Cybersecurity, information security, whatever the title in an organization, is a large program made up of several smaller programs. Each has its own objectives and a defined strategy to meet those objectives. The incident response program is no different. Incident response seeks to identify, contain, eradicate, and recover from information security events as quickly as possible, avoiding adverse impacts to the business assets and processes targeted. The leader of the program constructs a strategy for meeting the objectives and deploys resources accordingly.
Full-Time Effort Required
The effort necessary to accomplish everything discussed throughout this book is not trivial. Strategy development, leading the team, planning, and practicing take time. Documentation from tabletop sessions, events, and incidents cannot wait. Failing to update the response plan or key playbook is an unforced error with detrimental effects during a subsequent event. Most information security pros are not solely responsible for incident response. This program must be balanced against other competing priorities. However, incident response needs must take priority over other demands of the information security program.
Building a Program
A lot of work goes into establishing and maintaining the incident response program. Proper leadership is required for success—getting the prerequisite protection capabilities established, understanding risks and potential attack vectors, preplanning for incident response by having a plan and creating the necessary playbooks. Finally, it takes practice, and a lot of it, to become proficient at responding to events and incidents.
Leadership
There are many everyday circumstances that are beyond the control of information security leaders and members of incident response teams: limited budgets, executives who refuse to understand the reality of cyber threats, and many other factors too numerous to mention here. Good leaders see situations for what they are and what can be done to mitigate them, refusing to think about the what ifs. Maverick McNealy, professional golfer and son of Sun Microsystems cofounder Scott McNealy, credits his father with telling him, “If you can do something about it, do it. If not, don’t worry about it.”1
Low budgets
Lack of participation in incident response by management
Gaps in preferred technology
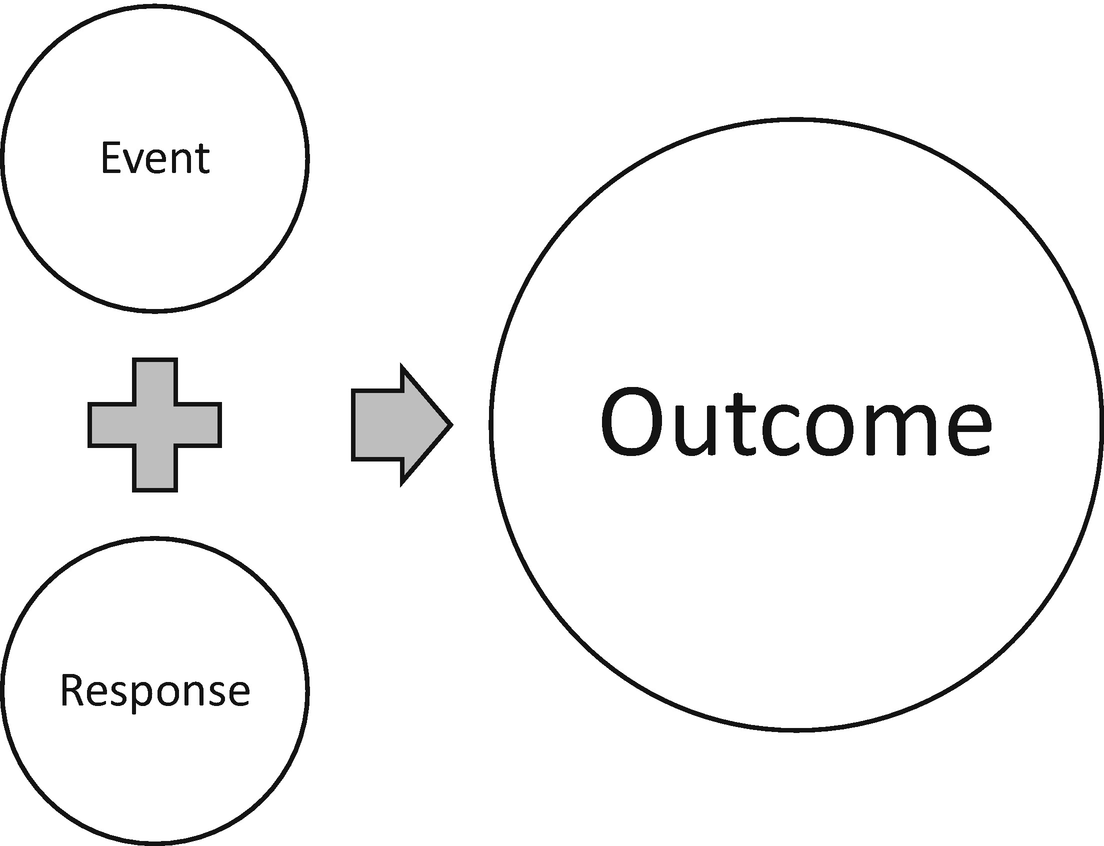
Meyer’s formula for a leader’s approach to his or her circumstances
Meyer believes that leaders cannot control events or outcomes, but the one piece of the equation under their control is response. For leaders of incident response, keeping in mind how one responds to situations affects outcomes and is controllable. Poor responses to challenging situations cause outcomes to worsen. The right response lessens the impact of challenging situations.
Continued Learning and Growth
Leaders also work on continued growth and improvement. Leaders of incident response programs must work on both their technical and leadership skills. Cybersecurity is an expansive field that is constantly changing. Threats change, exploits change, and detection methods change. Leaders must keep up on these changes. It is not necessary for them to have expertise in every competency, but leaders should know enough to enlist the help of those with the required skills and be able to spot where guidance is needed. That is the essence of building teams with the right people to get the job done. This segues into the next topic. Leaders must continue to develop their leadership skills. John Maxwell makes this point nearly every time he speaks and writes on this subject. Leaders must continue to grow, to hone the skills necessary to lead successful teams.
Balancing the Incident Response Program Against Other Priorities
The incident response leader often carries other titles. He or she may be a director or manager of the information security program or perform another similar role. The number of entities with dedicated incident response teams is few, compared to the total population, which makes prioritization of incident activities necessary.
Developing a Battle Plan
Unwanted “things” get into computer networks every day. Malicious e-mails, vulnerable software, and the constant probing by adversaries result in daily events, both major and minor. One common goal many entities share is complicating attackers’ paths to targeted information assets. Anything done to make lateral movement and privilege escalation more difficult improves network and system security. Many ways of doing this are documented in articles discussing cyber hygiene. Most of these items are not related to the incident response discussion, but one topic worth discussing in relation to incident response is segmenting the network.
Network Segmentation and Incident Response
Except in exceptional circumstances, servers should not talk to other servers, and end-user devices should not talk to other end-user devices.
vLANs and other network segments with important information assets should not allow access to any application, database, operating system, or other information system component, unless it is required as part of one’s job function.
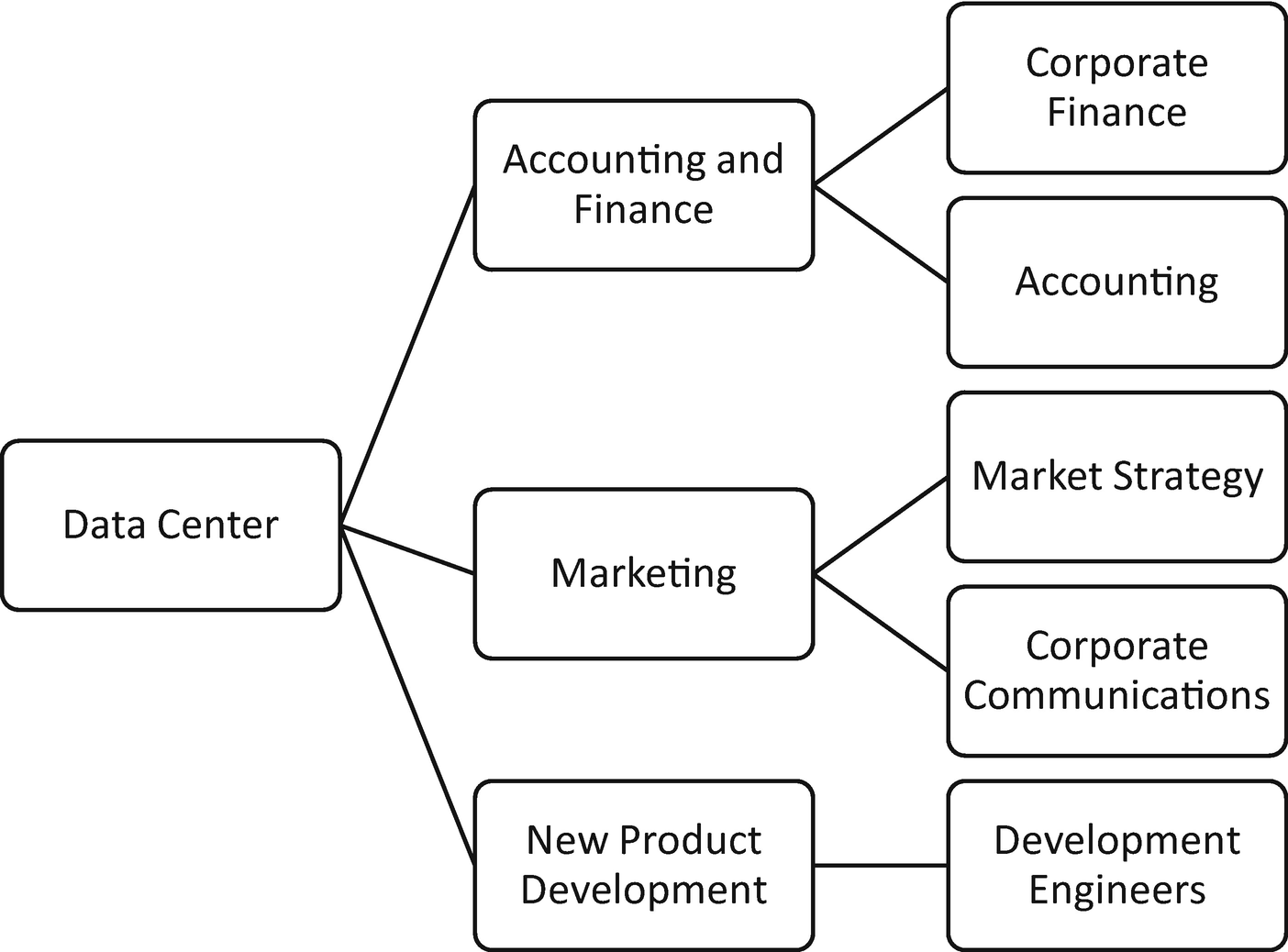
Simple breakdown of corporate groups by function
This figure shows a rudimentary structure for a manufacturing entity. This entity’s ability to thrive depends on new product development derived by the research and development team. The concept here is to break down the end users by function: examples exist for Accounting and Finance, Marketing, and New Product Development departments.
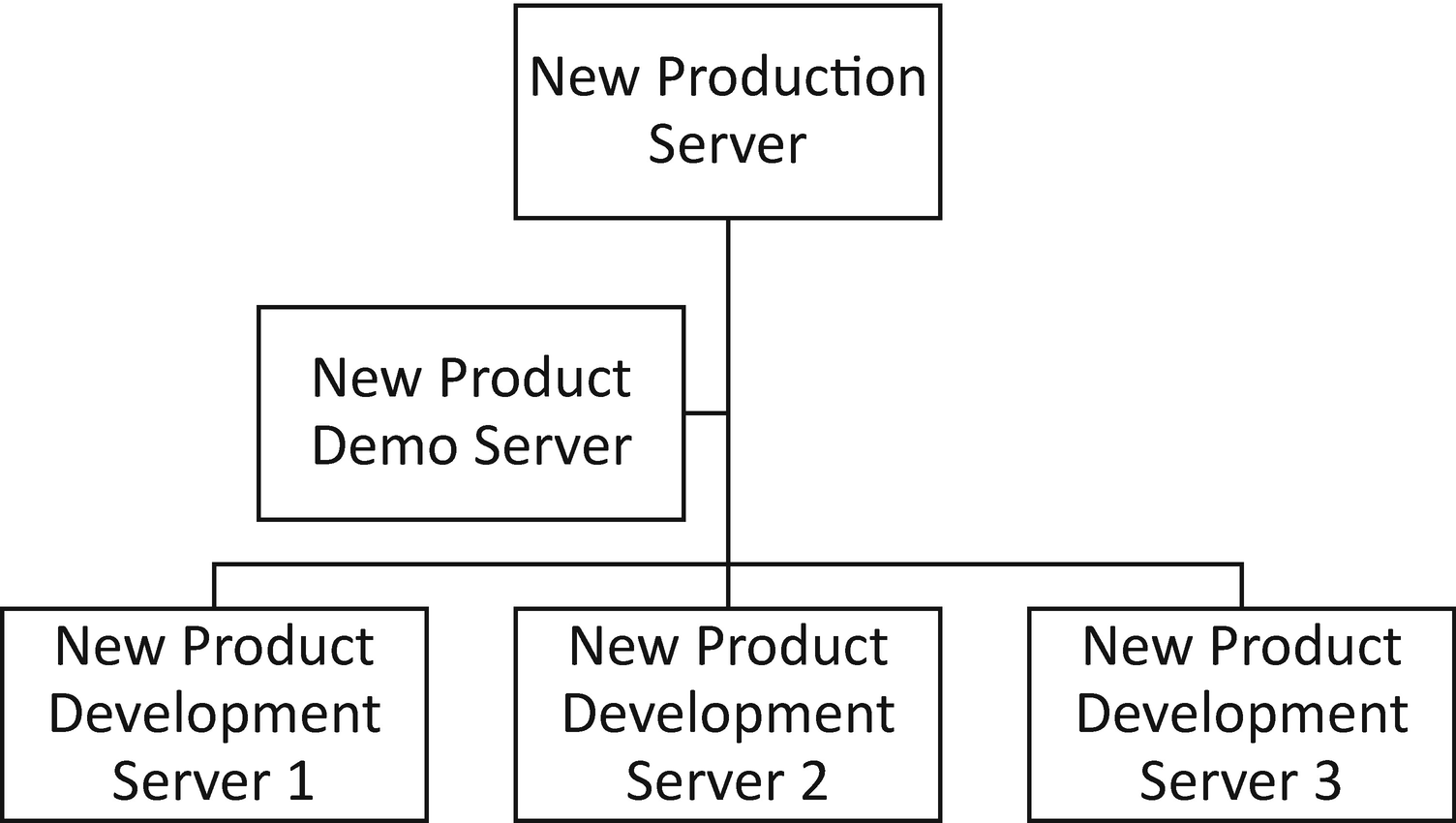
Sample infrastructure for New Product Development
Preplanning and Strategy Development
When designing the incident response strategy for this environment, the focus is to complicate the process for breaching intellectual property used in new product development. By forcing communication to occur only between laptops and servers, it makes pivoting through the environment much tougher. Any end users victimized by a phishing e-mail in Accounting or Marketing force the attacker to pivot between servers and laptops until a member of the development team is breached. Depending on the data targeted, controlling a laptop for someone working on New Product only has access to New Product Development Server 1. The same goes for New Product 2 and New Product 3. Production data is only accessible to the Production team. There is more work to be done by the intruder, and more opportunity to detect the intrusion.
The other value to preplanning and design of the network is understanding where ideal data collection points exist. In this environment, placing detection and traffic capture capabilities in line with communications related to all new products under development, being demonstrated, and produced is more valuable than any other internal data captures. If anything goes wrong, necessary data points to build a time line and investigate is available.
Identification
Applications and application servers
Firewalls
Intrusion detection and prevention systems
Packet captures
End point detection and response
DNS security monitoring
DLP solutions
EDR solutions
Infrastructure (operating systems and databases)
Many more
Data needs a place to go and a way for analysis to occur. Security events spawn many indicators. These indicators may make obvious that an attack is occurring, and others only hint at one. The increased use of SIEM solutions was designed to identify all the subtle hints of an attack and alert cybersecurity teams. These represent just some of the capabilities organizations must implement to identify potential security incidents.
Containment
Containment requires an organization to collect indicators of compromise. Indicators are attributes and artifacts left behind during events. Threat actors have specific attributes, based on tools, techniques, and procedures used. Specific types of malware or ransomware make changes to systems the incident response team use to search the remaining information systems and assets. When matches to the indicators hit, the incident response team can quarantine those systems, taking them offline for further analysis.
The process of gathering an initial set of indicators and searching for signs of each in the remaining systems are documented in playbooks used by the response team. Playbooks are specific to event types: malware/ransomware, denial of service, lost assets, data theft, and unauthorized use or misuse of company assets. This is not a complete list but identifies very common scenarios seen by incident response teams.
During the containment phase, forensic evidence used to determine the root cause and the time line illustrating how the event unfolded is also gathered. Images of the affected systems are obtained for complete analysis of all system characteristics during containment.
During this time, incident response teams deal with contact from members of the business and company leadership who are seeking answers. This is to be expected. The organization could be impacted, depending on the severity of the events in question, and these individuals have a need to know what is occurring. The key is to give facts and not speculate. Speculation causes more harm than good.
Eradication , Recovery, and Lessons Learned
Eradication is the process of removing the malicious artifacts from the environment. It also includes mitigating vulnerabilities exploited and other weaknesses, such as those exploited by the adversary. Recovery processes place systems back into production, in a stronger state, it is hoped Updates to network hardware, additional patches, and configuration changes designed to strengthen the systems from future attacks are key. Finally, ensuring that the team sits down and goes over the event is important. This requirement is often missed. Entities do not find the time to go over the incident response process and document what is effective and what needs improvement. Common examples include updating the incident response plan or playbooks, to add or modify steps, and discussing behaviors and actions of the team, to reinforce expectations. The goal at the end of the eradication phase is to document the incident and events in an executive report outlining actions taken, outcomes, and lessons learned, with metrics tracking activities directed at desired outcomes. Ultimately, management, or the body representing management at the cybersecurity table, must review the documentation and authorize necessary changes.
Summary
Building the incident response program requires significant planning and work. Successful programs are led by strong leaders willing to associate themselves with individuals smarter than they are, if necessary, to make the response program successful. These leaders must understand the risks to critical assets; the tactics, techniques, and procedures used by attackers; and how to respond to security events. Examples of these strategic decisions and deployments include segmenting networks and deploying detection capabilities necessary to identify the presence of intruders in the network. The goal of rapid identification of bad actors targeting sensitive assets and efficiently containing and eradicating the intrusion are primary for most entities. Detecting, responding, and recovering from security events is, arguably, the most important subprogram within the information security program.
