The incident response plan forms the blueprint and strategy for responding to events and incidents. It contains the purpose, scope, definitions and elements of incident response. Roles and responsibilities, definitions and escalation steps are common elements addressed in the incident response plan. The purpose presents the team with the “why” behind the plan. Why does the cybersecurity team care about planning for events and incidents? And why will time and money be invested in improving the entity’s ability to successfully respond to incidents? The scope of the plan highlights the authorization given the incident response team to take necessary steps when dealing with events. Taking systems offline until confirmation that nothing malicious occurred will not be popular if business operations are interrupted. Roles and responsibilities dictate who is on the response team and how he or she is expected to act when events are investigated. Definitions are important as well. What is an event, incident or breach? Outlining these in the plan takes the guesswork and, it is hoped, the debate out of the process. This is particularly important when events are present. Debating these definitions in the early stages wastes precious time.
Purpose
Incident response plans are designed to protect the organization, maintaining the confidentiality, integrity, and availability of data and other assets, to avoid disruptions to business and reputational damage foremost. Data assets include intellectual property, trade secrets, strategy, company financials and customer information. These elements, if affected by an incident, could have varying degrees of impact on the entity. Purpose is why the incident response team exists.
Scope
The scope section establishes the jurisdiction for the incident response plan. Any anomalies affecting the assets and information systems of the entity will be investigated by the incident response team according to the plan. The scope section can contain roles and responsibilities of the leader(s). The leader of the incident response process is named here, and authorized actions are stated. These include calling together the initial response team, once an event is escalated, up to the leader of the team. Other examples include consulting legal, collecting affected devices, and consulting without outside forensic firms, if such firms have been retained and are available.
Scope sometimes outlines high-level overviews of the process, descriptions of how events are triaged, and the escalation path and steps for addressing events and incidents.
Definitions
This section clearly defines what constitutes cybersecurity events, incidents and breaches. Not all plans use these exact definitions. Some might use incident and breach; it depends on the entity. Events are normally any atypical occurrence in an IT system or network, that is, anything out of the ordinary that is detected. Mature entities with established baselines of network traffic and user behavior see more events then entities with less mature detection capabilities. An administrative login occurring during off hours is an example of an event. Normally, incidents are violations of policy and threats to the entity’s assets. A user transmitting sensitive documents to third-hosting providers such as Dropbox in violation of company policy is an incident. Sometimes incidents become breaches. Breaches occur when unauthorized individuals view, change, or render assets unavailable. In healthcare, breaches are defined as the theft, misuse, or destruction of protected health information in electronic form, or ePHI (electronic protected health information). This would be confirmed via a risk of compromise assessment. In other sectors, breaches affect customer records, especially if those records contain personally identifiable information (PII), intellectual property, or trade secrets.
How to Respond to Incidents
Within the incident response plan, the strategy for the incident response program is outlined. This includes goals, roles, and responsibilities ; how to analyze and triage events; and the requirements for escalation. The stages of the incident response and the strategies for each are also documented. The most common incident response phases are identification, containment, eradication and recovery. The strategic importance and objectives of each are outlined in these sections.
Incident Response Goals
Protect the organization’s infrastructure, assets, and business operations.
Comply with federal, state, and local regulations.
Minimize the potential for negative publicity.
Prevent or minimize financial liabilities.
Minimize customer disruptions.
These are examples and may differ from entity to entity, based on the nuances of the business. What remains important is for management to work with the incident response and cybersecurity teams to document goals consistent with the needs of the entity.
Roles and Responsibilities
Roles and responsibilities state the expectations of each person on the team. Within the initial response team, the extended group involving legal, compliance, IT leadership, and external consultants, and the group involving senior management and external legal counsel, dozens of individuals have a role in incident response. No matter how the groups are organized and named, missing defined roles and responsibilities opens the door to chaos and actions not aligned with the incident response plan. Practice and discussion driving home better understanding of roles and the need to stick to actions outlined in each is important. It’s not uncommon to spend considerable time during post-incident reviews going over roles and responsibilities, emphasizing the need to adhere to what’s outlined in the plan.
Triage
When events are brought to the attention of help desk analysts, security analysts, or whoever is on the receiving end of alerts, it is up to these individuals to analyze and prioritize each. Many alerts are benign and closed by the analyst. Others require investigation before a conclusion is drawn. This requires escalation of the event. If managed security service providers (MSSPs), forensics investigations, and threat hunters are on retainer, conferring with these partners to assess the event might be necessary, based on the type of event.
Escalation
Potential incidents, by some definitions, are attacks against an entity’s network that are under way. When incidents are confirmed, notifying the incident response leader commences and the incident response plan is invoked. The plan must include escalation of all types, when an incident is suspected. Internal and external legal teams must evaluate the situation, because business agreements likely contain provisions dictating breach notification time lines. Vendors doing business with healthcare organizations are required to comply with notification rules in business associate agreements. The incident response team must take the time to properly evaluate potential incidents, keeping in mind notification requirements, based on data affected.
Event and Response Phases
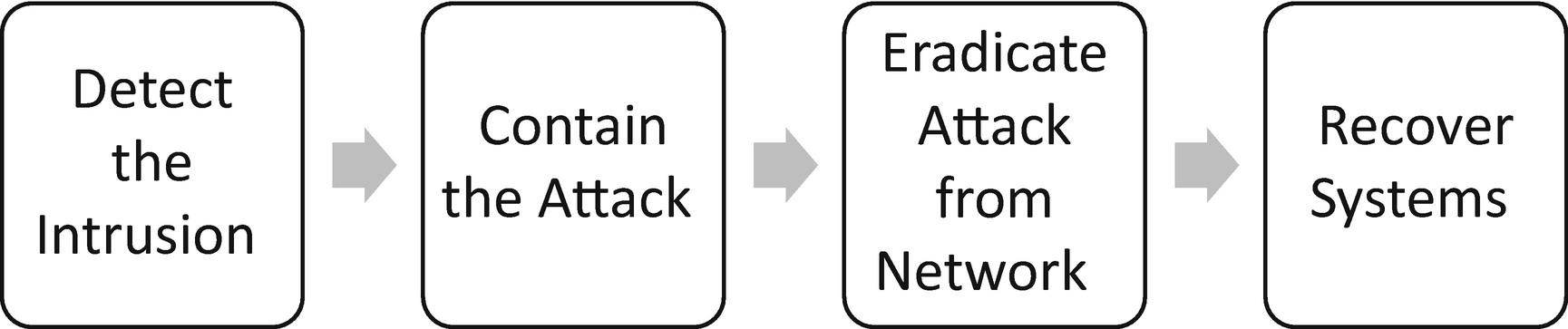
Four response phases found in many incident response plans
Intrusion detection at the perimeter
E-mail gateways and spam blocking
Data loss prevention
End point detection and response (EDR)
Log correlation and analysis
Effective log strategies require capturing logs from many different sources. Applications, servers, network devices and databases are needed to gain visibility over the entire entity. Outsourcing the correlation, analysis and maintenance of log capture and event correlation make economic sense for entities of all sizes. Successful partnerships are designed so that the service provider can analyze alerts and supplement each with context.
Containing the attack, identifying all the devices affected, calls for searching for indicators on end points and devices such as those present when the issues first began. With an MSSP or other service provider assisting, responsibility for finding all end points with IOCs might be better served with the service provider searching for other infected end points. The key is to compile a list of affected devices quickly while being thorough. The MSSP might achieve these objectives. Once identified, taking the devices offline keeps them from connecting or staying connected to others spreading the infection.
Eradicating the issues involves removing any malicious software and files loaded onto the affected systems. It also requires remediation, through patching or configuration changes, exploited vulnerabilities leading to the issues.
Once all the malicious files and programs are removed from affected end points and devices, systems are brought back onto the network, and production resumes. The cybersecurity team should keep a close eye on those systems, and the rest of the network, for signs the malicious software is present in the network.
Summary
The incident response strategy is outlined in the incident response plan. In it, the scope, definitions, and how to respond are outlined. The response section includes roles and responsibilities, how to triage and escalate events, and the steps to contain, eradicate, and recover from events, incidents, and breaches. All pieces of this plan are important, as each lays the foundation for tactics used to protect the entity from cyber events. The scope authorizes the incident response team to respond to events detected. Events are anomalous traffic and user behavior indicating that an attack against an entity’s information systems may be under way. Incidents indicate a violation of policy and that intended damage to an organization’s information assets is imminent. Finally, a breach means the confidentiality, integrity and availability of data assets have been compromised. This compromise is confirmed, and the incident response team must determine the extent of the damage, while executing the containment, eradication and recovery from the breach.
The incident response team, whether using internal resources or engaging outside firms with expertise, needs a strategy for containing and eradicating events and incidents. Many organizations use outside experts, because resource limitations make it difficult to employ individuals with expertise in these disciplines.
Roles and responsibilities outline expectations for each member of the response team. The importance of individuals following their activities in accordance with the plan cannot be overstated. When team members go off-script, trying to solve issues alone, problems occur. This is especially true when events are first discovered. Escalation requirements are also key. Determining right away the type of event—malware, ransomware, or other type of attack—and whether the malicious agent is a nation state, cybercriminal organization, or insider threat are factors considered when determining escalation requirements. The incident response plan’s strategic guidelines are the blueprint for developing tactical measures to mitigate cyber events and incidents and avoid breaches. This document must be reviewed and updated by the cybersecurity steering committee each time events occur and annually.
