Firewalls Are “The Security Policy”
What kind of traffic is allowed into or out of your network? How do you secure your network against attacks? What is your security policy? What happens to the people who do not follow the security policy? Who is responsible for writing and updating the security policy?
All these questions are valid, and they all deserve answers. Having a network that connects to the Internet via a firewall is only the first step to security; because this book is about first steps, this would be a perfect place to start. You should now know that the security policies form the basis of how firewall rules are determined and then implemented into a production network.
Do you remember the old saying, “No job is ever finished until the paperwork is done?” Well, no security solution is complete until you establish a written narrative of the rules and regulations that govern your organization’s security posture. This written version of your security rules and regulations is known as a security policy. Now, this policy document is different in nature and scope than a security plan, so be sure that you understand what makes a policy unique from every other security document an organization maintains. And just what is it that makes a security policy different from a security plan? Drum-roll please....
PUNISHMENT! That is correct; a security policy includes what is permissible and what will happen to you if you do not live by the law of the land. If you do not follow the rules, you can be
• Fired or dismissed
• Demoted
• Demoted and fined
• Fired, dismissed, and demoted
• Demoted, dismissed, and even punked!
• All the above
All kidding aside, the security policy document spells out in clear language exactly what the regulations and expectations are, who enforces them, and what happens to you if you break them. A security policy is all about the consequences of user actions coupled with audit in the form of AAA usually.
Having said that, how can a firewall be the security policy? Simple—a firewall does what it does by following the rules configured by a network engineer or information security officer (ISO). These rules should perfectly align with a written narrative version found in the security policy document you have on your shelf, next to the box of CDs at the back of the server room or sitting useless in some manager’s office. Grab that old dusty binder and check it out. You should see that the security policy document contains information and a listing of the network rules (refer to Chapter 2). The interesting thing is that all the rules in the policy document form the basis of what you must configure on the firewall.
Note
Wait a minute! We have a hand in the front row. Yes...you with the confused look on your face. Your question is, “Why is the binder that contains the security policy so dusty and located in such an obscure place?” As strange as that might sound, go ahead and put your hand down. I will tell you the answer to that question is that most organizations either do not have a security policy set, or the set that they have is so old that it was written during a previous presidential administration.
The configuration rules entered on a firewall should perfectly align with the rules outlined in an organization’s security policy. If you were to examine the firewall’s configuration file, you might see something like Example 7-1, which is a portion of a Cisco Adaptive Security Appliance (ASA) configuration.
Example 7-1 Sample Cisco ASA Firewall Rules
access-list OUTSIDE extended permit tcp any object-group HTTPS-SERVERS eq https
access-list OUTSIDE extended permit tcp any object-group WEB-SERVERS eq www
access-list OUTSIDE extended deny ip host 90.84.x.x any
access-list OUTSIDE extended permit icmp any any time-exceeded
access-list OUTSIDE extended permit icmp any any unreachable
access-list OUTSIDE extended permit icmp any any echo-reply
access-list OUTSIDE extended permit tcp any host 12.238.x.x eq ftp
access-list OUTSIDE extended permit tcp any host 12.238.x.x eq ftp-data
The access-list permit statements in Example 7-1 are most likely in keeping with some security policy statement that dictates what services are allowed, by name, to enter the protected network and the destinations to which those services are allowed to access. Specifically, this example shows the customer having web servers (www-80), secure web servers (https-443), and an FTP-21 server. These permit entries in your firewall’s configuration are your network’s security plan, and the security policy defines what they are and why they are present.
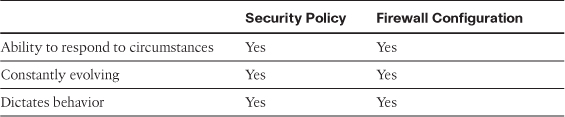
To expand on the firewall to security policy analogy, examine some additional security policy bullet points and how a firewall aligns with them:
• A security policy outlines what action will be taken in response to circumstances that arise.
• A security policy document is constantly evolving and changing to meet new security needs.
• A security policy dictates both acceptable and unacceptable usage parameters.
If you perform a point-by-point comparison of a security policy with a firewall configuration, you see that firewalls act with a written security policy document, as shown in Table 7-1.
Table 7-1 Comparing Security Policies and Firewall Configurations
The intention of this section is not to convince you that a firewall is a replacement for a security policy document, but to get you thinking about security as an all-encompassing philosophy of plans, policies, and security devices. You must put a great deal of thought into a complete solution—not simply rely on a single aspect to protect your network. When you are ready to plan your firewall’s configuration and develop the rules permitting or denying traffic, you should use your security policy as the starting point. Firewalls are the physical and logical manifestations of your security policy.
