Beacon frames are sent by access points at regular intervals, and client stations also send beacon frames when they are participating in ad hoc mode. A beacon frame contains important information about the network capabilities, such as channel information, timestamp, and configured SSIDs. Wireless clients can detect the presence of access points by listening for the beacon frames transmitted from Ops. They gather the information in Beacon frames to determine which networks are available and which access point to connect to. Typically, clients will choose to connect to an access point with a strong signal strength when all the other capabilities of the access point are equal. In this attack, an attacker fakes these beacon frames and sends them in large numbers to confuse the wireless clients; sometimes, this may make things difficult or prevent the wireless clients from connecting to their preferred networks.
In this attack scenario, we explore the fake beacon flood attack on wireless networks. This attack does not require a particular access point to be selected; instead, we use mdk3 to broadcast random SSIDs to the target network. This flood of available wireless networks may prevent legitimate clients from finding and connecting to the target network. In the second part of the attack, we use selective SSIDs to be broadcasted by MDK3.
Firstly, set up the wireless card for scanning, bring the card up, and create a monitor mode interface on the wireless card. Use the ifconfig utility to check the status of the available interfaces. Run the following commands to bring the card up. Here, we assume the wireless interface to be wlan0:
#ifconfig wlan0 up #airmon-ng start wlan0
We use MDK3 to perform a fake beacon flood attack against wireless clients in our range. To perform the fake beacon flood attack, we use mdk3 with option b:
- Run the following command to perform the attack:
#mdk3 mon0 b –w –g –t –m –c 6MDK3 injects random beacon frames onto the targeted channels toward nearby wireless clients. This type of attack fills up the Wi-Fi network browser of the client with many spoofed wireless SSIDs, making it difficult to identify the legitimate networks. This could lead to a denial of service condition.

The option
-cspecifies the channel,-gspecifies the 802.11g standard,-wsets the encryption flag, and-tspecifies the encryption of the network as WPA.
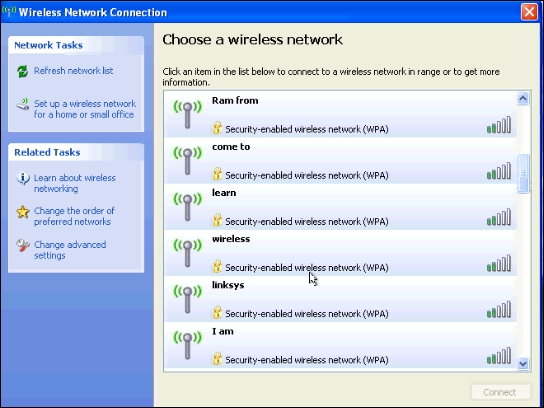
Go to any wireless client machine and browse for wireless networks. You will find random SSIDs flooding the area, generated by MDK3, as shown in the following screenshot:

Instead of generating random SSIDs, we can use a list of SSIDs from a file to be broadcasted with mdk3. The file containing the SSID list should be created before performing this attack. You can create a text file with the list of SSIDs and continue with the following instructions:
- Run the following command to perform fake beacon flood using selective SSIDs in a file; the
-foption specifies the target file with the list of SSIDs:# mdk3 mon0 b –f labfiles/denial-of-service/SSID-FAKE –w –g –t –m –c 6
As can be seen in the following screenshot, we can confirm that mdk3 is broadcasting the SSIDs of our choice:

Shown here is the file containing the sample SSIDs to be broadcasted by mdk3:

- Go to any wireless client machine and browse for wireless networks. You will find the same SSIDs in the sample file broadcasted by mdk3:
DoS attacks performed against wireless networks are available in many forms. Here, we explored a fake beacon flood attack on wireless networks. In the first part of the attack we used mdk3 to broadcast random SSIDs, and in second part of the attack we used selective SSIDs in a file to be broadcasted by MDK3. It is possible to perform these attacks on wireless networks even miles away from the target network. With Kali, you will find that there is a variety of tools to accomplish the goals of the penetration test.
In the next section, we perform a similar attack using the Metasploit framework.
