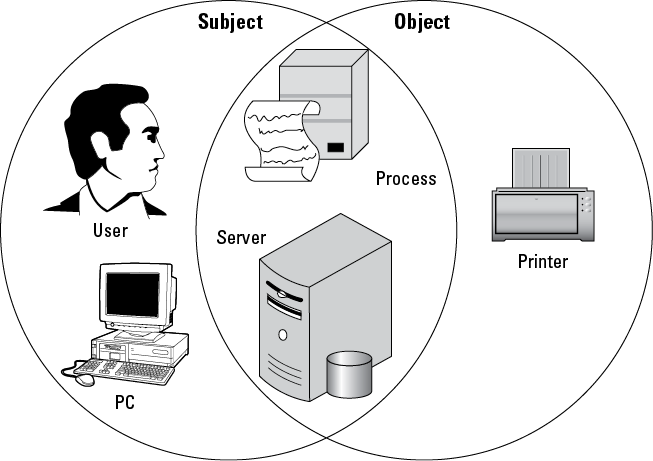
Figure 4-1: Objects and subjects in access control.
Basic Concepts of Access Control
Access control, in the context of information security, permits an organization’s management to define and control which systems or resources a user has access to, and what that user can do on that system or resource. More formally, access control is the ability to permit or deny the use of an object (a passive entity, such as a system or file) by a subject (an active entity, such as an individual or process). Such use is normally defined through sets of rules or permissions (such as Read, Write, Execute, List, Change, and Delete) and combinations of various security mechanisms (such as administrative, technical, and physical controls).
A subject is always the active entity that attempts to perform an action on (in this case, access) an object, which is always the passive entity being acted upon. You can’t always identify an object or subject in absolute terms. For example, a process isn’t always an object. An individual user (subject) may be attempting to access a database (object) or run a batch process (object). However, for example, a batch process may actually be the subject attempting to access a database (object) or write run results to a disk (object). In another example, an individual user runs an application to access a specific file. In this example, the user is always a subject, but the application is both an object and a subject. It’s an object being run by the user, but it’s a subject accessing a file on a file server (which are both objects). See Figure 4-1.