
Chapter 16
Network Basics
CERTIFICATION OBJECTIVES
![]() 1101: 2.1 Compare and contrast Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) ports, protocols, and their purposes
1101: 2.1 Compare and contrast Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) ports, protocols, and their purposes
![]() 1101: 2.2 Compare and contrast common networking hardware
1101: 2.2 Compare and contrast common networking hardware
![]() 1101: 2.3 Compare and contrast protocols for wireless networking
1101: 2.3 Compare and contrast protocols for wireless networking
![]() 1101: 2.6 Compare and contrast common network configuration concepts
1101: 2.6 Compare and contrast common network configuration concepts
![]() 1101: 2.7 Compare and contrast Internet connection types, network types, and their features
1101: 2.7 Compare and contrast Internet connection types, network types, and their features
![]() 1101: 3.1 Explain basic cable types and their connectors, features, and purposes
1101: 3.1 Explain basic cable types and their connectors, features, and purposes
![]() Two-Minute Drill
Two-Minute Drill
Q&A Self Test
Computer networks provide users with the ability to share files, printers, resources, and e-mail globally. Networks have become so important that they provide the basis for nearly all business transactions.
Obviously, a discussion of the full spectrum of network details and specifications is too broad in scope to be contained in this book. However, as a computer technician, you should be aware of basic networking concepts so you can troubleshoot minor problems on established networks. This chapter focuses on basic concepts of physical networks; Chapter 17 guides you through simple small office/home office (SOHO) network installation, and Chapter 19 provides the basis for troubleshooting common network problems.
CERTIFICATION OBJECTIVE
![]() 1101: 2.7 Compare and contrast Internet connection types, network types, and their features
1101: 2.7 Compare and contrast Internet connection types, network types, and their features
This section describes the types of networks based on how they are connected (topology) and based on the area they service (LAN, WAN, PAN, MAN), as required by CompTIA A+ 1101 exam Objective 2.7.
Network Classifications
For a computer professional working with PCs, the networked computer is the norm, not the exception. A computer not connected to a network has become a nearly extinct species as more and more PCs network together—even within homes.
To understand networks, you must first be familiar with basic network performance and classifications, which describe networks by speed, geography, and scale, beginning with the smallest networks up to globe-spanning ones.
We classify networks by geographic area types, and specific technologies are designed for each of them. Network builders select these technologies for the capabilities that match the distance needs of the network.

For the CompTIA A+ 220-1101 exam Objective 2.7, be sure that you understand the distinctions between the various location-based network types, including PAN, LAN, MAN, and WAN.
Personal Area Network
You may have your own personal area network (PAN) if you have devices such as smartphones, tablets, or printers that communicate with each other and/or your desktop computer. A PAN may use a wired connection, such as Universal Serial Bus (USB) or FireWire, or it may communicate wirelessly using one of the standards developed for short-range communications, such as Bluetooth.
As you learned in Chapter 14, Bluetooth uses radio waves, which do not require line-of-sight, but the signal can be disrupted by physical barriers as well as interference from other signals. The Bluetooth standard describes three classes, with power requirements and distance limits. The Bluetooth standard commonly used with computer peripherals and mobile devices is Class 3, limited to a distance of 1 meter, or Class 2, limited to about 10 meters.
Local Area Network
A local area network (LAN) is a network that covers a much larger area than a PAN, such as a building, home, office, or campus. Typically, distances measure in hundreds of meters. A LAN may share resources such as printers, files, or other items. LANs operate very rapidly, with speeds measured in megabits or gigabits per second, and have become extremely cost-effective. While there are many LAN technologies, the two most widely used in SOHO network installations are Ethernet and Wi-Fi.
Metropolitan Area Network
A metropolitan area network (MAN) is a network that covers a metropolitan area, connecting various networks together using a shared community network and often providing WAN connections to the Internet. A MAN usually runs over high-speed fiber-optic cable operating in the gigabits-per-second range. Although people tend to be less aware of MANs, they nonetheless exist. In fact, a MAN may well be somewhere between you and the Internet.
Wide Area Network
A wide area network (WAN) can cover the largest geographic area. A WAN connection is the connection between two networks over a long distance (miles). The term WAN is used to describe a wired WAN connection versus a wireless wide area network (WWAN), a wireless connection between two networks over a long distance.
Storage Area Network
A storage area network (SAN) is not the same kind of network as the other types covered so far. It’s a data network created for one purpose: to connect and manage large-scale storage devices, such as file servers, and make that storage capacity available to users who need it. Users do not directly access the storage on a SAN; they access a SAN server, which facilitates usage of the storage, making the actual location and configuration of the storage devices invisible to the end users. The server operating system maintains its own file system, and that file system is what user PCs interact with.

A SAN has its own hardware and software protocols and layers, but you don’t need to understand them in detail. Just make sure you know what a SAN is and what its benefits are.
Companies that have large-scale storage needs often implement SANs because they can aggregate the storage available from hundreds of different locations and load-balance the traffic among them, while the user sees the entire network as a single location.
CERTIFICATION OBJECTIVE
![]() 1101: 2.7 Compare and contrast Internet connection types, network types, and their features
1101: 2.7 Compare and contrast Internet connection types, network types, and their features
This section describes Internet connection types, as required by CompTIA A+ 1101 exam Objective 2.7.
Internet Connection Types
Next we’ll review the Internet connection types. They fall into two broad categories: wired and wireless. The wired ones are fiber, cable, and DSL, and the wireless ones are satellite, long-range fixed wireless, and cellular. Although satellite is technically “wireless” in that it receives and sends via a satellite dish rather than via cables, that satellite dish is wired to the location receiving the service, so although it is wireless, it isn’t mobile.

Make sure you understand how each Internet connection type works, its benefits/drawbacks, and in what situations it is the best choice.
Each of these Internet connection types (except cellular) can easily be shared within the service location by connecting it to a router, which also serves as a switch that connects the computers in that location as a LAN. The router shares the Internet connection with the entire LAN. In contrast, cellular is usually a one-device connection, such as a smartphone or cellular-enabled tablet. However, cellular devices can be set to serve as a mobile hotspot, and multiple devices can be tethered to it (usually wirelessly) to share its Internet connection. You learned about that in Chapter 15, and they’re also covered later in this chapter.
Understanding Bandwidth and Latency
When evaluating different Internet connection options, two important factors to consider are bandwidth and latency. Bandwidth is the amount of data that can travel over a network within a given time. It’s often used rather loosely to mean speed, but it’s more a measure of the amount of data that can be sent during a specific timeframe (1 second). It may be expressed in megabits per second (Mbps) or gigabits per second (Gbps)—that is, millions of bits per second or billions of bits per second. In this book we don’t provide specific bandwidth ratings for the different connection types because these are constantly in flux, with providers finding new ways to bump up their bandwidth almost weekly. In addition, most providers offer a variety of connection packages at different prices and bandwidths. In general, though, the following sections list the connection types from fastest to slowest.
Another network characteristic related to bandwidth is latency. Latency is the delay between sending a network request and the arrival of that request at its destination. In some cases, latency is determined by measuring the time it takes for a packet to make a round trip between two points. This can be a more important measurement, as it does not measure the speed at which the packets travel, but the length of time it takes a packet to get from point A to point B. It is like measuring the actual time it takes you to travel by car from Los Angeles to San Francisco. The actual time of travel varies by the amount of traffic you encounter and the interchanges you pass through. The same is true for a packet on a network.
Fiber Internet
Fiber-optic service (often abbreviated as just “fiber”) is an extremely high-bandwidth Internet service that uses fiber-optic cable to send and receive data using pulses of light. Many providers deploy fiber-optic cables all the way up to the subscriber address, making it possible to deliver Internet upload and download rates of 1 Gbps or more. This is sometimes referred to as pure fiber. Other providers use fiber to go into a neighborhood, but then use copper cables for the “last mile” of the connection to individual buildings. Fiber-optic cables are discussed in more detail later in this chapter. The main drawback of fiber is limited availability outside of major cities.
Cable Internet
Cable and fiber-optic providers battle back and forth for the title of highest-bandwidth Internet service, and their highest-rate plans are usually comparable. However, the actual rate of cable Internet is seldom as high as its theoretical capability, because whereas fiber and DSL services are point-to-point from the client to the ISP, a cable client shares the network with their neighboring cable clients. It is like when multiple PCs in your home share an Internet connection and several PCs are streaming high-definition video at once. The rate degrades as more locations share the local cable network.
Cable networks use coaxial cable to connect a cable modem to the network. They use the same cable to provide both Internet and cable TV, with a splitter used to connect both the broadband modem and the TV to the same wall jack if needed.
DSL Internet
Digital subscriber line (DSL) uses existing copper telephone wire for the communications circuit. A DSL modem splits the existing phone line into two bands to accomplish this: one for voice, the other for data. Voice phone calls happen normally, and the data connection is always on and available.
DSL service is available through phone companies, which offer a large variety of DSL services. Some services, such as asymmetric DSL (ADSL), offer asymmetric service in that the download rate is higher than the upload. Other, more expensive services aimed at business offer higher rates. Symmetric DSL (SDSL) offers matching upload and download rates.
Because DSL relies on standard copper wire phone lines, it can’t match the bandwidth of fiber. Its main advantage is broader availability; most urban and suburban areas have robust phone systems that can carry DSL data. Not every location that has telephone service can support DSL, though; the location must be within 18,000 feet of a central office (CO). The closer to the CO, the faster the speed available. At a certain point, the distance becomes too great to offer satisfactory DSL speed.
Many providers that have offered DSL in the past, such as AT&T and Verizon, are switching to fiber service instead, which offers much higher speeds. DSL, even the fastest versions of it, is increasingly becoming “old technology.”
Satellite Internet
Satellite Internet offers relatively high-speed Internet service to areas where fiber, cable, and DSL are not available. It uses a satellite dish for receiving and a transmitter mounted to the dish for sending. Both the dish and the transmitter connect to a terminal adapter that functions much like a cable or DSL modem.
Early satellite communications systems were very expensive to maintain and operate. Today, however, a number of companies offer decent Internet speeds at affordable prices. As with TV satellite service, you must have a place to mount the dish antenna with a clear view of the southern sky.
The problem with satellite service is not so much the raw speed, but the latency. Because the signal must travel into space and back, there is an unavoidable delay each time your computer requests data, which makes satellite service seem slower than raw speed tests would have you believe.
Long-Range Fixed Wireless
Long-range fixed wireless is a relatively new entry into the Internet service provider market. Like satellite, it connects locations with Internet service without having to run cables. But instead of connecting to an orbiting satellite, its antenna communicates with a transmitter/receiver on a land-based tower, like the towers used for cellular service. Its latency is much less than that of satellite.
The most common use for this technology is by wireless Internet service providers (WISPs), which provide wireless Internet access in rural and underserved areas via unlicensed frequencies. This brings high-speed Internet to people and locations that do not have access to fiber, cable, or DSL. The antennas installed at the service locations must have a line-of-sight to the tower.
The Federal Communications Commission (FCC) licenses most of the radio frequency (RF) spectrum to certain users, such as radio and TV providers. They pay a fee for exclusive rights to broadcast on a certain frequency in a certain geographic area. There are also unlicensed frequencies, but it’s a fairly small bandwidth. Anyone can broadcast on those frequencies, but if someone else is also broadcasting in the same area at the same time, it can cause conflicts.
To avoid a “Wild West” situation in the unlicensed spectrum, the FCC imposes regulatory limitations on the amount of broadcast power antennas can use, which in turn limits the distance that the antenna can be from the tower. These power regulations keep things orderly, but they prevent some locations from receiving service that might be able to take advantage of it if the broadcast power were increased.

Long-range fixed wireless is a new addition to the 1101 exam. Make sure you understand who can benefit from long-range fixed wireless and how WISPs provide Internet service using unlicensed bandwidth. You should also understand the relationship between broadcast power and the maximum distance between the antenna and the tower.
Cellular Internet
Long used mainly for voice, the cell networks provide cellular WAN Internet data connections, also referred to as WWAN. These data services have a range of broadband speeds, depending on the cellular provider and the level of service you have purchased.
Different technology generations are in use on different cellular networks. Third generation (3G) is considered old technology today, and 4G is on the wane; 5G is the current standard. 5G is superior to earlier generations in several ways, including higher speed, lower latency, and greater bandwidth.
EXERCISE 16-1
Testing Broadband Speeds
Regardless of the broadband service you use, they all vary in the actual speeds they provide from moment to moment. Connect to one of the many broadband speed-testing sites on the Internet and test yours now.
1. Open your favorite search engine and enter a search string that will locate an Internet speed testing website. We used network speed test.
2. From the results listed in the search engine, select a site (we chose www.speedtest.net). Often sites suggest downloading and running other software to test your computer, so be careful to only select the speed test and not to download or run programs you do not want.
3. Follow the instructions for testing your connection. Some sites test as soon as you connect, and some test sites ask you to select a city near you. The test may take several minutes.
4. View the results. Are the results congruent with the service you expect from your broadband connection?
5. Time permitting, try this at another time, or even on another day, and compare your results.

CERTIFICATION OBJECTIVES
![]() 1101: 2.1 Compare and contrast Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) ports, protocols, and their purposes
1101: 2.1 Compare and contrast Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) ports, protocols, and their purposes
![]() 1101: 2.3 Compare and contrast protocols for wireless networking
1101: 2.3 Compare and contrast protocols for wireless networking
![]() 1101: 2.6 Compare and contrast common network configuration concepts
1101: 2.6 Compare and contrast common network configuration concepts
This section details the topics required for CompTIA A+ 1101 exam Objective 2.6. DNS and DHCP coverage of CompTIA A+ 1101 exam Objective 2.1 is also included in this section because it is part of the TCP/IP story. It includes an explanation of both TCP and UDP protocols, as well as other TCP and UDP protocols and related services, and the ports used by TCP and UDP. This section also reviews the various IEEE 802.11 Wi-Fi standards, per CompTIA A+ 1101 exam Objective 2.3.
Network Software and Protocols
The software on a network is what gives us the network that we know and use. This is the logical network that rides on top of the physical network. In this section, we’ll explore several aspects of networking that are controlled by software, including the network roles, protocol suites, and network addressing of the logical network.
Network Roles
You can describe a network by the types of roles played by the computers on it. The two general computer roles in a network are clients, the computers that request services, and servers, the computers that provide services.
Peer-to-Peer Networks
In a peer-to-peer network, each computer system in the network may play both roles: client and server. They have equal capabilities and responsibilities; each computer user is responsible for controlling access, sharing resources, and storing data on their computer. In Figure 16-1, each of the computers can share its files, and the computer connected to the printer can share the printer. Peer-to-peer networks work best in a very small LAN environment, such as a small business office, with fewer than a dozen computers and users. Microsoft calls a peer-to-peer network a workgroup, and each workgroup must have a unique name, as must each computer.
FIGURE 16-1
A peer-to-peer network

Client/Server-Based Networks
A client/server-based network uses dedicated computers called servers to store data and provide print services or other capabilities. Servers are generally more powerful computer systems with more capacity than a typical workstation. Client/server-based models also allow for centralized administration and security. These types of networks are scalable in that they can grow very large without adding administrative complexity to the network. A large private internetwork for a globe-spanning corporation is an example of a client/server-based network. When configuring the network, the network administrator can establish a single model for security, access, and file sharing. Although this configuration may remain unchanged as the network grows, the administrator can make changes, if needed, from a central point. Microsoft calls a client/server network with Microsoft servers a domain. The domain must have a unique name, and each client or server computer must have a unique name.
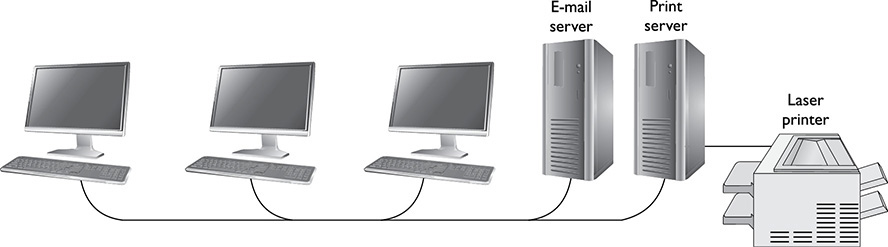
Organizations use client/server environments extensively in situations that need a centralized administration system. Servers can be multipurpose, performing a number of functions, or dedicated, as in the case of a web or e-mail server. Figure 16-2 shows a network with servers used for e-mail and printing. Notice in this example that each of the servers is dedicated to the task assigned to it.
FIGURE 16-2
A client/server environment where dedicated servers perform assigned functions
TCP/IP
Every computer network consists of physical and logical components controlled by software. Standards, also often called protocols, describe the rules for how hardware and software work and interact together.
These protocols control the addressing and naming of computers on the network, among other tasks. They combine into suites that include a group of protocols built around the same set of rules, with each protocol describing a small portion of the tasks required to prepare, send, and receive network data.
The CompTIA 220-1101 exam requires that A+ candidates understand the basics of the TCP/IP protocol suite because it is the most common protocol suite used on LANs and WANs, as well as on the Internet. It involves several protocols and other software components, and together, we call these a protocol stack or a protocol suite.
Transmission Control Protocol/Internet Protocol (TCP/IP) is by far the most common protocol suite on both internal LANs and public networks. It is the Internet’s protocol suite. TCP/IP requires some configuration, but it is robust, usable on very large networks, and routable (a term that refers to the ability to send data to other networks). At each junction of two networks is a router that uses special router protocols to send each packet on its way toward its destination.
TCP/IP allows for cross-platform communication, meaning that computers using different OSs (such as Windows and Linux) can send data back and forth, provided they are both using TCP/IP.
Although the TCP/IP suite has several protocols, the two main ones are the Transmission Control Protocol (TCP) and the Internet Protocol (IP). We now briefly describe these two cornerstone protocols of the TCP/IP suite.

The CompTIA A+ 220-1101 exam expects you to understand the basics of TCP/IP, the difference between TCP and UDP, and the purpose of the various protocols and their associated ports.
Internet Protocol
Messages sent over a network are broken up into smaller chunks of data, and each chunk is placed into a logical container called a packet. Each packet has information attached to the beginning of the packet, called a header. This packet header contains the IP address of the sending computer and that of the destination computer. The Internet Protocol (IP) manages this logical addressing of the packet so that routing protocols can route it over the network to its destination. We describe addressing in the upcoming section “Network Addressing.”
Transmission Control Protocol
When preparing to send data over a network, the Transmission Control Protocol (TCP) breaks the data into chunks, called datagrams. Each datagram contains information to use on the receiving end to reassemble the chunks of data into the original message. TCP places this information, both a byte-count value and a datagram sequence, into the datagram header before giving it to the IP protocol, which encapsulates the datagrams into packets with addressing information.
When receiving data from a network, TCP uses the information in this header to reassemble the data. If TCP is able to reassemble the message, it sends an acknowledgment (ACK) message to the sending address. The sender can then discard datagrams that it saved while waiting for an acknowledgment. If pieces are missing, TCP sends a non-acknowledgment (NAK) message back to the sending address, whereupon TCP resends the missing pieces.
An excellent 13-minute movie describing how TCP/IP works in an amusing and interesting fashion is available for viewing at www.warriorsofthe.net and is well worth watching.
Network Addressing
Identifying each computer or device directly connected to a network is important. We do this at two levels: the hardware level, in which the network adapter in each computer or network device has an address, and the logical level, in which a logical address is assigned to each network adapter.
Hardware Addressing
Every network interface card (NIC), and every device connected to a network, has a unique address placed in ROM by the manufacturer. This address, usually permanent, is called by many names, including Media Access Control (MAC) address, physical address, and NIC address.
A physical address is 48 bits long and usually expressed in hexadecimal. You can view the physical address of a NIC in several ways. It is usually, but not always, written on a label attached to the NIC. Figure 16-3 shows the label on a wireless USB NIC. The words “MAC Address” appear above the physical address. The actual address on this NIC is six 2-digit hexadecimal numbers, but on this label, the numbers are not separated. It is easier to read these numbers if separated by a dash, period, or space, like this: 00-11-50-A4-C7-20.
FIGURE 16-3
The physical address of a NIC, labeled “MAC Address,” and shown on the NIC

Locating the physical address is not always so easy. You can also discover the address of a NIC through Windows. Use the IPCONFIG command-line utility that is installed on a Windows computer with the TCP/IP protocol suite. This command lets you view the IP configuration of a network connection and perform certain administrative functions. To see the physical address as well as the rest of the IP configuration for a connection, simply open a Command Prompt window (as described in Chapter 5) and type the ipconfig /all command. The physical address is in the middle of the listing. Notice that it shows six 2-digit hexadecimal numbers, each separated by a dash.
This physical address identifies a computer located in a segment of a network. However, you use logical addresses to locate a computer that is beyond the local network segment.
Logical Addressing/IP Addressing
In addition to the hardware address, a computer in a TCP/IP network must have a logical address that identifies both the computer and the network. This address comes under the purview of the IP protocol. Internet Protocol version 4 (IPv4) and its addressing scheme have been in use for over the past three decades. It offers almost 4.3 billion possible IP addresses, but the way they have been allocated throughout the world reduces that number. The Internet is currently transitioning to Internet Protocol version 6 (IPv6) with a new addressing scheme that provides many more addresses.
An IP address identifies both a computer, a host in Internet terms, and the logical network on which the computer resides. This address allows messages to move from one network to another on the Internet. At the connecting point between networks, a special network device called a router uses its routing protocols to determine the route to the destination address before sending each packet along to the next router closer to the destination network. Each computer and network device that directly attach to the Internet must have a globally unique IP address. Both versions of IP have this much and more in common. Following are explanations of these addressing schemes to help you distinguish between them.
IPv4 Addresses An IPv4 address is 32 bits long, usually shown as four decimal numbers, 0 to 255, each separated by a period—for example, 192.168.1.41. Called dotted-decimal notation, this format is what you see in the user interface. However, the IPv4 protocol works with addresses in binary form, in which the preceding address looks like this: 11000000.10101000.00000001.00101001.
IPv4 addresses are routable because an IP address contains within it both the address of the host, called the host ID, and the address of the network on which that host resides, called the network ID (netID). A mask of 1s and 0s separates the two parts. When you put the mask over an address, the 1s cover up the first part, or network ID, and the 0s cover up the remaining part, or host ID. The address portion that falls under the 1s is the network address, and the address portion that falls under the 0s is the host address. In the preceding example, with a mask of 11111111.11111111.11111111.00000000, or 255.255.255.0, the network ID is 11000000.10101000.00000001.00000000 and the host ID is 00101001 (see Figure 16-4).
FIGURE 16-4
The subnet mask defines the network ID and host ID portions of an IP address.

In dotted-decimal form, the network ID is 192.168.1.0 and the host ID is 41. Often called a subnet mask, this mask is an important component in a proper IP configuration. After all, the IP address of a host does not make any sense until masked into its two IDs. When you enter the subnet mask into the Windows user interface in the Properties dialog box of the NIC, you will enter it in dotted-decimal notation, but we commonly use a shorthand notation when talking about the subnet mask, and you will see this notation in some user interfaces. For instance, a subnet mask of 255.255.255.0 is easily represented as /24. Therefore, using our example address from earlier, rather than saying the IP address is 192.168.1.41 with a subnet mask of 255.255.255.0, you can put it together as 192.168.1.41/24.

Be sure you understand how the subnet mask divides the host ID and network ID of an IP address. Also make sure that you understand the purpose of the following addresses as used in an IP configuration: default gateway, DNS server, and DHCP server.
IPv6 Addresses In preparation for the day when ISPs and the Internet routers are fully IPv6-ready, all modern Windows versions support both IPv6 and IPv4, as do most new network devices. In fact, some high-speed internetworks already use IPv6. IPv6 has 128-bit addressing, which theoretically supports a huge number of unique addresses—340,282,366,920,938,463,463,374,607,431,768,211,456 to be exact.
An IPv6 address is shown in eight groups of hexadecimal numbers separated by colons, such as this: 2002:470:B8F9:1:20C:29FF:FE53:45CA. Sometimes the address will contain a double colon (::)—for example, 2002:470:B8F9::29FF:FE53:45CA. This means there are consecutive groups of all 0s, so :: might be shorthand for :0000:0000:0000. Global unicast addresses, the public IPv6 addresses, have a prefix of 001.
IPv6 addresses use a network mask the same way IPv4 addresses do—to distinguish which portion of the address identifies the network. As is often done with IPv4, the mask is expressed with a front slash (/) and the number of bits in the mask; for example, 2002:470:B8F9:1:20C:29FF:FE53:45CA/64 implies a 64-bit network mask.
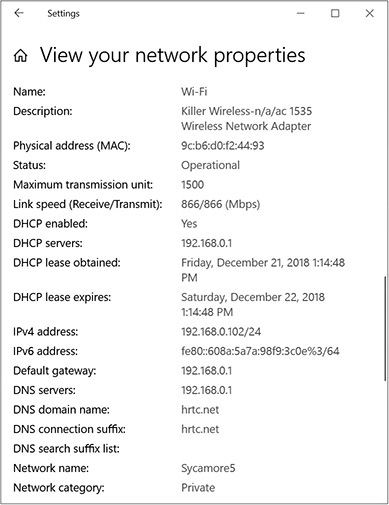
You can see both IPv4 and IPv6 data by using IPCONFIG at a command prompt or from a GUI interface. In Windows 10, click Start | Settings | Network & Internet | Status, and then scroll down in the right pane to the Change Your Network Settings section and click View Your Network Properties. See Figure 16-5. In Windows 11, click Start | Settings | Network & Internet | Properties.
FIGURE 16-5
Viewing your network’s properties in the Settings app in Windows 10
Addresses for IP Configuration
When you view the IP configuration for the NIC on your PC, you may be surprised to see other IP addresses besides that of the NIC. These include addresses labeled Default Gateway, DHCP Servers, and DNS Servers.
Default Gateway When your IP protocol has a packet ready to send, it examines the destination IP address and determines if it is on the same IP network (in the earlier example, this is 192.168.1.0) as your computer. If it is, then it can send the packet directly to that computer (host ID 41 in the example). If the destination IP address is on another IP network, then your computer sends it to the IP address identified as the default gateway. This address is on your network (same IP network ID), and it belongs to a router that will send the packet on to the next router in its journey to its destination. Without a default gateway, your computer does not know what to do with packets that have a destination address beyond your IP network. IPv6 also requires a default gateway setting to route packets to remote networks. This can be configured manually or delivered via a Dynamic Host Configuration Protocol (DHCP) device that supports IPv6.
DNS Server A DNS client uses the DNS server IP address for name resolution. The Domain Name System (DNS) manages access to Internet domain names, like mcgraw-hill.com. The server-side service maintains a database of domain names and responds to queries from DNS clients (called resolvers) that request resolution of Internet names to IP addresses. A client will do this before sending data over the Internet, when all it knows is the domain name. For instance, if you wish to connect to a McGraw Hill web server, you might enter www.mheducation.com in the address bar of your browser. Then, your computer’s DNS client (the resolver) sends a request to a DNS server, asking it to resolve the name to an IP address.
Once the DNS server has the answer (which it most likely had to request from another DNS server), it sends a response to your computer. The IP protocol on your computer now attaches the address to the packets your computer sends requesting a web page.
IPv4 clients query a DNS server for “A” records, which map to an IPv4 address. IPv6 clients query an IPv6 DNS server for “AAAA” (quad A) records to resolve names to IP addresses. Note that an IPv6 address (128 bits) is four times longer than an IPv4 address (32 bits)!
DNS also uses other records. For example, a mail exchange (MX) record is used to route e-mail messages to a mail server using Simple Mail Transfer Protocol (SMTP).

1101 exam Objective 2.6 lists A, AAAA, MX, and TXT as DNS configuration components. Make sure you understand the purpose of each.
Spam Management with DNS Another type of DNS record is Text (TXT). TXT records are used to send human-readable information about a server or network. 1101 Objective 2.6 lists only one use for TXT records: spam management. You add TXT records to your DNS server to help protect PCs against spamming, phishing, and other threats. Here are the specific record types the exam objective mentions:
![]() Domain Keys Identified Mail (DKIM) Signs messages with encryption to prevent your e-mail address from being spoofed by someone trying to send messages posing as you. It attaches a digital signature to your outgoing mail, which the receiving server can verify.
Domain Keys Identified Mail (DKIM) Signs messages with encryption to prevent your e-mail address from being spoofed by someone trying to send messages posing as you. It attaches a digital signature to your outgoing mail, which the receiving server can verify.
![]() Sender Policy Framework (SPF) Prevents attackers from using your domain to send spam by specifying which servers and domains are allowed to send e-mail.
Sender Policy Framework (SPF) Prevents attackers from using your domain to send spam by specifying which servers and domains are allowed to send e-mail.
![]() Domain-based Message Authentication, Reporting, and Conformance (DMARC) Provides instructions to receiving servers about how to handle messages that appear to come from your domain but don’t pass SPF or DKIM tests.
Domain-based Message Authentication, Reporting, and Conformance (DMARC) Provides instructions to receiving servers about how to handle messages that appear to come from your domain but don’t pass SPF or DKIM tests.

To add TXT records for your domain, sign into the site where you host your domain and use the administrative configuration tools there. The details will depend on the admin interface your host provides.
Assigning IP Addresses to NICs There are two ways to assign an IP address to a network host: manually (or statically) and automatically (or dynamically). We will discuss assigning an address manually here and automatically in the next section when we discuss DHCP. When you assign an address manually in Windows, you must open the Properties dialog box for the NIC and enter the exact IP address (obtained from your network administrator), subnet mask, and other configuration information, which includes the addresses for the default gateway and DNS server. An IP address configured in this manner is a static address. This address is not permanent, because an administrator can easily change it, but some documentation uses the term permanent rather than static.
DHCP Server When you install any non-server version of Windows, the Setup program installs the TCP/IP protocol suite and configures the computer (or its network card, to be more specific) as a DHCP client, meaning it configures it to obtain an IP address automatically from a DHCP server. A NIC configured as a DHCP client will send a request out on the network when Windows starts.
Now, you would think that a client computer without an IP address would not be able to communicate on the network, but it can in a very limited way. Using a special protocol called BOOTP, the computer sends a very small message that a Dynamic Host Configuration Protocol (DHCP) server can read. It cannot communicate with other types of servers until it has an IP address. A properly configured DHCP server will respond by sending the DHCP client an IP address and subnet mask (also using BOOTP). This configuration is the minimum it will assign to the client computer. In most cases, the server will provide the other IP configuration addresses, including the default gateway and DNS server.
A DHCP server does not permanently assign an IP address to a client. It leases it. Lease is the term used, even though no money changes hands in this transaction between a DHCP client and a DHCP server. When one half of the leased time for an IP address (and its associated configuration) has expired, the client tries to contact the DHCP server in order to renew the lease. As long as the DHCP server has an adequate number of unassigned IP addresses, it will continue to reassign the same address to the same client each session. In fact, this happens every day for a computer that is turned off at the end of the workday, at which point the DHCP client will release the IP address, giving up the lease.
The scope of a DHCP server is the range of addresses it can assign to clients on a certain subnet. Certain addresses may be reserved for certain devices, but outside of those reservations, clients requesting an IP address are assigned one from the available pool of addresses—and it may not be the same address each time.

Make sure you understand how a DHCP server leases IP addresses that are within its defined scope, honoring any address reservations that are configured in it.
Exercise 16-2 walks you through using a command that displays the physical address and IP address for your network card.
EXERCISE 16-2

Viewing the Physical and IP Addresses of a NIC
To view the physical and IP addresses of a NIC, follow these steps:
1. Open a command prompt.
2. In the Command Prompt window, enter the command ipconfig /all and press ENTER.
3. The result should look something like the following illustration, only with different addresses.
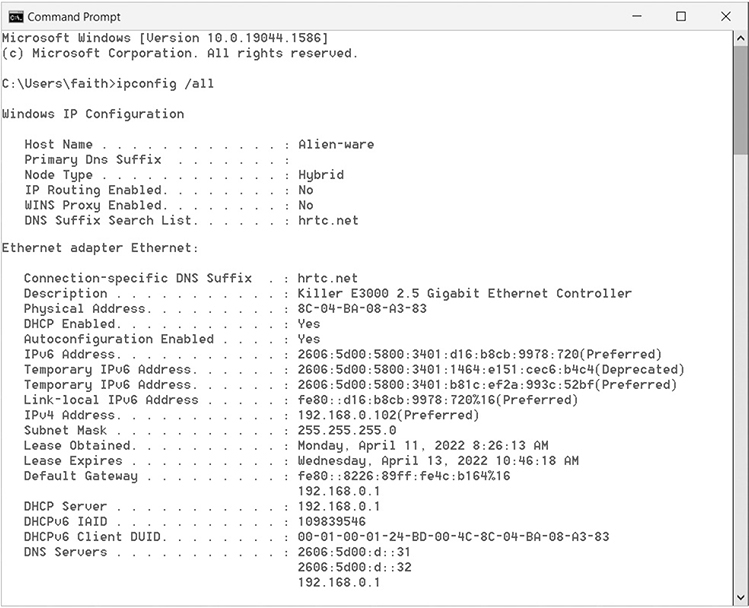
4. The address of the NIC is labeled Physical Address. Notice that the physical address is six pairs of hexadecimal numbers separated by hyphens.
5. Three lines below that is the NIC’s IPv6 address, and four lines below that is the IPv4 address.
6. Locate the other addresses discussed in the preceding text, including those of the default gateway, DNS servers, and DHCP server (if present).
Special IP Addresses You use public IP addresses on the Internet, and each address is globally unique. But there are some special IP addresses that are never allowed for computers and devices connected directly to the Internet. They are as follows:
![]() Loopback addresses Although it is generally believed that the address 127.0.0.1 is the IPv4 loopback address, any Class A address with a network ID of 127 is a loopback address, used to test network configurations. If you send a packet to a loopback address, it will not leave your NIC. Sounds like a useless address, but you will use it for testing and troubleshooting in Chapters 17 and 19. Also, note that the IPv6 loopback address is ::1 (0:0:0:0:0:0:0:1).
Loopback addresses Although it is generally believed that the address 127.0.0.1 is the IPv4 loopback address, any Class A address with a network ID of 127 is a loopback address, used to test network configurations. If you send a packet to a loopback address, it will not leave your NIC. Sounds like a useless address, but you will use it for testing and troubleshooting in Chapters 17 and 19. Also, note that the IPv6 loopback address is ::1 (0:0:0:0:0:0:0:1).
![]() Private IPv4 addresses If a network is not directly connected to the Internet, or if you wish to conceal the computers on a private network from the Internet, you use private IP addresses. Millions of locations all over the world use these addresses, and they are therefore not globally unique because they are never used on the Internet. In Chapter 17, we will describe how you can use these addresses on your private network, yet still access resources on the Internet, thanks to methods that hide your address when you are on the Internet.
Private IPv4 addresses If a network is not directly connected to the Internet, or if you wish to conceal the computers on a private network from the Internet, you use private IP addresses. Millions of locations all over the world use these addresses, and they are therefore not globally unique because they are never used on the Internet. In Chapter 17, we will describe how you can use these addresses on your private network, yet still access resources on the Internet, thanks to methods that hide your address when you are on the Internet.
![]() Private IPv6 addresses The FC00::/7 range has been set aside for private IPv6 network addressing. These addresses will not be routable by IPv6 Internet routers, but internal routers within an organization can route them much like they do IPv4 private addresses. The proper term for this type of address is a Unique Local Address (ULA).
Private IPv6 addresses The FC00::/7 range has been set aside for private IPv6 network addressing. These addresses will not be routable by IPv6 Internet routers, but internal routers within an organization can route them much like they do IPv4 private addresses. The proper term for this type of address is a Unique Local Address (ULA).
![]() Automatic Private IP Addressing (APIPA) address If a DHCP client computer fails to receive an address from a DHCP server, the client will give itself an address with the 169.254 /16 network ID. If a computer uses this range of addresses, it will not be able to communicate with other devices on the network unless they also have addresses using the same network ID, which means the other computers must also be using an APIPA address. These clients will not have a default gateway address and therefore will not be able to communicate beyond the local network. IPv6 behaves similarly, except that the self-assigned IPv6 address will have a prefix of FE80 and is always present, even if a routable IPv6 address was configured either statically or via DHCP. This is referred to as a “link local address.”
Automatic Private IP Addressing (APIPA) address If a DHCP client computer fails to receive an address from a DHCP server, the client will give itself an address with the 169.254 /16 network ID. If a computer uses this range of addresses, it will not be able to communicate with other devices on the network unless they also have addresses using the same network ID, which means the other computers must also be using an APIPA address. These clients will not have a default gateway address and therefore will not be able to communicate beyond the local network. IPv6 behaves similarly, except that the self-assigned IPv6 address will have a prefix of FE80 and is always present, even if a routable IPv6 address was configured either statically or via DHCP. This is referred to as a “link local address.”
Virtual LANs
Sometimes you might wish that physically separate LANs were all part of the same LAN, so you would operate on them as a group as a network administrator. A virtual LAN (VLAN) allows you to do just that. It enables devices from multiple wired and wireless networks to exist as a single logical network so you can administer them as a group.
To create a VLAN, all the routers and switches involved must support VLAN configuration. You’ll find VLAN controls in the router’s browser-based setup. The entire router or switch does not have to be on the same VLAN; you can set up individual ports on a switch to be part of a specific VLAN.

You don’t have to know the details of setting up a VLAN, but you should at least be able to explain what a VLAN is and why you would want one.
Common Ports
It isn’t enough for a packet to simply reach the correct IP address; each packet has additional destination information, called a port, which identifies the exact service it is targeting. For instance, when you want to open a web page in your browser, the packet requesting access to the web page includes both the IP address (resolved through DNS) and the port number of the service. In this case, it would be HTTP for many web pages and HTTPS for a secure web page where you must enter confidential information. All the services you access on the Internet have port numbers. These include the two services just mentioned, plus FTP, POP3, SMTP, Telnet, SSH, and many more. Each port is also associated with a protocol. The most common protocols for communicating with Internet applications are TCP and UDP. TCP is used for communications that are connection oriented, which is true of most services you are aware of using, whereas Universal Datagram Protocol (UDP) is used for connectionless communications, in which each packet is sent without establishing a connection. Therefore, in Table 16-1, we identify the protocol along with the port number for common TCP/IP services.
TABLE 16-1
Protocol and Port Numbers for Common Internet Services
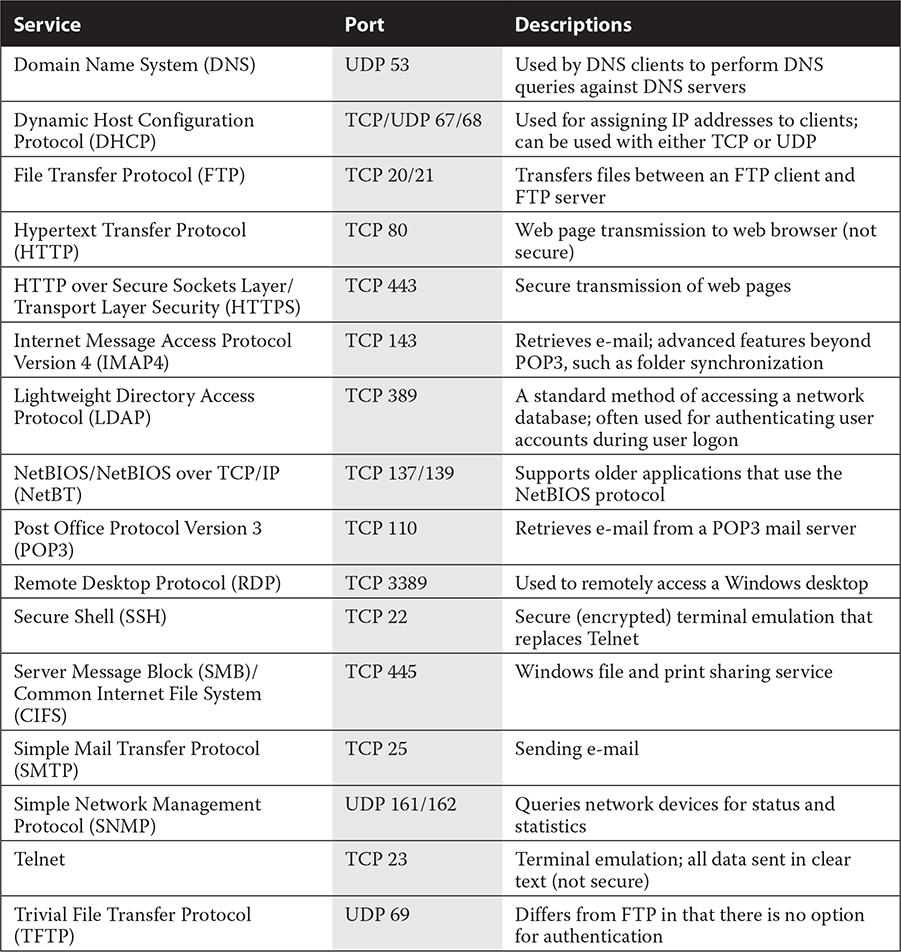

Make sure you understand that TCP is connection-oriented, whereas UDP is connectionless. DHCP can use either one. TFTP is an example of a port that always uses UDP, and HTTPS and SSH are examples of ports that always use TCP.

For the CompTIA A+ 220-1101 exam Objective 2.1, be sure you understand the common TCP and UDP ports and protocols mentioned in this section.

CompTIA A+ 220-1102 exam Objective 1.11 mentions Samba for Linux machines. Samba is an application suite that uses the SMB protocol to enable Linux machines to make network connections to Windows machines. You don’t need to know how to configure Samba, but you should know its purpose and be able to suggest it as a method of making such connections.
CERTIFICATION OBJECTIVES
![]() 1101: 2.2 Compare and contrast common networking hardware
1101: 2.2 Compare and contrast common networking hardware
![]() 1101: 2.3 Compare and contrast protocols for wireless networking
1101: 2.3 Compare and contrast protocols for wireless networking
![]() 1101: 3.1 Explain basic cable types and their connectors, features, and purposes
1101: 3.1 Explain basic cable types and their connectors, features, and purposes
In this section we will survey the various hardware devices used on networks—some of them for connecting networks to each other, and some for allowing client computers and devices to access networks. Knowledge of these is required for CompTIA A+ 1101 exam Objective 2.2. This discussion will also venture into the Wi-Fi networking standards implemented in wireless networking hardware, covered in CompTIA A+ 1101 exam Objective 2.3.
This section also covers the features and characteristics of network cabling, including fiber-optic, twisted-pair, and coaxial cabling, as well as their connectors, as required by CompTIA A+ 1101 exam Objective 3.1.
Network Hardware
Network hardware includes many network connection devices that are part of the infrastructure of small networks, as well as large internetworks, and of the largest internetwork, the Internet itself. We limit the hardware we describe in this section to the network adapters used in PCs, the medium that connects these adapters to the network, the devices that connect networks to one another, and a few miscellaneous devices included in the CompTIA A+ 220-1101 exam objectives.
Network Adapters
While we previously mentioned network interface cards (NICs) in this chapter, we now focus on this particular type of network hardware device. Each computer on a network must have a connection to the network provided by a NIC, also called a network adapter, and some form of network medium that makes the connection between the NIC and the network. NICs are identified by the network technology used (Ethernet or Wi-Fi) and the type of interface used between the NIC and the PC, such as the PCIe interface introduced in Chapter 8 or the USB interface defined in Chapter 9.
Most Ethernet NICs come with status indicators as lights on the card itself and/or software that displays the status on the notification area of the taskbar. You can use these when troubleshooting, as described in Chapter 19.
Transmission Media
The transmission medium for a network carries the signals. These signals may be electrical signals carried over copper-wire cabling, light pulses carried over fiber-optic cabling, or radio waves transmitted through the atmosphere. In these examples, the copper wire, fiber-optic cable, and atmosphere are the media. In this section, after an overview of cable in general, we’ll look at the basics of twisted-pair, coaxial, and fiber-optic cabling. We also look at Wi-Fi networking standards for wireless data transmission.
Cable Basics: What’s Inside a Cable?
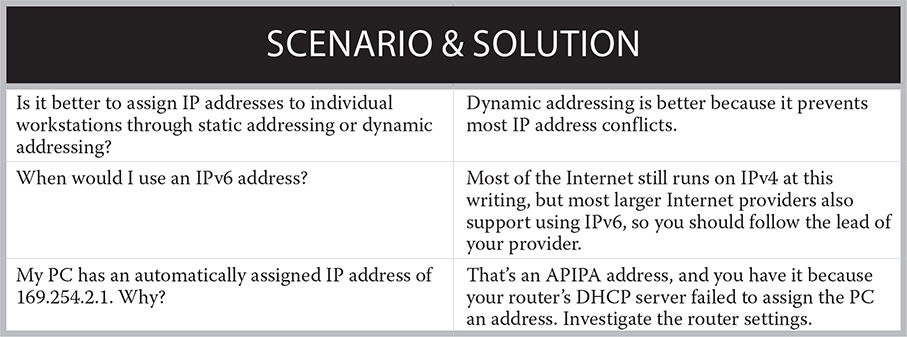
A wide variety of cables physically connect computer components and networks. These cables carry electronic signals for power, control of devices, and data. But what’s inside these cables? The basic cable types you will encounter are twisted-pair (shielded and unshielded), fiber-optic, and coaxial. All of these except fiber-optic are classified as copper cable.
A straight-pair cable consists of one or more metal wires surrounded by a plastic insulating sheath. A twisted-pair cable consists of two sheathed metal wires twisted around each other along the entire length of the cable to avoid electrical interference, with a plastic covering sheath surrounding it. A multicore twisted-pair cable has multiple pairs of twisted wires, but in practice even the multicore twisted-pair is simply called “twisted-pair.”

Copper cable includes unshielded twisted-pair categories (Cat 5, 5e, 6, and 6a), shielded twisted-pair, and coaxial.
A coaxial cable contains a single copper wire, surrounded by at least one insulating layer, a woven wire shield that provides both physical and electrical protection, and an outer jacket.
A fiber-optic cable has a core made of one or more optical fiber strands surrounded by a protective cladding, which is in turn reinforced by strength fibers; all of this is enclosed in an outer jacket. Fiber-optic cable carries light pulses rather than electrical signals, so it is not susceptible to electromagnetic interference (EMI).
Figure 16-6 displays these five basic cable types. We will revisit the use of various cables in future chapters.
FIGURE 16-6
Common cable types used to connect computer components and networks
Direct Burial Cable
Direct burial cable is cable that is buried underground outdoors, such as when running fiber-optic or coaxial cable from the street to a residence. Direct burial cable is extra sturdy, crush-resistant, and water-resistant, so it won’t degrade over time from the moisture and temperature fluctuations. Shielded twisted-pair and coaxial cable both come in direct burial versions.
Plenum vs. PVC
Many commonly used network cables use a polyvinyl chloride (PVC) outer sheath to protect the cable. PVC is not fire resistant, and, by code, you cannot use it in overhead or plenum areas in offices—those spaces in a building through which air conditioning and heating ducts run. Plenum cable uses a special fire-resistant outer sheath that will not burn as quickly as PVC. Plenum cable frequently costs more, but most areas require it. Most of the standard cables discussed in this chapter are available in plenum-grade ratings.

Remember that direct burial wire is required when running cables underground.

Do not confuse plenum cable, which has fire resistance, with shielded twisted-pair cable, which has electromagnetic resistance. Both are commonly run through ceilings, but for different reasons.
Twisted-Pair
Twisted-pair cable is the most popular cable type for internal networks. The term “twisted-pair” indicates that it contains pairs of wires twisted around each other. These twists help “boost” each wire’s signals and make them less susceptible to electromagnetic interference (EMI). The most common type of twisted-pair wiring is unshielded twisted-pair (UTP), which, although it has a plastic sheathing, does not have actual metal shielding.
There are several standards for twisted-pair cables, each with a different number of wires, certified speed, and implementation. We often refer to these standards as CAT (short for “category”) followed by a number. Currently, CAT 5, CAT 5e, CAT 6, and CAT 6a are the most common twisted-pair cable types. Table 16-2 summarizes twisted-pair cable standards. CAT 5e is an enhanced and more stringently tested version of CAT 5 that offers better transmission characteristics than CAT 5. CAT 6 and CAT 7 cable offer even higher bandwidth and improved signal-handling characteristics.
TABLE 16-2
Cable Categories
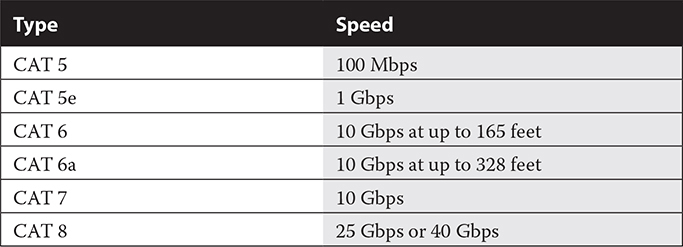

CAT 6 and CAT 6a are mostly the same, except Cat 6a is manufactured to tighter standards and uses thicker conductors and jackets, so it can reliably transmit at high speeds across greater distances.
The telecommunications standards organization, Telecommunication Industry Association/Electronics Industry Alliance (TIA/EIA), developed the TIA/EIA 568 standards for telecommunications cabling. TIA/EIA standards are now labeled per the standards group, the American National Standards Institute (ANSI), with an ANSI prefix. A portion of these standards, now called the ANSI/TIA/EIA-568-B standard, includes pin assignments for connecting eight-wire cabling to Ethernet connectors. One pin assignment is called T568A, and the other is T568B. Technically, as long as you standardize on one pin assignment, either is fine. However, T568B is recommended, and the use of T568A is only recommended if you want to create a cross-over cable, which you can accomplish by using the T568A standard on one end and the T568B standard on the other, as the main difference is in the assignment of the two wires that these two standards reverse.
According to the ANSI/TIA/EIA standard for CAT 5e copper cable (TIA/EIA 568-5-A), the maximum length for a structured wiring cable segment is 100 meters (328 feet) without need for a switch or a hub (repeater). With a repeater, you can run up to five segments for 10BaseT. For 100BaseT, you can use two hubs for a cable run of up to 200 meters (656 feet). Using modern switches with 100M and Gigabit LANs raises these limits. Consult the switch vendor’s specifications for details.
Twisted-pair cable is also available as shielded twisted-pair (STP), with an extra insulating layer that helps prevent data loss and blocks EMI. However, due to the expense of STP, UTP is more commonly used.
You can identify a twisted-pair cable by its use of RJ-45 connectors, which look like regular RJ-11 phone connectors but are slightly larger, as they contain eight wires, whereas RJ-11 connectors contain four wires.

The oldest cabling you should normally encounter in a business is CAT 5e, although it is certainly possible to find very old installations of CAT 5 or even CAT 3 cabling (used for regular analog telephone service), neither of which is adequate for modern networks.
Coaxial Cable
The type of cabling used to connect a cable modem to a cable network is coaxial cable, which consists of a central copper wire surrounded by an insulating layer, which is itself surrounded by a braided metal shield that protects the signals traveling on the central wire from outside interference. A plastic jacket encases all of this. Refer back to Figure 16-6.
Coaxial cable used for standard cable television and high-definition TV (HDTV), as well as cable-modem Internet access, is usually RG-6 cable with a 75-ohm rating. Theoretically, signals can travel up to 300 meters at 500 Mbps over RG-6 coax cables, but the practical limit is 50 Mbps, which still makes this medium very popular for broadband Internet connections. The specific distance and speed vary, depending on the type of signal and the devices generating the signal.
Expect an RG-6 cable to connect to the cable wall jack and cable modem with F-type connectors that you must securely screw on.
A splitter is a box that allows two cables to join to a single cable. Splitters are most common on coaxial cable, such as when splitting the incoming signal from a cable TV/Internet provider into two branches: one for the TV and one for the cable modem. Splitters do affect signal strength, so don’t use them unnecessarily. If you think that splitting may be degrading the signal to the point where errors are occurring, ask a service technician from the cable company to check the lines.

Splitters are also available for UTP cable, but you probably don’t want one. If you want to share a single incoming network signal with multiple devices, use a switch or router.
Fiber-Optic Cable and Connectors
Fiber-optic cable (fiber for short) has commonly been used to join separate networks over long distances, but until recently, LANs seldom used fiber-optic cable. Increasingly, however, many new homes, apartments, and businesses have both fiber and copper wiring installed when being built. Also, some phone companies are using fiber to connect directly to homes and businesses.
Fiber transmits light rather than electrical signals, so it is not susceptible to EMI. It is capable of faster transmission than other types of cable, but it is also the most expensive cable.
A single light wave passing down fiber cabling is a mode. Two variants of fiber used in fiber-optic cables are single-mode fiber (SMF) and multimode fiber (MMF). SMF allows only a single light wave to pass down the cable but supports faster transmission rates over longer distances. MMF allows multiple light waves to pass simultaneously and is usually larger in diameter than SMF; each wave uses a certain portion of the fiber cable for transmission. There are many Ethernet standards for fiber-optic cabling, with a wide range of maximum speeds and distances. MMF is used most often in LANs with speeds up to 1 Gbps and a maximum range of 1000 meters, whereas SMF has a range of dozens of miles with speeds in the terabits per second range.
Fiber-optic data transmission requires two cables: one to send and another to receive. Connectors enable fiber-optic cable to connect to transmitters, receivers, or other devices. Over the years, the various standards for connectors have continued to evolve, moving toward smaller connectors. Here are brief descriptions of three types of connectors used with fiber-optic cable:

You should be able to identify the following network-related connectors and explain their uses: F type, RJ11, RJ45, ST, SC, and LC.
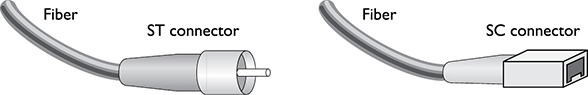
![]() Straight-tip (ST) A straight, round connector used to connect fiber to a network device. It has a twist-type coupling.
Straight-tip (ST) A straight, round connector used to connect fiber to a network device. It has a twist-type coupling.
![]() Subscriber connector (SC) A square snap coupling, about 2.5 mm wide, used for cable-to-cable connections or to connect cables to network devices. It latches with a push-pull action similar to audio and video jacks.
Subscriber connector (SC) A square snap coupling, about 2.5 mm wide, used for cable-to-cable connections or to connect cables to network devices. It latches with a push-pull action similar to audio and video jacks.
![]() Lucent connector (LC) Also called local connector, it has a snap coupling and, at 1.25 mm, is half the size of the SC connector.
Lucent connector (LC) Also called local connector, it has a snap coupling and, at 1.25 mm, is half the size of the SC connector.
Figure 16-7 shows ST and SC connectors.
FIGURE 16-7
The ST and SC connectors used with fiber-optic cable
Wireless Networking Standards
Wireless LAN (WLAN) communication (local area networking using radio frequency, or RF) is very popular. The most common wireless LAN implementations are based on the IEEE 802.11 group of standards, also called Wireless Fidelity (Wi-Fi). There are several 802.11 standards in use, and more have been proposed. These wireless standards use either 2.4-GHz or 5-GHz frequencies to communicate between systems. The range on these systems is relatively short, but they offer the advantage of not requiring cable for network connections.
Many public places, such as libraries, restaurants, and other businesses, offer free or pay access to Wi-Fi networks that connect to broadband Internet services. Such a point of connection to the Internet through a Wi-Fi network is called a hotspot. On an interesting twist on this concept, cellular providers and manufacturers of cellular-enabled mobile devices have cooperated to provide a newer type of service called a mobile hotspot. You can create a mobile hotspot (also called tethering) by connecting to the Internet with your smartphone’s cellular service and then using the smartphone’s Wi-Fi connectivity to allow other nearby Wi-Fi–enabled devices to share that Internet connection.

1101 exam Objective 2.3 lists all the 802.11 standards: a, b, g, n, ac (Wi-Fi 5), and ax (Wi-Fi 6). Make sure you can put them in order of oldest (slowest) to newest (fastest) and identify their maximum bandwidths and ranges.
Here is a brief description of several 802.11 standards and their features:
![]() 802.11a The 802.11a standard was developed by the IEEE at the same time as the slower 802.11b standard, but the “a” standard was more expensive to implement. Manufacturers therefore tended to make 802.11b devices. 802.11a uses the 5-GHz band, which makes 802.11a devices incompatible with 802.11b and the subsequent 802.11g devices. Because 802.11a devices do not provide downward compatibility with existing equipment using the 802.11b or newer 802.11g standards, they are seldom used. An 802.11a network has speeds up to 54 Mbps with a range of up to 150 feet.
802.11a The 802.11a standard was developed by the IEEE at the same time as the slower 802.11b standard, but the “a” standard was more expensive to implement. Manufacturers therefore tended to make 802.11b devices. 802.11a uses the 5-GHz band, which makes 802.11a devices incompatible with 802.11b and the subsequent 802.11g devices. Because 802.11a devices do not provide downward compatibility with existing equipment using the 802.11b or newer 802.11g standards, they are seldom used. An 802.11a network has speeds up to 54 Mbps with a range of up to 150 feet.
![]() 802.11b The 802.11b standard was the first widely popular version of Wi-Fi, with a speed of 11 Mbps and a range of up to 300 feet. Operating in the 2.4-GHz band that is also used by other noncomputer devices such as cordless phones and household appliances, these devices are vulnerable to interference if positioned near another device using the same portion of the radio spectrum.
802.11b The 802.11b standard was the first widely popular version of Wi-Fi, with a speed of 11 Mbps and a range of up to 300 feet. Operating in the 2.4-GHz band that is also used by other noncomputer devices such as cordless phones and household appliances, these devices are vulnerable to interference if positioned near another device using the same portion of the radio spectrum.
![]() 802.11g 802.11g replaced 802.11b. With a speed of up to 54 Mbps and a range of up to 300 feet, it also uses the 2.4-GHz radio band. 802.11g devices are normally downward compatible with 802.11b devices, although the reverse is not true.
802.11g 802.11g replaced 802.11b. With a speed of up to 54 Mbps and a range of up to 300 feet, it also uses the 2.4-GHz radio band. 802.11g devices are normally downward compatible with 802.11b devices, although the reverse is not true.
![]() 802.11n The 802.11n standard has speeds of up to 100+ Mbps and a maximum range of up to 600 feet. The standard defines speeds of up to 600 Mbps, which actual implementations do not achieve. MIMO (multiple input/multiple output) makes 802.11n speeds possible using multiple antennas to send and receive digital data in simultaneous radio streams that increase performance.
802.11n The 802.11n standard has speeds of up to 100+ Mbps and a maximum range of up to 600 feet. The standard defines speeds of up to 600 Mbps, which actual implementations do not achieve. MIMO (multiple input/multiple output) makes 802.11n speeds possible using multiple antennas to send and receive digital data in simultaneous radio streams that increase performance.
![]() 802.11ac The 802.11ac standard has multistation throughput of 1 Gbps and a single-link throughput of 500 Mbps. It accomplishes these higher speeds by using a wider RF bandwidth than 802.11n, more MIMO streams (up to eight), and high-density modulation. It can operate in both the 2.4-GHz and 5-GHz ranges, which allows for more available channels. It is also called Wi-Fi 5.
802.11ac The 802.11ac standard has multistation throughput of 1 Gbps and a single-link throughput of 500 Mbps. It accomplishes these higher speeds by using a wider RF bandwidth than 802.11n, more MIMO streams (up to eight), and high-density modulation. It can operate in both the 2.4-GHz and 5-GHz ranges, which allows for more available channels. It is also called Wi-Fi 5.
![]() 802.11ax The 802.11ax standard operates only in the 5-GHz range. It combines some advanced wireless techniques to achieve bandwidth improvements of up to 3.5 Gbps for a single stream (14 Gbps with four streams combined), while still maintaining backward compatibility with 802.11n and 802.11ac. It is also called Wi-Fi 6.
802.11ax The 802.11ax standard operates only in the 5-GHz range. It combines some advanced wireless techniques to achieve bandwidth improvements of up to 3.5 Gbps for a single stream (14 Gbps with four streams combined), while still maintaining backward compatibility with 802.11n and 802.11ac. It is also called Wi-Fi 6.

Although it’s not on the current exams, Wi-Fi 6e is now available, which uses the 6-GHz spectrum.
A frequency band such as 2.4 GHz is logically segmented into channels. A device will be configured to use a particular channel. You’ll learn more about channels in Chapter 17.

In 1101 exam Objective 2.3, channels 1 to 11 are referenced; those are the channels commonly used for the 2.4-GHz band.
When considering a wireless network, determining its speed and range can be nebulous at best. In spite of the maximums defined by the standards, many factors affect both speed and range. First, there is the limit of the standard, and then there is the distance between the wireless-enabled computer and the wireless access point (WAP), a network connection device at the core of a wireless network. Finally, there is the issue of interference, which can result from other wireless device signals operating in the same band or from physical barriers to the signals. In Chapter 17, you will learn about installing a WLAN to avoid interference and devices that will extend the range of the signals. You will also learn about the configuration options for wireless networks, including the use of identifiers for the wireless devices, secure encryption settings, and settings for keeping intruders out.

Be sure you understand that Wi-Fi alone does not give you a connection to the Internet, because it is a LAN technology. The reason people are able to connect to the Internet through a Wi-Fi connection is that the Wi-Fi network connects to a broadband connection through a device called a wireless router, a combination WAP and router.
Devices for Connecting to LANs and the Internet
Most LANs now connect to other LANs or through WAN connections to internetworks, such as the Internet. A variety of network connection devices connect networks. Each serves a special purpose, and a single device may contain two or more of these functions.
Repeater
A repeater is a device used to extend the range of a network by taking the signals it receives from one port and regenerating (repeating) those signals to another port. Repeaters are available for various networks. For instance, on an Ethernet network, you would use an Ethernet repeater, and on a Wi-Fi network you would use a wireless repeater (often called a signal booster) to boost the signal between wireless networks. In both cases, the repeater must be at the appropriate level and speed for the network.
Bridge
A bridge is a device used to connect two networks, and it passes traffic between them using the physical address of the destination device. Bridges segment large networks into smaller networks and only forward network traffic to the segment where the recipient station resides. A bridge is specific to the hardware technology in use. For instance, an Ethernet bridge looks at physical Ethernet addresses (MAC addresses) and forwards Ethernet frames with destination addresses that are not on the local network. Bridges are now seldom used, since a switch functions as both a bridge and a hub.
Optical Network Terminal
An optical network terminal (ONT) is a type of bridge that converts data from an optical network into a format that can be delivered using standard Ethernet cable. For a fiber to the home Internet installation, the ONT is typically mounted on the side of the home or in the garage. It may have a battery backup connected to it. An Ethernet cable then runs from the ONT to a wall jack in the home, to which you would connect your router.
Hub
A hub is a device that is the central connecting point of a classic Ethernet LAN. It is little more than a multiport repeater, because it takes a signal received on one port and repeats it on all other ports. An active hub will regenerate the signal and send it on to all devices connected to the network. A passive hub is simply a wiring panel or punchdown block for connecting or disconnecting devices.
Switch
After the introduction of 100BaseT, the switch replaced the classic hub. This is a more intelligent device that takes an incoming signal and sends it only to the destination port. This type of switch is both a bridge and a hub. At one time switches were very expensive, but now small eight-port switches are inexpensive and commonly used, even in very small LANs.
As always, each computer or other device in a network attaches to a switch of the type appropriate for the type of LAN. For example, computers using Ethernet cards must connect to an Ethernet switch; wireless devices attach wirelessly to a wireless hub, more often called a WAP or wireless router. Devices may combine these functions, as in the case of a WAP or wireless router that includes an Ethernet switch (look for one or more RJ-45 connectors). This last scenario is very common.
Switches can be either managed or unmanaged. An unmanaged switch has no configuration options and no interface with which to configure them. Managed switches enable you to control them by logging into them with a browser or some other method, such as an SNMP agent or a Telnet or Secure Shell (SSH) connection. There are two subclasses of managed switches. Smart switches (intelligent switches) have only a limited feature set and are used in small networks. Enterprise-managed switches have more options and are used in large business environments.
Router
Connections between networks usually require some form of routing capability. In the case of a connection to the Internet, each computer or device connected to the network requires a TCP/IP address. In order to reach a computer on another network, the originating computer must have a means of sending information to the other computer. To accomplish this, routes are established, and a router, a device that sits at the connection between networks, stores information about destinations.

You should be able to identify and compare common network hardware, including routers, switches, and access points, and explain how they perform different functions than Internet connection boxes such as cable and DSL modems.
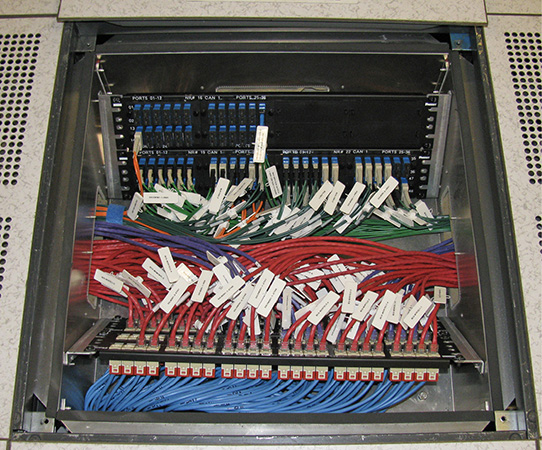
Patch Panels
In corporate networks with many clients, the sheer number of individual Ethernet cables running from individual PCs to routers is staggering. A patch panel can help keep the cable connections orderly by providing a central point into which the cables for many workstations can connect (see Figure 16-8). Some high-capacity switches also serve as patch panels, physically organizing a large number of cables, as well as distributing local network data.
FIGURE 16-8
A patch panel (Photo: https://commons.wikimedia.org/wiki/File:In_Floor_Patch_Panel_Fiber.jpg [Creative Commons license])
Power over Ethernet
Power over Ethernet (PoE) passes electrical power through twisted-pair Ethernet cabling. It allows one cable to serve as both data and electrical conduit to a device. It allows you to set up network devices in locations where there is no AC outlet and power them via the same Ethernet cable that connects them to the network. PoE is popular for use with security cameras, paging systems, wall clocks that get the time from the network, and routers placed in out-of-the-way locations.
A switch that supports PoE has power injection built in. In other words, it injects power into the cables that run to the PoE devices. A device called a midspan injector (or PoE injector) can be used to add PoE capability to regular non-PoE network switches and routers.
Wireless Access Point
A wireless access point, also called a WAP, allows wireless clients to connect to a wired network. Most access points also have built-in routing capability and, as such, are called wireless routers. Modern access points are configurable in “isolation mode,” which isolates wireless clients from one another, usually for security or privacy purposes.
Cable or DSL Modem
A cable modem (or DSL modem) is a communication box that sends/receives data between a cable or DSL ISP and a client’s local PC or network. Customers sometimes may buy their own boxes, but they are typically rented from the ISP and are swapped out for newer models as technology advances every few years to allow greater speeds.
Depending on the technology used for the Internet connection, there might or might not be translation between analog and digital, so technically these boxes may not be modems using the strictest definition of the term. Some people call them terminal adapters instead, which they insist is more accurate. Nevertheless, the terms cable modem and DSL modem are widely used.
Firewall
A firewall restricts or allows the flow of network traffic based on a set of rules. A firewall can be a hardware device or it can be software. Hardware firewalls run on network devices such as dedicated firewall appliances or routers or on a dedicated computer. Software firewalls run within an operating system and apply IP packet filtering, a service that inspects (or filters) each packet that enters or leaves the network; apply a set of security rules defined by a network administrator; and do not allow packets that fail inspection to pass between networks. When you change the rules to allow a certain type of traffic through a firewall, you are making an exception. To allow or deny traffic, you can base a firewall rule on many attributes, including
![]() Type of packet Defined by port; TCP 80 (HTTP website) or TCP 443 (HTTPS website) traffic might be allowed, whereas TCP 25 (SMTP outbound e-mail) traffic might be denied.
Type of packet Defined by port; TCP 80 (HTTP website) or TCP 443 (HTTPS website) traffic might be allowed, whereas TCP 25 (SMTP outbound e-mail) traffic might be denied.
![]() Source/destination SMTP traffic to a specific host might be allowed, but all other destination SMTP hosts could be denied.
Source/destination SMTP traffic to a specific host might be allowed, but all other destination SMTP hosts could be denied.
Firewalls are also covered in Chapter 22.
EXERCISE 16-3
Identifying Network Hardware
See what network hardware you can identify in your home, office, or school.
1. If you have a PC in your home and it has a connection to the Internet, locate and identify the network components.
2. If you use a dial-up connection, look for the modem, the telephone cable between the modem and the phone jack on the wall, and the RJ-11 connectors at either end of the telephone cable.
3. If you have a DSL connection, look for the Ethernet cable that runs between your computer and the hub/switch or modem. Examine the RJ-45 connectors on either end of the cable. The cable may connect to a single box that performs all of these functions.
4. If you have cable Internet service, look for an Ethernet cable between your computer and the cable modem, and then look for a coaxial cable between the modem and the wall connector.
5. At school or work, all you may find is an Ethernet cable connecting your computer to a wall jack that connects to the cable in the walls that connects to the network. Ask the network administrator to describe how you connect to the Internet through the network.
Software-Defined Networking
As Internet connectivity becomes faster and more reliable, some companies are turning to software-defined networking (SDN), a cloud-based solution for networking. It pushes much of the network routing and management functions to cloud services to enable secure connectivity between branch offices and buildings more inexpensively and reliably than a business could set up using their own hardware. Nearly any network function that can be achieved via local hardware can be done using SDN. Chapter 18 looks at cloud services in more detail.

A+ 1101 exam Objective 2.2 includes the term software-defined networking. Make sure you understand that some aspects of a network can be managed via software as an alternative to local hardware systems.
CERTIFICATION SUMMARY
IT professionals preparing for the CompTIA A+ 220-1101 and 220-1102 exams must understand the basic concepts of computer networks. More in-depth knowledge is required for other exams, such as the CompTIA Network+, Security+, and Server+ exams. Basic concepts include network topologies—the geographic classifications of networks into PANs, LANs, MANs, and WANs. You must also understand Internet connection methods, such as fiber, cable, DSL, and satellite. Be able to identify the most common cabling types, connectors, and common network adapters used in PCs.
Understand that TCP/IP is a protocol suite designed for the Internet and now used on most LANs and interconnected networks. Understand network-addressing concepts, including physical addresses assigned to network adapters and logical addresses assigned and used through the network protocols.
Understand the various addresses that are part of an IP configuration and their roles. These include the IP address and subnet mask of the network adapter, default gateway, and DNS server and DHCP server addresses and functions.
Be prepared to distinguish between various network hardware, including adapters, the transmission medium, network-to-network connection devices, and devices for connecting computers to a network (hubs and switches).
 TWO-MINUTE DRILL
TWO-MINUTE DRILL
Here are some of the key points covered in Chapter 16.
Network Classifications
![]() Networks fall into several classifications, including PAN, LAN, MAN, WAN, and SAN.
Networks fall into several classifications, including PAN, LAN, MAN, WAN, and SAN.
![]() PAN technologies include the use of standards for wireless transmissions over very short distances. These include infrared (IR/IrDA), limited to about 1 meter, and Bluetooth, which has a range of up to 10 meters.
PAN technologies include the use of standards for wireless transmissions over very short distances. These include infrared (IR/IrDA), limited to about 1 meter, and Bluetooth, which has a range of up to 10 meters.
![]() A LAN is a network that covers a building, home, office, or campus. Common LAN technologies include Ethernet in wired LANs and Wi-Fi in wireless LANs.
A LAN is a network that covers a building, home, office, or campus. Common LAN technologies include Ethernet in wired LANs and Wi-Fi in wireless LANs.
![]() A MAN covers a metropolitan area and generally uses fiber-optic cable.
A MAN covers a metropolitan area and generally uses fiber-optic cable.
![]() A WAN covers a large geographic area, connecting networks across long distances. A WWAN is a wireless WAN.
A WAN covers a large geographic area, connecting networks across long distances. A WWAN is a wireless WAN.
![]() A SAN is a data network that connects and manages large-scale storage devices.
A SAN is a data network that connects and manages large-scale storage devices.
![]() Dial-up WAN connections are the slowest and require initiation of the connection every time a user wishes to connect to a remote resource.
Dial-up WAN connections are the slowest and require initiation of the connection every time a user wishes to connect to a remote resource.
Internet Connection Types
![]() Bandwidth and latency are two important evaluative factors for Internet and network connections.
Bandwidth and latency are two important evaluative factors for Internet and network connections.
![]() Fiber is fast and reliable but is not available in all areas.
Fiber is fast and reliable but is not available in all areas.
![]() Cable Internet is also fast, but you have to share the bandwidth with your neighbors.
Cable Internet is also fast, but you have to share the bandwidth with your neighbors.
![]() DSL is an older technology, not as fast, that uses copper telephone lines.
DSL is an older technology, not as fast, that uses copper telephone lines.
![]() Satellite Internet is available almost anywhere but has high latency and tends to be more expensive than other options.
Satellite Internet is available almost anywhere but has high latency and tends to be more expensive than other options.
Network Software and Protocols
![]() The roles played by the computer on the network describe the network. The two most general roles are those of clients and servers.
The roles played by the computer on the network describe the network. The two most general roles are those of clients and servers.
![]() A network in which any computer can be both a client and a server is a peer-to-peer network. A client/server network is one in which most desktop computers are clients and dedicated computers act as servers.
A network in which any computer can be both a client and a server is a peer-to-peer network. A client/server network is one in which most desktop computers are clients and dedicated computers act as servers.
![]() A protocol suite is a group of related protocols that work together to support the functioning of a network. TCP/IP is the dominant protocol suite, as well as the protocol suite of the Internet.
A protocol suite is a group of related protocols that work together to support the functioning of a network. TCP/IP is the dominant protocol suite, as well as the protocol suite of the Internet.
![]() TCP/IP is a suite of protocols used for most networks today, including the Internet. Its two main protocols are TCP and IP.
TCP/IP is a suite of protocols used for most networks today, including the Internet. Its two main protocols are TCP and IP.
![]() TCP is a connection-oriented protocol used for transmissions where receipt must be verified. UDP is a connectionless protocol used for transmission where no verification of receipt is required.
TCP is a connection-oriented protocol used for transmissions where receipt must be verified. UDP is a connectionless protocol used for transmission where no verification of receipt is required.
![]() Network addressing occurs at both the physical level and the logical level. Every Ethernet network adapter from every Ethernet NIC manufacturer in the world has a unique physical address, also called a MAC address, which is 48 bits long and is usually shown in hexadecimal notation.
Network addressing occurs at both the physical level and the logical level. Every Ethernet network adapter from every Ethernet NIC manufacturer in the world has a unique physical address, also called a MAC address, which is 48 bits long and is usually shown in hexadecimal notation.
![]() Internet Protocol is concerned with logical addresses. An IPv4 address is 32 bits long and is usually shown in dotted-decimal notation, as in 192.168.1.41. IPv6 has 128-bit addressing, which theoretically supports a huge number of unique addresses.
Internet Protocol is concerned with logical addresses. An IPv4 address is 32 bits long and is usually shown in dotted-decimal notation, as in 192.168.1.41. IPv6 has 128-bit addressing, which theoretically supports a huge number of unique addresses.
![]() An IPv4 and IPv6 address configuration includes a subnet mask, which determines the host ID and network ID portions of the address. In addition, the IP configuration may include addresses for a default gateway, DNS server, and DHCP server.
An IPv4 and IPv6 address configuration includes a subnet mask, which determines the host ID and network ID portions of the address. In addition, the IP configuration may include addresses for a default gateway, DNS server, and DHCP server.
![]() Items that have IP addresses assigned to them include the NIC, default gateway, DHCP server, and DNS servers. IP addresses can be assigned in a static or dynamic way.
Items that have IP addresses assigned to them include the NIC, default gateway, DHCP server, and DNS servers. IP addresses can be assigned in a static or dynamic way.
![]() DNS servers store information in records. A records map to IPv4 addresses, and AAAA records map to IPv6 addresses. MX records route e-mail messages. DNS server records can be used for spam management via DKIM, SPF, and DMARC.
DNS servers store information in records. A records map to IPv4 addresses, and AAAA records map to IPv6 addresses. MX records route e-mail messages. DNS server records can be used for spam management via DKIM, SPF, and DMARC.
![]() A DHCP server dynamically assigns IP addresses. It leases an address to a device, within its defined scope, honoring any address reservations.
A DHCP server dynamically assigns IP addresses. It leases an address to a device, within its defined scope, honoring any address reservations.
![]() Special IP addresses include loopback, private addresses, and APIPA addresses. APIPA addresses are assigned if the client computer fails to receive an address from a DHCP server.
Special IP addresses include loopback, private addresses, and APIPA addresses. APIPA addresses are assigned if the client computer fails to receive an address from a DHCP server.
![]() A virtual LAN enables devices from multiple networks to exist as a single logical network.
A virtual LAN enables devices from multiple networks to exist as a single logical network.
![]() In addition to an IP address, a packet will contain a port number identifying the service on the target computer that should receive the packet’s contents. You should be familiar with the port numbers for common networking services.
In addition to an IP address, a packet will contain a port number identifying the service on the target computer that should receive the packet’s contents. You should be familiar with the port numbers for common networking services.
Network Hardware
![]() A network adapter provides the connection to the network medium. Network adapters (network interface cards) are available for the various networking technologies, such as Ethernet and Wi-Fi.
A network adapter provides the connection to the network medium. Network adapters (network interface cards) are available for the various networking technologies, such as Ethernet and Wi-Fi.
![]() Physical transmission media include twisted-pair, fiber-optic, and coaxial cable. UTP cable is categorized (CAT 5e, CAT 6, and so on). TIA/EIA T568A and T568B are wiring standards for twisted-pair cable.
Physical transmission media include twisted-pair, fiber-optic, and coaxial cable. UTP cable is categorized (CAT 5e, CAT 6, and so on). TIA/EIA T568A and T568B are wiring standards for twisted-pair cable.
![]() Coaxial cable is usually RG-6, with an F type connector. Fiber-optic cable can be single-mode or multimode, and can use an ST, SC, or LC connector.
Coaxial cable is usually RG-6, with an F type connector. Fiber-optic cable can be single-mode or multimode, and can use an ST, SC, or LC connector.
![]() Special-purpose cables include direct burial and plenum.
Special-purpose cables include direct burial and plenum.
![]() Wireless networking standards are governed by IEEE 802.11. Common standards within that specification are 802.11a, b, g, n, ac, and ax.
Wireless networking standards are governed by IEEE 802.11. Common standards within that specification are 802.11a, b, g, n, ac, and ax.
![]() A repeater is a device used to extend the range of a network by taking the signals it receives from one port and regenerating (repeating) those signals to another port.
A repeater is a device used to extend the range of a network by taking the signals it receives from one port and regenerating (repeating) those signals to another port.
![]() A bridge is a device used to connect two networks and pass traffic between them based on the physical address of the destination device. An ONT is a bridge used to connect a fiber network to a copper wire network.
A bridge is a device used to connect two networks and pass traffic between them based on the physical address of the destination device. An ONT is a bridge used to connect a fiber network to a copper wire network.
![]() A hub is a device that is the central connecting point of an old LAN, with all network devices on a LAN connecting to one or more hubs. More intelligent devices called switches or switching hubs now replace hubs on Ethernet networks. These take an incoming signal and send it only to the destination port.
A hub is a device that is the central connecting point of an old LAN, with all network devices on a LAN connecting to one or more hubs. More intelligent devices called switches or switching hubs now replace hubs on Ethernet networks. These take an incoming signal and send it only to the destination port.
![]() A router sits between networks and routes packets according to their IP addresses. Many routers combine routing and bridging and connect multiple network technologies, such as a LAN and a WAN.
A router sits between networks and routes packets according to their IP addresses. Many routers combine routing and bridging and connect multiple network technologies, such as a LAN and a WAN.
![]() A patch panel is like a switchboard for networking connections, helping to organize cables.
A patch panel is like a switchboard for networking connections, helping to organize cables.
![]() Power over Ethernet (PoE) enables you to deliver power to devices through the same network cable that carries its data. A midspan injector can add PoE capability to non-PoE equipment.
Power over Ethernet (PoE) enables you to deliver power to devices through the same network cable that carries its data. A midspan injector can add PoE capability to non-PoE equipment.
![]() A wireless access point (WAP) is a wireless switch.
A wireless access point (WAP) is a wireless switch.
![]() A cable or DSL modem is a box that communicates between an ISP and the client’s local network or PC.
A cable or DSL modem is a box that communicates between an ISP and the client’s local network or PC.
![]() A firewall is hardware or software that restricts the flow of network traffic based on a set of rules.
A firewall is hardware or software that restricts the flow of network traffic based on a set of rules.
![]() Software-defined networking (SDN) uses cloud services to handle network routing and management functions.
Software-defined networking (SDN) uses cloud services to handle network routing and management functions.
Q SELF TEST
The following questions will help you measure your understanding of the material presented in this chapter. Read all the choices carefully because there might be more than one correct answer. Choose all correct answers for each question.
Network Classifications
1. Which type of network enables two laptops in the same room to share files?
A. PAN
B. LAN
C. MAN
D. WAN
2. Which of the following statements is true about a LAN versus a WAN?
A. A LAN spans a greater distance than a WAN.
B. A WAN spans a greater distance than a LAN.
C. A LAN is generally slower than a WAN.
D. A WAN is used within a home or within a small business.
3. Which of the following is a PAN technology?
A. Ethernet
B. Satellite
C. Bluetooth
D. 802.11
4. What is the type of network that connects many private networks in one metropolitan community?
A. PAN
B. MAN
C. WAN
D. LAN
Internet Connection Types
5. Which of the following uses copper telephone lines for Internet service?
A. Fiber
B. DSL
C. Cable
D. Satellite
6. Which of the following Internet connection methods uses light rather than electricity to send and receive data?
A. Fiber
B. DSL
C. Cable
D. Satellite
7. Which of the following Internet connection types uses a network originally created for television transmissions?
A. DSL
B. Cellular
C. Cable
D. Fiber
8. Which of the following is a term that describes the amount of data that can travel over a network within a given time?
A. Bandwidth
B. Kilobits
C. Latency
D. IPv4
9. Which of the following is a term that describes the amount of time it takes a packet to travel from one point to another?
A. Bandwidth
B. Mbps
C. Latency
D. UDP
Network Software and Protocols
10. Which statement describing IPv4 versus IPv6 differences is correct?
A. IPv6 uses a subnet mask, while IPv4 uses 128-bit addressing.
B. IPv4 uses 128-bit addressing, while IPv6 uses 32-bit addressing.
C. IPv4 uses 32-bit addressing, while IPv6 uses 128-bit addressing.
D. IPv4 uses double colons to indicate consecutive groups of 0s.
11. Which port is the correct one for Hypertext Transfer Protocol (HTTP) and web page transmission to a browser?
A. TCP 80
B. UDP 53
C. TCP 443
D. TCP 110
12. What protocol used on the Internet is concerned with the logical addressing of hosts?
A. TCP
B. IP
C. UDP
D. MAC
13. What protocol adds the old Microsoft naming system to TCP/IP?
A. Fiber
B. NetBIOS
C. DHCP
D. DNS
14. What divides an IP address into its host ID and network ID components?
A. Default gateway
B. DNS server
C. DHCP server
D. Subnet mask
15. A NIC has this type of a permanent address assigned to it by the manufacturer.
A. IP address
B. Physical address
C. Host ID
D. Automatic address
16. A packet with a destination address not on the local network will be sent to the address identified by which label in the IP configuration?
A. Default gateway
B. DNS server
C. DHCP server
D. Subnet mask
Network Hardware
17. Which of the following statements is correct?
A. CAT 5 cable can transmit 1 Gbps.
B. CAT 6 cable can transmit 10 Gbps.
C. CAT 5, CAT 5e, and CAT 6 segments can all be a maximum of 200 meters long.
D. CAT 5e cable can transmit 10 Gbps.
18. Which of the following is not a network medium?
A. Plenum
B. Twisted-pair cable
C. Fiber-optic cable
D. Atmosphere
19. Which type of cable uses ST, SC, or LC connectors?
A. STP
B. UTP
C. Fiber-optic
D. Coaxial
20. Thousands of this type of device exist on the Internet between networks, direct the traffic of the Internet using the destination IP address of each packet, and pass the packets to their destinations along the interconnected networks of the Internet.
A. Router
B. Modem
C. NIC
D. Hub
A SELF TEST ANSWERS
Network Classifications
1. ![]() B. A local area network (LAN) enables devices in the same building or room to share files.
B. A local area network (LAN) enables devices in the same building or room to share files.
![]() A is incorrect because a PAN is used to connect peripherals to computers wirelessly at very short range. C is incorrect because a MAN is a network within a city or metro area. D is incorrect because a WAN is a network with a large geographical area.
A is incorrect because a PAN is used to connect peripherals to computers wirelessly at very short range. C is incorrect because a MAN is a network within a city or metro area. D is incorrect because a WAN is a network with a large geographical area.
2. ![]() B. A WAN spans a greater distance than a LAN.
B. A WAN spans a greater distance than a LAN.
![]() A, C, and D are incorrect because they are not true.
A, C, and D are incorrect because they are not true.
3. ![]() C. Bluetooth is a personal area network (PAN) technology used to connect devices and computers over very short distances.
C. Bluetooth is a personal area network (PAN) technology used to connect devices and computers over very short distances.
![]() A, B, and D are incorrect because none of these is a PAN technology. Ethernet is a wired LAN technology, satellite is a WAN technology, and 802.11 is a set of WLAN standards.
A, B, and D are incorrect because none of these is a PAN technology. Ethernet is a wired LAN technology, satellite is a WAN technology, and 802.11 is a set of WLAN standards.
4. ![]() B. MAN, a metropolitan area network, is the type of network that connects many private networks in one community.
B. MAN, a metropolitan area network, is the type of network that connects many private networks in one community.
![]() A is incorrect because a PAN is a personal area network that only connects devices in a very small area (usually a few meters). C is incorrect because a wide area network connects over long distances. D is incorrect because a local area network is limited to a distance of hundreds of meters and would not span an entire metropolitan community.
A is incorrect because a PAN is a personal area network that only connects devices in a very small area (usually a few meters). C is incorrect because a wide area network connects over long distances. D is incorrect because a local area network is limited to a distance of hundreds of meters and would not span an entire metropolitan community.
Internet Connection Types
5. ![]() B. DSL uses copper telephone lines.
B. DSL uses copper telephone lines.
![]() A is incorrect because fiber uses fiber-optic cable. C is incorrect because cable uses coaxial cable shared with TV cable service. D is incorrect because satellite uses a satellite dish with a transmitter.
A is incorrect because fiber uses fiber-optic cable. C is incorrect because cable uses coaxial cable shared with TV cable service. D is incorrect because satellite uses a satellite dish with a transmitter.
6. ![]() A. Fiber uses fiber-optic cable, which transmits data via light.
A. Fiber uses fiber-optic cable, which transmits data via light.
![]() B and C are incorrect because DSL and cable both use copper wire. D is incorrect because satellite transfers data wirelessly.
B and C are incorrect because DSL and cable both use copper wire. D is incorrect because satellite transfers data wirelessly.
7. ![]() C. Cable Internet uses the same coaxial cable used for television transmissions.
C. Cable Internet uses the same coaxial cable used for television transmissions.
![]() A is incorrect because DSL uses the same twisted-pair cable used for telephone. B is incorrect because cellular Internet uses cell phone towers. D is incorrect because fiber uses fiber-optic data lines.
A is incorrect because DSL uses the same twisted-pair cable used for telephone. B is incorrect because cellular Internet uses cell phone towers. D is incorrect because fiber uses fiber-optic data lines.
8. ![]() A. Bandwidth is the amount of data that can travel over a network within a given time.
A. Bandwidth is the amount of data that can travel over a network within a given time.
![]() B is incorrect because kilobits is a measurement of thousands of bits. C is incorrect because latency describes the amount of travel time for a packet. D is incorrect because IPv4 is the standard governing IP addressing.
B is incorrect because kilobits is a measurement of thousands of bits. C is incorrect because latency describes the amount of travel time for a packet. D is incorrect because IPv4 is the standard governing IP addressing.
9. ![]() C. Latency is the term for the time it takes a packet to travel from one point to another.
C. Latency is the term for the time it takes a packet to travel from one point to another.
![]() A is incorrect because bandwidth is the amount of data that can travel over a network within a given time. B is incorrect because Mbps is a measurement of millions of bits per second. D is incorrect because UDP is a type of connectionless protocol.
A is incorrect because bandwidth is the amount of data that can travel over a network within a given time. B is incorrect because Mbps is a measurement of millions of bits per second. D is incorrect because UDP is a type of connectionless protocol.
Network Software and Protocols
10. ![]() C. IPv4 uses 32-bit addressing, while IPv6 uses 128-bit addressing.
C. IPv4 uses 32-bit addressing, while IPv6 uses 128-bit addressing.
![]() A is incorrect because IPv4 uses 32-bit addressing. IPv6 can use a subnet mask also. B is incorrect because it is just the opposite. D is incorrect because it is IPv6 that uses the double colons to indicate consecutive groups of 0s.
A is incorrect because IPv4 uses 32-bit addressing. IPv6 can use a subnet mask also. B is incorrect because it is just the opposite. D is incorrect because it is IPv6 that uses the double colons to indicate consecutive groups of 0s.
11. ![]() A. TCP 80 is the correct port number for HTTP and web page transmission to a web browser.
A. TCP 80 is the correct port number for HTTP and web page transmission to a web browser.
![]() B is incorrect because UDP 53 is the port for Domain Name System used by clients to perform DNS queries against DNS servers. C is incorrect because TCP 443 is the port used by HTTPS for secure web page transmission. D is incorrect because TCP 110 is the port for Post Office Protocol that retrieves e-mail from a POP3 mail server.
B is incorrect because UDP 53 is the port for Domain Name System used by clients to perform DNS queries against DNS servers. C is incorrect because TCP 443 is the port used by HTTPS for secure web page transmission. D is incorrect because TCP 110 is the port for Post Office Protocol that retrieves e-mail from a POP3 mail server.
12. ![]() B. IP is the protocol used on the Internet that is concerned with the logical addressing of hosts.
B. IP is the protocol used on the Internet that is concerned with the logical addressing of hosts.
![]() A, C, and D are incorrect because these are not concerned with the logical addressing of hosts.
A, C, and D are incorrect because these are not concerned with the logical addressing of hosts.
13. ![]() B. NetBIOS is the protocol that adds the old Microsoft naming system to TCP/IP.
B. NetBIOS is the protocol that adds the old Microsoft naming system to TCP/IP.
![]() A is incorrect because fiber is a cable type. C is incorrect because DHCP is the protocol used for automatically allocating IP addresses. D is incorrect because DNS is the protocol that supports Internet-style names.
A is incorrect because fiber is a cable type. C is incorrect because DHCP is the protocol used for automatically allocating IP addresses. D is incorrect because DNS is the protocol that supports Internet-style names.
14. ![]() D. A subnet mask divides an IP address into its host ID and network ID components.
D. A subnet mask divides an IP address into its host ID and network ID components.
![]() A is incorrect because the default gateway is the name of the router address to which a computer directs packets with destinations beyond the local network. B is incorrect because the DNS server is where a network client sends queries to resolve DNS names into IP addresses. C is incorrect because the DHCP server is what automatically assigns IP addresses to DHCP client computers.
A is incorrect because the default gateway is the name of the router address to which a computer directs packets with destinations beyond the local network. B is incorrect because the DNS server is where a network client sends queries to resolve DNS names into IP addresses. C is incorrect because the DHCP server is what automatically assigns IP addresses to DHCP client computers.
15. ![]() B. The physical address is the type of permanent address assigned to a NIC by the manufacturer.
B. The physical address is the type of permanent address assigned to a NIC by the manufacturer.
![]() A is incorrect because an IP address is not a permanent address, but a logical address not permanently assigned to a NIC. C is incorrect because the host ID is the portion of an IP address that identifies the host. D is incorrect because an automatic address usually refers to an IP address assigned to a PC by a DHCP server.
A is incorrect because an IP address is not a permanent address, but a logical address not permanently assigned to a NIC. C is incorrect because the host ID is the portion of an IP address that identifies the host. D is incorrect because an automatic address usually refers to an IP address assigned to a PC by a DHCP server.
16. ![]() A. The default gateway is the address to which the router sends packets that have addresses not on the local network.
A. The default gateway is the address to which the router sends packets that have addresses not on the local network.
![]() B is incorrect because this server resolves DNS names. C is incorrect because the DHCP server assigns IP addresses automatically. D is incorrect because a subnet mask is not an address, but a mask used to divide an IP address into its host ID and network ID components.
B is incorrect because this server resolves DNS names. C is incorrect because the DHCP server assigns IP addresses automatically. D is incorrect because a subnet mask is not an address, but a mask used to divide an IP address into its host ID and network ID components.
Network Hardware
17. ![]() B. CAT 6 can indeed transmit 10 Gbps.
B. CAT 6 can indeed transmit 10 Gbps.
![]() A is incorrect because CAT 5 can only transmit 100 Mbps. C is incorrect because each of these cable categories requires a repeater or a switch at 100 meters. D is incorrect because CAT 5e can only transmit 1 Gbps.
A is incorrect because CAT 5 can only transmit 100 Mbps. C is incorrect because each of these cable categories requires a repeater or a switch at 100 meters. D is incorrect because CAT 5e can only transmit 1 Gbps.
18. ![]() A. Plenum is not a network medium, but rather a characteristic of certain network media (cables), indicating the cable sheath is fire resistant and appropriate to run in plenum space.
A. Plenum is not a network medium, but rather a characteristic of certain network media (cables), indicating the cable sheath is fire resistant and appropriate to run in plenum space.
![]() B, C, and D are incorrect because all are networking media.
B, C, and D are incorrect because all are networking media.
19. ![]() C. Fiber-optic cable uses ST, SC, or LC connectors.
C. Fiber-optic cable uses ST, SC, or LC connectors.
![]() A, B, and D are incorrect because they do not use ST, SC, or LC connectors.
A, B, and D are incorrect because they do not use ST, SC, or LC connectors.
20. ![]() A. A router is the device that exists on the Internet and passes IP packets from many sources to destinations along the Internet.
A. A router is the device that exists on the Internet and passes IP packets from many sources to destinations along the Internet.
![]() B is incorrect because a modem does not pass packets along the Internet, although it is a beginning point for a single computer to send packets. C is incorrect because a network interface card (NIC) is simply a device for connecting a single computer to a network. D is incorrect because a hub is an older device used at the heart of a LAN, but not an Internet device.
B is incorrect because a modem does not pass packets along the Internet, although it is a beginning point for a single computer to send packets. C is incorrect because a network interface card (NIC) is simply a device for connecting a single computer to a network. D is incorrect because a hub is an older device used at the heart of a LAN, but not an Internet device.
