THIS CHAPTER PROVIDES a general overview of network security threats and considerations, with a particular focus on wireless and mobile devices (where it applies). In an ideal setting, security professionals could easily lock down any network or network-enabled device to mitigate the risk of data loss or unauthorized access. Unfortunately, your practice must be applied in the real world, where the business’s needs, third-party requirements, and employee satisfaction must be balanced with the security team’s priorities. This chapter aims to give you an understanding of the threats as well as an appreciation for the many factors that go into implementing a security strategy. A pragmatic approach that provides the right balance of security and access is often the best path to success.
Chapter 4 Topics
This chapter covers the following concepts and topics:
• What you should protect
• What the general threat categories are
• What the threats to wireless networks and mobile devices are
• How to mitigate risk
• What authorization and access control are
• What information security standards are
• What regulatory compliance entails
When you complete this chapter, you will be able to:
• Describe the general threat categories in wireless and mobile environments
• Describe the five aspects of threat identification
• Describe the security vulnerabilities of Wi-Fi and mobile devices
• Describe defense in depth and how it used
• Understand the purpose and methods of authentication, authorization, and accountability
• Describe examples of information security standards
• Understand the benefits and consequences of regulatory compliance
• Understand how to reduce risk using risk-mitigation techniques
• Describe the threat-mitigation techniques for Wi-Fi and mobile devices
What to Protect?
In essence, information security refers to the processes and practices that must be implemented to secure the digital assets you wish to protect from various threats. The first step to formulating any security plan is to ask questions, such as the following:
• What are you trying to protect? Is it corporate data, intellectual property, customer data, or financial assets?
• Why are you trying to protect it? Is protection mandated by a government or industry agency, or is it an internal best practice?
• What is the value of the asset? Have the assets been quantified? Has the cost of a data breach been estimated?
• What are you protecting it from? Are the threats internal or external? Are they aimed at data theft, device control, or system access? Are the threats environmental or human in origin?
• What constraints prevent you from protecting the asset? Is broad access required? Does the data change or move around?
The answers to these basic questions will help you identify the assets you must secure, as well as the priority and value of each individual asset. This is vitally important. Security must be cost effective. An organization should spend enough on security to meet the risk-reduction objectives and no more.
Securing an organizational network is a lot more complex than most people think. Even securing a small business is not easy; it requires standards and best practices that meet the business’s needs and, in many cases, the industry’s requirements. Consequently, you need flexible guidelines but must also adhere to mandatory regulations.
In addition, the motivation for securing a small company may not be the same as that for securing a publicly listed company or a large government agency. Similarly, the head of sales or product development in a publicly held company may have a vastly different opinion than the chief security officer regarding the balance between ease of authorized access and robust external security.
General Threat Categories
What are the different threats to an organization’s assets? To determine this, you must first consider who or what are you protecting the assets from. Is it external attackers or employees? Some major business failings in recent times have come about through internal manipulation of company financial data or from malicious insiders—the lesson for companies being that they should treat both employees and external intruders with caution. Most companies employ the practice of least privilege, whereby personnel are given the rights and permissions to perform their jobs and nothing more. This does not solve all problems, but it does greatly reduce overall exposure to risk.
You must also consider which assets you wish to protect, as well as the constraints you face, both physical and from a business perspective. Not all assets can or even should be rigidly secured. Some assets, such as a Web server or an automatic teller machine (ATM), will need to have public exposure. Others, such as information on an internal database server, can be more robustly secured, as access requirements are more limited.
Your security procedures should align with the business objectives and the assets’ functions. For example, you cannot reasonably secure an e-commerce server by disconnecting it from the Internet. Yes, doing so would make it secure from threats of Internet attacks, such as denial of service attacks, sync attacks, or hacking attempts. But doing so would also make it useless for its purpose.
In short, the security measures should be proportional to the value of the assets, and should not create an impediment to the assets’ purpose and function. This is a key point that many security professionals miss: Information security should not become an impediment to authorized users performing authorized business functions. That said, having reasonable but visible security practices ensures that security is top of mind for employees who use or have access to protected data or systems.
The key is to ensure that information security processes, practices, and techniques are aligned with the business’s plans, goals, objectives, and functions. This requires user education, as many problems are the result of a lack of awareness or understanding. An information security policy is also key. Indeed, an information security policy is one of the most important security documents in any business. It is the foundation and the rationale behind all security measures implemented by security officers.
The information security policy should match the business requirements, objectives, and culture of the company it serves. This is especially true in these days of mobility and wireless technology, where employee productivity and mobility trump rigid access controls. Nowadays, businesses encourage employees to use their own devices and applications and provide them with freedom of access to information from any location and any device. Information security must therefore adapt to support these policies, initiatives, and practices, while at the same time securing and protecting the company’s assets. This is a significant cultural change from the norms of a decade ago.
Initiatives and practices may change over time as businesses adapt to new technologies. However, the core principles of information security and the C-I-A triad of confidentiality, integrity, and availability will remain. They have, however, been expanded to cater to the specific requirements of new technologies and business models. These expanded principles of information security are as follows:
• Confidentiality—Preventing unauthorized disclosure of information
• Integrity—Preventing unauthorized modification of information
• Availability—Preventing unauthorized withholding of resources or services
• Accountability—Making users accountable for their actions
• Nonrepudiation—Preventing the denial that an action has been taken
Confidentiality
Traditionally, confidentiality has been about securing access to information on storage devices and servers via access policies and rights. Administrators may have encrypted data or hidden it from view to protect it from unauthorized access by applying strict access policies on directories and folders. Similarly, administrators would protect data by encryption and authentication mechanisms, if deemed necessary, when it was traversing the local area network (LAN), wide area network (WAN), or Internet.
In today’s modern networks, when it comes to confidentiality you must consider both the privacy of information (protecting data from being seen) and its secrecy (hiding knowledge of data’s existence or whereabouts).
Additionally, you must consider the confidentiality of data stored on laptops, smartphones, and tablets. These devices are of particular concern because anytime information leaves the organization’s property, it becomes vulnerable. This is also an issue because the decreased size of these devices, along with the increased amount of time these devices are with people outside the office, has greatly increased the likelihood that the physical device will be lost. For example, it’s doubtful that 10 years ago many people would have taken their work laptop to the mall and left it behind in a coffee shop. The smaller size of smart devices, however, makes them easier to leave behind. In addition, the fact that their owners tend to carry them everywhere significantly increases the likelihood of their being lost. As a result, device loss, and the remote locking or wiping of a lost device, have become major challenges for information security.
Integrity
In a security sense, integrity refers to the assurance that information is genuine, that it remains true to its original form, and that it has not been manipulated or tampered with. Many applications use mathematical algorithms called message-digests or hashes to ensure the integrity of a document or file—that is, to ensure that the document or file has not been altered either by accidental corruption or deliberate manipulation. These algorithms produce a digest, or a hash, of the file or data.
This approach works because an identical file, when passed through the algorithm, will always produce the same hash number or numerical result. However, if you change just one single bit within the file, the algorithm will produce a different result. If you compare the hash number on each file and they match, you can be confident that both files are identical.
Hash algorithms provide assurance of data integrity when data is passing over unsecured networks such as the Internet. They also provide a method for mitigating man-in-the-middle attacks, whereby an attacker intercepts files or messages and alters them before passing them on to the intended recipient. In a wireless, Wi-Fi, or mobile environment, session hijacking is a particular concern.
Availability
With regard to information security, availability is concerned with ensuring that systems and services are available to users when they need them, and are not withheld by unauthorized means. This is quite different from availability from a system or network perspective, which is more a measure of reliability and is ensured through machine clusters and fail-over master/slave configurations.
In security, availability is largely about preventing denial of service (DoS) attacks, in which an attacker tries to prevent legitimate access to a system or service by making it unavailable. Attackers commonly launch DoS attacks through synchronization (SYN) flooding of Transmission Control Protocol/Internet Protocol (TCP/IP) devices on the Internet to disrupt the three-way handshake used by TCP to establish a session. This handshake involves the following steps:
1. The requester sends a synchronization request, called a SYN.
2. The server responds with an acknowledgment to the request, called a SYN-ACK.
3. The requester responds to the acknowledgment with a message of its own, called an ACK.
After this occurs, the client and server can communicate.
With a SYN flood attack, the attacker blasts the server with fake SYN requests. The server is obligated to respond, but the requester never replies with an ACK to establish a session. This leaves the host with incomplete connections. When this process is replicated thousands of times, the host’s finite capacity to open TCP connections will be consumed, and no more connections will be possible. This is a crude but highly effective attack on a system’s availability.
On a smaller scale, jamming techniques can prevent availability on Wi-Fi and mobile systems. In some cases, the mobile system itself is targeted. This may send users into a near panic, as they have come to expect uninterrupted connectivity.
Accountability
Accountability is important from a security standpoint. Despite diligent efforts to ensure confidentiality, integrity, and availability, a system’s access controls can still be bypassed either accidentally or deliberately. Serious security breaches sometimes occur from within the network, originated by authorized users rather than unauthorized attackers outside the firewalls. Therefore, there must be mechanisms in place for the accountability of internal users. These normally include audit trails and logs that authenticate users and record their actions.
The key point is authentication. A user cannot be accountable if the system has not authenticated him or her. Of course, the standard method for authentication is through network logons and combinations of usernames and passwords. This again raises the lost-device issue, however. If a lost device falls into the hands of a knowledgeable attacker, devastating damage can result. Timely reporting of the loss of devices and access tools (cards, fobs, and so on) is critical in these cases to limit the threat and mitigate damage.
Nonrepudiation
Nonrepudiation addresses when someone denies he or she took a certain action. That is, nonrepudiation provides undeniable evidence that the action was taken, and by whom. Nonrepudiation is important in e-commerce and financial transactions such as online trading.
A simple application of nonrepudiation is when sending and receiving documents. The sender may attach a read receipt, which the recipient signs and returns. That would appear to meet the requirements. Unfortunately, however, there is no guarantee that the person who read and signed was indeed the intended recipient. Therefore, the recipient can repudiate, or deny, the action.
With nonrepudiation, digital signatures are used. If the sender signs the document with his or her own digital signature, that is considered nonrepudiation of origin. Similarly, when the recipient receives the document, that person can use his or her digital signature to sign the receipt. That is considered nonrepudiation of delivery.
At issue here is users connecting over unsecured Wi-Fi links, where passwords can be stolen or where sessions can easily be hijacked. This makes the validity of nonrepudiation difficult to ascertain.
Threats to Wireless and Mobile Devices
While the expanded principles of information security are good in a general sense, they are not very instructive with regard to the day-to-day protection of mobile and wireless clients, devices, and networks. This section looks at some specific threats, which are broken into three categories:
• Data theft
• Device control
• System access
These categories will have some overlap, but they cover the full breadth of threats.
Before looking at specific mobile and Wi-Fi threats, it’s important to remember that virtually every threat that exists on wired networks also exists on wireless and mobile networks. In addition to these threats, some threats are specific to wireless and mobile, or now have wireless and mobile variants. This section will focus on these threats.
In a wireless or mobile environment, you can also deny service by creating radio interference that prevents clients from communicating with access points. Another method is by physically taking out a mobile backhaul connection to deny network access to smartphone subscribers. This is where the complexity of wireless and mobile security comes into play. On the surface, they are merely new means of accessing a network. But they represent entirely new dimensions of threats and vulnerabilities. That means managing mobile and Wi-Fi–enabled devices requires a broader approach to security management.
Data Theft Threats
Regardless of the method used to compromise or gain access to a mobile device, the hacker or cybercriminal typically has specific goals in mind, many of which pertain to data theft. Often, these hackers go after a target of opportunity rather than instigating a targeted attack on a specific company. In such a case they will look for personally identifiable information (PII), which is information that can be used to identify, contact, or locate a single person, or to identify an individual in context, with any business-related data considered a bonus. Typically, the areas of interest for cybercriminals are:
• Credentials for personal or business accounts
• Credentials for business or personal information
• Credentials for remote access software for business networks
• Access to data and phone services
With the huge proliferation of mobile devices that support 3G and broadband wireless data over the last few years, there has been an increase in mobile-specific attacks designed to steal data. The most common threats are as follows:
• Sniffing (also called snooping)—The most obvious vulnerability of any radio-based communication is that signals can be easily intercepted through a process called sniffing or snooping. No physical access to the medium is needed. Fortunately, this is easily circumvented with encryption. Although not all encryption methods are created equal, even so-called “weak” encryption is better than nothing. Yes, some methods of encryption can be cracked. But the reality is, most sniffing and snooping hacks are simply targets of opportunity. As such, having at least basic security will prevent most of these attacks. Basic or weak encryption will not stop a determined and talented hacker from breaching a specific target, but any company likely to be targeted would be expected to have robust data protection. For the vast majority, simple steps go a long way.
![]() NOTE
NOTE
Data theft can occur without depriving the owner of access. Any data or information that can be seen can be replicated and used elsewhere.
• Malicious applications (malware)—While malicious applications, or malware, have existed for many years, the 10,000-fold increase in the number of applications now available on smart devices (as compared to software downloaded on PCs) has opened many more attack vectors. These applications range from malware that can be auto-installed on phones to spyware that can copy e-mails, texts, and contacts. There is also a significant privacy issue due to the ability to track the location of a mobile device, not to mention the significant amount of PII that these devices contain. This can result in some new, formerly unheard-of implications. For example, a malicious application capable of logging Global Positioning System (GPS) locations and text messages on the phone of an executive—who, say, schedules a hotel rendezvous with a person who is not his or her spouse or performs some other potentially damaging deed—could be used to blackmail that executive for insider information or access. It may sound far-fetched, but this sort of thing actually happens, and is the reason strict restrictions on downloading apps must be put in place.
• Browser exploits—Specifically targeting mobile users, these exploits take advantage of vulnerabilities on mobile Web browsers. This a big consideration for bring your own device (BYOD) environments because unlike company-owned assets, on which updates can be mandated and managed, personal devices can and often are several updates behind. That means that simply by visiting an unsafe Web page, a user can trigger a browser exploit that installs malware or performs other actions on his or her device. This is another reason that mobile device management (MDM) is a critical tool in a BYOD environment.
• Wireless phishing—Phishing involves sending fake e-mails or Short Message Service (SMS) messages to a target in an attempt to get the victim to click a link that will take him or her to a fraudulent Web site. Once there, the user will be prompted to enter account credentials or other confidential information, which can then be used by the cyberthief to access the real account. Phishing is exacerbated by smart devices with small viewing screens, which can make it difficult to notice some of the telltale signs of phishing. Hackers can also take advantage of users who connect to rogue access points (and variants called evil twins).
• Lost or stolen devices—This is obvious and low tech, yet it remains one of the most common threats for mobile devices. Not only do lost or stolen devices result in data loss, they also can result in unauthorized system access. When a device is lost or stolen, the data on it is also lost. In addition, the device is compromised, especially if it has remote access software configured for access to the corporate network. Often, these secure virtual private network (VPN) connections are set up to auto-connect for convenience using weak passwords. Passcodes can prevent some issues—at least with the casually curious person who finds or takes a device—but once in the hands of a skilled hacker, these passcodes are easily circumvented. Timely notification and blocking or wiping the device are the best options if it is lost or stolen.
Device Control Threats
In addition to obtaining data resident on a device, a hacker often aims to control the device itself. With control of the device, the hacker not only has ongoing access to data, but can also use the device to launch other attacks or leverage the permissions on the device to gain access to higher-valued targets such as internal servers. This occurs through a process called lily padding, in which the hacker “hops” from one device to another, with each hop getting the hacker closer to the target. Examples of device control threats include the following:
• Unauthorized and modified clients—Users sometimes create vulnerabilities when they try to circumvent policies or device configurations. This can open back doors and other vulnerabilities. Examples of this include user hacks found on the Internet to alter a smart device (referred to as jailbreaking) and opening a smartphone hotspot (without security). This is a problem because the corporate network views these devices as authorized clients, which may be used by hackers to access systems or data. Again, this is a new issue brought about by BYOD, where some people see no issue with using their device however they see fit.
![]() NOTE
NOTE
Jailbreaking modifies Apple’s iOS to allow unsigned code to run on Apple devices such as iPhones and iPads. This allows the user to download and install third-party applications from sources other than Apple’s App Store. Rooting is a similar process, but it only applies to Android devices. Rooting grants the user access to the root account of Linux.
• Ad hoc connections and software-based access points—Ad hoc networks have been possible for many years, but setting one up formerly required a high level of technical skill. With new smart devices, however, it’s quite easy to make these connections, which are easily exploited.
• Endpoint attacks—Several tools now exist that can attack wireless clients directly. An automated tool called Metasploit, for example, can be used to probe Wi-Fi clients for thousands of known vulnerabilities. Once exposed and exploited, the Wi-Fi client can be controlled and/or monitored.
• Bluetooth Wi-Fi hacks—Traditionally, vulnerabilities in Bluetooth protocols have enabled hackers to gain access to and control of mobile devices. This is no longer as easy as it used to be, however, because Bluetooth is now switched off and set to non-discovery mode by default. If a user changes this setting, however, hackers can easily take control of a Bluetooth-enabled mobile device—a real concern for BYOD.
• Near field communication (NFC) and proximity hacking—One technology that allows an ad hoc wireless connection between two devices that are within a few feet of each other is near field communication (NFC). Unlike Bluetooth, the pairing process is automatic. Already used extensively for social media and to exchange contact information, the future of NCF includes the ability to auto-pay via credit card at point-of-sale (PoS) terminals and will likely become a prime target for hackers.
System Access Threats
As noted, hackers are often interested in deeper access into a network. For them, device control is simply a means to an end. However, there are cases in which hackers are more interested in breaking the network or disrupting network access for political or financial gain or in some cases to exact revenge for a real or perceived insult or injury. Examples of these types of system access threats include the following:
• Denial of service (DoS) attacks—As discussed, wireless local area networks (WLANs) and mobile networks are vulnerable to both network-based DoS attacks and those created specifically to attack the inherent weaknesses of radio-based systems. In the case of Wi-Fi, using the less-crowded 5 GHz band reduces the chance of an accidental DoS but does not help with targeted attacks. Modulation techniques that spread communication over multiple frequencies and channels help a great deal, but there are also sophisticated jamming techniques that hackers can bring to bear.
• Evil twin access points—An access point (AP) can easily be set to the same network name (SSID) as a legitimate WLAN or hotspot, fooling unsuspecting users into connecting. This is not a new problem, but there are new hacker tools that can listen to clients to see what SSIDs they are looking for and then configure themselves to look like one of those networks. The client will then connect without the user having done a thing. Once connected, the client is subject to a full host of network attacks.
• Rogue access points—Unauthorized or rogue access points have been a problem for as long as Wi-Fi has been commercially available. Today, the appearance of rogue APs is usually due to poor site planning, which results in wireless dead zones. Out of frustration, an employee may set up a rogue access point to gain access to the network. But if a hacker gains entry to a building, he or she can easily set one up as well. Unless regular site survey sweeps are conducted, rogue APs may go unnoticed by IT for some time, resulting in a lingering vulnerability.
Risk Mitigation
Several risk-mitigation methods can be applied to mobile devices and Wi-Fi clients to address the wide variety of threats discussed in the previous section. Typically, the worst-case scenario is a lost or stolen device that is completely vulnerable. The practices for protecting data on corporate-liable devices involve encryption, wiping lost devices, and remote locking. These practices are also necessary when employee-liable devices are allowed to access and download company data. Therefore, they should be considered mandatory when developing a BYOD or corporate owned, personally enabled (COPE) strategy.
The key methods to consider are as follows:
• Mobile device screen locks and password protection—These are the first line of defense against unauthorized access to business data and accounts residing on a mobile phone or tablet.
• Remote locks and data wipes for mobile devices—Passcode locks are usually sufficient to prevent a casually curious person from gaining access to a smart device, but a knowledgeable hacker can easily circumvent them. If a device is lost or stolen, a remote lock can temporarily secure a device. If the device is not recovered, a remote data wipe or swipe will prevent all future access to business data and accounts stored on the phone.
• Mobile GPS location and tracking—During the lifetime of any mobile phone device, it will collect and transmit a whole host of details regarding the phone’s environment and location. This is very useful data if people or assets need to be tracked. It’s also useful in locating lost or stolen devices.
• Stored data encryption—In most cases, device locks and data wipes are sufficient to mitigate the risk of data theft, data loss, and data leakage. But as an added security measure, executives and other employees with access to sensitive information should encrypt data on their personal devices. (There is little need for most employees to have data encrypted on their personal devices, however.)
These are four basic precepts of mobile device security practice. However, the best practice is to establish controls that ensure compliance with a business plan and policy. One of the key policies must be immediate notification when a device is lost. Once notified, IT can remotely lock the device and perform a GPS location trace. If the device can be retrieved, the remote lock can be removed. If not, the device is wiped. The key to risk mitigation is to minimize the window of vulnerability via timely notification. It’s worth noting, however, that thieves who target mobile devices know to put stolen devices in metal boxes so that they can’t receive radio signals (for example, the signal to lock the device). They then bring it to a room protected from radio signals, where they can pull data from it.
It’s also important to balance user satisfaction with risk mitigation. To maximize employee satisfaction (and policy acceptance), it’s essential to realize that some level of freedom and autonomy in the use of employees’ own devices makes for a happier workplace.
Mitigating the Risk of BYOD
The proliferation of wireless mobility throughout the general population has caused the BYOD trend to become a norm in business. It started when companies began issuing BlackBerry mobile devices to enable employees to access e-mail remotely. Soon, employees began requesting that their personal BlackBerry devices be configured for use with the BlackBerry server.
It wasn’t long before the BlackBerry found itself usurped by Apple, Android, and even Windows Mobile. It became common practice for employees, including CEOs and CTOs, to bring their personal devices to work and to use them to gain access. This allowed employees to consolidate all their communications, whether business or personal. Business policymakers, who were less risk-averse than IT, soon saw the potential benefits of having employees use their own devices. These benefits, which included increased productivity, creativity, collaboration, and mobility, were too good an opportunity to pass up, despite the obvious risks. It was therefore not a case of IT allowing BYOD; it was a matter of securing it.
To address the problems associated with having employee-owned devices active on a secure company network, it was imperative to develop access and acceptable use policies. After all, a business may be deemed culpable and responsible for a device using unlicensed or pirated applications on its network. Furthermore, it might find itself deep in litigation if an employee were to use a private mobile device with illegal content, were to be the source of a hate crime, or were to engage in pornography or something similar, which the authorities traced back to the company network. This is why mobile device management (MDM) and mobile application management (MAM) are so important to a company’s security policy.
Mobile Device Management
MDM is a technology that has emerged to enable network security administrators to manage mobile devices. MDM typically sends over-the-air signals to mobile devices to distribute applications and configuration settings for all makes of mobile phones and other mobile devices. The intent is to provide a central point of control and policy from which to enhance the functionality and efficiency of mobile communications while reducing costs and risk.
MDM architecture consists of a server element, which is the central management system, and a client element, which resides on the mobile device. The MDM server provides automatic identification and configuration of any new mobile device that attempts to join the network for the first time. Subsequently, it maintains a history of all configurations and updates sent to the devices on the network and can send new updates over the air (OTA) when required. However, the job of MDM is not just to keep mobile devices up to date. The application typically provides other essential services such as remote locking, location tracking, and wiping of the device in case of loss or theft.
The server can initiate MDM security features, which send the commands OTA to the remote mobile device. This is the case when activating remote locking and device wiping, which are crucial security measures when dealing with mobile devices that may contain sensitive or valuable company data. Device tracking, however, relies on the GPS functionality of the mobile device to report its current GPS location. With both company- and employee-owned devices, these measures—especially mobile device tracking—are sensitive subjects. While employees may allow the remote locking and wiping of data from their phones under certain circumstances, they are less likely to be thrilled by the possibility of their movements being logged, especially during non-office hours. For this reason, GPS tracking is usually activated only after a device has been reported lost or stolen.
MDM provides a valuable management facility for administering and securing mobile devices on large networks. MDM can be expensive for smaller companies, but that capital expense can be avoided through the use of a Software as a Service (SaaS) cloud-based MDM solution. No matter which MDM solution is implemented, it will facilitate the ability to manage and administer a potentially large number and wide variety of mobile devices.
Mobile Application Management
MDM provides a method for configuration and policy management, but what about application management and control? How do you securely manage the provisioning and delivery of mobile applications? The inherent risk of BYOD, which makes it so unpalatable to IT, is not so much about the physical devices. Rather, it is about the data they contain and the access they enable. Of particular concern are applications of unknown origin or quality residing on the employee’s device. After all, the employee is likely to download all sorts of recreational applications, some of which open back doors to the device. To mitigate this risk, you must take the following steps:
• Secure applications—Mobile applications have few, if any, access restrictions, and can open up all sorts of phone features without the user’s knowledge or explicit consent. These include location tracking and camera operation. There may or may not be some indication of this the End User License Agreement (EULA), the legal agreement between a software developer and users.
• Secure network access—Because a mobile device could well be shared by many authorized users, it is imperative to authenticate not just the user, but also the device. You must also authenticate both the user and the device with regard to context—that is, time, location, and destination.
• Encryption—You must ensure that data is encrypted when in transport and, ideally, in local storage, too. Also, it’s a good idea to compartmentalize the data storage, separating company files from the personal data such as the employee’s holiday pictures.
Mobile application management (MAM) is responsible for administering and managing applications on mobile devices. MAM software controls the provisioning and distribution of in-house mobile applications and, in some cases, commercially available applications through an enterprise application store. With MAM, the IT department can verify and authorize the download of in-house and commercial applications from the central store. This goes a long way toward establishing a secure application management system.
When you combine MAM with MDM, you typically have the features required to authenticate users, provide and deliver applications, handle application revision management, handle updates, produce performance and status reports, and control access to users and groups. With these technologies in place, you can:
• Empower people—You can let people use the device of their choice. This improves collaboration, mobility, and the ultimate goal, productivity.
• Protect sensitive information—You can restrict access to and the downloading of sensitive information.
• Protect devices and data from unauthorized access—By using techniques such as password blocking, remote locking, and device wiping, you can secure data on a remote device, even if it is stolen.
Other Risks with BYOD
While there may be positive claims with regard to BOYD, reduced costs for IT management and security are not among them. Logic would dictate that the cost of securing a remote mobile device is higher than the cost of securing a desktop computer just based on the number and variety of smart devices and software versions in service. In addition, BYOD and, to some extent, COPE suffer from some inherent vulnerabilities that must be addressed. These include the following:
• Legal separation between personal and business use—How can IT reasonably insist that users comply with its version of “acceptable use” on a device that is not company owned? After all, it is not the role of IT to apply its view of ethics to an employee outside business hours. But adhering to acceptable use policy is something that BYOD participants must agree to and accept under a BYOD policy.
• Leakage of company data into the wild—The biggest danger that arises with regard to data security is the downloading of information onto a device that is, strictly speaking, out of the company’s control. To address this, there must be an MDM application that controls and manages employee devices. Employees must accept this, even though the device belongs to them. Employees must also accept and sign a BYOD policy that enables the company to lock or remotely wipe a device if it is lost or stolen.
• Enforcement of policy and governance—Applying policy and governance on fixed desktop systems is straightforward, but it is not so easy to apply the same rules and policy to remote, employee-owned devices.
• Threat of loss and theft—Once a device is in the hands of an unauthorized user, half the security measures have already been circumvented. All that’s left is to break the username and password combination. This may seem like an acceptable risk until you realize that for many sites, users employ the same or similar login credentials. It is especially troublesome when employees use several types of mobile devices and have access to many different layers of security.
BYOD for Small-to-Medium Businesses
If you are a small-to-medium business (SMB) that cannot afford MDM or MAM, what are your alternatives? Implementing BYOD or COPE in an SMB environment is actually quite simple, and is an approach that businesses of all sizes should consider. Not only is it secure, but it is also very cost effective. The solution is desktop virtualization.
Desktop virtualization is simply the reproduction of the user’s desktop on an Internet-accessible server. By connecting to this virtual representation of their own company desktop, users can circumvent many of the security problems related to remote access. In this scenario, all execution and read/write operations are performed on the company server. Users may execute, write, read, and edit files, but the files remain on a company server, just as they would be if the users were to perform the same actions at their desks. There are no downloads to the remote device, as only keystrokes or screen changes traverse the network. This ensures that there is no data leakage. Furthermore, by using a virtual desktop, remote users have a common desktop and set of applications. There is no longer the problem of compatibility between applications on home, personal, and company devices.
Critics of this approach note that many virtualized applications suffer performance limitations on touchscreen devices, resulting in lower productivity. As always, a reasonable balance must be maintained between security and user satisfaction.
To defend against many different kinds of attacks, security professionals must put various types controls in place. They include the following:
• Physical controls—These are the physical security measures that safeguard the environment, such as doors, locks, cameras, security gates, and fences. Physical and environmental protection is included as one of the 18 control families in NIST SP 800-53 (discussed in the upcoming section “NIST SP 800-53”).
• Logical/technical controls—These include the more obvious hardware and software devices and appliances that protect the network, such as antivirus software, firewalls, host intrusion protection, and network intrusion protection. Wireless mobile devices such as smartphones rarely have these features installed by default.
• Administrative controls—These include security policies, processes, and procedures.
MDM and MAM can provide configuration tools and can be used to enforce company policy, download anti-malware software, and sandbox business and personal data (that is, run it in isolation) before a device joins the network. For wireless networks, this is an essential part of building a secure multilayer defense policy that adheres to the principles of defense in depth, or the thoughtful and strategic application of all these components in concert.
With defense in depth, security controls are applied to networks and systems in layers, the rationale being that should an attacker breach the perimeter, there will be layers of security devices to protect assets located deeper inside the network. By building security from the inside out, you can robustly defend the inner, high-value assets, with each subsequent layer radiating outward toward the perimeter having a reduced level of access control. (See Figure 4-1.)
This model allows for lower security requirements at the perimeter, where Web servers and intranet services will be located. This is preferable to a heavily defended perimeter model, sometimes called M&M security, based on an ad campaign for the popular candy that was touted to be crunchy (hard) on the outside and chewy (soft) in the middle. This latter model is effective only if no Web services are offered to public or remote users, which is rare. Besides, if you place all the defenses at the perimeter, it might keep intruders out, but if one should break through, there is nothing to prevent him or her from gaining access deep in the network.

Defense in depth is the practice of deploying multiple forms of security to reduce the risk of deep penetration from unauthorized users. Unauthorized users would have to breach several forms of security to reach an intended target.
To secure a multi-access (wired, wireless, mobile) network, best practices call for the use of multiple layers of defense. These include the following:
• External network layer—This is the perimeter layer where Web servers and services are exposed to the Internet. Typically, layered firewalls provide a secure demilitarized zone (DMZ), which exists between the untrusted Internet and the trusted (secure) internal network. The DMZ is used for Web services and secure virtual private network (VPN) access for remote users. Other controls may include host intrusion detection, logging, and vulnerability/penetration testing. If Internet/intranet access is being provided via Wi-Fi, then the access point should be attached to one of the less-secure outer-firewall interfaces. This will ensure that the firewall permits guest devices to access the Internet but denies them access to the company network.
• Perimeter network layer—This layer uses an inner firewall to segregate the external network from internal resources. This layer normally hosts more secure and restricted Web services—typically for external front-end e-mail servers and intranet Web servers for employees, partners, and vendors. Internet proxies and external Domain Name System (DNS) servers, which resolve IP addresses to URLs, may reside here. These may be protected by intrusion prevention systems (IPSes) (which prevent authorized access), stateful packet inspection firewalls (which monitor the state of the network while blocking traffic), and deep packet inspection firewalls (which look at the payload as well as the headers for signs of malicious traffic). This is similar to a DMZ but is not intended for external anonymous access. Rather, it is a layer that requires secure access via login. It is not a fully internal system.
• Internal network—This is the where user hosts reside. Security administrators protect this layer using IPS appliances and firewalls and/or router access lists between subnets.
• Application server network—This is an inner security zone protected by another layer of highly restrictive firewall rules.
• Database server network—This is the heart of the data network. It often features very tight security policies and multi-tiered access restrictions, segregated by very high security configuration and firewalls with limited open ports.
Authorization and Access Control
The key to applying security in any network, large or small, is to allow authorized users to go about their business unhindered, yet prevent unauthorized access to network resources. To achieve this, mechanisms must be in place to control access to the network. Furthermore, there must be a way to authenticate a user’s identity and then apply authorization rules and access controls to users, data, and other assets. This is termed AAA, which stands for authentication, authorization, and accountability.
AAA
Access to a network regardless of the device or technology, whether a fixed desktop or mobile wireless device, requires authentication, authorization, and accountability, defined as follows:
• Authentication—The process of validating a claimed identity, whether a user, device, or application
• Authorization—A process that works in conjunction with authentication to grant access rights to a user, group, system, or application
• Accountability—A chronological record of system activity that can be forensically examined to reconstruct a sequence of system events
Having robust AAA measures is important to a network’s general security. Securing assets from unauthorized access via the network is as important as preventing unauthorized access to the network by intruders. This is especially true today, where there has been shift from the traditional model of users being internal to the network toward one in which many users are external and beyond the firewalls. Additionally, access control must cater to the different security and access controls necessary to support employees’ remote access.
Only a few years ago, remote-access users had company laptops with secure VPN connections that were superficially protected by a username and password challenge. The actual security, however, was much deeper, with the device also being authenticated. In other words, there was a two-part measure of authentication: the laptop and the user. This level of security was sufficient because an unauthorized user could not simply copy the VPN client application or transfer it to another machine. A user could download the client and install it from the Internet, but the authentication would fail because the VPN server application had to create and publish the security keys to the VPN client. The devices used these keys to authenticate one another and to encrypt the traffic between the pair. The VPN client server model was therefore very secure.
Today, it’s common for employees to use their own devices for work, whether they be laptops, smartphones, tablets, or home PCs. They therefore require the same level of access and authorization on their own devices as they have on their company-assigned desktop PC. This new way of accessing network resources requires a new security approach. Now, security must take into account not just the authorization of the user and his or her device, but also the context.
Context-aware security devices came about as a method to provide greater granularity in applying access controls. Security policy dictates the rules that apply to the authentication process. These rules take into consideration not just the user’s details, but which device that person is using and even the location and time. By considering these extra criteria, security administrators can apply different access rights and authorization to different contexts. For example, a context-aware security device identifies the user (who), the application or Web site that the user is attempting to access (what), the time of the access attempt (when), the location or origin of the request (where), and the device on which the request has been made (how).
Context-aware firewalls bring a level of granularity not possible with traditional or even second-generation firewalls. This is due to their flexible, application-based rule structures. Non-context firewalls, which rely on IP addresses and port numbers when constructing access rules, lack the flexibility required in today’s business environments. For example, a context-based firewall will have business rules such as “deny or allow Skype” or “allow Yahoo! Messenger but not file sharing.” While a typical firewall cannot handle these common security requirements well, context firewalls can and do. In addition, they can identify and make decisions about the required attributes—including user, application, location, time, and device—to build simple but effective layered security policies for handling remote access from BYOD phones and tablets.
Access and authentication are merely the gatekeeper functions of security, however. Once the security device has authenticated and authorized the user, you must still police activity and protect company assets, including preventing information from leaving the network. The big difference between mobile devices and company desktops is that when a user downloads a file to a mobile device, the data leaves the company network to reside on said device, outside the company’s physical control. This is potentially a big problem and is one of the many security challenges brought about by the proliferation of smartphones and tablets as network access devices.
Information Security Standards
How can IT manage all these wireless devices and enforce a common policy? To assist with this and with the broader aspects of IT security, standards have been developed. Two such standards arose from joint subcommittees of the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), called the ISO/IEC. These voluntary standards, ISO/IEC 27001:2013 and ISO/IEC 27002:2013, address different aspects of and approaches to IT security. The National Institute of Standards and Technology (NIST) developed another standard, the NIST SP 800-53. Mandatory for all unclassified U.S. government–run networks, the NIST SP 800-53 has also become a de-facto standard for many foreign governments and for private organizations and businesses throughout the world.
ISO/IEC 27001:2013
The purpose of the ISO/IEC 27001:2013 standard is to “provide requirements for establishing, implementing, maintaining and continuously improving an Information Security Management System (ISMS).” This model of establishing and improving was heavily reliant on the PDCA cycle. As shown in Figure 4-2, PDCA stands for plan, do, check, act.
Later revisions of the standard moved the focus to evaluating and measuring the performance of IT security management. Its purpose, however, remained the same: to assist in the design and implementation of an organization’s security system. ISO/IEC 27001:2013, although still focused on PDCA, addresses establishing, reviewing, and improving the information security management system and its inherent processes.
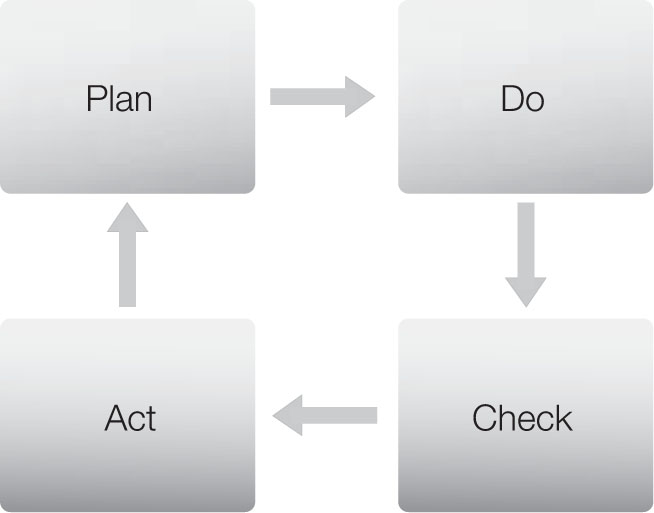
FIGURE 4-2
The PDCA cycle.
The ISO/IEC 27002:2013 standard consists of guidelines, techniques, and general principles for initiating, implementing, managing, and improving information security within an organization. The ISO/IEC 27002:2013 standard addresses 14 general groups, each with its own objectives. It also suggests 114 controls that are seen as best practices for achieving those objectives. The 14 groups are as follows:
• Information security policies
• Organization of information security
• Human resource security
• Asset management
• Access control
• Cryptography
• Physical and environmental security
• Operations security
• Communications security
• System acquisition, development, and maintenance
• Supplier relationships
• Information security incident management
• Information security aspects of business continuity management
• Compliance
This wide breadth of concern and responsibility for each of the 14 groups falls under the purview of information security within a business environment. However, it isn’t that simple, because these security standards are not mandatory. Rather, they are suggestions and best practices for addressing areas of concern. They may be highly recommended techniques and practices, but the standard remains flexible enough to allow security teams to tailor it to any situation. The ISO/IEC designed these standards to be comprehensive enough to cover even the largest of organizations.
NIST SP 800-53
The NIST SP 800-53 standard, titled “Security and Privacy Controls for Federal Information Systems and Organizations,” outlines a risk-management framework that addresses security controls for federal information. The specification covers 17 areas, including access control, incident response, business continuity, and disaster recovery.
To ensure that these safeguards are properly implemented, the NIST requires vendors seeking selection and implementation on federal networks to undergo a certification and accreditation process. These controls include management, operational, and technical safeguards, as well as countermeasures aimed at ensuring the confidentiality, integrity, and availability of systems and information.
In 2002, after the failure of such businesses as WorldCom and Enron, the U.S. government introduced new regulations aimed at preventing companies from intentionally or unintentionally losing, masking, or altering securities-related information. The collapse of these companies made it clear that ISO/IEC standards were not sufficient to protect investors and employees. Executive officers sometimes felt they were above the rules, and security officers did not question them. It simply did not occur to these security officers that financial data would need protection from modification by a company’s executive officers!
The failure of self-regulation brought about new, widespread regulations. These regulations dictated that the integrity of financial reporting was now the responsibility of auditors, executives, and members of the board. This spawned a wave of both government and industry regulations, all of which must be complied with. This has prompted the addition of the word compliance to the language of IT, in this case meaning obedience to the entire scope of security and business laws and regulations.
The Sarbanes-Oxley Act
The Sarbanes-Oxley Act (also referred to as SOX or SarbOx) was enacted to address investor confidence and corporate financial fraud through reporting standards for public companies. It ensured that public accounting firms would be liable for failures in financial reporting. Interestingly, Sarbanes-Oxley did not address information security directly. In fact, it barely got a mention. What it did address, however, was corporate governance and the integrity of financial reporting. However, because financial auditors were one of the principal targets of Sarbanes-Oxley—and they had experience implementing and auditing information security systems—the emphasis was on ensuring the integrity of financial data, which is an information security role.
The impact of this regulation was felt by all public companies, which were obliged by law to adhere to it. Of course, there were additional audits and regulations, but it also had a huge impact on information security—even though its actual aim was to regulate financial reporting and governance. Specifically, it required that “each annual report … contain an internal control report … [that] contains an assessment of … the effectiveness of the internal control structures and procedures of the issuer for financial reporting.”
This is of course a direct and unavoidable reference to securing the integrity of financial data. But for executives (and auditors), it was also a clause about information security. In one regard, that was a good thing, as it brought security to the forefront of corporate strategy (and increased security budgets along with it). Unfortunately, it also brought a shift in emphasis, because information-security efforts now had to comply with SOX. Consequently, companies targeted their information-security initiatives accordingly.
The purpose of the Gramm-Leach-Bliley Act (GLBA), originally enacted in 1999, is to secure and protect personally identifiable information held by financial institutions. The legislation explicitly states that institutions must protect the confidentiality and integrity of the financial information stored on their systems. GLBA concerns itself with confidentiality, integrity, and availability. The requirements are as follows: “Each bank shall implement a comprehensive written information security program [policy] that includes administrative, technical and physical safeguards.”
The Health Insurance Portability and Accountability Act and the Health Information Technology for Economic and Clinical Health Act
Although the Health Insurance Portability and Accountability Act (HIPAA) focuses on privacy and security for patients receiving healthcare, it has a direct impact on IT with regard to how electronic information is stored and transferred. HIPAA is concerned with confidentiality, integrity, and availability. The requirements are to “[i]mplement reasonable and appropriate policies and procedures to comply with the standards, implementation specifications, or other requirements of this subpart.”
Supplementing HIPAA is the Health Information Technology for Economic and Clinical Health (HITECH) Act, which was enacted as part of the American Recovery and Reinvestment Act of 2009. The HITECH Act addresses privacy and security concerns associated with the electronic transmission of health information and supplements and strengthens the enforcement of HIPAA rules.
The Payment Card Industry Data Security Standard
Arguably the most pervasive industry regulation is the Payment Card Industry Data Security Standard (PCI DSS), a comprehensive industry standard aimed at ensuring the safe and secure handling of credit cardholder information at all steps of the payment process. This mandatory industry regulation, which began as a series of separate programs at each of the major credit card companies, was developed in 2004. It now covers credit, debit, and ATM cards, as well as other forms of electronic payment.
PCI DSS specifies 12 requirements, which are organized into six control objectives:
• Build and maintain a secure network
• Protect cardholders
• Maintain a vulnerability management program
• Implement strong access control measures
• Regularly monitor and test networks
• Maintain an information security policy
At all levels of the payment process are checks, audits, and annual assessments that, depending on the size of the retailer (or processing company), can range from self-reported checklists to in-depth onsite visits and inspections by a team of auditors.
Given the huge financial gains for cybercriminals and the far-reaching implications of a breach of credit card information (not to mention the headlines and devastating consumer reaction), the PCI Standards Council has become one of the most powerful nongovernment regulatory bodies in the world.
Detrimental Effects of Regulations
For all their good intentions, there are negative sides to regulations—and some would argue they are big negatives.
One downside is that many regulations, such as SOX and HIPAA, do not actually address security standards, techniques, or practices. Instead, they address inflexible business requirements. Consequently, there is confusion within the security profession and in business in general about the difference between being secure and being compliant. Unfortunately, some fail to understand that regulatory compliancy is simply a subset of security, not the overriding goal.
This is a critical point, and one worth stating explicitly: Compliance and security are not the same thing. In fact several, companies that have suffered significant security breaches over the past five years—including retailers such as Target, Neiman-Marcus, and Michaels—were certified as being compliant at the time of the security incident. This is not to claim that regulations such as SOX, HIPAA, GLBA, and PCI DSS do not make companies more secure or that the practices they outline are not valid. It just means that on their own, they do not provide the strength and depth to secure an organization. In a nutshell, the following equation applies:
Security Best Practices + Regulatory Compliance = Corporate Security
Another downside of regulation is the bandwagon effect that has occurred in recent years. Worried about being left on the sidelines or motivated by the opportunity to introduce new legislation, virtually every industry, country, state, and, in some cases, city has created a data privacy regulation of its own, forcing companies that do business in their area of control to comply. In most cases, these regulations are redundant. Even so, companies bear the burden of proving compliance. Herein lies the problem. Security teams spend a significant portion of their time on compliance—or more specifically, on compliance paperwork. This takes them away from actually securing networks. Ironically, by focusing corporate governance and compliance on regulations, the industry may have made companies less secure.
Proponents of regulation argue that regulation is necessary. They believe that even more specific laws should be enacted to make industries compliant with best practices, the rationale being that companies will enforce security only if they are forced to do so. On the other end of the spectrum, opponents of regulation claim that regulations stifle innovation and prevent companies from using initiative and creativity to mitigate threats in a more economical fashion. They believe that the measure of compliance is through the validation of documented practices, procedures, and work orders. However, that means all these documents must be in order if the company is to pass an audit. The time and expense required to produce and maintain this documentation, not to mention train IT to follow the regulations and to police others in the organization, are prohibitive, especially given the scale of documentation required.
This is the problem with enforcing regulations (and indeed, any standards): An auditor can only audit what is documented. If the company keeps procedures and work practices to a minimum, then it is easier to pass the audit. The more documentation and procedures, the harder it is to comply. After all, the purpose of the audit is to check that the company’s employees do what the procedures say they will do through reasonable documented procedures, processes, and work practices. Therefore, as long as the company takes reasonable and documented measures to secure the company’s assets, that is sufficient to pass an audit.
![]() CHAPTER SUMMARY
CHAPTER SUMMARY
The existence of wireless and mobile smart devices on corporate networks presents some unique challenges to IT security professionals. When those devices are user-owned, the challenges are multiplied. Security teams must not only account for the inherent vulnerabilities of wired and mobile technologies, but must also deal with user behavior, which can be unpredictable. In addition, the increased risk associated with lost or misplaced devices far eclipses the risk associated with PCs. In response to this, IT security teams can employ processes and controls to reduce risk.
Sound planning backed by adherence to best practices must be balanced with the inherent need for legitimate access in support of the business. Likewise, compliance with government and industry regulations helps ensure that basic best practices are applied. Compliance is merely a component of a comprehensive security practice, however. It should not become a means unto itself.
Understanding the specific threats that target Wi-Fi and mobile devices and employing tools such as MDM and MAM are the keys to bringing risk down to acceptable levels without getting in the way of the business or being at odds with user norms.
AAA
Compliance
Deep packet inspection
Defense in depth
Demilitarized zone (DMZ)
Desktop virtualization
Domain Name System (DNS)
End User License Agreement (EULA)
Gramm-Leach-Bliley Act (GLBA)
Health Insurance Portability and Accountability Act (HIPAA)
Information security
Intrusion prevention systems (IPSes)
Jailbreaking
Least privilege
Mobile application management (MAM)
Mobile device management (MDM)
Near field communication (NFC)
Nonrepudiation
Payment Card Industry Data Security Standard (PCI DSS)
PDCA cycle
Personally identifiable information (PII)
Sarbanes-Oxley Act (SOX)
![]() CHAPTER 4 ASSESSMENT
CHAPTER 4 ASSESSMENT
1. What is the purpose of ISO/IEC 27002:2013?
A. To provide rules and methods for wireless security
B. To provide a standard for cross-vendor solution compatibility
C. To provide requirements for establishing, implementing, maintaining, and improving an information security management system
D. To give regulators something to do
2. PDCA stands for which of the following?
A. Plan, document, check, audit
B. Plan, do, check, act
C. People, documents, computers, access
D. None of the above
3. Compliance with the ISO/IEC 27002:2013 standard is mandatory.
A. True
B. False
4. Compliance with government and industry regulations is the best way to ensure network security.
A. True
B. False
5. The concept of least privilege does which of the following?
A. It identifies the haves and the have-nots.
B. It gives access to critical systems with minimal approval.
C. It limits access approval to one system per day.
D. It blocks access from all systems by default, giving access on an as-needed basis.
6. Mobility and Wi-Fi have made AAA-based access much easier.
A. True
B. False
7. Which of the following describes the strategy and practice of implementing multiple layers of security?
A. Defense in depth
B. Perimeter security
C. Least privilege
D. Trust but verify
8. Which of the following is a common security threat for mobile and Wi-Fi–enabled devices?
A. Physical loss and theft
B. Malicious applications
C. Phishing
D. Unsecure or rogue wireless access points
E. All of the above
9. Which of the following describes MDM?
A. It is an important security certification.
B. It is a technology that enables network security administrators to manage mobile devices.
C. It is a data privacy regulation that pertains to the healthcare industry.
D. It is a technology that enables network security administrators to manage applications on mobile devices.
10. MDM helps to do which of the following?
A. Empower employees by letting them choose their own smart devices for use at work
B. Protect sensitive information
C. Protect devices and data from unauthorized access
D. All of the above
