
Chapter 7
Client-Side Virtualization
CERTIFICATION OBJECTIVES
![]() 1101: 4.1 Summarize cloud-computing concepts
1101: 4.1 Summarize cloud-computing concepts
![]() 1101: 4.2 Summarize aspects of client-side virtualization
1101: 4.2 Summarize aspects of client-side virtualization
![]() Two-Minute Drill
Two-Minute Drill
Q&A Self Test
IT professionals who support desktop or server systems need to keep up to date on the newest operating systems (OSs) and applications. This can become expensive if they use dedicated computers for testing new software. But many do not. Instead, they use virtualization software to run the desktop or server OSs in a test environment, isolated from their organization’s network. You can too once you learn how to work with the latest technologies in virtualization.
This chapter explains the big picture of virtualization, with examples of the different types. Then it compares server-side virtualization with client-side virtualization and provides more details on client-side virtualization to guide you through the hands-on experience of installing and configuring the software that supports desktop virtualization as an example of client-side virtualization. When you complete this chapter, you will not only understand virtualization conceptually, but you will know how to install and configure a hypervisor and set up a guest operating system.
CERTIFICATION OBJECTIVES
![]() 1101: 4.1 Summarize cloud-computing concepts
1101: 4.1 Summarize cloud-computing concepts
![]() 1101: 4.2 Summarize aspects of client-side virtualization
1101: 4.2 Summarize aspects of client-side virtualization
As you prepare for the CompTIA A+ certification exams, be ready to answer questions about the basics of client-side virtualization, including being able to define a hypervisor and install and use one. You should understand the purpose of virtual machines and be able to describe resource requirements for client-side virtualization, emulators, and networks, as well as the security requirements. In this chapter we go beyond the actual CompTIA A+ exam objectives to give you a broader understanding of client-side virtualization and some hands-on experience with it.
Although this section is not specifically about cloud computing (which is covered in Chapter 18), it does briefly cover one virtualization-related topic included in 1101 exam Objective 4.1: virtual desktop infrastructure (VDI).
Introduction to Virtualization
In this section, we detail the many purposes of virtualization and compare server-side virtualization to client-side virtualization. We will explore the types of client-side virtualization in preparation for the section that follows in which you will implement it.
Purposes of Virtualization
Virtualization is the creation of an environment that seems real but isn’t. Virtualization is everywhere these days, and there are many types.
For example, you can explore a virtual world, such as Second Life or one of many massively multiplayer online games. Each of these virtual worlds contains a simulated environment within which participants create an online community. Within a virtual world a user often selects an avatar, an animated computer-generated human or animal image, to represent him or her. Virtual worlds are used in online training, in marketing of products, and in games because virtual worlds usually allow your avatar to interact with those of other people.
A virtual classroom is an e-learning tool for distance learning, usually provided as a service from an Internet-based source, such as eLecta Live (www.e-lecta.com) or Blackboard (www.blackboard.com). If you have taken online classes, you have probably experienced virtual classrooms used by instructors for presenting interactive lectures and even completion of coursework.
Many organizations use storage virtualization in which client computers can utilize many networked hard drives as though they are one drive or location. Network engineers work with network virtualization in which they create a network address space that exists within one or more physical networks. It is logically independent of the physical network structure, and users on computers accessing this virtual network are not aware of the underlying network. A virtual network can exist over a physical network, or one can be fully virtualized within a host computer.
Then there is server virtualization, in which a single computer hosts one or more server operating systems, each in a virtual machine and each performing tasks independently from the other virtual machines and from the host. Companies that provide low-cost web hosting services can create a separate virtual web server for each customer.
With only a small leap from server virtualization, we come to desktop virtualization. This is virtualization of a desktop computer into which you can install a desktop operating system, its unique configuration, and all the applications and data used by (normally) a single person. Each simulation of a machine is a virtual machine (VM).
Today, desktop operating systems and their installed apps are clients to numerous services on private and public networks. The typical computer user seamlessly connects to a home network, corporate network, or the Internet to access services such as file and print sharing, e-mail, media streaming, social networking, and much more. For that reason, people often refer to desktop operating systems as clients, and it follows that when you create a virtual machine for Windows, it is called Windows client virtualization.

The purpose of a virtual machine is to simulate a real computer environment without requiring separate physical hardware.
Uses for Virtual Machines
IT professionals use virtual machines for a variety of functions, including these:
![]() Sandboxes When IT professionals make changes to systems, such as introducing new hardware or rolling out patches and updates to software, they need to test it in a no-risk environment where any problems that occur will not affect production systems. This is known as a sandbox environment. A virtual machine makes an ideal sandbox because it is isolated from other systems.
Sandboxes When IT professionals make changes to systems, such as introducing new hardware or rolling out patches and updates to software, they need to test it in a no-risk environment where any problems that occur will not affect production systems. This is known as a sandbox environment. A virtual machine makes an ideal sandbox because it is isolated from other systems.
![]() Test development Developers use virtual machines to test new software as they are creating it, checking out how it works in a variety of simulated hardware environments. This is a tremendous time and cost saver because developers do not need to actually own all the different hardware configurations they wish to test on.
Test development Developers use virtual machines to test new software as they are creating it, checking out how it works in a variety of simulated hardware environments. This is a tremendous time and cost saver because developers do not need to actually own all the different hardware configurations they wish to test on.
![]() Application virtualization IT professionals can virtualize applications, making them available to end users via virtual machines rather than directly installing them on user hardware. This has two main use cases:
Application virtualization IT professionals can virtualize applications, making them available to end users via virtual machines rather than directly installing them on user hardware. This has two main use cases:
![]() Legacy software/OS If an application is old (that is, legacy), it may have been written for older hardware or an older OS version. A virtual machine enables that application to run on the hardware and software platform it was written for.
Legacy software/OS If an application is old (that is, legacy), it may have been written for older hardware or an older OS version. A virtual machine enables that application to run on the hardware and software platform it was written for.
![]() Cross-platform virtualization If a certain application needs to be available to users who have different systems (such as macOS, Windows, Linux, and so on), a virtual machine can make a single version of that application available to everyone, regardless of their OS or hardware.
Cross-platform virtualization If a certain application needs to be available to users who have different systems (such as macOS, Windows, Linux, and so on), a virtual machine can make a single version of that application available to everyone, regardless of their OS or hardware.

1101 exam Objective 4.2 specifically mentions the three functions described here: sandboxes, test development, and application virtualization (and the use cases of legacy software/OS and cross-platform virtualization). Make sure you understand how each of those use cases is enabled by virtual machines.
Server-Side Virtualization vs. Client-Side Virtualization
A client is software that connects over a network to related server software. The term “client” can also refer to the operating system or to the computer hardware supporting the client software. Therefore, client-side virtualization is any virtualization that happens on the client side of a client-server relationship. When you install software that allows you to run different operating systems on a single PC in a virtual environment, that’s client-side virtualization.
You can host one or more virtual machines on your PC if it meets the requirements for both the hypervisor and for each guest OS. Common examples of client-side virtualization of desktop environments include hypervisors that allow you to run Windows, Linux, Unix, and even DOS guest OSs in virtual machines on Windows, Linux, Unix, or macOS host OSs. For example, Figure 7-1 shows a Windows 11 desktop with a window open to a virtual machine that is running Ubuntu Linux. The hypervisor in this case is Oracle VM VirtualBox, a free and very capable hypervisor.
FIGURE 7-1
Ubuntu Linux running in a virtual machine on a Windows 11 PC

Virtual environments can also be hosted on specialized servers that clients connect to via network or Internet connections. This is server-side virtualization. For example, Microsoft’s Windows 365 Cloud PC is a virtual version of Windows that displays on the user’s screen as if the operating system were local. The value of this approach is that the local computer can be an older, less powerful computer because it only needs to run software to connect to the server, transfer video downstream to the thin client, and send mouse clicks and keystrokes upstream to the app on the server. It isn’t doing the heavy lifting of processing; the server does that. This hosting of desktop environments and applications on servers centralizes all support tasks, simplifying the upgrading and patching of the operating system and applications in the virtual machines within the server or servers. This same centralization also gives IT more control over the security of the desktop.

The term used today for hosting and managing multiple virtual desktops (often thousands) over a network is virtual desktop infrastructure (VDI). The term is attributed to VMware in distinguishing its virtual desktop server products from the products offered by competitors, specifically Citrix and Microsoft. Today VDI applies to any server product that provides full virtual desktop support. 1101 exam Objective 4.1 mentions VDI, both on-premises and in the cloud.
Types of Client-Side Virtualization
While we will use desktop virtualization in our working examples, client-side virtualization is not just about desktops. In recent webcasts from Microsoft, they featured three types of client-side virtualization: desktop virtualization, application virtualization, and presentation virtualization. We have already defined desktop virtualization and will soon move into more details about that type. Here we will describe presentation virtualization and application virtualization.
In presentation virtualization, a user connects to a server from their desktop or laptop and accesses an application rather than an entire desktop environment. The application user interface (window) is “presented” on the user’s desktop as if it were running locally, but it is actually running on the server. This allows the user to use an application that is incompatible with their local operating system or that cannot run on the local computer because the computer hardware is old or underpowered. Microsoft currently uses Windows Server running Remote Desktop Services for presentation virtualization. Notice that this is client-side virtualization, but it physically occurs on the server side and is presented on the client side, as shown in Figure 7-2. Specialized software sends the screens to the client computer and returns all input to the application on the server.
FIGURE 7-2
Presentation virtualization

Another type of client-side virtualization is application virtualization, in which the application runs in a virtualized application environment on the local computer. The application is isolated from the surrounding system, interacting with the hardware (and user) through application virtualization software, a virtual machine with only the support required by the app (see Figure 7-3). This isolation of the application on the desktop computer requires a sufficiently powerful computer, but it has the advantage of being a compatibility solution when older, critical apps will not run on newer hardware or software. Another benefit is that a virtualized app is under IT control because they can install or update it over a network as a complete application without concern for the underlying system beyond the application virtualization software. Microsoft’s current implementation of application virtualization is Microsoft Application Virtualization (App-V).
FIGURE 7-3
Application virtualization

Implementing Client-Side Desktop Virtualization
This section begins by describing hypervisors, the software that supports desktop virtualization. Then it looks at specific hypervisors and their resource and network requirements. Finally, you will find out how to select and install a hypervisor on a desktop computer and create one or more virtual machines in preparation for installing an OS onto that virtual machine.
Hypervisors
To do desktop or server virtualization, you first need a hypervisor. A hypervisor, also called a virtual machine manager (VMM), is the software that creates a virtual machine, providing access to the necessary hardware on the host machine in isolation from other virtual machines and the host operating system, if present. This allows multiple operating systems to run simultaneously on a single physical computer, such as a network server or desktop computer. A hypervisor must create a virtual CPU compatible with that of the underlying machine—mainly either an Intel or an AMD CPU. This means that the installed OS must be capable of installing directly on the underlying computer.
Today’s hypervisors require, or at least work best on, computers with hardware-assisted virtualization (HAV) features, either Intel Virtualization Technology for x86 (Intel VT-x) or AMD Virtualization (AMD-V). HAV supports and improves the performance of virtual machines on the host. Both Intel and AMD CPUs have supported HAV since 2006.
Virtual Machine Management Service, also known as VMMS or vmms.exe, is the main module in the Microsoft Windows operating system that controls all aspects of Hyper-V server virtualization. Hyper-V’s hardware requirements are
![]() 64-bit processor with second-level address translation (SLAT)
64-bit processor with second-level address translation (SLAT)
![]() CPU support for VM Monitor Mode Extension (VT-x on Intel CPUs)
CPU support for VM Monitor Mode Extension (VT-x on Intel CPUs)
![]() 4 GB of RAM (at a minimum; more is better)
4 GB of RAM (at a minimum; more is better)
Having the right hardware is not enough, though; the right settings must also be enabled in the system BIOS/UEFI:
![]() Virtualization technology (the name may vary somewhat depending on the motherboard)
Virtualization technology (the name may vary somewhat depending on the motherboard)
![]() Hardware-enforced data execution prevention (DEP)
Hardware-enforced data execution prevention (DEP)
Virtualization vs. Emulation
You may have heard the term emulation or mention of something called an emulator. At first glance, emulation and virtualization seem synonymous, but in computing, these terms are very different. Emulation differs very much from the virtualization of servers or desktops we discuss here. The key is compatibility. When we use a virtual machine, the hypervisor that creates and manages it must create a virtual machine compatible with the underlying virtual machine, even while isolating the virtual machine from the underlying hardware.

Be sure you understand the resource requirements for virtualization using a hypervisor, including HAV.
An emulator, on the other hand, is software that allows you to run an OS or device on hardware with which it is completely incompatible. This is done to run a critical application designed for an old type of computer system that is no longer available. In fact, in the early days of PCs many organizations used special adapter cards and software on PCs to emulate the old dumb terminals that connected to their large mini- or mainframe computer systems. Now we do this with terminal emulation software, such as the VT Series terminal emulators from Ericom (www.ericom.com) used to emulate physical terminal hardware systems by DEC, Compaq, and Hewlett-Packard. Vendors such as Ericom offer versions of their terminal emulation software that will run on Windows, macOS, or Linux operating systems. Today developers wanting to write apps for phones running the Android OS can use software that will emulate the underlying CPU and other hardware of an Android phone and run an Android OS—all on their desktop computer.
There are two types of hypervisors: Type I and Type II, as Figure 7-4 shows. A Type I hypervisor—sometimes called a bare-metal hypervisor—can run directly on a computer without an underlying host operating system and then manage one or more virtual machines. A Type II hypervisor requires a host operating system, such as Windows, macOS, or Linux. The Type II hypervisor runs as an app in that host operating system, putting more software layers between each virtual machine and the hardware.
FIGURE 7-4
Comparison of Type I and Type II hypervisors

Type I hypervisors first appeared on high-powered servers running server OSs in virtual machines. Examples of current Type I server hypervisors include VMware ESXI and Citrix XenServer. Type I hypervisors are very appealing because, when compared to an equivalent Type II hypervisor, a Type I hypervisor has a smaller layer of software between each guest OS running in a virtual machine and the underlying hardware.
The hypervisors we use in our examples and exercises in this chapter are all Type II hypervisors requiring an underlying operating system, the host OS, which is the operating system installed directly on the computer, and one or more guest OSs, which are the operating systems running within virtual machines.
You have several choices for Type II hypervisors for desktops. The major sources of hypervisors are VMware, Citrix, Parallels, Microsoft, and Oracle. There are many other players in the field, with virtualization topics appearing in the technical press every week. You can install a Type II hypervisor on your Linux, Windows, or macOS desktop and test another operating system without the expense of a separate computer.
Planning a Desktop Virtualization Implementation
To implement desktop virtualization, you must first determine what desktop OS you will use as a guest OS. When it comes to selecting and installing a hypervisor, the general considerations and steps remain the same, whether you are planning server virtualization or desktop virtualization. For our purposes, we will focus on selecting and installing a Type II client hypervisor on a desktop computer for testing Windows and Linux operating systems.
Security for Virtual Machines
We cannot emphasize enough that you must keep your guest OS as secure as the host OS. At a minimum, you should create a strong password for the account used to log in to the guest OS and install security software in your guest OS. Chapters 20 and 21 give the bigger story of computer security, and you can flip forward to those chapters for details. However, there are many excellent free security suites from third parties, and Microsoft Windows comes with the free security tool Windows Defender.

Remember that you must treat a virtual machine as you would a physical machine and take the same security precautions, such as creating a strong password for the account used to log in to the guest OS and installing security software in your guest OS.
Networking Requirements
While it is possible to do desktop virtualization on a computer without an Internet connection, it would be very awkward for several reasons. First, the easiest way to obtain a hypervisor is over the Internet, and updates to the hypervisor, host OS, and guest OS are easily available with an Internet connection. Furthermore, if you create a virtual machine to test an operating system or other software for use in a normal environment, then you certainly should include testing how it works on a network. Therefore, the hypervisors we use simulate a network card within each virtual machine, as well as a network on the host, so that multiple virtual machines can communicate with each other and the underlying host. Then, through a virtual connection to the host computer’s physical network adapter, each VM has access to an external network, and through that to the Internet, if available. Of course, you can turn off these and other features for a VM, if you desire.
Selecting a Guest OS for Desktop Virtualization
The selection of a guest OS for virtualization may be less selection and more necessity. Perhaps you need to learn Linux for a class you are taking, but you do not have a spare computer. Or maybe you would like to look at an older version of Windows without installing it on one of your PCs. Or maybe you just need to select an OS so that you can experiment with desktop virtualization. Whatever the reason, you will need a legal license to install it, just as you do on any computer. If you plan to install Linux, you will find many free versions online, and if you are testing a pre-release version of Windows, simply download it and save it as an ISO file.

Recall that while a network may not be required for a virtual machine, it is essential to have network access to easily update all the software and to create a real-world environment in which a computer is connected to a network.
If you are looking for an OS to install just for learning to work with virtualization, consider using an older version of Windows, if you happen to have an old disc around along with the product key. As you learned in Chapter 4, a product key is a string of alphanumeric characters, usually five groups of five each, printed on the packaging for retail editions of Microsoft software. You must provide this product key either during the installation or within 30 days, or the software will be disabled. This is Microsoft’s protection against piracy. Ubuntu Linux is also a good choice for a guest OS because it is free and easy to obtain. It also has modest system requirements, so it runs well even on older PCs.
Selecting a Host OS for Desktop Virtualization
Deciding on the host OS and a host computer for desktop virtualization seems like the chicken and egg situation—which comes first? Well, it depends on what is available to you. However, since the CompTIA A+ exams focus mainly on the Windows OS, we will use the Windows OS as our host OS in the following exercises. But if you have a Linux or macOS system, there are hypervisors for them too.
Selecting a Host Computer for Desktop Virtualization
If possible, select a PC that supports HAV as the host computer. Not all hypervisors require it, but most will take advantage of the feature if it’s available. Without HAV, some hypervisors will limit you to 32-bit installations of some operating systems.
How can you discover if your computer supports HAV? One of the BIOS/UEFI settings on a computer with HAV support will be virtualization and the ability to enable or disable it. If you are uncertain, skip ahead to Chapter 8’s Exercise 8-5, “Viewing the Firmware Settings,” to learn how to enter BIOS/UEFI settings and make sure virtualization is present and enabled.
Selecting a Type II Client Hypervisor
You have several options—both commercial and free—for running Linux or Windows on a Windows desktop computer. At this writing, you cannot run any version of macOS in a virtual machine on a PC, due more to licensing issues than technical issues. (Okay, technically there are ways to do it, but they require acquiring disk images illegally and then hacking them. The Internet will explain it.)
Of the non-Microsoft hypervisors, we selected Oracle VirtualBox to cover in this chapter. It’s free, well designed, and mostly hassle free, and versions are available for Windows (all versions and editions), Linux, and macOS.
Hyper-V Manager is a hypervisor application that comes with the 64-bit Pro and Enterprise versions of Windows 8 and later. It’s got some quirks and can be difficult to set up; frankly, we prefer VirtualBox and you probably will too, but it’s good to have options. Hyper-V is available only in Pro and Enterprise versions of Windows.
There are other free hypervisors, most notably VMware Player, which doesn’t have a version for macOS. The free VMware Player also has fewer features than the industry-leading hypervisor, VMware Workstation (the retail product), which also does not come in a version for macOS hosting. The entire suite of VMware products is very popular in large organizations, so you may want to download and install VMware Player on your own to become familiar with the VMware virtualization look and feel. All these hypervisors are downloadable from the Internet and they all work in a similar way, so working with one will teach you the basics of working with desktop virtualization.
This chapter would not be complete without some mention of Parallels Desktop for Mac, a very popular hypervisor for macOS hosts. It does not come in a free version, only a 14-day trial, which you may want to download from their website (www.parallels.com). While Parallels has versions for Windows and Linux hosts, their main efforts go to their product for macOS hosts, and the other versions are not kept as up to date. Therefore, since we work on both Windows and macOS hosts, we prefer to use Oracle VirtualBox on both platforms.
Installing and Configuring Oracle VirtualBox
Oracle VirtualBox will run on a variety of host operating systems, including Windows, Linux, and macOS. It is free, open-source software under the terms of the GNU General Public License (GPL) version 2. It will also run on hardware that does not support virtualization, but we strongly recommend you use a system with HAV when possible for the best performance.
The minimum requirements for VirtualBox include the following:
![]() CPU Any recent Intel or AMD CPU, but the more powerful the better. Streaming SIMD Extensions 2 (SSE2) support is required. Software-based virtualization is no longer supported as of version 6.1, so if you don’t have HAV, you will need to download version 6.0 or earlier.
CPU Any recent Intel or AMD CPU, but the more powerful the better. Streaming SIMD Extensions 2 (SSE2) support is required. Software-based virtualization is no longer supported as of version 6.1, so if you don’t have HAV, you will need to download version 6.0 or earlier.
![]() Disk space At least 25 GB free space recommended.
Disk space At least 25 GB free space recommended.
![]() Memory At least 4 GB of RAM recommended.
Memory At least 4 GB of RAM recommended.
![]() Host OS Windows, Linux, Solaris, or macOS.
Host OS Windows, Linux, Solaris, or macOS.
![]() Guest OS Versions of Windows, Linux, Solaris, Open Solaris, OS/2, Open BSD, or DOS.
Guest OS Versions of Windows, Linux, Solaris, Open Solaris, OS/2, Open BSD, or DOS.
Learn more about VirtualBox at the VirtualBox website (www.virtualbox.org), where you will find the online user manual and a link to download the software.
Downloading VirtualBox
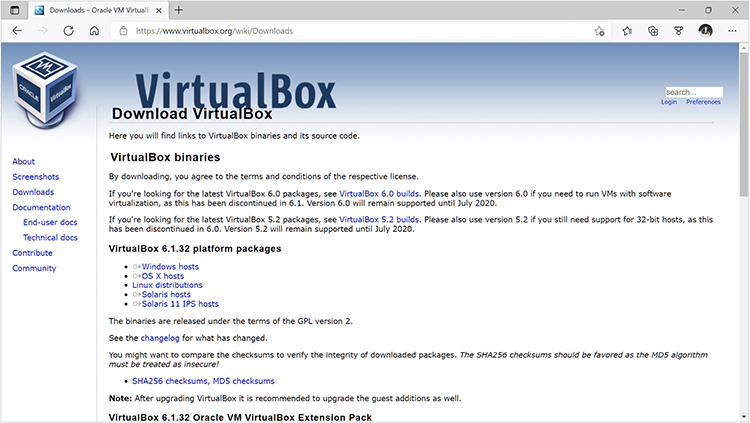
To complete Exercise 7-1, you will need to download VirtualBox. To do that, click the Downloads link on the home page. On the Download VirtualBox page, shown in Figure 7-5, locate the version for the host OS you plan to use and select it for download. In our case, we clicked the link for VirtualBox for Windows hosts. Once it completes downloading, you are ready to install it on your system. The screens and steps will vary depending on the version of VirtualBox and the host OS you use. For instance, the file downloaded to a macOS host (described on the VirtualBox download page as simply “OS X hosts”) will have a .dmg extension.
FIGURE 7-5
Select the correct download for your host OS.
Setting Up VirtualBox
Using the file you downloaded, run the VirtualBox installation wizard to install it on your Windows computer. To complete Exercise 7-1, you will need a system that meets the hardware and host OS requirements listed earlier. In addition, you will need the following:
![]() The user name and password of an administrator account for this computer
The user name and password of an administrator account for this computer
![]() A broadband Internet connection
A broadband Internet connection
After you install VirtualBox, you will need to create at least one VM in it, covered in Exercise 7-2.
EXERCISE 7-1
Installing Oracle VirtualBox
Follow these steps to install VirtualBox:
1. Locate and double-click the installation program. Your version will be newer than the one we used, called “VirtualBox-6.1.32--149290-Win.exe.”
2. Run the downloaded file, following the prompts to install the application. If prompted with a warning about network interfaces, click Yes.
3. At the end of the setup process, click Finish.
4. If you see a prompt about having an old version of an extension pack, click Download and wait for the new one to be downloaded, and then click Install and wait for it to be installed.
Congratulations! Oracle VM VirtualBox Manager is now installed. Move on to Exercise 7-2.
EXERCISE 7-2

Creating a Virtual Machine in VirtualBox
This exercise picks up where Exercise 7-1 left off. You’ve installed VirtualBox, and now you’ll create a new virtual machine. These steps assume you are using 64-bit Ubuntu Linux as the guest OS, which you can acquire from Ubuntu.com. Download an ISO, and then follow these steps.
1. On the VirtualBox application’s toolbar, click New.
2. Type the name for the VM in the Name box. It is customary (and recommended) to include the guest OS name in the VM name.
3. Open the Type drop-down list and select the OS you plan to install, and then open the Version drop-down list and select the version. For this exercise, choose Linux as the type and Ubuntu (64-bit) as the version. Then click Next.
4. On the Memory Size page, if needed, drag the slider to 1 GB (1024 MB) and then click Next.
5. On the Hard Disk page, click Create A Virtual Hard Disk Now and click Create.
6. On the Hard Disk File Type page, select VDI (unless you have a reason to select something else) and click Next.
7. On the Storage On Physical Hard Disk Page, leave Dynamically Allocated selected and click Next.
8. On the File Location And Size Page, leave the default of 10 GB selected and click Create.
9. To start the VM, select it and click Start. A box will pop up asking you to choose the optical disc from which to install the OS. Point it to the ISO file or the physical optical drive and then follow the prompts.
10. If the VM you are installing is Ubuntu, you will see a Welcome screen with the choices Try Ubuntu and Install Ubuntu. We recommend Install because you will be using this VM for other chapters, and it will improve performance to have it installed. Make your selection and follow the prompts to complete the installation. Accept the defaults for any setting you are not sure about.
11. After Ubuntu restarts, you may see a message asking you to remove the ISO file as you are rebooting. To do that, open the Devices menu in VirtualBox, point to Optical Drives, and then select the Ubuntu ISO to remove the check mark next to its name. If you get a message that it can’t be ejected, offering to let you do a force dismount, do that. With the ISO removed, you will be able to boot from the virtual hard disk where Ubuntu is installed.
Configuring VirtualBox
Your virtual machines appear in the left pane in the Oracle VM VirtualBox Manager window. You can click any VM and then click Settings on the toolbar to open its settings. In the Settings window, select a category on the left, and then select a tab across the top to view the pages of settings for that category (see Figure 7-6). Some settings may not be available when the VM is running.
FIGURE 7-6
Adjusting a VM’s settings in VirtualBox

Capturing and Releasing the Mouse and Keyboard in a Guest OS
Once you have a guest OS installed into a virtual machine, the guest OS and host OS are sharing the same physical hardware, but each physical device can serve only one master at a time.
Most hypervisors have extensions for most modern operating systems that allow control of the keyboard and mouse to pass seamlessly back and forth between the VM and the host system. (These are called guest additions in VirtualBox. You learn how to enable them in the next section.) When the VM window is active, the keyboard and mouse work within it. When the mouse moves outside the VM window and clicks, control returns to the host OS.
However, with some OSs, that smooth transfer doesn’t happen automatically. In some cases you may be able to install extensions that enable the feature, but in other cases you may need to press a certain key sequence to release the mouse from the guest OS window each time you want to return to the host OS. This is called the host key.
The hypervisor assigns a host key. For instance, VirtualBox on a Windows computer uses the right CTRL key as the host key. VirtualBox on a macOS system uses the left COMMAND key.
Improving Guest OS Performance
After you install a guest OS into a guest VM, no matter which hypervisor you use, you may find that the screen and performance are not up to par, with only a low resolution available to you. Hypervisors usually have special software that you can install into the guest OS.
VirtualBox has special drivers and other software called collectively Guest Additions, and you install them after you install a guest OS. To do this, you start up your guest OS, and then access the VirtualBox menu system on the window containing your guest OS, and click the Devices menu. Click Install Guest Additions and follow the instructions to run the program.
If you don’t see the Install Guest Additions command on the Devices menu, or if you see Insert Guest Additions CD Image, you might need to point it to the CD image. Choose Devices | Optical Drives | Choose Disc File to locate it. Look in C:Program FilesOracleVirtualBox. The filename is VBoxGuestAdditions.iso. If prompted whether to run it, click Run.
When the Guest Additions are installed, you will be prompted to reboot the virtual machine. This is necessary before the changes take effect. Oracle VirtualBox configures your guest client to check for updates to the Guest Additions, so after you reboot the VM, if you are connected to the Internet through the host OS, you may see a message stating that there are updates—even if, as we did, you downloaded and installed VirtualBox on the same day.

Each hypervisor has its own set of drivers and other programs to improve the virtual machine performance, but they are all guest OS specific, and each vendor gives their group of guest OS drivers and programs a different name.
The result should be better performance overall, and you may find that Windows will have more resolution options for configuring your display.

CERTIFICATION SUMMARY
A technician should understand the basics of client-side virtualization; the purpose of virtual machines; and the various requirements, including resources on the host computer, emulator needs, security, and network. Also important is understanding what a hypervisor is and the types of hypervisors available.
 TWO-MINUTE DRILL
TWO-MINUTE DRILL
Here are some of the key points covered in Chapter 7.
Introduction to Virtualization
![]() Virtualization is the creation of an environment that seems real but isn’t.
Virtualization is the creation of an environment that seems real but isn’t.
![]() Virtualization is used for many purposes, such as a virtual world, a virtual classroom, storage virtualization, network virtualization, server virtualization, and desktop virtualization.
Virtualization is used for many purposes, such as a virtual world, a virtual classroom, storage virtualization, network virtualization, server virtualization, and desktop virtualization.
![]() Client-side virtualization occurs on the client side of a client-server arrangement.
Client-side virtualization occurs on the client side of a client-server arrangement.
![]() Server-side virtualization occurs on the server side of a client-server relationship.
Server-side virtualization occurs on the server side of a client-server relationship.
![]() Virtual desktop infrastructure (VDI) is the hosting and managing of multiple virtual desktops on network servers.
Virtual desktop infrastructure (VDI) is the hosting and managing of multiple virtual desktops on network servers.
![]() Examples of desktop virtualization include Windows, Unix, or Linux virtual machines running on Windows, macOS, or Linux systems.
Examples of desktop virtualization include Windows, Unix, or Linux virtual machines running on Windows, macOS, or Linux systems.
![]() Examples of client-side virtualization include presentation virtualization, application virtualization, and desktop virtualization.
Examples of client-side virtualization include presentation virtualization, application virtualization, and desktop virtualization.
Implementing Client-Side Desktop Virtualization
![]() A hypervisor, also called a virtual machine manager (VMM), is the software that creates a virtual machine, providing access to the necessary hardware on the host machine in isolation from other virtual machines and from a host operating system, if present.
A hypervisor, also called a virtual machine manager (VMM), is the software that creates a virtual machine, providing access to the necessary hardware on the host machine in isolation from other virtual machines and from a host operating system, if present.
![]() Most hypervisors require, or at least work better with, hardware-assisted virtualization (HAV), features of Intel Virtualization Technology for x86 (Intel VT-x), or AMD Virtualization (AMD-V).
Most hypervisors require, or at least work better with, hardware-assisted virtualization (HAV), features of Intel Virtualization Technology for x86 (Intel VT-x), or AMD Virtualization (AMD-V).
![]() In virtualization, the hypervisor must create a virtual machine compatible with that of the underlying machine, whereas emulation allows you to run an OS or device on hardware with which it is completely incompatible.
In virtualization, the hypervisor must create a virtual machine compatible with that of the underlying machine, whereas emulation allows you to run an OS or device on hardware with which it is completely incompatible.
![]() Sometimes a virtual machine may emulate some piece of hardware that is either not present or not compatible in the underlying hardware.
Sometimes a virtual machine may emulate some piece of hardware that is either not present or not compatible in the underlying hardware.
![]() Internet access is important for working with virtual machines and keeping the hypervisor and its guest OSs up to date. A hypervisor will provide virtual network adapters, as well as a virtual network, on the host computer.
Internet access is important for working with virtual machines and keeping the hypervisor and its guest OSs up to date. A hypervisor will provide virtual network adapters, as well as a virtual network, on the host computer.
![]() The security requirements for a guest OS are the same as those for the host system. Therefore, immediately after installing a guest OS, install a security suite.
The security requirements for a guest OS are the same as those for the host system. Therefore, immediately after installing a guest OS, install a security suite.
![]() Oracle VM VirtualBox Manager is a free hypervisor that runs on a variety of platforms and is easy to set up and use.
Oracle VM VirtualBox Manager is a free hypervisor that runs on a variety of platforms and is easy to set up and use.
Q SELF TEST
The following questions will help you measure your understanding of the material presented in this chapter. Read all the choices carefully because there might be more than one correct answer. Choose all correct answers for each question.
Introduction to Virtualization
1. You may use one of these animated graphic objects to represent you in a virtual world.
A. Gadget
B. Guest
C. Avatar
D. Snap-in
2. What type of virtualization is used in distance learning for interactive presentations by instructors?
A. Server-side virtualization
B. Virtual classroom
C. Client-side virtualization
D. Application virtualization
3. This type of virtualization only provides support for an app’s user interface and the user interface itself exists on a client computer, while the app runs on a server.
A. Application virtualization
B. Storage virtualization
C. Presentation virtualization
D. Server virtualization
4. In network virtualization, what portion of a network exists within one or more physical networks, creating a virtual network?
A. Network adapters
B. Network address space
C. Switch
D. Router
5. What acronym represents the term for hosting and managing multiple virtual desktops on a network?
A. VMM
B. HAV
C. VDI
D. App-V
6. In this type of client-side virtualization, a user runs an application in a virtualized application environment on the local computer, isolating the application.
A. Storage virtualization
B. Application virtualization
C. Virtual world
D. Thin client
Implementing Client-Side Desktop Virtualization
7. Which acronym is a generic term for virtualization support found in modern CPUs?
A. VMM
B. VDI
C. HAV
D. App-V
8. Which of the following terms is used in computers to describe the use of software that allows you to run an OS or device on hardware with which it is completely incompatible?
A. Virtualization
B. Hardware-assisted virtualization
C. Emulation
D. Linux
9. Which of the following is a free hypervisor by Oracle with versions for Linux, Windows, and macOS hosts?
A. VirtualBox
B. Parallels
C. Player
D. Hyper-V Manager
10. Which of the following does not require a host OS?
A. Type II hypervisor
B. Type I hypervisor
C. Oracle VirtualBox
D. Hyper-V Manager
11. Which of the following terms is synonymous with hypervisor?
A. Type I
B. Virtual machine manager (VMM)
C. Type II
D. Remote Desktop
12. Which hypervisor is available only in 64-bit Pro and Enterprise versions of Windows?
A. Hyper-V Manager
B. Parallels
C. Windows Virtual PC
D. VirtualBox
13. What legal issue must you consider when installing a guest OS in a virtual machine?
A. Security
B. Licensing
C. Copyright
D. Credentials
14. Which of the following will release the mouse and keyboard from control of a virtual machine?
A. Host key
B. Guest key
C. Windows key
D. Product key
15. In desktop virtualization, the OS installed directly on the hardware is the ______ and the OS installed in a virtual machine is the _____.
A. Guest, host
B. Host, guest
C. Primary, secondary
D. Secondary, primary
16. Put the following steps in order: (1) Install guest OS; (2) Install hypervisor; (3) Create virtual machine; (4) Install security software.
A. 1, 2, 3, 4
B. 1, 4, 3, 2
C. 2, 3, 1, 4
D. 4, 1, 3, 2
17. Which OS cannot legally be used as a guest OS in a Type II hypervisor?
A. Linux
B. Windows 7
C. macOS
D. Windows 10
18. Which of the following identifies Intel’s CPUs with hardware-assisted virtualization technology?
A. HAV
B. App-V
C. VMM
D. VT-x
19. Which of the following describes a Type I hypervisor?
A. App-V
B. Guest OS
C. VDI
D. Bare-metal hypervisor
20. Which of these is a recommended way of securing a guest OS?
A. Not allowing additional monitors to be connected
B. Not allowing local access to the guest OS
C. Removing the password from the guest OS
D. Using a strong password to sign into the guest OS
A SELF TEST ANSWERS
Introduction to Virtualization
1. ![]() C. An avatar is an animated, computer-generated human or animal image that represents a computer user in a virtual world.
C. An avatar is an animated, computer-generated human or animal image that represents a computer user in a virtual world.
![]() A is incorrect, as a gadget is a small program. B is incorrect because the only use of the term “guest” in this chapter is in the context of “guest OS,” the OS running within a VM. D is incorrect because a snap-in is a utility module added to a Microsoft Management Console.
A is incorrect, as a gadget is a small program. B is incorrect because the only use of the term “guest” in this chapter is in the context of “guest OS,” the OS running within a VM. D is incorrect because a snap-in is a utility module added to a Microsoft Management Console.
2. ![]() B. A virtual classroom is a type of virtualization used in distance learning for interactive presentations by instructors.
B. A virtual classroom is a type of virtualization used in distance learning for interactive presentations by instructors.
![]() A and C are both incorrect because these are simply terms for the hosting location of virtualization. D is incorrect because this is a type of client-side virtualization.
A and C are both incorrect because these are simply terms for the hosting location of virtualization. D is incorrect because this is a type of client-side virtualization.
3. ![]() C. Presentation virtualization is a type of virtualization in which only support for an app’s user interface, and the user interface itself, exist on a client computer, while the app itself runs on a server.
C. Presentation virtualization is a type of virtualization in which only support for an app’s user interface, and the user interface itself, exist on a client computer, while the app itself runs on a server.
![]() A is incorrect because in this type of virtualization, the entire app is virtualized and the user interface is not separated from the app, but is isolated in a VM. B is incorrect because this type of virtualization allows client computers to utilize many networked hard drives as though they are one drive or location. D is incorrect because in server virtualization a single machine hosts one or more server operating systems, each in a virtual machine and each performing tasks independently from the other virtual machines and from the host.
A is incorrect because in this type of virtualization, the entire app is virtualized and the user interface is not separated from the app, but is isolated in a VM. B is incorrect because this type of virtualization allows client computers to utilize many networked hard drives as though they are one drive or location. D is incorrect because in server virtualization a single machine hosts one or more server operating systems, each in a virtual machine and each performing tasks independently from the other virtual machines and from the host.
4. ![]() B. Network address space exists within one or more physical networks, creating a virtual network.
B. Network address space exists within one or more physical networks, creating a virtual network.
![]() A is incorrect because it is the address space that is virtualized in network virtualization. C and D are incorrect because these are both types of network hardware not described in this chapter and are not used to create a virtual network.
A is incorrect because it is the address space that is virtualized in network virtualization. C and D are incorrect because these are both types of network hardware not described in this chapter and are not used to create a virtual network.
5. ![]() C. VDI, virtual desktop infrastructure, describes the hosting and managing of multiple virtual desktops over a network.
C. VDI, virtual desktop infrastructure, describes the hosting and managing of multiple virtual desktops over a network.
![]() A is incorrect because virtual machine manager (VMM) is another term for hypervisor. B is incorrect because hardware-assisted virtualization (HAV) is hardware-level support for virtualization found in Intel and AMD CPUs. D is incorrect because Application Virtualization (App-V) is the term for Microsoft’s application virtualization software.
A is incorrect because virtual machine manager (VMM) is another term for hypervisor. B is incorrect because hardware-assisted virtualization (HAV) is hardware-level support for virtualization found in Intel and AMD CPUs. D is incorrect because Application Virtualization (App-V) is the term for Microsoft’s application virtualization software.
6. ![]() B. Application virtualization is the type of client-side virtualization in which a user runs an application in a virtualized application environment on the local computer, isolating the application.
B. Application virtualization is the type of client-side virtualization in which a user runs an application in a virtualized application environment on the local computer, isolating the application.
![]() A is incorrect because storage virtualization allows client computers to utilize many networked hard drives as though they are one. C is incorrect because a virtual world is an artificial environment that users can explore, often using an avatar. D is incorrect because a thin client is a low-cost PC that runs software to connect to a server, transfer video downstream to the thin client, and send mouse clicks and keystrokes upstream to the application on the server.
A is incorrect because storage virtualization allows client computers to utilize many networked hard drives as though they are one. C is incorrect because a virtual world is an artificial environment that users can explore, often using an avatar. D is incorrect because a thin client is a low-cost PC that runs software to connect to a server, transfer video downstream to the thin client, and send mouse clicks and keystrokes upstream to the application on the server.
Implementing Client-Side Desktop Virtualization
7. ![]() C. HAV (hardware-assisted virtualization) is the generic term for virtualization support found in modern CPUs.
C. HAV (hardware-assisted virtualization) is the generic term for virtualization support found in modern CPUs.
![]() A is incorrect because virtual machine manager (VMM) is simply another term for a hypervisor. B is incorrect because virtual desktop infrastructure (VDI) is a term for the creation and management of multiple virtual desktops. D is incorrect because App-V is a Microsoft term for their application virtualization software.
A is incorrect because virtual machine manager (VMM) is simply another term for a hypervisor. B is incorrect because virtual desktop infrastructure (VDI) is a term for the creation and management of multiple virtual desktops. D is incorrect because App-V is a Microsoft term for their application virtualization software.
8. ![]() C. Emulation is the use of software that allows you to run an OS or device on hardware with which it is completely incompatible.
C. Emulation is the use of software that allows you to run an OS or device on hardware with which it is completely incompatible.
![]() A is incorrect, as virtualization is the creation of an environment that seems real but is not. While that is close to emulation, in the context of virtualization on computers, these terms are often kept separate. B is incorrect because hardware-assisted virtualization (HAV) is simply hardware support for virtualization built into modern CPUs. D is incorrect because Linux is simply an operating system.
A is incorrect, as virtualization is the creation of an environment that seems real but is not. While that is close to emulation, in the context of virtualization on computers, these terms are often kept separate. B is incorrect because hardware-assisted virtualization (HAV) is simply hardware support for virtualization built into modern CPUs. D is incorrect because Linux is simply an operating system.
9. ![]() A. VirtualBox is the free hypervisor by Oracle with versions for Linux, Windows, and macOS hosts.
A. VirtualBox is the free hypervisor by Oracle with versions for Linux, Windows, and macOS hosts.
![]() B is incorrect because Parallels is not by Oracle and is not free. C is incorrect because Player is by VMware, not Oracle, and it does not come in a version for macOS hosts. D is incorrect because Hyper-V Manager is by Microsoft, not Oracle, and it does not come in a version for macOS hosts.
B is incorrect because Parallels is not by Oracle and is not free. C is incorrect because Player is by VMware, not Oracle, and it does not come in a version for macOS hosts. D is incorrect because Hyper-V Manager is by Microsoft, not Oracle, and it does not come in a version for macOS hosts.
10. ![]() B. A Type I hypervisor does not require a host OS.
B. A Type I hypervisor does not require a host OS.
![]() A is incorrect because a Type II hypervisor does require a host OS. C and D are incorrect because they are both Type II hypervisors that require a host OS.
A is incorrect because a Type II hypervisor does require a host OS. C and D are incorrect because they are both Type II hypervisors that require a host OS.
11. ![]() B. Virtual machine manager (VMM) is synonymous with hypervisor.
B. Virtual machine manager (VMM) is synonymous with hypervisor.
![]() A and C are incorrect because while they are types of hypervisors, Type I and Type II are not synonymous with hypervisor. D is incorrect because Remote Desktop is a Windows feature that enables you to remotely access other systems; these are real systems, not virtual machines, and no hypervisor is involved.
A and C are incorrect because while they are types of hypervisors, Type I and Type II are not synonymous with hypervisor. D is incorrect because Remote Desktop is a Windows feature that enables you to remotely access other systems; these are real systems, not virtual machines, and no hypervisor is involved.
12. ![]() A. Hyper-V Manager is available in 64-bit versions of Windows 8 and higher in Pro and Enterprise editions.
A. Hyper-V Manager is available in 64-bit versions of Windows 8 and higher in Pro and Enterprise editions.
![]() B is incorrect because Parallels is primarily for the macOS and is not included in Windows. C is incorrect because Virtual PC is for Windows 7, not for later Windows versions. D is incorrect because VirtualBox is an Oracle product and is not included in any version of Windows.
B is incorrect because Parallels is primarily for the macOS and is not included in Windows. C is incorrect because Virtual PC is for Windows 7, not for later Windows versions. D is incorrect because VirtualBox is an Oracle product and is not included in any version of Windows.
13. ![]() B. Licensing of the guest OS is very important.
B. Licensing of the guest OS is very important.
![]() A is incorrect because although security is very important for both the guest and host OSs, it is not, strictly speaking, a legal issue. C and D are incorrect because neither is a legal issue with a guest OS.
A is incorrect because although security is very important for both the guest and host OSs, it is not, strictly speaking, a legal issue. C and D are incorrect because neither is a legal issue with a guest OS.
14. ![]() A. A host key is a special key or key combination that will release the mouse and keyboard from control of a virtual machine.
A. A host key is a special key or key combination that will release the mouse and keyboard from control of a virtual machine.
![]() B is incorrect because a guest key is not the key or key combination that will release the mouse and keyboard from control of a virtual machine. C is incorrect because the windows key (on the keyboard) works within Microsoft software on its own and in combination with other keys, and is many things other than a host key. D is incorrect, as the product key is not an actual key on the keyboard, but a string of characters used by Microsoft for piracy protection.
B is incorrect because a guest key is not the key or key combination that will release the mouse and keyboard from control of a virtual machine. C is incorrect because the windows key (on the keyboard) works within Microsoft software on its own and in combination with other keys, and is many things other than a host key. D is incorrect, as the product key is not an actual key on the keyboard, but a string of characters used by Microsoft for piracy protection.
15. ![]() B. The OS installed on the hardware is the host, and the VM OS is the guest.
B. The OS installed on the hardware is the host, and the VM OS is the guest.
![]() A is incorrect because these answers are opposite of the correct ones. C and D are both incorrect because primary and secondary are terms used to describe hardware interfaces (as in primary IDE, secondary IDE); they are not applicable to virtualization.
A is incorrect because these answers are opposite of the correct ones. C and D are both incorrect because primary and secondary are terms used to describe hardware interfaces (as in primary IDE, secondary IDE); they are not applicable to virtualization.
16. ![]() C. (2) Install hypervisor; (3) Create virtual machine; (1) Install guest OS; (4) Install security software.
C. (2) Install hypervisor; (3) Create virtual machine; (1) Install guest OS; (4) Install security software.
![]() A, B, and D are incorrect because they are not in the proper order as described in this chapter.
A, B, and D are incorrect because they are not in the proper order as described in this chapter.
17. ![]() C. macOS cannot be used as a guest OS legally. It is available only preinstalled on Mac hardware.
C. macOS cannot be used as a guest OS legally. It is available only preinstalled on Mac hardware.
![]() A, B, and D are incorrect because they all can be guest OSs in a hypervisor.
A, B, and D are incorrect because they all can be guest OSs in a hypervisor.
18. ![]() D. VT-x identifies Intel’s CPUs with hardware-assisted virtualization technology.
D. VT-x identifies Intel’s CPUs with hardware-assisted virtualization technology.
![]() A is incorrect because HAV is simply the acronym for the generic term. B is incorrect because App-V is the abbreviation for Microsoft Application Virtualization. C is incorrect because VMM is the acronym for virtual machine manager, another term for hypervisor.
A is incorrect because HAV is simply the acronym for the generic term. B is incorrect because App-V is the abbreviation for Microsoft Application Virtualization. C is incorrect because VMM is the acronym for virtual machine manager, another term for hypervisor.
19. ![]() D. Bare-metal hypervisor describes a Type I hypervisor because it does not require a host OS between it and the hardware.
D. Bare-metal hypervisor describes a Type I hypervisor because it does not require a host OS between it and the hardware.
![]() A is incorrect because App-V is Microsoft’s application virtualization technology. B is incorrect because the guest OS is the OS running within a virtual machine. C is incorrect because virtual desktop infrastructure (VDI) describes hosting and managing multiple virtual desktops (often thousands) over a network.
A is incorrect because App-V is Microsoft’s application virtualization technology. B is incorrect because the guest OS is the OS running within a virtual machine. C is incorrect because virtual desktop infrastructure (VDI) describes hosting and managing multiple virtual desktops (often thousands) over a network.
20. ![]() D. A strong password is an effective way to secure a guest OS.
D. A strong password is an effective way to secure a guest OS.
![]() A is incorrect because the number of monitors does not affect security. B is incorrect because local access is the most common way to access a guest OS. C is incorrect because removing the password would be detrimental to security.
A is incorrect because the number of monitors does not affect security. B is incorrect because local access is the most common way to access a guest OS. C is incorrect because removing the password would be detrimental to security.
