In addition to determining relationships, critical services, and determining targets for additional attacks, a wealth of information can be gathered from the packet capture itself. Many of the services used on IP WLANs are transmitted between the client and the destination unencrypted. Wireshark makes it easy to extract sensitive information from this communication.
Hypertext Transfer Protocol (HTTP) is an application-layer protocol used to browse the Internet and can also be used to send control traffic between nodes. Web browsers have become the primary way that a user interacts with applications, not only on the Internet but also on their local networks. HTTP is a clear text protocol. You can easily extract any data passed using HTTP from your packet capture. The information contained within this capture could reveal sensitive information like login credentials, office documents, downloaded files, and data submitted via forms.
HTTP communications use a request and response model. An HTTP client, usually a web browser such as Firefox, IE, or Chrome, will make requests to HTTP servers. Servers in turn send the response to the client's request along with status codes. Data sent via HTTP is not encrypted, and any third party sees this full exchange between the client and server if they are able to capture the traffic.
The following graphic shows the nature of the HTTP request/response model. A client requests or submits information to the web server, which in turn responds with the information requested or an acknowledgement that the information has been received.

In this model, we can expect potentially sensitive information to be sent from the client via HTTP POST commands, such as logging in to an application or submitting information into a form. The server replies can also deliver cookie information back to the client in the response, as we have seen, and can be used for session hijacking.
Let us consider a scenario: we have a sample packet capture of a web session in which a user's login credentials are sent via HTTP. From the earlier example, we can determine which devices are providing network services or could be part of the network infrastructure. Using this information, we can craft a display filter that is able to isolate the unencrypted HTTP traffic between any of the clients and this network equipment. In this section, we will use various display filters that help us to focus on HTTP traffic and extract the login credentials for this device.
Use the display filter http to focus on HTTP traffic. You can also drill down to specific packets using advance display filters.
- Type
httpin the Filter box to view all HTTP-specific data. You can extract the username and password sent in plain text over the web (excluding HTTPS).
- Type
http.request.method == "POST"in the Filter box to view all POST data sent from the client to a web server. It is common for HTTP POSTs to contain important information like usernames and passwords. - Open the stream content and examine it to see if it contains any sensitive information. To open stream content, right-click on the packet and select Follow TCP Stream.

The next figure shows that the capture file has got admin credentials of the wireless router. It means that the administrator of the wireless network was authenticating to the access point when the attacker captured the data and it was done over an unsecured protocol. In this scenario, we were able to see the username of admin passed unsecured; however, the password is base64 encoded. To know the password, we need to decode the value using a base64 decoder tool. base64 is a tool available in Kali Linux for just this purpose. We will use this tool to decode the value.
- Find the encoded password value in the POST data, put it in a text file and save the file with the name
base64decode.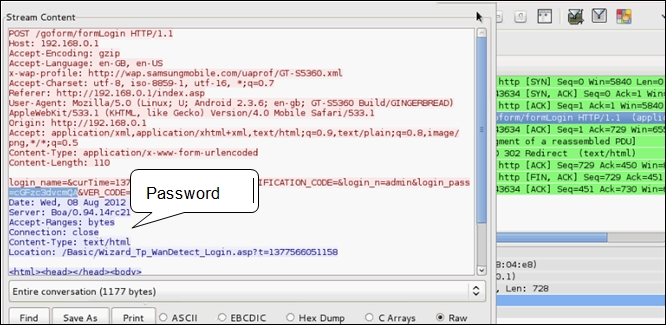
- Use any file editor available in Kali and paste the Base64 encoded string into the file, as shown:

- Now look at the file:

- Run the following command to decode the value:
#base64 –decode base64decode
The preceding output shows that the value is successfully decoded. It is password. Now we have the administrative credentials to the wireless access point. This clearly enables many new attack scenarios. We can target the clients by changing the configuration of the access point or perhaps testing for password reuse on other infrastructure devices or applications.
In addition to simple user credentials, we are also able to extract more complex elements from the HTTP traffic. All the documents downloaded or viewed from sites over HTTP can be extracted by using the HTTP objects option in Wireshark. Navigate to File | Export Objects | HTTP. You can select the objects from the HTTP objects pane and save them to the disk for future reference.

It can be seen from the preceding figure that many different file types are contained within the HTTP communications. In addition to the HTML files you would expect to see, you also have graphics files, the JavaScripts run by the web browsers, and any files that may have been downloaded during the capture session. All of these files can be downloaded to your attack workstation in a format that you can dig through by clicking on Save All. These files may contain normally protected information important to your client or other administrative information that can get you deeper into the network.
Simple Mail Transfer Protocol (SMTP) is used to send e-mails between clients and servers on the network. By default, SMTP communications occur on TCP port 25. Similar to HTTP described earlier, the client and server exchange commands and status codes during the communication in addition to the actual e-mail information the client sees in their mail reader. The following figure shows a typical SMTP exchange:

SMTP by default is not secure; any third party capable of sniffing the communication between the SMTP client and SMTP server can read the e-mail in clear text. Apply display filter SMTP to focus on e-mail traffic. At times, we come across sensitive e-mails in PCAP that help us to penetrate further. POP is used to retrieve e-mails from the server. Use display filter pop to focus on POP traffic.

As a more secure alternative to SMTP, SMTP over SSL is used. In SMTPS, a secure channel is established between the SMTP client and server before sending the e-mail out. By default, SMTP over SSL uses port 587. If SMTPS is utilized, even if the attacker captures the traffic between the two parties, they cannot read the e-mail without decrypting it. The key used to secure the channel is private and resides on the e-mail servers. Unless the key itself is compromised, there is no way to read the e-mail sent. Look for any sensitive e-mail exchanges in the pcap which can help us further penetrate the network.
