THE FOLLOWING COMPTIA SECURITY+ EXAM OBJECTIVES ARE COVERED IN THIS CHAPTER:
1.4 Recognize the following attacks and specify the appropriate actions to take to mitigate vulnerability and risk
DoS/DDoS (Denial of Service/Distributed Denial of Service)
Back Door
Spoofing
Man in the Middle
Replay
TCP/IP Hijacking
Social Engineering
Password Guessing
Brute Force
Dictionary
Software Exploitation
1.5 Recognize the following types of malicious code and specify the appropriate actions to take to mitigate vulnerability and risk
Viruses
Trojan Horses
Logic Bombs
Worms
1.6 Understand the concept of and know how reduce the risks of social engineering
1.7 Understand the concept and significance of auditing, logging, and system scanning
2.2 Recognize and understand the administration of the following email security concepts
SPAM
Hoaxes

In this chapter, we'll look at several types of attacks, as well as some of the reasons why your network is vulnerable. In many instances, the vulnerabilities you must deal with are a result of the operating systems manufacturers' implementations of networking technologies, coupled with the trusting nature of TCP/IP.
Note
Objective 1.4 addresses numerous types of attacks. Some of those are covered in this chapter, while those related to cryptography are covered in Chapter 7, "Cryptography Basics, Methods, and Standards."
In computing, a lot of the terminology used comes from other fields, such as the military. That seems to be particularly true when it comes to security. Using that line of logic, an attack occurs when an unauthorized individual or group of individuals attempts to access, modify, or damage your systems or environment. These attacks can be fairly simple and unfocused, or they can appear to be almost blitzkrieg-like in their intensity.
One of the main reasons for differences in attacks is that they occur in many ways and for different reasons. Regardless of how they occur, they generally try to accomplish one or more of these three goals:
In an access attack, someone who should not be able to wants access to your resources.
During a modification and repudiation attack, someone wants to modify information in your systems.
A denial-of-service (DoS) attack tries to disrupt your network and services.
Those who are attacking you may be doing it for the sheer fun of it, they may be criminals attempting to steal from you, or they can be individuals or groups who are using the attack to make a political statement or commit an act of terrorism. Regardless of the motive, your job is to protect the people you work with from these acts of aggression. You are, in many cases, the only person in your organization charged with the responsibility of repulsing these attacks.
This section deals with the general types of attacks you'll experience.
Note
The following are considered attack strategies. We'll look at the specific attacks—each of which will fall within one or more of these strategies—later in this chapter, in the section titled "Recognizing Common Attacks." Remember that for this exam, CompTIA wants you to have general knowledge about the various types of attacks and attack strategies, rather than knowing the specifics of how attacks are created, deployed, and so on.
The goal of an access attack is straightforward. Access attacks are an attempt to gain access to information that the attacker isn't authorized to have. These types of attacks focus on breaching the confidentiality of information. They occur through either internal or external access; they may also occur when physical access to the information is possible.
Dumpster diving is a common physical access method. Companies generate a huge amount of paper in the normal course of events, most of which eventually winds up in dumpsters or recycle bins. These dumpsters may contain information that is highly sensitive in nature. In high-security and government environments, sensitive papers are either shredded or burned. Most businesses don't do this. In addition, the advent of "green" companies has created an increase in the amount of recycled paper. This paper may contain all kinds of juicy information about a company and its individual employees.
A second common method used in access attacks is to capture information en route between two systems; rather than finding paper, such attacks find data. Some common methods in such access attacks include:
- Eavesdropping
Eavesdropping is the process of listening in on or overhearing parts of a conversation. Eavesdropping also includes attackers listening in on your network traffic. This type of attack is generally passive. For example, a coworker may overhear your dinner plans because your speakerphone is set too loud. The opportunity to overhear a conversation is coupled with the carelessness of the parties in the conversation.
- Snooping
Snooping occurs when someone looks through your files in the hopes of finding something interesting. These files may be either electronic or on paper. In the case of physical snooping, people might inspect your dumpster, recycling bins, or even your file cabinets; they can look under the keyboard for Post-It notes, or look for scraps of paper tacked to your bulletin board. Computer snooping, on the other hand, involves someone searching through your electronic files trying to find something interesting.
- Interception
Interception can be either an active or a passive process. In a networked environment, a passive interception would involve someone who routinely monitors network traffic. Active interception might include putting a computer system between the sender and receiver to capture information as it's sent. From the perspective of interception, this process is covert. The last thing a person on an intercept mission wants is to be discovered. Intercept missions can occur for years, without the knowledge of the intercepted parties.
Government agencies routinely run intercept missions to gather intelligence about the capabilities and locations of enemies. For instance, the FBI has several products that they install on ISPs to gather and process e-mail looking for keywords. These keyword searches become the basis of an investigation.
The major difference between these types of attacks is how they're accomplished. The ultimate objective is to gain access to information that isn't authorized.
Modification attacks involve the deletion, insertion, or alteration of information in an unauthorized manner that is intended to appear genuine to the user. These attacks can be very hard to detect. They're similar to access attacks in that the attacker must first get to the data on the servers, but they differ from that point on. The motivation for this type of attack may be to plant information, change grades in a class, fraudulently alter credit card records, or something similar. Website defacements are a common form of modification attack; they involve someone changing web pages in a malicious manner.
A variation of a modification attack is a repudiation attack. Repudiation attacks make data or information appear to be invalid or misleading (which can be even worse). For example, someone might access your e-mail server and send inflammatory information to others under the guise of one of your top managers. This information might prove embarrassing to your company and possibly do irreparable harm. Repudiation attacks are fairly easy to accomplish because most e-mail systems don't check outbound mail for validity. Repudiation attacks, like modification attacks, usually begin as access attacks.
Tip
The opposite of repudiation is nonrepudiation. When you purchase something from an online vendor, the vendor often asks for information—such as the PIN number on your credit card, not just the credit card number—to prove that you are who you say you are. By proving your identity, the company has nonrepudiated evidence that the sale is valid.
A common type of repudiation attack involves a customer who claims that they never received a service for which they were billed. In this situation, the burden of proof is on the company to prove that the information used to generate the invoice is accurate. If an external attacker has modified the data, verifying the information may be difficult.
Denial-of-service (DoS) attacks prevent access to resources by users authorized to use those resources. An attacker may attempt to bring down an e-commerce website to prevent or deny usage by legitimate customers. DoS attacks are common on the Internet, where they have hit large companies such as Amazon, Microsoft, and AT&T. These attacks are often widely publicized in the media. Most simple DoS attacks occur from a single system, and a specific server or organization is the target.
Tip
There isn't a single type of DoS attack, but a variety of similar methods that have the same purpose. It's easiest to think of a DoS attack by imagining that your servers are so busy responding to false requests that they don't have time to service legitimate requests. Not only can the servers be physically busy, but the same result can occur if the attack consumes all the available bandwidth.
Several types of attacks can occur in this category. These attacks can deny access to information, applications, systems, or communications. In a DoS attack on an application, the attack may bring down a website while the communications and systems continue to operate. A DoS attack on a system crashes the operating system (a simple reboot may restore the server to normal operation). A DoS attack against a network is designed to fill the communications channel and prevent access to authorized users. A common DoS attack involves opening as many TCP sessions as possible; this type of attack is called a TCP SYN flood DoS attack.
Two of the most common types of DoS attacks are the ping of death and the buffer overflow attack. The ping of death crashes a system by sending Internet Control Message Protocol (ICMP) packets (think echoes) that are larger than the system can handle. Buffer overflow attacks, as the name implies, attempt to put more data (usually long input strings) into the buffer than it can hold. Code Red, Slapper, and Slammer are all attacks that took advantage of buffer overflows, and sPing is an example of a ping of death.
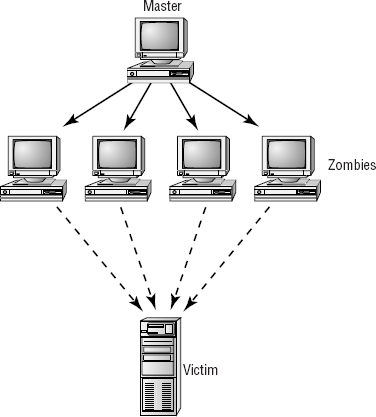
A distributed denial-of-service (DDoS) attack is similar to a DoS attack. This type of attack amplifies the concepts of a DoS by using multiple computer systems to conduct the attack against a single organization. These attacks exploit the inherent weaknesses of dedicated networks such as DSL and cable. These permanently attached systems usually have little, if any, protection. An attacker can load an attack program onto dozens or even hundreds of computer systems that use DSL or cable modems. The attack program lies dormant on these computers until they get an attack signal from a master computer. This signal triggers these systems, which launch an attack simultaneously on the target network or system. Figure 2.1 shows an attack occurring and the master controller orchestrating the attack. The master controller may be another unsuspecting user. The systems taking direction from the master control computer are referred to as zombies. These systems merely carry out the instruction they've been given by the master computer.
Tip
Remember that the difference between a DoS attack and a DDoS attack is that the latter uses multiple computers—all focused on one target.
The nasty part of this type of attack is that the machines used to carry out the attack belong to normal computer users. The attack gives no special warning to those users. When the attack is complete, the attack program may remove itself from the system or infect the unsuspecting user's computer with a virus that destroys the hard drive, thereby wiping out the evidence.
Most attacks are designed to exploit potential weaknesses. Those weaknesses can be in the implementation of programs or in the protocols used in networks. Many types of attacks require a high level of sophistication and are rare. You need to know about them so that you can identify what has happened in your network.
In the following sections, we'll look at these attacks more closely.
The term back door attack can have two different meanings. The original term back door referred to troubleshooting and developer hooks into systems. During the development of a complicated operating system or application, programmers add back doors or maintenance hooks. These back doors allow them to examine operations inside the code while the code is running. The back doors are stripped out of the code when it's moved to production. When a software manufacturer discovers a hook that hasn't been removed, it releases a maintenance upgrade or patch to close the back door. These patches are common when a new product is initially released.
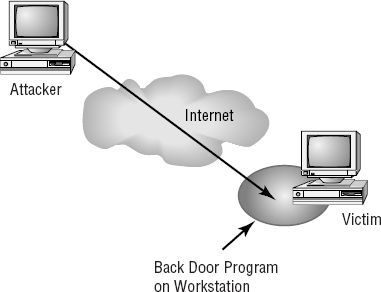
The second type of back door refers to gaining access to a network and inserting a program or utility that creates an entrance for an attacker. The program may allow a certain user ID to log on without a password or gain administrative privileges. Figure 2.2 shows how a back door attack can be used to bypass the security of a network. In this example, the attacker is using a back door program to utilize resources or steal information.
Such an attack is usually used as either an access or modification attack. A number of tools exist to create back door attacks on systems. One of the more popular tools is Back Orifice, which has been updated to work with Windows Server 2003 as well as earlier versions. Another popular back door program is NetBus. Fortunately, most conventional antivirus software will detect and block these types of attacks.
Note
Back Orifice and NetBus are remote administration tools used by attackers to take control of Windows-based systems. These packages are typically installed using a Trojan horse program. Back Orifice and NetBus allow a remote user to take full control of systems that have these applications installed. Back Orifice and NetBus run on all of the current Windows operating systems.
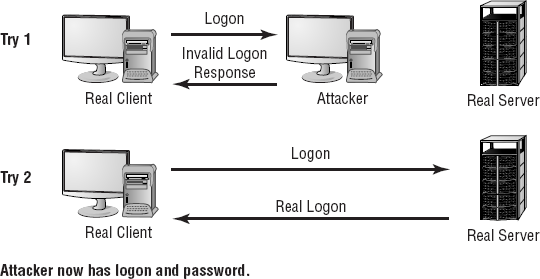
A spoofing attack is an attempt by someone or something to masquerade as someone else. This type of attack is usually considered an access attack. A common spoofing attack that was popular for many years on early Unix and other timesharing systems involved a programmer writing a fake logon program. This program would prompt the user for a user ID and password. No matter what the user typed, the program would indicate an invalid logon attempt and then transfer control to the real logon program. The spoofing program would write the logon and password into a disk file, which was retrieved later.
The most popular spoofing attacks today are IP spoofing and DNS spoofing. With IP spoofing, the goal is to make the data look as if it came from a trusted host when it didn't (thus spoofing the IP address of the sending host). With DNS spoofing, the DNS server is given information about a name server that it thinks is legitimate when it isn't. This can send users to a website other than the one they wanted to go to, reroute mail, or do any other type or redirection wherein data from a DNS server is used to determine a destination.
Tip
Always think of spoofing as fooling. Attackers are trying to fool the user, system, and/or host into believing they're something they aren't. Because the word spoof can describe any false information at any level, spoofing can occur at any level of network.
Figure 2.3 shows a spoofing attack occurring as part of the logon process on a computer network. The attacker in this situation impersonates the server to the client attempting to log in. No matter what the client attempts to do, the impersonating system will fail the login. When this process is finished, the impersonating system disconnects from the client. The client then logs in to the legitimate server. In the meantime, the attacker now has a valid user ID and password.
The important point to remember is that a spoofing attack tricks something or someone into thinking something legitimate is occurring.
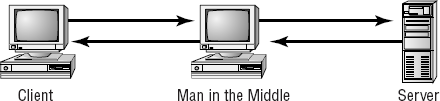
Man-in-the-middle attacks tend to be fairly sophisticated. This type of attack is also an access attack, but it can be used as the starting point for a modification attack. The method used in these attacks clandestinely places a piece of software between a server and the user that neither the server administrators nor the user are aware of. This software intercepts data and then sends the information to the server as if nothing is wrong. The server responds back to the software, thinking it's communicating with the legitimate client. The attacking software continues sending information on to the server, and so forth.
If communication between the server and user continues, what's the harm of the software? The answer lies in whatever else the software is doing. The man-in-the-middle software may be recording information for someone to view later, altering it, or in some other way compromising the security of your system and session.
Tip
A man-in-the-middle attack is an active attack. Something is actively intercepting the data and may or may not be altering it. If it's altering the data, the altered data masquerades as legitimate data traveling between the two hosts.
Figure 2.4 illustrates a man-in-the-middle attack. Notice how both the server and client assume that the system they're talking to is the legitimate system. The man in the middle appears to be the server to the client, and it appears to be the client to the server.
In recent years, the threat of man-in-the-middle attacks on wireless networks has increased. Because it's no longer necessary to connect to the wire, a malicious rogue can be outside the building intercepting packets, altering them, and sending them on. A common solution to this problem is to enforce Wired Equivalent Privacy (WEP) across the wireless network.
Tip
An older term generically used for all man-in-the-middle attacks was TCP hijacking. TCP hijacking is addressed in more detail later in this chapter.
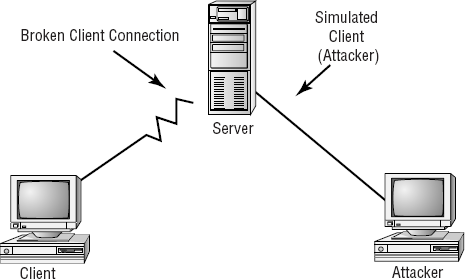
Replay attacks are becoming quite common. These attacks occur when information is captured over a network. Replay attacks are used for access or modification attacks. In a distributed environment, logon and password information is sent between the client and the authentication system. The attacker can capture this information and replay it again later. This can also occur with security certificates from systems such as Kerberos: The attacker resubmits the certificate, hoping to be validated by the authentication system and circumvent any time sensitivity.
Figure 2.5 shows an attacker presenting a previously captured certificate to a Kerberos-enabled system. In this example, the attacker gets legitimate information from the client and records it. Then, the attacker attempts to use the information to enter the system. The attacker later relays information to gain access.
If this attack is successful, the attacker will have all the rights and privileges from the original certificate. This is the primary reason that most certificates contain a unique session identifier and a time stamp: If the certificate has expired, it will be rejected, and an entry should be made in a security log to notify system administrators.
Password-guessing attacks occur when an account is attacked repeatedly. This is accomplished by sending possible passwords to the account in a systematic manner. These attacks are initially carried out to gain passwords for an access or modification attack. There are two types of password-guessing attacks:
- Brute-force attack
A brute-force attack is an attempt to guess passwords until a successful guess occurs. This type of attack usually occurs over a long period. To make passwords more difficult to guess, they should be much longer than two or three characters (six should be the bare minimum), be complex, and have password lockout policies.
- Dictionary attack
A dictionary attack uses a dictionary of common words to attempt to find the user's password. Dictionary attacks can be automated, and several tools exist in the public domain to execute them.
Some systems will identify whether an account ID is valid and whether the password is wrong. Giving the attacker a clue as to a valid account name isn't a good practice. If you can enable your authentication to either accept a valid ID/password group or require the entire logon process again, you should.
As a security professional, one of your biggest problems is working with TCP/IP. You could say that the ease of connectivity TCP/IP offers is one of the most significant difficulties we face. Virtually all large networks, including the Internet, are built on the TCP/IP protocol suite. It has become an international standard.
TCP/IP was designed to connect disparate computer systems into a robust and reliable network. It offers a richness of capabilities and support for many different protocols. Once TCP/IP is installed, it will generally operate reliably for years.
TCP/IP has been a salvation for organizations that need to connect different systems together to function as a unified whole. Because of this easy-to-use, well-documented network, the Internet has numerous holes. You can easily close most of the holes, but you must first know about them.
Note
You need to have a good understanding of the processes TCP/IP uses in order to know how attacks to TCP/IP work. The emphasis in this section is on the types of connections and services. As the exam objectives state, the Security+ candidate should have basic hardware and network skills. If you're weak in those areas, you'll do well to supplement your study with basic networking information that can be found on the Web.
The following sections delve into issues related to TCP/IP and security. Many of these issues will be familiar to you if you've taken the Network+ or Server+ exam from CompTIA. If there are any gaps in your knowledge of the topics, however, be sure to read the sections carefully.
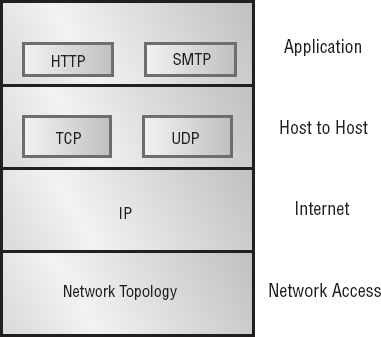
The TCP/IP protocol suite is broken into four architectural layers:
Application layer
Host-to-Host or Transport layer
Internet layer
Network Interface layer
Computers using TCP/IP use the existing physical connection between the systems. TCP/IP doesn't concern itself with the network topology or physical connections. The network controller that resides in a computer or host deals with the physical protocol or topology. TCP/IP communicates with that controller and lets the controller worry about the network topology and physical connection.
In TCP/IP parlance, a computer on the network is a host. A host is any device connected to the network that runs a TCP/IP protocol suite or stack. Figure 2.6 shows the four layers in a TCP/IP protocol stack. Notice that this drawing includes the physical or network topology. Although it isn't part of the TCP/IP protocol, topology is essential to conveying information on a network.
The four layers of TCP/IP have unique functions and methods for accomplishing work. Each layer talks to the layers that reside above and below it. Each layer also has its own rules and capabilities.
The following sections discuss the specific layers of the TCP/IP protocol as well as the common protocols used in the stack and how information is conveyed between these layers. We also discuss some of the more common methods used to attack TCP/IP-based networks. Finally, we briefly discuss encapsulation, the process used to pass messages between the layers in the TCP/IP protocol.
The Application layer is the highest layer of the suite. This layer allows applications to access services or protocols to exchange data. Most programs, such as web browsers, interface with TCP/IP at this level. The most commonly used Application layer protocols include:
- Hypertext Transfer Protocol (HTTP)
HTTP is the protocol used for web pages and the World Wide Web. HTTP applications use a standard language called Hypertext Markup Language (HTML). HTML files are normal text files that contain special coding that allows graphics, special fonts, and characters to be displayed by a web browser or other web-enabled applications.
- File Transfer Protocol (FTP)
FTP is an application that allows connections to FTP servers for file uploads and downloads. FTP is a common application used to transfer files between hosts on the Internet.
- Simple Mail Transfer Protocol (SMTP)
SMTP is the standard protocol for e-mail communications. SMTP allows e-mail clients and servers to communicate with each other for message delivery.
- Telnet
Telnet is an interactive terminal emulation protocol. It allows a remote user to conduct an interactive session with a Telnet server. This session can appear to be the same as if the client were a local session.
- Domain Name Service (DNS)
DNS allows hosts to resolve hostnames to an Internet Protocol (IP) address. IP is discussed in the Internet layer section.
- Routing Information Protocol (RIP)
RIP allows routing information to be exchanged between routers on an IP network.
- Simple Network Management Protocol (SNMP)
SNMP is a management tool that allows communications between network devices and a management console. Most routers, bridges, and intelligent hubs can communicate using SNMP.
- Post Office Protocol (POP)
POP is a protocol used in many e-mail systems. It allows for advanced features and is a standard interface in many e-mail servers. POP is used for receiving e-mail.
The Host-to-Host layer or Transport layer provides the Application layer with session and datagram communications services. The Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) operate at this layer. These two protocols provide a huge part of the functionality of the TCP/IP network:
- TCP
TCP is responsible for providing a reliable one-to-one connection-oriented session. TCP establishes a connection and ensures that the other end receives any packets. Two hosts communicate packet results to each other. TCP also makes sure that packets are decoded and sequenced properly. This connection is persistent during the session. When the session ends, the connection is broken.
- UDP
UDP provides an unreliable connection-less communication method between hosts. UDP protocol is considered a best-effort protocol, but it's considerably faster than TCP. The sessions don't establish a synchronized session like the kind used in TCP, and UDP doesn't guarantee error-free communications. The primary purpose of UDP is to send small packets of information. The application is responsible for acknowledging the correct reception of the data.
The Internet layer is responsible for routing, IP addressing, and packaging. The Internet layer protocols accomplish most of the behind-the-scenes work in establishing the ability to exchange information between hosts. Here are the four standard protocols of the Internet layer:
- Internet Protocol (IP)
IP is a routable protocol, and it's responsible for IP addressing. IP also fragments and reassembles message packets. IP only routes information; it doesn't verify it for accuracy. Accuracy checking is the responsibility of TCP. IP determines if a destination is known and, if so, routes the information to that destination. If the destination is unknown, IP sends the packet to the router, which sends it on.
- Address Resolution Protocol (ARP)
ARP is responsible for resolving IP addresses to Network Interface layer addresses, including hardware addresses. ARP can resolve an IP address to a Media Access Control (MAC) address. MAC addresses are used to identify hardware network devices such as a Network Interface Card (NIC).
Note
You'll notice the acronym MAC used a lot. The acronym MAC is also used for identify Mandatory Access Control, which defines how access control operates in an authentication model. You'll also see MAC used in cryptography, where it stands for Message Authentication Code. This MAC verifies that an algorithm is accurate.
- Internet Control Message Protocol (ICMP)
ICMP provides maintenance and reporting functions. This protocol is used by the Ping program. When a user wants to test connectivity to another host, they can enter the
PINGcommand with the IP address, and the system will test connectivity to that system. If connectivity is good, ICMP will return data to the originating host. ICMP will also report if a destination is unreachable. Routers and other network devices report path information between hosts with ICMP.- Internet Group Management Protocol (IGMP)
IGMP is responsible primarily for managing IP multicast groups. IP multicasts can send messages or packets to a specified group of hosts. This is different from a broadcast, which all users in a network receive.
The lowest level of the TCP/IP protocol suite is the Network Interface layer. This layer is responsible for placing and removing packets on the physical network through communications with the network adapters in the host. This process allows TCP/IP to work with virtually any type of network topology or technology with little modification. If a new physical network topology were installed—say, a 10GB Fiber Ethernet connection—TCP/IP would only need to know how to communicate with the network controller in order to function properly. TCP/IP can also communicate with more than one network topology simultaneously. This allows the protocol to be used in virtually any environment.
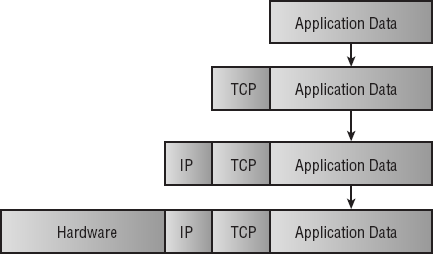
One of the key points in understanding this layering process is the concept of encapsulation. Encapsulation allows a transport protocol to be sent across the network and utilized by the equivalent service or protocol at the receiving host. Figure 2.7 shows how e-mail is encapsulated as it moves from the application protocols through the transport and Internet protocols. Each layer adds header information as it moves down the layers.
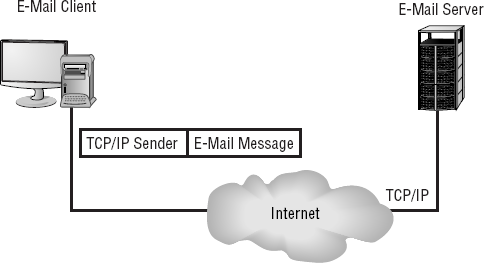
Transmission of the packet between the two hosts occurs through the physical connection in the network adapter. Figure 2.8 illustrates this process between two hosts. Again, this process isn't comprehensive but illustrates the process of message transmission.
Once encapsulated, the message is sent to the server. Notice that in Figure 2.8, the message is sent via the Internet; it could have just as easily been sent locally. The e-mail client doesn't know how the message is delivered, and the server application doesn't care how the message got there. This makes designing and implementing services such as e-mail possible in a global or Internet environment.
It's imperative that you have a basic understanding of protocols and services to pass this exam. Although it isn't a requirement, CompTIA recommends that you already hold the Network+ certification before undertaking this exam. In the event that you're weak in some areas, this section will discuss in more detail how TCP/IP hosts communicate with each other. We'll discuss the concepts of ports, handshakes, and application interfaces. The objective isn't to make you an expert on this subject, but to help you understand what you're dealing with when attempting to secure a TCP/IP network.
Simply stated, ports identify how a communication process occurs. Ports are special addresses that allow communication between hosts. A port number is added from the originator, indicating which port to communicate with on a server. If a server has this port defined and available for use, it will send back a message accepting the request. If the port isn't valid, the server will refuse the connection. The Internet Assigned Numbers Authority (IANA) has defined a list of ports called well-known ports.
Note
You can see the full description of the ports defined by IANA on the following website: www.iana.org. Many thousands of ports are available for use by servers and clients.
A port is nothing more than a bit of additional information added to either the TCP or UDP message. This information is added in the header of the packet. The layer below it encapsulates the message with its header.
Many of the services you'll use in the normal course of utilizing the Internet use the TCP port numbers identified in Table 2.1. Table 2.2 identifies some of the well-known UDP ports that are common.
Table 2.1. Well-Known TCP Ports
TCP Port Number | Service |
|---|---|
20 | FTP (data channel) |
21 | FTP (control channel) |
22 | SSH |
23 | Telnet |
25 | SMTP |
49 | TACACS authentication service |
80 | HTTP (used for the World Wide Web) |
110 | POP3 |
119 | NNTP |
139 | NetBIOS session service |
143 | IMAP |
389 | LDAP |
443 | HTTPS (used for secure web connections) |
Table 2.2. Well-Known UDP Ports
UDP Port Number | Service |
|---|---|
53 | DNS name queries |
69 | Trivial File Transfer Protocol (TFTP) |
137 | NetBIOS name service |
138 | NetBIOS datagram service |
161 | SNMP |
162 | SNMP trap |
The early documentation for these ports specified that ports below 1024 were restricted to administrative uses. However, enforcement of this restriction has been voluntary and is creating problems for computer security professionals. As you can see, each of these ports potentially requires different security considerations depending on the application they're assigned for. All the ports allow access to your network; even if you establish a firewall, you must have these ports open if you want to provide e-mail or web services.
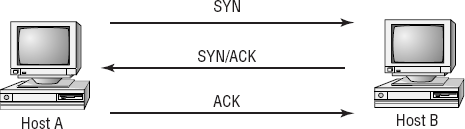
TCP, which is a connection-oriented protocol, establishes a session using a three-way handshake. A host called a client originates this connection. The client sends a TCP segment, or message, to the server. This client segment includes an Initial Sequence Number (ISN) for the connection and a window size. The server responds with a TCP segment that contains its ISN and a window size indicating its buffer or window size. The client then sends back an acknowledgment of the server's sequence number.
Figure 2.9 shows this three-way handshake occurring between a client and a server. When the session or connection is over, a similar process occurs to close the connection.
A web request uses the TCP connection process to establish the connection between the client and the server. After this occurs, the two systems communicate with each other; the server uses TCP port 80. The same thing occurs when an e-mail connection is made, with the difference being that the client (assuming it's using POP3) uses port 110.
In this way, a server can handle many requests simultaneously. Each session has a different sequence number even though all sessions use the same port. All the communications in any given session use this sequence number to keep the sessions from becoming confused.
Interfacing to the TCP/IP protocol is much simpler than interfacing to earlier network models. A well-defined and well-established set of Application Program Interfaces (APIs) are available from most software companies. These APIs allow programmers to create interfaces to the protocol. When a programmer needs to create a web-enabled application, they can call or use one of these APIs to make the connection, send or receive data, and end the connection. The APIs are prewritten, and they make the job considerably easier than manually coding all of the connection information.
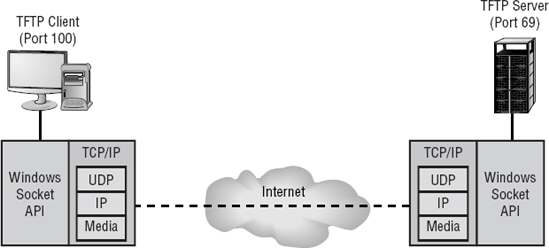
Microsoft uses an API called a Windows socket (WinSock) to interface to the protocol. It can access either TCP or UDP protocols to accomplish the needed task. Figure 2.10 illustrates how the Windows socket connects to the TCP/IP protocol suite.
Attacks on TCP/IP usually occur at the Host-to-Host or Internet layer, although any layer is potentially vulnerable. TCP/IP is susceptible to attacks from both outside and inside an organization.
The opportunities for external attacks are somewhat limited by the devices in the network, including the router. The router blocks many of the protocols from exposure to the Internet. Some protocols, such as ARP, aren't routable and aren't generally vulnerable to outside attacks. Other protocols, such as SMTP and ICMP, pass through the router and form a normal part of Internet and TCP/IP traffic. TCP, UDP, and IP are all vulnerable to attack.
Your network is very exposed to inside attacks. Any network-enabled host has access to the full array of protocols used in the network. A computer with a network card has the ability to act as a network sniffer with the proper configuration and software.
The following sections introduce you to the specific attacks that a TCP/IP-based network is susceptible to when using off-the-shelf software or shareware.
A network sniffer is a device that captures and displays network traffic. Your existing computers have the ability to operate as sniffers. Network cards usually only pass information up to the protocol stack if the information is intended for that computer; any network traffic not intended for that computer is ignored. Most NIC cards can be placed into what is called promiscuous mode, which allows the NIC card to capture all information that it sees on the network. Most networks are bus-oriented, in that all traffic is sent to all internal computer systems. Devices such as routers, bridges, and switches can be used to separate or segment networks within a larger network (known as virtual LANs, or VLANs). Any traffic in a particular segment is visible to all stations in that segment.
Adding a network sniffer such as the one included by Microsoft in its Systems Management Server (SMS) package allows any computer to function as a network sniffer. This software is widely available and is very capable. A number of public domain or shareware sniffers are also available online.
Using a sniffer, an internal attacker can capture all the information transported by the network. Many advanced sniffers can reassemble packets and create entire messages including user IDs and passwords. This vulnerability is particularly acute in environments where network connections are easily accessible to outsiders. For example, an attacker could put a laptop or a portable computer in your wiring closet and attach it to your network.
A TCP/IP network makes many of the ports available to outside users through the router. These ports respond in a predictable manner when queried. For example, TCP attempts synchronization when a session initiation occurs. An attacker can systematically query your network to determine which services and ports are open. This process is called port scanning, and it's part of fingerprinting a network; it can reveal a great deal about your systems. Port scans can be performed both internally and externally. Many routers, unless configured appropriately, will let all protocols pass through them.
Tip
Port scans are used to figure out what services are running on a network.
Individual systems within a network may also have applications and services running that the owner doesn't know about. These services could potentially allow an internal attacker to gain access to information by connecting to that port. Many Microsoft Internet Information Server (IIS) users don't realize the weak security offered by this product. If they didn't install all of the security patches when they installed IIS on their desktops, attackers can exploit the weaknesses of IIS and gain access to information. This has been done in many cases without the knowledge of the owner. These attacks might not technically be considered TCP/IP attacks, but they are, because they use the inherent trust of TCP to facilitate the attacks.
Once they know the IP addresses of your systems, external attackers can attempt to communicate with the ports open in your network, sometimes simply using Telnet.
Note
To check whether a system has a particular protocol or port available, all you have to do is use the telnet command and add the port number. For example, you can check to see if a particular server is running an e-mail server program by entering telnet www.youreintrouble.com 25. This initiates a Telnet connection to the server on port 25. If the server is running SMTP, it will immediately respond with logon information. It doesn't take much to figure out how to talk to SMTP; the interface is well documented. If an e-mail account didn't have a password, this system is now vulnerable to attack.
This process of port scanning can be expanded to develop a footprint of your organization. If your attacker has a single IP address of a system in your network, they can probe all the addresses in the range and probably determine what other systems and protocols your network is utilizing. This allows the attacker to gain knowledge about the internal structure of your network.
Note
A study done by University of Maryland's A. James Clark School of Engineering in 2005 intended to downplay that port scans signal attacks. The numbers found by monitoring two honey pots, however, indicated that 38 percent of attacks were preceded by vulnerability scans. The combination of port scans with vulnerability scans created a lethal combination that often led to an attack.
TCP operates using synchronized connections. The synchronization is vulnerable to attack; this is probably the most common attack used today. As you may recall, the synchronization, or handshake, process initiates a TCP connection. This handshake is particularly vulnerable to a DoS attack referred to as a TCP SYN flood attack. The protocol is also susceptible to access and modification attacks, which are briefly explained in the following sections.
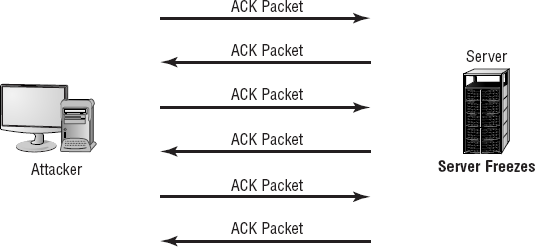
The TCP SYN flood, also referred to as the TCP ACK attack, is very common. The purpose of this attack is to deny service. The attack begins as a normal TCP connection: The client and server exchange information in TCP packets. Figure 2.11 illustrates how this attack occurs. Notice that the TCP client continues to send ACK packets to the server. These ACK packets tell the server that a connection is requested. The server responds with an ACK packet to the client. The client is supposed to respond with another packet accepting the connection, and a session is established.
In this attack, the client continually sends and receives the ACK packets but doesn't open the session. The server holds these sessions open, awaiting the final packet in the sequence. This causes the server to fill up the available sessions and denies other clients the ability to access the resources.
This attack is virtually unstoppable in most environments without working with upstream providers. Many newer routers can track and attempt to prevent this attack by setting limits on the length of an initial session to force sessions that don't complete to close out. This type of attack can also be undetectable. An attacker can use an invalid IP address, and TCP won't care because TCP will respond to any valid request presented from the IP layer.
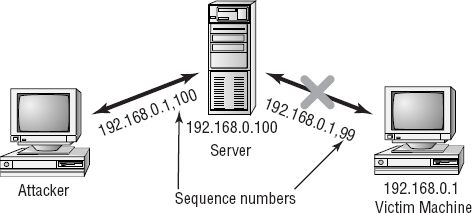
TCP sequence number attacks occur when an attacker takes control of one end of a TCP session. This attack is successful when the attacker kicks the attacked end off the network for the duration of the session. Each time a TCP message is sent, either the client or the server generates a sequence number. In a TCP sequence number attack, the attacker intercepts and then responds with a sequence number similar to the one used in the original session. This attack can either disrupt or hijack a valid session. If a valid sequence number is guessed, the attacker can place himself between the client and server. Figure 2.12 illustrates a sequence number attack in process against a server. In this example, the attacker guesses the sequence number and replaces a real system with their own.
In this case, the attacker effectively hijacks the session and gains access to the session privileges of the victim's system. The victim's system may get an error message indicating that it has been disconnected, or it may reestablish a new session. In this case, the attacker gains the connection and access to the data from the legitimate system. The attacker then has access to the privileges established by the session when it was created.
This weakness is again inherent in the TCP protocol, and little can be done to prevent it. Your major defense against this type of attack is knowing that it's occurring. Such an attack is also frequently a precursor to a targeted attack on a server or network.
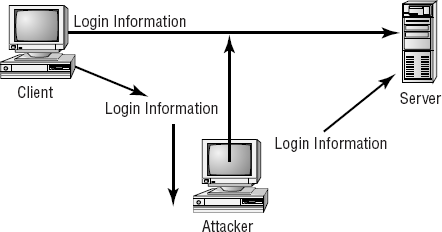
TCP/IP hijacking, also called active sniffing, involves the attacker gaining access to a host in the network and logically disconnecting it from the network. The attacker then inserts another machine with the same IP address. This happens quickly and gives the attacker access to the session and to all the information on the original system. The server won't know this has occurred and will respond as if the client is trusted. Figure 2.13 shows how TCP/IP hijacking occurs. In this example, the attacker forces the server to accept its IP address as valid.
TCP/IP hijacking presents the greatest danger to a network because the hijacker will probably acquire privileges and access to all the information on the server. As with a sequence number attack, there is little you can do to counter the threat. Fortunately, these attacks require fairly sophisticated software and are harder to engineer than a DoS attack, such as a TCP SYN attack.
A UDP attack attacks either a maintenance protocol or a UDP service in order to overload services and initiate a DoS situation. UDP attacks can also exploit UDP protocols.
Note
One of the most popular UDP attacks is the ping of death discussed earlier in the section, "Identifying Denial-of-Service (DoS) and Distributed DoS (DDoS) Attacks."
UDP packets aren't connection oriented and don't require the synchronization process described in the previous section. UDP packets, however, are susceptible to interception, and UDP can be attacked. UDP, like TCP, doesn't check the validity of IP addresses. The nature of this layer is to trust the layer below it, the IP layer.
The most common UDP attacks involve UDP flooding. UDP flooding overloads services, networks, and servers. Large streams of UDP packets are focused at a target, causing the UDP services on that host to shut down. UDP floods also overload the network bandwidth and cause a DoS situation to occur.
ICMP attacks occur by triggering a response from the ICMP protocol when it responds to a seemingly legitimate maintenance request. From earlier discussions, you'll recall that ICMP is often associated with echoing.
ICMP supports maintenance and reporting in a TCP/IP network. It's part of the IP level of the protocol suite. Several programs, including Ping, use the ICMP protocol. Until fairly recently, ICMP was regarded as a benign protocol that was incapable of much damage. However, it has now joined the ranks of common attack methods used in DoS attacks. Two primary methods use ICMP to disrupt systems: smurf attacks and ICMP tunneling.
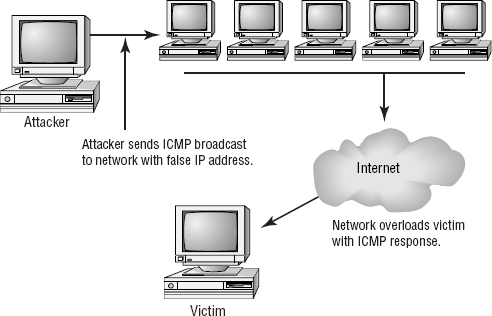
Smurf attacks are becoming common and can create havoc in a network. A smurf attack uses IP spoofing and broadcasting to send a ping to a group of hosts in a network. When a host is pinged, it sends back ICMP message traffic information indicating status to the originator. If a broadcast is sent to a network, all of the hosts will answer back to the ping. The result is an overload of the network and the target system.
Figure 2.14 shows a smurf attack under way in a network. The attacker sends a broadcast message with a legal IP address. In this case, the attacking system sends a ping request to the broadcast address of the network. This request is sent to all the machines in a large network. The reply is then sent to the machine identified with the ICMP request (the spoof is complete). The result is a DoS attack that consumes the network bandwidth of the replying system, while the victim system deals with the flood of ICMP traffic it receives.
Smurf attacks are very popular. The primary method of eliminating them involves prohibiting ICMP traffic through a router. If the router blocks ICMP traffic, smurf attacks from an external attacker aren't possible.
ICMP messages can contain data about timing and routes. A packet can be used to hold information that is different from the intended information. This allows an ICMP packet to be used as a communications channel between two systems. The channel can be used to send a Trojan horse or other malicious packet. This is a relatively new opportunity to create havoc and mischief in networks.
The countermeasure for ICMP attacks is to deny ICMP traffic through your network. You can disable ICMP traffic in most routers, and you should consider doing so in your network.
Tip
Many of the newer SOHO router solutions (and some of the Personal Firewall Solutions on end-user workstations) close down the ICMP ports by default. Keep this in mind as it can drive you nuts when you are trying to see if a brand new station/server/router is up and running.
The term software exploitation refers to attacks launched against applications and higher-level services. They include gaining access to data using weaknesses in the data access objects of a database or a flaw in a service. This section briefly outlines some common exploitations that have been successful in the past. The following exploitations can be introduced using viruses, as in the case of the Klez32 virus, or by using access attacks described earlier in this chapter.
- Database exploitation
Many database products allow sophisticated access queries to be made in the client/server environment. If a client session can be hijacked or spoofed, the attacker can formulate queries against the database that disclose unauthorized information. For this attack to be successful, the attacker must first gain access to the environment through one of the attacks outlined previously.
- Application exploitation
The macro virus is another example of software exploitation. A macro virus is a set of programming instructions in a language such as VBScript that commands an application to perform illicit instructions. Users want more powerful tools, and manufacturers want to sell users what they want. The macro virus takes advantage of the power offered by word processors, spreadsheets, or other applications. This exploitation is inherent in the product, and all users are susceptible to it unless they disable all macros.
- E-mail exploitation
Hardly a day goes by without another e-mail virus being reported. This is a result of a weakness in many common e-mail clients. Modern e-mail clients offer many shortcuts, lists, and other capabilities to meet user demands. A popular exploitation of e-mail clients involves accessing the client address book and propagating viruses. There is virtually nothing a client user can do about these exploitations, although antivirus software that integrates with your e-mail client does offer some protection. To be truly successful, the software manufacturer must fix the weaknesses—an example is Outlook's option to protect against access to the address book. This type of weakness isn't a bug, in many cases, but a feature that users wanted.
Warning
Users should always be taught to exercise discretion when opening any e-mail attachment.
- Spyware
Spyware differs from other malware in that it works—often actively—on behalf of a third party. Rather than self-replicating, like viruses and worms, spyware is spread to machines by users who inadvertently ask for it. The users often do not know they have asked for it, but have done so by downloading other programs, visiting infected sites, and so on.
The spyware program monitors the user's activity and responds to them by offering unsolicited pop-up advertisements (sometimes known as adware), gathers information about them to pass on to marketers, or intercepts personal data such as credit card numbers. One thing separating spyware from most other malware is that it almost always exists to provide commercial gain. The operating systems from Microsoft are the ones most affected by spyware, and Microsoft has released Microsoft AntiSpyware to combat the problem.
- Rootkits
Recently, rootkits have become the software exploitation program du jour. Rootkits are software programs that have the ability to hide certain things from the operating system. With a rootkit, there may be a number of processes running on a system that do not show up in Task Manager, or connections established or available that do not appear in a
netstatdisplay—the rootkit masks the presence of these items. The rootkit is able to do this by manipulating function calls to the operating system and filtering out information that would normally appear.Unfortunately, many rootkits are written to get around antivirus and antispyware programs that are not kept up to date. The best defense you have is to monitor what your system is doing and catch the rootkit in the process of installation.
Tip
As these new threats have developed, so have some excellent programs for countering them. Within any search engine, you can find a rootkit analyzer for your system. I also highly recommend Spybot, Spyware Doctor, and AdAware.
One of the most important measures you can take to proactively combat software attacks is to know common file extensions and the applications they're associated with. For example, .scr files are screensavers, and viruses are often distributed through the use of these files. No legitimate user should be sending screensavers via e-mail to your users, and all .scr attachments should be banned from entering the network.
Table 2.3, while not comprehensive, contains the most common file extensions that should or should not, as a general rule, be allowed into the network as e-mail attachments.
Malicious code refers to a broad category of software threats to your network and systems. These threats include viruses, Trojan horses, bombs, and worms. Your users depend on you to help keep them safe from harm and to repulse these attacks. When successful, these attacks can be devastating to systems, and they can spread through an entire network. One such incident involved the Melissa virus that effectively brought the entire Internet down for a few days in March 1999. This virus spread to millions of Outlook and Outlook Express users worldwide. Variants of this virus are still propagating through the Internet.
The following sections will briefly introduce you to the types of malicious code you'll encounter, including viruses, Trojan horses, logic bombs, and worms. We'll also explain the importance of antivirus software.
A virus is a piece of software designed to infect a computer system. The virus may do nothing more than reside on the computer. A virus may also damage the data on your hard disk, destroy your operating system, and possibly spread to other systems. Viruses get into your computer in one of three ways: on a contaminated floppy or CD-ROM, through e-mail, or as part of another program.
Viruses can be classified as several types: polymorphic, stealth, retroviruses, multipartite, armored, companion, phage, and macro viruses. Each type of virus has a different attack strategy and different consequences.
Note
Estimates for losses due to viruses are in the billions of dollars. These losses include funds as well as lost productivity.
The following sections will introduce the symptoms of a virus infection, explain how a virus works, and describe the types of viruses you can expect to encounter and how they generally behave. We'll also discuss how a virus is transmitted through a network and look at a few hoaxes.
Many viruses will announce that you're infected as soon as they gain access to your system. These viruses may take control of your system and flash annoying messages on your screen or destroy your hard disk. When this occurs, you'll know that you're a victim. Other viruses will cause your system to slow down, cause files to disappear from your computer, or take over your disk space.
You should look for some of the following symptoms when determining if a virus infection has occurred:
The programs on your system start to load more slowly. This happens because the virus is spreading to other files in your system or is taking over system resources.
Unusual files appear on your hard drive, or files start to disappear from your system. Many viruses delete key files in your system to render it inoperable.
Program sizes change from the installed versions. This occurs because the virus is attaching itself to these programs on your disk.
Your browser, word processing application, or other software begins to exhibit unusual operating characteristics. Screens or menus may change.
The system mysteriously shuts itself down or starts itself up and does a great deal of unanticipated disk activity.
You mysteriously lose access to a disk drive or other system resources. The virus has changed the settings on a device to make it unusable.
Your system suddenly doesn't reboot or gives unexpected error messages during startup.
This list is by no means comprehensive.
A virus, in most cases, tries to accomplish one of two things: render your system inoperable or spread to other systems. Many viruses will spread to other systems given the chance and then render your system unusable. This is common with many of the newer viruses.
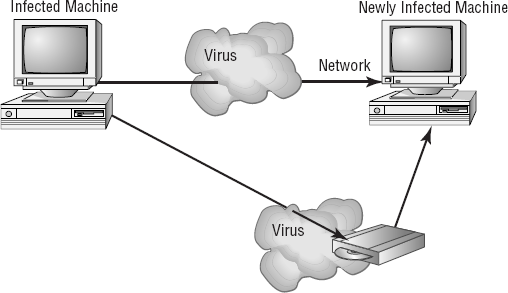
If your system is infected, the virus may try to attach itself to every file in your system and spread each time you send a file or document to other users. Figure 2.15 shows a virus spreading from an infected system either through a network or by removable media. When you give this disk to another user or put it into another system, you then infect that system with the virus.
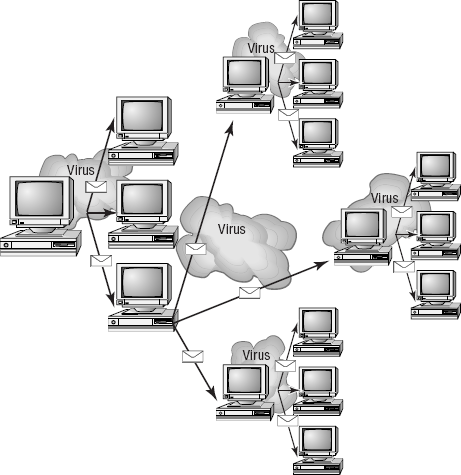
Many newer viruses spread using e-mail. The infected system includes an attachment to any e-mail that you send to another user. The recipient opens this file, thinking it's something you legitimately sent them. When they open the file, the virus infects the target system. This virus may then attach itself to all the e-mails the newly infected system sends, which in turn infect the recipients of the e-mails. Figure 2.16 shows how a virus can spread from a single user to literally thousands of users in a very short time using e-mail.
Viruses take many different forms. This section briefly introduces these forms and explains how they work. These are the most common types, but this isn't a comprehensive list.
Polymorphic viruses change form in order to avoid detection. These types of viruses attack your system, display a message on your computer, and delete files on your system. The virus will attempt to hide from your antivirus software. Frequently, the virus will encrypt parts of itself to avoid detection. When the virus does this, it's referred to as mutation. The mutation process makes it hard for antivirus software to detect common characteristics of the virus. Figure 2.17 shows a polymorphic virus changing its characteristics to avoid detection. In this example, the virus changes a signature to fool antivirus software.
A stealth virus attempts to avoid detection by masking itself from applications. It may attach itself to the boot sector of the hard drive. When a system utility or program runs, the stealth virus redirects commands around itself in order to avoid detection. An infected file may report a file size different from what is actually present in order to avoid detection. Figure 2.18 shows a stealth virus attaching itself to the boot sector to avoid detection. Stealth viruses may also move themselves from fileA to fileB during a virus scan for the same reason.
A retrovirus attacks or bypasses the antivirus software installed on a computer. You can consider a retrovirus to be an anti-antivirus. Retroviruses can directly attack your antivirus software and potentially destroy the virus definition database file. Destroying this information without your knowledge would leave you with a false sense of security. The virus may also directly attack an antivirus program to create bypasses for the virus.
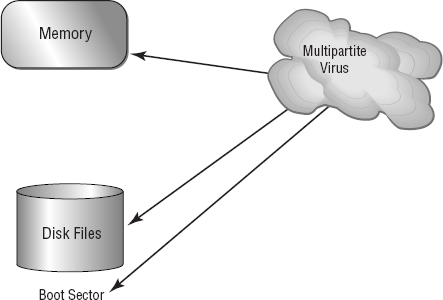
A multipartite virus attacks your system in multiple ways. It may attempt to infect your boot sector, infect all of your executable files, and destroy your applications files. The hope here is that you won't be able to correct all the problems and will allow the infestation to continue. The multipartite virus in Figure 2.19 attacks your boot sector, infects applications files, and attacks your Microsoft Word documents.
An armored virus is designed to make itself difficult to detect or analyze. Armored viruses cover themselves with protective code that stops debuggers or disassemblers from examining critical elements of the virus. The virus may be written in such a way that some aspects of the programming act as a decoy to distract analysis while the actual code hides in other areas in the program.
From the perspective of the creator, the more time it takes to deconstruct the virus, the longer it can live. The longer it can live, the more time it has to replicate and spread to as many machines as possible. The key to stopping most viruses is to identify them quickly and educate administrators about them—the very things that the armor intensifies the difficulty of accomplishing.
A companion virus attaches itself to legitimate programs and then creates a program with a different file extension. This file may reside in your system's temporary directory. When a user types the name of the legitimate program, the companion virus executes instead of the real program. This effectively hides the virus from the user. Many of the viruses that are used to attack Windows systems make changes to program pointers in the Registry so that they point to the infected program. The infected program may perform its dirty deed and then start the real program.
A phage virus modifies and alters other programs and databases. The virus infects all of these files. The only way to remove this virus is to reinstall the programs that are infected. If you miss even a single incident of this virus on the victim system, the process will start again and infect the system once more.
A macro virus exploits the enhancements made to many application programs. Programs such as Word and Excel allow programmers to expand the capability of the application. Word, for example, supports a mini-BASIC programming language that allows files to be manipulated automatically. These programs in the document are called macros. For example, a macro can tell your word processor to spell-check your document automatically when it opens. Macro viruses can infect all the documents on your system and spread to other systems using mail or other methods. Macro viruses are the fastest growing exploitation today.
Upon infection, some viruses destroy the target system immediately. The saving grace is that the infection can be detected and corrected. Some viruses won't destroy or otherwise tamper with a system; they use the victim system as a carrier. The victim system then infects servers, file shares, and other resources with the virus. The carrier then infects the target system again. Until the carrier is identified and cleaned, the virus continues to harass systems in this network and spread.
Network users have plenty of real viruses to worry about. Yet some people find it entertaining to issue phony threats to keep people on their toes. Some of the more popular hoaxes that have been passed around are the Good Time and the Irina viruses. Millions of users received e-mails about these two viruses, and the symptoms sounded awful.
Both of these viruses claimed to do things that are impossible to accomplish with a virus. When you receive a virus warning, you can verify its authenticity by looking on the website of the antivirus software you use, or you can go to several public systems. One of the more helpful sites to visit to get the status of the latest viruses is the CERT organization (www.cert.org). CERT monitors and tracks viruses and provides regular reports on this site.
When you receive an e-mail you suspect is a hoax, check the CERT site before forwarding the message to anyone else. The creator of the hoax wants to create widespread panic, and if you blindly forward the message to coworkers and acquaintances, you're helping the creator accomplish their task. For example, any e-mail that says "forward to all your friends" is a candidate for hoax research. Disregarding the hoax allows it die a quick death and keeps users focused on productive tasks.
Tip
Symantec and other vendors maintain pages devoted to bogus hoaxes (www.symantec.com/avcenter/hoax.html). You can always check there to verify whether an e-mail you've received is indeed a hoax.
While spam is not truly a virus or a hoax, it is one of the most annoying things an administrator can contend with. Spam is defined as any unwanted, unsolicited email, and not only can the sheer volume of it be irritating, but it can often open the door to larger problems. Some of the sites advertised in spam may be infected with viruses, worms, and other unwanted programs. If users begin to respond to spam by visiting those sites, then your problems will only multiple.
Just as you can, and must, install good antivirus software programs, you should also consider similar measures for spam. Filtering the messages out and preventing them from ever entering the network is the most effective method of dealing with the problem.
Trojan horses are programs that enter a system or network under the guise of another program. A Trojan horse may be included as an attachment or as part of an installation program. The Trojan horse could create a back door or replace a valid program during installation. It would then accomplish its mission under the guise of another program. Trojan horses can be used to compromise the security of your system, and they can exist on a system for years before they're detected.
The best preventive measure for Trojan horses is to not allow them entry into your system. Immediately before and after you install a new software program or operating system, back it up! If you suspect a Trojan horse, you can reinstall the original programs, which should delete the Trojan horse. A port scan may also reveal a Trojan horse on your system. If an application opens a TCP or IP port that isn't supported in your network, you can track it down and determine which port is being used.
Tip
Is a Trojan horse also a virus? A Trojan horse is anything that sneaks in under the guise of something else. Given that general definition, it's certainly possible that a virus can (and usually does) sneak in, but this description most often fits the definition of a companion virus. The primary distinction, from an exam perspective, is that with a Trojan horse you always intentionally obtained something (usually an application) and didn't know an unpleasant freeloader was hidden within. An example is spyware, which is often installed (unknown to you) as part of another application.
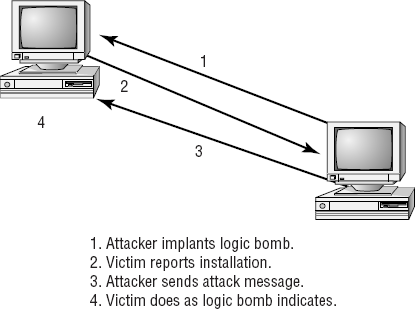
Logic bombs are programs or snippets of code that execute when a certain predefined event occurs. A bomb may send a note to an attacker when a user is logged on to the Internet and is using a word processor. This message informs the attacker that the user is ready for an attack.
Figure 2.20 shows a logic bomb in operation. Notice that this bomb doesn't begin the attack, but tells the attacker that the victim has met the needed criteria or state for an attack to begin. Logic bombs may also be set to go off on a certain date or when a specified set of circumstances occurs.
In the attack depicted in Figure 2.20, the logic bomb sends a message back to the attacking system that the logic bomb has loaded successfully. The victim system can then be either used to initiate an attack such as a DDoS attack, or they can grant access at the time of the attacker's choosing.
A worm is different from a virus in that it can reproduce itself, it's self-contained, and it doesn't need a host application to be transported. Many of the so-called viruses that have made the papers and media were, in actuality, worms and not viruses. However, it's possible for a worm to contain or deliver a virus to a target system.
Note
The Melissa virus (which was actually a worm) spread itself to more than 100,000 users in a relatively short period when it first came out, according to CERT. One site received more than 32,000 copies of the Melissa virus in a 45-minute period.
Worms by their nature and origin are supposed to propagate and will use whatever services they're capable of to do that. Early worms filled up memory and bred inside the RAM of the target computer. Worms can use TCP/IP, e-mail, Internet services, or any number of possibilities to reach their target.
Note
In recent years, one of the most common worms is Sober and different variants of it. It spreads to as many systems as possible, then lies dormant on each system until a specific date is reached (anniversary of the launch of the Nazi party, for example). When the date arrives, it reenergizes its efforts, sending out copies at a rapid pace and triggering the system to download additional infected code.
The primary method of preventing the propagation of malicious code involves the use of anti-virus software. Antivirus software is an application that is installed on a system to protect it and to scan for viruses as well as worms and Trojan horses. Most viruses have characteristics that are common to families of virus. Antivirus software looks for these characteristics or fingerprints to identify and neutralize viruses before they impact you.
More than 60,000 known viruses, worms, bombs, and other malicious codes have been defined. New ones are added all the time. Your antivirus software manufacturer will usually work very hard to keep the definition database files current. The definition database file contains all of the known viruses and countermeasures for a particular antivirus software product. You probably won't receive a virus that hasn't been seen by one of these companies. If you keep the virus definition database files in your software up to date, you probably won't be overly vulnerable to attacks.
Tip
The best method of protection is to use a layered approach. Antivirus software should be at the gateways, at the servers, and at the desktop. If you want to go one step further, you can use software at each location from different vendors to make sure you're covered from all angles.
The second method of preventing viruses is education. Teach your users not to open suspicious files and to open only those files that they're reasonably sure are virus free. They need to scan every disk, e-mail, and document they receive before they open them.
In the previous sections, you learned how attacks work. You also learned about TCP/IP and some of its vulnerabilities. You were also exposed to the issues that your users will face so you can help them from a technical perspective. A key method of attack that you must guard against is called social engineering.
Social engineering is a process in which an attacker attempts to acquire information about your network and system by social means, such as talking to people in the organization. A social engineering attack may occur over the phone, by e-mail, or by a visit. The intent is to acquire access information, such as user IDs and passwords.
Tip
Always think of a social engineering attack as one that involves others who are unwitting.
These types of attacks are relatively low-tech and are more akin to con jobs. Take the following example. Your Help Desk gets a call at 4:00 a.m. from someone purporting to be the vice president of your company. She tells the Help Desk personnel that she is out of town to attend a meeting, her computer just failed, and she is sitting in a Kinko's trying to get a file from her desktop computer back at the office. She can't seem to remember her password and user ID. She tells the Help Desk representative that she needs access to the information right away or the company could lose millions of dollars. Your Help Desk rep knows how important this meeting is and gives the vice president her user ID and password over the phone.
Another common approach is initiated by a phone call or e-mail from your software vendor, telling you that they have a critical fix that must be installed on your computer system. If this patch isn't installed right away, your system will crash and you'll lose all your data. For some reason, you've changed your maintenance account password and they can't log on. Your systems operator gives the password to the person. You've been hit again.
Note
Users are bombarded with e-mails and messages on services such as AOL asking them to confirm the password they use. These attacks appear to come from the administrative staff of the network. The attacker already has the user ID or screen name; all they need to complete the attack is the password. Make sure your users never give their user IDs or passwords. Either case potentially completes an attack.
With social engineering, the villain doesn't always have to be seen or heard to conduct the attack. The use of e-mail was mentioned earlier, and in recent years the frequency of attacks via instant messaging has also increased. Attackers can send infected files over Instant Messaging (IM) as easily as they can over e-mail. A recent virus on the scene accesses a user's IM and communicates with them as if it were a person trying to communicate. It then uses the infected user's buddy list to send messages to other users and infect their machines as well.
Note
According to IMlogic (www.imlogic.com), the number of IM-related security threats went from 134 in 2004 to 2,403 in 2005.
Phishing is a form of social engineering in which you simply ask someone for a piece of information that you are missing by making it look as if it is a legitimate request. An e-mail may look as if it is from a bank and contain some basic information, such as the user's name. In the e-mail, it will often state that there is a problem with the person's account, access, or some such other issue. They will be told to click on a link to correct the problem. Once they click on the link—which goes to a site other than the bank's—they are asked for their user-name, password, account information, and so on. The person instigating the phishing can then use the values entered there to access the legitimate account.
Tip
One of the best counters to phishing is to simply mouse over the Click Here link and read the URL. Almost every time it is pointing to an adaptation of the legitimate URL as opposed to a link to the real thing.
The only preventive measure in dealing with social engineering attacks is to educate your users and staff to never give out passwords and user IDs over the phone, via e-mail, or to anyone who isn't positively verified as being who they say the are. Social engineering is a recurring topic that will appear several times throughout this book as it relates to the subject being discussed at that time.
Most systems generate security logs and audit files of activity on the system. These files do absolutely no good if they aren't periodically reviewed for unusual events. Many web servers provide message auditing, as do logon, system, and application servers.
The amount and volume of information these files contain can be overwhelming. You should establish a procedure to review them on a regular basis.
Note
A rule of thumb is to never start auditing by trying to record everything, because the sheer volume of the entries will make the data unusable. Approach auditing from the opposite perspective and begin auditing only a few key things, and then expand the audits as you find you need more data.
These files may also be susceptible to access or modification attacks. The files often contain critical systems information, including resource sharing, security status, and so on. An attacker may be able to use this information to gather more detailed data about your network.
In an access attack, these files can be deleted, modified, and scrambled to prevent systems administrators from knowing what happened in the system. A logic bomb could, for example, delete these files when it completes. Administrators might know that something happened, but they would get no clues or assistance from the log and audit files.
You should consider periodically inspecting systems to see what software is installed and whether passwords are posted on sticky notes on monitors or keyboards. A good way to do this without attracting attention is to clean all the monitor faces. While you're cleaning the monitors, you can also verify that physical security is being upheld. If you notice a password on a sticky note, you can "accidentally" forget to put it back. You should also notify that user that this is an unsafe practice and not to continue it.
You should also consider obtaining a vulnerability scanner and running it across your network. A vulnerability scanner is a software application that checks your network for any known security holes; it's better to run one on your own network before someone outside the organization runs it against you. One of the best-known vulnerability scanners is SAINT—Security Administrator's Integrated Network Tool.
This chapter focused on the types of attacks you'll encounter and your network's vulnerabilities. You learned the areas where your network is most vulnerable, including:
Attack methods
TCP/IP
Malicious code
Social engineering
Attack methods include denial of service, distributed denial of service, back door attacks, spoofing attacks, man-in-the-middle attacks, and replay attacks. Each of these attacks takes advantage of inherent weaknesses in the network technologies most commonly used today.
TCP/IP is particularly vulnerable to attacks at the Host-to-Host or Transport layer and the IP layer. Transport layer attacks are designed to take advantage of the synchronization method used by TCP, the unsynchronized characteristics of UDP, and the maintenance messages generated by ICMP.
Common attacks on TCP include the SYN or ACK flood attack, TCP sequence number attack, and TCP/IP hijacking.
UDP is vulnerable to flooding attacks. Flooding attacks are DoS attacks, and they're designed to prevent access by authorized users.
TCP/IP uses protocols and services at each layer of the network model. These protocols and services offer ports to receive and send messages to other services or applications. The ports are vulnerable to attack depending on the protocol. Thousands of ports are available for use in TCP/IP. The ports numbered below 1024 are considered well known, and they usually require administrative access to be used.
Applications interface with the TCP/IP protocol suite using either APIs or Windows sockets. These interfaces are well established and published.
Each layer of the protocol suite communicates with the layers above and below it. The process of preparing a message for transmission involves adding headers as the packet moves down this stream. This process is called encapsulation.
Malicious code describes an entire family of software that has nefarious intentions in your networks and computers. This includes viruses, Trojan horses, logic bombs, and worms. Viruses and worms are becoming a major problem on the Internet. The best prevention methods available include antivirus software and user education.
The process of using human intelligence to acquire access to information and systems is called social engineering. Social engineering involves someone contacting a member of the organization and attempting to con them out of account and password information. The best method of minimizing social engineering attacks is user education and positive verification of the identity of the person committing the attack.
Audit files and system logs are a very effective manner of tracking activity in a network or on a server. These logs should be reviewed regularly to identify if unauthorized activity is occurring. Systems should be routinely inspected to verify whether physical security procedures are being followed.
- Be able to describe the various types of attacks to which your systems are exposed.
Your network is vulnerable to DoS attacks caused by either a single system or multiple systems. Multiple system attacks are called distributed DDoS. Your systems are also susceptible to access, modification, and repudiation attacks.
- Be able to describe the methods used to conduct a back door attack.
Back door attacks occur using either existing maintenance hooks or developmental tools to examine the internal operations of a program. These hooks are usually removed when a product is prepared for market or production. Back door attacks also refer to the insertion of a program or service into a machine that allows authentication to be bypassed and access gained.
- Be able to describe how a spoofing attack occurs.
Spoofing attacks occur when a user or system masquerades as another user or system. Spoofing allows the attacker to assume the privileges and access rights of the real user or system.
- Be able to describe a man-in-the-middle attack.
Man-in-the-middle attacks are based on the principle that a system can be placed between two legitimate users to capture or exploit the information being sent between them. Both sides of the conversation assume that the man in the middle is the other end and communicate normally. This creates a security breach and allows unauthorized access to information.
- Be able to describe a replay attack.
A replay attack captures information from a previous session and attempts to resend it to gain unauthorized access. This attack is based on the premise that if it worked once, it will work again. This is especially effective in environments where a user ID and password are sent in the clear across a large network.
- Be able to describe a TCP/IP hijacking.
TCP/IP hijacking occurs when an unauthorized system replaces the authorized system without being detected. This allows access privileges to be kept in the session. Hijacking attacks are hard to detect because everything appears to be normal, except the hijacked system. Hijacking attacks take advantage of the sequencing numbers used in TCP sessions.
- Be able to explain how social engineering occurs.
Social engineering describes a process where an unauthorized person attempts to gain access to information by asking the Help Desk or other employees for account and password information. This assault typically occurs by the attacker representing himself or herself as someone who would legitimately have a right to that information.
- Be able to describe the two methods used in password guessing.
The two methods used to guess passwords are brute force and dictionary. Brute-force attacks work by trying to randomly guess a password repeatedly against a known account ID. Dictionary methods apply a set of words, such as a dictionary, against the identified account.
- Be able to explain how software exploitation occurs.
Software exploitation involves using features or capabilities of a software product in a manner either unplanned for or unanticipated by the software manufacturer. In many cases, the original feature enhanced the functionality of the product but, unfortunately, creates a potential vulnerability.
- Be able to explain the characteristics and types of viruses used to disrupt systems and networks.
Several different types of viruses are floating around today. The most common ones include polymorphic viruses, stealth viruses, retroviruses, multipartite viruses, and macro viruses.
- Be able to explain the characteristics of Trojan horses and logic bombs.
Trojan horses are programs that enter a system or network under the guise of another program. Logic bombs are programs or snippets of code that execute when a certain predefined event occurs.
- Be able to describe how worms operate.
Worms attack systems and attempt to procreate and propagate. Worms spread using files, e-mail, and physical media, such as a floppy disk. A worm will also frequently contain a virus that causes the destruction of a system.
- Be able to describe how antivirus software operates.
Antivirus software looks for a signature in the virus to determine what type of virus it is. The software then takes action to neutralize the virus based on a virus definition database. Virus definition database files are regularly made available on vendor sites.
- Be able to describe how audit files can help detect unauthorized activity on a system or network.
Most operating systems provide a number of audit files to record the results of activities on a system. These log files will frequently contain unsuccessful logon attempts, as well as excessive network traffic. These files should be reviewed on a regular basis to determine what is happening on a system or a network.
It is important to know what processes are running on a machine at any given time. In addition to the programs that a user may be using, there are always many others that are required by the operating system, the network, or other applications.
All recent versions of Windows—Windows Server 2003, Windows 2000, Windows XP—include the Task Manager to allow you to see what is running. To access this information, follow these steps:
Right-click on an empty location in the Windows taskbar.
Choose Task Manager from the pop-up menu that appears.
The default is to open to Applications and show what the user is actually using. Click the Processes tab. Information about the programs that are needed for the running applications is shown, as well as all other processes running. (If the checkbox Show Processes From All Users appears beneath this tab, be sure to click it.) Many of the names of the processes will appear cryptic, but definitions for most (good and bad) can be found at
http://www.liutilities.com/products/wintaskspro/processlibrary/.Examine the list and look for anything out of the ordinary. After doing this a few times, you will become familiar with what is normally there and will be able to spot oddities quickly.
Notice the values in the CPU column. Those values will always total 100, with System Idle Processes typically making up the bulk. High numbers on another process can indicate that there is a problem with it. If the numbers do not add up to 100, it can be a sign that a rootkit is masking some of the display.
Close the Task Manager.
Most versions of Linux include a graphical utility to allow you to see the running processes. Those utilities differ based on the distribution of Linux you are using and the desktop that you have chosen.
All versions of Linux, however, do offer a command line and the ability to use the ps utility. Because of that, this is the method employed in this lab. To access this information, follow these steps:
Open a shell window, or otherwise access a command prompt.
Type ps –ef | more.
The display shows the processes running for all users. The names of the processes will appear in the rightmost column, and the processor time will be in the column closest to it. The names are cryptic, but definitions for most can be found by using the
mancommand followed by the name of the process. Those that are application specific can usually be found through a web search.Examine the list and look for anything out of the ordinary. After doing this a few times, you will become familiar with what is normally there and will be able to spot oddities quickly.
Pay particular attention to those processes associated with the root user (the user appears in the first column). Since the root user has the power to do anything, only necessary daemons and processes should be associated with that user.
Exit the shell.
Which type of attack denies authorized users access to network resources?
DoS
Worm
Logic bomb
Social engineering
As the security administrator for your organization, you must be aware of all types of attacks that can occur and plan for them. Which type of attack uses more than one computer to attack the victim?
DoS
DDoS
Worm
UDP attack
A server in your network has a program running on it that bypasses authorization. Which type of attack has occurred?
DoS
DDoS
Back door
Social engineering
An administrator at a sister company calls to report a new threat that is making the rounds. According to him, the latest danger is an attack that attempts to intervene in a communications session by inserting a computer between the two systems that are communicating. Which of the following types of attacks does this constitute?
Man-in-the-middle attack
Back door attack
Worm
TCP/IP hijacking
You've discovered that an expired certificate is being used repeatedly to gain logon privileges. Which type of attack is this most likely to be?
Man-in-the-middle attack
Back door attack
Replay attack
TCP/IP hijacking
A junior administrator comes to you in a panic. After looking at the log files, he has become convinced that an attacker is attempting to use an IP address to replace another system in the network to gain access. Which type of attack is this?
Man-in-the-middle attack
Back door attack
Worm
TCP/IP hijacking
A server on your network will no longer accept connections using the TCP protocol. The server indicates that it has exceeded its session limit. Which type of attack is probably occurring?
TCP ACK attack
Smurf attack
Virus attack
TCP/IP hijacking
A smurf attack attempts to use a broadcast ping on a network; the return address of the ping may be a valid system in your network. Which protocol does a smurf attack use to conduct the attack?
TCP
IP
UDP
ICMP
Your Help Desk has informed you that they received an urgent call from the vice president last night requesting his logon ID and password. What type of attack is this?
Spoofing
Replay attack
Social engineering
Trojan horse
A user calls you in a panic. He is receiving e-mails from people indicating that he is inadvertently sending viruses to them. Over 200 such e-mails have arrived today. Which type of attack has most likely occurred?
SAINT
Back door attack
Worm
TCP/IP hijacking
Your system has just stopped responding to keyboard commands. You noticed that this occurred when a spreadsheet was open and you dialed in to the Internet. Which kind of attack has probably occurred?
Logic bomb
Worm
Virus
ACK attack
You're explaining the basics of security to upper management in an attempt to obtain an increase in the networking budget. One of the members of the management team mentions that they've heard of a threat from a virus that attempts to mask itself by hiding code from antivirus software. What type of virus is he referring to?
Armored virus
Polymorphic virus
Worm
Stealth virus
What kind of virus could attach itself to the boot sector of your disk to avoid detection and report false information about file sizes?
Trojan horse virus
Stealth virus
Worm
Polymorphic virus
A mobile user calls you from the road and informs you that his laptop is exhibiting erratic behavior. He reports that there were no problems until he downloaded a tic-tac-toe program from a site that he had never visited before. Which of the following terms describes a program that enters a system disguised in another program?
Trojan horse virus
Polymorphic virus
Worm
Armored virus
Your system has been acting strangely since you downloaded a file from a colleague. Upon examining your antivirus software, you notice that the virus definition file is missing. Which type of virus probably infected your system?
Polymorphic virus
Retrovirus
Worm
Armored virus
Internal users are reporting repeated attempts to infect their systems as reported to them by pop-up messages from their virus scanning software. According to the pop-up messages, the virus seems to be the same in every case. What is the most likely culprit?
A server is acting as a carrier for a virus.
You have a worm virus.
Your antivirus software has malfunctioned.
A DoS attack is under way.
Your system log files report an ongoing attempt to gain access to a single account. This attempt has been unsuccessful to this point. What type of attack are you most likely experiencing?
Password guessing attack
Back door attack
Worm attack
TCP/IP hijacking
A user reports that he is receiving an error indicating that his TCP/IP address is already in use when he turns on his computer. A static IP address has been assigned to this user's computer, and you're certain this address was not inadvertently assigned to another computer. Which type of attack is most likely underway?
Man-in-the-middle attack
Back door attack
Worm
TCP/IP hijacking
You're working late one night, and you notice that the hard disk on your new computer is very active even though you aren't doing anything on the computer and it isn't connected to the Internet. What is the most likely suspect?
A disk failure is imminent.
A virus is spreading in your system.
Your system is under a DoS attack.
TCP/IP hijacking is being attempted.
You're the administrator for a large bottling company. At the end of each month, you routinely view all logs and look for discrepancies. This month, your e-mail system error log reports a large number of unsuccessful attempts to log on. It's apparent that the e-mail server is being targeted. Which type of attack is most likely occurring?
Software exploitation attack
Back door attack
Worm
TCP/IP hijacking
A. A DoS attack is intended to prevent access to network resources by overwhelming or flooding a service or network.
B. A DDoS attack uses multiple computer systems to attack a server or host in the network.
C. In a back door attack, a program or service is placed on a server to bypass normal security procedures.
A. A man-in-the-middle attack attempts to fool both ends of a communications session into believing the system in the middle is the other end.
C. A replay attack attempts to replay the results of a previously successful session to gain access.
D. TCP/IP hijacking is an attempt to steal a valid IP address and use it to gain authorization or information from a network.
A. A TCP ACK attack creates multiple incomplete sessions. Eventually, the TCP protocol hits a limit and refuses additional connections.
D. A smurf attack attempts to use a broadcast ping (ICMP) on a network. The return address of the ping may be a valid system in your network. This system will be flooded with responses in a large network.
C. Someone trying to con your organization into revealing account and password information is launching a social engineering attack.
C. A worm is a type of malicious code that attempts to replicate using whatever means are available. The worm may not have come from the user's system; rather, a system with the user's name in the address book has attacked these people.
A. A logic bomb notifies an attacker when a certain set of circumstances has occurred. This may in turn trigger an attack on your system.
A. An armored virus is designed to hide the signature of the virus behind code that confuses the antivirus software or blocks it from detecting the virus.
B. A stealth virus reports false information to hide itself from antivirus software. Stealth viruses often attach themselves to the boot sector of an operating system.
A. A Trojan horse enters with a legitimate program to accomplish its nefarious deeds.
B. Retroviruses are often referred to as anti-antiviruses. They can render your antivirus software unusable and leave you exposed to other, less formidable viruses.
A. Some viruses won't damage a system in an attempt to spread into all the other systems in a network. These viruses use that system as the carrier of the virus.
A. A password guessing attack occurs when a user account is repeatedly attacked using a variety of different passwords.
D. One of the symptoms of a TCP/IP hijacking attack may be the unavailability of a TCP/IP address when the system is started.
B. A symptom of many viruses is unusual activity on the system disk. This is caused by the virus spreading to other files on your system.
A. A software exploitation attack attempts to exploit weaknesses in software. A common attack attempts to communicate with an established port to gain unauthorized access. Most e-mail servers use port 25 for e-mail connections using SMTP.