ACCESS CONTROL SYSTEMS ARE AN ESSENTIAL PART of any organization. An access control system protects both the organization and its users. Limiting who can have access to certain documents, computer systems, or applications but ensuring those who need full access have it is a security measure that needs to be developed and continuously tested.
Identifying and implementing an access control system can be challenging. This chapter addresses how policies, standards, guidelines, and procedures help you implement and maintain an access control system. The procedures you create should be easily understood by those implementing them and the users who must abide by them.
As you learned in other chapters, access controls limit who can be in a specific area and what they can do once they get into an area. This area can be physical, such as a building, or logical, like a file structure. Limiting access on a personal or enterprise network will assist in securing what "lives" on that network, such as documents and personal information. Access controls are a cornerstone to a secure and vital network.
An important part of any access control system is creating clear guidelines and instructions for using it. In this section, you will learn how to use policies and standards as the foundation for creating access control system guidelines and procedures. The following are items to help you get started:
Begin the formal process with a plan. State your goals, what you need to reach them, and how you'll achieve them.
Determine which policies and standards you will reference. You don't have to reinvent the wheel when other documents and resources already exist that can help you create your own guidelines and procedures.
Determine how you can make the documentation process and system implementation easy for everyone. Once a task and process becomes difficult, people will reject the entire concept.
Come up with effective ways to spread the message and ensure that everyone understands the policies, standards, guidelines, and procedures.
Everything starts with a policy. A policy specifies the requirements or rules that need to be followed. A policy sets the direction for the organization. An example of a policy is an acceptable use policy stating how employees may use employer-owned computer resources, including the network and systems. A standard specifies how to support the policy. The standards can be industry standards or organization-specific, or a combination of both. Guidelines provide recommendations on how the requirements are to be met. Procedures define how the policies, standards, and guidelines will be implemented. An example of this process is:
Policy—The organization must ensure that all employer-owned computer systems are secure.
Standard—The organization may implement ISO 27002.
Guideline—The organization recommends that passwords should be a minimum or 8 characters and a maximum of 16.
Procedure—The organization should follow the steps in the Password Creation procedure to support the policy and standard.
There are various approaches an organization can take when implementing access controls. You should consider each approach when creating procedures. Two of these approaches are the phased approach and prioritization.
A phased approach starts at the beginning and works through to the end, but only on one section of a project at a time. For example, a systems administrator performs an assessment of the infrastructure, determines the goals, and sets the procedures based on the goals. He or she must then implement the procedure. After all systems have been configured, they must be tested and the results evaluated. Let's say a user named Kevin breached the security of a network folder. A systems administrator may review all the steps that led up to the breach. Was Kevin correctly granted access to the network? Was Kevin correctly allowed access to a particular folder? How did the access control pertaining to the folder fail, or did it not fail? How do you validate the necessary changes?
Note
A phased approach may be used when an organization has specific controls in place that ensure all steps that are related to each other are resolved together. In other words, changing one control does not affect another control. If an organization has the time to address all problems, a phased approach may be used.
Note
A prioritization approach is used when an organization has limited resources and wants to resolve the important processes first.
A prioritization approach means the administrator deals with procedures and network changes on a case-by-case basis. If an attack has occurred on the network, the administrator may make appropriate changes to adjust for that immediate weakness in the system. For example, if a user breaches network security and accesses a folder without authorization, a prioritization approach would require a systems administrator to resolve the access control failure. Very little testing may be done after the remediation occurs. Prioritization may be used when an organization feels that ranking the tasks from most important to least important will provide an efficient system for resolving the tasks.
Once you decide which approach to take, you can begin turning policy statements into implementation tasks and procedures. Various questions that need to be addressed are:
What is the mission of the implementation? What is the organization trying to achieve? In this case, you are taking a plan of action and putting the controls around it to ensure the policy is implemented.
What are the factors needed to ensure the policy is met? An organization must consider multiple factors when implementing a policy. Some examples of factors are access controls, secure communications to networks outside of the corporate network, and authentication measures.
Which tools will you need to address the access controls, secure communications, and authentication? What standards will be followed? Which access controls, such as discretionary access control (DAC), mandatory access control (MAC), and role-based access control (RBAC) will be used? What secure protocols such as Secure Sockets Layer (SSL) will be implemented? What authentication methods, such as user ID and password or multi-factor authentication, will be implemented?
How will the methods be implemented? Will they be put in place all at once or in a phased approach? What risks are associated with the timing of the implementation?
How will these access, secure communications, and authentication measures be tested? How often will they be tested? What will the organization do with the results?
How often will the policies be reviewed? How will you document the policies and implementation tasks?
Transforming policies into implementation procedures ensures that all business units are aware of the policies and security needs of the organization. The implementation procedures formalize the structure and policies of the corporation and allow the organizations within the company to be measured against them. These implementation tasks help ensure a safer organization by having a common mission and implementation method that all employees will follow.
Standards are an important baseline for incorporating security and specifically access controls within an organization. Standards were introduced in Chapter 4. This section examines some of the organizations that set security and technology standards, and which standards are important for creating access control implementation procedures.
IEEE was created in 1963. This not-for-profit professional organization has created over 1,100 information technology standards. Some of these standards include IEEE 802.1X, which addresses authentication for layer 2 (bridges and switches) devices when communicating on a network. The standard 802.1AC defines Media Access Control (MAC), and 802.1AE discusses MAC security. The IEEE Standards Association (IEEE-SA) is the standards contributor to IEEE. The IEEE-SA promotes "the engineering process by creating, developing, integrating, sharing, and applying knowledge about electro- and information technologies and sciences."1
NIST was founded in 1901 as a non-regulatory federal agency under the U.S. Department of Commerce. NIST's mission is "to promote U.S. innovation and industrial competitiveness by advancing, measurement science, standards, and technology in ways that enhance economic security and improve quality of life."2 When it comes to information technology, NIST was given direction by the Computer Security Act of 1987, the Cyber Security Research and Development Act of 2002, and the Federal Information Security Management Act (FISMA) of 2002. Under these three acts is the development of cryptographic standards and procedures, guidelines, and best practices for federal IT security. This IT security includes Federal Information Processing Standards (FIPS) and NIST Special Publications.
Note
NIST Special Publication 800-53 Revision 3 provides guidelines for selecting and specifying security controls for information systems.
FISMA was created in 2002 under the E-Government Act. Title III of the act required each federal agency to "develop, document, and implement an agency-wide program to provide information security for the information and information systems that support the operations and assets of the agency, including those provided and managed by another agency, contractor, or another source."3 NIST sets the FISMA standards for federal IT systems. According to FISMA, an information security policy should consist of:
Periodic risk assessments
Policies and procedures based on the risk assessments
Subordinate plans for providing adequate information security
Security awareness training
Periodic testing and evaluation of the effectiveness of information security policies
Process for planning, implementing, evaluating, and documenting remedial actions
Procedure for detecting, reporting, and responding to security incidents
Plans and procedures to ensure continuity of operations
As previously discussed, you must understand risk to appropriately identify or create security policies for your organization. You should use your knowledge of that risk to implement a framework of controls. FISMA has built a risk management framework that you can apply to new and current systems to manage your risk:
Step 1: Categorize the information system.
Step 2: Select a baseline of security controls.
Step 3: Implement the security controls and document how the controls are deployed.
Step 4: Assess the security controls.
Step 5: Authorize information system operations based on a determination of risk.
Step 6: Monitor and assess selected security controls.
ISO is the largest developer and publisher of international standards. ISO is not associated with any government entity but works with the public and private sectors. Approximately 18,000 standards have been established through ISO including:
ISO 9001, "Quality Management Systems"
ISO 31000, "Risk Management—Principals and Guidelines"
ISO/IEC 27001, "Information Technology—Security Techniques—Information Security Management System Implementation Guidance"
ISO/IEC 27006, "Information Technology—Security Techniques—Requirements for Bodies Providing Auditing and Certification of Information Security Management Systems"
ISO develops standards based on recommendations from industries and those that may be affected by the standard. The recommendation is passed on to an ISO member and the technical committee that would create the standard. If the technical committee feels that the standard is needed and is a global requirement, the committee discusses the relevance and will work together to develop the standard.
Note
An ISO/IEC prefix indicates joint work between ISO and the International Electrotechnical Committee (IEC). Its mission is to provide information about standards and standardization.
In 2008, IEEE and ISO joined forces to create the Partner Standards Development Organization (PSDO). This organization combines the resources from both governing bodies to "focus on the subjects of information technology, intelligent transport systems, and health informatics."4
The Internet Engineering Task Force (IETF) was formed in 1986. IETF is an international organization that focuses on the Internet and Internet protocols. This includes the Transmission Control Protocol/Internet Protocol (TCP/IP) suite, which includes the application layer, transport layer, Internet layer, and data-link layer (described in RFC 1122). The IETF develops Requests for Comments (RFCs). An RFC addresses the methods and behaviors of Internet systems including routers, switches, and computer systems. Each RFC has its own set of numbers assigned to it. These numbers are never changed. If an RFC needs to be rewritten or have additions, a revised document is written and released. RFCs can be superseded by other RFCs making the original or previous RFC obsolete. Examples of some RFCs are:
RFC 1457 addresses the security-level framework for the Internet.
RFC 1938 addresses one-time password messages.
RFC 2716 touches on transport layer (layer 3) security.
RFC 4301 focuses on the security architecture for Internet Protocol (IP).
The PCI Security Standards Council was developed in 2006 for developing, managing, educating, and providing awareness for the Payment Card Industry (PCI) security standards. These standards include the Data Security Standard (DSS), payment application data security standard, and pin-entry device requirements. Companies that founded the PCI Security Standards Council are American Express, MasterCard, Visa, Discover, and JCB International.
Payment Card Industry Data Security Standard (PCI DSS) is a security standard for security management, policies and procedures, network architecture, software design, and other protective measures. This standard helps organizations protect customer payment card account data. PCI DSS specifies six primary requirements that merchants need to meet to process credit and debit card transactions:
Build and maintain a secure network.
Protect cardholder data.
Maintain a vulnerability management program.
Implement strong access control measures.
Regularly monitor and test networks.
Maintain an information security policy.
The Center for Internet Security (CIS) in a non-profit independent community of professionals that provides best practice standards for the secure configuration of network devices such as Apple iPhone, Check Point Firewall software, and Cisco devices, just to name a few. The professionals associated with CIS establish:
Benchmarks detailing best practice security configurations for IT systems
Benchmark Audit Tools that enable IT and security professionals to assess their IT systems for compliance with benchmark and security best practices
Metrics that can be used across organizations to collect and analyze data on security processes and performance outcomes
CIS promotes consensus-based standards that organizations can use and implement to increase the security, privacy, and integrity of the business and other functions and transactions that occur on the Internet.
Although standards have been established by credible organizations in the United States and internationally, you need to incorporate them into your procedures in a way that's easy for users to follow. Policies, too, need to be incorporated and expanded upon with details that specify how to perform tasks and when.
Converting a policy into an implementation task requires multiple steps. You must first identify a policy that addresses your needs. Some examples of policies are a password policy and a system configuration policy. You then compare your current system to the system described in the policy. You must perform a gap analysis to understand which steps will need to be implemented.
Let's walk through a policy-standard-procedures-guidelines example for an organization. This example will show you how theory is put into practice:
Policy—The organization wants to implement a more defined password policy for its access-control policies. Not only does this include individual computer systems, such as desktops and laptops, but servers that are maintained throughout the organization as well.
Standard—The organization has determined that it wants to implement the standards and recommendations that NIST has established, for example, NIST Special Publication (SP) 800-53. This document provides the recommended security controls for federal information systems. Although this organization is not a federal entity, it feels that the standards and recommendations that NIST has established meet its stringent needs.
The recommended actions in NIST SP 800-53 are as follows:
Protect the password from unauthorized disclosure and modification when the password is stored and transmitted.
Prohibit passwords from being displayed as they are entered into the system.
Enforce the minimum and maximum lifetime of the password.
Prohibit the reuse of passwords for a specific number of times.
By continuing to use the standards and recommendations established by NIST, NIST SP 800-118, "Guide to Enterprise Password Management," will be used. This document recommends the following constraints for password usage and creation:
Storage:
Encrypt files that maintain passwords.
Use operating system access control features to restrict access to files that contain passwords.
Store the cryptographic hashes of the passwords, instead of storing the actual password.
Transmission:
Encrypt the passwords of the communication when transmitting passwords.
Transmit cryptographic password hashes versus a plaintext password.
Use secure protocols when transmitting passwords (Secure Shell or HTTPS).
Use network segregation and switched networks for internal networks in order to reduce the possibility of an attacker identifying the password.
Use a secure password-based authentication protocol (Kerberos).
User knowledge and behavior:
Be aware of nontechnical tactics for password capturing such as shoulder surfing. Although a password may be hidden by asterisks, an attacker may still be able to gain certain characters in the password that can be used to determine the full password.
Be aware of technical tactics for password capturing such as keystroke logging. Protect the systems to ensure malware is not loaded onto the computer systems. Users should also not enter their password into public computer systems such as airports or hotels, which are high risk, or the password may be compromised.
Be aware of social engineering. An attacker might ask a user specific questions to gather additional data that will be used to determine the password or to reset a password. Phishing e-mails are an example of social engineering that is used to gather password data.
Be aware of malicious insiders that may use the passwords or provide passwords to others to gather data or files for the organization, even though they or others are not allowed access to them.
Password guessing and cracking:
Lock out a user after a number of consecutive failed logon attempts.
Have a specific wait time after each failed attempt, for example, wait 5 seconds after the first failed attempt, wait 10 seconds after the second failed attempt, and so on.
Use strong passwords by requiring a minimum and maximum length.
Employ strong passwords by requiring a specific set of characters.
Procedures—These are the steps that an administrator takes to implement controls. In this example, part of the procedure for implementing passwords is to identify all the systems that require passwords. Once they are identified, it is necessary to apply the procedures to make sure the passwords meet the password policy and standards. Documenting the specific procedures based on protection of passwords, strength of passwords, and reuse of passwords will help assure the goals are met.
Guidelines—These are suggestions and best practices based on standards. Regarding a password policy, for example, the organization has decided to base its guidelines on the best practices established by NIST. If employees follow the guidelines, the organization will be in compliance with the standards.
These steps are put in place to ensure a secure organization and computer systems.
Guidelines are optional actions or controls that are based on policies, standards, and procedures. Guidelines are also recommendations and best practices that are provided by the standards bodies such as NIST, ISO, and CIS. Creating guidelines that employees follow can be difficult or easy. How this is determined is based on the steps that were taken beforehand. Previously you learned about procedures and that they need to be simple and easy to follow. If this philosophy is not adopted, the subsequent steps for implementing security will be much more challenging. When the security teams within an organization focus on security, they must realize that this needs to be accepted by both technical and non-technical parties. This is where broad-based security training can benefit everyone. Administrators and employees need to understand the value and importance of what they are being asked to do.
Such guidelines that may be established based on the password policy example, NIST standards, and password procedures are:
Encrypt all passwords.
Ensure secure communications are used for each entry.
Educate employees on shoulder surfing, malware, and social engineering, and how these tactics are used to retrieve passwords.
Lock out users after five failed logon attempts.
Require all passwords to be a minimum of 8 characters and a maximum of 16 characters.
Require all passwords to include a minimum of one capital letter, one number, and two special characters.
Ensure that passwords are changed every 90 days.
Configure the system to store up to five previous passwords so that they cannot be reused.
Use an enterprise-wide password database system.
Note
An enterprise-wide password database system, also called a single sign-on system, allows individual users to encrypt their user ID and password. These tools allow users to store their user IDs and passwords for multiple systems and applications. The data is encrypted and can only be unlocked by a user's password. Instead of having to remember several passwords, the user will only need to remember one.
Guidelines within the organization assist in educating administrators. Guidelines identify what is expected of various groups to ensure compliance with policies and standards. Security is a day-to-day mandate and requires everyone to participate in the actions, policies, and guidelines. All employees should receive training to fully understand the value of security to the organization.
Identity management is a way to identify all associates within an organization. Identity can take many forms, such as a user ID, biometrics, or smart card. Once everyone has been identified by such aspects as their user ID, location, and role, the access that the user and systems should be provided can be granted, and subsequently revoked.
Reviewing identities and ensuring they are categorized correctly will limit mistakes, such as providing the wrong access to the wrong person. Every organization has its own standards for acceptable identity depending on the risk associated with the system or location. For example, a highly classified room may require a biometrics scan versus a personal identification number (PIN). In addition, an administrator needs to ensure identities are not reused. Once an identity has been assigned, it should not be reassigned to another employee or system. Allowing an identity to be used only once allows an administrator to verify what was done by a user at any point in time.
Implementing access controls based on one's identity within an organization helps to ensure access to resources is correct, or whether a user has found a way around the controls. Monitoring the behavior of the network and monitoring access of files, systems, and applications provides the baselines for the types of access control that a specific identity does or does not require. Centralizing identity management provides a single location to create, remove, or adjust an identity's access. A centralized system allows an administrator to easily make adjustments based on a user's or application's behavior. For example, if users access a certain system only at the end of each quarter, it may be appropriate to remove all access to the system until the last month of each quarter to ensure the information is not accessed at other times.
As changes occur to applications and systems, it is important to monitor user and system access and behavior to increase safety. Because attackers have become more sophisticated and the rewards for "stealing" particular information have increased, identity management has become essential for organizations. Continuous monitoring helps ensure valuable data does not get into the wrong hands.
Identifying how users, applications, and networks behave helps create a baseline for the infrastructure. By understanding normal behavior, you are able to detect activities that are unusual. For example, an accounting employee named Scott ordinarily accesses financial servers; this is considered normal behavior. If Scott begins accessing engineering servers, you know that the access control is not working correctly and you may need to question Scott's actions. Is there a virus on his system, or is he trying to obtain intellectual property? Tracking the behavior of all systems on a network will help you understand normal activities and identify breaches as well.
Examining user behavior reveals the times a user may log on to a system, the applications he or she uses and how often, the Web sites a user frequents, and servers that are accessed. In general, user behavior is any type of activity that defines a user's actions.
Application analysis has similar characteristics. By analyzing applications, you may learn:
How often applications are accessed
Who accesses them
What actions are performed once an application is accessed
You must understand these aspects of an application for security and management purposes. If an administrator is aware that an application is not accessed from 2:00 a.m. to 5:00 a.m., he or she may decide to schedule system upgrades during that time. This ensures that resources are available when needed and that adjustments won't affect the majority of employees. Availability is an essential part of network security, and user behavior analysis and application analysis provides the data needed to ensure systems are available.
Network analysis provides details on both users and applications as well as network traffic. Understanding the behavior of the network verifies the access and security controls that are in place. It provides guidelines for normal and abnormal activity. For example, if Scott's system is sending out abnormal traffic, there could be a virus on the network. Analyzing all inbound and outbound traffic may pinpoint attackers coming in as well as internal employees creating havoc within the network. Network analysis ensures that security controls are in place and indicates whether they are effective.
Understanding the behavior of users, applications, and network activities assists in identity and access management. It identifies access controls that are not functioning correctly and lets an administrator know if changes are needed. Behavior analysis can prove that access is set up correctly because network patterns and access are working as planned. Combining behavior analysis and identity and access management provides a blueprint for the network regarding normal behaviors and the expectations of the systems.
Creating a complete inventory of IT assets is one of the first steps in implementing access controls. What servers, routers, firewalls, workstations, databases, and so on are on the network, and where are they located? What are the software, folders, and files that are on the servers and workstations? What data is in the database? Once you determine the asset inventory, it is important to determine the risk associated with the assets and data. You can determine risk by evaluating the value of the data and the cost to the organization if the data were exposed or had to be replaced.
The access control system you implement should be based on the risk against the data and network access. Understanding how the staff and assets are distributed within the organization will help determine the controls needed for accessing high-, medium-, and low-risk assets. For example, if there is high risk associated with specific data, additional access controls may need to be placed on the data. If you have a large staff, it may be beneficial to implement a single sign-on tool. This enables you to centralize management of assets and the access granted to them.
Network administrators must always be aware of which assets are available to be accessed and where these assets are. For example, if human resources (HR) information is available on a network that has been segmented for finance, a security breach may occur. Administrators must ensure that the network and computer resources support the staff and staffing requirements. Administrators must ensure the tools that employees use are available when employees need them.
You cannot secure users, objects, and tools if you don't know they exist. Unencrypted files on a server, applications on computer resources that open ports on the network, and servers that maintain intellectual property are targets for attack. Large infrastructures can be difficult for an administrator to manage. In addition, if a server that holds quarterly confidential financials is only available during normal business hours, an employee might copy or e-mail these files to work on them during off hours. This poses a security risk. E-mailing the document via an unencrypted connection provides an opportunity for an attacker to see this data. Leaving confidential data on a laptop poses a risk if the laptop is stolen.
It is important to have the tools available that allow an administrator to manage any size staff and assets. Large organizations tend to experience a flux of employees, due to hiring, terminations, and resignations. Administrators need to be able to add and remove employees and groups in a matter of hours. Ensuring that authentication and authorizations systems are able to handle a large-scale employee base is important when designing and implementing an organization's infrastructure.
Implementing multiple layers in security is providing a defense-in-depth mechanism and therefore stronger protection for the network and users. Multiple layers provide multiple road blocks for a user and attacker. Having multiple controls in place before something can be accessed may be tiresome for a user; however, the goal is to have the same effect on an attacker. If an attacker is able to find a hole and access a company's network, additional layers of security might stop the attacker from reaching other systems, applications, or sensitive data.
Creating layers within the network can be done physically by segmenting users and servers onto separate networks. This can also be done logically through virtual local area networks (VLANs). Implementing security measures at each logical level of access such as application access or file access puts up additional road blocks for attackers. Making security a hierarchical structure with layers versus implementing just a few controls provides the strong defense needed to protect the overall infrastructure.
User access control profiles identify authorizations allowable for each user, such as what access is allowed and what is denied. You can implement user access control profiles with role-based access controls. Implementing a role-based access control allows you to manage the infrastructure with greater control. Role-based access is implemented for a large group of people that perform similar tasks, and helps prevent a single user within a role from having more rights than others. Role-based security saves you time by ensuring all controls are applied to a particular role. For example, you've already defined the access controls for the Sales Reps role. When a new sales representative is hired, you simply assign him to the Sales Rep role instead of assigning access controls separately.
This technique benefits a multilayered access control implementation because the role may have additional access controls added or removed, depending on the risk associated with a user's job functions. If the risk associated with a role increases, the access controls placed on the roles can change with it. For example, sales representatives may be given less access to their territories' sales figures at the end of the quarter because the finance department is compiling the financials for all regions. Allowing the sales representatives to change data while the finance department is using the data would create a problem for the entire organization.
System access controls lists (SACLs) identify which users have access to systems and what rights they have once each system is accessed. Is the system a read-only database or can users write to the database? Providing accessibility metrics and monitoring user actions help ensure the system is secure. They can also indicate that access changes need to occur.
Designing a system that meets the needs of the users but does not provide more access than is needed should be at the core of system security. Restricting access at the system level limits what changes can occur on the system. One example is restricting the installation of software, which makes the system more secure and limits the chances of Trojan horses and malware from being installed. Figure 11-1 identifies categories of software restriction policies in the Microsoft Windows Vista and Windows 7 operating systems.
The three policies that can be implemented for software download restrictions are:
Enforcement—Enforces additional policies automatically (see Figure 11-2).
Designated File Types—Determines what types of files can be downloaded to the system such as .exe, scripts, or ActiveX controls (see Figure 11-3).
Trusted Publishers—Provides the ability to allow or not allow code that was provided from a trusted source (see Figure 11-4).
Implementing security at the system level is important when implementing a multilayer access control system. It limits access to the greater system. This ensures that employees who should not be installing software or making changes to the system are not given access. As you learned earlier in the chapter, best practices for computer systems have been established by standards bodies. If an organization bases its computer system configuration on these best practices, an administrator should ensure there are no computer system configuration changes that will result in an unsecure system.
Employees may be given full or limited amounts of access to the systems and applications that access data. Applications may have direct controls placed on them, such as limiting execution. Once launched, an application may have access controls that allow only specific users to view certain fields or that allow certain features to be used within the application.
In addition, applications may be read-only for some users but not others. Changes or additions may be restricted to only the owner or administrator of an application. Policies are established for each application, ensuring the accessible information is not compromised by a user or an attacker. These controls can also identify the types of data each user can view in the application and how the data should be displayed.
For example, an administrator can place specific controls on Microsoft SQL Server to ensure users cannot access data, create new databases, or change the application without appropriate permission. A SQL server has various roles that provide specific access. Several of these roles and the access granted are:
These access controls provide yet another layer of security on top of controls at the system level. If a failure occurs at the system level, the application access controls provide security. These layers ensure that the system and data are not completely vulnerable to attacks.
If users are not given access to certain applications, access to the location of the data may be limited as well. Assigning controls to files and folders adds yet another layer to a multilayer structure. Limiting read and write access to files and folders ensures the data cannot be compromised. Privileges need to be limited by whom and what can access specific files and folders. Administrators should assign privileges based on need.
Scott, for example, has documents that are customer-specific, such as organizational charts and contact information on his corporate computer system. Scott's customer wants assurance that this information is not available to its competitors. Scott needs to block access to his coworkers who support his customer's competitors. Figure 11-5 shows how these controls could be put in place against a file or folder.
Employing this access control provides yet another layer of protection in a multilayer access control implementation.
After passing through most of the layers of access control, limiting access to the data itself is your last method of protecting it. A privilege such as read or write is an example of a security measure placed against data. As mentioned previously, many database applications, such as Microsoft SQL Server, provide controls to limit access to data.
Results or statistics are only as reliable as the data that they are based on. If the data is changed or augmented, the work that is being done on the data will be unreliable. Limiting access to data protects all who rely on the data, including individuals and systems. Allowing full access leaves data vulnerable to attack, and human error. It may not be the intent of an individual to erase or destroy data, but accidents happen.
Companies have many types of identities that need access to the network. The identities include employees, remote employees, customers, and business partners. Managing the access controls of various identity groups can be cumbersome. An administrator must understand how they will access the network, when they will access the network, and the amount of access that is required by role.
For example, a business partner of a software development company may need full access to documentation and software but not to the source code. The business partner may be treated like an employee, but the partner cannot receive access to everything an employee in a similar role would have. For example, a business partner should not have access to internal distribution lists, the HR site, or IT sites that are provided specifically for employees. Business partners are important to an organization, but they still work for another company and data needs to remain separate. Careful consideration must be given to every role as well as every group they are a part of. Customers may have access to product A documentation but this does not mean that they should have access to documentation for products B and C as well. There are multiple tools available for providing access to employees, remote employees, customers, and business partners, which are discussed in the following sections.
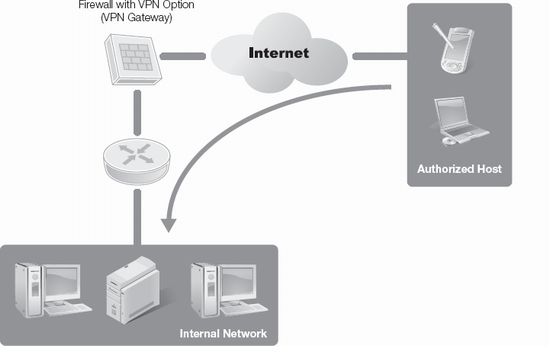
Remote access virtual private networks (VPNs) are established to allow remote employees access to an organization's internal network. The idea is to provide the same capabilities off-site that you have on-site. A remote VPN provides a secure connection by creating an encrypted tunnel from point A to point B, usually across the Internet. If point B is an organization's internal network, point A is a computer system or mobile device that can be located anywhere, such as a coffee shop, a house, an airport, or any place that provides Internet access. Figure 11-6 provides an overview of VPN communications.
The benefits associated with remote access VPNs are:
Reduces costs by allowing the user to work at locations other than an employer site. This may reduce facility costs for electricity and floor space.
Improves flexibility by giving users the ability to work whenever and wherever. For example, an employee may be given access to employer resources after hours. The employee may also work at a coffee shop before a customer meeting.
Provides secure communication through encryption and access rights based on the user.
Before remote access VPNs were available, many organizations used expensive leased lines. This technology was not considered a secure option because the line can easily be tapped and the communication monitored. With the advent of VPNs with encryption and access controls, security was enabled by protecting the data and controlling who has access to which resources within an organization's domain. Remote access VPNs provide secure communications for laptops, mobile devices such as personal digital assistants (PDAs), and even external servers.
Remote access VPN access controls are managed through authentication of the user, VPN firewalls, VPN routers, and applications. Access controls can be based on user IDs or mandatory access control limitations. The ability for remote access VPNs to provide security and access controls establishes an optimal solution for remote employees as well as customers and business partners. This solution gives the administrator a more granulated access control by limiting or allowing access based on:
Authentication methods—Incorporating a multi-factor authentication method adds the extra level of security for gaining access to the corporate network. For example, when Scott goes into the office, he may use a user ID and password. If Scott is at home and accessing the corporate network remotely, he will still use his user ID and password, but another layer of authentication will be required with the VPN server.
Membership in groups—Creating groups based on a user's role within the organization ensures that customers and business partners only have access to specific files and applications and limited access to others.
An intranet is an internal private network. Intranets generally consist of Web applications or portals and provide a system for internal employees to collaborate securely. Intranets limit outside communication by only allowing systems and users that have been authenticated on the corporate network. Intranets may be set up to allow a group of people such as a software development team to collaborate, or it can be a tool available to all employees. Some common items stored on an intranet are:
Company directory
Company locations and directions to them
Organizational charts
Corporate announcements
Search capabilities for additional corporate resources
Intranets have been set up as a single repository for all employer-focused information. An intranet can update employees as to holiday dates, building closures due to inclement weather, and changes to 401K or benefits information. It can also be a tool for employees to provide thoughts or opinions about the organization. Portals can also be developed for products. These portals can have software updates, roadmaps, documentation, and a section where questions can be asked and answered about a particular product.
With the growing popularity of Web 2.0, some employees have requested a employer-hosted social media sites, which allows them to discuss and receive information from the organization. Social media sites include blogs, Really Simple Syndication (RSS) feeds, and discussion areas. More and more individuals entering the work force today want and expect their organizations to have an intranet where they can access all the news, data, and resources available to them—all in one convenient location.
Note
Web 2.0 is the phase of technology for the Web that focuses on social media sites, blogs, wikis, and other communities that deal with communication and collaboration.
Securing the intranet can be done using the same tools that are used for protecting any Web application that is maintained by the employer. Authentication, access controls, and tools such as single sign-on or identity and access management will ensure the information is accessed only by people with the proper credentials.
Extranets extend an intranet, providing access to business partners, distributors, and resellers. For example, an organization has a product site for its partners and distributors that contains software downloads and updates, documentation, and questions and answers regarding a specific product.
Extranets expand the usage and availability of intranets. Extending access to your external supply chain, business partners, distributors, and resellers lets these parties know that your relationship with them is important. Giving them the same access to materials and accessibility to resources that customer service and engineering have helps build the relationship and the trust between your organizations.
Security for extranets is provided via isolation, access controls, authentication, and encryption, if the communication between the user and Web portal is needed. Isolation of the network into a private and public network ensures that only certain users have access to certain networks. Extranets provide remote access to only the public network within a company's infrastructure. Extranets also limit access to specific resources on the extranet. Limiting access to specific applications, services, files and folders, and data ensures that confidential information does not get into the wrong hands. As previously discussed, authentication factors verify that users are who they say they are. Employing a stronger authentication method ensures their identities. Encryption secures the communication paths between the systems so that no one can access the data while on the network.
E-commerce portals are a way for business to business (B2B) or business to customer (B2C) transactions to occur. In other words, e-commerce is e-shopping or shopping online. In order to buy items online, the communication must be secure. If it is not, the credit card data can be stolen by an attacker and used maliciously. Protection of an e-commerce portal can be achieved with SSL 128-bit encryption. SSL encryption uses cryptographic techniques to ensure the communication between point A and point B is authenticated and secure. In e-commerce, point A would be a Web browser and point B would be the e-commerce site. SSL is a presentation layer protocol and was developed by Netscape. SSL is not tied to a particular cryptographic algorithm but instead provides a means of negotiation.
Three phases for SSL are negotiation, key exchange, and data transfer. The SSL process is as follows:
The Web server sends its digital certificate to the Web browser. The Web browser extracts the Web server's public key from the digital certificate.
The Web browser verifies the Web server's certificate by comparing the certificate authority with the trusted authority list that the Web browser was shipped with. The Web browser computes a hash of the certificate and compares it with the hash in the certificate. The hash is decrypted using the trusted authority's public key.
If the hash matches, the certificate has not been tampered with. The Web browser checks the validity date to ensure the certificate has not expired. The browser also checks to verify that the system that sent the certificate has the same uniform resource locator (URL) that was encoded into the identification information. After these checks match, the public key of the server is extracted from the server's certificate.
The Web browser generates a random symmetric encryption key. This key will be used to encrypt the conversation between the Web browser and the Web server. The symmetric encryption key is encrypted with the Web server's public key—in other words, the symmetric encryption key has been "wrapped." Remember that the Web server's public key was extracted from the Web server's digital certificate.
The Web browser sends the wrapped key to the Web server. The Web server decrypts the wrapped key with its private key. At this time, the Web browser and the Web server have the same symmetric encryption key. This encryption key will be used to start an encrypted conversation. The symmetric key will be used to encrypt and decrypt the messages.
Tip
How do you know if a Web site is encrypted? If the Web address starts with "https" and displays an icon that looks like a padlock, the Web site is secure.
Protecting the communication with the Web browser and the Web server ensures protected information. Someone purchasing a product or service online should only do so from e-commerce sites with a minimum of SSL 128-bit encryption. This encryption protects both the purchaser and the e-commerce site.
Online banking is another Web portal access that implements encryption capabilities. The user and the bank want to ensure that the credentials entered are not retrieved through a separate entity such as an attacker. Banks that provide online access will also limit the amount of access available. If one user is able to see the accounts of a separate user, a security risk has occurred. Limiting the access for each user ID is a component on online banking.
Online banking sites require specific controls to not only protect the user's access but to protect the bank's as well. The Federal Financial Institutions Examinations Council (FFEIC) is a body of the U.S. government that provides standards for financial institutions. The FFEIC has stated that an information security strategy should be based on the following:
Consideration for prevention, detection, and response mechanism
Implementation of least privilege and the least permissive controls
Layered controls between threats and organization assets
Policies that guide employees and officers in implementing a security program
The FFEIC has established best practices for administering access rights. These access controls are:
Assigning users and devices only the required access to perform their necessary functions
Updating access controls based on personnel or system changes
Reviewing users' access rights periodically based on the risk associated with the application or system
Designing the acceptable use policies and have the users agree to them
Formal access control administration consists of the following processes:
An enrollment for all new users.
An authentication process to identify the specific users. The appropriate authentication process should match the risk associated with the user. These authentication methods can include multi-factor authentication as well as challenge and response mechanisms.
An authorization process for authorized users. This process will employ controls around a user's ability to add, delete, or modify applications, files, and specific information pertaining to that user.
Monitoring and managing the access rights of the specific users.
Encrypting the transmission of user ID and passwords.
The FFEIC has also established best practices for financial institutions to ensure secure access over multiple layers to protect against unauthorized access. These actions are:
Group network servers, applications, data, and users into security domains.
Establish the appropriate access requirements within and between the security domains.
Implement the appropriate technical controls to ensure the access requirements.
Monitor cross-domain access for security policy violations and anomalous activity.
Implementing access controls for applications used by financial institutions is done via:
Using authentication and authorization controls based on the risk of the application
Monitoring the access rights to ensure that only the minimum access controls are granted to the users
Using time of day access controls
Logging of access and security events
Using software that enables analysis of users' activities
Best practices for remote access to financial institutions are identified by the FFEIC as:
Disabling remote access if no business exists
Controlling access through approval by management and audits
Implementing controls on both ends of the communication in order to avoid malicious activities
Logging and monitoring of all remote access communications
Securing remote access devices
Using strong authentication and encryption to secure communications
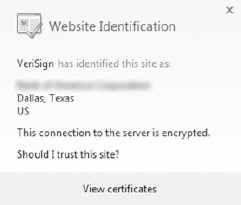
As previously discussed, a Web portal with SSL 128-bit encryption is at the current time the safest method for protecting credentials and transaction information such as banking accounts. When Scott logs into his online banking portal, he ensures the Web address is "https" and that the padlock icon is present. As a secondary precaution, he will ensure the certification was provided by a trusted certificate authority, as shown in Figure 11-7. This information is available to him by clicking on the padlock icon. He can get further details by clicking the View Certificates link. The data provided allows Scott to know he can trust this portal and can continue with his logon and banking transactions or payments.
Online banking sites require multiple modes of authentication. Scott should be comfortable sending this information if the site uses secure communications. Online banking portals may require Scott to follow strict password polices, ensuring he has a strong password. This authentication information will identify his separate accounts and ensure that he is the only person who can access them. Scott wants to ensure that others cannot see his accounts and account number, and he does not want access to accounts he should not have access to. Employing access controls reduces the security risks for both Scott and his bank.
As identified by the FFEIC in 2001, accessing an Internet banking environment with only single-factor authentication is not adequate enough for high-risk transactions that include access to customer information and movement of funds. The FFEIC recommends that if a financial institution provides an Internet-based service to customers, the appropriate multi-factor authentication should be employed. Providing the appropriate authentication method for users is necessary for protecting customer information. Not employing these mechanisms can result in credentials being compromised and therefore identity theft, money laundering, and fraud can occur. The level of authentication should match the level of risk that a financial institution is willing to undertake.
Online banking portals may provide secondary tactics for users to verify that their communications have not been hijacked. If a session were to be hijacked, a user would be providing his or her credentials to an attacker, and the account would most likely be compromised. Using a second authorization and identification provides a second layer of security. Identification that the Web site is a valid Web site protects Scott.
Some online banking portals enable you to choose a custom image when you first set up your account. This image often appears before you enter your password. If the image you see is not the same image you originally selected, you know you should not continue logging on. Some banking portals even allow customers to create custom phrases, further enhancing the security of your financial information. You are likely required to enter a PIN as well to gain access to your accounts. Online banking portals aim to provide multiple layers of security to ensure both the user's information and the banking information is secure.
Ensuring an organization has the highest level of security is a daily exercise for security professionals. Some best practices for access controls and their implementation are:
Understand the roles within the organizations—Identify users and their roles to determine which access controls to put in place. Segregating access by role ensures that someone in the customer service department, for example, does not have access to the company's financial records.
Understand the data that resides on the network—An administrator cannot protect what he or she does not know; this includes data and software. If a certain application needs access to specific ports, the administrator needs to ensure these ports are open but that other tools or attackers do not have access as well. Knowing where all the data resides, on which servers, and on which network is necessary to configure proper access controls. Knowledge of this data is also necessary for designing policies and limiting where the data can be stored.
Establish a baseline—Understanding normal behavior on a network helps you understand which access controls are necessary and pinpoints when unusual activities occur.
Monitor activities on a continuous basis—After establishing a baseline, it is important to monitor it on a regular basis. Monitoring can identify new activities that are allowed, such as use of new software, or malicious activity such as a virus on the network.
Create guidelines and policies that are easy to understand and implement—No one wants to follow rules that cannot be understood. Security is a role that everyone within an organization must know, advocate, and adhere to daily. If employees feel that rules hinder their job performance, they look for ways around the system and cause a larger security risk.
Manage user accounts appropriately—Removing access for a user that has left the company and not reusing user IDs once deactivated reduces security risks.
Manage remote access capabilities—Access for business partners, customers, and remote users must be managed effectively and securely. Ensure that communications are secure and protect organization resources from those who should not have access.
Provide strong security—Protecting assets, files, people, and applications is a best practice for any organization. The risk associated with data getting into the wrong hands is not something an organization can afford. Ensure proper access controls are in place, make sure authentication is efficient and effective, and communicate the security message to employees.
In order to understand some of the concepts discussed with access control implementations, it is beneficial to see how they are used in the real world. The following sections provide three case studies from real-world situations that cover some of the topics previously discussed.
A small tax filing company employs contractors for the tax season. Three contractors handle state taxes, and two of those contractors file federal taxes. The administrator needs to ensure that the two contractors have access to the state and federal forms for a select number of clients, and the other contractor has access only to the state returns. The administrator has access to all client information.
The administrator applied access controls to the folders to limit the amount of access each of the contractors needs. It was also determined that each of these contractors would need their own account on the network. Limiting the amount of access for the three contractors ensures that the client information is kept secure and only seen by the appropriate user. Providing full access to everyone within the company would create risk the administrator was not willing to accept.
Ensuring each contractor had their own user ID allowed for tracking purposes in case a client was audited and the tax returns needed to be reviewed. If additional access needed to be added for emergency purposes, the administrator granted the access on a temporary basis. The administrator also audited all of the activities to ensure correct access was provided.
These policies were shared with the clients and they felt secure knowing that the data would not get into the wrong hands. Implementing access controls proved successful for the company, and because the policy was documented and followed, updates could be done easily for each new batch of contractors.
This case study is an example of implementing a multilayer access control approach. The tax filing company defined the roles that each of the employees and contractors had within the organization and defined the access based on role. Each contractor was provided his or her own user ID for auditing as well, complementing the multilayer approach. The user role allowed contractors to see federal and state forms, as appropriate, but they could not see every client's forms.
The U.S. government manages millions of employees, consultants, and contractors. These entities are assigned identity credentials to access various agencies' networks and systems. In many cases, individuals must remember a user ID and password for network access, and another user ID/password combination for each application they access. Although security personnel in each agency manage credentials for their users, the effort is still time-consuming and expensive. Overall security is also a concern. The current decentralized management of identities allows attackers to move from one system to another without their patterns being noticed right away.
For budgetary and strategic reasons, U.S. government security leaders have been collaborating on a project to create a centralized identity management system. The CIO Council lent a hand to the effort in 2009 by creating an implementation roadmap. The U.S. Department of Agriculture has already started a project to centralize 70 identity databases. Employees will receive a smart card and a PIN to access multiple databases rather than using unique credentials for each database as they do now. The Department of Homeland Security has started a similar initiative as well.
Some of the expected benefits of a centralized identity management system include:
A more consistent approach to security
A reduction of risk in inconsistent policy enforcement and mishandled passwords
Reduced administrative expenses, including help desk calls to reset passwords
Better cross-agency communications
Security leaders admit that the cost of implementation will be high, but they believe the cost of doing nothing may be even higher.
Reliant, a large health care facility, needed to upgrade its paper system to an electronic version. Knowing that the upgrade was needed, Reliant decided to implement a more secure infrastructure by implementing access controls to protect confidential information and upgrading its network configuration.
Access to the Reliant database is available through the corporate network. Employees use computers and handheld devices to access the data. Each patient at Reliant has personal data pertaining to them such as their medical history, allergies, and blood type. Data such as the patients' likes and dislikes and emergency contact information is also available. Doctors and nurses are able to review all the medical information on every patient in the database. Some health care providers are only able to see patients' history from the present date to one year back. Hospital volunteers are not able to see any patient medical histories but are able to see the emergency contacts as well as each patient's likes and dislikes.
Reliant established an intranet for schedules, planned activities, food menus, and any updates pertinent to all. Access points were established for visitors and the handheld devices used by the doctors and nurses. The handheld devices were required to have an SSL VPN connection to ensure the communication is encrypted. The devices also required user IDs and passwords as a form of authentication. Biometrics was not considered because the staff often wore gloves and the scanners could not read the fingerprints.
The information that is stored in Reliant's system is confidential and must be kept secure. Access to the documents must be limited and constrained to only those individuals who have the rights to see it. Each user has a specific user ID that limits his or her access. Authentication and access is audited daily to ensure the constraints are in place and the patient data is not accessed. The access controls were carefully implemented and tested after every step to ensure they worked properly. Having volunteers see patients' medical histories would have violated Reliant's policy, and the health care facility could not risk access controls being set up incorrectly. Implementing the access control on the access points was vital as well. Ensuring that visitors were not able to access the intranet or any of the corporate resources was important. Providing encryption on the handheld devices protected the data from getting into the wrong hands.
All of these implementations for access control and encryption ensured the electronic version was safer than the paper records. It protected the patients, all health care providers, and the volunteers.
Understanding the importance of access controls and security policies is vital for every organization. Security is only as strong as the weakest link, and if employees feel that security measures negatively impact their job performance, they may find ways around it.
We have discussed best practices for access controls and how they benefit everyone in an organization. Whether it is implementing system access controls, application access, file and folder access controls, or data access controls, or combining them in a multilayer implementation, access control systems are essential for protecting all data, systems, and applications. We have also examined ways to secure remote connections and extranets. Data can be secured through VPNs and SSL 12 8-bit encryption to protect it while in transit over the Internet.
Algorithm
Application layer
Assessment
Baseline
Business to business (B2B)
Business to customers (B2C)
Data-link layer
Digital certificate
Internet layer
Private key
Public key
Transport layer
E-commerce and banking sites should have no encryption enabled because the communication between the two points is already protected via the user ID.
True
False
_______is the largest developer and publisher of international standards.
Intranets are extensions of the corporate network for business partners and customers.
True
False
Which of the following indicates you are using a secure Web site? (Select two.)
Web address starts with "shttp"
Web address starts with "https"
Padlock icon
Key icon
Which of the following are characteristics of Web 2.0? (Select three.)
Encryption
Wikis
Blogs
Secure Web sites
Social media Web sites
Which organization develops RFCs?
NIST
FISMA
ISO
IETF
_______is a body of the U.S. government that provides standards for financial institutions.
E-commerce implementations using SSL should use a minimum of____-bit encryption.
What is a trusted source for an SSL certificate called?
Trusted certificate
Trusted authority
Certificate authority
Certificate trusted
_______sets the FISMA standards for the federal IT systems.
1. "IEEE-SA Overview" (IEEE Standards Association, 2010). http://standards.ieee.org/sa-mem/sa-view.html (accessed April 14, 2010).
2. "Mission, Vision, Core Competencies, and Core Values" (NIST, July 10, 2009). http://www.nist.gov/public_affairs/mission.cfm (accessed May 20, 2010).
3. "Detailed Overview" (NIST—Computer Security Division—Computer Security Resource Center, May 20, 2010). http://csrc.nist.gov/groups/SMA/fisma/overview.html (accessed May 20, 2010).
4. "ISO—News—ISO and IEEE strengthen partnership for development of international standards." ISO—International Organization for Standardization. http://www.iso.org/iso/pressrelease?refid=Ref1125 (accessed May 20, 2010).