Chapter 7. Security for Virtual Environments: Guarding the Treasure
What Is Security for Virtual Environments?
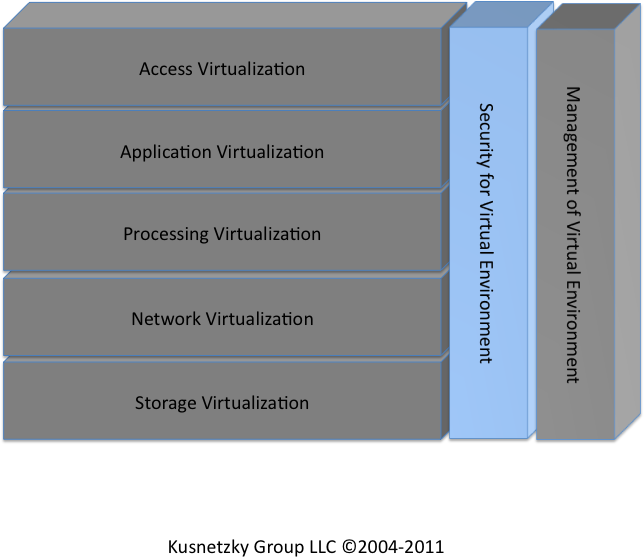
There are two segments of the Kusnetzky Group Model that cut across all of the functional segments. Security and management for virtual environments protect and manage all of the other layers. This time, we’re going to examine security for virtual environments (see Figure 7-1). Security for virtual environments refers to the tools necessary to control access to and use of all of the other layers of virtualization technology.
Depending upon the approach, security can require a small piece of software, often called an agent, to be added to each virtual resource. This, of course, can be quite a task in itself. This approach also means that part of each system’s time is spent doing security processing. If we consider a physical system supporting 40 virtual servers, each of which is supporting multiple workloads and communicating to thousands of client systems, the task of installing and maintaining all of that security software could be an overwhelming task.
Other suppliers have developed a different approach. Their approach is to capture the stream of network communication going from server to server, from application to application, from storage device to server, and funnel it through a separate security appliance server. This way, a great deal of processing can be done on each stream of communication to filter out worms, viruses, malware, and the like. This function is often combined with other management functions, such as configuration management, performance management, or automation of tasks. This approach does not require that agents be installed on each resource.
This technology is a far more recent addition to virtualized environments. It started to appear in the late 1980s as a way to protect midrange and industry-standard systems from intrusions coming from the network.
What Does Security for Virtual Environments Do?
Security for virtual environments guards access to each of the layers of virtualization found in an organization.
It is best if security for virtualized environments is part of the architecture (that is, part of the plan, rather than added on later). As systems become increasingly complex, they expose more interfaces, sometimes called “surface area,” to the network and, thus, to potential attackers.
When Is Security for Virtual Environments Needed?
The goals of security in a virtual environment are really simple. This layer is meant to protect all information and computing resources so that only authorized use is made of them. While simple in concept, this is exceedingly difficult to accomplish in reality.
As each new application or layer of virtualization technology is added, there are new areas to attack. Organizations should consider security when moving functions into a virtual environment and then deploy the appropriate security tools.
Players in the Security for Virtual Environments World
Although there are many players in the security for virtual environments market, a short summary of some of the suppliers follows:
- CA
CA has long been a major player in security. It is natural as virtual environments become more popular that CA would enhance its products to protect them.
- Cisco
Cisco offers security products that work in conjunction with its network virtualization servers and, more recently, with its unified computing systems (UCS).
- HP
HP has offered security products for its computing environments for a long time.
- IBM Tivoli
Tivoli, like CA, has been a security player for many years.
- Juniper Systems
Juniper, like Cisco, offers security products that work in conjunction with its network virtualization servers.
A Few Examples of Security for Virtual Environments in Use
There are many different environments in which security for virtual environments can be beneficial. The following list contains only a few examples:
- Access virtualization
When remote devices are accessing applications through access virtualization, security technology on the server can monitor attempts to connect to the server and overall application usage. This technology ensures that access is allowed only to authorized individuals, using appropriate devices, at authorized times, and only from authorized places. Usually this function is based on a directory of computing resources, individuals, and roles within the company.
- Application virtualization
The encapsulation technology used in application virtualization may contain tools that communicate with directory and security services back at the remote server. The encapsulated application can disable itself if it finds that it has been asked to run on the wrong system, at the wrong time, or from some unknown part of the network. The application virtualization technology would disable the encapsulated application and report the attempted misuse to the remote systems security monitoring system so that it can be logged.
- Processing virtualization
In processing virtualization configurations, security monitoring can determine if anyone attempts unauthorized use of computing resources, regardless of whether they are physical or virtual. Only authorized individuals would be able to use applications managed by workload managers/load balancers, virtual desktops, virtual servers, or clustered servers.
- Storage virtualization
Security software can monitor access to storage devices and storage servers. Only authorized applications or servers would be allowed access to information resources.
- Network virtualization
Security monitors can monitor network traffic and only allow authorized users, applications, or systems to send and receive messages. Unauthorized users or systems would not be able to use the network, even if physically attached to the network.