Firewall Frequently Asked Questions
Before looking at the overall operation of a firewall, the following sections examine and answer some of the fundamental questions about them.
Who Needs a Firewall?
This is perhaps the most frequently asked security question. If you plan to connect to the Internet, you need a firewall. It does not matter whether you connect from home or your company connects—you need a firewall, period! The increased penetration of broadband Internet services to the home and their always-on Internet connections make home security even more important.
Why Do I Need a Firewall?
You read about security threats in the papers or hear about them on the evening news almost every day: viruses, worms, denial-of-service (DoS) attacks, hacking, and new vulnerabilities to your computer. For example, Code Red, Slammer, and other threats/vulnerabilities. are changing with the prevalence of malware and botnets.
It is no secret that hackers are out there, and they are out to get you. Often, you do not know who they are, but you do know where they are and where you do not want them to be (in your network). Like pirates of old who roamed the seas, hackers freely roam the open expanses of the Internet. You do not want them to enter your network and roam among the computers that connect to it, and that is where a firewall becomes a requirement.
You know that you must protect your network from these attackers, and one of the most efficient methods of protecting your network is to install a firewall. By default, any good firewall prevents network traffic from passing between the Internet and your internal network. This does not mean that the firewall can stop all traffic—that defeats the purpose of being on the Internet. It does mean that the firewall is configured to allow only web browsing (HTTP/port 80) to access it from the Internet. Along the way, the firewall provides Stateful Packet Inspection (SPI) rules to every incoming packet (as discussed previously in Chapter 2, “Security Policies.”)
The alternative to having a firewall is allowing every connection into your network from anyone, anywhere—there wouldn’t be any sort of packet inspection to determine whether an attack is hidden within one of the incoming packets. Not having a firewall is ill-advised and will make your organization wide open to everyone on the Internet.
Do I Have Anything Worth Protecting?
I often hear people say, “I understand that if I had something worth protecting, I would definitely need a firewall. However, I do not have anything an attacker would want, so why should I worry about a firewall?”
Networks and their resources are important to the way our society conducts business and operates. In practical terms, this means that there is value to your network and having it effectively operate. This increased role of networks means that you definitely have something worth protecting to some degree, as documented in the following list:
• Downstream liability: This sounds like a confused Bassmasters fishing show title, but it is perhaps the next big step in the legal evolution of the Internet. Downstream liability involves allegations that an attacker has taken control of a target computer (yours) and used it to attack a third party. Assume that it is your company’s computer that has been compromised by a hacker. Your company’s failure to protect its own systems has resulted in the damaging of a third party; the attacker used your computer as a weapon against the third party. Your company is therefore negligent due to lack of due diligence because it failed to protect against reasonable risks—specifically, no firewall was in place, or it was improperly configured, which is just as bad.
The prudent person’s responsibility for security here is to use reasonable care. You can find a more detailed definition in Prosser, Wade, and Schwartz’s Cases and Materials on Torts: “...requiring the actor to conform to a certain standard of conduct, for the protection of others against unreasonable risks.” Who says Hollywood liberalism doesn’t contribute to society?
• Lost data: You have probably heard the stories of companies that lost all their business data in hurricanes such as Katrina or the September 11 attacks, and many companies did not recover. What if your company experienced the same loss of data because you did not have a firewall and an attacker deleted your data because he could? What would happen to your business? Would it cost money to re-create everything? Would you suffer lost sales? Would you still be employed the next day?
• Compromise confidential data: Every organization has data it considers confidential and, if lost, might cause financial problems, legal difficulties, or extreme embarrassment. These things might be caused by the loss of customer information such as credit card numbers, secret plans for the new weight loss formula, or secret product plans that end up in the hands of a competitor. The list goes on, and when you have been hacked, you must assume the worst. Perhaps this is why most cybercrimes go unreported—it is embarrassing, and admitting to being hacked is a sign of weakness that could affect the reputation and brand of a company.
• Network downtime: Have you ever gone to an ATM machine or a grocery store to get cash and paid with your cash card in the swipe card readers? The networks enabling these devices to operate usually work fine; however, if they were not protected, an attacker might cause them to go down. The loss of revenue from these networks can quickly grow if they are unavailable. Downtime is the bane of any network, and a cost is always associated with these types of events.
Ultimately, everyone has something worth protecting, and failure to do so is ill-advised; it is just a matter of time before something happens. The next question is, “What does a firewall do to protect my network?”
What Does a Firewall Do?
A firewall examines traffic as it enters one of its interfaces and applies rules to the traffic—in essence, permitting or denying the traffic based on these rules. Figure 7-1 shows a firewall filters both inbound and outbound traffic.
Figure 7-1 Firewall in Operation
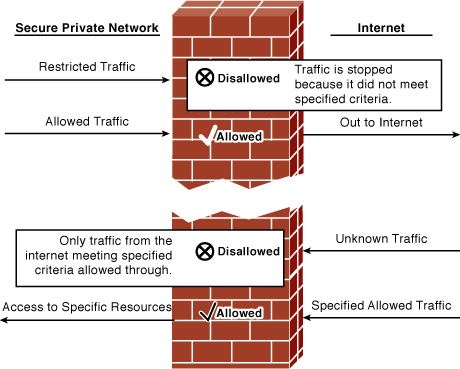
Firewalls use access control lists (ACLs) to filter traffic based on source/destination IP addresses, protocol, and the state of a connection. In other words, normally you might not allow FTP/21 into your network (via the firewall), but if a user inside your network begins an FTP session out to the Internet, it is allowed because the session was established from inside the network. By default, firewalls trust all connections to the Internet (outside) from the trusted internal network (inside).
A firewall can also log connection attempts with certain rules that might also issue an alarm if they occur. Finally, firewalls enable you to perform Network Address Translation (NAT) from internal private IP addresses to public IP addresses. The section “Firewall Operational Overview” discusses the roles of a firewall; however, here you can tie the firewalls back to Chapter 2’s security policy discussions by examining how a firewall enforces your security policy.
