Where Are Attacks Coming From?
It is clear by now that the bad guys are out there on the Internet using all kinds of tools, from automated to those that target you specifically. Everyone knows that a public IP address is required to connect to the Internet. These addresses are allocated across the globe, so you should be able to find out where these attacks are going.
“Each quarter, Akamai publishes a quarterly “State of the Internet” report. This report includes data gathered across Akamai’s global server network about attack traffic, average & maximum connection speeds, Internet penetration and broadband adoption, and mobile usage, as well as trends seen in this data over time.” (www.akamai.com/stateoftheinternet/)
Figure 1-4 shows the results for Q4 & Q3 for 2009 in a top 10 format by country originating the attacks. This report is available free upon registering on the Akamai website; it is an interesting report and worth reading.
Figure 1-4 Q4 2009 - Attack Traffic Top 10 Originating Countries
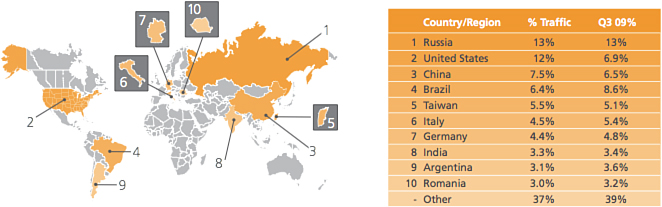
The interesting aspect of this data is that Akamai maps out the ports that it is seeing generating these attacks, as shown in Figure 1-5. This top 10 list of attacked ports is dominated by Microsoft-DS (tcp port 445) used by its Server Message Block (SMB) running on TCP to enable a variety of things, most notably file sharing. It is speculated that this domination of list is because of the global infection of PCs running Windows that have been infected by Confiker.
Figure 1-5 Q4 2009 - Top 10 Attack Ports
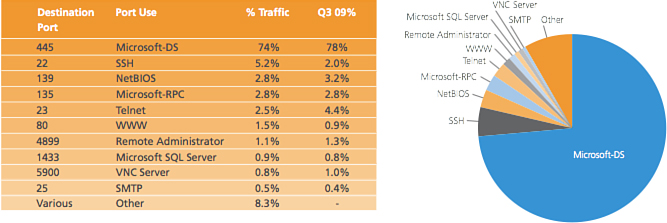
Conficker is a computer worm that was first detected in 2008. It uses TCP port 445 aka Microsoft-DS by targeting the Windows operating system. This worm is believed to have the largest number of infected PCs since the inception of the Internet; estimates vary, but 6 million plus is generally agreed to be the low estimate. Although Microsoft has announced a $250,000 reward for information leading to the arrest of the Conficker creator, this author feels that the money would be better spent making its software more secure given how many of that attacks relate to it. Cisco also has free global correlation for IPS intelligence to provide additional visibility into attack mitigation. OWASP, owasp.org, also maintains its top 10 application threats as it evolves—remediation tools including test tools such as Web Goat and well-documented application security guides.
