Figure 7-4: An example of a phishing e-mail message.
System Attack Methods
Attackers develop new attack methods as fast as new products and technologies are introduced. It seems as though as soon as something new and cool comes out, only days — or even hours — later, you hear that someone has found a way to attack it.
Malicious code
As soon as data found a way to move easily from computer to computer, a creative individual with a bad attitude figured out that he could include some code that would play a not-so-practical joke, such as delete or alter files on someone else’s computer. And more recently, criminal organizations have figured out that they can steal valuable information — such as bank account numbers and credit card numbers, or the login credentials to high-value sites such as online banking — from peoples’ computers.
Unfortunately, several types of malicious code are out there; we define the most interesting ones here.
Viruses
The main purpose of a computer virus, a (usually) small program, is to replicate itself. Early computer viruses attached themselves to floppy disks’ boot sectors or to executables (such as .com or .exe files). Boot-sector viruses spread if a user booted the PC with an infected diskette. Viruses attached to executable files would spread when a user ran those executable files. Multi-partite viruses spread by using both the boot sector and executable files.
Today, viruses spread in many other ways, including macros found in documents, as well as in image files, JavaScript and ActiveX controls. We’ve also seen viruses spread through cross-site scripting vulnerabilities in websites and through instant messaging software. Virus writers — known as VXers — are always seeking new ways to propagate viruses and other malicious code.
If you find this topic fascinating (we sure do), you might consider picking up a copy of Computer Viruses For Dummies (John Wiley and Sons, Inc.; yes, one of us — Peter — wrote that book).
Worms
A worm is very similar to a virus: Both are designed to replicate quickly, but worms don’t attach themselves to programs the way viruses do. Instead, worms propagate by attacking known weaknesses on computer systems. On those systems where the worm finds a weakness, it can successfully break in and enter. Whatever the weakness happens to be, the result is the same: The worm can assume enough control of the system (or just of the application whose weakness it exploited) to use it as a base to launch attacks against more systems. And in the meantime, the worm may also have some destructive characteristics as well: It could change or delete data on the system.
Some of the most successful malicious code events (Conficker, Storm, NIMDA, and Code Red) were worms.

Rootkits
A rootkit is a malicious program that’s designed to hide itself on the target system in order to evade detection. The purpose of a rootkit varies according to its maker. A rootkit may perform any of the actions that most other types of malware are capable of, including destroying, altering, or stealing data; intercepting or altering data transmissions; or changing the behavior of the target system.
What makes a rootkit different from other types of malware is the fact that it uses some means to hide itself. Types of rootkits include
![]() Hardware: Present in the computer’s hardware. A hardware rootkit usually requires a compromise in the system manufacturer’s supply chain that permits the substitution of an approved component in a computer with one that includes rootkit code. In 2008, such an attack was successful: A brand of credit card swipe readers in Europe was infiltrated with chips that captured credit card numbers and sent them to overseas crime syndicates.
Hardware: Present in the computer’s hardware. A hardware rootkit usually requires a compromise in the system manufacturer’s supply chain that permits the substitution of an approved component in a computer with one that includes rootkit code. In 2008, such an attack was successful: A brand of credit card swipe readers in Europe was infiltrated with chips that captured credit card numbers and sent them to overseas crime syndicates.
![]() Firmware: Present in the target system’s firmware. Most newer computers have firmware that firmware updates can overwrite. Malware can insert itself into a system’s firmware, where it may then avoid detection: Most types of systems do nothing to check the integrity or contents of its firmware.
Firmware: Present in the target system’s firmware. Most newer computers have firmware that firmware updates can overwrite. Malware can insert itself into a system’s firmware, where it may then avoid detection: Most types of systems do nothing to check the integrity or contents of its firmware.
![]() Hypervisor: Operates as a virtual machine, running between the hardware and the operating system. The running operating system is a guest on the hypervisor’s environment. Although you can find several “friendly” (we mean commercial, such as VMware) hypervisor software products, one that’s malicious and even transparent (hidden from the user) may exist and be difficult to detect. A hypervisor-based rootkit can intercept all communications, as well as input-output with devices such as disk drives.
Hypervisor: Operates as a virtual machine, running between the hardware and the operating system. The running operating system is a guest on the hypervisor’s environment. Although you can find several “friendly” (we mean commercial, such as VMware) hypervisor software products, one that’s malicious and even transparent (hidden from the user) may exist and be difficult to detect. A hypervisor-based rootkit can intercept all communications, as well as input-output with devices such as disk drives.
![]() Kernel: Utilizes malicious code that’s been inserted into the operating system kernel. Done correctly, such code may be difficult or impossible to find.
Kernel: Utilizes malicious code that’s been inserted into the operating system kernel. Done correctly, such code may be difficult or impossible to find.
![]() Library: Inserts rootkit code into an operating system’s code library. Rather than alter the disk copy of a library file, a rootkit alters the memory image only, making its presence difficult to detect.
Library: Inserts rootkit code into an operating system’s code library. Rather than alter the disk copy of a library file, a rootkit alters the memory image only, making its presence difficult to detect.
Antivirus programs have a difficult time detecting rootkits (once installed), because the rootkits exist in a location that the antivirus program is unable to access or is not designed to access. For example, antivirus programs do not typically examine a system’s firmware (such as a ROM-BIOS) to see whether it’s been altered, and an operating system can’t detect whether it’s a virtual machine guest of a hypervisor.
Trojan horses
A Trojan horse, like its storybook namesake, is an object that claims to be one thing but turns out to be something far different (and not very nice).
Trojan horses generally don’t spread by replicating themselves, but they can be very damaging nonetheless. Trojan horses became prevalent with the rise of the Internet and e-mail. A typical Trojan horse arrives in the payload of an e-mail message, usually an attached executable file or a file with macros. The text portion of the e-mail message may read something like Viagra without a prescription, click here or See Britney Spears naked!! or some other enticing message designed to lure people into executing the Trojan horse and aiding in its sword-wielding propagation through cyberspace.
Another type of Trojan horse is a pop-up window that appears on the screen with information that prompts the user to act by clicking it. The window may pretend to be a Microsoft Windows error message saying that the victim’s computer has been infected by malware (in truth, it is about to be!) and that the user should “click here to install antivirus software.” This class of Trojan is known as scareware.
Hoaxes
While the popularity of e-mail increased, viruses rode the rails and propagated themselves via e-mail. Conscientious people everywhere, hearing about real viruses, would write up warning messages and send them to their friends and colleagues. But chip-on-their-shoulder virus writers decided to attack on another front: creating phony virus-warning messages in order to instill panic and occasionally to get naive users to do harmful things unwittingly. Such false warnings, like their offline predecessors, are called hoaxes.
Typically, a virus hoax arrives via e-mail, making a plea such as Please watch your inbox and DO NOT OPEN any message that has “Pictures for you” in the subject line. Whatever you do, do not open the message or your entire hard drive will be reformatted. I know — it happened to me two weeks ago, and I just got my computer back today.
Even hoaxes serve a purpose: They can account for millions of productivity hours lost in companies around the world. Sometimes, hoax messages clog e-mail systems, which is often one of the intentions of the perpetrator of the hoax.
Logic bombs
A logic bomb is a program designed to cause damage when some computer/network event has occurred. For instance, a logic bomb could destroy files when a user invokes a certain program, such as a text editor. Logic bombs don’t replicate themselves, but viruses or worms can leave them behind.
A common logic bomb is malicious code that activates on a certain date. Disgruntled programmers sometimes plant logic bombs that activate and destroy data long after those programmers leave their jobs. Nice parting gift, eh? This doozy alone justifies the use of code reviews and controls that prevent unauthorized changes from being inserted into software and systems.
Malicious applets
ActiveX and Java applets can carry malicious code and wreak havoc on users’ computers. Strictly speaking, attackers can write destructive ActiveX applets more easily than Java applets because the applets have unfettered access to the entire computer. Destructive Java applets are far more difficult to write because they must exploit some weakness in the Java sandbox in order to break out of it and do whatever damaging deed it was designed to do. For more about applets, read the earlier section “Adding applets to the mix.”
Trap doors
A trap door is a type of logic bomb that functions as part of a program. The trap door performs an undocumented function when certain conditions are met. Often these functions are designed to bypass security and other control mechanisms. One such trap door that we saw many years ago was planted in the /bin/login program on a UNIX system. When any ordinary user logged in to the system, the login program behaved normally. But when a special password was typed in (the publisher won’t let us tell you what it is), the login program would log the person in as root; further, the login program, which usually logs the session to an audit file, would conveniently forget to log the trap-door session. The login program was hard to detect because its date, size, and checksum were the same as the software maker’s original login program. It was a very effective — and terrible — trap door.
Hidden code
If an attacker can modify or replace programs on the target system, he or she may elect to install hidden code. Hidden code is a set of computer instructions hiding inside another program that carries out some usually-malicious act. An example of hidden code would be an application’s reporting program that also happens to erase certain entries from the audit trail.
An alteration of authorized code is an attack similar to a trap door, in which a program that has specified privileges (for instance, the system’s administrator account or an application’s master user account) is modified to carry out some illicit functions of the attacker’s choosing.
Injection attacks
An injection attack is one where the attacker is attempting to insert computer instructions into a computer program’s input field, in an attempt to trick the target computer into performing functions unintended by the program’s designer. These functions can range from displaying sensitive data to allowing the attacker to change or remove data from the system.
Examples of injection attacks include
![]() SQL Injection: Here, the attacker is injecting SQL statements in an attempt to trick the back-end database server to perform specific functions.
SQL Injection: Here, the attacker is injecting SQL statements in an attempt to trick the back-end database server to perform specific functions.
![]() Frame Injection (also known as cross-frame scripting, or XFS): Here, the attacker is attempting to load arbitrary code into a browser in order to steal data from other frames present in the browser session.
Frame Injection (also known as cross-frame scripting, or XFS): Here, the attacker is attempting to load arbitrary code into a browser in order to steal data from other frames present in the browser session.
Cross-site scripting attacks
A cross-site scripting attack, commonly known as XSS, is one where an attacker is able to inject client-side script into web pages viewed by other intended victims. This attack allows an attacker to bypass security mechanisms present in websites and web browsers.
The two principal types of XSS attacks are non-persistent and persistent attacks. In a typical non-persistent attack, the attacker must trick the victim into clicking a malicious URL that contains malicious script, which will be executed on the victim’s browser. Such a script could, for instance, steal the victim’s session cookies — which could then be used by the attacker to access the victim’s session.
In a persistent attack, the attacker arranges to store malicious code on a website (such as a message board, or comments in a blog). Then any users who click the malicious link will be executing malicious script on their systems.
Cross-site request forgery
In a cross-site request forgery (CSRF) attack, the attacker is attempting to trick a victim into clicking a link that will perform some action that the victim would not otherwise approve.
For example, an attacker creates a web page with images that users can click in order to view larger versions of the images. The attacker could place code on the image such as this example:
<img src=http://www.bank.com/transfer?from-account=mary&amt=100000&to-account=fred>
If victim Mary happens to be logged in to bank.com when she clicks the link, she will initiate a transfer of $100,000 to attacker Fred’s account.
A common method used to protect users from CSRF attacks is the inclusion of one-time-use hidden variables (known as a “nonce”) on important pages. The website keeps track of these hidden variables; any variation (or repeat) will indicate possible tampering.
Another method used to protect users against CSRF attacks is the inclusion of a secondary approval dialogue for any significant transaction. That way, if the attacker is able to sneak in a CSRF link that the victim clicks, the attack won’t be successful unless the victim also approves the transaction.
Escalation of privilege
One technique commonly used by attackers is known as escalation of privilege. Here an attacker accesses a system, and then uses any number of attack techniques (such as an injection attack) to increase the attacker’s privilege level from (say) that of an ordinary user to that of an administrator. The attacker’s logic (which is often correct) is that sensitive or valuable information may be more readily accessible if the attacker can somehow increase his or her privileges on the target system.
Denial of Service
The Denial of Service (DoS) attack is an interesting one because the attacker never does gain entry into the targeted computer system — then again, he or she isn’t trying to get in. Instead, the attacker is trying to make the target system unavailable for its users.
There are two types of DoS attacks. In the first, the attacker floods the victim’s system with such a large number of network packets that legitimate users of the system can’t reach it. The most successful DoS attacks not only slow down the system, but actually cause it to crash. Some methods of DoS attacks, such as the SYN attack, exhaust the system’s resources to the point that it can no longer function. True, SYN attacks are old hat, but they reveal a little bit about the creative thinking of the black hats out there.
The second type of DoS attack is one where the attacker creates a specific message that is designed to cause the target system to malfunction and stop running. In this attack, it’s usually unnecessary to send large quantities of messages — just a single message that is crafted just right.
A form of DoS attack, called Distributed Denial of Service (DDoS), occurs when an attacker uses hundreds, or even thousands or tens of thousands, of systems to attack a target simultaneously.
Dictionary attacks
The dictionary attack is a method used to crack computer account passwords by using common words found in a dictionary.
Most commonly, a dictionary-attack tool acquires a copy of the UNIX password or shadow file, or the Windows SAM file. The hacker then loads the file on his or her local system and runs a password-cracking program to attempt to discover account passwords by guessing dictionary words and combinations of dictionary words and numbers: for example, 4food.
This type of attack has prompted companies to require their employees and customers to pick good passwords — meaning passwords that consist of random letters interspersed with numbers and special characters: !@#)(*&^%;[]{}:’”><. So, rather than an easily guessed password such as Alexis, a user would use a more difficult-to-guess password such as Al3x1s*. Such a good password is practically impossible to break with a dictionary attack.
(See also the section, “Brute force,” later in this chapter.)
Spoofing
In a spoofing attack, the attacker changes the network identity of a computer or program some way so as to trick the targeted system into granting access to the attacker. For instance, a targeted computer may accept Telnet requests only from systems that have specific IP addresses. Knowing this, the attacker can send spoofed TCP/IP packets to the system in an attempt to fool the target system and break in.
Spam
Spam is the scourge of e-mail around the world. At times, it may make up as much as 95 percent of all e-mail on the Internet.
We don’t feel that it’s especially useful to discuss the methods that spammers use to build their mailing lists in any great detail. Spammers harvest e-mail addresses from newsgroups, and social networking sites; unscrupulous website operators sell e-mail addresses to spammers, and malware harvests e-mail addresses from hacked e-mail accounts. Sometimes spammers just get lucky and guess e-mail addresses, and some of the vile product gets through.
The effects of spam
The important thing to discuss about spam is prevention. You want to block spam for several reasons:
![]() E-mail volume: Spam clogs e-mail servers, reducing performance and raising costs by requiring larger hard drives to store all that e-mail. The volume of spam also consumes a lot of network bandwidth, stealing resources away from legitimate activities — such as social networking, or checking your stock prices or sports team scores.
E-mail volume: Spam clogs e-mail servers, reducing performance and raising costs by requiring larger hard drives to store all that e-mail. The volume of spam also consumes a lot of network bandwidth, stealing resources away from legitimate activities — such as social networking, or checking your stock prices or sports team scores.
![]() Distraction and clutter: Because spam can account for such a large volume of e-mail, legitimate e-mails may get deleted in attempts to delete all the spam. Plus, it just takes a lot of time to click the Delete button over and over.
Distraction and clutter: Because spam can account for such a large volume of e-mail, legitimate e-mails may get deleted in attempts to delete all the spam. Plus, it just takes a lot of time to click the Delete button over and over.
![]() Malware: A large proportion of spam contains malware, or links to websites that contain malware, designed to silently poison unprotected computers. Blocking spam reduces your risk of malware infections: If the tempting e-mails aren’t in your inbox, you don’t have to fight off the urge to click those tantalizing ads about low-cost prescription drugs, sweepstakes winnings, or magical ways to change the size and shape of your body.
Malware: A large proportion of spam contains malware, or links to websites that contain malware, designed to silently poison unprotected computers. Blocking spam reduces your risk of malware infections: If the tempting e-mails aren’t in your inbox, you don’t have to fight off the urge to click those tantalizing ads about low-cost prescription drugs, sweepstakes winnings, or magical ways to change the size and shape of your body.
Preventing spam
Blocking spam is very much a normal operational activity, like antivirus measures and backups are. You can use several types of anti-spam solutions and find many options available of each type, which translates into low-cost solutions that you can use fairly easily.
The types of spam-blocking solutions include these:
![]() Centralized appliance: The dominant method for blocking spam. Easy-to-administer appliances connect to the network, often ahead of the e-mail server, relieving the e-mail server of ever having to store spam e-mail messages in the first place. Most web-based spam-blocking appliances are managed with a web-based interface. Some also filter out malware. Many multifunction security appliances can also perform other functions such as website filtering, intrusion detection, and data leakage prevention.
Centralized appliance: The dominant method for blocking spam. Easy-to-administer appliances connect to the network, often ahead of the e-mail server, relieving the e-mail server of ever having to store spam e-mail messages in the first place. Most web-based spam-blocking appliances are managed with a web-based interface. Some also filter out malware. Many multifunction security appliances can also perform other functions such as website filtering, intrusion detection, and data leakage prevention.
![]() Spam-blocking service: A third-party service receives an organization’s e-mail, blocks out the spam, and forwards only the legitimate e-mail to the organization’s e-mail server. The organization doesn’t have to install anything. The advantage of a spam-blocking service is the complete absence of spam consuming any network resources on the corporate network. Like spam-blocking appliances, spam-blocking services are usually administered through a simple web-based interface.
Spam-blocking service: A third-party service receives an organization’s e-mail, blocks out the spam, and forwards only the legitimate e-mail to the organization’s e-mail server. The organization doesn’t have to install anything. The advantage of a spam-blocking service is the complete absence of spam consuming any network resources on the corporate network. Like spam-blocking appliances, spam-blocking services are usually administered through a simple web-based interface.
![]() Spam-blocking software: Formerly a favored type of solution but now declining in popularity. This type of solution comes in the form of anti-spam software that runs on the e-mail server, plucking out spam messages when they enter or after they’re stored.
Spam-blocking software: Formerly a favored type of solution but now declining in popularity. This type of solution comes in the form of anti-spam software that runs on the e-mail server, plucking out spam messages when they enter or after they’re stored.
![]() Workstation-based software: Formerly popular but almost never used anymore.
Workstation-based software: Formerly popular but almost never used anymore.
Social engineering
Social engineering is an attack against people as a way of getting access to targeted systems. The classic case of social engineering occurs when a hacker makes a number of telephone calls to various people in an organization and gets a tidbit of information from each one. For instance, he or she can get modem access numbers from one person, IP addresses and system names from another, a user ID from another, and a password reset from a help-desk employee. And voilà, the attacker puts these pieces together to log in to the company’s system by using its established remote-access facilities.
Another common social engineering ploy is one in which the attacker, posing as the system or security administrator, tells people to change their passwords to a specified value. The attacker then tries to log in to the system by using that account to see whether any suckers did what he or she asked them to.
Even social engineering has gone high-tech: A good deal of the spam that floods the Internet is in the form of phishing and pharming attacks, described here:
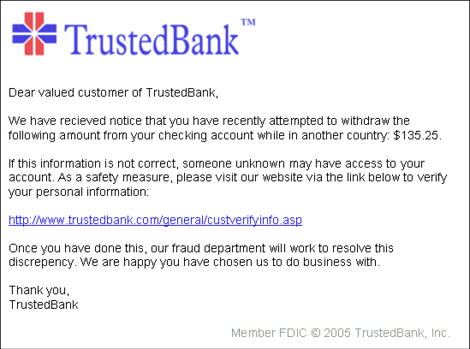
![]() Phishing: A perpetrator creates genuine-looking e-mail messages that appear to have originated from real, high-value sites, such as online banking. The purpose of the e-mail is to trick the recipient into clicking the hyperlink that takes the user to a realistic-looking login page. When the user inputs his or her credentials, the perpetrator records them and then later uses them to attempt to steal funds from the victim. A typical phishing e-mail is shown in Figure 7-4.
Phishing: A perpetrator creates genuine-looking e-mail messages that appear to have originated from real, high-value sites, such as online banking. The purpose of the e-mail is to trick the recipient into clicking the hyperlink that takes the user to a realistic-looking login page. When the user inputs his or her credentials, the perpetrator records them and then later uses them to attempt to steal funds from the victim. A typical phishing e-mail is shown in Figure 7-4.
![]() Pharming: The end result of pharming is very similar to phishing: A user goes to an imposter website whose owner wants to steal users’ login credentials. The method of attack, however, is quite different. In a pharming attack, the attacker targets the user’s DNS environment so that it returns incorrect values, leading victims to imposter sites. For example, if an attacker can successfully attack an organization’s local DNS server, it can redirect all DNS queries for MyBank.com from its real site to a fake site that’s run by the attacker.
Pharming: The end result of pharming is very similar to phishing: A user goes to an imposter website whose owner wants to steal users’ login credentials. The method of attack, however, is quite different. In a pharming attack, the attacker targets the user’s DNS environment so that it returns incorrect values, leading victims to imposter sites. For example, if an attacker can successfully attack an organization’s local DNS server, it can redirect all DNS queries for MyBank.com from its real site to a fake site that’s run by the attacker.
![]() Spear phishing: A type of phishing in which the attacker targets certain users or groups of users. For example, if phishers can determine which online financial institutions their potential victims use, those phishers may be able to produce more effective fraud schemes.
Spear phishing: A type of phishing in which the attacker targets certain users or groups of users. For example, if phishers can determine which online financial institutions their potential victims use, those phishers may be able to produce more effective fraud schemes.
![]() Whaling: A type of phishing attack that targets senior executives in one or more organizations. For example, officers in an organization can be targeted through a message claiming to be related to a lawsuit or subpoena against the organization.
Whaling: A type of phishing attack that targets senior executives in one or more organizations. For example, officers in an organization can be targeted through a message claiming to be related to a lawsuit or subpoena against the organization.
Pseudo flaw
A pseudo flaw attack is a special form of social engineering in which an attacker, posing as a system or security administrator or vendor, tells unsuspecting users that a security flaw has been discovered on their system and that they should install a certain patch, which is usually a Trojan horse.
Figure 7-5 shows a pop-up window from a scareware program that pretends to be anti-spyware when it is actually malware.
Figure 7-5: An example of scareware.

Remote maintenance
Organizations need to be especially wary of vendors who need to connect via modem, VPN, or remote desktop connection to their systems or networks in order to troubleshoot a problem or perform maintenance. If the vendor’s employee is dishonest, he or she may perform any number of acts that would constitute abuse, at best — hacking, at worst. This person may steal information or services, insert trap doors or logic bombs, or use his or her customer’s system to attack other systems in the enterprise or on the Internet.
In all fairness, most vendors have honest intentions when they legitimately need to connect to a customer’s computer in order to fix a problem. But a few dishonest employees in these vendor organizations have made this an activity that you should think twice about. Vendors should be able to connect to your systems only at your request, and only for a defined period of time. The privileges that you give to the vendor should be the minimum needed for its employee to quickly get in, fix the problem, and get out.
Maintenance hooks
Legitimate remote maintenance is one thing, but it’s quite another for a software developer to bury illicit hooks in software code that permit a program to expose features, functions, or data inappropriately. For instance, if the user enters certain values in data fields, a program could drop into Maintenance mode or Debug mode, thereby exposing internal system information.
Sniffing and eavesdropping
An intruder (or employee) may devise some means for listening to traffic on the organization’s internal network by using a sniffer program. Sniffer programs can listen for and capture login sessions, recording user IDs and passwords. Systems that encrypt the login password on the wire aren’t necessarily better off in the case of sniffers. Hacking tools can capture the encrypted password and later perform a dictionary or brute force attack against it to discover the password. This process can, however, take months or even years, so encrypted passwords over the network are substantially safer than cleartext password transmission.
Eavesdropping isn’t limited to the high-tech approach. One can listen in on conversations in airports, restaurants, and other public places. An intruder can install listening devices in conference rooms, on telephone lines, or in gifts given to the intended victim. (“Here, have this large, attractive lapel pin.”)
Traffic analysis and inference
An attacker can analyze network traffic patterns and other types of transmissions in order to make inferences about something that he or she wants to know more about. In this type of attack, the attacker doesn’t have access to the contents of the transmissions — only their patterns. For instance, the attacker could be in a position to know the workload on a network and thus infer that the network’s high utilization from 10:00 p.m. to 1:00 a.m. is the organization performing backups over the network. The attacker can use this information to his or her advantage by attempting to sabotage systems shortly before 10:00 p.m. in order to prevent a backup from occurring. Usually, traffic analysis and inference isn’t an end to itself, but part of a bigger plan.
Brute force
As attacks go, brute force is the most time-consuming; attackers use it as a last resort when more devious or clever methods fail. Whatever the target, the perpetrator of a brute-force attack repeatedly hits his or her target, making small changes each time, hoping that he or she can eventually get in.
You most often see brute-force attacks in the form of an attacker trying to log in with some user ID and trying every possible password until he or she finds the right one. Most newer computer systems are designed to repel this sort of attack by locking out accounts that have had too many unsuccessful login attempts. An honest user sees this lockout mechanism sometimes when he or she tries to log in to his or her account at work, only to be locked out — and then he or she remembers changing that password the day before. (D’oh!)

 Strictly speaking, a virus spreads by making (usually) identical copies of itself on files that are likely to be transported to other computers. Other types of malicious code, such as worms and Trojan horses, are often mistakenly called viruses.
Strictly speaking, a virus spreads by making (usually) identical copies of itself on files that are likely to be transported to other computers. Other types of malicious code, such as worms and Trojan horses, are often mistakenly called viruses.

