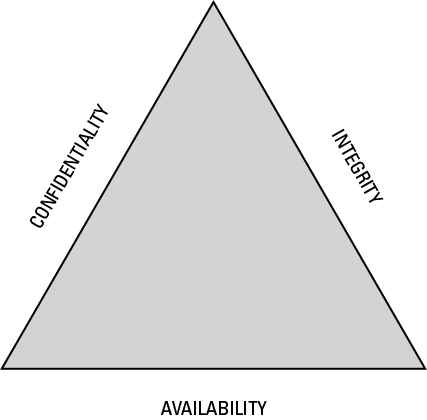
Figure 6-1: The C-I-A triad.
Information Security Governance Concepts and Principles
As a CISSP candidate, you must fully understand the three fundamental information security concepts that comprise the C-I-A triad and form the basis of information security (see Figure 6-1):
![]() Confidentiality
Confidentiality
![]() Integrity
Integrity
![]() Availability
Availability
As with any triangular shape, all three sides depend on each other (think of a three-sided pyramid or a three-legged stool) to form a stable structure. If one piece falls apart, the whole thing falls apart. All other domains within the CISSP Common Body of Knowledge (CBK) are based on these three important concepts.
Where security is concerned, you also need to understand the defense-in-depth concept, how to avoid single points of failure, and how to incorporate these concepts into security planning.
Confidentiality
Confidentiality prevents the unauthorized use or disclosure of information, ensuring that only those who are authorized to access information can do so. Privacy is a closely related concept that’s most often associated with personal data. Various U.S. and international laws exist to protect the privacy (confidentiality) of personal data.
Personal data most commonly refers to personally identifiable information (PII), which includes names, addresses, Social Security numbers, contact information, and financial or medical data. Personal data, in more comprehensive legal definitions (particularly in Europe), may also include race, marital status, sexual orientation or lifestyle, religious preference, political affiliations, and any number of other unique personal characteristics that may be collected or stored about an individual.
Read more about U.S. and international privacy laws in Chapter 12.
Integrity
Integrity safeguards the accuracy and completeness of information and processing methods. It ensures that
![]() Unauthorized users or processes don’t make modifications to data.
Unauthorized users or processes don’t make modifications to data.
![]() Authorized users or processes don’t make unauthorized modifications to data.
Authorized users or processes don’t make unauthorized modifications to data.
![]() Data is internally and externally consistent, meaning a given input produces an expected output.
Data is internally and externally consistent, meaning a given input produces an expected output.
Availability
Availability ensures that authorized users have reliable and timely access to information, and associated systems and assets, when needed. Availability is easily one of the most overlooked aspects of information security. In addition to Denial of Service attacks, other threats to availability include single points of failure, inadequate capacity (such as storage, bandwidth, and processing) planning, equipment malfunctions, fail-safe control mechanisms, and business interruptions or disasters.
Defense in depth
Defense in depth is an information security strategy based on multiple layers of defense. It’s often the (desired) result of a holistic approach to information security. Here’s a rundown of the integral parts of a defense-in-depth strategy:
![]() Security management principles: Include data classification, personnel security policies and practices, and information security awareness programs
Security management principles: Include data classification, personnel security policies and practices, and information security awareness programs
![]() Security technologies: Include firewalls, antivirus software, and intrusion detection systems
Security technologies: Include firewalls, antivirus software, and intrusion detection systems
![]() Vendor solutions: These include software solutions that are implemented in your technology infrastructure.
Vendor solutions: These include software solutions that are implemented in your technology infrastructure.
For example, to achieve defense in depth, an organization might deploy antivirus software from one vendor on servers and a completely different vendor’s antivirus software on user workstations.
Although using multiple solutions increases the management burden for these systems (different support issues and requirements, incompatible logs, and so on), it does produce a blended, dense, diverse defense — and typically helps to eliminate single points of failure. In short, a security posture that doesn’t rely on any single vendor or solution is more likely to be a successful one.


