THIS CHAPTER TAKES A DEEP LOOK into computer networking, with a review of networking fundamentals. From this foundation, the chapter will then explore how wireless networking relates to the broader topic of networking in general. You will find that the specifications that define wireless networking are but a small fraction of the broader networking picture. You will also find, however, that the effects of wireless networking from a business, social, economic, and security perspective are disproportionally large.
Chapter 2 Topics
This chapter covers the following concepts and topics:
• What the origin, purpose, and function of the OSI Reference Model are
• What the origins of wireless technology are
• What the economic impact of wireless networking is
• How wireless networking has changed the way people work
• How big the Wi-Fi market is
• What the impact of Wi-Fi on developing nations is
• What the Internet of Things is
When you complete this chapter, you will be able to:
• Describe the function of the OSI Reference Model
• Understand and describe the functions of each layer in the OSI Reference Model
• Describe IP addressing and the key differences between IPv4 and IPv6
• Describe MAC addresses and how they differ from IP addresses
• Provide examples of how wireless networking is used in health care, warehousing, and retail
Networking and the Open System Interconnection Reference Model
Before examining how wired networks evolved into wireless networks (along with the associated security implications), it’s important to have a fundamental grasp of basic networking. The logical place to start is the Open Systems Interconnection (OSI) Reference Model. Initially proposed in 1984, the OSI Reference Model was industry’s response to the issues created by proprietary data networking and equipment development at the dawn of the networking era. Before this, most equipment manufacturers had developed their own proprietary methods for data networking. These included unique communication protocols, connection interfaces, and procedures for data storage and retrieval, to name a few. In some cases, vendors did this because much of the development in this area was new. But many insisted on going their own way in an attempt to gain a competitive advantage.
This may have seemed like a good idea for the companies breaking into this newly developing market. But it was bad for customers because it locked them into a single vendor solution. Concerns over the limited scope of solutions and clients’ natural hesitance to remain locked into a single vendor ultimately stalled the market. This, of course, was not only bad for customers, it was also bad for vendors, because it put an artificial limitation on opportunities.
The answer was to develop a model that defined standards for communication protocols as well as for the physical and logical interfaces between machines and subsystems. Published by the International Organization for Standardization, the OSI Reference Model defines seven layers (referred to as a stack) that describe standards from the physical wire all the way up to the application interfaces on computers. Further, the standard was written such that each layer has a specific function, common among all devices, and a specific way of communicating with the layer above and the layer below in the stack.
FYI
In many cases, the term stack is used in reference to a particular protocol, such as IP. However, you will often see cases in which the phrase “moving up or down the stack” refers to the OSI layers. For example, firewalls were originally Layer 3 (IP) devices, but application firewall vendors are now said to have gone “up the stack” to Layer 7. In cases such as this, the context of how and where the term is used helps identify which meaning of the term applies.
As a result of this standardization, different companies were able to specialize in specific solutions or products, confident that their products would be compatible with products from other manufacturers, even if there were no up-front collaboration. This led to a great deal of innovation. It also greatly improved the number of available solutions, because the barriers to entering the market were greatly reduced. It’s much easier to start a company based on a niche product than to create an entire end-to-end solution.
More importantly, though, the OSI Reference Model proved to be an enormous benefit to consumers—businesses, universities, and governments—who enjoyed greater choice and the opportunity to choose “best in breed” products rather than be forced to standardize around a single vendor. Most economists and network historians agree that it was this willingness to adopt the OSI Reference Model that helped propel the networking industry into the economic power that it has become.
The Seven Layers of the OSI Reference Model
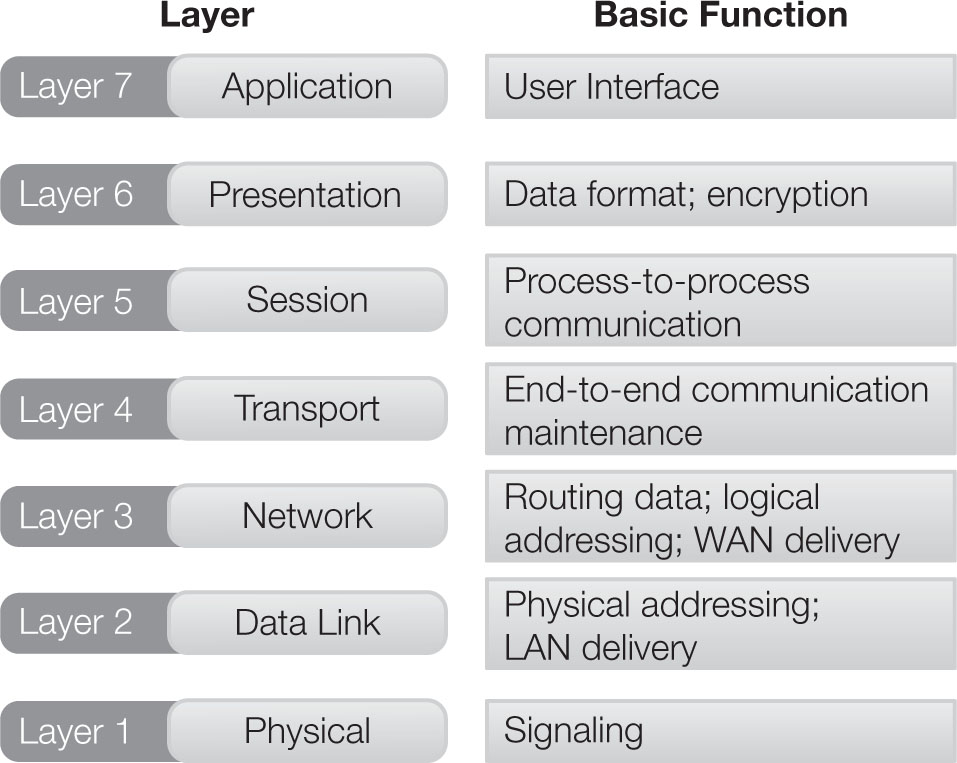
As noted, the OSI Reference Model has seven layers, each with a specific function and a standard way of communicating with the adjacent layers. From the bottom up, the layers are as follows:
• Layer 1 (Physical Layer)—The Physical Layer is the signal path over which data is transmitted. This can include copper wires; optical fibers; radio signals such as Wi-Fi, WiMAX, and Bluetooth; and any other transmission path. The units of information at this layer are bytes or bits.
• Layer 2 (Data Link Layer)—The Data Link Layer helps establish the communication path by specifying the media access control (MAC) address of each device. Layer 2 is viewed as the “switching” layer because it is the layer where switching paths are determined in LANs. Ethernet is a Layer 2 protocol. The unit of information at Layer 2 is the data frame.
• Layer 3 (Network Layer)—The Network Layer is typically viewed as the routing or IP layer, although over the years, the line between routing and switching has blurred. This layer handles communication paths between LANs. The Internet Protocol (IP) exists at Layer 3. As such, communication paths are defined in terms of their IP addresses. The unit of information at Layer 3 is the packet.
• Layer 4 (Transport Layer)—Known as the Transport Layer, Layer 4 is the bridge between the network and the application-processing software on devices. This is where data from applications is broken down into small chunks, or packets, that are suitable for transport from the sending device, and then reassembled on the receiving device.
• Layer 5 (Session Layer)—The Session Layer defines and manages communications between applications on separate devices.
• Layer 6 (Presentation Layer)—Known as the Presentation Layer, Layer 6 formats information sent to and from applications.
• Layer 7 (Application Layer)—At the top of the stack is the Application Layer, which connects software applications to the network.
![]() NOTE
NOTE
An easy way to remember the layer names in order is to use a mnemonic. There are dozens of them, ranging from funny, to topical, to outrageous. A good top-to-bottom one that is suitable in the workplace is All People Seem To Need Data Processing.
Inter-stack communication is accomplished through the use of headers. As data is created (at the Application Layer) and sent down the stack and across the network to another device, each layer adds its own set of instructions for the corresponding layer on the other machine and for the layer below or above the stack on the same machine. Although the OSI Reference Model does provide a clear framework, over the years, the lines have begun to blur. For example, many people lump Layers 5 through 7 together, referring to them as the “Application Layers.” Layer 3 and Layer 4 are closely associated due the use of Transmission Control Protocol/Internet Protocol (TCP/IP), the de facto standard for communication over the Internet. Finally, as mentioned, the functional lines between switches and routers have been greatly blurred as innovation and processing power have continued to accelerate, allowing for greater efficiency in multitasking devices. As a result, Layer 2 and Layer 3 are no longer the sole domains of switching and routing, respectively.
An OSI layer can communicate only with the layers immediately above and below it on the stack and with its peer layer on another device. This process of passing instructions to the layer above or below must be used so that information (including data and stack instructions) can be passed down the stack, across the network, and back up the stack on the peer device. Figure 2-1 shows the seven layers in relation to each other along with their basic functions.
Communicating over a Network
While a detailed look at the fundamentals of data communication is beyond the scope of this text, a brief overview of a few key aspects of network communication is necessary. In particular, you will look at those aspects of networking that weigh heavily in understanding wireless security. At the simplest level, the two main keys to communication over a network are conditioning the data for transport and ensuring that the data reaches the correct destination.
In the context of this simplified definition, the role of the Application Layers is to condition data for transport over the network or to reassemble data for use by the application on the receiving end. While there are many security considerations at these layers, they are largely independent of the method of transport (either wired or wireless), and are beyond the scope of this text. With the advent of network-connected mobile devices, all known issues that exist in fixed settings become moving targets.
Communication at the Network Layer is achieved through a logical addressing scheme that enables routers to move packets across the network to the correct destination. (In this case, “logical” means that the addresses are assigned and can be changed if needed.) This addressing scheme, called IP addressing, allows for data communication between (switched) local area networks (LANs) via routed wide area networks (WANs).
IP Addressing
IP addressing enables a network to correctly route packets across a network. For most of the past 30 years, an IP addressing scheme called Internet Protocol version 4 (IPv4) was used. This scheme used a format called dotted decimal, which consists of four octets (groups of eight in binary code) that define the location of a source or destination LAN—much in the same way a home or business address includes the street number, street, town, state or province, postal code, and country. A typical IP address has the format 198.10.249.168, where one or more of the first octets defines the network segment and the remaining octets define the computers or devices (referred to as hosts) on that network. Again using the analogy of a street address, you can think of the network as being like the street (for example, 5th St.) and the hosts as being like houses on that street (for example, 121 5th St., 122 5th St., etc.). Each octet ranges from a minimum of 1 to a maximum of 255. The maximum number is 255 because it is the largest eight-digit binary number (11111111). Certain numbers, such as 0 and 255, are reserved for certain types of communication.
When IPv4 was first developed, it was thought to be sufficient to allow for future expansion. After all, the total number of combinations is more than 4 trillion—although, due to disallowed combinations, as noted, the actual number of usable addresses is in the billions. Even so, that seemed like a lot of addresses. But this was before the Internet exploded and every business office, nearly every home in the developed world, and every smartphone needed an IP address. As a result, address space quickly became scarce. (For more on this, see the upcoming section, on IPv6.)
Subnetting
In addition to being able to identify a local network, network architects discovered a need to segment networks to improve communication, increase bandwidth efficiency, and segment user groups. To achieve this, network architects used subnetting. Subnetting enables network engineers to segment devices (called hosts) within a network. This is achieved using a subnet mask, which is a second 32-bit number that uses the same dotted decimal format as the IP address. Extending the analogy of the street address, a subnet could be viewed as multi-family dwelling such as an apartment building. The method of subnetting is beyond the scope of this text, but readers are encouraged to learn more about it.
Network Address Translation
Network address translation (NAT) is a method to mask the address of devices on a network from the outside world. Through NAT, a company can have one public address, which can be accessed from the Internet, and another set of private addresses, which can only be accessed internally. This has some obvious security benefits—for example, outsiders cannot target or spoof inside users or devices—but it also helps extend the use of limited IP address space. That is, you can shift the addressing scheme to have many networks with fewer hosts, and then use NAT to accommodate the large number of hosts or devices that exist on large enterprise, education, or government networks.
Dynamically Assigned IP Addresses
Another method to deal with the shortage of IP addresses was to assign them on an as-needed basis. This worked especially well for devices that were not in full-time use, such as home routers. Rather than tying up an unused IP address, Dynamic Host Configuration Protocol (DHCP) was used to automatically assign IP addresses to devices as needed. In addition to (slightly) freeing up address spaces, this also reduced personnel costs because it eliminated the need for support people to manually assign and configure addresses. DHCP is still very common with Internet service providers (ISPs), who use it to assign addresses to home subscribers.
Both NAT and DHCP helped extend the life of IPv4 addressing, but both proved to be only stopgap measures given the quick adoption of IP-enabled devices. The real answer to the problem was IPv6.
Unlike IPv4, whose 32-bit addresses yielded about 4 billion usable addresses, Internet Protocol version 6 (IPv6), a 128-bit address scheme, allows more than 3.5 undecillion addresses. That’s a number with 38 zeroes after it. Given this very large number, it’s a good bet that address space will no longer be an issue no matter how many network-connected smart devices come along. There are other benefits to IPv6 as well, including the following:
• Auto-configuration
• Improved address management
• Built-in security/encryption capability
• Optimized routing
An IPV6 address contains eight fields of four-digit hexadecimal (base 16) numbers (0 to 9 and a to f) as follows:
2051:0011:13A2:0000:0000:03b2: 000a:19aa
The notation also allows for a shorthand method that eliminates leading zeroes, with an all-zero field represented by a single zero:
2051:11:13a2:0:0:3b2:a:19aa
Further, successive fields of all zeroes can be shortened with a double colon (::) as follows:
2051:11:13a2::3b2:a:19aa
The changeover to IPv6 has been discussed for many years. Initial predictions in the late 1990s suggested the conversion would need to occur around 2002. As of this writing, however, the changeover is not yet complete, despite an explosion in the use of devices that has far exceeded any predictions in the early part of the century. IPv4 remains in wide use because converting to IPv6 requires massive upgrades that will cost millions and perhaps billions of dollars, and because so far, the workarounds seem to work. The conversion does seem to be slowly taking shape, however, as most new devices are IPv6 enabled. The tipping point of the conversion will likely be when most networking devices have gone through the natural refresh process over a 7- to 10-year period and are replaced with devices that can accommodate the new addressing scheme.
The Data Link Layer
Layer 2, the Data Link Layer, has been dominated by the Ethernet protocol for the better part of 25 years. Used primarily in LANs, Ethernet is how switches move data between machines. Over the years, Ethernet has been expanded. It is used in massive data centers and large metro area networks, furthering its hold on Layer 2 just as IP has dominated Layer 3.
Switches have always been a critical part of networks. Recently, however, switching has claimed a dominant position in networking. Why? One reason is that switch vendors have added functionality to switches, including features such as Power over Ethernet (PoE). This enabled VoIP phones to work without an additional power cord (they still needed an Ethernet cable, of course), and gave them Layer 3 and even Layer 4 forwarding capabilities. Improved performance drove ever-increasing speeds, from 1 gigabit (Gb) to 10 Gb to 40 and even 100 Gb Ethernet. Now the IEEE is in the process of ratifying the specifications for 400 Gb Ethernet. These improvements weighed heavily as dedicated data centers came into prominence in enterprise networks. They have greatly accelerated with the advent of virtualization, where fast switching within massive virtualized data centers is a primary design criterion.
Unlike IP, which was meant to connect LANs with each other, Ethernet connects data between machines that are all on the same network. As such, one of the key components of Ethernet deals with preventing data collisions that occur when multiple computers transmit data at the same time on the same segment of the network.
Much in the way that routers are associated with Layer 3, switches rule Layer 2. A switch connects different network segments together via switch ports, each of which can have multiple machines (or other switches in a hierarchical network). When a data frame (the Layer 2 version of a packet) arrives on a switch port, the switch looks up the source and destination media access control (MAC) address (a unique identifier assigned by manufacturers to any network-connected device) and makes a forwarding decision based on the rule set associated with the destination MAC address.
Unlike IP addresses, MAC addresses are physically assigned to every individual device that can connect to a network by the manufacturer as it rolls off the factory assembly line. MAC addresses are intended to be both unique and permanent. It is possible to spoof a MAC address, however, which—not surprisingly—has significant security implications.
The Physical Layer
At bottom of the stack, the OSI Reference Model specifies standards for the medium over which data is transmitted. While not often discussed in the same way as Layer 2 or Layer 3, the standards specified at Layer 1 are quite complex. This text will emphasize their importance because wireless LAN (WLAN) communication standards are specified here.
Layer 1 defines how the actual bits are transmitted between devices, including specifications on the following:
• Transmission—Bit-by-bit procedures
• Electrical—Signal levels, amplification, and attenuation
• Mechanical—Specifications for cables (type, length) and connectors
• Procedural—Modulation schemes, synchronization, signaling, and multiplexing
• Wireless transmissions—Frequencies, signal strength, and bandwidth
• Throughput—Bit rates
• Topologies—Bus, ring, mesh, point-to-point, and point-to-multipoint
Protocols defined at Layer 1 include the following:
• Synchronous Optical Networking (SONET)/Synchronous Digital Hierarchy (SDH)
• Digital subscriber line (DSL)
• T1/E1
• Integrated Services for Digital Networks (ISDN)
• Ethernet Physical Layer
• Bluetooth
• 802.11 (WLAN)
From Wired to Wireless
The networking industry began to grow in the 1980s and exploded in the 1990s with the culmination of affordable personal computers and growing popularity of the Internet and the World Wide Web. Already on an incredible trajectory in the late 1990s, the industry benefited from another incredible boost in the form of wireless networking—and there was another even bigger boost to come.
This “second wave” of networking was initially made possible as a result of a groundbreaking decision by the U.S. regulatory body in charge of telecommunication rules, the Federal Communications Commission (FCC)—the opening of several bands (contiguous ranges of radio frequencies) of the radio spectrum for unlicensed use in 1985. This was a big change, given that apart from ham radio, which was valued as a nationwide emergency communication system, the radio spectrum was a tightly controlled government asset that required licensed approval for use. This visionary decision (not a phrase often associated with a government regulatory body) had a profound effect on networking as well as on several other industries.
The frequency bands in question—900 MHz, 2.4 GHz, and 5.8GHz—had previously been reserved for things such as microwave ovens, among others. The FCC’s decision allowed anyone to use these bands (or any company to build a product that used these bands) as long as they managed interference with other devices. This made products such as cordless phones and remote-controlled ceiling fans—and, soon, wireless networks—possible.
At first glance, it’s hard to see exactly why wireless had such a huge impact. At the time, wireless performance was not that great. In fact, compared to a hard-wired Ethernet connection, it was pretty lousy. As it turned out, though, users were far more interested in convenience than performance—at least initially. Before the advent of WLAN, if you wanted to connect to a network, you had to go to where the computer was tethered to an Ethernet port. Or, if you had a laptop (these were also becoming cheaper), you had to go where the connection port was. This may not seem like a big deal, but “going to the computer” meant leaving where you were and dropping what you were doing.
Wireless networking changed all that. With WLAN, you brought your computer to where you wanted to be and connected to the network from there. The ability to connect in a meeting room or on your couch in front the TV far outweighed the slower connection speed, especially since there were very few high-speed network applications at the time. (Streaming media meant waiting 5 or 10 minutes to download one song, for example.) This convenience factor created a massive surge in WLAN usage. In response, manufacturers poured millions into research and development (R&D), which improved performance, which in turn attracted more users.
The first generation of WLAN operated at about 500 kilobits per second (Kbps) on an unlicensed frequency band. In this case, “unlicensed” meant that anyone could use it. It was not restricted or reserved for commercial or government use as long as the transmission power was kept low. The second generation boosted performance to 2 megabits per second (Mbps), a 400-percent improvement. (Note that the term “generation” is used here in the generic sense rather than as a name, as it is when describing mobile network technology.)
In 1990, the IEEE established a working group to create a standard for WLANs. In 1997, the IEEE 802.11 standard was ratified, specifying the use of the 2.4 GHz band with data rates of up to 2 Gbps. Different versions of the 802.11 standard were developed in subsequent years and were noted via extensions such as a, b, g, and n. Notationally, this would appear as “802.11b,” for example.
The Economic Impact of Wireless Networking
To understand how wireless became available almost everywhere, you must understand the desire for mobility. It is no longer acceptable to be located at a fixed network point of access. Nowadays, consumers demand the right to move around—to be mobile.
The first wave of the wireless revolution included early adopters who provided fixed-line PC-based Internet services at cafés and shopping malls. Their fee-based services, which were fraught with security issues—typically keyboard sniffers to capture passwords and banking details—soon succumbed to free public wireless broadband offerings.
Soon, it became common to have high-speed ADSL and broadband fixed-line networks in residential properties. To reduce churn, ISPs often supplied Wi-Fi–enabled gateways to consumers. Churn is the movement of a subscriber from one network to another and is one of the key performance indicators (KPIs) most relevant to overall performance. These measures helped Wi-Fi gain traction in homes and small businesses, but they alone cannot account for the fact that in 2005, wireless broadband accounted for productivity gains of $28 billion.
Wireless Networking and the Way People Work
It’s somewhat difficult to separate the business impact of Wi-Fi from its economic impact because they are intrinsically tied to together. This section will focus on one key point, however: the way in which wireless has changed how companies work. As mentioned, wireless networking has changed how people work in the office—particularly knowledge workers (that is, professionals whose jobs involve the use and manipulation of data). These were the first wave of employees to use computers and, later, laptops. These workers found it very useful to be able to connect to the network from anywhere in the office, such as meeting rooms, particularly given the collaborative nature of their work.
This was an important change, of course. But there were some industries for which wireless fundamentally changed the way they did business. A few of them are discussed here.
Health Care
One of the first industries to adopt wireless technology was health care, and it has profoundly changed how hospitals work and how doctors and nurses interact with patients. In 2005, productivity improvements from the use of mobile wireless broadband solutions across the U.S. health care industry were valued at almost $6.9 billion. By 2016, this number is forecast to triple to $27.2 billion.
Health care is one of the most labor-intensive industries, as well as one of the most sensitive to keeping personal data private. Nonetheless, health care has managed to use wireless technology to improve communication, as well as provide instant access to information portals for diagnosis and general health information such as diets and lifestyle plans. These improvements in efficiency alone don’t explain the savings in health care, however. Another $900 million was gained by reducing inventory loss through the use of wireless tagging or radio frequency identification (RFID).
One of the obvious improvements that wireless brings to the health care industry is that it allows modern medical devices and monitors to be moved with patients as they travel to different places in the hospital—from their room to a lab, to pre- and post-op, to recovery, and back to their room. Before the availability of wireless, there was the constant need to disconnect, move, and reconnect these devices and monitors, which presented numerous opportunities for errors or breakdowns. Cables, connectors, and ports break down with extended use—and this is compounded when they are used next to hospital beds because of the frequent need to adjust the bed’s height and position (from sitting to prone, for example). The result was often pinched or severed cables, many of which went unnoticed for some time, leaving patients unmonitored.
Another benefit to patients, health care professionals, and insurance companies is that wireless technology allows for real-time data at the point of care. This has a couple of significant implications. First, it means the patient can always be monitored, which improves staff reaction time to alerts—a potential lifesaver. Second, it allows for real-time access to patients’ files. This is profound. Prior to wireless technology, patients often had a paper chart at the foot of their bed, which a doctor or nurse would look at prior to administering care or running a test. These charts were highly prone to errors, however—from lost or missing pages, to misinterpreted handwriting, to out-of-date or incomplete information. With wireless, caregivers now have real-time access to patients’ digital records, where information is backed up and complete. This also allows for features such as auto alerts, which help eliminate errors with treatment, incompatible prescriptions, or incorrect dosages. These are lifesaving improvements. Of course, many important security considerations go along with using wireless technology in this manner.
A less dramatic use of wireless in health care—but nonetheless an important one—is that most hospitals offer free Wi-Fi to patients and visitors. In this way, hospitals have greatly improved the satisfaction of patients and visitors alike. For all the drama of a medical emergency, the reality is that the vast majority of the time in a hospital for both visitors and patients is spent sitting around waiting. Offering free access to the Internet provides the perfect distraction.
Warehousing and Logistics
Seemingly at the opposite end of the technology spectrum from health care is the warehousing and logistics industry. Nevertheless, wireless networking has made a significant impact here as well.
Prior to the advent of wireless networking, warehouse personnel logged storage locations on paper and used written notes to retrieve them. This method was fraught with errors and inefficiencies, especially in bigger warehouses, which can be as large as 1 million square feet.
Wireless networking allows for much greater efficiency throughout the entire process, from receiving, to shelving, to picking (retrieval), to outbound distribution. Specifically wireless networking helps with the following:
• Asset tracking—With wireless networking, companies can automatically track assets in real time, providing a major productivity gain over manual, semiannual inventory checks.
• Picking efficiency—Retrieving inventory for distribution (picking the item off the warehouse floor) used to be a long process. Often, workers walked (or rode) several hundred yards through a warehouse, only to arrive and not find the item. The worker would then have to walk (or ride) all the way back, try to find the error, and repeat the process. With wireless technology, location accuracy is much improved, as is the picking process. This saves a great deal of time and money.
• Loss control—Another Wi-Fi automation success has been the savings gained by reducing inventory loss. In a 2004 report by Ovum, several companies reported substantial inventory management savings through using wireless technology. When these figures were extrapolated across other industries, the savings were $272 million in 2004 and estimated to be as much as $26 billion by 2016.
Retail
The retail industry has also taken great advantage of wireless technology. As with the back end of the business, discussed in the preceding section, the front end of the business has also changed as a result of wireless networking. Specifically, wireless has resulted in the following key changes:
• Inventory counts—Retailers always want the most popular products on hand, but they must carefully manage their inventory to avoid overstocking. Accurate inventory counts and direct front-of-store and point-of-customer interaction can put warehouse orders into motion in real time.
• Customer satisfaction—Retailers spend a great deal of money getting shoppers into their stores. Once shoppers are there, retailers must do their best to convert them into buyers. This can be difficult, however, in an industry with a transient workforce, especially during those critical shopping seasons when a retail business can be made (or ruined). Arming sales staff with wireless devices turns even brand-new employees into product experts by allowing them to verify back-of-store inventory, suggest popular merchandise tie-ins or up-sells, or check with other local outlets for popular items.
General Business and Knowledge Workers
While it’s true that specific industries have taken advantage of wireless networking, the biggest impact of wireless networking has been the way it has fundamentally changed how, where, and when people work. Before the wide adoption of wireless networking, people tended to work mostly in the office. When workers did work outside the office, either after hours or while traveling, they were often limited to offline work. Alternatively, if they went through e-mails, for example, they submitted work in batches.
With wireless, of course, there is greater flexibility with regard to where you can work—whether it’s on the deck of a beach house, at a coffee shop, in an airport terminal, or on a plane traveling 500 miles per hour, 30,000 feet in the air. As a result, worker productivity has gone up, and continues to rise.
This is great for many, but it does come at a cost. Perhaps most significant is the fact that the line between “work” and “not work” has blurred to the point that it’s hard to distinguish where work ends and one’s personal life begins. More and more, it seems that businesses expect their employees to available and checking e-mails late at night, on weekends, and on vacations. More on topic for this discussion is that using a portable work device to access a network via a public Wi-Fi connection opens a vast array of potential security vulnerabilities that must be accounted for.
Nevertheless, Wi-Fi has brought about considerable increases in savings and overall efficiency. Its impact on the economy was considerable—even in its fledgling state, back in the early 2000s, before the advent of high-speed devices and mobile Web applications. Even then, those who embraced the technology found that it delivered major benefits to their businesses.
The Wi-Fi Market
In 2013, the worldwide WLAN market was an estimated $7.5 billion per year. About half of that was attributed to growth in the enterprise space, suggesting that large companies are embracing the idea of users connecting to the network over wireless most, if not all, of the time. This annual spending on WLAN equipment is only part of the story, though. As noted, Wi-Fi technology has changed the way many organizations do business. Indeed, it has created whole new business models.
Coffee shops, bookstores, and cafés have embraced wireless connectivity in two waves. The first wave involved providing wireless access to a private LAN that charged for a one-time use or for a subscription. Many such businesses felt this was a nice add-on feature and an opportunity for revenue. What’s interesting, however, is that most of these businesses have converted to free access, choosing to forego the additional revenue in favor of attracting more customers, whom they welcome to come in and stay. In other words, they encourage clients to actually use their stores as an office, for two reasons:
• Those customers tend to buy other goods and services while there.
• It creates a regular and loyal customer base.
Hotels have also been transformed. Not surprisingly, providing Internet access to guests has become essential. Perhaps the biggest impact of wireless technology on the hotel industry is that fact that it has drastically lowered the cost of providing Internet access. This is particularly important in situations where retrofitting an older hotel to offer a wired network would be prohibitively expensive. If not for wireless technology, many hotels would have to choose between a very expensive upgrade and the potential loss of revenue. With wireless technology, Internet access can be provided at a much lower cost.
Much like cafés, some hotels offer free network access, especially in the lobby, where they encourage users—especially business travelers—to meet. Interestingly, however, many hotels charge for access in rooms and even offer tiered options for basic or high-speed connectivity. The theory is that outside of resort towns, a high percentage of hotel rooms are booked by business travelers, who can simply expense the cost of connectivity along with their hotel bill.
How Wi-Fi Affects Developing Nations
A great many parts of the world lack the physical infrastructure that developed countries have long taken for granted. This so-called digital divide between the haves and have-nots reveals a great disparity between developed nations, where more than 75 percent of people have access to the Internet, and developing nations, where less than 24 percent have access. This is an enormous distinction, given that above all, the Internet is a great equalizer.
Access to the Internet means access to global commerce, enabling any and every businessperson, artist, and craftsman to tap into a worldwide set of customers. Access to the Internet also provides access to the entirety of human knowledge, including free classes from renowned institutions of learning ranging from the Massachusetts Institute of Technology to Oxford University.
In short, access to the Internet changes lives for the better and gives opportunities to those who would not otherwise have them. Until the advent of wireless networking, however, it was often cost prohibitive to install the infrastructure needed to allow access on a broad scale. In some places, the development of this infrastructure was thwarted by thieves, who frequently tore copper lines out of the ground for their salvage value within hours of installation.
Wireless networking, however, is much more cost effective to install. Moreover, last-mile connectivity—that is, the connection between a person’s house or other termination point and the local switch that connects to the network backbone—can be achieved with point-to-point microwave links, eliminating the need to install and protect physical lines. As a result, many developing nations have started to close the digital divide and are enjoying improvements in productivity, which are both sustainable and self-reinforcing.
The Internet of Things
In 2005, having wireless access in the workplace or home was still a something of a novelty. Today, wireless networking is so prevalent that one can obtain wireless access on a trans-continental flight. Indeed, passengers will even complain to the flight attendant if the connection is slow or unstable!
Looking ahead, wireless technology is the key to something known as the Internet of Things (IoT). IoT refers to the potential interconnection of virtually any electronic devices that can be controlled and optimized via automation or remotely via an Internet connection. With the IoT, most people’s interactions will be via smart homes and electronics, allowing energy-saving programming, automated lighting, safety programming, and home entertainment. Unlike obtaining broadband access on a plane, which is likely a novel but infrequent experience for most, the IoT will dramatically shape the way people live and interact with their home environment and electronic devices. The IoT will also extend to enterprise and industrial settings, and even into implanted medical devices such as heart monitors.
The IoT has long been available through wired networks, but adoption among the general public has been slow and limited to those in high-end homes due to the costs associated with wiring and, in older homes, retrofitting. This key barrier has been removed in recent years due to the reduction in the size and cost of wireless technology.
As the IoT becomes a reality over the next several years, people will truly live in a wireless world, where everything is connected and controllable. And although this will have a great many benefits with regard to safety, energy efficiency, and convenience, it will also open a whole new world of security threats and vulnerabilities. It’s one thing to have your computer files destroyed due to a virus or other malware, or to have your credit card run up by a cyber thief. It’s another thing altogether to have a hacker lock people out of their house, ransom control of their heating system in the dead of winter, or take control of a moving vehicle. For those in the information security business, this will be another front in the cybersecurity war that sees no end in sight.
![]() CHAPTER SUMMARY
CHAPTER SUMMARY
Wireless networking has changed the world in a many ways. It has altered entire industries and brought productivity gains even to sectors that had seemingly squeezed out as much productivity as possible. More than that, wireless networking has changed not only how and where people work, but also the very relationship between employees and employers. Wireless technology has brought work into people’s homes in a way that previously did not exist.
In a macro sense, wireless technology has made it easier to bring Internet access to people and places that for too long have been on the wrong side of the digital divide. This extended access improves not only the lives of those directly affected, but also the surrounding community and, to some degree, the world at large. As they say, a rising tide lifts all boats.
You could argue that the business and human effects of wireless technology far outweigh the small part of the OSI Reference Model that defines the standards for how it works. That said, before you can understand the technical and security implications of wireless technology, you must be well grounded in the fundamentals of networking. This chapter served as an overview. But you should review your understanding of basic networking on regular basis.
Application Layer
Data Link Layer
Dotted decimal
Dynamic Host Configuration Protocol (DHCP)
Federal Communications Commission (FCC)
Internet of Things (IoT)
Internet Protocol version 4 (IPv4)
Internet Protocol version 6 (IPv6)
IP addressing
Knowledge workers
Media access control (MAC) address
Network address translation (NAT)
Network Layer
Open Systems Interconnection (OSI) Reference Model
Physical Layer
Presentation Layer
Session Layer
Stack
Subnetting
Transport Layer
![]() CHAPTER 2 ASSESSMENT
CHAPTER 2 ASSESSMENT
1. Switches primarily operate at which layer of the OSI Reference Model?
A. Physical Layer
B. Data Link Layer
C. Network Layer
D. Transport Layer
E. None of the above
2. Wireless networking standards are defined at the Network Layer.
A. True
B. False
3. Which of the following reflects the correct order of the OSI Reference Model from Layer 1 to Layer 7?
A. Application, Presentation, Session, Transport, Network, Data Link, Physical
B. Physical, Data Link, Network, Transport, Session, Presentation, Application
C. Physical, Application, Presentation, Session, Transport, Network, Data Link
D. Network, IP, Data Link, Application, Logical, Presentation, Physical, Session
4. Layers 4 to 7 are often grouped together and referred to as the “Application Layers.”
A. True
B. False
5. IP addressing is specified in which layer?
A. Layer 1
B. Layer 2
C. Layer 3
D. Layer 4
E. All of the above
6. The Data Link Layer uses a logical addressing scheme to switch data frames.
A. True
B. False
7. The IPv6 address 23a2:0001:0000:00a3:0000: 0000:00ba:c0f2 can be written as which of the following?
A. 23a2:1:a3:ba:cf2
B. 232.10.030:0f2
C. 23a2::a3:: c0f2
D. 23a2:1:0:a3::ba:c0f2
8. MAC addresses are often changed by IT personnel to accommodate growing networks.
A. True
B. False
9. Which of the following is not a use of Wi-Fi in warehousing?
A. Asset tracking
B. Loss control
C. Forklift automation
D. Picking efficiency
10. Over the next several years, the most significant impact of widespread wireless connectivity for most people will be which of the following?
A. Being able to check e-mail while on a plane
B. Free wireless hotspots in malls and coffee shops
C. The emergence of the Internet of Things, which will connect household appliances and systems to the network
D. Lower Internet rates