So far, we’ve been focused on cybersecurity and privacy for adults. If you’re a parent, grandparent, or educator, this chapter will help you understand how to better protect the kids in your care.
The Internet Is Everywhere
I’ll tell you right off that this was probably the hardest chapter in the book for me to write. Why? While I’m perfectly comfortable giving you advice adult to adult, it feels like lecturing as soon as I try to give you advice on what you should do for your children. I raised two girls myself who are now in college, and I know that what makes sense for my kids may not make sense for yours. Every parent, every child, and every family’s social dynamic is different. Obviously, what makes sense for adults doesn’t always make sense for kids. But what makes sense for a given child can change drastically just a year or two later. So, it’s important to realize that the suggestions in this chapter need to be carefully considered for each child individually and continually reconsidered as they grow older.
All the risks for adults that I discuss in this book apply to kids, as well. However, kids have a lot less maturity and life experience than adults do. Kids are very focused on the now and just don’t have the context required to think more than a few days into the future. Furthermore, you are not likely to be there when they have to make a decision about what to do or not do. Access to the Internet is everywhere. Even if your particular child doesn’t have a smartphone, you can bet that most of their friends do. According to a Common Sense Media study in late 2019,1 53 percent of kids have their own smartphone by the time they hit 11 years old and up to 69 percent by age 12. Overall, 85 percent of teenagers have their own phones. They probably also have access to other Internet-connected devices: tablets, smart TVs, set-top boxes like Apple TV or Fire TV, and even browse the web using an e-reader like a Kindle. If it has a place to enter a Wi-Fi password, then it can connect to the Internet.
So, while you can certainly take some measured precautions and set reasonable limits on the things you can control, you just have to realize that Internet access today is everywhere. You simply cannot keep your kids from it, unless you want to move away from civilization (in which case you don’t need this book).
As just one example, I heard my daughters talking a couple years ago about what someone had posted on their “finsta” account. I knew about Instagram, of course, but I had never heard of finsta. So, I asked what it was, and they casually explained that it’s fake Instagram account (as opposed to their “real” account, or “rinsta”). While the rinsta account is wide open and public, the finsta account is much more restricted—usually just very close friends. It’s more popular with girls than boys, apparently, too. Was I worried? No, not really. I trusted my girls, but I also knew that at their ages, there wasn’t much I could do to prevent things like this short of taking away their phones and their laptops. It’s just a fact of modern-day life.
As I said before, most of the security and privacy recommendations in this book apply to people of any age, so in this chapter, I’m really just adding a few other thoughts to consider that apply specifically to children.
The Grandmother Rule
The Internet is everywhere…and the Internet is also forever. Anything that happens in cyberspace has the potential to remain there not just for the rest of your life but for as long as our race survives. Digital information doesn’t decay and can be copied infinitely without degrading in quality one bit. (Get it? One bit?) Digital stuff just yearns to break free. Once you take that picture or send that message or record that video, you should assume that one day it could be seen by someone you didn’t intend to see it. And don’t be fooled by any device or software manufacturer that claims they can lock this stuff down, preventing copying or transfer or whatever. Also, don’t count on claims that messages will “self-destruct” or that you can delete messages after you send them. If it can be seen by the recipient, then it can be captured and shared with someone else. If you can manage to drill one thing into your kid’s head about the Internet, this is it. They should consider that anything they post on social media could someday by seen by college admissions officers, potential employers, and (eventually) their own kids. It’s less likely that private messages will be made public, but especially when the recipients are also kids, I would assume that anything is possible.
This leads me to the Grandmother Rule: don’t do anything online that you wouldn’t gladly share with your grandmother. I don’t even have to explain that. Somehow Grandma is the gold standard on proper behavior. She just is. It’s not quite WWGD (what would Grandma do) because Grandma likely doesn’t have a finsta account. But tell your kids that if they would feely squeamish about showing something to Grandma, then they probably should reconsider doing it. Most laws in this country apply differently to minors, and much of your legal record may be expunged when you turn 18. That does not apply to Internet stuff. Once it’s out there, you can’t get it back.
Cyberbullying
One of the most amazing uses for the Internet is communication. With our smart devices and computers, we can send messages to dozens of people around the globe simultaneously and nearly instantaneously. We can have a face-to-face chat with anyone on the planet as if they were standing right in front of us. And we can share our thoughts on any subject at any time with friends as well as complete strangers. While the benefits are undeniable, this power comes with a dark side for our kids: cyberbullying.
As long as we’ve been a sentient species, there have been bullies—kids who take some sort of sick pleasure in harassing or embarrassing another child. But unlike traditional bullying, cyberbullying can happen anytime and anywhere. It’s also possible for cyberbullies to act anonymously, making it hard to stop. Finally, as we’ve just established, it can be nigh impossible to erase this stuff from the Internet. Embarrassing pictures or hurtful messages can live forever.
The original rule of human society, the Golden Rule, applies in cyberspace just as it applies in real life: treat others the way you wish to be treated. The Internet can seem unreal to kids because it’s not personal. Something you would never do or say to someone in person is somehow a lot easier to do with a web or phone app. So, tell your children to imagine that they’re doing it in person…in front of their grandmother…and then see if it still feels right.
Adult Content
This is a tough one. The Internet is chock-full of adult content —from simple nudity to unbelievably graphic violence and pornography. There are some ways you can try to restrict their devices and your home network (and I’ll discuss them in this chapter and the next), but the reality is that kids have many, many other ways to get on the Internet that you can’t control. Your best approach here, in my view, is to have The Talk with your kids and include a discussion about the Internet. Encourage them to come to you with any questions they have and counsel them to use their best judgment. If you plan to set up technological restrictions on their phones and computers, explain that you’re trying to protect them from seeing things you can’t unsee and that there will be plenty of opportunity to explore these things when they’re an adult and have the maturity to handle it.
Don’t Panic
I’m not trying to scare you. Like I said at the beginning of this book, any powerful tool can be used for good and for evil and everything in between. When all is said and done, the best thing you can do, for yourself and your children, is to get educated. You can’t let fear of a few bad actors cause you to deny your children the amazing benefits of a connected world and easy access to the collected knowledge of humanity. The trick is to alert your children to the risks while preserving the sense of wonder and adventure that should accompany such a magnificent and powerful tool.
Summary
Kids have all the same risks on the Internet as you do, but they don’t have the same experience or maturity, which makes it harder for them to weigh the consequences of their actions.
The Internet is forever. Don’t do anything on the Internet that you wouldn’t gladly do in front of your grandmother.
Treat others on the Internet the same as you’d treat them if they were standing right in front of you, in front of all your friends (and your grandmother).
Don’t panic! The Internet is just a tool, though a powerful one. The benefits far outweigh the risks, and you should embrace it. Focus on education and staying engaged.
Checklist
This list is by no means exhaustive. I strongly encourage you to use the links provided at the end of this checklist to do some further reading. Many excellent websites have been created to specifically address online safety for kids, and I am just scratching the surface with this list. However, these are some of my favorite tips for helping to keep your kids safe and happy on the Internet.
Tip 10-1. Create a Dedicated Account for Each Child
Every child’s needs and maturity levels are different. Creating a computer account for each child will allow you (and the child) to customize the settings, preferences, background images, web bookmarks, and so on. It’s not just about custom parental controls, it’s also about giving everyone their own space and the opportunity to express their individuality. (It can also contain the damage if they somehow get infected with malware.) Use the steps outlined in Chapter 5’s checklist to create these accounts. On both Windows and Mac OS, you have the option to designate these new accounts as “family” accounts or accounts that have “parental control.” Go ahead and select that option as you create the account.
This is also a good tip for online accounts and streaming services like Netflix. Don’t share your accounts with your kids—get them their own accounts or profiles so you can individually control the content and usage.
Tip 10-2. Use Parental Controls for Young Children
Both Windows and Mac OS have built-in parental control settings. This software can be used to limit what websites your kids can access and how much time they spend on the computer. In my experience, these tools work well until they get to the point where your kids need to use the Internet consistently for school work. Many perfectly normal websites that can be used for homework can be blocked by these utilities. While you can try to approve each of them as needed, you may find that you constantly have to tweak the settings. When I got to that point (probably when they went to high school), I just turned off the website blocking. And remember… statistically speaking, they probably have a smartphone, anyway, so you’d have to block their access there, as well. It’s hard to do.
When you get into the parental controls configuration, there are lots of possible settings. Just use some trial and error here. You’re going to need to tweak these over time anyway as your child gets older and is able to handle more mature material.
Tip 10-3. Creating Email Accounts for Children
Most kids today will prefer to using messaging and social media apps to communicate, but there will still be many times when they will need to have an email account. When Gmail first came on the scene, my daughters were infants—but I decided to create accounts with their names right away, so they didn’t end up with something like “grrrrrrl152” or something when they got older. Of course, data privacy wasn’t as big of an issue then. I wish I had also created another account for public stuff that didn’t contain their names. So when you create this account, be sure not to include their names (even their first name), address, phone number, birth date, or even birth year.
ZillaMail: https://zilladog.com
KidsEmail: https://www.kidsemail.org
ZooBuh: https://www.zoobuh.com
TocoMail: https://tocomail.com
You need to realize a couple things, though. First, it’s quite likely that your child’s school will require them to set up a Google email account or similar, so that students can easily collaborate online. Many teachers will assign and collect homework online this way, too. Also realize that if you are too restrictive, your kids will find a way to get their own email accounts. So the preceding options are probably only good for elementary school kids.
For older kids, I would look at the same services I recommended in Chapter 8. However, I would also assume that this email address (that doesn’t contain any identifiable information) will become their “public” email address when they get older—that is, the one they’ll give out to retailers, newsletters, and other spam-inducing stuff. For this purpose, I really like Fastmail. Yes, it costs money (about $30/year), but it’s a really powerful service with decent privacy protections. But the killer feature for fighting spam is that each account can have up to 600 email aliases! These are basically extra email addresses that all route to you, but allow you to cut them off at any time.
Tip 10-3a. Microsoft Windows 10
With Windows 10, Microsoft requires both you and your children to have a Microsoft account to use parental controls. I personally find it ridiculous that Microsoft requires children to register to have parental controls on a home computer. If this was an added feature with extra benefits, that would be okay—but requiring it for any level of parental control seems to me like a poor policy. This means your child will need to have an email address, for example.
- 1.
Create a Microsoft account for yourself, if you haven’t already. You can do this in Windows 10 (see Chapter 5 for help).
- 2.
Create a Microsoft account for each child who will require parental controls (again, see Chapter 5 for details).
- 3.
While signed into Windows at the parent, create a family group with Microsoft by going to this website:
- 4.Click “Create a family group”. If necessary, sign in using your Microsoft account credentials.
 Figure 10-1
Figure 10-1Windows 10 Create a family group
- 5.If you have another parent or guardian, you can add them first as an Organizer. Enter their email address and click “Send invite”. They will then need to check their email inbox and accept the invitation.
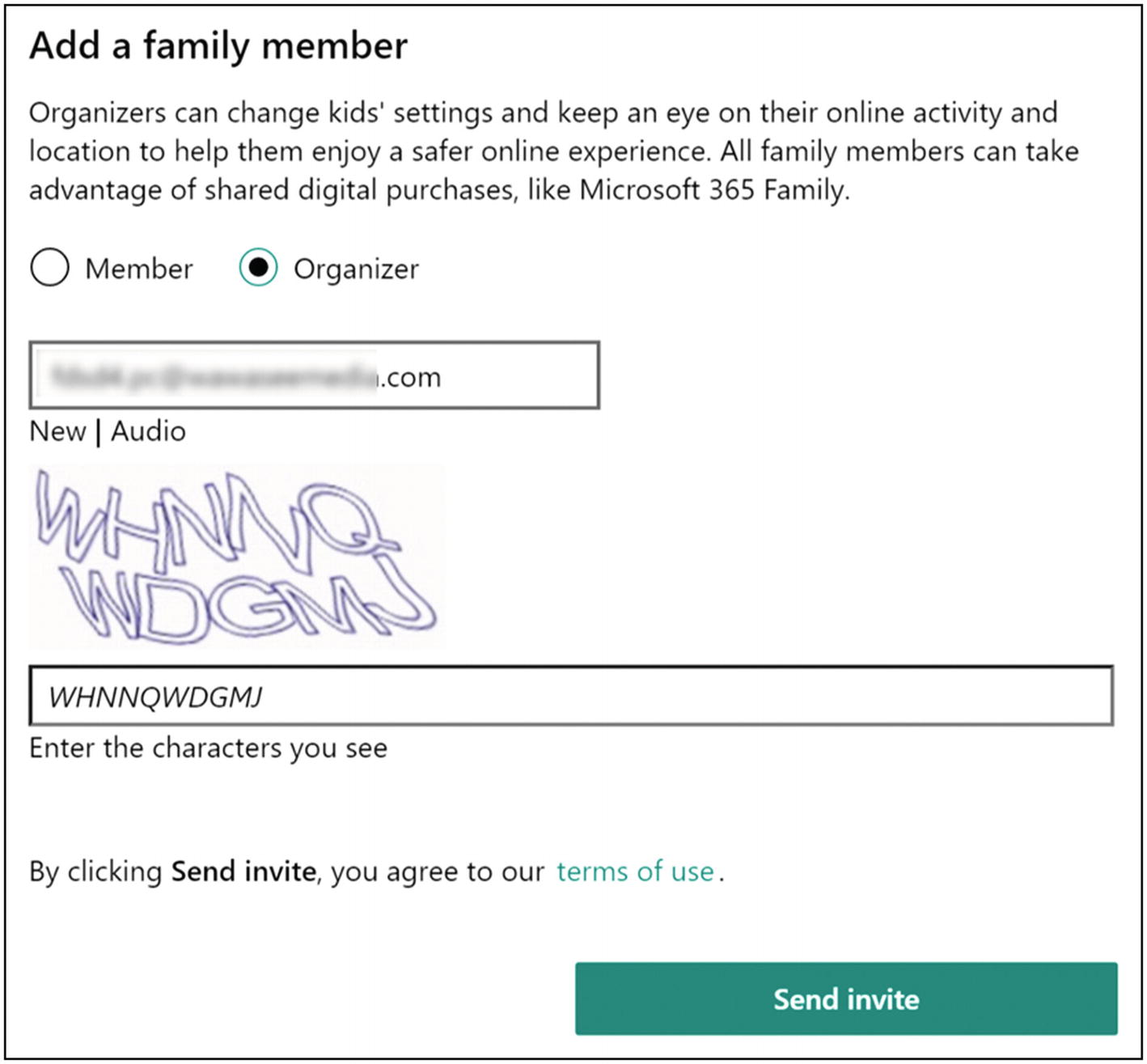 Figure 10-2
Figure 10-2Windows 10 Add a family member
- 6.
Repeat the previous step for each child, but make sure to check the “Member” option (not “Organizer”). Accept the invitation via email to complete the sign-up process.
- 7.
For children under age 13, you’ll need to jump through a few more hoops. One question you’ll be asked is whether you want to allow them to sign into third-party apps. I would say no to this, personally. You can change this later.
- 8.Once accepted, you can adjust their parental controls, and you can manage their parental control settings on your Microsoft account on the Web. This includes things like restricting websites, screen time, and spending (Figure 10-3).
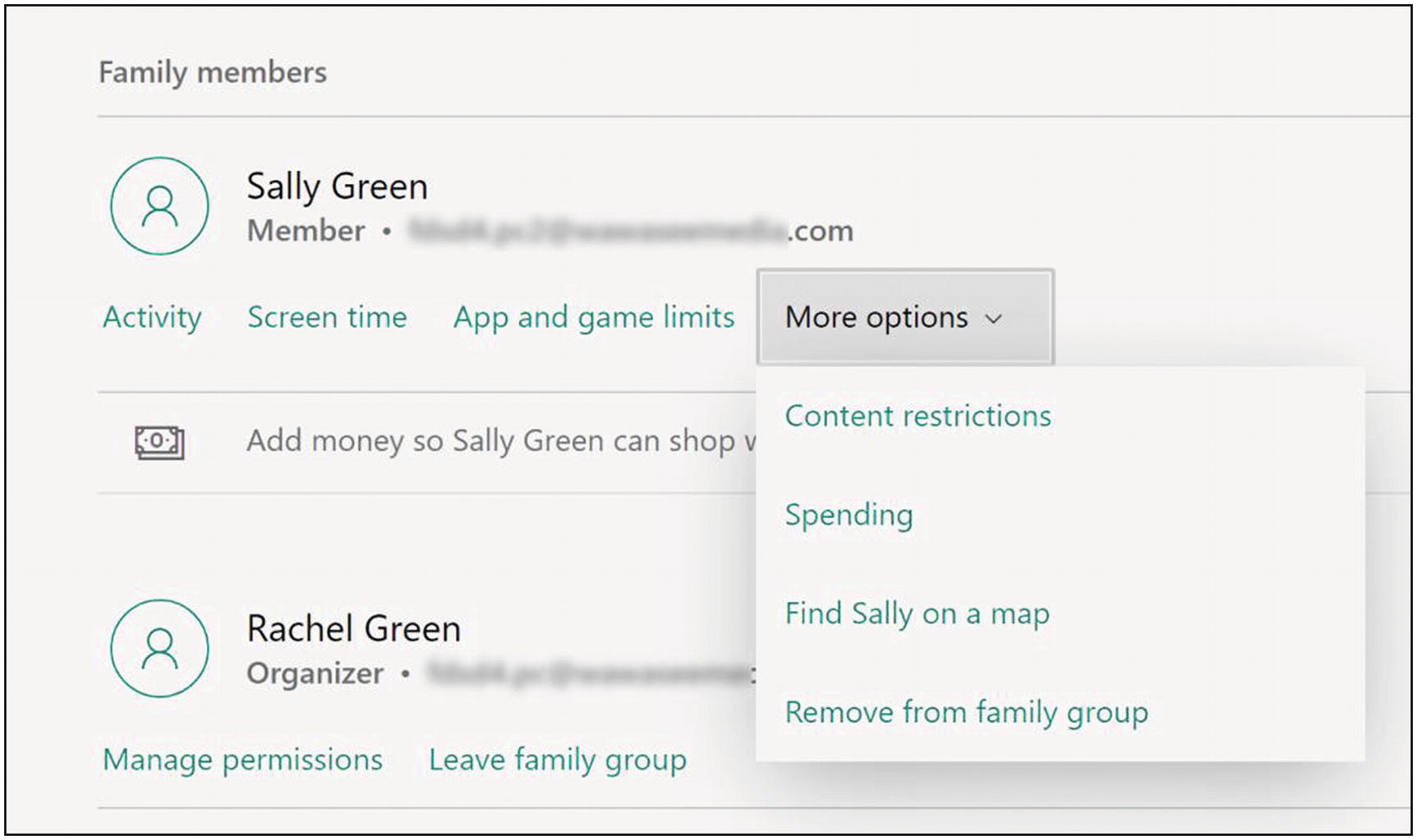 Figure 10-3
Figure 10-3Windows 10 Family members settings
Tip 10-3b. Mac OS
- 1.
In order to set up parental controls, you need to set up a few things first, unfortunately. You will want to do these steps while you’re logged in to your main parent account on your Mac.
- 2.
If you haven’t created a separate account for your child yet, do so now. See Chapter 5 for help. Be sure to make this a “Standard” account (not “Administrator”).
- 3.
Next, you will need to set up Family Sharing. Note that this will require either a credit card or debit card because it will enable family members to make purchases using the shared card (with controls, obviously). If you don’t already have this card associated with your Apple ID, pick the card you want to use and have it handy.
- 4.Open System Preferences and click the “Family Sharing” icon at the upper right. You can enable the sharing of purchases among family members (Figure 10-4). Apps, music, movies, and many other things will only need to be bought once and shared by all. (Note that some random things can’t be shared due to licensing issues.) Make your choice and click “Next”.
 Figure 10-4
Figure 10-4Mac OS Family Sharing shared purchases
- 5.
If you don’t already have a credit or debit card associated with your Apple ID, you will be asked to add one here. Follow the instructions to add a card that will be used by family members to make purchases (you’ll have the opportunity to require approval for your kids’ purchases).
- 6.You will now be asked to confirm that all family purchases will use this card (Figure 10-5). Select the proper card and click the “Next” button.
 Figure 10-5
Figure 10-5Mac OS Choose shared payment card
- 7.
You will then be asked if you want to share your location with your family. Make your choice and click “Done”.
- 8.Before you can set up Screen Time (parental controls), you’ll need to add your children to your new “family”. Click the “Family” tab at the left, and then click “Add Family Member” (Figure 10-6).
 Figure 10-6
Figure 10-6Mac OS Add a family member
- 9.
This process is a little involved and has a lot of different paths depending on what you already have set up for each child—too many to try to cover here. Just follow the instructions to add each child. If you choose to create an Apple ID for your child, use their real name and age. This will also create a new iCloud email account for them (which is used as their Apple ID). For the security questions, I would enter false info that you can remember (store it in LastPass to be safe).
- 10.
Once all your children have been added to your Family Sharing, you can now customize their parental controls. From System Preferences, click the Screen Time icon. There will be several options here. Select your child using the menu at the upper left, and then go through each tab at the left to customize their settings for allowed times and duration of usage, application restrictions, communication, and content restrictions. Repeat for each child. You can also use this control panel to monitor your child’s computer and iPhone usage.
- 11.
Apple has a website entirely devoted to parental controls and family sharing of applications, movies, and music. Be sure to check it out:
Tip 10-4. Research Before Allowing Your Kids to Sign Up
I can’t stress this enough. Don’t trust what anyone else tells you because most people really don’t know what they’re talking about. Spend the time to check out the site yourself and search the Web for parental reviews (see some of the sites I list at the end of this checklist). Also, be sure to check the date on the reviews and favor the ones that are most recent—at least within the last year or two.
Tip 10-5. Teach Your Kids to Protect Their Identities
When signing up for websites or social media or whatever, enter as little identifying information as possible. Teach your kids to never give out their full name, address, phone number, email address, or even school name to strangers. Tell them to leave their names and birth date out of any user ID’s they create, too.
Tip 10-6. Be Able to Access All Accounts and Devices
At least for young children, you should always have the login credentials to all of your kid’s accounts and devices (computer accounts, smartphones, tablets, game consoles). If a device has a fingerprint reader or face scanner, you can just add your fingerprint and/or faceprint to the allowed list. Your kids should know that at any point you can log in and see what they’ve up to. You might even schedule some somewhat random check-ins to drive this home and make it feel real. When they get old enough (whatever age that is for your child), you can relax this restriction. At some point, you’re going to want to give them their privacy and establish an honor system.
Tip 10-7. Honor the Age Restrictions
Almost all websites and Internet services require that users be at least 13 years of age to join. You have to enter your birthday as part of the registration process, though they have no way to verify this. Nevertheless, it’s not good to teach your children to lie about their age in order to gain access to a website. Some sites and services will have overrides that allow parents to grant access after sufficient covering of their butts.
Note that you might want to consider using an incorrect birth date, however—maybe a date that’s one to three weeks after the actual date. It’s just one more piece of identifying info that you should avoid, if you can. Just be sure to write down what date you chose (and anything you fibbed out) so you’ll be able to verify these details if for some reason you need to recover the account.
Tip 10-8. Friends Must First Be Met in Person
Teach your children that people on the Internet may not be what or who they claim to be. A good rule of thumb is to insist that they first know someone in real life (or as the kids say, “IRL”) before they can “friend” them in social media or communicate with them via chat rooms, email, social media, or text. That is, they must have met this person face to face, in person. You must approve any exceptions to this rule.
Tip 10-9. Lock Down Chromebook Settings
Tip 10-10. Remember the Golden Rule
The Golden Rule applies in virtual realms, as well. But beyond just being good policy, it’s important for your children to realize that anything they do on the Internet can potentially be leaked to people they don’t intend. That basically means that anything they post online could be seen by anyone, possibly many years in the future.
Tip 10-11. Keep Computers in a Common Area of the House
While children should have a certain degree of privacy in their communications, it’s just asking for trouble to allow them to surf the Internet in a closed room. This applies to smartphones and tablets, as well. You can require them to put their phones and tablets on the charger before going to bed (and that charger should not be in their rooms). I don’t care how good your kids are, the temptation to respond to the inevitable chat/video requests in the middle of the night will be too great. This rule also ensures that their phones are fully charged at the start of each day.
Tip 10-12. Use Family Friendly DNS
As we covered earlier in this book, whenever your computer wants to talk to another computer on the Internet, it needs to first look up its address. This is done using Domain Name Service (DNS)—DNS is what converts “google.com” to an IP address that is routable.
Cloudflare 1.1.1.1 for Families: https://blog.cloudflare.com/introducing-1-1-1-1-for-families
See Chapter 7 for help changing your DNS settings.
Tip 10-13. Use Device Tracking (Judiciously and Fairly)
Both Android and iOS (iPhone, iPad) have the ability to locate a device, and you should enable it for your child. You should use it only if the device is lost or stolen or if you need to find your child in an emergency situation. You should also make it clear to your child that you have this ability but will use it only in these special situations, and any other situations you deem valid (lay it out for them). You don’t want to be oppressive and you want to foster trust, so try to be reasonable here. The key is to be very clear about your family privacy policy and stick to it. You can revise this as time goes on, of course, and in response to misbehavior.
Tip 10-14. Create a Contract for Your Kids
Tip 10-15. Parental Resources
Common Sense Media: https://www.commonsensemedia.org
ConnectSafely: https://www.connectsafely.org
Protecting Kids Online: https://www.consumer.ftc.gov/topics/protecting-kids-online
