Chapter 8. Physical Security
This chapter helps you prepare for the Certified Information Systems Auditor (CISA) exam by covering the following ISACA objectives, which include understanding the role and importance of physical security. This includes items such as the following.
Tasks
Evaluate the design, implementation, and monitoring of environmental controls to prevent or minimize loss.
Evaluate the design, implementation, and monitoring of physical access controls to ensure that information assets are adequately safeguarded.
Evaluate the processes and procedures used to store, retrieve, transport, and dispose of confidential information assets.
Knowledge Statements
Knowledge of environmental protection practices and devices (e.g., fire suppression, cooling systems, water sensors)
Knowledge of physical security systems and practices (e.g., biometrics, access cards, cipher locks, tokens)
Knowledge of data classification schemes (e.g., public, confidential, private, and sensitive data)
Knowledge of the processes and procedures used to store, retrieve, transport, and dispose of confidential information assets
Environmental Protection Practices
Heating, Ventilation, and Air Conditioning (HVAC)
Fire Prevention, Detection, and Suppression
Deploying and Implementing Policies
Physical Asset and Information Control
This chapter addresses information you need to know about physical security. An organization can have the best logical controls in the world; however, they are of little use if no physical security is present. Most of the information you need to pass the CISA exam deals with logical access and controls such as encryption, firewalls, antivirus software, and intrusion detection. Yet physical security is also required and is one of the items that must be examined during an audit. The following are the primary topics a CISA candidate should review for the exam:
![]() Understand the threats to physical security
Understand the threats to physical security
![]() Know the ways in which a layered defense can be designed to provide defense-in-depth
Know the ways in which a layered defense can be designed to provide defense-in-depth
![]() Know what controls, procedures, and mechanisms are needed to protect the safety of employees
Know what controls, procedures, and mechanisms are needed to protect the safety of employees
![]() Describe the various types of physical access controls including gates, locks, and guards
Describe the various types of physical access controls including gates, locks, and guards
![]() Know personal safety controls, including fire prevention and fire detection
Know personal safety controls, including fire prevention and fire detection
Introduction
Physical security might not be a topic you automatically think of when you hear the words “IT audit,” but it is a key component. You could have the best firewall, IDS, and wireless encryption in the world, yet it would do little good if someone can walk into your server room and simply walk out with a hard drive or computer. Physical security is not just about the protection of assets; it is also about people. This means having the right controls in place for the protection of life. This includes fire detection, alarm, and suppression systems; protection against blackout, humidity, and temperature controls; and plans and procedures in case of emergencies.
Physical Security
Tasks
![]() Evaluate the design, implementation, and monitoring of physical access controls to ensure that information assets are adequately safeguarded.
Evaluate the design, implementation, and monitoring of physical access controls to ensure that information assets are adequately safeguarded.
![]() Evaluate the design, implementation, and monitoring of environmental controls to prevent or minimize loss.
Evaluate the design, implementation, and monitoring of environmental controls to prevent or minimize loss.
![]() Evaluate the processes and procedures used to store, retrieve, transport, and dispose of confidential information assets.
Evaluate the processes and procedures used to store, retrieve, transport, and dispose of confidential information assets.
The most important aspect of physical security is control. If you can gain physical control of a device, it almost always means that this can be leveraged to control the behavior of the device. This is what makes physical security such an important piece of overall security. Physical security can be attacked from many different angles, from stealing data, to hardware modification, to the bypass of security controls. Each angle offers the potential to gain access or understanding of how a security control works.
It might be argued that physical security is more important now than at any time in the past. This bold statement holds true because businesses do have better logical controls—better firewalls, antivirus, IDS, and encryption—than ever. For the attacker or malicious individual, this can mean that physical access offers the most attractive means to target an organization. In the past, the few computers that an organization had were probably well-secured mainframes that were locked in a server room. Today there is a computer on every desk, a fax machine in every office, and employees with camera phones, PDAs, and iPods that can quickly move pictures or gigabytes of data out of the organization almost instantly. Many employees also have USB thumb drives that can hold a gigabyte of data or more. How many sensitive documents would one of these devices hold?
This section begins by looking at physical security exposures and then looks at some of the various types of physical security controls that can be used to protect the organization. These include equipment controls, area controls, facility controls, and personal safety controls. Next, you will learn about environmental protection practices and authentication and authorization.
Physical Security Exposures
Whereas logical security exposures are centered on disclosure, denial of service, and alteration, physical security exposures deal with theft, vandalism, and destruction. These threats can be caused by natural, man-made, or technical events. Companies might have to deal with several of these at the same time. We start by reviewing the types of natural events that organizations can be exposed to:
![]() Floods—Floods result from too much rain, when the soil has poor retention properties or when creeks and rivers overflow their banks. There’s also the risk of internal building flooding from broken pipes, or a water main pipe breaking near or in the server/document storage room.
Floods—Floods result from too much rain, when the soil has poor retention properties or when creeks and rivers overflow their banks. There’s also the risk of internal building flooding from broken pipes, or a water main pipe breaking near or in the server/document storage room.
Note
Population Growth Is Booming in Storm-Prone Areas Information from http://www.noaa.gov shows that Americans are moving disproportionately into storm-prone areas. From 1930 to 2000, the population of the United States rose only 230%, yet the population of storm-prone areas rose exponentially. For example, the population of Miami-Dade County rose 1,800%. Broward County, Florida, grew at a whopping 8,000% during the same time.
![]() Fire—Many controls such as smoke alarms and sprinklers can be put in place to minimize damage from this common natural disaster and reduce the threat to physical security.
Fire—Many controls such as smoke alarms and sprinklers can be put in place to minimize damage from this common natural disaster and reduce the threat to physical security.
![]() Hurricanes and tropical storms—Hurricanes are the most destructive force known to man. These natural events have the power to cause monumental damage. A good example of this was Hurricane Katrina, the power of which was enough to destroy New Orleans.
Hurricanes and tropical storms—Hurricanes are the most destructive force known to man. These natural events have the power to cause monumental damage. A good example of this was Hurricane Katrina, the power of which was enough to destroy New Orleans.
![]() Tidal waves—Tidal waves are also known as tsunamis. The word tsunami is based on a Japanese word that means “harbor wave.” This natural phenomenon consists of a series of widely dispersed waves that cause massive damage when they come ashore. The December 2004 Indian Ocean tsunami is believed to have killed more than 230,000 people.
Tidal waves—Tidal waves are also known as tsunamis. The word tsunami is based on a Japanese word that means “harbor wave.” This natural phenomenon consists of a series of widely dispersed waves that cause massive damage when they come ashore. The December 2004 Indian Ocean tsunami is believed to have killed more than 230,000 people.
![]() Earthquakes—Earthquakes are caused from movement of the earth along fault lines. Many areas of the earth are vulnerable to earthquakes if they are on or near a fault line.
Earthquakes—Earthquakes are caused from movement of the earth along fault lines. Many areas of the earth are vulnerable to earthquakes if they are on or near a fault line.
Although other chapters will focus more on disaster recovery and business continuity, it’s possible that companies might have to deal with more than one physical threat at any particular time. For example, consider New Orleans and Hurricane Katrina. Businesses in New Orleans were faced with the need to address a hurricane, flooding, and loss of communication almost simultaneously.
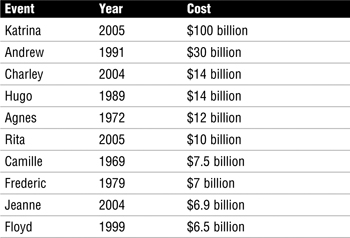
Storms can be extremely costly. Table 8.1 ranks, by cost, ten of the worst hurricanes from 1900 to 2005, according to the National Hurricane Center.
Table 8.1 Top 10 Most Costly Hurricanes
Exposures occur not just from natural events, but they can also be man-made. They are sometimes accidental, but they might also be deliberate. They can come from any direction: Outsiders or insiders might threaten the physical security of the organization. In most business environments, insiders pose a bigger threat to the organization than do outsiders. Why? Because typically, committing a crime requires three elements: means, opportunity, and motive. Although outsiders might have a motive, the means and opportunity might be hard for them to obtain. Compare this to the trusted insider, who most likely has the means and opportunity and lacks only a motive. Basically, insiders have two of the three things needed for an attack. The following list looks at some of these potential man-made events.
![]() Unauthorized entry—Controlling who enters a facility, when they enter, and what they have access to is critical to the security of an organization.
Unauthorized entry—Controlling who enters a facility, when they enter, and what they have access to is critical to the security of an organization.
![]() Vandalism or damage—Since the Vandals sacked Rome in 455 A.D., the term vandalism has been synonymous with the willful destruction of the property of others.
Vandalism or damage—Since the Vandals sacked Rome in 455 A.D., the term vandalism has been synonymous with the willful destruction of the property of others.
![]() Theft—Theft of company assets can range from mildly annoying to extremely damaging. Your CEO’s laptop might be stolen from the airport. In this case, is the real loss the laptop or the plans for next year’s new product release?
Theft—Theft of company assets can range from mildly annoying to extremely damaging. Your CEO’s laptop might be stolen from the airport. In this case, is the real loss the laptop or the plans for next year’s new product release?
Note
Identity Theft Is a Growing Problem Current and past U.S. military veterans came close to learning the value of theft of personal identification when it was revealed that personal details of as many as 26.5 million veterans had been lost by means of a stolen laptop. Although the laptop and data were eventually recovered, it does not negate the breach of confidentiality or the fact that stronger security controls had not been used.
![]() Access to sensitive information—This exposure is linked directly to the loss of confidentiality. Information has value, and the loss of sensitive information can be extremely expensive. As an example, a trusted insider might place a keystroke logger on a co-worker’s computer to find out more about a sensitive project that is being considered.
Access to sensitive information—This exposure is linked directly to the loss of confidentiality. Information has value, and the loss of sensitive information can be extremely expensive. As an example, a trusted insider might place a keystroke logger on a co-worker’s computer to find out more about a sensitive project that is being considered.
![]() Alteration of equipment setting or information—If an employee can access a system or change a setting, he can bypass access controls and any useful audit information can be altered or destroyed. As an example, a quick visit to the Cisco site provides you with the information needed to reset passwords and gain entry into any Cisco device.
Alteration of equipment setting or information—If an employee can access a system or change a setting, he can bypass access controls and any useful audit information can be altered or destroyed. As an example, a quick visit to the Cisco site provides you with the information needed to reset passwords and gain entry into any Cisco device.
![]() Disclosure of information—This category of exposure covers all threats that involve the deliberate or accidental disclosure of sensitive information. The privacy of information is affected because information is exposed without authorization. As an example, the insider that collected information by means of keystroke logging might offer it to a competitor for a large amount of money.
Disclosure of information—This category of exposure covers all threats that involve the deliberate or accidental disclosure of sensitive information. The privacy of information is affected because information is exposed without authorization. As an example, the insider that collected information by means of keystroke logging might offer it to a competitor for a large amount of money.
![]() Abuse of resources—This exposure can include any use of a resource that is not authorized by policy and procedure. This can include playing time-consuming computer games, using computer accounts for work not authorized for that account, and sending chain letters or other items for personal profit or illegal purposes.
Abuse of resources—This exposure can include any use of a resource that is not authorized by policy and procedure. This can include playing time-consuming computer games, using computer accounts for work not authorized for that account, and sending chain letters or other items for personal profit or illegal purposes.
![]() Blackmail—This is the act of threatening to perform a damaging action or make public sensitive information about a person or company unless certain demands are met.
Blackmail—This is the act of threatening to perform a damaging action or make public sensitive information about a person or company unless certain demands are met.
![]() Embezzlement—This is the fraudulent appropriation of money or services from the organization.
Embezzlement—This is the fraudulent appropriation of money or services from the organization.
![]() Destruction—This threat can come from insiders or outsiders and can include vandalism and damage. The destruction of physical assets can cost organizations huge sums of money.
Destruction—This threat can come from insiders or outsiders and can include vandalism and damage. The destruction of physical assets can cost organizations huge sums of money.
Note
Top Losses Reported by Organizations FBI statistics compiled in 2005 noted that the top three losses by organizations were due to computer viruses, unauthorized access, and theft of proprietary information. As an example, even the FBI faces this problem—in the last three years, the FBI has lost or suffered the theft of 61 laptops holding extremely sensitive information (http://www.itbusinessedge.com/item/?ci=24214).
Potential threats to physical security can come from all angles, and it’s important to consider all the ways in which an organization can suffer from undue exposure. Discarded media is one of these exposures. A malicious individual needs only to sift through an organization’s trash to potentially find many types of useful information. This activity is known as dumpster diving. Figure 8.1 illustrates what the results of dumpster diving can yield.
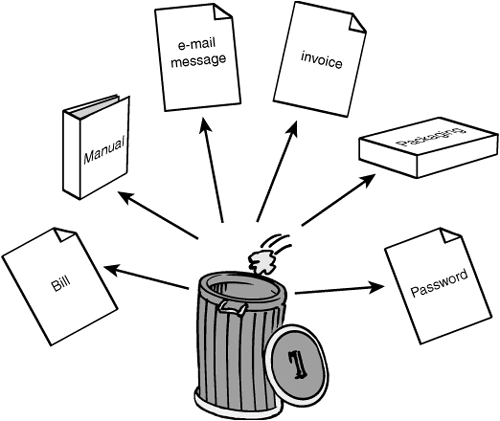
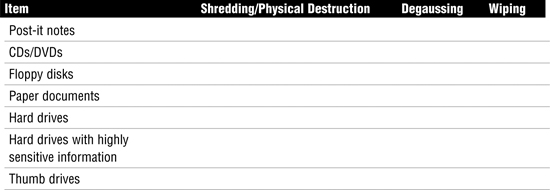
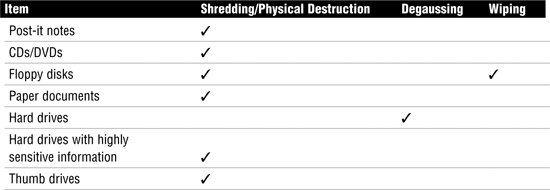
Dumpster diving can reveal usernames, passwords, account numbers, and even enough information for identity theft. To prevent this type of activity, good policies should be implemented detailing what can and cannot be thrown away. Paper shredders should also be located throughout the facility so that employees can properly dispose of sensitive information. Many of these shredders can also shred DVDs and CDs. If this feature is not built in, organizations should purchase separate media shredding equipment. Hard drives and floppies also need to be properly disposed of. For these types of durable media, overwriting and degaussing are the preferred techniques:
![]() Drive wiping—This is the act of overwriting all information on the drive. As an example, DoD.5200.28-STD (7) specifies overwriting the drive with a special digital pattern through seven passes. Drive wiping allows the drive to be reused.
Drive wiping—This is the act of overwriting all information on the drive. As an example, DoD.5200.28-STD (7) specifies overwriting the drive with a special digital pattern through seven passes. Drive wiping allows the drive to be reused.
![]() Degaussing—This process is used to permanently destroy the contents of the hard drive or magnetic media. Degaussing works by means of a powerful magnet that uses its field strength to penetrate the housing of the hard drives and reverse the polarity of the magnetic particles on the hard disk platters. After a drive has been degaussed, it cannot be reused. Next to physical destruction, degaussing is the most secure way to ensure that the drive cannot be reused.
Degaussing—This process is used to permanently destroy the contents of the hard drive or magnetic media. Degaussing works by means of a powerful magnet that uses its field strength to penetrate the housing of the hard drives and reverse the polarity of the magnetic particles on the hard disk platters. After a drive has been degaussed, it cannot be reused. Next to physical destruction, degaussing is the most secure way to ensure that the drive cannot be reused.
Exam Alert
Destroying Sensitive Information The CISA exam expects candidates to know that the best way to destroy paper, plastic, or photographic data is through physical destruction, such as shredding or incineration. Also, the best way to destroy durable or magnetic media is by degaussing or overwriting.
The two types of shredders are strip-cut and cross-cut:
![]() Strip-cut shredder—Slices the paper into long, thin strips. Strip-cut shredders generally handle a higher volume of paper with lower maintenance requirements. This type of shredder is cheap but doesn’t shred well enough to prevent reassembly of the shredded document.
Strip-cut shredder—Slices the paper into long, thin strips. Strip-cut shredders generally handle a higher volume of paper with lower maintenance requirements. This type of shredder is cheap but doesn’t shred well enough to prevent reassembly of the shredded document.
![]() Cross-cut—Provides more security by cutting paper vertically and horizontally into confetti. Although this type of shredder is more expensive, the shredded documents are much more difficult to reconstruct or reassemble. Some organizations pay for vendors to come on-site and shred their sensitive documents while an employee or monitor watches. These vendors might also handle disposal.
Cross-cut—Provides more security by cutting paper vertically and horizontally into confetti. Although this type of shredder is more expensive, the shredded documents are much more difficult to reconstruct or reassemble. Some organizations pay for vendors to come on-site and shred their sensitive documents while an employee or monitor watches. These vendors might also handle disposal.
Possible Perpetrators
Remember earlier in the chapter when the concept of means, opportunity, and motive (MOM) was introduced? If you apply this model to insiders and outsiders, who comes up as the greater risk? Insiders do: They possess two of the three items needed to commit a crime—means and opportunity. Outsiders typically have motive but not means or opportunity. Insiders are even more of a risk today because of advances in technology. Malicious insiders have many tools at their disposal, such as key chain–size hard drives, steganography, encryption, and wireless technology, that might make them harder to detect.
Note
Insider Attacks The FBI and the Computer Security Institute conduct an annual FBI/CSI Computer Crime and Security Survey of U.S. corporations, government agencies, financial institutions, and universities. In 2005, the information security professionals who responded to this survey reported that disgruntled and dishonest employees represented almost 80% of the known attacks on their computer systems.
This doesn’t mean that all exposures are malicious, of course. The most likely source of exposure is human error, accidents, or unintentional acts. People make mistakes, and without proper controls, this can have devastating effects. Table 8.2 shows some of the individuals who might be the source of an attack and their relationship to the organization.
Table 8.2 Perpetrators and Their Motives
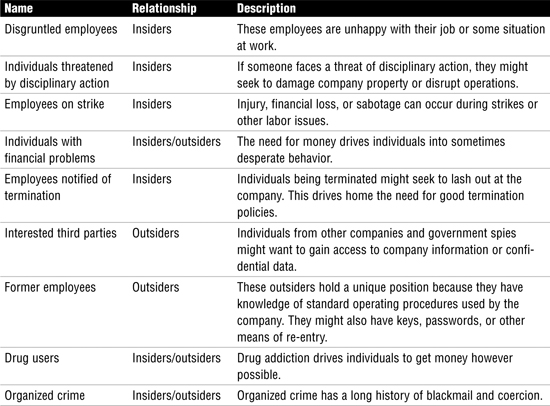
Organizations can be attacked in many different ways. Unfortunately, not all exposures are mistakes—many are purposeful and are usually the most damaging. A determined perpetrator can target a company for a low-tech social-engineering attack or dumpster diving, or might attempt physical entry. Depending on their motives, attackers can do a huge amount of damage if they are successful. Let’s look now at physical controls to see how to better protect an organization.
Physical Security Controls
A need for physical security has always existed. In the ancient history of man, castles were built for the safety and protection of the inhabitants. Even in the United States, the Anasazi Indians built their homes in the sides of cliffs to protect them from attack. In the modern world, physical security controls are designed to protect the organization from unauthorized access. These controls support the concept of confidentiality, integrity, and availability. As with any other control, these work best when layered. This offers the maximum amount of protection to slow intruders or make their target so unattractive that they move on. Physical security controls have three primary goals:
8.1 Building Layered Control to Deter Attackers
1. Deter the attacker by using controls such as security lighting, No Trespassing signs, and armed guards.
2. Delay the attacker by using fences, gates, locks, access controls, and mantraps. Each of the techniques slows the attacker and makes the task more difficult.
3. Detect the attacker by using controls such as closed-circuit TV (CCTV) and alarms.
Let’s continue this discussion by looking at some different types of controls, such as exterior, interior, and personal controls.
Exterior Controls
The first line in the defense-in-depth model is the design and placement of exterior controls. These controls prevent unauthorized individuals from gaining access to the facility. If you are involved in the design of a new facility, you might have the ability to ensure that many of these controls are added during design. That’s not always the case, however: Often you are tasked with examining an existing facility. In both new and old facilities, the goal should be to look for controls that have been designed so that the breach of any one defensive layer will not compromise the physical security of the organization. Perimeter security controls can be any physical barrier, such as a wall, card-controlled entry, or a staffed reception desk. Perimeter security requires examination of the following:
![]() Natural boundaries at the location
Natural boundaries at the location
![]() Fences or walls around the site
Fences or walls around the site
![]() Gates, access doors, the delivery dock, and entry points
Gates, access doors, the delivery dock, and entry points
![]() The design of the outer walls of a building
The design of the outer walls of a building
![]() Lighting and exterior design of the complex
Lighting and exterior design of the complex
Fences, Gates, and Bollards
Fences are one of the first layers of defense and one of the key components of perimeter security. When it is of the proper design and height, fencing can delay an intruder and also work as a psychological barrier. Just think about the Berlin Wall. This monument to the Cold War was quite effective in preventing East Germans from escaping to the west. Before its fall in 1989, most individuals that escaped to the west did so by hiding in trunks of cars or by bribing guards. The wall worked as a strong physical as well as psychological barrier. Does the height or gauge of wire used in the fence matter? Yes, taller fences with thicker gauge wire work better at deterring determined intruders, as outlined in Table 8.3. and Table 8.4.
Table 8.3 Fence Mesh and Gauge
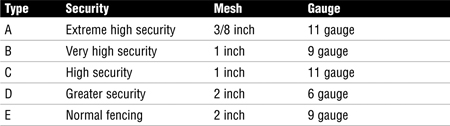
Table 8.4 Fence Height and Purpose

Organizations that require very high security might consider using a perimeter intrusion and detection assessment system (PIDAS). This special fencing system works somewhat like an intrusion-detection system, in that it has sensors to detect anyone climbing or cutting the fence.
Note
Deterrence by Design The design of the physical environment and proper layout of access controls can increase security in many ways. An entire discipline actually was built around this concept, known as crime prevention through environmental design (CPTED); see http://www.cpted.net/.
Although fences are a good start, more physical controls, such as proper gates, can help. Gates act as a chokepoint to control the ingress and egress of employees and visitors into and out of the facility. Just as with fences, standards govern the strength of gates and the security of their design, as detailed in UL Standard 325.
Not only people need to be restricted on the grounds of a facility—vehicles must also be controlled. One method of controlling vehicles is to use bollards. Made of concrete or steel, bollards are used to block vehicular traffic. You might have noticed them in front of the doors of the facility or even at the local mall; sometimes they even look like large flower pots. Regardless of their shape, they are designed for one purpose: to prevent cars and trucks from ramming into a building and smashing doors. Recently designed bollards have electronic sensors to detect collisions and notify building inhabitants that someone has rammed the facility.
Although fences are considered the first line of defense, bollards are a close second because they further protect employees and the facility from common smash-and-grab techniques and terrorist car bombings.
Exam Alert
Auditing Physical Controls Exam candidates must understand that some physical controls cannot be tested. As an example, you most likely will not set off a fire extinguisher, but you can make sure that the fire extinguisher has been serviced regularly and refilled as regulations recommend. Auditing physical controls requires mainly observation. While touring a facility, visually observe the safeguards discussed throughout this chapter and note their presence or absence.
Other Exterior Concerns
A few other exterior controls can further secure the facility:
![]() Using dogs for guard duty—Breeds such as German shepherds and chows have been used for centuries to guard facilities and assets. Dogs can be trained and are loyal, obedient, and steadfast, yet they are sometimes unpredictable and could bite or harm the wrong person. Because of these factors, dogs are usually restricted to exterior premises control and should be used with caution.
Using dogs for guard duty—Breeds such as German shepherds and chows have been used for centuries to guard facilities and assets. Dogs can be trained and are loyal, obedient, and steadfast, yet they are sometimes unpredictable and could bite or harm the wrong person. Because of these factors, dogs are usually restricted to exterior premises control and should be used with caution.
![]() Adopting a low-key design—The last thing an organization that handles sensitive information or high-value assets wants to do is to advertise its presence to attackers or others that might target the facility. The building or department should be discreetly identified. Server rooms, computer rooms, and other sensitive areas should not be easily visible and should contain no windows.
Adopting a low-key design—The last thing an organization that handles sensitive information or high-value assets wants to do is to advertise its presence to attackers or others that might target the facility. The building or department should be discreetly identified. Server rooms, computer rooms, and other sensitive areas should not be easily visible and should contain no windows.
![]() Controlling points of entrance—Just as gates are used to control how individuals can enter and leave the property, doors should be used to control access into the building itself. All unnecessary entry points to the grounds and the facility should be eliminated.
Controlling points of entrance—Just as gates are used to control how individuals can enter and leave the property, doors should be used to control access into the building itself. All unnecessary entry points to the grounds and the facility should be eliminated.
![]() Using adequate lighting—Lighting is great perimeter protection. Far too much criminal activity happens at night or in poorly lit areas. Outside lighting discourages prowlers and thieves. Failure to adequately light parking lots and other high-traffic areas also could lead to lawsuits if an employee or visitor is attacked in a poorly lit area. Effective lighting means that the system is designed to put the light where it is needed in the proper wattage. More light isn’t necessarily better: Too much light causes overlighting and glare.
Using adequate lighting—Lighting is great perimeter protection. Far too much criminal activity happens at night or in poorly lit areas. Outside lighting discourages prowlers and thieves. Failure to adequately light parking lots and other high-traffic areas also could lead to lawsuits if an employee or visitor is attacked in a poorly lit area. Effective lighting means that the system is designed to put the light where it is needed in the proper wattage. More light isn’t necessarily better: Too much light causes overlighting and glare.
What else can be done? Warning signs or notices should be posted to deter trespassing. A final review of the grounds area should be conducted to make sure that nothing has been missed. This includes securing any opening that is 96 square inches or larger within 18 feet of the ground, such as manholes and tunnels, gates leading to the basement, elevator shafts, ventilation openings, and skylights. Even the roof, basement, and walls of a building might contain vulnerable points of potential entry and should, therefore, be assessed. When these activities have been completed, you can move on to analyzing interior controls.
Interior Controls
Maybe you’ve heard the phrase “security starts at the front door.” This applicable statement is of utmost importance to keep unauthorized individuals out of the facility or areas where they do not belong. This means you provide only the minimum level of access required for authorized employees and restrict unauthorized individuals so they have no access. Interior controls include the following:
![]() Doors
Doors
![]() Windows
Windows
![]() Receptionists or security guards
Receptionists or security guards
![]() Walls
Walls
![]() Locks
Locks
![]() Access control
Access control
Doors, Windows, and Walls
The weakest point of a structure is usually the first to be attacked. This is an important item to consider because, I assure you, a criminal will. The door itself is an easy target.
Doors must be of sufficient strength to protect critical assets. The interior doors at your house might be hollow core, but that is not of sufficient strength for a server room or other critical asset; these doors should have a solid core. Doors also have fire ratings and should be of the same specification as the walls to which they are attached. In addition, you should look closely at the placement of the hinges. Most doors open out, for safety reasons, but hinges need to be protected. Also, if the ceiling above the door has a plenum, the attacker might be able to climb over the door into the room via the plenum. For assets such as a server room, hinges should be on the inside of the door. The door should also have a strong strike plate and sturdy frame as shown in Figure 8.2; otherwise, an attacker can simply place a car jack into the frame and pry it open.
Figure 8.2 A strike plate helps prevent the bypassing of locked doors.

A great solid-core door is of little use if someone can simply remove the hinges to gain entry. Doors come in various configurations:
![]() Personal doors
Personal doors
![]() Industrial doors
Industrial doors
![]() Vehicle access doors
Vehicle access doors
![]() Bulletproof doors
Bulletproof doors
![]() Vault doors
Vault doors
A final note about doors involves when to use electric locks. These locks can operate in one of two ways when power fails:
![]() Fail safe—These doors fail in the locked position if power is cut. Although this means that the facility is secure, it also means that employees might not be able to get out of the facility.
Fail safe—These doors fail in the locked position if power is cut. Although this means that the facility is secure, it also means that employees might not be able to get out of the facility.
![]() Fail soft—Locks of this type fail open. Employees can easily leave if power is disrupted, but intruders can also easily enter.
Fail soft—Locks of this type fail open. Employees can easily leave if power is disrupted, but intruders can also easily enter.
Windows are a common point of entry for thieves, burglars, and others seeking access; they are actually much more of a problem than doors because they are usually designed with aesthetics, not security, in mind. The Romans were the first to use glass windows, and ever since, we have valued them as a way to let light in while providing a view. That view does come with a cost. Interior and exterior windows should be fixed in place and should be shatter proof. If critical operations are taking place in areas with windows, the windows should be either opaque or translucent. It’s also a good idea to use sensors on the windows that can trip an alarm in case of breakage or damage.
Strong windows are not enough; walls are another important consideration. A reinforced wall can keep a determined attacker from entering an area through a way other than the defined doors. Walls should also be designed to slow the spread of fires to protect employees. If the floor is raised, as is the practice in a server room, you will want to verify that antistatic measures have been put in place. Many buildings use false ceilings. Areas such as server rooms should have walls that go all the way up to the roof; there should be no way someone can lift a ceiling panel and crawl from one room to another.
Locks and Access Control
Mechanical locks are one of the most effective and widely used forms of access control. Nothing provides as great of a level of protection for so little cost. Locks have been used for at least 4,000 years. The Egyptians used locks made of wood. Lock design improved during the 1700s, when warded and tumbler locks began to be used. These are the two most common types of locks used even today.
The warded lock, the most basically designed mechanical lock still in use, uses a series of wards that a key must match up to. This is the cheapest type of mechanical lock and also the easiest to pick. You can find these at any local hardware store, but they should not be used to protect a valuable asset.
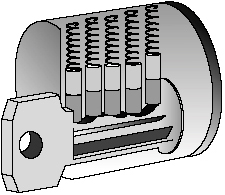
Tumbler locks are considered more advanced because they contain more parts and are harder to pick. Linus Yale patented the modern tumbler lock in 1848. When the right key is inserted into the cylinder of a tumbler lock, the pins are lifted to the right height so that the device can open or close. The correct key has the proper number of notches and raised areas that allow the pins to be shifted into the proper position. The pins are spring-loaded so that when the key is removed, the pins return to the locked position. Figure 8.3 shows an example of a tumbler lock.
Another common form of lock is a tubular lock. Tubular locks are also known as Ace locks and are considered very secure because they are harder to pick. Tubular locks require a round key, as the lock itself has the pins arranged in a circular pattern. These are used for computers, vending machines, and other high-security devices.
When examining locks, just remember that you get what you pay for. More expensive locks are usually better made. The quality of a lock is determined by its grade. Table 8.5 describes the three grades of locks.
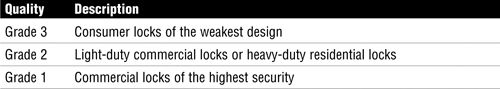
Different types of locks provide different levels of protection. The American National Standards Institute (ANSI) defines the strength and durability of locks. As an example, Grade 3 locks are designed to function for 200,000 cycles, a Grade 2 lock must function for 400,000 cycles, and a Grade 1 lock must function for 800,000 cycles. Higher-grade locks are designed to withstand much more usage, are less likely to fail sooner, or wear so that they can be easily bypassed. Thus, it’s important to select the appropriate lock to obtain the required level of security.
One way to bypass a lock is to pick it. This is usually not a criminal’s preferred method. Breaking a window, prying a doorframe, or even knocking a hole in sheetrock might all be faster methods to gain access. Individuals who pick locks do so because it is a stealthy way to bypass security controls and might make it harder for victims to figure out that they have been compromised. These basic components are used to pick locks:
![]() Tension wrenches—These are not much more than a small angled flathead screwdriver. They come in various thicknesses and sizes
Tension wrenches—These are not much more than a small angled flathead screwdriver. They come in various thicknesses and sizes
![]() Picks—As the name implies, these are similar to a dentist pick. Picks are small, angled, and pointed
Picks—As the name implies, these are similar to a dentist pick. Picks are small, angled, and pointed
Together, these tools can be used to pick a lock. One of the easiest techniques to learn is scrubbing, which is accomplished by applying tension to the lock with the tension wrench and then quickly scraping the pins. Some of the pins are placed in a mechanical bind and stuck in the unlocked position.
Tip
Control Physical Access Company keys should be stamped “Do Not Duplicate.”
Note
Bump Keys Present New Danger Bump keys, or “999” keys, are keys that have been cut to the deepest allowable position. They present a new threat, as they can be used to gain unauthorized access. These special keys gained prominence after a 2005 Dutch TV special that highlighted the fact that many locks were vulnerable. Attackers place the bump key into the lock and give it a quick tap. A vulnerability in many locks drives the pins upward and allows the lock to open. For more information about this threat, take a look at http://stadium.weblogsinc.com/engadget/videos/lockdown/bumping_040206.pdf.
Personnel Controls
Organizations can have a large number of individuals moving about the facility during the working day. These individuals are usually a mix of people, including employees, suppliers, salesmen, contractors, and even the folks who stock the vending machines in the break room. Personnel controls limit the access and freedom of these individuals, and also provide a means of audit. Organizations must have a way to hold individuals accountable for their actions and activities.
Guards
Guards are a very basic type of protection. Guards have one very basic skill that sets them apart from computerized gear: discernment. Guards have the ability to make a judgment call, to look at something and know that it is just not right. Computerized premises-control equipment has actually increased the need for guards because someone must manage all these systems. Guards also can play a dual role by answering the phone, taking on the role of a receptionist and escorting visitors while in the facility. If guards are being used at a facility you are visiting, look closely to see how they are used because the principle of defense-in-depth can also be applied here. Guards are most useful with locked doors used in conjunction with closed-circuit TV (CCTV) systems. The CCTV systems can be actively monitored or recorded and watched later. CCTV systems don’t prevent security breaches; they just alert the guard to a potential problem as it is occurring or afterward.
Guards do have some disadvantages—after all, they are only human. Guards are capable of poor judgment and can make mistakes. Therefore, if an organization hires guards from an external vendor, they should be bonded to protect the agency from loss.
Whether or not a guard is in place, the movement of visitors throughout the facility should be controlled. Anyone entering the building, including friends, visitors, vendors, contractors, and even maintenance personnel, should be escorted. Mantraps or a deadman door can control access into or out of the facility; these usually are found at the entryways of high security areas and require the outer door to be closed before authentication can take place and the inner door is opened. This is really just a system of doors that are arranged so that when one opens, the other remains locked.
Identification
ID badges are a simple method of identification. Policy should dictate that all the organization’s employees must wear and display them. Table 8.6 lists the most common types of ID badges.
Table 8.6 Basic Identification Types
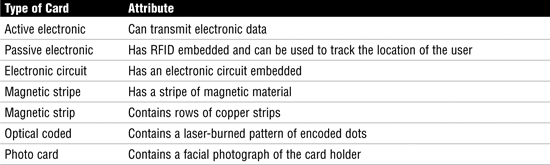
Badges can range from the rather simple photo ID badge to the more sophisticated electronic ID badge. The cards described in Table 8.6, such as those with active electronics or electronic circuits, are really a type of smart card that might require the user to insert them into a card slot; others might require only that the user get the card close to the access-control device.
Intrusion Detection
Physical intrusion-detection systems (IDS) can also monitor the movement of individuals. These systems are particularly useful for detecting unauthorized physical access and can be designed to trigger from many types of sensors. These sensors can be placed around windows, attached to doors, or placed in pressure mats to trigger when someone steps on them. Three common types exist:
![]() Photoelectric—Uses infrared light
Photoelectric—Uses infrared light
![]() Motion detectors—Triggered from audio, wave pattern, or capacitance
Motion detectors—Triggered from audio, wave pattern, or capacitance
![]() Pressure sensitive—Sensitive to weight
Pressure sensitive—Sensitive to weight
The disadvantages of physical IDS is that these systems can produce a large number of false positives. They also require monitoring and response. When an alarm sounds, someone must respond and ascertain whether the event was a true positive.
Exam Alert
Auditing Intrusion Detection When auditing a physical IDS, you should always verify that it has been properly tied to a backup power supply. This is a key control because, without acceptable backup power, someone can bypass the IDS by killing the power.
We have talked about a range of safeguards and controls throughout the last couple of sections. Your area of concern should not stop here. During an actual audit, you should ensure that these controls extend beyond the organization’s facility. These controls should also be present at remote locations, shared sites, service provider facilities, or other third parties. The IT auditor should examine each of these if sensitive information or assets are stored there.
Environmental Protection Practices
Knowledge Statement
![]() Knowledge of environmental protection practices and devices (e.g., fire suppression, cooling systems, water sensors)
Knowledge of environmental protection practices and devices (e.g., fire suppression, cooling systems, water sensors)
Electrical power is the lifeblood of computer systems. As an IT auditor, you must make sure that the data center and critical systems have the power they need and that it is clean and usable.
Power Anomalies
Power systems can suffer from a range of problems. Table 8.7 outlines the most common power system problems and their solutions.
Table 8.7 Common Power System Problems and Solutions
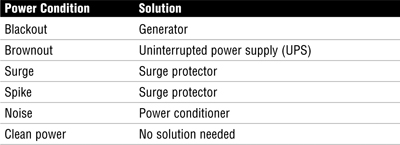
Even if you have taken measures to prevent these problems, you should be aware of others. Florescent lights can generate electrical problems, a phenomenon known as radio frequency interference (RFI). Power lines are also subject to line noise and can suffer from electromagnetic interference (EMI). Even electrical motors can cause EMI.
Power Protections
Keeping power to critical systems is an important task. One way to help ensure that the power keeps flowing is to use power leads from two substations. This might not always be possible, but it is feasible when you are selecting the location of your own facility. Power grids are usually divided along highways, so you might be able to place a facility within a short distance of two substations. If you can accomplish this, don’t defeat the purpose by placing both cables on the same set of poles or in the same trench. The idea is to try to avoid any single point of failure.
Although electricity is a great thing, at times you might need to kill power quickly, especially if someone is accidentally electrocuted or if there is danger of flooding. National fire-protection code NFPA 70 (http://www.nfpa.org) requires that you have an emergency power-off (EPO) switch located near the exit door to kill power quickly, if needed. These big red buttons are easy to identify.
Exam Alert
Protecting Against False Alarms CISA candidates should know what are considered important preventive controls. As an example, the EPO switch should have a durable plastic cover installed over the switch to prevent anyone from accidentally activating it.
Uninterrupted power supplies (UPS) and standby generators are two other power-protection mechanisms. A UPS is a device with one or more lead acid batteries and a circuit board that can intelligently monitor power and sense if power is lost. If power is lost, the UPS can supply power for a limited amount of time so that the system can be shut down properly or a generator can be started. The most common types of power backup systems are as follows:
![]() Online systems—An online system uses AC power to charge a bank of DC batteries. These batteries are held in reserve until power fails. At that time, a power inverter converts the DC voltage back to AC for the computer systems to use. These systems are good for short-term power outages.
Online systems—An online system uses AC power to charge a bank of DC batteries. These batteries are held in reserve until power fails. At that time, a power inverter converts the DC voltage back to AC for the computer systems to use. These systems are good for short-term power outages.
![]() Standby system—This type of system monitors the power line for failure. When a failure is sensed, backup power is switched on. These systems rely on generators or power subsystems to keep computers running for longer power outages.
Standby system—This type of system monitors the power line for failure. When a failure is sensed, backup power is switched on. These systems rely on generators or power subsystems to keep computers running for longer power outages.
![]() Generator—The generator is a longer-term device. When the UPS signals the generator, it can power up and assume power responsibilities. Most standby generators work on diesel fuel or natural gas:
Generator—The generator is a longer-term device. When the UPS signals the generator, it can power up and assume power responsibilities. Most standby generators work on diesel fuel or natural gas:
![]() Diesel fuel—Should maintain at least 12 hours of fuel
Diesel fuel—Should maintain at least 12 hours of fuel
![]() Natural gas—Should be suitable for areas that have a good supply of natural gas and are geologically stable
Natural gas—Should be suitable for areas that have a good supply of natural gas and are geologically stable
Heating, Ventilation, and Air Conditioning (HVAC)
Do you know what can be hotter than Houston in the summer? A room full of computers without proper HVAC. Plan for adequate power for the right locations. Rooms that have servers or banks of computers and IT gear need adequate cooling to protect the equipment. Electronic equipment is quite sensitive; temperatures above 110°F to 115°F can damage circuits. Most data centers are kept to temperatures of around 70°F.
High humidity can be a problem because it causes rust and corrosion. Low humidity increases the risk of static electricity, which could damage equipment. The ideal humidity for a data center is 35%–45%.
Ventilation is another important concern. Facilities should maintain positive pressurization and ventilation. This controls contamination by pushing air outside. This is especially important in case of fire because it assures that smoke will be pushed out of the facility instead of being pulled in.
The final issue with HVAC is access control. Control of who has access to the system and how they can be contacted is an import issue. The bombing of the World Trade Center and the anthrax scare of 2001 increased awareness of the role HVAC systems play in protecting the health and safety of employees. These systems must be controlled to protect organizations and their occupants from the threat of chemical and biological threats.
Fire Prevention, Detection, and Suppression
Each year, fires result in injuries, deaths, and business losses. Organizations can avoid such injuries and losses by being prepared and practicing good fire-prevention practices. A big part of prevention is making sure people are trained and know how to prevent possible fire hazards. Fires need three things: oxygen, heat, and fuel. With those components, fires can present a lethal threat and can be devastating. Employees should be trained to deal with fires. Holding random periodic fire drills is another important component. Employees should be instructed to go to a designated area outside the facility, in a safe zone. Supervisors or others should be in charge of the safe zones to ensure that everyone is present and accounted for. Employees should also badge in after the drill when everyone is re-entering the building. This is a perfect time for an outsider to sneak in as a “tailgater” behind other employees streaming back into the building.
Fire detectors can work in different ways. They can be activated by the following:
![]() Heat—A fixed temperature thermostat is usually set to trigger above 200°F or when the temperature rises quickly.
Heat—A fixed temperature thermostat is usually set to trigger above 200°F or when the temperature rises quickly.
![]() Smoke—A smoke-activated sensor can be powered by a photoelectric optical detector or a radioactive smoke-detection device.
Smoke—A smoke-activated sensor can be powered by a photoelectric optical detector or a radioactive smoke-detection device.
![]() Flame—A flame-activated sensor functions by sensing either ultraviolet radiation or the pulsation of the flame.
Flame—A flame-activated sensor functions by sensing either ultraviolet radiation or the pulsation of the flame.
Fires are rated according to the types of materials that are burning. Whereas it might be acceptable to throw some water on smoldering paper, it would not be a good idea to try that with a grease fire. Table 8.8 lists four common fire types and their corresponding suppression methods.
Table 8.8 Fire-Suppression Methods

Exam Alert
Minimum Protection Levels CISA candidates need to know the minimum protection standards for data centers. As an example, data center walls should have at least a two-hour fire rating.
Water Sprinklers
Water sprinklers are an effective means of extinguishing Class A fires. Water is easy to work with, is widely available, and is nontoxic. The disadvantage of using sprinkler systems is that water is damaging to electronics. Any time the data center is adjacent to any water pipe, water detector sensors should be adequately placed to give fair warning of a potentional flood. When water is used in the computer room, water detectors should be used. These should be under the raised floor and near drains, to quickly detect problems.
Four variations of sprinkler systems are available:
![]() Dry pipe—As the name implies, this sprinkler system maintains no standing water. When activated, air flows out of the system and water flows in. The benefit of this type of system is that it reduces the risk of accidental flooding and gives some time to cover or turn off electrical equipment.
Dry pipe—As the name implies, this sprinkler system maintains no standing water. When activated, air flows out of the system and water flows in. The benefit of this type of system is that it reduces the risk of accidental flooding and gives some time to cover or turn off electrical equipment.
![]() Wet pipe—Wet pipe systems are widely used and ready for activation; this system is charged and full of water. The next time you are staying in a hotel, take a look around and you will probably see this type of system. They typically use some type of fusible link that allows discharge when the link breaks or melts.
Wet pipe—Wet pipe systems are widely used and ready for activation; this system is charged and full of water. The next time you are staying in a hotel, take a look around and you will probably see this type of system. They typically use some type of fusible link that allows discharge when the link breaks or melts.
![]() Preaction—This is a combination system. Pipes are initially dry and do not fill with water until a predetermined temperature is reached. Even then, the system will not activate until a secondary mechanism triggers. The secondary mechanism might be some type of fusible link, as used in a wet pipe system.
Preaction—This is a combination system. Pipes are initially dry and do not fill with water until a predetermined temperature is reached. Even then, the system will not activate until a secondary mechanism triggers. The secondary mechanism might be some type of fusible link, as used in a wet pipe system.
![]() Deluge—This is similar to a dry pipe system, except that when the system is triggered, there is no holding back the water: A large volume of water will cover a large area quickly.
Deluge—This is similar to a dry pipe system, except that when the system is triggered, there is no holding back the water: A large volume of water will cover a large area quickly.
Halon
Halon was originally used in computer rooms for fire suppression. For years, it was considered a preferred fire-suppression system because it mixes easily with air, doesn’t harm computer equipment, and, when dissipates, leaves no solid or liquid residue. Halon is found in two configurations:
![]() Halon 1211—Used in portable extinguishers and stored as a liquid
Halon 1211—Used in portable extinguishers and stored as a liquid
![]() Halon 1301—Used in fixed flooding systems and stored as a gaseous agent
Halon 1301—Used in fixed flooding systems and stored as a gaseous agent
The downside is that Halon is 3–10 times more damaging to the ozone layer than chlorofluorocarbons (CFCs). Because of this, the Montreal Protocol of 1987 designated Halon as an ozone-depleting substance. Halon also is toxic if subject to high temperatures of 900°F or more because it degrades into hydrogen fluoride, hydrogen bromide, and bromine. People should not breathe this toxic compound.
Existing Halon systems should be replaced. Some common EPA-approved replacements include the following:
![]() FM-200
FM-200
![]() NAF-S-3
NAF-S-3
![]() Argon
Argon
Physical Authentication
Task
![]() Evaluate the design, implementation, and monitoring of physical access controls to ensure that information assets are adequately safeguarded.
Evaluate the design, implementation, and monitoring of physical access controls to ensure that information assets are adequately safeguarded.
Knowledge Statement
![]() Knowledge of physical security systems and practices (e.g., biometrics, access cards, cipher locks, tokens)
Knowledge of physical security systems and practices (e.g., biometrics, access cards, cipher locks, tokens)
Controlling access into a facility or within various parts of the organization is a good security practice. Employees should be restricted to only the areas of the facility that they need access to for the completion of their daily tasks.
Authentication Methods
Authentication ensures that the correct person is granted access. This is accomplished in three basic ways:
![]() Something You Know—Passwords, PIN numbers.
Something You Know—Passwords, PIN numbers.
![]() Something You Have—USB tokens, smart cards, magnetic strip cards. Figure 8.4 depicts a smart card.
Something You Have—USB tokens, smart cards, magnetic strip cards. Figure 8.4 depicts a smart card.
![]() Something You Are—Based on what you are, such as a fingerprint, retina scan, or voice print.
Something You Are—Based on what you are, such as a fingerprint, retina scan, or voice print.
Figure 8.4 Generic smart card.

Biometrics
Biometric systems have made a lot of progress in the last decade; events such as 9/11 have increased the acceptance of biometric systems. Many different types of biometric systems exist, as described in this list (shown in order of best response times and lowest error rates):
1. Palm scan—System that analyzes characteristics associated with the palm, such as the creases and ridges of a user’s palm.
2. Hand geometry—Another biometric system that uses the unique geometry of a user’s fingers and hand to determine the user’s identity. It is one of the oldest biometric techniques.
3. Iris recognition—A very accurate eye-recognition system, with more than 400 points of reference. It matches the person’s blood vessels on the back of the eye.
4. Retina pattern—This system requires the user to remove any glasses and stare at a specific point for 10–15 seconds.
5. Fingerprint—System that is widely used for access control to facilities and items such as laptops. It works by distinguishing 30–40 details about the peaks, valleys, and ridges of the user’s fingerprint.
6. Facial scan—System that requires the user to place his or her face about 2 to 5 feet from the camera.
7. Voice recognition—System that uses voice analysis for identification and authentication. Its main advantage is that it can be used for telephone applications.
Biometric systems have varying levels of accuracy. For example, fingerprint-scanning systems base their accuracy on an analysis of minutiae. These are the ridge endings and bifurcations found on the fingertips, as shown in Figure 8.5. Although the number of minutiae varies from finger to finger, the information can be stored electronically in file sizes that usually range from 250 to 1,000 bytes. When a user logs in, the stored file containing the minutiae is compared to the individual’s finger being scanned.
Figure 8.5 Fingerprint recognition.

The accuracy of biometric devices is measured by the percentage of Type 1 and Type 2 errors they produce. Type 1 errors, false rejection rate (FRR), are a measurement of the percentage of individuals who should have gotten in but were not allowed access. Type 2 errors, false acceptance rate (FAR), are a measurement of the percentage of individuals who gained access but should not have been allowed in. When these two values are combined, the accuracy of the system is established. The point at which the FRR and FAR meet is known as the equal error rate (EER).
Although many items should be considered when deploying a biometric authentication system, this is one of the key accuracy factors—the lower the EER, the more accurate the system. Another attribute of biometric systems is that you cannot easily loan a fingerprint, retina, or hand to someone else. However, studies have demonstrated that these systems can be bypassed by using not much more than fake fingerprints made with gelatin in a clay mold. You can read more about this ingenious attack at http://www.puttyworld.com/thinputdeffi.html.
Note
Backup Authentication If biometrics is being used, the auditor should verify that backup authentication methods are available in case the biometric system fails.
Policies and Procedures
Knowledge Statements
![]() Knowledge of data classification schemes (e.g., public, confidential, private, and sensitive data)
Knowledge of data classification schemes (e.g., public, confidential, private, and sensitive data)
![]() Knowledge of the processes and procedures used to store, retrieve, transport, and dispose of confidential information assets
Knowledge of the processes and procedures used to store, retrieve, transport, and dispose of confidential information assets
We have seen that the physical realm is an important area of concern because of the many areas of potential exposure. We also have looked at various types of controls to protect the facility, to control the access of individuals, and to identify and authenticate who goes where in the organization. The key to making all these controls work is policy; the best intentions in the world are of little use without the backing of policy. Establishing security policies, guidelines, and procedures is a critical step in securing the physical infrastructure and its information. Policies encompass much more than just physical security. Policies also address administrative and technical concerns. The lack of well-designed viable security polices and documents is one of the biggest vulnerabilities many organizations have. Building a policy framework is not easy. According to www.complianceandprivacy.com, 60% of companies do not have an information security policy. After a policy is defined, the next challenge is to implement it and get employees to follow it. The following sections discuss the types of security policies, how to define appropriate policies, how to deploy policies, and the lifecycle of security policies.
Types of Policies
Policies come in many shapes and sizes. With so many types of policies, how can you keep track of them all? National Institute of Standards and Technology (NIST) documentation classifies policies in three broad categories:
![]() Management—These policies define security roles and responsibilities within an organization. They also define how policy is created, revised, and retired.
Management—These policies define security roles and responsibilities within an organization. They also define how policy is created, revised, and retired.
![]() Operational—These policies deal with operational aspects of the organization, including physical security and employee training and awareness.
Operational—These policies deal with operational aspects of the organization, including physical security and employee training and awareness.
![]() Technical—These policies address all things technical. These are the policies that IT employees are familiar with. These types of policies cover such things as identification and authentication and account management.
Technical—These policies address all things technical. These are the policies that IT employees are familiar with. These types of policies cover such things as identification and authentication and account management.
Within these categories of policies are many different individual policies. Combined, these policies should control every aspect of security within an organization. Policies are not technology specific. This type of control is left for lower-level documents, such as procedures.
Purpose of Policies
Policies play a very specific role in the document structure. Policy must flow from the top. If management does not support it, it will fail. On a broad level, policies should do six things for an organization:
1. Protect confidential, proprietary, and sensitive information from unauthorized disclosure, modification, theft, or destruction
2. Define appropriate and inappropriate activities of employees
3. Reduce or eliminate legal liability to employees and outsiders
4. Prevent waste of company IT resources
5. Comply with federal, state, local, and regulatory requirements
6. Demonstrate due diligence and due care
Most of these six items deal with preventing or reducing risk. Therefore, some type of risk assessment is usually performed before policies are created. Nothing happens in a void.
Defining Policies
Before drafting an actual policy, a clear objective must be decided. Organizations also must determine who the policy applies to and who is responsible for the policy. These three key sections are as follows:
1. Purpose—Articulates why the policy was created, its purpose, and what the organization will gain from its creation. Policies can be created because of regulatory requirements, to be informative, or to advise on certain required activities or behaviors.
2. Scope—Specifies who the policy applies to. It might address all users who telecommute, those who have computer access, or only those who have access to the server room.
3. Responsibility—Defines who is responsible. Someone must be in charge of the policy to verify that it has been properly implemented and that employees are aware of its requirements and have received adequate training.
When the draft policy is developed, it must be approved by upper management and evaluated to ascertain that the objectives that drove the policy development were met or exceeded.
Note
Change Management Auditors involved in this process should make sure that the policy has been designed so that it can be updated and changed as needed. As with everything else in the world, policies require periodic change.
Deploying and Implementing Policies
After polices have been created, they must be deployed and made operational. Employee awareness and employee buy-in are needed to make this step successful. Employees must be made aware that the policies exist and should be provided training as to the purpose and meaning of specific policies.
Auditors are not always involved in the development process and many times examine the role of policies only after they have been deployed. In this situation, the auditor should look for indications of potential problems. These can include the following:
![]() Policies and procedures that are out-of-date and have not been updated
Policies and procedures that are out-of-date and have not been updated
![]() Policies that do not comply with the law
Policies that do not comply with the law
![]() The lack of a review process for current policies and procedures
The lack of a review process for current policies and procedures
![]() The lack of documented policies and procedures
The lack of documented policies and procedures
![]() Reliance on key personnel for instructions and guidance instead of the policy or procedure
Reliance on key personnel for instructions and guidance instead of the policy or procedure
![]() Undefined process that lacks policies and procedures
Undefined process that lacks policies and procedures
Exam Alert
Compliance Verification Auditors typically verify compliance by conducting interviews with employees, observing information-processing methods, and reviewing procedures, manuals, and documents.
Physical Asset and Information Control
All organizations encounter a lot of paper documents. These might contain information that is rather trivial or might hold the company’s most valuable secrets. Information must be protected while in storage and also in transit. The information owners are ultimately responsible for determining how assets and resources are protected.
Exam Alert
Document Transportation IT auditors should examine how organizations store and transport written documents. One area of concern is interoffice communication. Regulations such as HIPAA have increased the need for secure distribution. Document-distribution carts should be secured to prevent unauthorized access. An example of this type of inter-office communication cart can be found at http://www.filingtoday.com/Mailroom_Mail_Room_HIPAA_Lock_Top_Carts_Systems_REI.html.
The primary means of establishing value is establishing data classification levels so that sufficient controls can ensure their confidentiality. Two widely used systems have been adopted to protect information:
![]() Government classification system—Focused on secrecy
Government classification system—Focused on secrecy
![]() Commercial classification system—Focused on integrity
Commercial classification system—Focused on integrity
Let’s look at each one in a little more detail. The governmental information classification system developed by the Department of Defense (DoD) is most concerned with protecting the confidentiality of information. Therefore, it is divided into categories of Unclassified, Confidential, Secret, and Top Secret, as described in Table 8.9.
Table 8.9 DoD Classification System

The commercial information classification system is categorized as public, sensitive, private, and confidential, as shown in Table 8.10.
Table 8.10 Commercial Classification System
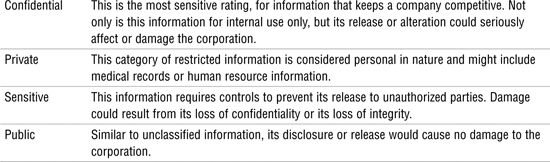
Note
Choosing the Right Classification System The classification methods described in Table 8.10 are just examples of data classification. The amount of classification levels, the requirements for each level, and the controls associated with each level should be analyzed specifically at every organization that is working on implementing such a system.
Regardless of the system being used, the role of an IT auditor is to see that the system was well developed and is being followed. A process must evaluate the value of information and determine its value and an approved method of storing documentation must de developed. After establishing a data classification schema, one method of classification is as follows:
1. Identify the administrator or custodian who will be in charge of maintaining the data.
2. Specify the criteria that will be used to identify how the data will be classified and at what layer of sensitivity.
3. The data owner must indicate and acknowledge the classification of the data.
4. Specify and document any exceptions that are allowed to the classification policy.
5. Indicate the security controls that will be implemented to protect each classification level.
6. Specify the end-of-life (EOF) procedures for declassifying the information and procedures for transferring custody of the information to another entity.
7. Integrate these issues into an employee-awareness program so that individuals understand and acknowledge the classification controls.
The information-classification process is of critical importance because it forces organizations to ask themselves what would happen if specific information was released and how its release would damage or affect the organization; possible legal requirements such as data retention should also be considered.
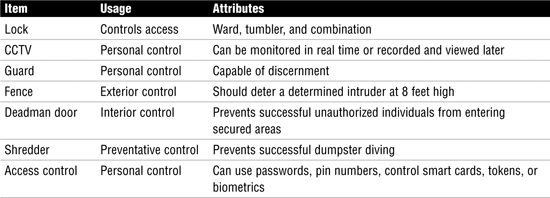
Review Break
Physical security is like logical security, in that it benefits from defense-in-depth. Notice how each of the following physical security controls offers a different type of control.
Chapter Summary
In this chapter, you learned about physical security. Physical security is as important as logical security and should be examined closely during an IT audit or assessment. Physical security might been seen as something that only prevents unauthorized access, but its usefulness cannot be overstated. Physical controls do not just involve the protection of property; they also protect employees and equipment. Items such as smoke detectors, fire alarms, and fire-suppression systems all add to security, as does lighting. They protect employees and can aid in evacuation. During the 1993 World Trade Tower attack, it took nearly four hours for people to evacuate the dark, smoky, poorly lit stairwells
Physical security works best when set up as defense-in-depth, layering one security mechanism on top of another. Therefore, you need locked servers located in a controlled access room, protected by a solid-core door and walls of the same strength. The facility should also be secure, with items such as CCTV cameras and controlled access such as mantraps. Together these layers make it much harder for someone to penetrate. Even the exterior of the facility can be made more secure by adding fences, gates, and possibly guards.
Finally, the chapter reviewed policies, procedures, and the classification of information. Documents are not just in electronic form; paper documents should be classified so that employees know their value and can take measures to protect them against theft or duplication. Without policies, there is no controlling mechanism in place. Policies reinforce physical security and provide control. Policies detail what management expects and provide a general roadmap on how these items will be achieved. Policies also show management’s commitment to support employees and what types of controls are put in place to protect sensitive information. Policies outline acceptable and unacceptable behavior and can be used to enhance physical, logical, and administrative controls.
Key Terms
![]() Bollards
Bollards
![]() Closed-circuit TV (CCTV)
Closed-circuit TV (CCTV)
![]() Commercial information classification system
Commercial information classification system
![]() Fire detection
Fire detection
![]() Fire prevention
Fire prevention
![]() Fire suppression
Fire suppression
![]() Governmental information classification system
Governmental information classification system
![]() Man-made threat
Man-made threat
![]() Shoulder surfing
Shoulder surfing
![]() Social engineering
Social engineering
![]() Tailgating
Tailgating
![]() Tumbler lock
Tumbler lock
![]() Warded lock
Warded lock
Apply Your Knowledge
This chapter stressed the importance of physical security. Logical controls are of little good if someone can just walk in, sit down, and start accessing computer networks and data.
Exercises
8.1 Physical Security Checklist
In this exercise, you examine common concerns of physical security.
Estimated Time: 30 Minutes
1. Download the physical security checklist at http://www.callio.com/expertise/tmpldesc.asp?domid=7&id=34.
2. Complete the checklist using your organization as an example.
3. Examine the list. Do you feel that your organization is taking physical security seriously? Could more be done?
Exam Questions
1. The IS auditor is examining the authentication system used and has been asked to make a recommendation on how to improve it. Which of the following choices is generally considered the most effective form of two-factor authentication?
![]() A. Token and pin
A. Token and pin
![]() B. Token and photo ID card
B. Token and photo ID card
![]() C. Pin and password
C. Pin and password
![]() D. Fingerprint and hand geometry
D. Fingerprint and hand geometry
2. Which of the following is the first step in the data-classification process after establishing a data classification schema?
![]() A. Reviewing security controls
A. Reviewing security controls
![]() B. Reviewing existing security policies
B. Reviewing existing security policies
![]() C. Determining data sensitivity
C. Determining data sensitivity
![]() D. Identifying the custodian
D. Identifying the custodian
3. Various types of locks have been developed for security. Which type of programmable lock uses a keypad for entering a pin number or password?
![]() A. Cipher lock
A. Cipher lock
![]() B. Device lock
B. Device lock
![]() C. Warded lock
C. Warded lock
![]() D. Tumbler lock
D. Tumbler lock
4. The equal error rate (EER) is used by which of the following?
![]() A. Locks
A. Locks
![]() B. Physical risk assessment
B. Physical risk assessment
![]() C. Biometrics
C. Biometrics
![]() D. Firewalls
D. Firewalls
5. Which of the following best describes a system used to detect physical attackers?
![]() A. Fences
A. Fences
![]() B. Lights
B. Lights
![]() C. Closed-circuit TV (CCTV)
C. Closed-circuit TV (CCTV)
![]() D. Locks
D. Locks
6. You have been asked to examine a biometrics system that will be used for a high-security area. With this in mind, which of the following is the most important rating to examine?
![]() A. The false rejection rate (FRR)
A. The false rejection rate (FRR)
![]() B. Finding a biometric system with a low equal error rate (EER)
B. Finding a biometric system with a low equal error rate (EER)
![]() C. The speed of the biometric system
C. The speed of the biometric system
![]() D. The false acceptance rate (FAR)
D. The false acceptance rate (FAR)
7. This system is usually not tested and is verified by reviewing documentation.
![]() A. Smoke detectors
A. Smoke detectors
![]() B. Generators
B. Generators
![]() C. Fire-suppression systems
C. Fire-suppression systems
![]() D. Emergency evacuation plans
D. Emergency evacuation plans
8. Which of the following is the best replacement for Halon?
![]() A. Low-pressure water mists
A. Low-pressure water mists
![]() B. FM-200
B. FM-200
![]() C. NAT-4000
C. NAT-4000
![]() D. Hydrogen bromide
D. Hydrogen bromide
9. Which of the following is the classification of a gasoline or oil fire?
![]() A. Class A
A. Class A
![]() B. Class B
B. Class B
![]() C. Class C
C. Class C
![]() D. Class D
D. Class D
10. Which of the following best describes a physical control that would control the flow of employees into the facility and allow security to hold those who fail authorization?
![]() A. A turnstile
A. A turnstile
![]() B. A deadman door
B. A deadman door
![]() C. A piggyback
C. A piggyback
![]() D. Biometric authentication
D. Biometric authentication
Answers to Exam Questions
1. A. A token and pin is the only two-factor authentication method shown. Answers B, C, and D all represent single-factor authentication methods. Therefore answers B, C, and D are incorrect.
2. D. The first step is to identify the administrator or custodian. Next, it is important to specify the criteria that will be used to identify how the data will be classified. The data owner must acknowledge the classification of the data, followed by any exceptions that are allowed to the classification policy. The security controls that will be implemented to protect each classification level should be indicated next. The end-of-life (EOF) procedures for declassifying the information and procedures for transferring custody of the information to another entity should be specified. The final step is integration.
3. A. A cipher lock is one in which a keypad is used for entering a pin number or passwords. These are commonly used on secured doors to control access. Answer B is incorrect because a device lock is used to secure a piece of equipment such as a laptop. Answer C is incorrect because a warded lock is a basic low-end padlock that can be easily picked. Answer D is incorrect because a tumbler lock is an improved version of a warded lock. Tumblers make it harder for the wrong key to open the wrong lock.
4. C. The equal error rate is a biometric measurement of the point at which the FAR and the FRR intersect. When these two values are combined, the accuracy of the system is established. The lower the EER, the more accurate the biometric system. Locks, risk assessment, and firewalls do not use EER ratings; therefore, answers A, B, and D are incorrect.
5. C. CCTV is a good example of a system used to detect physical attacks. Answer A is incorrect because fences are used to deter or delay intruders; answers B and D are incorrect because lights and locks also deter and delay intruders.
6. D. The FAR provides a way to measure how many people who should not have access could be able to gain entry into a high-security area. Although answers A, B, and C are all important, they are not the most important issue in this situation.
7. C. Fire-suppression systems are usually not tested because of the high cost involved. They are verified by reviewing documentation. Answers A, B, and D are incorrect because these systems are tested at least once yearly.
8. B. FM-200 is the preferred replacement for Halon because it does not damage equipment, as water mists would. Answers A, C, and D are incorrect because water is damaging, NAT-4000 is not used for fire suppression, and hydrogen bromide is a byproduct of Halon when exposed to high temperatures.
9. B. A gas or oil fire is considered Class B. Class A covers common combustibles, Class C covers electrical fires, and Class D covers metals. Therefore answers A, C, and D are incorrect.
10. B. A deadman door is a set of two doors. The idea is that only one person can enter at a time; the outer door must shut before the inner door will open. Answer A is incorrect because a turnstile controls the flow of human traffic and is similar to a one-way gate. Answer C is incorrect because piggybacking is the act of riding in on someone’s coat tails. Answer D is incorrect because biometric authentication would not prevent more than one person at a time from entering.
Need to Know More?
![]() Physical Security Audit Information Available from ASIS International: http://www.asisonline.org/
Physical Security Audit Information Available from ASIS International: http://www.asisonline.org/
![]() Physical Security Audit Checklist: http://tinyurl.com/35or2b
Physical Security Audit Checklist: http://tinyurl.com/35or2b
![]() High-Availability Power: http://www.powerquality.com/mag/power_high_availability_electrical/
High-Availability Power: http://www.powerquality.com/mag/power_high_availability_electrical/
![]() How Locks Work: http://home.howstuffworks.com/lock-picking.htm
How Locks Work: http://home.howstuffworks.com/lock-picking.htm
![]() Lock Picking: http://www.gregmiller.net/locks/
Lock Picking: http://www.gregmiller.net/locks/
![]() All About Halon: http://en.wikipedia.org/wiki/Halon
All About Halon: http://en.wikipedia.org/wiki/Halon
![]() Fire Suppression Without Halon: http://tinyurl.com/3a5nfg
Fire Suppression Without Halon: http://tinyurl.com/3a5nfg
![]() Building an Information Classification System: http://tinyurl.com/2vxgsr
Building an Information Classification System: http://tinyurl.com/2vxgsr
![]() Data Classification the Easy Way: http://www.security-manual.com/classify.htm
Data Classification the Easy Way: http://www.security-manual.com/classify.htm