As mentioned before, DNS, or Domain Name Services, maps a name to an IP address. This process is very similar to the process described earlier with reference to DHCP. When the client supplies a DNS name when making a request for a resource, such as in the URL bar in a browser or when Telnetting or SSHing to a host via the command line, the operating system will first look to its local hosts file to see if a mapping is available there. In most cases, this fails to return a result and the operating system next asks the DNS server to provide the mapping. Where this is similar to DHCP is that when a DNS request is initiated, the client will listen for the first response it hears, with the appropriate sequence number used to test the validity of responses, and then will disregard any DNS replies that come after the initial one. This creates a race condition to return a response back to the client that the attacker wants instead of the legitimate response from the local DNS server. In most cases, since the DNS server is so close to the client, it is unlikely that an outside observer will have the ability to beat the DNS server's response and have the correct sequence number. However, if we are a man-in-the-middle and the client is sending all of their traffic through us, there is a very good chance that a spoofed DNS response will make it back to the client.
In the following example, you will see how we can use Ettercap's DNS spoofing plugin to redirect the victim to a website of your choosing when they attempt to access a legitimate resource. To increase the credibility of this attack, it is recommended that you use Kali's Social Engineering Toolkit, or S.E.T., to mirror a legitimate administrative interface or website that you would like to try to capture credentials from.
- If you have not yet installed S.E.T., run the following command:
#apt-get install set
- Once this process completes, you can run the S.E.T. to begin the process of cloning the administrative or login interface of the protected resource you'd like to capture credentials for.
#setoolkit - Choose option 1 for Social Engineering Attacks.
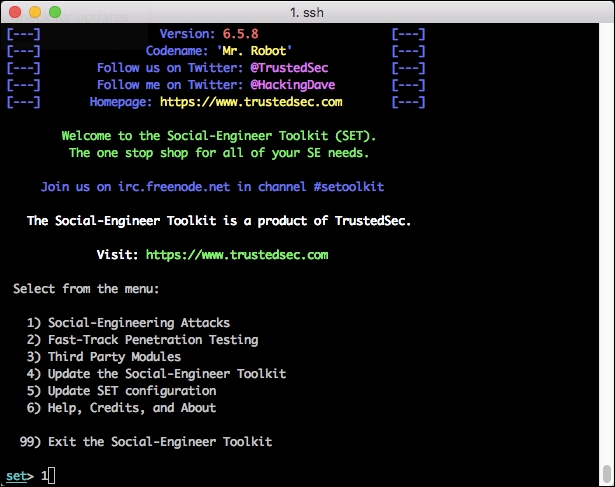
- Choose option 2: Website Attack Vectors.

- Choose option 3: Credential Harvester Attack Method.
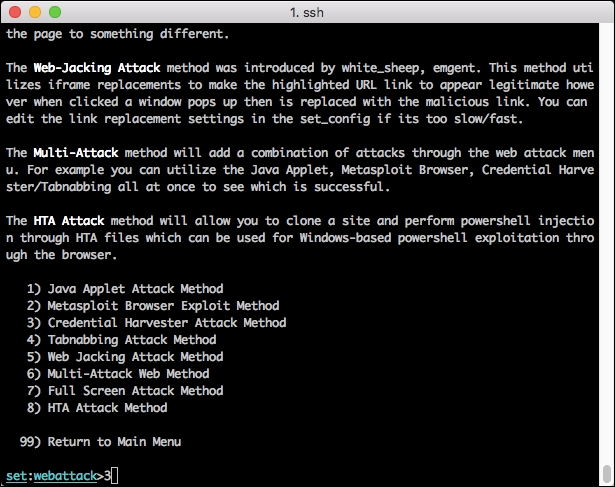
- Choose option 2: Site Cloner.
The tool is now looking for the IP address for the POST back in Harvester. For this value, you will use the IP address currently assigned to your Kali attack host. Running
ifconfigfrom a separate terminal window should provide you with this information.
- Next, you will enter the URL that you would like to clone to the local web server. For this example, we will use the administrative interface of the wireless router. This will hopefully allow us to capture the username and password from a targeted administrator who is attempting to access the administrative interface on the wireless router.

Now the website is cloned and we're ready to start intercepting the login attempts to our fake administrative page. Before this is possible, we need to redirect the administrator to our fake page without their knowledge. To do this, we will be using Ettercap's DNS spoofing feature. The administrator will attempt to access the wireless routers administrative interface using http://gateway.local. This is the address they would typically go to and would normally resolve to 192.168.0.1. Instead, we will spoof the DNS reply back to the victim and it will return 192.168.0.147, the address of our Kali instance. S.E.T. will then feed up the bogus administrative page and when the administrator tries to log in, the credentials will be captured.
