Man in the middle attacks are a class of attacks where a third party can intercept, capture, or alter the communication between two entities. Abbreviated as MITM, these attacks exploit the open nature of wireless networks that allow an attacker to see all wireless traffic being transmitted from clients to the access point. If the communication is sent in the clear or in a way that can be decrypted by the attacker, the information gleaned from a successful MITM attack could lead to a successful compromise of the target client and potentially the network infrastructure.
On wireless networks, capturing the traffic sent between two devices is relatively easy; anyone within range of the wireless signal can capture the traffic. Open networks, such as those found in public hotspots, are notoriously easy to manipulate. Though it is slightly more difficult when the target network is encrypted, it is not impractical. As we have seen in previous chapters, it is possible to capture wireless traffic and decrypt pre-shared keys or compromise credentials to authenticate to the wireless network. Once the attacker is able to join the target network, they can attempt to insert themselves into the traffic flow from the clients also connected to this same network. By manipulating the fundamental services provided by the infrastructure, including name and address resolution, an attacker can redirect client traffic through their device allowing them to capture it or tamper with it. A successful MITM attack on clients connected to the target network could allow an attacker to capture credentials, steal web application session cookies, or even hijack a session an administrator may have to critical infrastructure.
In this chapter, we will discuss various techniques to perform Man-in-the-Middle attacks over a wireless network. These are:
- MAC address spoofing
- Rogue DHCP server
- DNS attacks
- NBNS spoofing
The goal of any Man-in-the Middle attack is to be able to redirect traffic, not intended for you, through a device that you control. If an attacker is connected to the same wireless network as a targeted client, they can utilize various techniques to accomplish this. Kali provides many of the tools required to manipulate network services that will modify the destination of where legitimate clients are sending traffic. Once the modifications are in place, the clients will rely on the attacker's computer for doing things like name resolution or as the next hop for their IP traffic. Having this position in the network allows the attacker to spoof replies to the client or capture any traffic normally destined for the network gateway.
The following diagram depicts the typical state of the network where the normal communication traffic flows between the client computer and the default gateway:

On any IP-based network, wireless or otherwise, address resolution is fundamental to mapping between the layers of the OSI stack. When a client needs to communicate with another network device that is on the same Layer 2 segment as it, it will ask other devices for an IP to MAC (Media Access Control) mapping through a process called ARP (Address Resolution Protocol). This process will result in an IP address to MAC address mapping being stored in the client's ARP table. After this process, when it needs to send data to another device on the same network segment, it will use the ARP table to determine which MAC address to send it to. This functionality can be exploited by an attacker if they are able to manipulate a client's ARP table and insert themselves as that destination MAC address. The attack that is used to accomplish this is known as MAC address spoofing or ARP poisoning. This technique will trick the victim device into thinking that your attacking computer is actually the gateway of the network.
The legitimate gateway will still exist, so we must send the victim an update to their TCP/IP stack that says that a new device, or computer, is now the next hop where they should send all of their traffic rather than the device they had originally been assigned as the gateway.

You can see that the attacker and the victim are both connected to the same wireless network and in this scenario, the default gateway is also acting as the wireless access point for the network. ARP (Address Resolution Protocol) is a Layer 2 protocol that maps IP addresses to physical (or virtual) adapters. For this attack to succeed, both the intended target and your computer will need to be in the same Layer 2 network (VLAN) and both of you must be able to reach the default gateway.
Once the ARP poisoning attack has been launched, the attacker computer will spoof the client's MAC address as its own adapter to the router and at the same time the router's MAC address will also be spoofed on the victim computer to make it look like the attacker's computer is now the default gateway for the network. If this succeeds, both devices will now send their traffic through the attacker's computer, who will then bridge the connections together to make it look to both sides like nothing has changed. This will then put our attacker's computer right in the middle of any communication from the victim that is destined for networks outside of the local VLAN including the Internet.
To accomplish this, we will first have to update Kali and install an additional package, Ettercap, which is excellent at automating this ARP poisoning and sniffing scenario. ARP spoofing can very easily turn into a Denial-of-Service attack to the victim whose ability to reach the default gateway will be interrupted if the attacker fails to bridge the networks together properly if either one of the ARP poisoning attacks goes awry.
Ettercap handles the identification of victim and router MAC addresses, the ARP poisoning attack, and the sniffing of information off of the new bridged network connection. However, once this attack succeeds, many of the other Man-in-the-Middle attacks documented later in this chapter will then be possible since the attacker computer now can see all traffic flowing from the victim to the Internet.
- We start by updating the
aptdatabase using theapt-get updatecommand.#apt-get update
- Install Ettercap and the graphical interface for Ettercap using the following command:
#apt-get install ettercap-graphical
- To launch Ettercap using the GUI, issue the following command:
#ettercap –GThis brings up the GTK interface for Ettercap. Within this application, we can set up the ARP poisoning attack between the victim and the router and also sniff the traffic looking for any sensitive information including usernames and passwords that are sent in the clear.

- Next, we will enable Unified Sniffing, which is what will allow us to bridge the connections together and sniff the traffic that traverses our interfaces. Click on Sniff | Unified Sniffing…

The status box at the bottom of the Ettercap application is where you will see the results of the commands, or captures, that are generated. After starting Unified Sniffing, Ettercap will initialize and load plugins and Starting Unified Sniffing… will be displayed, as seen in the following screenshot:
- This changes the menu options you have across the top of the application. Next, click on Hosts | Hosts List to see all of the hosts that Ettercap has identified on the local network. This list will be returned as both IP addresses and MAC addresses. You will need to know ahead of time the IPs that are associated with the victim's computer and that of the default gateway for the network. This can be done using reconnaissance tools like nmap, fping, or any other tool that allows you to enumerate network hosts.

The total number of hosts discovered on the Layer 2 segment will be displayed with their corresponding MAC and IP addresses, as seen in the following screenshot:

For this example,
192.168.0.1and the corresponding74:DE MACwill be the default gateway for this wireless network, and192.168.0.112, orA7:BF, will be the victim computer that we are trying to capture traffic from. - Select the first host, in this case
192.168.0.1, and choose Add to Target 1 from the bar below the Host List. Then select the victim computer,192.168.0.112, and choose Add to Target 2. The resulting command output will display in the following status box: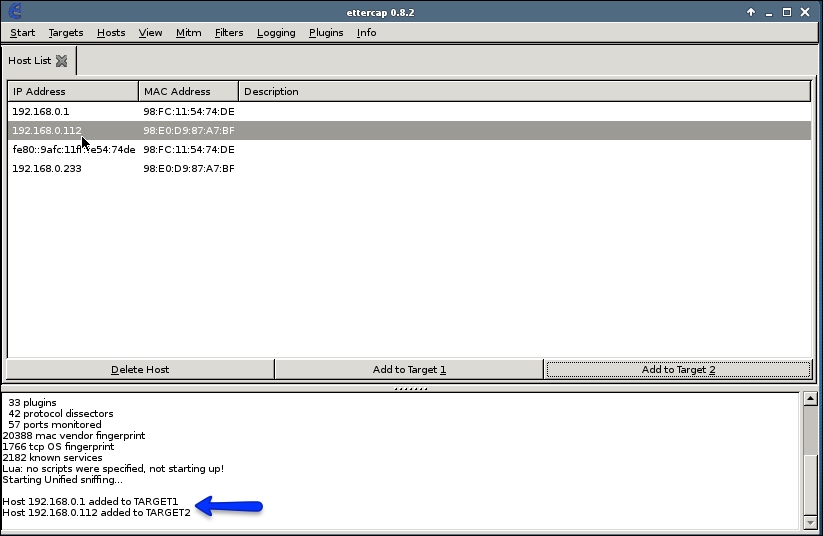
- After you ensure that you have your two hosts added to the Target Lists, you will launch the ARP poisoning via the Mitm menu on the title bar. Mitm | ARP poisoning…, as shown in the following screenshot:

Two options then appear on the resulting dialog box. Sniff remote connections, and Only poison one-way. These options have the following effects:
- Sniff remote connections: This tells Ettercap that you want to sniff the network traffic in both directions (inbound and outbound) from the two targets that were selected before. This option is what will allow us to act as the man-in-the-middle and attempt to pull out any sensitive or unprotected traffic using Ettercap itself. With the ARP poisoning attack in place, we can also use other applications besides Ettercap to attack the victim.
- Only poison one-way: This option will ARP poison the router with the attacker's MAC address and impersonate the client; however, the router's MAC address on the victim will not be modified creating a triangle of traffic, in effect. This option does not poison the client, but relies on the traffic destined for the client to be routed through the attacker. In our case, we want to see the outbound and inbound traffic and will not select this option.

- After clicking OK, the man-in-the-middle attack is launched on both the victim and the router, which in this case is our wireless router. The Ettercap status box will now begin to display any interesting traffic that is being sent either from or to the victim.
In this example, you can see that the client has connected to a remote host using Telnet, which is an unencrypted protocol. A username and password were discovered through our universal sniffing process and were displayed for the attacker, as seen in the following window:

