoperate.
• Environment. The systems that wish to interoperate are discovered at runtime or are known prior to runtime.
• Response. The request to interoperate results in the exchange of information. The information is understood by the receiving party both syntactically and semantically. Alternatively, the request is rejected and appropriate entities are notified. In either case, the request may be logged.
• Response measure. The percentage of information exchanges correctly processed or the percentage of information exchanges correctly rejected.
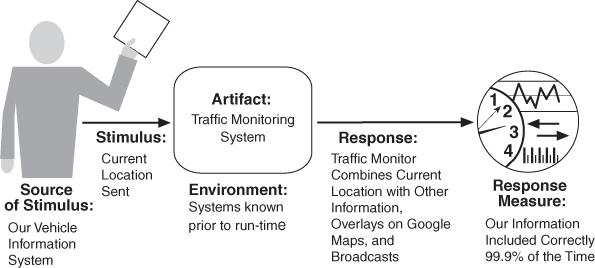
Figure 6.1 gives an example: Our vehicle information system sends our current location to the traffic monitoring system. The traffic monitoring system combines our location with other information, overlays this information on a Google Map, and broadcasts it. Our location information is correctly included with a probability of 99.9%.
Figure 6.1. Sample concrete interoperability scenario
Table 6.2 presents the possible values for each portion of an interoperability scenario.
Table 6.2. General Interoperability Scenario

6.2. Tactics for Interoperability
Figure 6.2 shows the goal of the set of interoperability tactics.
Figure 6.2. Goal of interoperability tactics
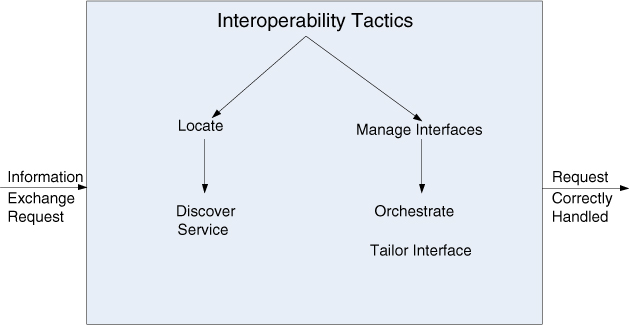
We identify two categories of interoperability tactics: locate and manage interfaces.
Locate
There is only one tactic in this category: discover service. It is used when the systems that interoperate must be discovered at runtime.
• Discover service. Locate a service through searching a known directory service. (By “service,” we simply mean a set of capabilities that is accessible via some kind of interface.) There may be multiple levels of indirection in this location process—that is, a known location points to another location that in turn can be searched for the service. The service can be located by type of service, by name, by location, or by some other attribute.
Manage Interfaces
Managing interfaces consists of two tactics: orchestrate and tailor interface.
• Orchestrate. Orchestrate is a tactic that uses a control mechanism to coordinate and manage and sequence the invocation of particular services (which could be ignorant of each other). Orchestration is used when the interoperating systems must interact in a complex fashion to accomplish a complex task; orchestration “scripts” the interaction. Workflow engines are an example of the use of the orchestrate tactic. The mediator design pattern can serve this function for simple orchestration. Complex orchestration can be specified in a language such as BPEL.
• Tailor interface. Tailor interface is a tactic that adds or removes capabilities to an interface. Capabilities such as translation, adding buffering, or smoothing data can be added. Capabilities may be removed as well. An example of removing capabilities is to hide particular functions from untrusted users. The decorator pattern is an example of the tailor interface tactic.
The enterprise service bus that underlies many service-oriented architectures combines both of the manage interface tactics.
Figure 6.3 shows a summary of the tactics to achieve interoperability.
Figure 6.3. Summary of interoperability tactics
6.3. A Design Checklist for Interoperability
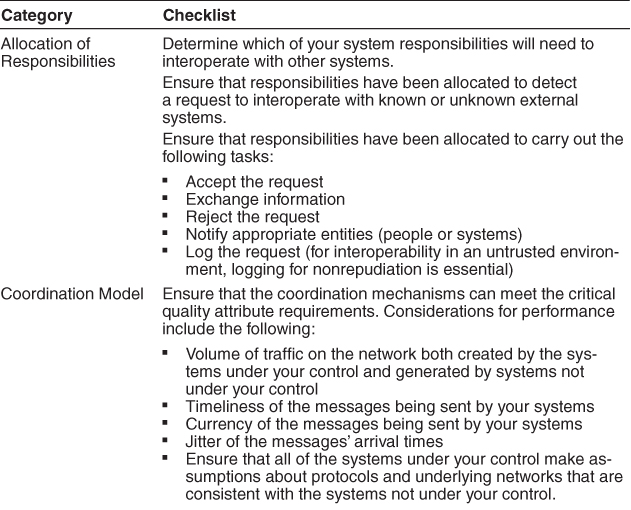
Table 6.3 is a checklist to support the design and analysis process for inter-operability.
Table 6.3. Checklist to Support the Design and Analysis Process for Interoperability

6.4. Summary
Interoperability refers to the ability of systems to usefully exchange information. These systems may have been constructed with the intention of exchanging information, they may be existing systems that are desired to exchange information, or they may provide general services without knowing the details of the systems that wish to utilize those services.
The general scenario for interoperability provides the details of these different cases. In any interoperability case, the goal is to intentionally exchange information or reject the request to exchange information.
Achieving interoperability involves the relevant systems locating each other and then managing the interfaces so that they can exchange information.
6.5. For Further Reading
An SEI report gives a good overview of interoperability, and it highlights some of the “maturity frameworks” for interoperability [Brownsword 04].
The various WS* services are being developed under the auspices of the World Wide Web Consortium (W3C) and can be found at www.w3.org/2002/ws.
Systems of systems are of particular interest to the U.S. Department of Defense. An engineering guide can be found at [ODUSD 08].
6.6. Discussion Questions
1. Find a web service mashup. Write several concrete interoperability scenarios for this system.
2. What is the relationship between interoperability and the other quality attributes highlighted in this book? For example, if two systems fail to exchange information properly, could a security flaw result? What other quality attributes seem strongly related (at least potentially) to interoperability?
3. Is a service-oriented system a system of systems? If so, describe a service-oriented system that is directed, one that is acknowledged, one that is collaborative, and one that is virtual.
4. Universal Description, Discovery, and Integration (UDDI) was touted as a discovery service, but commercial support for UDDI is being withdrawn. Why do you suppose this is? Does it have anything to do with the quality attributes delivered or not delivered by UDDI solutions?
5. Why has the importance of orchestration grown in recent years?
6. If you are a technology producer, what are the advantages and disadvantages of adhering to interoperability standards? Why would a producer not adhere to a standard?
7. With what other systems will an automatic teller machine need to interoperate? How would you change your automatic teller system design to accommodate these other systems?