Figure 4-2: Use CER to compare FAR and FRR.
Categories of Access Control
The two categories of access controls are
![]() System access controls: Controls in this category protect the entire system and provide a first line of defense for the data contained on the system.
System access controls: Controls in this category protect the entire system and provide a first line of defense for the data contained on the system.
![]() Data access controls: Controls in this category are specifically implemented to protect the data contained on the system.
Data access controls: Controls in this category are specifically implemented to protect the data contained on the system.
System access controls
System access controls are the hard and crunchy outside of a system, providing the first line of defense in information security. They protect systems and information by restricting access to the system.
Although system access controls can provide complete authentication, authorization, and accountability (AAA), they’re renowned for authentication.
You can base authentication on any of three factors:
![]() Something you know, such as a password or a personal identification number (PIN): This concept is based on the assumption that only the owner of the account knows the secret password or PIN needed to access the account. Username and password combinations are the simplest, least expensive, and therefore most common authentication mechanism implemented today. Of course, passwords are often shared, stolen, guessed, or otherwise compromised — thus they’re also one of the weakest authentication mechanisms.
Something you know, such as a password or a personal identification number (PIN): This concept is based on the assumption that only the owner of the account knows the secret password or PIN needed to access the account. Username and password combinations are the simplest, least expensive, and therefore most common authentication mechanism implemented today. Of course, passwords are often shared, stolen, guessed, or otherwise compromised — thus they’re also one of the weakest authentication mechanisms.
![]() Something you have, such as a smart card or token: This concept is based on the assumption that only the owner of the account has the necessary key to unlock the account. Smart cards, USB tokens, and key fobs are becoming more common, particularly in relatively secure organizations, such as government or financial institutions. Although smart cards and tokens are somewhat more expensive and complex than other, less-secure authentication mechanisms, they’re not (usually) prohibitively expensive or overly complicated to implement, administer, and use, and they provide a significant boost to authentication security. Of course, keys are often lost, stolen, or damaged.
Something you have, such as a smart card or token: This concept is based on the assumption that only the owner of the account has the necessary key to unlock the account. Smart cards, USB tokens, and key fobs are becoming more common, particularly in relatively secure organizations, such as government or financial institutions. Although smart cards and tokens are somewhat more expensive and complex than other, less-secure authentication mechanisms, they’re not (usually) prohibitively expensive or overly complicated to implement, administer, and use, and they provide a significant boost to authentication security. Of course, keys are often lost, stolen, or damaged.
![]() Something you are, such as fingerprint, voice, retina, or iris characteristics: This concept is based on the assumption that the finger or eyeball attached to your body is actually yours and uniquely identifies you. (Of course, fingers and eyes can be lost or . . . .) Actually, the major drawback with this authentication mechanism is acceptance — people are sometimes uneasy about using these systems. Biometric systems are also among the most expensive authentication mechanisms to deploy.
Something you are, such as fingerprint, voice, retina, or iris characteristics: This concept is based on the assumption that the finger or eyeball attached to your body is actually yours and uniquely identifies you. (Of course, fingers and eyes can be lost or . . . .) Actually, the major drawback with this authentication mechanism is acceptance — people are sometimes uneasy about using these systems. Biometric systems are also among the most expensive authentication mechanisms to deploy.
Two-factor authentication requires two of these three authentication factors for authentication. Three-factor authentication requires all three factors for authentication.
Strong authentication requires at least two of the factors in the preceding list (something you know, something you have, and/or something you are).
Identification and authentication
The various identification and authentication (I&A) techniques that we discuss in the following sections include passwords/passphrases and PINs (knowledge-based); biometrics and behavior (characteristic-based); and one-time passwords, tokens, and single sign-on (SSO).
The identification component is normally a relatively simple mechanism based on a username or, in the case of a system or process, based on a computer name, Media Access Control (MAC) address, Internet Protocol (IP) address, or Process ID (PID). Identification requirements include only that it must uniquely identify the user (or system/process) and shouldn’t identify that user’s role or relative importance in the organization (the identification shouldn’t include labels such as accounting or CEO). Common or shared accounts, such as root, admin, or system should not be permitted. Such accounts provide no accountability and are prime targets for malicious beings.
Passwords and passphrases
“A password should be like a toothbrush. Use it every day; change it regularly; and DON’T share it with friends.” –USENET
Passwords are easily the most common — and weakest — authentication mechanism in use today. Although there are more advanced and secure authentication technologies available, including tokens and biometrics, organizations typically use those technologies as supplements to or in combination with — rather than as replacements for — traditional usernames and passwords.
A passphrase is a variation on a password; it uses a sequence of characters or words, rather than a single password. Generally, attackers have more difficulty breaking passphrases than breaking regular passwords because longer passphrases are generally more difficult to break than complex passwords. Passphrases also have the following advantages:
![]() Users frequently use the same passwords to access numerous accounts; their corporate networks, their home PCs, their Hotmail or Yahoo! e-mail accounts, their eBay accounts, and their Amazon.com accounts, for example. So an attacker who targets a specific user may be able to gain access to his or her work account by going after a less secure system, such as his or her home PC, or by compromising an Internet account (because the user has passwords conveniently stored in that bastion of security — Internet Explorer!). Internet sites and home PCs typically don’t use passphrases, so you improve the chances that your users have to use different passwords/passphrases to access their work accounts.
Users frequently use the same passwords to access numerous accounts; their corporate networks, their home PCs, their Hotmail or Yahoo! e-mail accounts, their eBay accounts, and their Amazon.com accounts, for example. So an attacker who targets a specific user may be able to gain access to his or her work account by going after a less secure system, such as his or her home PC, or by compromising an Internet account (because the user has passwords conveniently stored in that bastion of security — Internet Explorer!). Internet sites and home PCs typically don’t use passphrases, so you improve the chances that your users have to use different passwords/passphrases to access their work accounts.
![]() Users can actually remember and type passphrases more easily than they can remember and type a much shorter, cryptic password that requires contorted finger acrobatics to type on a keyboard.
Users can actually remember and type passphrases more easily than they can remember and type a much shorter, cryptic password that requires contorted finger acrobatics to type on a keyboard.
![]() A passphrase (or a password for that matter) that is 15 characters or longer cannot be stored in Active Directory or in the local Security Account Manager (SAM) accounts database using the LanManager hash, which effectively eliminates the well-known vulnerabilities associated with this hash function.
A passphrase (or a password for that matter) that is 15 characters or longer cannot be stored in Active Directory or in the local Security Account Manager (SAM) accounts database using the LanManager hash, which effectively eliminates the well-known vulnerabilities associated with this hash function.
However, passphrases also have a downside:
![]() Users can find passphrases inconvenient, so you may find passphrases difficult to implement. (“You mean I need to have a 20-character password now?!”)
Users can find passphrases inconvenient, so you may find passphrases difficult to implement. (“You mean I need to have a 20-character password now?!”)
![]() Not all systems support passphrases. Such systems ignore anything longer than the system limit (for example, eight characters).
Not all systems support passphrases. Such systems ignore anything longer than the system limit (for example, eight characters).
![]() Many command-line interfaces and tools don’t support the space character that separates words in a passphrase.
Many command-line interfaces and tools don’t support the space character that separates words in a passphrase.
![]() Ultimately, a passphrase is still just a password (albeit, a much longer and better one) and thus shares some of the same problems associated with passwords.
Ultimately, a passphrase is still just a password (albeit, a much longer and better one) and thus shares some of the same problems associated with passwords.
You, as a CISSP candidate, should understand the general problems associated with passwords, as well as common password controls and management features.
Password/passphrase problems include that they’re
![]() Insecure: Passwords are generally insecure for several reasons, including
Insecure: Passwords are generally insecure for several reasons, including
• Human nature: In the case of user-generated passwords, users often choose passwords that they can easily remember and consequently attackers can easily guess (such as a spouse’s or pet’s name, birthday, anniversary, or hobby). Users may also be inclined to write down passwords (particularly complex, system-generated passwords) or share their passwords with others.
• Transmission and storage: Many applications and protocols (such as file transfer protocol [FTP] and password authentication protocol [PAP]) transmit passwords in clear text. These applications and protocols may also store passwords in plaintext files, or in a security database that uses a weak hashing algorithm.
![]() Easily broken: Passwords are susceptible to brute-force and dictionary attacks (which we discuss in the section “Methods of attack,” later in this chapter) by readily available programs such as John the Ripper and L0phtCrack (pronounced loft-crack).
Easily broken: Passwords are susceptible to brute-force and dictionary attacks (which we discuss in the section “Methods of attack,” later in this chapter) by readily available programs such as John the Ripper and L0phtCrack (pronounced loft-crack).
![]() Inconvenient: Easily agitated users can find entering passwords tiresome. In an attempt to bypass these controls, users may select an easily typed, weak password; they may automate log-ons (for instance, selecting the Remember My Password check box in a browser); and they can neglect to lock their workstations or log out when they leave their desks.
Inconvenient: Easily agitated users can find entering passwords tiresome. In an attempt to bypass these controls, users may select an easily typed, weak password; they may automate log-ons (for instance, selecting the Remember My Password check box in a browser); and they can neglect to lock their workstations or log out when they leave their desks.
![]() Refutable: Transactions authenticated with only a password don’t necessarily provide absolute proof of a user’s identity. Authentication mechanisms must guarantee non-repudiation, which is a critical component of accountability. (For more on non-repudiation, see the section “Accountability,” earlier in this chapter.)
Refutable: Transactions authenticated with only a password don’t necessarily provide absolute proof of a user’s identity. Authentication mechanisms must guarantee non-repudiation, which is a critical component of accountability. (For more on non-repudiation, see the section “Accountability,” earlier in this chapter.)
Passwords have the following login controls and management features that you should configure in accordance with an organization’s security policy and security best practices:
![]() Length: Generally, the longer the better. A password is, in effect, an encryption key. Just as larger encryption keys (such as 1024-bit or 2048-bit) are more difficult to crack, so too are longer passwords. You should configure systems to require a minimum password length of six to eight characters. Of course, users can easily forget long passwords or simply find them too inconvenient, leading to some of the human-nature problems discussed earlier in this section.
Length: Generally, the longer the better. A password is, in effect, an encryption key. Just as larger encryption keys (such as 1024-bit or 2048-bit) are more difficult to crack, so too are longer passwords. You should configure systems to require a minimum password length of six to eight characters. Of course, users can easily forget long passwords or simply find them too inconvenient, leading to some of the human-nature problems discussed earlier in this section.
![]() Complexity: Strong passwords contain a mix of upper- and lowercase letters, numbers, and special characters such as # and $. Be aware that some systems may not accept certain special characters, or those characters may perform special functions (for example, in terminal emulation software).
Complexity: Strong passwords contain a mix of upper- and lowercase letters, numbers, and special characters such as # and $. Be aware that some systems may not accept certain special characters, or those characters may perform special functions (for example, in terminal emulation software).
![]() Aging: You should set maximum password aging to require password changes at regular intervals: 30-, 60-, or 90-day periods are common. You should also set minimum password aging — one day is usually recommended — to prevent users from easily circumventing password history controls (for example, by changing their password five times within a few minutes, then setting it back to the original password).
Aging: You should set maximum password aging to require password changes at regular intervals: 30-, 60-, or 90-day periods are common. You should also set minimum password aging — one day is usually recommended — to prevent users from easily circumventing password history controls (for example, by changing their password five times within a few minutes, then setting it back to the original password).
![]() History: Password history settings (five is usually recommended) allow a system to remember previously used passwords for a specific account. This security setting prevents users from circumventing maximum password aging by alternating between two or three familiar passwords when they’re required to change their passwords.
History: Password history settings (five is usually recommended) allow a system to remember previously used passwords for a specific account. This security setting prevents users from circumventing maximum password aging by alternating between two or three familiar passwords when they’re required to change their passwords.
![]() Limited attempts: This control limits the number of unsuccessful log-on attempts and consists of two components: counter threshold (for example, three or five) and counter reset (for example, 5 or 30 minutes). The counter threshold is the maximum number of consecutive unsuccessful attempts permitted before some action occurs (such as automatically disabling the account). The counter reset is the amount of time between unsuccessful attempts. For example, three unsuccessful log-on attempts within a 30-minute period may result in an account lockout for a set period (for example, 24 hours); but two unsuccessful attempts in 25 minutes, and then a third unsuccessful attempt 10 minutes later, wouldn’t result in an account lockout. A successful log-on attempt also resets the counter.
Limited attempts: This control limits the number of unsuccessful log-on attempts and consists of two components: counter threshold (for example, three or five) and counter reset (for example, 5 or 30 minutes). The counter threshold is the maximum number of consecutive unsuccessful attempts permitted before some action occurs (such as automatically disabling the account). The counter reset is the amount of time between unsuccessful attempts. For example, three unsuccessful log-on attempts within a 30-minute period may result in an account lockout for a set period (for example, 24 hours); but two unsuccessful attempts in 25 minutes, and then a third unsuccessful attempt 10 minutes later, wouldn’t result in an account lockout. A successful log-on attempt also resets the counter.
![]() Lockout duration (or intruder lockout): When a user exceeds the counter threshold that we describe in the preceding bullet, the account is locked out. Organizations commonly set the lockout duration to 30 minutes, but you can set it for any duration. If you set the duration to forever, an administrator must unlock the account. Some systems don’t notify the user when it locks out an account, instead quietly alerting the system administrator to a possible break-in attempt. Of course, an attacker can use the lockout duration as a simple means to perform a Denial of Service attack (intentionally making repeated bad log-on attempts to keep the user’s account locked).
Lockout duration (or intruder lockout): When a user exceeds the counter threshold that we describe in the preceding bullet, the account is locked out. Organizations commonly set the lockout duration to 30 minutes, but you can set it for any duration. If you set the duration to forever, an administrator must unlock the account. Some systems don’t notify the user when it locks out an account, instead quietly alerting the system administrator to a possible break-in attempt. Of course, an attacker can use the lockout duration as a simple means to perform a Denial of Service attack (intentionally making repeated bad log-on attempts to keep the user’s account locked).
![]() Limited time periods: This control restricts the time of day that a user can log in. For example, you can effectively reduce the period of time that attackers can compromise your systems by limiting users’ access to business hours only. However, this type of control is becoming less common in the modern age of the workaholic and the global economy, both of which require users to legitimately perform work at all hours of the day.
Limited time periods: This control restricts the time of day that a user can log in. For example, you can effectively reduce the period of time that attackers can compromise your systems by limiting users’ access to business hours only. However, this type of control is becoming less common in the modern age of the workaholic and the global economy, both of which require users to legitimately perform work at all hours of the day.
![]() System messages: System messages include the following:
System messages: System messages include the following:
• Login banner: Welcome messages literally invite criminals to access your systems. Disable any welcome message and replace it with a legal warning that requires the user to click OK to acknowledge the warning and accept the legal terms of use.
• Last username: Many popular operating systems display the username of the last successful account log-on. Users (who only need to type in their password) find this feature convenient — and so do attackers (who only need to crack the password without worrying about matching it to a valid user account). Disable this feature.
• Last successful log-on: After successfully logging on to the system, this message tells the user the last time that he or she logged on. If the system shows that the last successful log-on for a user was Saturday morning at 2:00 a.m. and the user knows that he couldn’t possibly have logged in at that time because he has a life, he knows that someone has compromised his account, and he can report the incident accordingly.
We’re sure that you know many of the following widely available and well-known guidelines for creating more secure passwords, but just in case, here’s a recap:
![]() Use a mix upper- and lowercase letters, numbers, and special characters (for example, !@#$%).
Use a mix upper- and lowercase letters, numbers, and special characters (for example, !@#$%).
![]() Do not include your name or other personal information (such as spouse, street address, school, birthdays, and anniversaries).
Do not include your name or other personal information (such as spouse, street address, school, birthdays, and anniversaries).
![]() Replace some letters with numbers (for example, replace e with 3).
Replace some letters with numbers (for example, replace e with 3).
![]() Use nonsense phrases, misspellings, substitutions, or before-and-after words and phrases (combining two unrelated words or phrases, such as “Wheel of Fortune Cookies”).
Use nonsense phrases, misspellings, substitutions, or before-and-after words and phrases (combining two unrelated words or phrases, such as “Wheel of Fortune Cookies”).
![]() Combine two words by using a special character (for example, sALT&pEPPER or BaCoN+EgGs).
Combine two words by using a special character (for example, sALT&pEPPER or BaCoN+EgGs).
![]() Use a combination of all the other tips in this list (for example, “Snow White and the Seven Habits of Highly Effective People” becomes SW&t7HoH3P!).
Use a combination of all the other tips in this list (for example, “Snow White and the Seven Habits of Highly Effective People” becomes SW&t7HoH3P!).
![]() Do not use repeating patterns between changes (for example, password1, password2, password3).
Do not use repeating patterns between changes (for example, password1, password2, password3).
![]() Do not use the same passwords for work and personal accounts.
Do not use the same passwords for work and personal accounts.
![]() Do not use passwords that are too difficult to remember.
Do not use passwords that are too difficult to remember.
![]() Do not use any passwords you see in a published book, including this one. (But you knew that.)
Do not use any passwords you see in a published book, including this one. (But you knew that.)
The problem with these guidelines is that they’re widely available and well known! In fact, attackers use some of these same guidelines to create their aliases or handles: super-geek becomes 5up3rg33k. Also, a password such as Qwerty12 technically satisfies these guidelines, but it’s not really a good password because it’s a relatively simple and obvious pattern (the first row on your keyboard). Many dictionary attacks include not only word lists, but also patterns such as this one.
Personal Identification Numbers (PINs)
A PIN in itself is a relatively weak authentication mechanism because you have only 10,000 possible combinations for a four-digit numeric PIN. Therefore, organizations usually use some other safeguard in combination with a PIN. For example, most ATMs confiscate your ATM card after three incorrect PIN attempts. A PIN used with a one-time token password and an account lockout policy is also very effective, allowing a user to attempt only one PIN/password combination per minute and then locking the account after three or five failed attempts as determined by the security policy.
Biometrics and behavior
The only absolute method for positively identifying an individual is to base authentication on some unique physiological or behavioral characteristic of that individual. Biometric identification uses physiological characteristics, including fingerprints, hand geometry, and facial features such as retina and iris patterns. Behavioral biometrics are based on measurements and data derived from an action, and they indirectly measure characteristics of the human body. Behavioral characteristics include voice, signature, and keystroke patterns.
Biometrics are based on the third factor of authentication — something you are. Biometric access control systems apply the concept of identification and authentication (I&A) slightly differently, depending on their use:
![]() Physical access controls: The individual presents the required biometric characteristic and the system attempts to identify the individual by matching the input characteristic to its database of authorized personnel. This type of control is also known as a one-to-many search.
Physical access controls: The individual presents the required biometric characteristic and the system attempts to identify the individual by matching the input characteristic to its database of authorized personnel. This type of control is also known as a one-to-many search.
![]() Logical access controls: The user enters a username or PIN (or inserts a smart card), and then presents the required biometric characteristic for verification. The system attempts to authenticate the user by matching the claimed identity and the stored biometric image file for that account. This type of control is also known as a one-to-one search.
Logical access controls: The user enters a username or PIN (or inserts a smart card), and then presents the required biometric characteristic for verification. The system attempts to authenticate the user by matching the claimed identity and the stored biometric image file for that account. This type of control is also known as a one-to-one search.
The necessary factors for an effective biometrics access control system include
![]() Accuracy: The most important characteristic of any biometric system. The uniqueness of the body organ or characteristic that the system measures to guarantee positive identification is an important element of accuracy. In common biometric systems today, the only organs that satisfy this requirement are the fingers/hands and the eyes.
Accuracy: The most important characteristic of any biometric system. The uniqueness of the body organ or characteristic that the system measures to guarantee positive identification is an important element of accuracy. In common biometric systems today, the only organs that satisfy this requirement are the fingers/hands and the eyes.
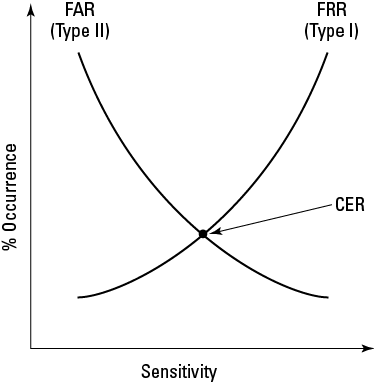
Another important element of accuracy is the system’s ability to detect and reject forged or counterfeit input data. The accuracy of a biometric system is normally stated as a percentage, in the following terms:
• False Reject Rate (FRR) or Type I error: Authorized users to whom the system incorrectly denies access, stated as a percentage. Reducing a system’s sensitivity reduces the FRR but increases the False Accept Rate (FAR).
 The False Reject Rate (or Type I error) is the percentage of authorized users to whom the system incorrectly denies access.
The False Reject Rate (or Type I error) is the percentage of authorized users to whom the system incorrectly denies access.
• False Accept Rate (FAR) or Type II error: Unauthorized users to whom the system incorrectly grants access, stated as a percentage. Increasing a system’s sensitivity reduces the FAR but increases the FRR.
 The False Accept Rate (or Type II error) is the percentage of unauthorized users to whom the system incorrectly grants access.
The False Accept Rate (or Type II error) is the percentage of unauthorized users to whom the system incorrectly grants access.
• Crossover Error Rate (CER): The point at which the FRR equals the FAR, stated as a percentage. (See Figure 4-2.) Because you can adjust the FAR and FRR by changing a system’s sensitivity, the CER is considered the most important measure of biometric system accuracy.
 The Crossover Error Rate is the point at which the FRR equals the FAR, stated as a percentage.
The Crossover Error Rate is the point at which the FRR equals the FAR, stated as a percentage.
![]() Speed and throughput: The length of time required to complete the entire authentication procedure. This time measurement includes stepping up to the system, inputting a card or PIN (if required), entering biometric data (such as inserting a finger or hand in a reader, pressing a sensor, aligning an eye with a camera or scanner, speaking a phrase, or signing a name), processing the input data, and opening and closing an access door (in the case of a physical access control system). Another important measure is the initial enrollment time required to create a biometric file for a user account. Generally accepted standards are a speed of less than five seconds, a throughput rate of six to ten per minute, and enrollment time of less than two minutes.
Speed and throughput: The length of time required to complete the entire authentication procedure. This time measurement includes stepping up to the system, inputting a card or PIN (if required), entering biometric data (such as inserting a finger or hand in a reader, pressing a sensor, aligning an eye with a camera or scanner, speaking a phrase, or signing a name), processing the input data, and opening and closing an access door (in the case of a physical access control system). Another important measure is the initial enrollment time required to create a biometric file for a user account. Generally accepted standards are a speed of less than five seconds, a throughput rate of six to ten per minute, and enrollment time of less than two minutes.
![]() Data storage requirements: Though less significant these days, data storage requirements are still an interesting issue because costs have decreased for data storage media. The size of a biometric system’s input files can be as small as 9 bytes or as large as 10,000 bytes, averaging 256 to 1,000 bytes.
Data storage requirements: Though less significant these days, data storage requirements are still an interesting issue because costs have decreased for data storage media. The size of a biometric system’s input files can be as small as 9 bytes or as large as 10,000 bytes, averaging 256 to 1,000 bytes.
![]() Reliability: Reliability is an important factor in any system. The system must operate continuously and accurately without frequent maintenance outages.
Reliability: Reliability is an important factor in any system. The system must operate continuously and accurately without frequent maintenance outages.
![]() Acceptability: Getting users to accept a biometric system is the biggest hurdle to widespread implementation. Certain privacy and ethics issues arise with the prospect of organizations using these systems to collect medical or other physiological data about employees. Other factors that might potentially alarm users include intrusiveness of the data collection procedure and undesirable physical contact with common system components, such as pressing an eye against a plastic cup or placing lips close to a microphone for voice recognition.
Acceptability: Getting users to accept a biometric system is the biggest hurdle to widespread implementation. Certain privacy and ethics issues arise with the prospect of organizations using these systems to collect medical or other physiological data about employees. Other factors that might potentially alarm users include intrusiveness of the data collection procedure and undesirable physical contact with common system components, such as pressing an eye against a plastic cup or placing lips close to a microphone for voice recognition.
Table 4-1 summarizes the generally accepted standards for the factors described in the preceding list.
Table 4-1 Generally Accepted Standards for Biometric Systems
|
Characteristic |
Standard |
|
Accuracy |
CER < 10% |
|
Speed |
5 seconds |
|
Throughput |
6–10 per minute |
|
Enrollment time |
< 2 minutes |
Common types of physiological biometric access control systems include
![]() Fingerprint recognition and finger scan systems: The most common biometric systems in use today. They analyze the ridges, whorls, and minutiae (bifurcations and ridge endings, dots, islands, ponds and lakes, spurs, bridges, and crossovers) of a fingerprint to create a digitized image that uniquely identifies the owner of the fingerprint. A fingerprint recognition system stores the entire fingerprint as a digitized image. A disadvantage of this type of system is that it can require a lot of storage space and resources. More commonly, organizations use a finger scan system, whichstores only sample points or unique features of a fingerprint and therefore requires less storage and processing resources. Also, users may more readily accept the technology because no one can re-create an entire fingerprint from the data in a finger scan system. See Table 4-2 for general characteristics of finger scan systems.
Fingerprint recognition and finger scan systems: The most common biometric systems in use today. They analyze the ridges, whorls, and minutiae (bifurcations and ridge endings, dots, islands, ponds and lakes, spurs, bridges, and crossovers) of a fingerprint to create a digitized image that uniquely identifies the owner of the fingerprint. A fingerprint recognition system stores the entire fingerprint as a digitized image. A disadvantage of this type of system is that it can require a lot of storage space and resources. More commonly, organizations use a finger scan system, whichstores only sample points or unique features of a fingerprint and therefore requires less storage and processing resources. Also, users may more readily accept the technology because no one can re-create an entire fingerprint from the data in a finger scan system. See Table 4-2 for general characteristics of finger scan systems.
 Finger scan systems, unlike fingerprint recognition systems, don’t store an image of the entire fingerprint — only a digitized file describing its unique characteristics. This fact should allay the privacy concerns of most users.
Finger scan systems, unlike fingerprint recognition systems, don’t store an image of the entire fingerprint — only a digitized file describing its unique characteristics. This fact should allay the privacy concerns of most users.
![]() Hand geometry systems: Like finger scan systems, hand geometry systems are also nonintrusive and therefore generally more easily accepted than other biometric systems. These systems generally can more accurately uniquely identify an individual than finger scan systems, and they have some of the smallest file sizes compared with other biometric system types. A digital camera simultaneously captures a vertical and a horizontal image of the subject’s hand, acquiring the three-dimensional hand geometry data. The digitized image records the length, width, height, and other unique characteristics of the hand and fingers. See Table 4-2 for general characteristics of hand geometry systems.
Hand geometry systems: Like finger scan systems, hand geometry systems are also nonintrusive and therefore generally more easily accepted than other biometric systems. These systems generally can more accurately uniquely identify an individual than finger scan systems, and they have some of the smallest file sizes compared with other biometric system types. A digital camera simultaneously captures a vertical and a horizontal image of the subject’s hand, acquiring the three-dimensional hand geometry data. The digitized image records the length, width, height, and other unique characteristics of the hand and fingers. See Table 4-2 for general characteristics of hand geometry systems.
Table 4-2 General Characteristics of Finger Scan and Hand Geometry Systems
|
Characteristic |
Finger Scan |
Hand Geometry |
|
Accuracy |
< 1%–5% (CER) |
< 1%–2% (CER) |
|
Speed |
1–7 seconds |
3–5 seconds |
|
File size |
~250–1500 bytes |
~10 bytes |
|
Advantages |
Nonintrusive, inexpensive |
Small file size |
|
Disadvantages |
Sensor wear and tear; accuracy may be affected by swelling, injury, or wearing rings |
Sensor wear and tear; accuracy may be affected by swelling, injury, or wearing rings |
![]() Retina pattern: These systems record unique elements in the vascular pattern of the retina. Major concerns with this type of system are fears of eye damage from a laser (which is actually only a camera with a focused low-intensity light) directed at the eye and, more feasibly, privacy concerns. Certain health conditions, such as diabetes and heart disease, can cause changes in the retinal pattern, which these types of systems may detect. See Table 4-3 for general characteristics of retina pattern systems.
Retina pattern: These systems record unique elements in the vascular pattern of the retina. Major concerns with this type of system are fears of eye damage from a laser (which is actually only a camera with a focused low-intensity light) directed at the eye and, more feasibly, privacy concerns. Certain health conditions, such as diabetes and heart disease, can cause changes in the retinal pattern, which these types of systems may detect. See Table 4-3 for general characteristics of retina pattern systems.
![]() Iris pattern: By far the most accurate of any type of biometric system. The iris is the colored portion of the eye surrounding the pupil. The complex patterns of the iris include unique features such as coronas, filaments, freckles, pits, radial furrows, rifts, and striations. The characteristics of the iris, formed shortly before birth, remain stable throughout life. The iris is so unique that even the two eyes of a single individual have different patterns. A camera directed at an aperture mirror scans the iris pattern. The subject must glance at the mirror from a distance of approximately 3 to 10 inches. It’s technically feasible — but perhaps prohibitively expensive — to perform an iris scan from a distance of several feet. See Table 4-3 for general characteristics of iris pattern systems.
Iris pattern: By far the most accurate of any type of biometric system. The iris is the colored portion of the eye surrounding the pupil. The complex patterns of the iris include unique features such as coronas, filaments, freckles, pits, radial furrows, rifts, and striations. The characteristics of the iris, formed shortly before birth, remain stable throughout life. The iris is so unique that even the two eyes of a single individual have different patterns. A camera directed at an aperture mirror scans the iris pattern. The subject must glance at the mirror from a distance of approximately 3 to 10 inches. It’s technically feasible — but perhaps prohibitively expensive — to perform an iris scan from a distance of several feet. See Table 4-3 for general characteristics of iris pattern systems.
Table 4-3 General Characteristics of Retina and Iris Pattern Systems
|
Characteristic |
Retina Pattern |
Iris Pattern |
|
Accuracy |
1.5% (CER) |
< 0.5% (CER) |
|
Speed |
4–7 seconds |
2.5–4 seconds |
|
File size |
~96 bytes |
~256–512 bytes |
|
Advantages |
Overall accuracy |
Best overall accuracy |
|
Disadvantages |
Perceived intrusiveness; sanitation and privacy concerns |
Subject must remain absolutely still; subject can’t wear colored contact lenses or glasses (clear contacts are generally okay) |
Common types of behavioral biometric systems include
![]() Voice recognition: These systems capture unique characteristics of a subject’s voice and may also analyze phonetic or linguistic patterns. Most voice recognition systems are text-dependent, requiring the subject to repeat a specific phrase. This functional requirement of voice recognition systems also helps improve their security by providing two-factor authentication: something you know (a phrase) and something you are (your voice). More advanced voice recognition systems may present a random phrase or group of words, which prevents an attacker from recording a voice authentication session and later replaying the recording to gain unauthorized access. See Table 4-4 for general characteristics of voice recognition systems.
Voice recognition: These systems capture unique characteristics of a subject’s voice and may also analyze phonetic or linguistic patterns. Most voice recognition systems are text-dependent, requiring the subject to repeat a specific phrase. This functional requirement of voice recognition systems also helps improve their security by providing two-factor authentication: something you know (a phrase) and something you are (your voice). More advanced voice recognition systems may present a random phrase or group of words, which prevents an attacker from recording a voice authentication session and later replaying the recording to gain unauthorized access. See Table 4-4 for general characteristics of voice recognition systems.
![]() Signature dynamics: These systems typically require the subject to sign his or her name on a signature tablet. The enrollment process for a signature dynamics system captures numerous characteristics, including the signature pattern itself, the pressure applied to the signature pad, and the speed of the signature. Of course, signatures commonly exhibit some slight changes because of different factors, and they can be forged. See Table 4-4 for general characteristics of signature dynamics systems.
Signature dynamics: These systems typically require the subject to sign his or her name on a signature tablet. The enrollment process for a signature dynamics system captures numerous characteristics, including the signature pattern itself, the pressure applied to the signature pad, and the speed of the signature. Of course, signatures commonly exhibit some slight changes because of different factors, and they can be forged. See Table 4-4 for general characteristics of signature dynamics systems.
![]() Keystroke or typing dynamics: These systems typically require the subject to type a password or phrase. The keystroke dynamic identification is based on unique characteristics such as how long a user holds down a key on the keyboard (dwell time) and how long it takes a user to get to and press a key (seek or flight time). These characteristics are measured by the system to form a series of mathematical data representing a user’s unique typing pattern or signature, which is then used to authenticate the user.
Keystroke or typing dynamics: These systems typically require the subject to type a password or phrase. The keystroke dynamic identification is based on unique characteristics such as how long a user holds down a key on the keyboard (dwell time) and how long it takes a user to get to and press a key (seek or flight time). These characteristics are measured by the system to form a series of mathematical data representing a user’s unique typing pattern or signature, which is then used to authenticate the user.
Table 4-4 General Characteristics of Voice Recognition and Signature Dynamics Systems
|
Characteristic |
Voice Recognition |
Signature Dynamics |
|
Accuracy |
< 10% (CER) |
1% (CER) |
|
Speed |
10–14 seconds |
5–10 seconds |
|
File size |
~1,000–10,000 bytes |
~1,000–1,500 bytes |
|
Advantages |
Inexpensive; nonintrusive |
Nonintrusive |
|
Disadvantages |
Accuracy, speed, file size; affected by background noise, voice changes; can be fooled by voice imitation |
Signature tablet wear and tear; speed; can be fooled by a forged signature |
One-time passwords
A one-time password is a password that’s valid for one log-on session only. After a single log-on session, the password is no longer valid. Thus, if an attacker obtains a one-time password that someone has already used, that password has no value. A one-time password is a dynamic password, meaning it changes at some regular interval or event. Conversely, a static password is a password that remains the same for each log-on. Similar to the concept of a one-time pad in cryptography (which we discuss in Chapter 8), a one-time password provides maximum security for access control.
Tokens
Tokens are access control devices such as key fobs, dongles, smart cards, magnetic cards, software (known as soft tokens and installed on a tablet, mobile device, smartphone, laptop, or PC), and keypad or calculator-type cards that store static passwords (or digital certificates) or that generate dynamic passwords. The three general types of tokens are
![]() Static password tokens: Store a static password or digital certificate.
Static password tokens: Store a static password or digital certificate.
![]() Synchronous dynamic password tokens: Continuously generate a new password or passcode at a fixed time interval (for example, 60 seconds) or in response to an event (such as each time you press a button). Typically, the passcode is valid only during a fixed time window (say, one minute) and only for a single log-on (so, if you want to log on to more than one system, you must wait for the next passcode).
Synchronous dynamic password tokens: Continuously generate a new password or passcode at a fixed time interval (for example, 60 seconds) or in response to an event (such as each time you press a button). Typically, the passcode is valid only during a fixed time window (say, one minute) and only for a single log-on (so, if you want to log on to more than one system, you must wait for the next passcode).
![]() Asynchronous (or challenge-response) dynamic password tokens: Generate a new password or passcode asynchronously by calculating the correct response to a system-generated random challenge string (known as a nonce) that the owner manually enters into the token.
Asynchronous (or challenge-response) dynamic password tokens: Generate a new password or passcode asynchronously by calculating the correct response to a system-generated random challenge string (known as a nonce) that the owner manually enters into the token.
Tokens provide two-factor authentication (something you have and something you know) by either requiring the owner to authenticate to the token first or by requiring that the owner enters a secret PIN along with the generated password. Both RADIUS and Terminal Access Controller Access Control System (TACACS+; which we discuss in the section “Centralized access controls,” later in this chapter) support various token products.
You can use tokens to generate one-time passwords and provide two-factor authentication.
Single sign-on (SSO)
The concept of single sign-on (SSO) addresses a common problem for users and security administrators alike. Multiple accounts mean multiple vulnerabilities. Every account that exists in a system, network, or application is a potential point of unauthorized access. Multiple accounts belonging to a single user represent an even greater vulnerability:
![]() Users who require access to multiple systems or applications must often maintain numerous different passwords, which inevitably leads to shortcuts in creating and recalling passwords. Users create weak passwords that have only slight variations, and they likely write down those passwords.
Users who require access to multiple systems or applications must often maintain numerous different passwords, which inevitably leads to shortcuts in creating and recalling passwords. Users create weak passwords that have only slight variations, and they likely write down those passwords.
![]() Multiple accounts also affect user productivity (and sanity!) because the user must stop to log in to different systems. Someone also has to create and maintain accounts, which involves supporting, removing, resetting, and disabling passwords, as well as unlocking accounts.
Multiple accounts also affect user productivity (and sanity!) because the user must stop to log in to different systems. Someone also has to create and maintain accounts, which involves supporting, removing, resetting, and disabling passwords, as well as unlocking accounts.
At first glance (alas), SSO seems the “perfect” solution that users and security administrators alike thirst for and seek. SSO allows a user to present a single set of log-on credentials, typically to an authentication server, which then transparently logs the user in to all other enterprise systems and applications for which that user is authorized. Of course, SSO does have some disadvantages, which include
![]() Woo-hoo!: After you’re authenticated, you have the keys to the kingdom. Read that as unrestricted access to all authorized resources! The security professional’s nightmare.
Woo-hoo!: After you’re authenticated, you have the keys to the kingdom. Read that as unrestricted access to all authorized resources! The security professional’s nightmare.
![]() Complexity: Implementing SSO can be difficult and time-consuming. You have to address interoperability issues between different systems and applications. But, hey — that’s why you get paid (or should get paid) the big bucks!
Complexity: Implementing SSO can be difficult and time-consuming. You have to address interoperability issues between different systems and applications. But, hey — that’s why you get paid (or should get paid) the big bucks!
SSO is commonly implemented by third-party ticket-based solutions, including
![]() Kerberos: Kerberos, commonly used in the Sun Network File System (NFS) and Windows 2000, 2003, and 2008, is perhaps the most popular ticket-based symmetric key authentication protocol in use today. Kerberos is named for the fierce, three-headed dog that guards the gates of Hades in Greek mythology. (Not to be confused with Ker-beer-os, the fuzzy, six-headed dog sitting at the bar that keeps looking better and better!) Researchers at the Massachusetts Institute of Technology (MIT, also known as Millionaires in Training) developed this open-systems protocol in the mid-1980s. The CISSP exam requires a general understanding of Kerberos operation. Unfortunately, Kerberos is a complex protocol that has many different implementations and no simple explanation. The following step-by-step discussion is a basic description of Kerberos operation:
Kerberos: Kerberos, commonly used in the Sun Network File System (NFS) and Windows 2000, 2003, and 2008, is perhaps the most popular ticket-based symmetric key authentication protocol in use today. Kerberos is named for the fierce, three-headed dog that guards the gates of Hades in Greek mythology. (Not to be confused with Ker-beer-os, the fuzzy, six-headed dog sitting at the bar that keeps looking better and better!) Researchers at the Massachusetts Institute of Technology (MIT, also known as Millionaires in Training) developed this open-systems protocol in the mid-1980s. The CISSP exam requires a general understanding of Kerberos operation. Unfortunately, Kerberos is a complex protocol that has many different implementations and no simple explanation. The following step-by-step discussion is a basic description of Kerberos operation:
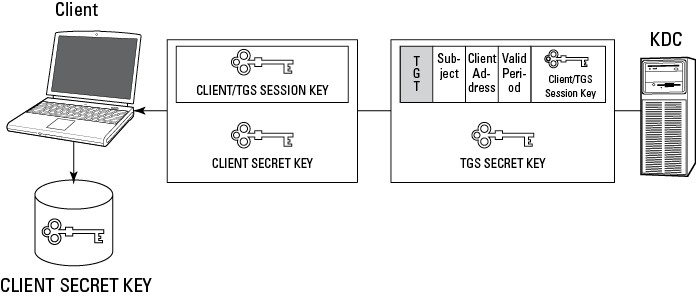
1. The client prompts the subject (such as a user) for identification and authentication (for example, username and password). Using the authentication information (password), the client temporarily generates and stores a secret key for the subject by using a one-way hash function and then sends only the subject’s identification (username) to the Key Distribution Center’s (KDC) Authentication Server (AS). The password/secret key isn’t sent to the KDC. See Figure 4-3.
 See Chapter 8 for a discussion of hash functions.
See Chapter 8 for a discussion of hash functions.
2. The AS on the KDC verifies that the subject (known as a principal) exists in the KDC database. The KDC Ticket Granting Service (TGS) then generates a Client/TGS Session Key encrypted with the subject’s secret key, which only the TGS and the client know. The TGS also generates a Ticket Granting Ticket (TGT), consisting of the subject’s identification, the client network address, the valid period of the ticket, and the Client/TGS Session Key. The TGS encrypts the TGT by using its secret key, which only the TGS knows, then sends the Client/TGS Session Key and TGT back to the client. See Figure 4-4.
Figure 4-3: Kerberos: Log-on initiation (Step 1).

Figure 4-4: Kerberos: Client/TGS Session Key and TGT generation (Step 2).
3. The client decrypts the Client/TGS Session Key — using the stored secret key that it generated by using the subject’s password — authenticates the subject (user), and then erases the stored secret key to avoid possible compromise. The client can’t decrypt the TGT, which the TGS encrypted by using the TGS secret key. See Figure 4-5.
4. When the subject requests access to a specific object (such as a server, also known as a principal), it sends the TGT, the object identifier (such as a server name), and an authenticator to the TGS on the KDC. (The authenticator is a separate message that contains the client ID and a timestamp, and uses the Client/TGS Session Key to encrypt itself.) See Figure 4-6.
5. The TGS on the KDC generates both a Client/Server Session Key (which it encrypts by using the Client/TGS Session Key) and a Service Ticket (which consists of the subject’s identification, the client network address, the valid period of the ticket, and the Client/Server Session Key). The TGS encrypts the Service Ticket by using the secret key of the requested object (server), which only the TGS and the object know. The TGS then sends the Client/Server Session Key and Service Ticket back to the client. See Figure 4-7.
Figure 4-5: Kerberos: Log-on completion (Step 3).

Figure 4-6: Kerberos: Requesting services (Step 4).

6. The client decrypts the Client/Server Session Key by using the Client/TGS Session Key. The client can’t decrypt the Service Ticket, which the TGS encrypted by using the secret key of the requested object. See Figure 4-8.
7. The client can then communicate directly with the requested object (server). The client sends the Service Ticket and an authenticator to the requested object (server). The client encrypts the authenticator (comprising the subject’s identification and a timestamp) by using the Client/Server Session Key that the TGS generated. The object (server) decrypts the Service Ticket by using its secret key. The Service Ticket contains the Client/Server Session Key, which allows the object (server) to then decrypt the authenticator. If the subject identification and timestamp are valid (according to the subject identification, client network address, and valid period specified in the Service Ticket), then communication between the client and server is established. The Client/Server Session Key is then used for secure communications between the subject and object. See Figure 4-9.
Figure 4-7: Kerberos: Client/Server Session Key and Service Ticket generation (Step 5).
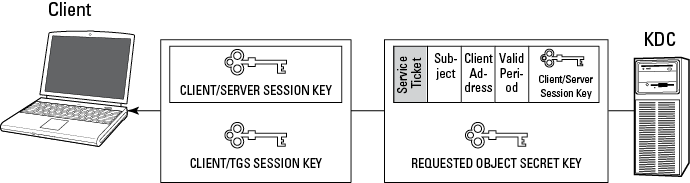
Figure 4-8: Kerberos: Decrypt Client/Server Session Key (Step 6).

Figure 4-9: Kerberos: Client/server communications (Step 7).

See Chapter 8 for more on symmetric key cryptography.
 In Kerberos, a session key is a dynamic key that is generated when needed, shared between two principals, then destroyed when it is no longer needed. A secret key is a static key that is used to encrypt a session key.
In Kerberos, a session key is a dynamic key that is generated when needed, shared between two principals, then destroyed when it is no longer needed. A secret key is a static key that is used to encrypt a session key.
![]() SESAME: The Secure European System and Applications in a Multi-vendor Environment (SESAME) project, developed by the European Computer Manufacturer’s Association (ECMA), is a ticket-based system, like Kerberos, with some additional functionality. It uses both symmetric and asymmetric cryptography to distribute secret keys and securely transmit data. By using public key cryptography, SESAME can securely communicate between different organizations or security domains. It incorporates a trusted authentication server at each host (known as a Privileged Attribute Server, or PAS), employs MD5 and CRC-32 one-way hash functions, and uses two separate certificates (known as a Privileged Attribute Certificates, or PACs) to provide authentication and define access privileges. However, SESAME also has some serious security flaws in its basic implementation, including these:
SESAME: The Secure European System and Applications in a Multi-vendor Environment (SESAME) project, developed by the European Computer Manufacturer’s Association (ECMA), is a ticket-based system, like Kerberos, with some additional functionality. It uses both symmetric and asymmetric cryptography to distribute secret keys and securely transmit data. By using public key cryptography, SESAME can securely communicate between different organizations or security domains. It incorporates a trusted authentication server at each host (known as a Privileged Attribute Server, or PAS), employs MD5 and CRC-32 one-way hash functions, and uses two separate certificates (known as a Privileged Attribute Certificates, or PACs) to provide authentication and define access privileges. However, SESAME also has some serious security flaws in its basic implementation, including these:
It uses an XOR function for encryption.
It performs authentication based on a small segment of the message rather than on the entire message.
Its key generation is not really very random.
It’s vulnerable to password-guessing attacks. (Want to bet that somebody thought “open” was a pretty clever password?)
 See Chapter 8 for more information on one-way hash functions, XOR functions, and key generation.
See Chapter 8 for more information on one-way hash functions, XOR functions, and key generation.
![]() KryptoKnight: Developed by IBM, KryptoKnight is another example of a ticket-based SSO authentication and key distribution system that establishes peer-to-peer relationships between the Key Distribution Center (KDC) and its principals. In addition to user authentication with SSO, KryptoKnight provides two-party authentication, key distribution, and data integrity services. KryptoKnight is an extremely compact and flexible protocol that can be easily exported to other systems and applications, and it can function at any layer of the OSI model. Unlike Kerberos, KryptoKnight doesn’t require clock synchronization (it uses nonces instead).
KryptoKnight: Developed by IBM, KryptoKnight is another example of a ticket-based SSO authentication and key distribution system that establishes peer-to-peer relationships between the Key Distribution Center (KDC) and its principals. In addition to user authentication with SSO, KryptoKnight provides two-party authentication, key distribution, and data integrity services. KryptoKnight is an extremely compact and flexible protocol that can be easily exported to other systems and applications, and it can function at any layer of the OSI model. Unlike Kerberos, KryptoKnight doesn’t require clock synchronization (it uses nonces instead).
A nonce is literally a number used once. Similar in concept to an initialization vector (see Chapter 8), a nonce is a randomly generated value (usually based on a timestamp) that can be used only once to authenticate a session.
See Chapter 5 for a complete discussion of the OSI model.
Methodologies and implementation
Access control methodologies are generally classified as either centralized or decentralized. Each of these classifications contains numerous protocols and models for implementation. For the CISSP exam, you should be able to identify the various protocols and models used in centralized and decentralized access control systems.
Centralized access controls
Centralized access control systems maintain user account information in a central location. Centralized access control systems allow organizations to implement a more consistent, comprehensive security policy, but they may not be practical in extremely large enterprises. For example, an enterprise that has several thousand employees working at major locations throughout the world may find it burdensome and bureaucratic to contact a main office in another region of the world for account provisioning or to change an individual’s access rights. In such cases, a decentralized access control system (described in the following section) may be more appropriate.
Examples of centralized access control systems and protocols commonly used for authentication of remote users include
![]() LDAP: Lightweight Directory Access Protocol (LDAP) is both an IP protocol and a data model. LDAP (pronounced EL-dap) is used to support authentication and directory functions for both people and resources. Several vendors have implemented LDAP, including
LDAP: Lightweight Directory Access Protocol (LDAP) is both an IP protocol and a data model. LDAP (pronounced EL-dap) is used to support authentication and directory functions for both people and resources. Several vendors have implemented LDAP, including
• Microsoft Active Directory
• CA eTrust Directory
• Apache Directory Server
• Novell eDirectory
• IBM SecureWay and Tivoli Directory Server
• Sun Directory Server
You can also find several open-source versions of LDAP available, including OpenLDAP and tinyldap.
![]() RAS: Remote Access Service (RAS) servers utilize the Point-to-Point Protocol (PPP) to encapsulate IP packets and establish dial-in connections over serial and ISDN links. PPP incorporates the following three authentication protocols:
RAS: Remote Access Service (RAS) servers utilize the Point-to-Point Protocol (PPP) to encapsulate IP packets and establish dial-in connections over serial and ISDN links. PPP incorporates the following three authentication protocols:
• PAP: The Password Authentication Protocol (PAP) uses a two-way handshake to authenticate a peer to a server when a link is initially established. PAP transmits passwords in clear text and provides no protection from replay attacks (in which part of a session is captured or recorded, then played back to the system) or brute force attacks.
 A two-way handshake refers to a communications session in which the communicating devices, for example a remote PC and a remote access server, establish a connection by sending an initial TCP SYN (Synchronize) packet to each other, each device receiving the other’s SYN packet before receiving an ACK (Acknowledgment) packet to indicate that its own SYN packet has reached the other device and been accepted.
A two-way handshake refers to a communications session in which the communicating devices, for example a remote PC and a remote access server, establish a connection by sending an initial TCP SYN (Synchronize) packet to each other, each device receiving the other’s SYN packet before receiving an ACK (Acknowledgment) packet to indicate that its own SYN packet has reached the other device and been accepted.
• CHAP: The Challenge Handshake Authentication Protocol (CHAP) uses a three-way handshake to authenticate both a peer and server when a link is initially established and, optionally, at regular intervals throughout the session. CHAP requires both the peer and server to be preconfigured with a shared secret that must be stored in plain text. The peer uses the secret to calculate the response to a server challenge by using an MD5 one-way hash function. MS-CHAP, a Microsoft enhancement to CHAP, allows the shared secret to be stored in an encrypted form.
• EAP: The Extensible Authentication Protocol (EAP) adds flexibility to PPP authentication by implementing various authentication mechanisms, including MD5-challenge, S/Key, generic token card, digital certificates, and so on. Many wireless networks implement EAP.
![]() RADIUS: The Remote Authentication Dial-In User Service (RADIUS) protocol is an open-source, client-server networking protocol — defined in more than 25 current IETF (Internet Engineering Task Force) RFCs (Request For Comments) — that provides authentication, authorization, and accountability (AAA) services. RADIUS is an Application Layer protocol that utilizes User Datagram Protocol (UDP) packets for transport. UDP is a connection-less protocol, which means it’s fast but not as reliable as other transport protocols.
RADIUS: The Remote Authentication Dial-In User Service (RADIUS) protocol is an open-source, client-server networking protocol — defined in more than 25 current IETF (Internet Engineering Task Force) RFCs (Request For Comments) — that provides authentication, authorization, and accountability (AAA) services. RADIUS is an Application Layer protocol that utilizes User Datagram Protocol (UDP) packets for transport. UDP is a connection-less protocol, which means it’s fast but not as reliable as other transport protocols.
 See Chapter 5 for a complete discussion of UDP.
See Chapter 5 for a complete discussion of UDP.
RADIUS is commonly implemented in Internet service provider (ISP) networks, as well as corporate remote access service (RAS) and virtual private networks (VPNs). RADIUS is also becoming increasingly popular in corporate wireless networks. A user provides username/password information to a RADIUS client by using PAP or CHAP. The RADIUS client encrypts the password and sends the username and encrypted password to the RADIUS server for authentication.
Note: Passwords exchanged between the RADIUS client and RADIUS server are encrypted, but passwords exchanged between the PC client and the RADIUS client are not necessarily encrypted — if using PAP authentication, for example. If the PC client happens to also be the RADIUS client, however, all password exchanges are encrypted, regardless of the authentication protocol used.
![]() Diameter: This next-generation RADIUS protocol was developed to overcome some of RADIUS’s deficiencies, but it has yet to overcome RADIUS’s popularity, so it’s not yet widely implemented.
Diameter: This next-generation RADIUS protocol was developed to overcome some of RADIUS’s deficiencies, but it has yet to overcome RADIUS’s popularity, so it’s not yet widely implemented.
Like RADIUS, Diameter provides AAA services and is an open protocol standard defined in 11 current RFCs.
Unlike RADIUS, Diameter utilizes Transmission Control Protocol (TCP) and Stream Control Transmission Protocol (SCTP) packets to provide a more reliable, connection-oriented transport mechanism. Also, Diameter uses Internet Protocol Security (IPSec) or Transport Layer Security (TLS) to provide network security or transport layer security (respectively) — rather than PAP or CHAP (used in RADIUS) — to provide a more secure connection.
 See Chapter 5 for a complete discussion of TCP and SCTP, IPSec and TLS, and the OSI model.
See Chapter 5 for a complete discussion of TCP and SCTP, IPSec and TLS, and the OSI model.
Diameter isn’t fully backward-compatible with RADIUS, but it does provide an upgrade path for RADIUS-based environments. Diameter isn’t an acronym, but a pun on the term RADIUS. (In geometry, the diameter of a circle is twice its radius.)
![]() TACACS: The Terminal Access Controller Access Control System (TACACS) is a remote authentication control protocol, originally developed for the MILNET (U.S. Military Network), which provides AAA services. The original TACACS protocol has been significantly enhanced, as XTACACS (no longer used) and TACACS+ (which is the most common implementation of TACACS). However, TACACS+ is a completely new protocol and therefore isn’t backward-compatible with either TACACS or XTACACS. TACACS+ is TCP based on (port 49) and supports practically any authentication mechanism (PAP, CHAP, MS-CHAP, EAP, token cards, Kerberos, and so on). The major advantages of TACACS+ are its wide support of various authentication mechanisms and granular control of authorization parameters. TACACS+ can also use dynamic passwords; TACACS uses static passwords only.
TACACS: The Terminal Access Controller Access Control System (TACACS) is a remote authentication control protocol, originally developed for the MILNET (U.S. Military Network), which provides AAA services. The original TACACS protocol has been significantly enhanced, as XTACACS (no longer used) and TACACS+ (which is the most common implementation of TACACS). However, TACACS+ is a completely new protocol and therefore isn’t backward-compatible with either TACACS or XTACACS. TACACS+ is TCP based on (port 49) and supports practically any authentication mechanism (PAP, CHAP, MS-CHAP, EAP, token cards, Kerberos, and so on). The major advantages of TACACS+ are its wide support of various authentication mechanisms and granular control of authorization parameters. TACACS+ can also use dynamic passwords; TACACS uses static passwords only.
Decentralized access controls
Decentralized access control systems keep user account information in separate locations, maintained by different administrators, throughout an organization or enterprise. This type of system makes sense in extremely large organizations or in situations where very granular control of complex user access rights and relationships is necessary. In such a system, administrators typically have a more thorough understanding of their users’ needs and can apply the appropriate permissions — say, in a research and development lab or a manufacturing facility. However, decentralized access control systems also have various potential disadvantages. For example, organizations may apply security policies inconsistently across various systems, resulting in the wrong level of access (too much or not enough) for particular users; and if you need to disable numerous accounts for an individual user, the process becomes much more labor-intensive and error-prone.
Examples of decentralized access control systems include
![]() Multiple domains and trusts: A domain is a collection of users, computers, and resources (such as printers) that have a common security policy and single administration. Smaller organizations may have a single domain defined, which is considered a centralized access control. Larger organizations or enterprises may establish multiple domains (or a Forest in Microsoft-speak) along organizational or geographical boundaries — such as separate Marketing, Accounting, Sales, and Research domains, or separate Chicago, Seattle, Paris, and Tokyo domains. One-way trust relationships or trust models facilitate communications between multiple domains. For example, if the Marketing domain explicitly trusts the Research domain, then all users in the Research domain can access resources in the Marketing domain. Unless the Research domain establishes a trust relationship in the reverse direction (Research trusts Marketing), users in the Marketing domain can’t access resources in the Research domain.
Multiple domains and trusts: A domain is a collection of users, computers, and resources (such as printers) that have a common security policy and single administration. Smaller organizations may have a single domain defined, which is considered a centralized access control. Larger organizations or enterprises may establish multiple domains (or a Forest in Microsoft-speak) along organizational or geographical boundaries — such as separate Marketing, Accounting, Sales, and Research domains, or separate Chicago, Seattle, Paris, and Tokyo domains. One-way trust relationships or trust models facilitate communications between multiple domains. For example, if the Marketing domain explicitly trusts the Research domain, then all users in the Research domain can access resources in the Marketing domain. Unless the Research domain establishes a trust relationship in the reverse direction (Research trusts Marketing), users in the Marketing domain can’t access resources in the Research domain.
![]() Databases: A database management system (DBMS) controls access to databases. A DBMS restricts access by different subjects (users) to various objects (such as data and operations) in a database. A view is a logical operation that can be used to restrict access to specific information in a database, hide attributes, and restrict the queries available to a user. Views are a type of constrained user interface that can restrict access to specific functions by not allowing a user to request those functions.
Databases: A database management system (DBMS) controls access to databases. A DBMS restricts access by different subjects (users) to various objects (such as data and operations) in a database. A view is a logical operation that can be used to restrict access to specific information in a database, hide attributes, and restrict the queries available to a user. Views are a type of constrained user interface that can restrict access to specific functions by not allowing a user to request those functions.
We cover additional database security methods in Chapter 7.
Data access controls
Data access controls are, well, the hard and crunchy middle. Probably not your favorite candy (freeze-dried Cadbury’s Creme Egg, anyone?), but effective information security requires defense in depth.
Data access controls protect systems and information by restricting access to system files and user data based on object identity. Data access controls also provide authorization and accountability, relying on system access controls to provide identification and authentication.
Access control techniques
Data access control techniques are generally categorized as either discretionary or mandatory. You, as a CISSP candidate, must fully understand the concept of discretionary and mandatory access controls and be able to describe specific access control methods that fall under each category.
Discretionary access control
A discretionary access control (DAC) is an access policy determined by the owner of a file (or other resource). The owner decides who’s allowed access to the file and what privileges they have.
Two important concepts in DAC are
![]() File and data ownership: Because the owner of the resource (including files, directories, data, system resources, and devices) determines the access policy, every object in a system must have an owner. Theoretically, an object without an owner is left unprotected. Normally, the owner of a resource is the person who created the resource (such as a file or directory), but in certain cases, you may need to explicitly identify the owner.
File and data ownership: Because the owner of the resource (including files, directories, data, system resources, and devices) determines the access policy, every object in a system must have an owner. Theoretically, an object without an owner is left unprotected. Normally, the owner of a resource is the person who created the resource (such as a file or directory), but in certain cases, you may need to explicitly identify the owner.
![]() Access rights and permissions: The controls that an owner can assign to individual users or groups for specific resources. Various systems (Windows-based, UNIX-based, and Novell-based) define different sets of permissions that are essentially variations or extensions of three basic types of access:
Access rights and permissions: The controls that an owner can assign to individual users or groups for specific resources. Various systems (Windows-based, UNIX-based, and Novell-based) define different sets of permissions that are essentially variations or extensions of three basic types of access:
• Read (R): The subject can read contents of a file or list contents of a directory.
• Write (W): The subject can change the contents of a file or directory (including add, rename, create, and delete).
• Execute (X): If the file is a program, the subject can run the program.
Access control lists (ACLs) provide a flexible method for applying discretionary access controls. An ACL lists the specific rights and permissions that are assigned to a subject for a given object.
Role-based access control is another method for implementing discretionary access controls. Role-based access control assigns group membership based on organizational or functional roles. Individuals may belong to one or many groups (acquiring cumulative permissions or limited to the most restrictive set of permissions for all assigned groups), and a group may contain only a single individual (corresponding to a specific organizational role assigned to one person). Access rights and permissions for objects are assigned to groups, rather than (or in addition to) individuals. This strategy greatly simplifies the management of access rights and permissions, particularly in organizations that have large functional groups or departments, and organizations that routinely rotate personnel through various positions or otherwise experience high turnover.
Major disadvantages of discretionary access control techniques such as ACLs or role-based access control include
![]() Lack of centralized administration
Lack of centralized administration
![]() Dependence on security-conscious resource owners
Dependence on security-conscious resource owners
![]() Many popular operating systems defaulting to full access for everyone if the owner doesn’t explicitly set permissions
Many popular operating systems defaulting to full access for everyone if the owner doesn’t explicitly set permissions
![]() Difficult, if not impossible, auditing because of the large volume of log entries that can be generated
Difficult, if not impossible, auditing because of the large volume of log entries that can be generated
Mandatory access control
A mandatory access control (MAC) is an access policy determined by the system, rather than by the owner. Organizations use MAC in multilevel systems that process highly sensitive data, such as classified government and military information. A multilevel system is a single computer system that handles multiple classification levels between subjects and objects. Two important concepts in MAC are
![]() Sensitivity labels: In a MAC-based system, all subjects and objects must have assigned labels. A subject’s sensitivity label specifies its level of trust. An object’s sensitivity label specifies the level of trust required for access. In order to access a given object, the subject must have a sensitivity level equal to or higher than the requested object. For example, a user (subject) with a Top Secret clearance (sensitivity label) is permitted to access a file (object) that has a Secret classification level (sensitivity label) because his or her clearance level exceeds the minimum required for access.
Sensitivity labels: In a MAC-based system, all subjects and objects must have assigned labels. A subject’s sensitivity label specifies its level of trust. An object’s sensitivity label specifies the level of trust required for access. In order to access a given object, the subject must have a sensitivity level equal to or higher than the requested object. For example, a user (subject) with a Top Secret clearance (sensitivity label) is permitted to access a file (object) that has a Secret classification level (sensitivity label) because his or her clearance level exceeds the minimum required for access.
 We discuss classification systems in Chapter 6.
We discuss classification systems in Chapter 6.
![]() Data import and export: Controlling the import of information from other systems and the export to other systems (including printers) is a critical function of MAC-based systems, which must ensure that the system properly maintains and implements sensitivity labels so that sensitive information is appropriately protected at all times.
Data import and export: Controlling the import of information from other systems and the export to other systems (including printers) is a critical function of MAC-based systems, which must ensure that the system properly maintains and implements sensitivity labels so that sensitive information is appropriately protected at all times.
Rule-based access control is one method of applying mandatory access control. Actually, all MAC-based systems implement a simple form of rule-based access control by matching an object’s sensitivity label and a subject’s sensitivity label to determine whether the system should grant or deny access. You can apply additional rules by using rule-based access control to further define specific conditions for access to a requested object.
Lattice-based access controls are another method of implementing mandatory access controls. A lattice model is a mathematical structure that defines greatest lower-bound and least upper-bound values for a pair of elements, such as a subject and an object. Organizations can use this model for complex access control decisions involving multiple objects and/or subjects. For example, given a set of files that have multiple classification levels, the lattice model determines the minimum clearance level that a user requires to access all the files.
Major disadvantages of mandatory access control techniques include
![]() Lack of flexibility
Lack of flexibility
![]() Difficulty in implementing and programming
Difficulty in implementing and programming
![]() User frustration
User frustration
Access control models
Applications use models to express access control requirements in a theoretical or mathematical framework that precisely describes or quantifies the application’s function. Common access control models include Bell-La Padula, Biba, Clark-Wilson, noninterference, access matrix, and information flow.
Bell-La Padula (Basic security theorem)
Published in 1973 and designed for the U.S. military to address storage and protection of classified information, the Bell-La Padula model was the first formal confidentiality model of a mandatory access control system. Bell-La Padula is a state machine model that addresses only the confidentiality of information. A state machine model defines and maintains a secure state during transitions between states. The basic premise of Bell-La Padula is that information can’t flow downward. Bell-La Padula defines the following two properties:
![]() simple security property (ss property): A subject can’t read information from an object that has a higher sensitivity label (no read up, or NRU).
simple security property (ss property): A subject can’t read information from an object that has a higher sensitivity label (no read up, or NRU).
![]() *-property (star property): A subject can’t write information to an object that has a lower sensitivity label (no write down, or NWD).
*-property (star property): A subject can’t write information to an object that has a lower sensitivity label (no write down, or NWD).
Biba
Published in 1977, the Biba integrity model (sometimes referred to as Bell-La Padula upside down) was the first formal integrity model. Biba is a lattice-based model that addresses the first goal of integrity — ensuring that unauthorized users or processes don’t make modifications to data. For more on lattice-based models, read the section “Mandatory access control,” earlier in this chapter. See Chapter 6 for a complete discussion of the three goals of integrity. Biba defines the following two properties:
![]() simple integrity property: A subject can’t read information from an object that has a lower integrity level (no read down).
simple integrity property: A subject can’t read information from an object that has a lower integrity level (no read down).
![]() *-integrity property (star integrity property): A subject can’t write information to an object that has a higher integrity level (no write up).
*-integrity property (star integrity property): A subject can’t write information to an object that has a higher integrity level (no write up).
Clark-Wilson
Published in 1987, the Clark-Wilson integrity model establishes a security framework for use in commercial activities, such as the banking industry. Using the Clark-Wilson model, data cannot be directly accessed by a user. Instead, it must be accessed through an application which controls the access. Clark-Wilson addresses all three goals of integrity (read more about these goals in Chapter 6) and identifies special requirements for inputting data based on the following items and procedures:
![]() Unconstrained data item (UDI): Data outside the control area, such as input data
Unconstrained data item (UDI): Data outside the control area, such as input data
![]() Constrained data item (CDI): Data inside the control area (integrity must be preserved)
Constrained data item (CDI): Data inside the control area (integrity must be preserved)
![]() Integrity verification procedures (IVP): Checks validity of CDIs
Integrity verification procedures (IVP): Checks validity of CDIs
![]() Transformation procedures (TP): Maintains integrity of CDIs
Transformation procedures (TP): Maintains integrity of CDIs
Noninterference model
A noninterference model ensures that objects and subjects don’t see the actions of different objects and subjects on the same system — and that those actions don’t interfere with them. For example, if a user with a higher level of access made a change to a file, a user with a lower level of access would not see those changes and would not be able to deduce any information from those changes.
Access matrix model
An access matrix model provides object access rights (read/write/execute, or R/W/X) to subjects in a DAC system. An access matrix consists of access control lists (ACLs) and capability lists. For more on DAC and ACLs, peruse the section “Discretionary access control,” earlier in this chapter.
Information flow model
An information flow model is a lattice-based model in which the system assigns objects a security class and value, and a security policy controls their direction of flow.

 A commonly cited example of an access control system that uses two-factor authentication is an automatic teller machine (ATM) card and a PIN. Purists might argue that the ATM card is actually a form of identification that you present to the ATM machine to establish your identity and that the PIN is the only authentication factor involved; thus an ATM doesn’t provide two-factor authentication. Save this debate for engaging conversation at a wild party. For the CISSP exam, this scenario is considered two-factor authentication.
A commonly cited example of an access control system that uses two-factor authentication is an automatic teller machine (ATM) card and a PIN. Purists might argue that the ATM card is actually a form of identification that you present to the ATM machine to establish your identity and that the PIN is the only authentication factor involved; thus an ATM doesn’t provide two-factor authentication. Save this debate for engaging conversation at a wild party. For the CISSP exam, this scenario is considered two-factor authentication.