3
Internet of Things
3.1 Overview
The Internet of Things (IoT) environment is as versatile as the word ‘things’ just sounds. It basically refers to a vast set of all kinds of equipment connected to the Internet, including surveillance cameras, refrigerators, printers, self‐driving cars and telematics boxes which are able to communicate and perform actions. Remarkably, IoT also refers to yet‐to‐be‐seen devices that may be so innovative that we might not have a clue about their future form. The key idea of IoT is the facilitation of useful functions via the ‘always‐on’ connectivity everywhere and at any time, providing fluent and seamless user experiences, and making our lives easier in the transition from the information society towards the truly connected society.
This chapter discusses the principles of IoT by interpreting its typical definitions and analysing the suitability of it in different environments. The overall development of IoT is explained by investigating the evolution of M2M solutions and mobile connectivity, the Connected Living concept, and other relevant industry forum, alliance and standardization initiations. This chapter also presents technical descriptions of current key case examples of IoT in environments such as telemetry, automotive and e‐health. The aim is to identify trends and development of IoT for novelty and future solutions such as wearable devices, household appliances, industry solutions, robotics, self‐driving cars to understand their role and how they relate to IoT.
To complement the overall picture, this chapter also discusses the contributing role and technologies of utilities, i.e., the ways they are relying on wireless technologies and their importance in the electric domain, including generation, transmission, distribution and area networks, mobility and smart grid applications.
3.2 Foundation
3.2.1 Definitions
IoT is a term that has been publicly visible for many years. Even before the appearance of the term ‘IoT’, it existed as an idea for a very long time, as can be interpreted from early activities involved with connected devices in the 1G and 2G mobile communications environment at the beginning of the 1990s – which represented an era well before the adaptation of the graphical World Wide Web (WWW). With only a limited and text‐based Internet, the (highly unusually utilized external) data connectivity of analogue systems like Nordic Mobile Telephony (NMT) and SMS of GSM networks were utilized to test ideas that were in fact quite similar to current IoT thoughts. The early mobile devices were used as remote management tools for a variety of inventions, e.g., providing automatic slow‐scanning surveillance video contents that could be triggered via sensors [15], opening garage doors, and even warming up saunas. As important facilitators, the public Internet, the WWW with Graphical User Interface (GUI) and more advanced mobile communications services, finally provided a suitable user‐friendly base for all kinds of communications wirelessly and via wired connections.
In general, the term ‘IoT’ itself indicates the blurriness of the environment, generalizing the presence and utilization of services and connected devices under the highly interpretable word ‘things’. A concrete example of this environment is the M2M communications which does not require the intervention of persons, and can be interpreted as belonging to part of, or in many cases, be even a synonym for IoT. In fact, IoT and M2M are often understood to refer to the same environment although M2M is a subset of IoT. This is due to the nature of IoT which, in addition to the pure machines communicating with each other, can be understood to also include communications between machines and human‐operated devices [27].
The GlobalPlatform (GP) defines IoT as uniquely identifiable objects and their virtual representations in an Internet‐like structure [1,2]. IoT can thus refer to the overall trend of increasing amounts of devices that are connected to the Internet, by all means, and especially in a wireless manner. To mention some examples, there is a clear tendency to include IoT functionality to automotive, medical, home and utility devices by enhancing the User Experience (UX) and by automatizing functionalities.
Investigating further the definitions of the GlobalPlatform, IoT devices need to perform measurements of physical properties and gather information via sensors, and to influence or modify their environment by, e.g., performing measurements via actuators. In addition, IoT may include devices capable of processing the data obtained by sensors, perform tasks like correlation of measurement data and analysis of the information, possibly to be delivered further to some other entity for post‐processing. In practice, a single device may be able to perform one or more of the above‐mentioned tasks. Furthermore, IoT devices need to be able to communicate with the external world, either via local wireless connectivity such as proximity or vicinity technologies (NFC, RFID, Bluetooth LE, etc.), Wi‐Fi, wider range systems such as cellular networks or fixed networks such as Asymmetric Digital Subscriber Line (ADSL). The connectivity may be done via any known standardized or proprietary technology, and via licensed or unlicensed RF bands, as long as the IoT devices are able to deliver their messages to the counterparty, which may be system or other device performing functions or relaying the messages. Figure 3.1 summaries the principle.
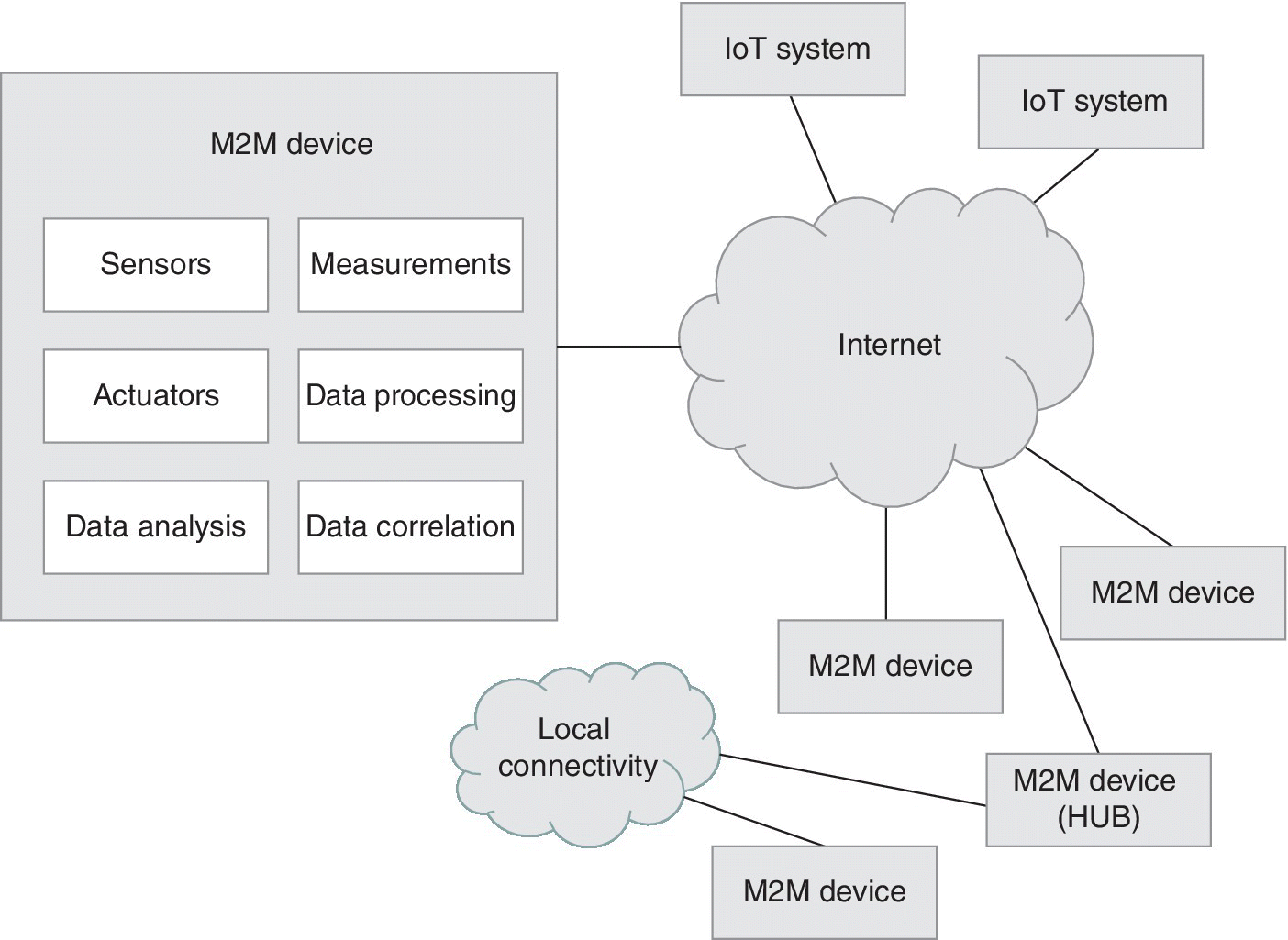
Figure 3.1 IoT consists of devices that are able to perform functions such as measurements and data processing, as stated in Refs. [1,2]. The connectivity can be based on all known data transfer techniques, including mobile communications networks, local wireless and wired networks, and even direct connectivity. IoT may have communications with other consumer devices, and furthermore, part of the devices can act as hubs to connect the local equipment to the Internet
From a multitude of IoT definitions, Ref. [6] summarizes it in the following sentence: The Internet of Things (IoT) is a computing concept that describes a future where every‐day physical objects will be connected to the Internet and be able to identify themselves to other devices. The term is closely identified with RFID as the method of communication, although it also may include other sensor technologies, wireless technologies or QR codes.
Furthermore, Ref. [6] emphasizes the importance of IoT as an object that can represent itself digitally and become something greater than the object itself. In other words, the object will be connected to surrounding objects and database data to be part of a whole environment. This is fascinating because as soon as a multitude of objects are acting in unison, they can be considered to have ambient intelligence.
The RFID has been mentioned in various early sources related to IoT. Nevertheless, as the communications is being adapted into the modern IoT environment, the connectivity may actually be any of the known methods, including fixed and wireless technologies. In the most typical cases, wireless radio access technology is used from which the cellular connectivity provides the widest service areas while Wi‐Fi is typical for the local solutions. Many other short‐range technologies can be used such as low‐energy Bluetooth and light‐based communications (Li‐Fi) that function within limited coverage ranges.
3.2.2 Security Considerations of IoT
IoT provides a vast amount of new possibilities for managing, coordinating, automatizing and benefiting in general from M2M communications without human intervention, as well as by taking human interactions into account when needed. At the same time, new types of equipment will be introduced into the market as a base for innovative services. In addition to such a huge amount of new opportunities, this also opens known and totally new security threats that may compromise the identity of users and confidentiality of information, which in turn may jeopardize the safety of, e.g., economic funds, and in the worst case, threaten even the personal well‐being of persons as in compromised medical or traffic control applications. One of the current, highly concrete demonstrations of such life‐threatening risks is related to the possibility of taking over remotely the control of connected, self‐driven vehicles [7,8].
To ensure protection against the known and future security breaches, IoT needs to take into account the underlying technical mechanisms. As presented by the GlobalPlatform, some of the items that contribute to security are the following [2]:
- The Secure Element (SE) has the form of the SIM/UICC, embedded SIM or external card and is protected against physical and logical security attacks. It thus provides a suitable means for hosting multiple stakeholders’ applications.
- The Security Domain (SD) serves for storing cryptographic content for each stakeholder on the SE. It also provides a means for secure communications between the content and external entity, and for managing the content.
- The Trusted Service Manager (TSM) is a service delivery broker which is able to establish business agreements and technical relationships between stakeholders.
- The Controlling Authority (CA) manages the confidential post‐issuance of new stakeholders onto the SE.
- The Trusted Execution Environment (TEE) is a secure and trusted area on the mobile equipment HW, which is used for safe and protected storing and processing of sensitive data by isolating it from the ‘normal’ world.
These technologies together with other relevant bases for IoT are described and analysed throughout this book.
3.2.3 The Role of IoT
The role of both fixed and wireless telecommunications has increased and provides a platform for essential functionalities in daily life for personal and business environments, as well as government services. The amount of current information flow via data networks is breathtaking. The utilization of the Internet is growing steadily as can be seen in Figure 3.2[16].
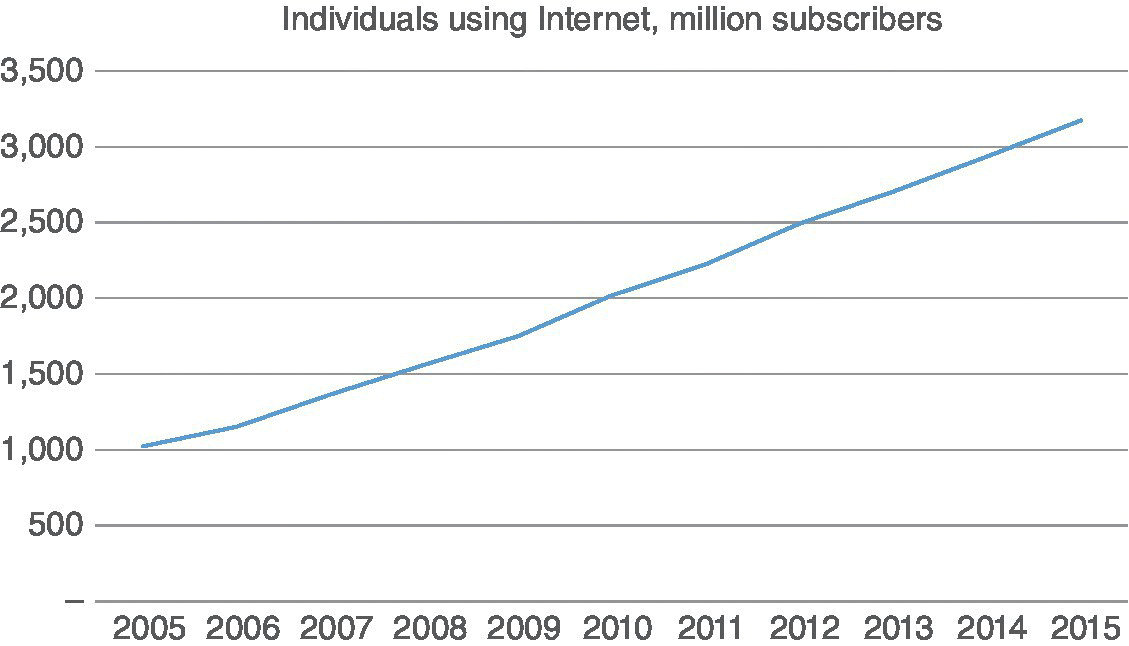
Figure 3.2 Individuals using the Internet [16]
In fact, along with the enhancements of IoT, the information society – with ever evolving technological solutions for more efficient communications – is converting the world to a vast integrated information system [3]. Looking at this groundbreaking evolution, the old saying about the telecommunications network being the biggest machine in the world may indeed need to be reviewed because the Internet now serves as an umbrella for such a great amount of services, telecommunications being in fact only one of its parts in a set of all kinds of subsystems and devices. Thus, it is justified to state that the Internet is nowadays the world’s biggest machine.
Human‐based communications still represents a high share of the total information flow, but the fully automatized M2M communications is taking over with giant leaps. IoT with sensors and actuators embedded in physical objects are preparing us for a totally new era of a socio‐techno‐economical ecosystem where old business rules and earning models are refreshed on a daily basis. There is plenty of room for enhancing current services via M2M devices as well as by taking totally new innovations into use, via wired and wireless, current and future networks that rely typically on IP connecting the uncountable machines to the Internet.
Along with the increased amount of M2M equipment, the level of data transferred increases, which needs special attention so that MNOs can deploy new networks and enhance the capacity of the current ones to maintain or enhance the quality level required by solutions from background data exchange up to extremely delay‐sensitive real‐time solutions. The estimation for the growth of M2M and the resulting increase for data utilization is an extremely hard task to perform, but the following summarizes some of the publicly available forecasts. Ref. [4] has noted that according to industry experts, IoT was expected to include more than 15 billion connected devices by 2015 while the estimate for 2020 is 50 billion. This reference mentions that the major part of the devices would not be conventional computers or smartphones, but small, economical, interconnected and partially autonomously communicating devices like home appliances, security systems, smart thermostats, smart meters, portable medical devices, health and fitness trackers and smart watches. Ref. 4 foresees 26 billion installed IoT units by 2020 without counting personal computers, tablets or smartphones, while ABI Research estimates that the total number of connected devices will reach at least 40 billion IoT units by 2020 [19].
In such a dynamically developing environment, it is most challenging to forecast precise values for the number of IoT devices – and after all, it might not be even necessary or possible to form such statistics as the devices are based on such a variety of systems and communications technologies. Nevertheless, the overall messages from all these efforts indicate that the IoT market will be of extremely high relevance and surpass even today’s smartphone sales. It can thus be expected that IoT has big direct and indirect impacts on the telecommunications development as it creates totally new business opportunities and impacts notably on our lifestyle. It could be argued that after the information society, the next big step in human life would, in fact, be the new connected society era.
There will be more and more enhanced and novelty equipment types in the market, like integrated miniature telemetry devices and cameras with short‐range wireless communications that are embedded into medical pills. Other examples could be an environment where M2M devices observe processes like animal populations in isolated remote areas, and communicating with food and medical supply chains to provide automatic refills when required. In an urban environment, there are unlimited possibilities for optimizing announcement types via real‐time knowledge of the preferences of people present in the area, e.g., by displaying the most relevant messages based on user profiles. The question in this highly developing environment might be whether it will happen too fast. Imagine an example of such personalized announcements in a public environment, the systems knowing exactly the preferences of the users and displaying related information on screens on the streets as the individuals walk by.
The IoT era is thus most fascinating as it counts for more possibilities for data mining than ever before, and, at the same time, there will be need to maintain at least some level of personal privacy, or provide users with the means to opt out from the personalized messaging. The basic problems are who has the right to collect and store information of individuals, who has right to protect the data and, in general, who may protect who and with what cost of privacy. The task is more than challenging in the modern environment with increasing levels of cyber‐attacks, which needs to be addressed by increasing cyber surveillance, the entities being not only individuals but also governments and a whole ecosystem of banks, production chains, armed forces, educational institutes, etc. IoT can thus be also interpreted as an elemental component in the cyber world.
3.2.4 IoT Environment
Being used so widely all around the globe, one may wonder what the origin of the term ‘Internet of Things’ is. Various sources, like Ref. [5], summarize the key steps towards IoT and discuss who should be credited for ‘inventing’ IoT. In fact, as for the terminology, IoT definitely sounds sufficiently general to express the big impact it is causing on society by blurring the technicalities in such a compact yet intuitive way. Nevertheless, the meaning of IoT – regardless of the popularizing of the term as such – is after all a result of a long chain of innovations related to the theories and technologies such as electricity, communication methods, transistors, microprocessors, modulation and coding schemes, communications devices, protocol stacks, signalling methods, computers, programming, audio and video technologies, wired and wireless systems, measurement and antenna technologies, and of course, the Internet as it has emerged from early ARPANET and TCP/IP. These areas represent only a tiny snapshot of the building blocks that have paved the way to automatized functionality of connected devices in the form of IoT, M2M communications, Internet of Everything, Connected Society, Intelligent Home or any other term we want to express the areas of IoT.
It can be argued that the environment called ‘IoT’ would not exist without all the efforts made by an impossible‐to‐estimate number of inventors, technicians, commercial people and other contributors to the standardization, development, deployment and marketing of communications technologies. As for the term ‘IoT’ itself, according to several public sources like [5,9], it was utilized in this form by sensor researcher Kevin Ashton in 1999 as part of his presentation about early predictions of the development of the Internet. The term has been ever since widely adopted and it seems to be established as a part of the countless abbreviations of the telecommunications technologies. More background information for the development of IoT terminology can be found, e.g., in Ref. [5]
Based on the publicly available information, the very early enabler for the IoT type of environment has been the RFID, which provides the possibility to read basic information from a short distance. Some early examples of the RFID were related to inventory management by reading wirelessly the pre‐embedded tags from items or to a supermarket where an RFID reader scans the customer purchases wirelessly in an instant fashion. This automatized identification and tracking of objects containing an RFID tag represents one‐way wireless communications between passive objects and could in fact be considered as one of the very initial technology steps leading into the fuller scale IoT.
Nevertheless, the relatively simple data transfer between object and RFID reader represents a rather limited methodology and does not exactly comply completely with the modern IoT environment. Instead of merely passive objects, the current IoT can be understood as a set of both passive and active physical objects that are part of the information network in a fluent and seamless way, by participating in the functioning of whole systems and contributing to the actions of various areas of everyday life such as learning, healthcare, telematics and businesses. In fact, IoT is paving the way to a completely novel society which integrates the ‘traditional’ physical word, the digital world, and the virtual cyber world, as depicted in Figure 3.3[5].
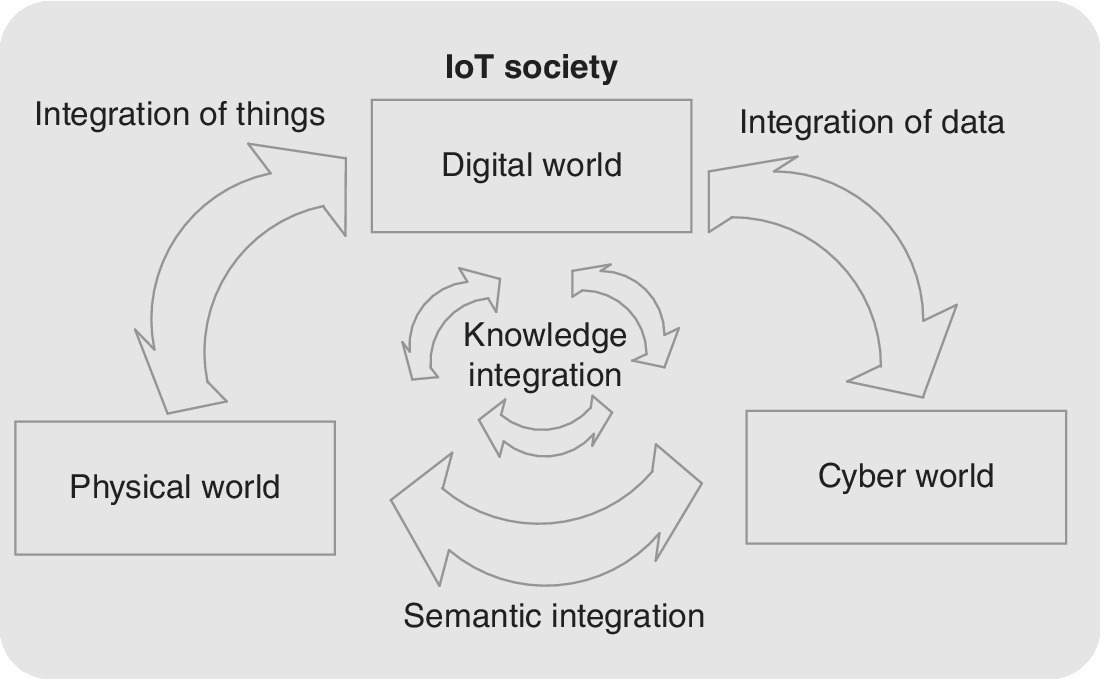
Figure 3.3 The main components of IoT
In many sources, IoT development is presented as waves, each containing more advanced functionalities of IoT solutions as a function of time. The RFID typically has been seen as an early trigger for IoT, especially as an automatized basis for the supply chain to tackle more efficiently inventory management and optimize deliveries [4]. This phase could be generalized as belonging to the first IoT wave. The second wave includes more versatile means for the communications and has been a base for, e.g., applications of many vertical markets like healthcare, transport and security. The next, forthcoming third wave includes even more advanced means for developing services for locating objects and users. Additional waves could include, e.g., means for monitoring and controlling remote objects via presence and management over the WWW. The respective technology areas, along with all of the IoT waves, develop, thus facilitating further enhancements of the M2M and consumer solutions. In fact, this process can be understood as an iterative one, so that the new technology enablers trigger new types of IoT solutions and respective technologies, which again contribute to the further development of technology areas as depicted in Figure 3.4.
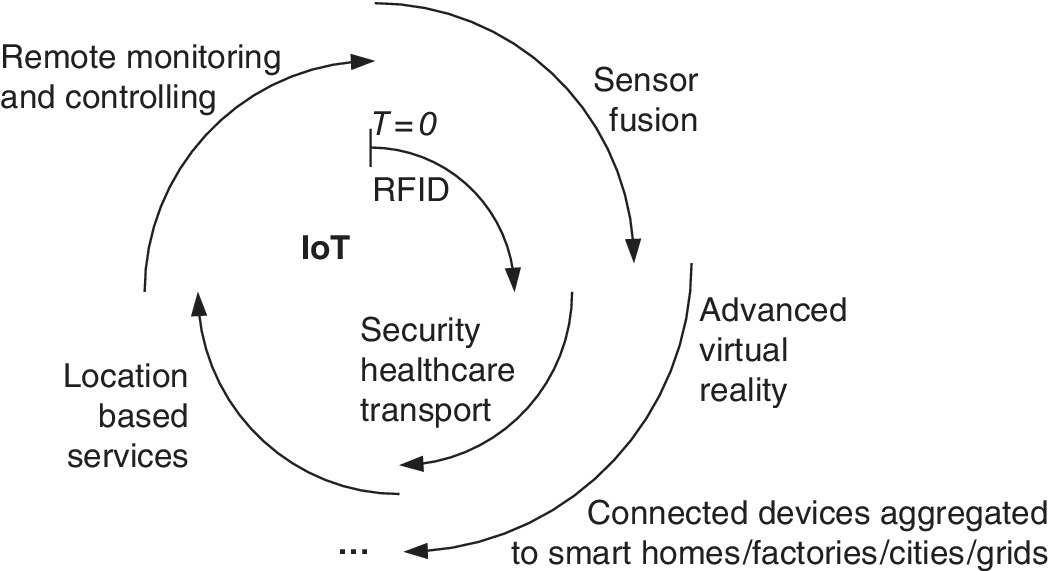
Figure 3.4 The IoT environment is developing along with the technological enablers, each phase or wave influencing the further planning of the enablers in an iterative way
It can be claimed that IoT is an integral part of the overall technological development together with many other areas such as advanced telecommunications networks, sensors, mobile applications and related security solutions such as biometric authentication, cloud‐based solutions, gesture recognition and NFC payment. IoT is thus a fairly suitable term to emphasize the inclusion and involvement of such a variety of entities communicating and participating actively in the contribution to the overall ‘intelligence’ via this always‐aware and always‐connected environment. Some IoT devices include weather‐monitoring tools that can pre‐process data for easing the actual predictions, smart meters for monitoring energy consumption, utility networks control and monitoring systems for gas and water consumption, industrial appliances that measure physical, technical and chemical values, home and office automation systems that can control the living environment based on input from the connected sensors, traffic, transport tracking and medical solutions with sensors that facilitate remote diagnostics, among others. The complete list is in fact close to infinity as new innovative devices are introduced into commercial markets, making our life easier and more fluent. One of the highly relevant domains increasing the reliance on the IoT environment is the automotive, including advanced means for self‐driving vehicles.
To sum up the high‐level picture of the IoT – it can be divided into individual, community and society levels as indicated in Ref. [35]. Some examples of individual IoT devices are smartphones and wearables meant for personal health and money transactions, whereas some community IoT devices include connected cards, health devices and smart homes. Examples of society level IoT devices are smart cities and smart grids.
3.2.5 IoT Market
The advanced consumer device markets are indicating that, together with the evolution of computing, the importance of IoT will be much higher relatively soon [4]. As a reference, personal computers resulted in commercial markets of around 100 million units per year, and there are around a billion PCs and related devices in the consumer markets. Furthermore, the mobile communications markets have introduced – in addition to the advanced feature phones – highly powerful hand‐held devices like smartphones and tablets that represent the business scale for around a billion units per year. At the moment, forecasts indicate that IoT could reach a computing market of around 10 billion units per year [4]. It is a logical and ‘mathematically beautiful’ result of the IT evolution, since it fits nicely into the milestones of over 1 million mainframe computers in the 1960s and over 10 million mini computers in the 1970s, followed by hundreds of millions of PCs and desktop Internet devices between the late 1980s and 2000s, which all led to the current status of billions of mobile Internet devices. The next big step is the explosion of the IoT device markets within the forthcoming decade in a range of tens of billions of units. That is in fact one of the most concrete justifications for the deployment of the vast address base of IPv6.
IoT involves a huge number of stakeholders and businesses as well as many connectivity technologies that enable the always‐connected devices. Although the device might not be switched on and permanently reserve the communication channels, the term ‘always connected’ refers to the ability to ‘wake up’ and exchange information with the network in an autonomic way whether it happens frequently (say, once per second), or only occasionally as needed (like remote low‐power telematics devices emptying the measurement data buffers on a monthly basis).
In fact, the ultra‐low power devices that operate in physically difficult‐to‐reach locations have very special requirements for power consumption and energy sources so that they are able to work automatically without human intervention or physical maintenance efforts during extensive time periods. The deep knowledge and new innovations of this energy efficiency are some of the key components, not only for remote devices but also in general for IoT application and device development. The connected devices may work perhaps for several years by relying on modern energy‐saving techniques such as solar power panels and radio frequency energy which is harvested from the inducted RF energy. This domain has been noted as important to develop further, as it would benefit all the IoT devices equipped with such novelty energy‐saving functionalities.
At the same time, HW and SW developers need to ensure the quality of their products so that the need for maintenance can be minimized, which further optimizes the costly site visits and reparation efforts. This is all a matter of balancing the processing chips, memory types, individual equipment and whole system expenses, quality and performance, interoperability, security and user experiences, among other aspects forming the complete IoT environment.
At the component level, one of the key development areas is the processor power efficiency to ensure an even more feasible base for the connected devices. At the other extreme, on top of the protocol layers, the app developers need to consider the best practices for creating energy‐efficient functionalities. One example is the always‐on communications based on periodic ‘heartbeat signalling’ that forces the user equipment to stay in an active stage without a network. It may greatly impact on the device energy and network capacity utilization. This type of heartbeat signalling may make the device respond faster when needed as there is no initial connection setup signalling for the packet data protocol context activation, but reserving the signalling capacity may prevent other users entering the network. Thus, the app developers need to ideally cooperate with the network infrastructure operators to balance accordingly the benefits and drawbacks of such solutions.
In addition to the power consumption of the device, the evolved battery technologies can further optimize the environment. Ref. [13] identifies the potential for the near future solutions related to IoT Systems on Chips (SoCs) by integrating low‐energy processors with multi‐protocol wireless transceivers and sensor interfaces into a single‐chip integrated circuit. The benefit of such integrated solutions are the reduced cost, complexity and power of IoT applications.
3.2.6 Connectivity
The IoT devices rely on a variety of connectivity technologies because a single technology cannot fit optimally into all the imaginable environments. The challenge of this topic is achieving the optimal balance between costs and supported technologies of the IoT devices, so as an example, not all economical IoT devices can be equipped with LTE connectivity. Instead, some other short‐range solution would serve better, combined by a gateway device that manages the local IoT network and connects it to the external word via, e.g., Wi‐Fi or cellular network access.
Wi‐Fi is a suitable method for connecting devices to the Internet as the respective IP protocols match by default, however, a tiny battery‐operated IoT device may not be able to provide sufficient power for the longer term Wi‐Fi connectivity. The selection of the proper connectivity technology is thus one of the many optimization tasks of the device manufacturers and other IoT stakeholders. Some guidelines may suggest that for applications requiring high data rates and wide coverage areas, LTE/LTE‐A or previous cellular systems may serve best while local high data rate applications can be served via Wi‐Fi. In fact, the best proofs of the increased consideration of the LTE as a base for IoT are seen in the 3GPP standardization items: the LTE‐U for unlicensed operation and LTE‐M for the M2M environment, standardized and added as part of the other LTE variants.
For the lower data rate solutions in limited areas, low‐energy Bluetooth (BLE) can serve small amounts of IoT devices while ZigBee can manage more devices via mesh networking, both being more energy efficient compared to Wi‐Fi or cellular connectivity. High energy efficiency is typically a requirement for battery‐powered connected IoT devices that may remotely monitor and control, e.g., security systems. These devices may be based on programmable microcontrollers, embedded sensors and actuators which monitor and respond to environmental phenomena such as an opening door, breaking window, change of temperature, humidity and lightning. Especially in critical environments such as surveillance data monitoring and transmission, controlling and alarming environments with potential life‐threatening conditions involved, the assurance of energy as well as connectivity is essential. Also, even less critical environments such as home sensors for controlling temperature or lights benefit from reliable energy and connectivity solutions. One solution for the management of such environments is based on the distributed intelligence of IoT with interconnected devices to optimize the monitoring and delivery of sensor data in real time, combined with cloud computing resources for post‐processing and analysing the data. Users may also be able to control the respective IoT devices via smart devices or other remote methods.
The development of smart sensor solutions is thus one of the key areas in IoT, to provide data for the controlling and management of smart homes (varying humidity, temperature and lighting depending on the physical presence of users and user‐based profiles etc.), and to provide information for the safety and security, including the health check and alarms related to home appliances that are failing (to act before the incidence happens). There are endless amounts of opportunities in the IoT environment for current and new stakeholders, providing interesting business opportunities that may benefit from partnerships and cooperation.
IoT handles vast amounts of real‐time data from the field via always‐connected devices such as intelligent sensors, forming part of the ‘big data’ environment. The IoT devices themselves and respective systems analyse the data and provide processed results as a base for decision making. IoT is thus suitable for managing, controlling and connecting devices such as home appliances, cars, businesses and complete cities in a highly automatized way without the need for human interactions. With so important a share of exposure in data collection and processing, the respective security is becoming one of the most essential elements in this environment with a high level of integration. There is thus room for combining current security solutions in an innovative way to ensure safety of the users, as well as for completely new security solutions.
The IoT environment is transparent for the physical radio (or fixed) connectivity while the messages from the IoT devices such as sensors are delivered or relayed to the destination, and vice versa (for the two‐way systems). The wireless IoT connectivity can therefore be based on the licensed or unlicensed bands which are used by, e.g., mobile communications systems, wireless local area networks, low‐range systems such as Bluetooth and ZigBee, etc. The typical division of the networks categorized by the operational range: Personal Area Network (PAN), Local Area Network (LAN), Neighborhood Area Network (NAN) and Wide Area Network (WAN), the latter being, e.g., the Internet itself covering the whole globe [14].
As the term suggests, IoT refers to connecting all kinds of devices to the Internet in one or another way. The devices that connect directly to the Internet are based on the IP protocol suite which enables by default the interoperable functions and data transfer between all the other Internet‐connected devices. One of the challenges of the other, often varying connectivity technologies is the interoperability – or better said, the lack of it. In fact, in many cases, the internal IoT system might have been designed by utilizing non‐IP or even proprietary connectivity technologies in order to simplify the TCP/IP structure – which in many cases is indeed unnecessarily heavy. So, the local network devices may use protocols deviating from the standard IP in the internal communications while connectivity to the Internet of these devices may be done via a gateway which supports the IP connectivity for the communication with the external world, and the non‐IP connectivity within the internal network [14]. The physical connectivity of these gateways, or hubs, may be any of the networks able to communicate via IP such as mobile networks.
3.2.7 Regulation
IoT does not yet have a dedicated regulation. Nevertheless, there are such vast impacts foreseen from the deployment of the billions of IoT devices within the forthcoming years that the need to review current regulation is obviously needed. The discussions include especially the principles of storing the data and protecting the privacy of the users.
As Ref. [35] indicates, IoT can be expected to impact on licensing, spectrum management, standards, competition, security and privacy. There are already familiar aspects in current regulations that match with the forthcoming IoT, and that have been managed in previous systems. This is the case especially in the telecommunications and ICT regulation that has been involved with aspects related to competition, privacy and data protection. Also, the regulatory consequences are sometimes quite logical as is the case in the need for very large address spaces in order to identify the billions of connected objects. One of the obvious solutions for this is the IPv6, which requires proper management of the addresses. Ref. [35] also emphasizes the implications that are not necessarily obvious. One of such phenomenon under active investigation by the Federal Communications Commission (FCC) is the additional load that IoT brings to current services such as Wi‐Fi and mobile networks, yet it is expected that new spectrum will not be explicitly allocated to the increasing IoT communications. As an example, the European Commission sponsored investigations indicate that a license‐exempt model may support IoT development by avoiding contractual negotiations before devices are manufactured and used, which promotes large‐scale production of more economical devices. Nevertheless, there is a need to follow up the advances to monitor how the market dominance will develop along with IoT devices and services – which belongs to the role of the competition regulators to ensure the balance between competitive market and innovation.
There is also regulation involved at least indirectly with IoT connectivity, especially related to the high‐level frequency strategies in global and regional levels. As an example of the frequency regulation, the additional definition of the LTE/LTE‐A bands is a joint effort of 3GPP, 3GPP2, industry and regulatory bodies, and there is obviously a great need to take into account the M2M and IoT traffic which can be seen, e.g., via the inclusion of the LTE‐M as a part of the specifications. The identification of the frequencies suitable for the M2M communications has been discussed, and the liberation of previously utilized bands should ease the task. The general principle of the frequency regulation has been to actively identify new possibilities for the band utilization in such a way that the broadband spectrum needs to be flexible. The main body, ITU and World Radio Conference (WRC) events in 2012 and 2015 have identified the clarification of the Digital Dividend (DD) as one of the priority tasks aligned with cross‐border coordination.
The DD spectrum, as one of the many options suitable for the M2M traffic, has been allocated to 790–862 MHz. The band was used for commercial LTE deployment in the USA and Germany as of 2010. In the USA, the DD spectrum was auctioned in 2008, and the concrete LTE deployment is advancing via Verizon Wireless that opened commercially the 700 MHz LTE network at the end of 2010. In addition to the already identified DD spectrum, there is also growing interest to extend the band in Europe below the already existing band. The strongest argument for the extension is the previous analogue TV bands that had already been ramped down by the end of 2011 in most European countries.
3.2.8 Security Risks
3.2.8.1 Overall Issues
The basic question in the IoT environment is how to reliably identify IoT devices and ensure secure communications between the devices and systems. One of the early‐day principles of the Internet‐connected devices is to provide a MAC address that identifies explicitly the devices. This is the case for basically all the IP‐connected devices like printers, Wi‐Fi cards, etc. The MAC address thus sounds like the most logical way to distinguish between the IoT devices. The issue of the MAC address is that even if it is hard‐coded into each device to ensure the uniqueness, it is straightforward to alter in the IP communications via suitable software. Thus, the IoT system cannot for sure conclude if the connected devices really form part of the legitimate equipment or if there are possibly some cloned devices connected into the system which may aim to capture confidential traffic.
The more secure way to identify IoT devices is based on, e.g., a public key structure, or by including some suitable HW‐based storage into the device that is hard to tamper with such as a SIM card, embedded SE or TEE. The issue of these solutions is the cost as the business model of the most economical devices would not tolerate such an additional expense. Another, possibly more cost‐effective approach for the deployment and user experience may be related to the tokenization although the basic question remains on how to identify the correct IoT devices and how to securely transport and store the tokens into the devices.
Along with the advances of the SIM card and remote subscription management in an interoperable way – as it is currently under standardization by various organizations – there are new methods presented for these items such as PKI‐based developed key distribution and secure channels for accessing the contents of the SE, which refers to the development of the variants of the SCP.
3.2.8.2 Network Element Considerations
Ref. [11] has identified a highly relevant security issue in the growing IoT environment which is related to the embedded systems. These embedded vulnerabilities are a result of years of deployment which has resulted in many kinds of equipment still forming part of the uncountable number of elements in the Internet infrastructure, such as routers and bridges. The issue with these network devices can potentially be such that the security vulnerabilities are not patched automatically as is the case typically with consumer devices like laptops and smart devices. Instead, the security vulnerability may stay unmonitored and open doors for malicious intentions to overload the element, access further the network, and scan and modify the traffic within the respective core network. The correct way is obviously not the hiding the problems by the equipment manufacturers and operating entities as the knowledge about these security holes would, once revealed, spread very fast among the interested parties.
The very challenge of this area of potential middleware vulnerability is the difficulty to provide and manage updates for the security holes of the SW. The impact may be considerable as Ref. [11] indicates by referring to the Def Con event where a researcher investigated a set of commercial home routers and managed to break into half of them, including some of the most common brands. One of the basic root causes for these issues is that the respective systems are equipped with computer chips that are typically very economical. Due to the highly competitive environment, the chip manufacturers have limited ways to differentiate from each other for features and bandwidth. These chips often contain Linux‐based OS and open‐source SW components. This environment does not encourage the companies to enhance further the security aspects of the chip as it may require reservation of the very tight resources from the further manufacturing of the following chip generations.
The routers, bridges and other IP core elements are typically made by OEMs that might not get the brand name visible in the final product and thus do not have too much incentive to exceed the requirements for the chips, while the company representing the brand might have equally low interest in any security enhancements for the final product. As soon as the equipment is commercialized and deployed, it might be equally challenging to get security updates for the chip‐related issues because of the low priority for maintaining old variants of the chips and products.
Furthermore, as Ref. [11] emphasizes, the SW might be relatively old even for new devices. Regardless of the relatively low possibility of new security patches developed for the chips, some components might lack patching which leads to security vulnerabilities as the systems age; one reason for this situation being the lack of the original complete source code. If the patch is available, the user normally needs to proactively download and install it. Nevertheless, the issue is that there is not often alerts for these patches, and if the ISP does not have a process for remotely installing the upgrades, the users might not be experienced enough to perform such upgrades for routers, modems, etc. Ref. [11] concludes that there might be a considerable amount of unpatched and insecure devices in the Internet. Some potential security breaches arise thus, e.g., via malicious DNS changer type of attacks against home routers and computers, and mentions an example of a Linux worm that can target routers, cameras and other embedded devices.
Along with the exponential growth of IoT devices, they could also potentially suffer from the same type of issues as a result of possibly low levels of SW patch maintenance, unless it is specifically addressed by the device manufacturers in an early phase. It has already been evident that some of the current and forthcoming variants of routers and modems are under special risks because they are located in the interface between users and the Internet. That makes it almost impossible to simply switch these vulnerable equipment off upon security breach events occurring. They also are increasingly powerful regarding the processing performance and the amount of embedded functionalities which makes them comparable with computers. Furthermore, as they are typically always‐on‐connected, they are increasingly attractive target for malicious attacks.
3.2.8.3 IoT Security as Defined by the GlobalPlatform
The GlobalPlatform has identified several security concerns for IoT as described in Ref. [2]. One highly relevant observation is related to the fact that the current and expected IoT devices are often used in environments that include critical infrastructure and systems such as transportation and medical devices. The potential security issues in this domain are related to the overall security of the devices as well as the users’ privacy as a result of the IoT technology that interacts by definition with the physical world, which in turn may expose security holes compromising the private data. The GlobalPlatform emphasizes the special importance of unattended devices like electricity meters that are able to broadcast sensitive data without our awareness, and that require protection from potential attackers. Not only the M2M traffic but all the involved stakeholders need to ensure IoT security, including consumers, network element and mobile device manufacturers, network operators, service providers and application developers. The old saying about the chain being as strong as its weakest link applies in this environment excellently.
In order for the IoT market to evolve favourably, and to ensure that the development takes into account the security aspects, the GlobalPlatform has identified some key principles. These include the requirement for IoT devices to support a multi‐actor environment that facilitates the varying of security and access settings per involved party. Furthermore, service providers should independently have means to remotely manage their own security parameters. It is also important to be able to add services and service providers to a device after it is deployed in the field. The service subscriber must be able to change service providers during the expected lifetime of the device which may be considerable depending on the use case and environment, the automotive being one representative for long‐term device utilization. All this basically refers to the evolved subscription management concept which is actively under standardization at the GlobalPlatform as well as by various other organizations. More details of the enhanced, interoperable Subscription Management (SubMan) concept is described in later chapters of this book.
Being involved in many mobile telecommunications development items, the GlobalPlatform also acts in the role of IoT standardization and provides open technical specifications that focus on the interoperability and security of connected devices. The specifications of the GlobalPlatform include features that aim to enhance the privacy and security of IoT, such as the SE which works as a separate chip hardened against physical and logical attacks, and enables secure hosting of applications for various stakeholders. The GlobalPlatform also works on SD which stores cryptographic content for a stakeholder on the SE and provides mechanisms to manage such content and establish secure communications with external entities. Other related items of GlobalPlatform are the Trusted Service Manager (TSM) which is a third‐party broker establishing business agreements and technical relationships between different stakeholders in a service delivery, the CA which allows for confidential post‐issuance introduction of new stakeholders onto an SE, and the TEE which is a secure area residing on a mobile device that ensures sensitive data is safely stored, processed and protected in a trusted environment on that device [2].
The GlobalPlatform has identified various use cases for emphasizing the need of M2M security including healthcare, automotive, wearable devices and energy. Ref. [2] details how the GlobalPlatform specifications can address the privacy and security concerns for the deployment of IoT and M2M devices by relying on embedded technologies for new forms of secure communication and data transmission. Ref. [2] also presents descriptions of the use cases, introduces the function of IoT devices and details how vulnerabilities in security and privacy can be resolved.
3.2.8.4 Threats and Protection
Ref. [18] identifies some concrete key threats in the IoT environment and potential risks related to the security and privacy of the connected devices. In comparison to the currently typical hacking efforts against companies, with IoT, the hacks will be remarkably personal. In fact, as our homes may contain various IoT devices, they could open security holes for someone hacking into living rooms, baby monitors, smart TVs and other connected consumer devices without our awareness.
According to Ref. [18], the IoT devices are typical representatives of Minimum Viable Products (MVPs). The MVP is a product that needs to be released fast while the concrete enhancement feedback comes from the customers which, in turn, helps to make the product better. In the case of IoT devices, this means that there is no time or resources for ensuring the security and privacy of the equipment especially for the most economic ones. Also, for the simple devices, additional security may result in lower fluency for the user experiences. Thus, a strong password may not be attractive for setting up a new, highly economical IoT device during the out‐of‐the‐box phase.
Ref. [20] summarizes further the reasoning behind such a huge amount of security breaches of IoT so far. The base for these phenomena is the very fast pace of digitally connected devices becoming an essential part of our daily life, including our homes, offices, cars and even the very close proximity in the body area. Along with the growth of the IPv6 and Wi‐Fi network deployments, the IoT environment is shaping fast – and can have large amount of potential security holes. The positive side of IoT is definitely the existence of a completely new set of platforms that enable us to perform something totally new, but at the same time the drawback is that IoT is becoming an increasingly attractive target for cybercriminals along with the increased number of connected devices that can expose more attack vectors.
Some of the compromised IoT devices that have been reported in public include IoT baby monitors that may provide a door for criminals to monitor the feeds, to change camera settings and to authorize external users to remotely view and control the monitor. Another widely reported case relates to Internet‐connected cars with indications of potential risks for criminals being able to take control of the entertainment system, unlock the doors or even shut down the car in motion. Ref. [20] further emphasizes the increasingly important role of wearables that may become a source of security threats as hackers could potentially target the motion sensors embedded in, e.g., smartwatches to interpret the contents, or to steal personal sensor data from health devices.
In addition to the compromised personal data, the more severe security breaches are related to those cases that may have impact on personal physical security. An example could be medical device monitoring and maintaining vitals such as pacemakers which, in case of any disturbances such as altering the results of the heart‐rate functioning, could cause unrepairable damage or even death.
As an example of the industry forums, the IoT Security Foundation is a non‐profit industry body responsible for vetting Internet‐connected devices for vulnerabilities and offers security assistance to tech providers, system adopters and end‐users. The aim of the Foundation is to raise awareness through cross‐company collaboration and encourage manufacturers to consider security of connected devices at the HW level [31]. There are also efforts by many companies to set up platforms enabling large networks of IoT devices to identify and authenticate each other in order to provide higher security and prevent data breaches. Other examples can be found from various research works to enhance IoT security through device and smartphone linking.
Some simple guidelines are often sufficient in the initial phase of IoT device deployments. From the consumer’s point of view, upon installing a new IoT device such as an Internet‐connected toaster, baby monitor or any other ‘always‐connected’ device, the rule of thumb is to change the default password immediately before the equipment is used. For the manufacturers, it would be ideal to totally isolate personal health‐related functions from the open Internet, even if it were well protected via passwords. Furthermore, the protected data (cloud, devices, bitlocker) is justified for both industries and consumers as it is highly risky to leave any plain data (texts, images) if the contents could be accessed by non‐authorized persons. For the device manufacturers, the assurance of the data storage either via the utilization of HW‐based secure elements, as much as reasonable cost‐wise, guarantees the highest protection level. Solely SW‐based security is typically more vulnerable than, e.g., micro‐SD, embedded SE, removable UICC or TEE based methods.
It is always recommended to check the weakest links in the end‐to‐end security. Even if the IoT device looks relatively innocent, and the home environment is otherwise well protected, a device such as a non‐protected sensor‐containing freezer that is connected to the same home network could open a surprisingly easy security breach door for criminals. It is also a good idea to keep up to date with security news such as the latest advances in the DNS protection, firewalls and virus protection SW for all the relevant devices.
3.2.9 Cloud
Due to its usefulness for many consumer and M2M environments, the cloud can be considered as an important – if not integral – part of IoT. Cloud computing is based on the sharing of resources in order to obtain capacity gain, to distribute processing resources and to achieve economies of scale. The drawback of dedicated data delivery networks is that their typical load is only a fraction of the dimensioned maximum capacity due to the fact that there are occasional load peaks that demand considerably more capacity. Instead of all the capacity operators managing this type of highly over‐dimensioned networks for the sake of the serving of these capacity peaks, the whole delivery infrastructure may, instead, be concentrated into a single, large IP cloud. As the capacity peaks of different operators or areas within a single operator typically won’t occur at exactly the same time according to statistical probability characteristics, the total offered capacity of the cloud can be considerably lower than the sum of the individual networks.
This concentration of capacity into the cloud is one of the benefits of cloud computing in telecommunications [10]. Furthermore, the uploading and downloading of cloud data in thee mobile environment is especially fluent via LTE/LTE‐A as they provide fast data rate and low latency. Taking into account the charging of data transmission over air via mobile networks, one of the typical solutions is the utilization of Wi‐Fi Offloading together with the LTE/LTE‐A radio access. Cloud computing is a solution that enables on‐demand network access to a set of shared computing resources that are configurable. The initial evolution of cloud networks and services has been driven by the needs of large companies, but it can be assumed that cloud computing is also becoming an increasingly important daily tool for smaller companies and end‐users.
As the cloud concept is still relatively new, there might be concerns about the connectivity control, security and privacy as the functionality and contents are distributed outside the previously highly local, much more isolated and thus more manageable environment. The important task for the network service providers is thus to address these concerns and make the respective measures to minimize potential security risks. The proper encryption and protection of user accounts are some of the priority tasks of service providers.
An important need for cloud computing is to outsource IT tasks to cloud services available over the Internet. The benefit of this evolution is that an increasing amount of resources can be managed via a single point and utilized by applications and services based on need. Naturally, it may take years for the large‐scale support of cloud services. The server virtualization is one of the ways to create internal and external cloud networks and services. There are also other areas that need to be initiated and developed like the meta‐operating system that eases the management of distributed resources as a single computing pool. The meta‐operating system is a virtualization layer between applications and distributed computing resources. It takes advantage of the distributed computing resources in order to manage and control applications and related tasks such as error control. In addition, there is also a need for a service governor for the decision making about the final allocation and prioritizing of the computing resources for applications.
Cloud computing offers dynamic network structuring. An example of this functionality is SW‐based networking as part of cloud computing access via low‐cost and flexible adjustments by the cloud customers. Cloud networks also provide safety features for essential network functions like IP routing, address management, Network Address Translation (NAT), authentication and QoS.
Via SW‐based networking of cloud computing, the network architecture of the customers can be replicated regardless of the location. The replication includes changes to topologies and policies, making cloud networking a logical platform for disaster recovery in a dynamic and cost‐effective way.
Specifically for the IoT environment, it is essential to facilitate the secure communications with the cloud as well as the storage without exposure to external users. Some cloud‐related use cases include secure payment via HCE and cloud storage for IoT telematics and traffic analysing service. The cloud concept is highly useful as it makes an abstraction to IoT communications and can give added value in many type of environments, e.g., a tokenization entity for banking and safe storage for telematics.
3.2.10 Cellular Connectivity
3.2.10.1 RF Band Deployment Scenarios
The cellular RF bands form one of the most useful bases for IoT devices that require connectivity within a wide range. With only a small set of quadruple bands, GSM can provide global functioning. Even by adding the latest bands such as 450 MHz, GSM connectivity is relatively straightforward to deploy by device manufacturers as well as by the network operators as it is part of such a robust technology. The same principle applies to 3G technologies such as UMTS, which provides global functioning with only five RF bands. The benefit of 2G technologies, especially for GSM, is the widely available service area. The networks are typically deployed on 900 and 1800 MHz or 850 and 1900 MHz bands, which are able to provide very large coverage for IoT devices far into future assuming the systems are maintained in a parallel fashion along with the 3G and evolving 4G systems – and of course, during the ITU‐R compliant 5G systems that will be deployed as of 2020.
The current environment is much more diverse with the pre‐4G LTE and fully ITU‐compliant 4G LTE‐A as there are also considerably more RF bands available. At the same time, it ensures a sufficient set of options for the stakeholders (terminals and networks optimized per region), on the other hand, a single device can hardly support all the possible frequency options if it is supposed to be techno‐economically feasible. The selection of the most optimal frequencies by the device manufacturers and operators is thus one of the most important tasks in the device selection, deployment and operation of the networks, and it clearly depends on each market. The following sections summarize the global status for the LTE/LTE‐A bands in order to present the challenges of RF band fragmentation.
3.2.10.2 LTE/LTE‐A Spectrum in Practice
The high number of possible LTE and LTE‐Ad bands provides a large set of options per ITU region, continent and country. There is such a variety of e possibilities that regulators, operators and device manufacturers need to form their strategies with great care. One example of the diversity can be seen in Figure 3.5 that indicates the LTE Frequency Division Multiplex (FDD) and Time Division Multiplex (TDD) frequency deployments or plans in the Latin America region. Figure 3.6 shows the typical, assumed LTE/LTE‐A band deployment and carrier aggregation scenarios for the rest of the world. The information is based on various publicly available indications about regional frequency plans.
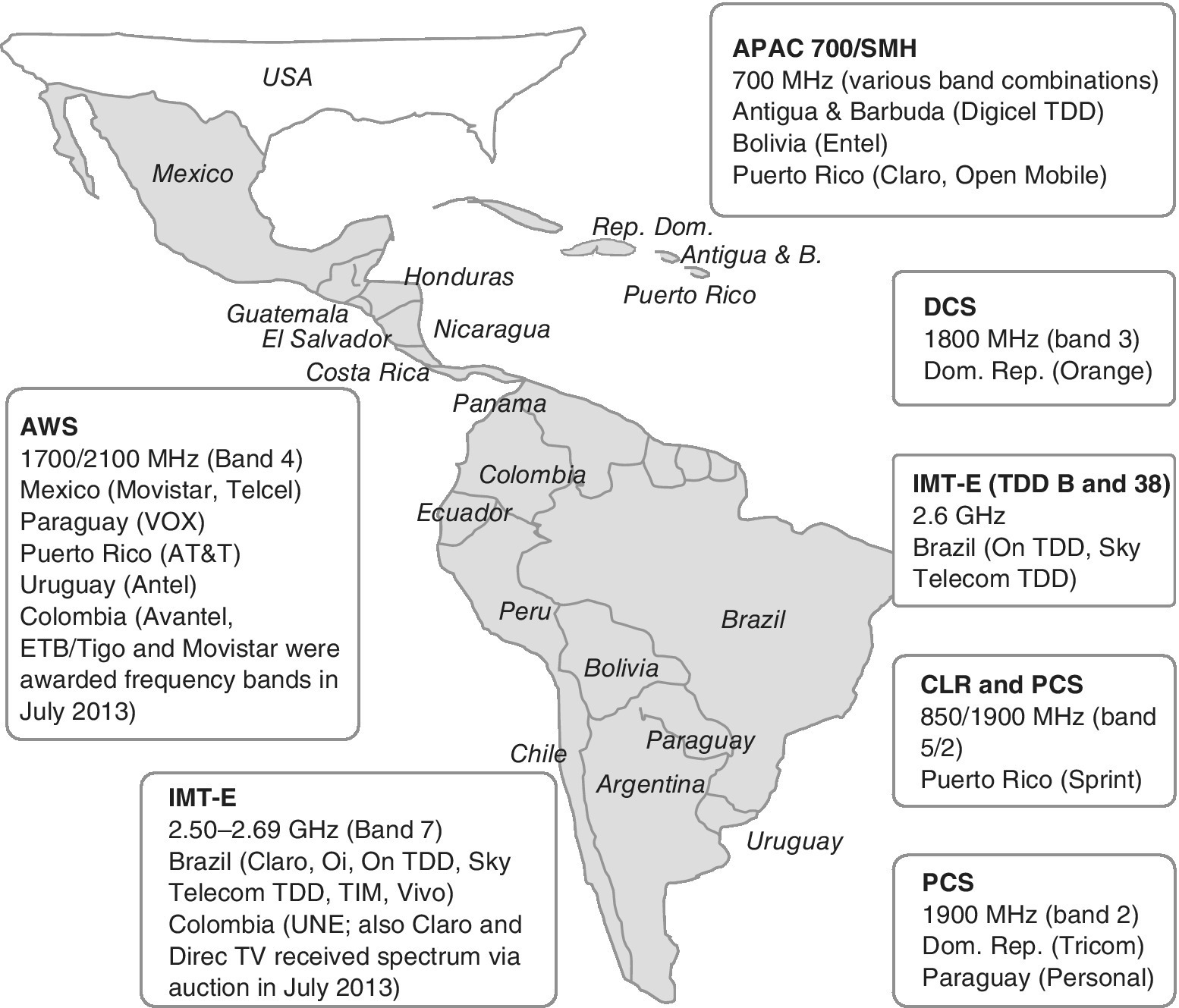
Figure 3.5 An example of the potential LTE spectrum plans of Latin America
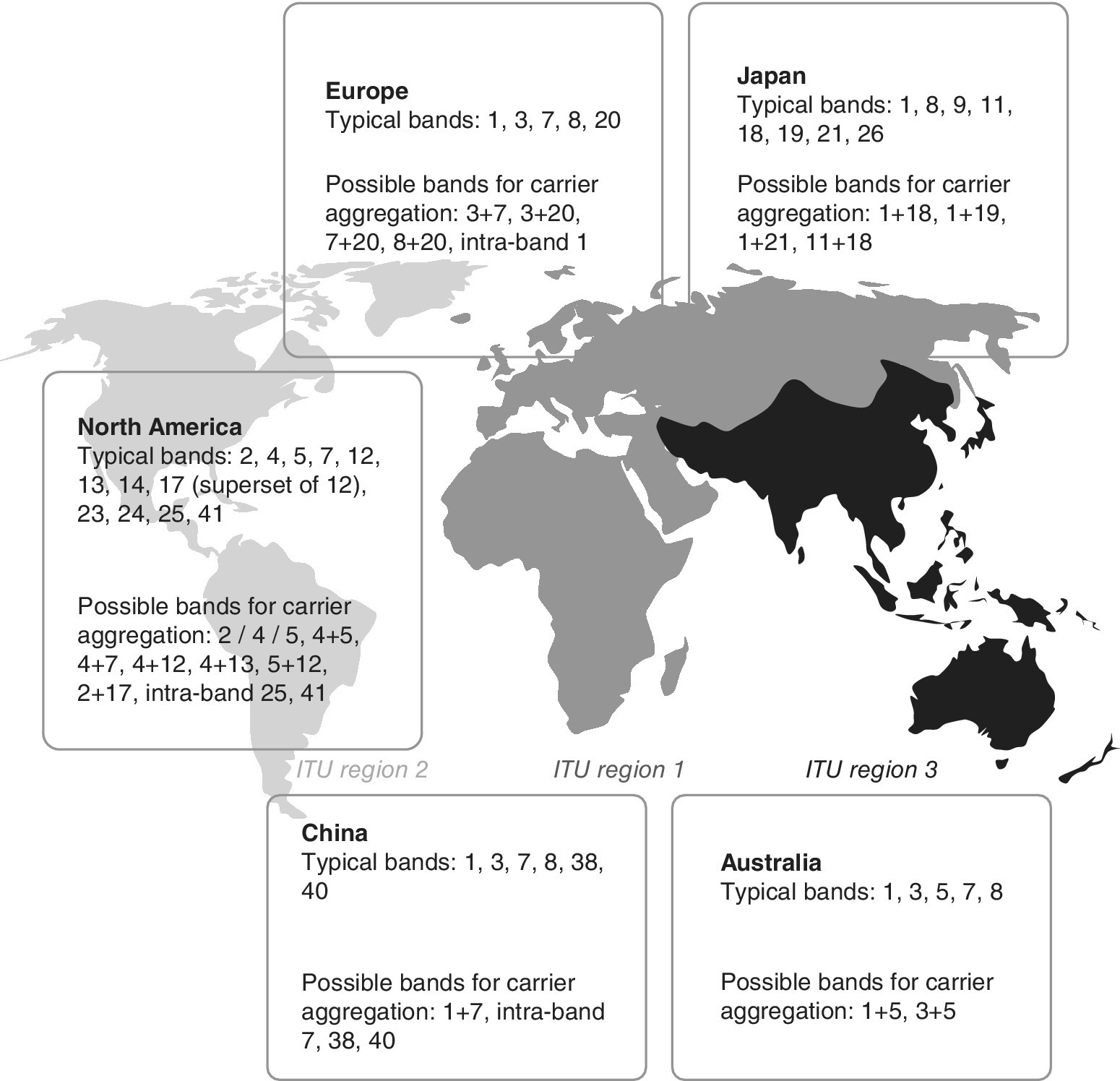
Figure 3.6 Typical LTE/LTE‐A band scenarios and potential carrier aggregation deployment in the rest of the world
As can be noted from Figures 3.5 and 3.6, there is a very wide set of potential LTE/LTE‐A RF band variants in the world, and many differences even within smaller regions. The planning of the LTE/LTE‐A devices – both consumer devices as well as IoT devices – is thus much more complicated than with previous mobile communications systems. The optimization of the device’s band support depends on many aspects like target markets, device category and size. Chapter 6 discusses in more detail the methodology the device vendor may consider for optimizing the device RF band set.
The first commercial LTE networks were deployed at the end of 2009, and the initial significant launches were seen in the USA and Japan by the end of 2010. In addition to the FDD frequency band, the TDD spectrum also provides increasing opportunity for LTE/LTE‐A developments, despite the fact that traditionally the TDD spectrum has been less attractive to operators than the FDD spectrum. Based on recent developments, it can be expected that the role of TDD will increase significantly during the forthcoming years.
The LTE networks have been implemented on many frequency bands. It can already be seen that the fragmentation of the RF bands is a reality, which is noted by the industry, vendors, operators and chipset developers. The availability of options offers possibilities but also interoperability challenges which need to be optimized.
In addition to the various bands, LTE/LTE‐A also supports various frequency bandwidths depending on the frequency and region. The range may vary between 1.4 MHz, 3 MHz, 5 MHz, 10 MHz, 15 MHz and 20 MHz. The flexibility ensures that the operators are able to select the most adequate strategies for LTE/LTE‐A deployment in align with the already deployed GSM and UMTS RF bands especially in 850, 900, 1700/2,100, 1800, 1900 and 2100 MHz bands. This flexibility provides highly dynamic re‐farming in such a way that while the capacity of the previous systems lowers, the customers may be directed gradually to utilize more efficiently the LTE/LTE‐A system. In the initial phase, the utilization of the narrowest bandwidths 1.4 MHz and 3 MHz may often make sense in order to introduce LTE/LTE‐A into the commercial market although the achieved data rates would logically be relatively low. As the situation develops, LTE/LTE‐A may reserve more bandwidth up to 20 MHz, and with carrier aggregation up to 100 MHz when applicable which provides the highest data rates.
In the frequency bands without previous legacy systems, such as 700 MHz and 2600 MHz, LTE/LTE‐A may be deployed with the maximum possible bandwidth from scratch. Especially the 700 MHz band, as well as the latest addition of 450 MHz, may be highly suitable for wide rural areas. It should be noted though that the antenna size of the lowest range, e.g., on the 450 MHz band, needs to be relatively large in the UE in order to fully exploit the benefit of the lower frequency propagation characteristics. For small‐size equipment like hand‐held smart devices, the small antenna may compensate the benefit of the wide propagation due to the relatively high antenna loss, so the 450 MHz band probably suits best for larger‐size equipment like integrated LTE/LTE‐A tablets.
A feasible solution for both device and network would be the support of combined low bands (selected frequency around 700–900 MHz) and high bands (selected frequency from 1800 MHz up to 2.6 GHz or even 3.5 GHz). The low bands provide large coverage while the high bands provide more capacity and highest data throughput.
Even if the 3GPP list of frequencies looks overwhelming, it allows the selection of the most suitable network deployment scenarios at the regional level – as long as the network vendors and OEMs ensure the availability of sufficient sets of equipment per region. As an example, the new band 2600 MHz is increasingly important in many regions like Latin America, Europe, Asia (Pacific), the Middle East and Africa, as can be interpreted from spectrum acquisitions and publicly available near‐future plans of these regions. Also the reorganization of the television frequencies due to the ramping down of the analogue systems brings new opportunities for e LTE/LTE‐A deployments in the DD spectrum, and the re‐farming scenarios in 850/900 and 1800 MHz bands are also logical options for the LTE/LTE‐A networks. The 700 MHz frequency spectrum especially has triggered much discussion and concrete steps for deployments. The Asia‐Pacific (APAC) band 28 has been identified as one of the most potential candidates in the Latin America region. Japan is also active in the initial deployment of 2100 and 1500 MHz bands. The benefit of 2300, 2500 and 2600 MHz bands is the wide availability of the spectrum.
The new LTE/LTE‐A options include s new opportunities for the deployment in the DD spectrum and in the 2600 MHz band, as well as on many other new frequency bands like the L‐band and 1800 MHz band. The first concrete steps in the deployment of DD spectrum bands were taken in the USA and Germany, and continued by more auctions. The deployment of the 2600 MHz band is especially popular in Europe, and there seems to be increasing interest in the 1800 MHz band in Europe and Asia Pacific. There are also some concrete ideas for further enhancing LTE/LTE‐A spectrum utilization via cognitive radio and the white space concept. The development of the white space concept is driven by the USA and the UK, and might offer considerable benefits as part of the band strategies.
3.2.10.3 Advanced RF Utilization
Cognitive radio is another idea for more efficient LTE/LTE‐A spectrum utilization. Nevertheless, the concept is still at an early stage and commercial deployments are not as yet taking concrete steps. The first deployments are US‐driven along with the utilization of white space spectrums. As the idea is still relatively new, it must also need regulative bodies to make efforts.
As for the more concrete LTE‐A items, the utilization of Carrier Aggregation (CA) is growing fast in order to increase the capacity. CA is one of the major items for paving the way to the ITU‐compatible 4G era and respective higher data rates. The additional benefit of CA is that it is able to take advantage of the otherwise isolated frequencies. Furthermore, CA may be used for unidirectional frequencies. An example of this option is the reassignment of the former US MediaFLO band 29, which is only defined for Downlink (DL), to LTE/LTE‐A.
3.2.11 WLAN
WLAN with various variants is currently one of the most popular Internet access methods. Along with the general development of wired Internet access methods and packet core networks, WLAN solutions have gone through major enhancements. As a result, the bit rate has increased exponentially since the 1990s, and the functional area of the networks grows constantly. The first‐phase WLAN was formed by the early IEEE 802.11 standards, which are being gradually complemented. Table 3.1 summarizes the current most relevant WLAN variants [17].
Table 3.1 The key WLAN IEEE 802 standards
| Version | Name | Frequency band | Bit rate (maximum theoretical) |
| IEEE 802.11 (legacy) | WLAN | 2.4 GHz | 1 Mb/s–2 Mb/s |
| IEEE 802.11a | WLAN (Wi‐Fi) | 5 GHz | 54 Mb/s |
| IEEE 802.11b | WLAN (Wi‐Fi) | 2.4 GHz | 11 Mb/s |
| IEEE 802.11 g | WLAN (Wi‐Fi) | 2.4 GHz | 54 Mb/s |
| IEEE 802.11n | WLAN (Wi‐Fi) | 2.4 and 5 GHz | 300 Mb/s |
| IEEE 802.11 ac | WLAN (Wi‐Fi) | 5 GHz | 1 Gb/s (total area) and 500 Mb/s (single station) |
| IEEE 802.11ad | WiGig | 60 GHz (and backwards 2.4/5 GHz) | 7 Gb/s |
| IEEE 802.15.1 | Bluetooth | 2.4 GHz | 1 Mb/s |
| IEEE 802.15.3/3a | UWB | Various bands | 10–500 Mb/s |
| IEEE 802.15.4 | ZigBee | 2.4 GHz, 915 MHz (America), 868 MHz (Europe) | 250 kb/s |
| IEEE 802.16 | WiMAX | 10–66 GHz | 120 Mb/s |
| IEEE 802.16a/e | WiMAX | 2–11 GHz | 70 Mb/s |
| IEEE 802.16 m | WiMAX 2 | Licensed IMT‐Advanced bands | 100 Mb/s, 1 Gb/s |
| IEEE 802.20 | WMAN/WAN | 3.5 GHz | 1 Mb/s |
| IEEE 802.22 | Wireless Regional Area Network | VHF/UHF TV bands | 19 Mb/s |
As is the case for the mobile networks, security is an important aspect in private and business WLAN environments. In practice, if the radio interface of the WLAN is not protected by a password, it is basically available for public use. In the worst case, the Access Point (AP) can be used for illegal purposes by external attackers. Setting up the server as a delivery element for image, music or video contents without the permission of the content owners is only one of the countless examples on how the open access can be misused.
The most elemental and easy option for increasing the security level of the WLAN networks is to activate the access code request upon establishing the connections with the AP. Insecure WEP is used for the initial WLAN access restriction, and it has been enhanced via several versions. Chapter 2 details the modern methods for the WLAN protection.
3.2.12 Low‐Range Systems
While the cellular systems provide the widest coverage area for IoT (apart from the satellite systems which are probably too costly for general use), the local connectivity methods can be used for information sharing between the devices within the area, or via hubs which could be further connected to, e.g., the cloud. There are various methods for the local connectivity available in the commercial market, and each solution has pros and cons depending on the use case, mobility, required data rate and maximum needed coverage. Some of the key technologies for the connectivity are:
- Bluetooth. The popularity of this method has been increasing along with the technical advances since the first versions. The low‐energy variant of Bluetooth (BLE) is especially feasible in the IoT/M2M environment as it requires only low power consumption yet offers sufficient coverage for local coverage.
- Wi‐Fi. The importance of Wi‐Fi has been increasing gradually as more hotspots become available in public places. Wi‐Fi is typically a method to connect to Internet services as an affordable alternative to cellular connectivity. Typically, the SW updates of smart devices are increasingly done via Wi‐Fi as an alternative to the SW downloading via a laptop/PC that is connected to the mobile device. Operators are also getting interested in offering wider Wi‐Fi Offloading solutions to the consumers to balance the cellular network load.
- Near Field Communications (NFC). This is the closest range technology that has been gradually appearing into new markets since 2012. It can be used in many solutions via a tap gesture of the consumer, including information sharing (similar to RFID), establishing connections for audio/video and performing secure payment.
- Radio Frequency ID (RFID). This is based on readable and optionally writeable tags. It represents a very basic connectivity of the IoT mobile device, although it can be integrated into the overall functionality of the device/SIM.
- Wireless USB. A short‐range, high‐bandwidth wireless radio communication protocol designed by the Wireless USB Promoter Group. It is maintained by the WiMedia Alliance. Wireless USB was based on the Ultra‐Wide Band (UWB) platform of the WiMedia Alliance, providing 480 Mb/s within a 3 m distance, or 110 Mb/s within a 10 m coverage range. The bandwidth was 3.1–10.6 GHz. The Current implementation is W‐USB, which is able to form USB systems including host, devices and interconnection support. It is based on the USB hub‐spoke model that allows a maximum of 127 wireless devices connected wirelessly via PTP links, or spokes, with the host, or the hub. There is a single host controller in the system. The topology is comparable to a star network.
- Ultra‐Wide Band (UWB). A wireless technology based on very low energy and short‐range distance to be utilized in high‐bandwidth communications over a large portion of the radio spectrum. Typical use cases for UWB are short‐distance radar imaging, sensor data collection, precision locating and tracking. UWB was evaluated as a base for PAN networks, and it was present in the IEEE 802.15.3a draft PAN documentation. Nevertheless, the IEEE 802.15.3a task group was dissolved and the development was taken over by the WiMedia Alliance and the USB Implementer Forum. Although technically functional, the un‐ideal progress and techno‐economic suitability have limited the use of UWB in consumer products.
- ZigBee. An IEEE 802.15 standard designed to carry small‐scale data within short distances, and it uses only a low amount of power. Unlike Wi‐Fi, ZigBee represents a mesh networking standard. The nodes of the ZigBee network are thus connected to each other. It provides a fixed data rate of 250 kb/s.
- 6LoWPAN. Combines the IPv6 and low‐power PAN, providing IP‐based wireless transfer for very small and low‐processing powered devices.
- Symphony Link. A wide‐area, low‐power wireless system. End‐users may employ a long‐range radio activity module for the communications with the gateway. It is based on star topology networking, i.e., the end nodes communicate with a single gateway. The gateway manages the stars and interacts with the modules in a flexible way.
- Optical reader technologies for barcodes (variants: 1D, 2D, 3D).
There also are (practically) obsolete legacy systems like Infrared (IR) which could be used to create a link between two devices (e.g., mobile to mobile, or mobile to laptop) for information sharing, including photos, contacts and other contents. The importance of this method has dramatically decreased in recent years, and the modern devices no longer include IR. Nevertheless, the method is still useful for the older devices that support IR. In those cases, the security aspects need to be considered especially in open communications as the traffic may be eavesdropped within the visible line of sight.
Figure 3.7 summarizes the currently most relevant local connectivity technologies that are especially suitable for the IoT environment, and the following sections detail further the principles of the NFC, barcode, RFID and Bluetooth.
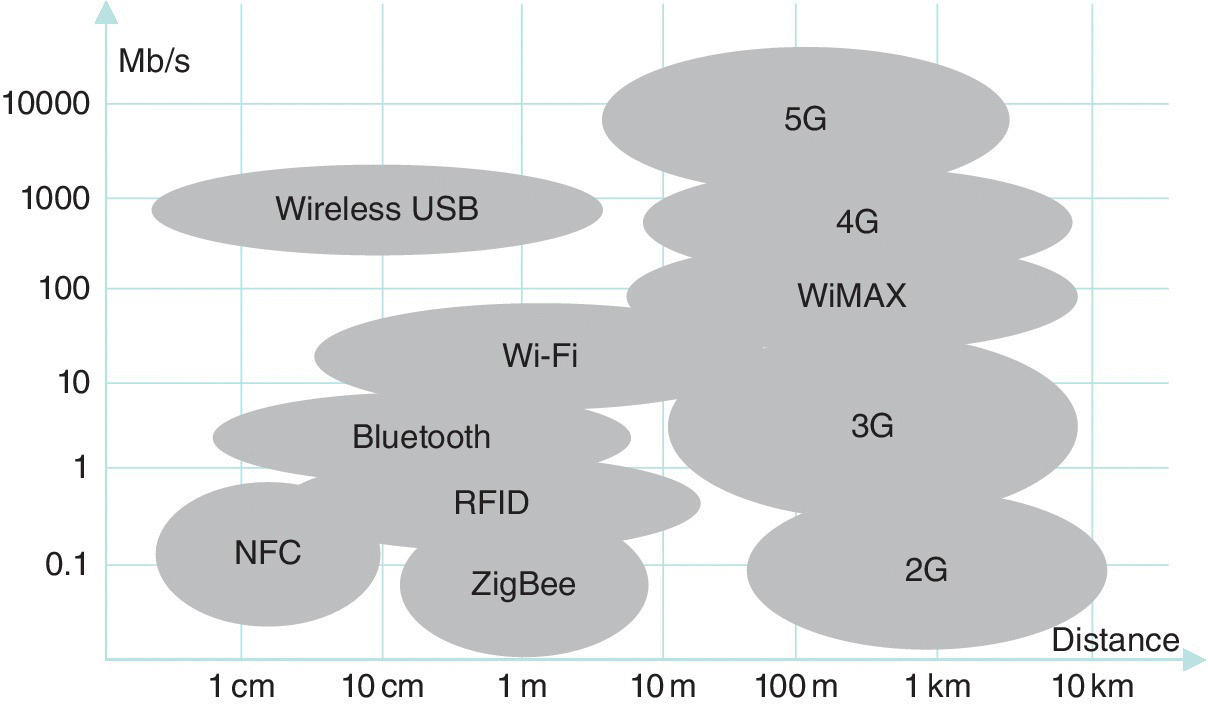
Figure 3.7 High‐level examples of wireless connectivity solutions with respective coverage and data rate
3.2.12.1 Bluetooth
Bluetooth replaces wires between equipment like computers, their peripherals and mobile devices. Bluetooth has low power consumption and a relatively short functional range which depends on the standardized power classes. Bluetooth provides low‐cost transceiver technology for many types of devices like wireless headsets and microphones. As the interface is based on the RF, one of the benefits over older technologies like IR is that no line of sight is required as long as the received power level is high enough. Table 3.2 presents the power classes of Bluetooth [17].
Table 3.2 The theoretical distances of Bluetooth devices per class
| Class | Max power (mW) | Max power (dBm) | Distance (m) |
| 1 | 100 | 20 | 100 |
| 2 | 2.5 | 4 | 10 |
| 3 | 1 | 0 | 5 |
Bluetooth profiles can be defined as general behaviours through which Bluetooth‐enabled devices communicate with other devices. This means that in order to be able to connect the devices together via Bluetooth technology, both must support and understand the common Bluetooth profile in use. The Bluetooth profile describes the possible applications that can be used in the connection, and how Bluetooth is used. As an example of the profile, a File Transfer profile defines how devices should use Bluetooth in order to transfer files between devices, which can be physically, e.g., mobile device and a Personal Digital Assistant (PDA).
In order for the Bluetooth devices to connect with another, both devices must share at least one of the same Bluetooth profiles. An example would be a Bluetooth headset that is utilized via a Bluetooth‐enabled cell phone. Both the headset and the mobile device should have and use the Headset (HS) profile, which basically defines the way to initiate, maintain and release the connection between, e.g., headsets and mobile devices.
Various Bluetooth profiles have been developed. The manufacturer of the Bluetooth device assigns a set of Bluetooth profiles for the device to a certain set of applications that work with other Bluetooth devices. According to the Bluetooth standards, all the Bluetooth profiles should include as a minimum the following set of information: (1) dependencies on other profiles; (2) recommended user interface formats; and (3) particular parts of the Bluetooth protocol stack used by the profile. To perform the planned functions, each profile uses particular options and parameters at each layer of the stack. This may include an outline of the required service record, if applicable. Most Bluetooth devices are given just a few profiles. For example, a Bluetooth headset will use the HS profile, but not the LAN Access profile which defines how devices use Bluetooth technology to connect to local area networks.
Bluetooth pairing can be done via strong but optional pre‐shared key authentication and encryption algorithms. The Bluetooth security depends largely on the length and randomness of the password for pairing Bluetooth devices. This procedure performs mutual authentication when done for the first time, and sets up a link key for later authentication and encryption. anther parameter related to the security is the visibility setting of the Bluetooth device, so it is recommended to make devices visible only when needed. Furthermore, the optional user authorization gives additional protection in the case of incoming linking requests.
The potential security risks of Bluetooth are related to the lack of centralized administration and security enforcement infrastructure. As Ref. [32] has identified, the Bluetooth specification is highly complex and supports more than two dozen voice and data services. The challenge arises from the fact that devices and services supporting Bluetooth are based on a variety of chipsets, devices and operating systems, as well as different user interfaces, security programming interfaces and default settings that are not constantly the same for all. The respective Bluetooth attacks include identity detection, location tracking, DoS, control and access of data and voice channels without permission, to mention just a few. One of the simplest ways for security breaches is based on a weak default password that may be, e.g., ‘0000’. Also, the support for the HS profile that provides telephony signalling commands may open means for misuse of the device via Bluetooth. More information about the Bluetooth security aspects and protection can be found in Ref. [33], and Ref. [34] which detail examples of real‐world Bluetooth attacks such as unauthorized downloading of phone books and call lists, the sending and reading of SMS messages from the attacked phone, and breaches from relatively long distances (more than 100 m).
3.2.12.2 RFID
RFID technology belongs to the Automatic Identification and Data Capture (AIDC) methodology. The AIDC, or Auto‐ID, is in turn a set of methods for identifying objects, collecting object data and entering respective data into computer systems in an automatized way. In addition to the RFID, the AIDC technologies include barcodes, biometrics technologies, magnetic stripes, Optical Character Recognition (OCR), smartcards and voice recognition [21].
RFID is based on wireless data transfer in order to automatically identify and track tags that are attached to objects. The tags identify the respective objects based on electrically stored information. Unlike the case of optically readable barcodes, the RFID reader does not need to be located in Line‐Of‐Sight (LOS) with the tag as the radio waves also propagate through material.
There are a variety of RFID tags available. They can function in standalone environments without an external power source based on the electromagnetic induction of magnetic fields upon reading the tag, while other RFID types harvest electromagnetic energy from the interrogating radio waves in a passive transponder mode. RFID may also be based on its own power source, e.g., a battery, which also provides larger coverage area of the tag compared to the induction‐based passive mode.
RFID tags work on a set of unlicensed frequencies such as 3–8 MHz, 13 MHz, 27 MHz, 433 MHz, 902–928 MHz, 2.4 GHZ and 5.8 GHz. There are also various use cases for the tags. They are useful in tracking objects during the production, storing, logistics and after‐sales market. In addition to goods and products, they are equally useful in identifying living objects such as pets via an embedded RFID chip under the skin, or runners in a sports event with the tag attached to clothes.
Figure 3.8 depicts the RFID system architecture which consists of the RFID tag attached to the object, antenna, reader and host computer which in turn is connected to the application such as Enterprise Resource Planning (ERP).
Figure 3.8 The RFID system architecture
According to Ref. [22], the potential security breaches related to RFID are currently under control, or at an acceptable level. The source indicates that the current data protection provided by the EPCglobal generation 2 protocol represents an advance over previous protocols and is acceptable for still rather limited RFID deployments within the supply chain. While the IP communication between RFID readers and the network is secure due to standard IP network security, the threat in this domain is related to the RF communication between tags and readers which needs to be taken into account in the further development of protocols.
The potential future RFID security threats may include clone tags and unauthorized readers, as well as malicious intentions to intercept reader data via external devices. There is also – although still only a theoretical – possibility to deliver viruses via RFID tags. Ref. [22] thus suggests that the future deployments need updated security and 3G protocols along with the increasing importance of RFID deployments in the consumer domain.
Ref. [23] also discusses RFID security claiming that security breaches can happen at the RFID tag, network or data level. One of the potential issues in adopting sufficiently protective solutions and standards is the very low cost and light functionality of the tags. This means that the functional and improved security tools do not make production of the tags feasible cost wise, and additional encryption within a tag would impact negatively on the tag's processing power. Nevertheless, the industry is considering these issues. The EPCglobal UHF generation 2 protocol is expected to work with ISO 18000‐6C RFID wireless interface specifications. Furthermore, EPCglobal has enlisted security vendor VeriSign Inc. as its infrastructure provider.
Ref. [24] further mentions the DoS attacks. In the case of RFID, a relatively simple radio jammer or signal oscillator set on the RFID tag frequency may interfere with the communications located nearby. The result may be significant in environments such as mobile payment or security applications. The requirements of very close RFID tag proximity to the reader reduces these risks but it would not prevent completely the effects of a powerful jammer located near the reader. Ref. [24] also mentions the possibility to eavesdrop on the communications between reader and tag, and the cloning of RFID devices. Furthermore, strong encryption methods require more memory and more complex chip designs than the typical RFID tags support, which results in weak encryption and thus vulnerabilities for malicious attacks.
3.2.12.3 Barcodes
The barcode is an optical machine‐readable representation of data relating to the object to which it is attached. The original 1D form of barcodes represents data via different widths and spacing of parallel lines. The further development of barcodes has brought 2D formats that contain a variety of optical representations such as rectangles, dots and hexagons. The barcodes can be interpreted optically by using barcode readers as well as with equipment capable of digital imaging such as smart devices with respective barcode scanner apps.
The typical use cases for any form of barcodes include the retail product tagging for the price information, as well as goods tagging in warehouse and logistics supply chains. As is the case with RFID, barcodes also belong to the AIDC. The benefit of the barcode is the simplicity, universal use and low cost. The drawback is the need for LOS.
Barcodes are not considered as subject to important security breaches although it may be possible to embed instructions to the image that some smart devices may execute, such as the displaying of the IMEI. It is not typical that user devices are capable of executing some other, more harmful code based on the barcode, such as initiation of a phone call upon scanning the code. Nevertheless, barcodes can present web links that can be entered automatically by the smart device; it is thus a matter of ensuring protection mechanisms in the device side to prevent the browser establishing connections to malicious web pages.
3.2.12.4 NFC
NFC is a short‐range wireless communication technology which enables the exchange of data between devices like hand‐held mobile phones and readers such as Point of Sales (POS) equipment of retail stores. The communications of the NFC is based on the high‐frequency radio interface that provides functional connections within a maximum distance of about 10 cm between the NFC‐enabled devices. For payment solutions, there may be separate certification processes that dictate different requirements for the useful distance. NFC is a subset of the RFID domain, and is based on a proximity range frequency of 13.56 MHz. This frequency range is dominated by the ISO‐14443A, ISO‐14443B, FeliCa and ISO‐15693 tag standards.
It should be noted that ISO‐14443A, ISO‐14443B and ISO‐15693 do not define security architecture. The ECMA‐340 standard is meant for information exchange between devices that have more capabilities than merely simple memory storage. It is based on the stack utilized in the ISO‐14443A standard, but it allows more functionality in addition to the reading and writing memory. Nevertheless, it does not contain security architecture so the protection needs to be ensured, e.g., in the application level.
3.3 Development of IoT
The following sections summarize some of the key concepts in the IoT domain such as the GSMA Connected Living concept and other industry forum, alliance and standardization initiations.
3.3.1 GSMA Connected Living
The GSMA Connected Living concept is planned to enable IoT, creating an environment in which consumers and businesses can enjoy rich new services, connected by an intelligent and secure mobile network [12]. The focus of the Connected Living programme is to ease the task of mobile network operators in adding value to the services as well as to accelerate the delivery of connected devices and respective services in the M2M market. The ways of work of this programme are based on industry collaboration, regulation, network optimization and development of key enablers to support the growth of M2M in the near future and longer term. The programme takes into account the safe communications of the IoT devices and applications via the mobile network.
As the number of IoT devices is predicted to grow considerably, one of the most essential tasks of the MNOs is to plan and optimize the networks accordingly in order to support thousands of simultaneously communicating devices. For that reason, GSMA is developing guidelines for efficient, trusted and reliable IoT services – not only the operators and service providers but also the app developers are in a key position to create such solutions that do not waste the valuable capacity of the networks. One example of such dangers is the heart‐beat signalling to keep the PDP context alive even if there are no actual communications; this does not cause too much harm in cells with low amounts of devices, but as the numbers of equipment increase there could be potentially hundreds or thousands of such devices fighting for the signalling resources – and those highly loaded signalling areas would not be able to serve all the devices without app‐level optimization. With the help of the Connected Living guidelines, the IoT device and application developers are able to ensure a common approach and fair utilization of the precious resources in such a way that they can scale as the IoT market grows.
In practice, GSMA cooperates with IoT ecosystem partners in the creation of the guidelines that describe how the IoT equipment can communicate within mobile networks efficiently. This approach is elemental as there are hardly better ways to guarantee the fluent functioning of the connectivity of huge amount of IoT devices in a scalable network, so the commonly created rules by the stakeholders ensures a fair share of the efficient connectivity.
3.3.2 The GlobalPlatform
The GlobalPlatform discusses the current development and potential next steps of IoT in Ref. [2], arguing that the ongoing IoT environment is still relatively young which means that existing proprietary solutions will suffice for current use cases. Nevertheless, along with the growth of the number of IoT devices in the market, the level of security and privacy concerns increase also increase. The GlobalPlatform has noted that this is an important threat to general public and critical infrastructures.
Thus, the GlobalPlatform has reasoned that open standards are essential for ensuring interoperability between connected devices in such a way that along with the development of IoT devices the respective security level they offer is sufficiently high. One of the important tasks of the GlobalPlatform is thus to enhance the respective specifications and engage industry participants to guarantee that the needs of the IoT market are met [1].
As a concrete step, the GlobalPlatform has an IoT Task Force which is open to its members and which facilitates the discussion of forthcoming business requirements for network‐capable objects. It also aims to identify ways for progressing GlobalPlatform technology. In addition, it collects feedback from the industry for contributing efficiently to the IoT market.
3.3.3 Other Industry Forums
There are many IoT‐related organizations and industry forums that are actively seeking solutions for the overall functionality, performance and security of always‐connected devices. One of these setups is the IoT Forum, which is considering the future of IoT networks [25]. The IoT Forum recognizes that the GSMA is working to establish common capabilities among mobile operators to enable a network that supports value creation for all stakeholders, including security, billing and charging and device management. The IoT Forum recognizes that all these items can enhance IoT by enabling the development of new services, and that through the provision of the respective value added services, mobile network operators can – in addition to providing cellular connectivity – act as a trusted partner for the end‐users. The IoT Forum notes that the operator capabilities need to be tailored for the emergent M2M business model, building a trusted infrastructure that all stakeholders can rely on and profit from.
Some of the concrete means for making this happen is the remote M2M provisioning, and the related GSMA Embedded SIM Specification, which is meant to accelerate growth and operational efficiency for the M2M environment. The GSMA’s embedded SIM delivers a technical specification to enable the remote provisioning and management of embedded SIMs to allow the Over‐the‐Air (OTA) provisioning of an initial operator subscription and the subsequent change of subscription from one operator to another.
The IoT Forum also considers IoT business enablers for M2M services. The Forum reckons that the growing IoT provides socio‐economic benefits, but there is a big need to develop devices, applications and services in such a way that consumers can trust their data is secure. The GSMA supports a constructive policy and regulatory framework that can unlock the benefits of M2M services for consumers and businesses, building confidence and network capability. The GSMA thus advocates a sustainable M2M environment that will enable operators to unlock the consumer and business benefits of new and profitable services.
3.4 Technical Description of IoT
3.4.1 General
IoT is involved with secure execution of code as well as secure transport of confidential data between devices and systems, including keys. There are several ways to handle these procedures, based on current and future solutions. The IoT device may need to store the data confidentially which can be done, e.g., with HW‐based SE or TEE. As the GlobalPlatform defines, SE can be a removable or non‐removable semiconductor device with form factors such as a smartcard, SIM/UICC and an embedded, permanently installed secure device. The role of the SE is to host sensitive data and applications securely for service providers, application providers and other relevant stakeholders.
The idea of the SE is to provide a data storage and means for sharing among only the allowed parties and it functions as a logical base for remote and post‐issuance secure management such as subscription data. The management of the SE can happen directly by the respective parties or via third‐party solutions such as a TSM in order to provide remote updates within the SE. Figure 3.9 depicts the principle of the TSM.
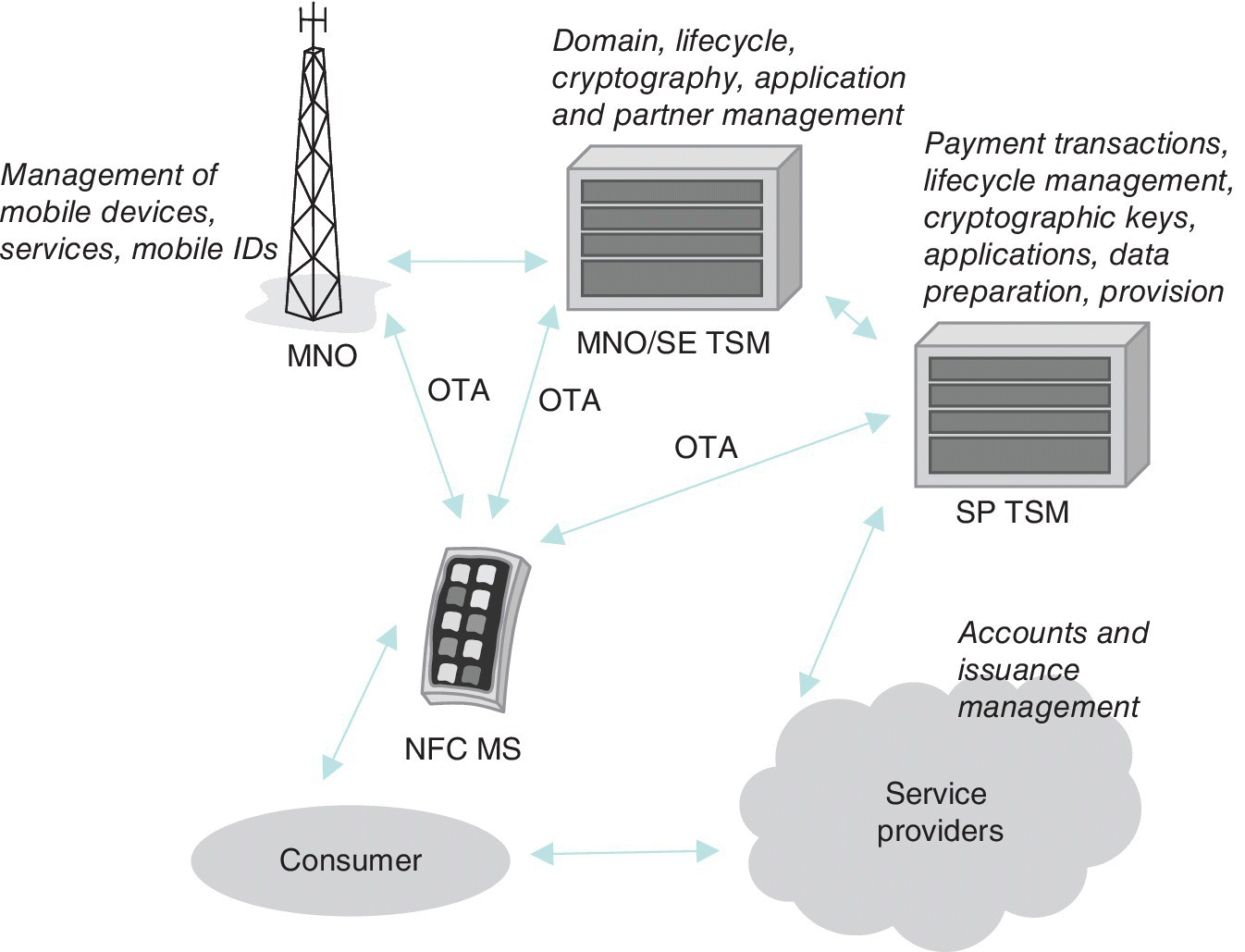
Figure 3.9 The principle of the TSM
The GlobalPlatform defines an SD which is basically a dedicated area within the SE reserved for a certain stakeholder in such a way that others have no visibility to the contents outside of their own SD. Figure 3.10 depicts the principle of the SD.
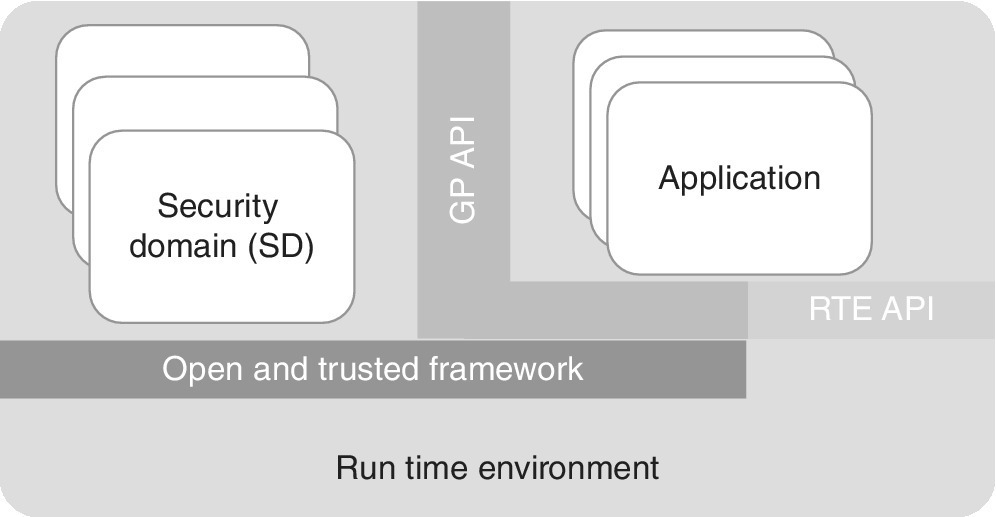
Figure 3.10 The principle of the SD
The same physical card can contain several SDs, and they can be used, e.g., for issuers, CAs and secure application providers. The SD is in practice an application on the SE that can be used to store credentials and as a base for managing securely the SE contents via secure channels and Application Protocol Data Units (APDUs). As there may be multiple stakeholders, each reserving their own SD (also called ‘tenants’), the SDs can be organized in a form of a hierarchical structure by varying the privileges independently from each other. The actual management may happen via all the supported bearers like SMS although the most cost‐efficient communications are done over IP connectivity, e.g., via HTTP. The applications within each SD have own Application ID (AID), and they can be individually installed, provisioned and deleted via the TSM.
The TSM is one way of managing the SDs. It is a trusted broker establishing business agreements and technical relationships for the stakeholders such as MNOs, OEMs and such as payment institutions for mobile wallet utilization in the consumer domain, or utility meter reading in the M2M environment. The TSM can be used to manage the card for uploading, installing, updating and deleting data and other remote procedures in both consumer and IoT environments.
One of the important components in this environment is the CA. Its role is to facilitate SE post‐issuance procedure for new stakeholders by maintaining the confidentiality. More concretely, the CA can create keys for the new SDs on behalf of other parties in such a way that the SE owner does not have visibility to the contents of the service.
In addition to the SE, the confidentiality of the data within the device, such as a smart device or IoT device, can be handled by the TEE which refers to the secured part of the main processor itself. It can thus be utilized without a separate SE based on, e.g., SIM/UICC although nothing prevents the joint utilization of it with the TEE. The TEE provides area for trusted app execution by ensuring protection, confidentiality, integrity and access rights. One example of the benefits of TEE is the protection of the display and PIN code entries so that they cannot be recorded via malicious SW.
3.4.2 Secure Communication Channels and Interfaces
The secure channels are essential to transport data between entities such as SIM/UICC and respective servers. As an example, GSMA defines the Secure Channel Protocol (SCP) suite that contains, e.g., SCP03, SCP80 and SCP81. These are discussed in more detail in section 4.11.1 along with descriptions of current (e)UICC Subscription Management solutions.
3.4.3 Provisioning and Key Derivation
The base for the consumer and IoT device and application initialization is to establish cryptographic keys for the device and the service the device is using. The initial settings can be included in the manufacturing process, but the challenge arises from the dynamic nature of the modern subscription data; the data might change, new data could appear and old data might need to be removed during the lifetime of the device, so the remote subscription management definitely eases the updating of such devices especially if the respective SE is embedded into the device. Also, it might be challenging to even know about the initial services and operators involved with the device such as automotive IoT products that may end up in different countries along with the cars they have been embedded into. As an example, the GlobalPlatform enables trusted SE issuers to perform preliminary provisioning of the credentials into the IoT devices yet maintain the confidentiality between the stakeholders.
The key derivation is needed to establish secure communication channels between the consumer and IoT devices, and respective services. The procedure includes authentication, authorization and encrypted communications. The keys can be divided between a long‐lasting ‘master key’ and short‐term ‘session key’. The master key needs to be securely stored, e.g., into a tamper‐resistant SE to provide highest protection, and the varying short‐term key can be derived from it for each session. The maximum security can be furthermore ensured by dedicating a separate master key independently for each stakeholder, e.g., in the case of multiple ‘tenants renting’ SDs.
3.4.4 Use Cases
This section describes some typical or expected examples of the IoT environment.
3.4.4.1 Telemetry
Telemetry is one of the most logical environments for IoT devices such as intelligent sensors which are able to collect data autonomously from the field, pre‐process the results and forward the data to the IoT systems. As the telemetry is utilized increasingly by industry as well as in the everyday M2M environment (such as controlling thermostats and basing billing to the telemetry data received from electricity consumption), so the respective security is becoming increasingly important. The security relates to the privacy of the consumer and system data as well as to the protection of fraudulent intentions to alter billing data.
3.4.4.2 Connected Security Systems
According to Ref. [26], connected security systems typically rely on sensors to monitor events such as opening doors or windows or movement within the monitored location. Also, automatization systems may include elements at home that can be controlled remotely, e.g., via smartphones for locking and unlocking doors, switching on and off the lights and audio systems etc. These systems may rely largely on the cellular network connectivity between the home security system and controlling smartphone with respective control app. These type of security systems are able to inform the user about the event, such as a text message telling parents that children have returned home. More complete systems may include video surveillance cameras installed at the user’s property.
3.4.4.3 Automotive
According to Ref. [28], the GlobalPlatform has identified the automotive industry as being one of the most important areas moving towards SW‐based control, giving increasing authority to computer‐based systems. There can be a multitude of supported systems such as maintenance, location and entertainment services with respective means for SW updates. At the same time, the connectivity of the automotive systems is taking form between each other and external entities so that there could be various connectivity solutions activated at the same moment. This trend may also open unknown security holes for potential malicious attacks. There are solutions tailored for the vehicular environment such as Vehicle‐to‐Vehicle (V2V) and Vehicle‐to‐Infrastructure (V2I), together denoted as V2X which employs public key cryptography to authenticate OTA messages. V2X is defined in the USA via IEEE 1609 standards set and ETSI ITS G5 defines it in Europe. The standardization bodies have selected Elliptic Curve Cryptography (ECC) as a basis for the solution, the benefit being the small size of signatures and keys. The signatures are based on the Elliptic Curve Digital Signature Algorithm (ECDSA) by applying 224‐bit or 256‐bit key length. Furthermore, the vehicles are equipped with private and public key pairs that are changed frequently for added protection level. The public keys are distributed by certificates that are based on Certificate Authority (CA) [36].
The GlobalPlatform presents a practical use case in Ref. [28] involving a car manufacturer, Secure Element Issuer (SEI), several Application Providers (APs) and IoT Device Manufacturer (DM). In this scenario, the DM integrates the SE and/or TEE into the device. The DM may make SE patches originated from the Secure Element Supplier (SES) and integrates the SE into the Onboard Unit (OBU) of the car. The OBU may have applications and provide connectivity for several services like location‐based services and maintenance service.
Now, the owner of the vehicle (IoT Service Subscriber, SS) may be subscribed into several application services such as remote diagnostics and location‐based service. It also might be that the user does not want these application providers AP‐1, AP‐2, …, AP‐n tpo know about the data transferred between the user and any of the other APs, or the user might want only a limited set of the APs to have visibility to all the data.
Ref. [28] details that in this case, each AP may ask the TSM previously selected by the car manufacturer to install its application in the OBU. The SE issuer and car owner in turn authorize the action, with the SD of the CA, and optionally the CA, assisting in setting up the confidential keys.
3.4.4.4 E‐health
Ref. [28] presents a use case for e‐health which contains a sensor gateway with an integrated SE. The healthcare system provider procures medical sensors and gateways to be integrated into Remote Patient Monitoring (RPM) equipment. The medical sensors can communicate with the RPM gateway by establishing the connectivity and security parameters. The RPM equipment is sold or rented to healthcare providers (AP). Finally, the medical personnel of the healthcare provider gives the RPM equipment to a patient to be utilized at home. To set up the equipment, the AP contacts the TSM selected by the SE issuer for the installation of the new SD on the gateway on behalf of the AP. The SD of the CA, and optionally the CA, takes part in establishing the AP’s secret keys in the SD. The AP can now provision the needed parameters like IP address and public key by using the secure channel. The connectivity from the patient’s side can be based on a cellular network which makes the MNO a logical option to serve as the Network Provider (NP). As the AP takes care of the connectivity expenses, it is a logical option to be a Network Subscriber (NS). In this case, either party or even a third party can act as a Service Provider (SP) while the patient is an SS. Please note that because the patient does not own the RPM equipment, the patient by default is unable to change the SP. Nevertheless, the patient may own other types of e‐health IoT equipment such as a blood pressure measurement device via other SPs.
3.4.4.5 Utilities
The utilities have an increasingly important contributing role in the IoT environment, being one of the first types of M2M machines in realistic field deployments [29]. The utilities are also developing along with modernized technologies, such as smart grids. The utilities may rely on various types of wireless technologies although the most logical connectivity for these equipment is based on cellular radio technologies. As the amount of transmitted and control data is typically very low and the requirements for the real‐time transfer are not too strict, even the most basic cellular technologies such as GSM SMS or packet data are useful for this environment. In fact, as the 2G networks are well established with relatively large radio coverage areas, and there is such a large amount of utilities such as power meter readers connected in the 2G network, it may be one of the most relevant reasons for not ramping down the 2G networks straightaway, even if the 3G and 4G networks are more spectral efficient. The role in the electric domain, including generation, transmission and distribution is also increasingly relying on the IoT solutions for better understanding the local near real‐time power consumption.
The Smart Grid (SG) is one of the big raising items in the energy domain. The SG merges the EPS with energy and information technology, end‐user applications and loads as defined in IEEE standard 2030‐2011. Figure 3.11 depicts the respective graphical representation of IEEE while the NIST presents the SG via a higher level conceptual model. There are also other intentions to describe the SG as for the smart infrastructure, smart management and smart protection system [30].
Figure 3.11 SG model as interpreted from the IEEE 2030‐2011
As can be seen in Figure 3.11, the area types for the IEEE SG include the Home Area Network (HAN), Business/Building Area Network (BAN) and Industrial Area Network (IAN). The communications methods of SG include cellular networks (GPRS, 3G, LTE and 4G), Wi‐Fi (IEEE 802.11), fixed Ethernet, WiMAX (IEEE 802.16), fibre optics, xDSL, PLC, WSN/WPAN (IEEE 802.15.4), ZigBee and DASH7. In Figure 3.11, the terminology is the following: NAM refers to the Neighborhood Area Network, AMI to Advanced Metering Infrastructure, EAN to Extended Area Network, FAN to Field Area Network, HAN to Home Area Network.
As the importance of the SG is increasing, and the power systems are highly strategic, the related security vulnerabilities need to be minimized. It is not hard to imagine the magnitude of damage a security breach may cause if the connectivity exposes security holes for, say, switching off the power system of a complete city even for a short time period.
The GlobalPlatform presents a use case for the utilities in Ref. [28]. The GlobalPlatform scenario is about a smart meter manufacturer (Device Manufacturer, DM) which produces smart meters with an integrated SE. The SE is provided by an SE supplier. An energy provider (which in this case acts as an SEI and SP) obtains and installs the smart meter in a house while an energy distribution network provider or grid operator company (acting as an AP) requests its TSM to install on the device an application providing measures and management of the line quality. In order to protect this information the cryptographic keys are already installed during the deployment. Another AP (local energy provider) typically bills the consumer for energy usage and will load its own application on the meter to monitor energy usage.
In addition, the house owner or tenant (in a role of SS) may be able to select an energy supplier which differs from the grid company so the user may have the opportunity to optimize energy costs depending on living styles that best map with the selected SS. Now, these various suppliers involved may need different information for calculating the rate, and involved energy distribution network operators may want to monitor different parameters to optimize their grid management.
The use case of Ref. [28] is related to the event of the homeowner changing energy supplier. The new service provider needs to contact the TSM associated with the utility grid company to be able to replace the old supplier’s rate information in the smart meter, as well as the secret keys used for protecting the transmitted records. Understandably, the keys should be maintained confidential from the competition. The SD of the CA, and optionally the CA itself, is thus involved. In one scenario, the grid company can become the NP by using power line communications for backhaul while the new energy supplier may be the network subscriber paying the grid company for its connectivity costs. In alternative scenario, where the smart meter supports cellular connectivity, an MNO may act as NP which means that the grid operator would be a logical NS and charge the energy supplier for its connectivity costs. Finally, in the third scenario, the homeowner (being in the service subscriber role) could also have their own application activated in the device for measuring energy consumption which means that the homeowner would be another AP.
References
- [1] GlobalPlatform, IoT. http://www.globalplatform.org/medguideiot.asp (accessed 24 January 2015).
- [2] GlobalPlatform, Leveraging GlobalPlatform to improve security and privacy in the Internet of Things. Whitepaper, May 2014.
- [3] B. Meynert. The Internet of Things. 24 December 2012. http://www.sagevita.com/business/the‐internet‐of‐things/ (accessed 26 July 2015).
- [4] T. Tuttle, Silicon Labs. The Internet of Things: The Next Wave of Our Connected World. Embedded Systems Conference ’15. http://www.embedded.com/design/connectivity/4430102/The‐Internet‐of‐Things–the‐next‐wave‐of‐our‐connected‐world (accessed 26 July 2015).
- [5] A brief history of Internet of Things. http://postscapes.com/internet‐of‐things‐history (accessed 26 July 2015).
- [6] Technopedia. Definition of Internet of Things. 2015. http://www.techopedia.com/definition/28247/internet‐of‐things‐iot (accessed 27 July 2015).
- [7] A. Greenberg. Hackers remotely kill a jeep on the highway – with me in it. 21 July 2015. http://www.wired.com/2015/07/hackers‐remotely‐kill‐jeep‐highway/ (accessed 27 July 2015).
- [8] C. Thompson. 14‐year‐old hacked a car with $15 worth of parts. 19 February 2015 http://www.cnbc.com/2015/02/19/14‐year‐old‐hacked‐a‐car‐with‐15‐worth‐of‐parts.html (accessed 27 July 2015).
- [9] Newsweek . Meet Kevin Ashton, Father of the Internet of Things, 23 February 2015. http://www.newsweek.com/2015/03/06/meet‐kevin‐ashton‐father‐internet‐things‐308763.html (accessed 7 November 2015).
- [10] Cloud networks. http://www.networkworld.com/news/2008/111208‐private‐cloud‐networks.html (accessed 9 September 2012).
- [11] Wired . The Internet of Things is wildly insecure – and often unpatchable, 1 June 2014. http://www.wired.com/2014/01/theres‐no‐good‐way‐to‐patch‐the‐internet‐of‐things‐and‐thats‐a‐huge‐problem/ (accessed 15 November 2015).
- [12] GSMA Connected Living. http://www.gsma.com/connectedliving/ (accessed 15 November 2015).
- [13] T. Tuttle. Internet of Things: The next wave in computing. eMedia, 2014.
- [14] G. Reiter. Wireless connectivity for the Internet of Things. Texas Instruments, 2014.
- [15] D. Bjorklund, J. Rautio and J. Penttinen. NMTImage. DMR (Digital Mobile Radio) Conference, Stockholm, Sweden, June 1994.
- [16] ITU statistics, end‐2015 estimates for key ICT indicators, 16 November 2015. http://www.itu.int/en/ITU‐D/Statistics/Pages/facts/default.aspx (accessed 16 November 2015).
- [17] J. Penttinen. The Telecommunications Handbook. John Wiley & Sons, Inc., Hoboken, NJ, 2015.
- [18] M. Marjapuro. 7 reasons why IoT device hacks keep happening, 2 November 2015. https://iot.f‐secure.com/2015/11/02/7‐reasons‐why‐iot‐device‐hacks‐keep‐happening/ (accessed 22 November 2015).
- [19] The Internet of Things will drive wireless connected devices to 40.9 billion in 2020. 20 August 2014. https://www.abiresearch.com/press/the‐internet‐of‐things‐will‐drive‐wireless‐connect/ (accessed 22 November 2015).
- [20] B. Dickson. Why IoT security is so critical, 24 October 2015. http://techcrunch.com/2015/10/24/why‐iot‐security‐is‐so‐critical/#.i8ddwze:sh4q (accessed 22 November 2015).
- [21] The GS1. Fundamental concepts of AIDC and RFID. http://www.gs1us.org/DesktopModules/Bring2mind/DMX/Download.aspx?command=core_download&entryid=51&language=en‐US&PortalId=0&TabId=785 (accessed 27 November 2015).
- [22] ThingMagic. Security breaches of RFID. http://www.thingmagic.com/index.php/rfid‐security‐issues (accessed 27 November 2015).
- [23] InformationWeek . RFID's security challenge, 11 November 2014. http://www.informationweek.com/rfids‐security‐challenge/d/d‐id/1028389? (accessed 27 November 2015).
- [24] Enterprise Risk Management. RFID; Great benefits also come with a security risk. http://www.emrisk.com/sites/default/files/newsletters/ERMNewsletter_July_2010.pdf (accessed 27 November 2015).
- [25] IoT Forum, 27 November 2015. http://iotforum.org/ (accessed 27 November 2015).
- [26] GSMA. The impact of the Internet of Things; The Connected Home. http://www.gsma.com/newsroom/wp‐content/uploads/15625‐Connected‐Living‐Report.pdf (accessed 27 November 2015).
- [27] GSMA. Understanding the Internet of Things (IoT). July 2014.
- [28] GlobalPlatform. Leveraging GlobalPlatform to improve security and privacy in the Internet‐of‐Things. White paper, May 2014.
- [29] C. Lima. Enabling a smarter grid, September 2010, Silicon Valley. Smart Grid Series, Smart Grid Communications.
- [30] D. Bakken (editor). Smart Grids: Clouds, Communications, Open Source, and Automation.
- [31] The IoT Security Foundation. https://iotsecurityfoundation.org/ (accessed 27 November 2015).
- [32] NSA. Bluetooth security. https://www.nsa.gov/ia/_files/factsheets/i732‐016r‐07.pdf (accessed 27 November 2015).
- [33] Bluetooth security and protection. http://blog.bluetooth.com/bluetooth‐security‐101/ (accessed 27 November 2015).
- [34] Bluetooth attacks. http://www.trifinite.org (accessed 27 November 2015).
- [35] ITU. Regulation and the Internet of Things, 6 November 2015. https://itunews.itu.int/en/6024‐Regulation‐and‐the‐Internet‐of‐Things.note.aspx (accessed 4 January 2016).
- [36] Auto‐talks. V2X Security Portfolio, v. 1.3. White paper, 2016. http://www.uato‐talks.com (accessed 24 May 2016).
