In this chapter, we will focus on enhancing your App with branding elements, workflows, event types, tags, macros, data models, and more. None of these items are a strict requirement. However, they will definitely increase your appeal to end users and customers alike. Choosing elements that are memorable will cement your App in the minds of your users and will make your App shine. We will start with working with your data, and then move on from there to presenting your App with custom logos, navigation, CSS overrides, and other stock modifications of the SimpleXML dashboards. We will end this chapter by seeing how to use Splunk acceleration technologies and methods to speed up searches in large datasets. As we move into working with actual data, we will be using example data and real data. Some of the data here was consumed from the https://meh.com/ website. They have an API, and the data was collected every five minutes using a scripted input. This data will be the basis for some examples and some dashboards that highlight various features. More important than the data is to grasp the concept. Grasp the concept; rule the software.
Workflows integrate with your data and are designed to help you move quickly through your data, or help you to integrate easily with other services. They can be used to drill down to another Splunk dashboard with prepopulated data in the request, perform an nslookup on an IP address in an event, open a ticket in an external ticket tracking system, or even launch an external search-all based on data found within the event. Workflows are displayed inline with the events you are working with. They don't have to apply for every single event. You can restrict a workflow to be revealed only when target events are listed, or a set of fields are listed. Workflows can be configured via the Web or configuration files.
Building a workflow in the web interface is straightforward. As part of our Splunk Developer's Guide (SDG) App, we will create a workflow that will interface with the http://mxtoolbox.com/ website to perform a reverse DNS lookup based on an IP address in the src_ip field found in some sample data. The first step is to navigate to the configuration area for workflows. This is found in the top-right corner of the screen. Navigate to Settings | Fields | Workflows, as seen in the following screenshot:
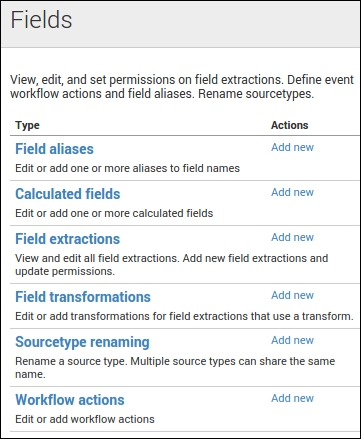
Click on Workflows to be taken to the correct manager. Now you have a form to fill in, as shown in the following screenshot. Don't we all just love paperwork? So, let's walk through it:
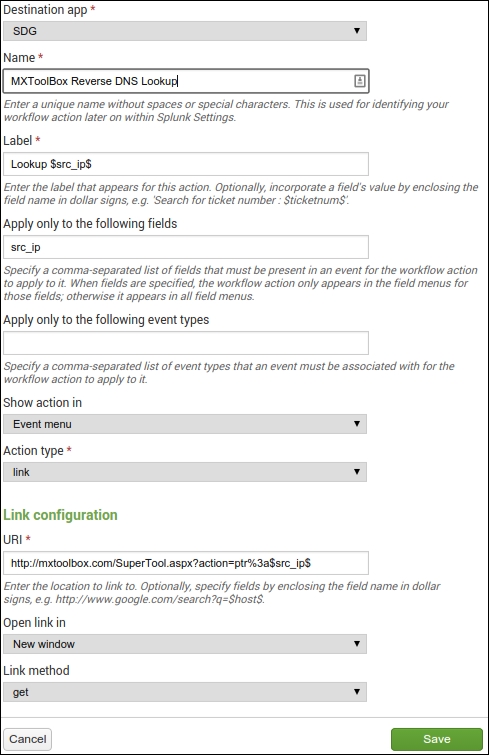
Give it a name, something descriptive. The name won't show up in the Web interface; that is the purpose of the Label field. In the Label field, you can place variables that are relevant to the data. So, for example, if you have an event with src_ip=75.75.75.75, then the Label will expand to Lookup 75.75.75.75. The next field details which fields are mandatory in the event in order for the workflow to be visible. Do the same for the event types textbox. The Show action in drop-down dictates where the clickable menu item will be shown. The Action type drop-down menu can have a link or a search option. The only time it won't be a link is when you want Splunk to perform a new search based on that data. Once those are set, you can configure the actual action. In this case, the URL we need is http://mxtoolbox.com/SuperTool.aspx?action=ptr%3a$src_ip$, which will automatically expand to http://mxtoolbox.com/SuperTool.aspx?action=ptr%3A75.75.75.75 based on the sample data. Finish it off with the New window option and a get configuration, and you are done! Note that after creating the workflow, the permissions are changed to be App only, where everyone can read but only admins can write, as shown in the following screenshot:
Setting up a workflow via a configuration file is just as easy. Let's make a Google search for a specific field. Navigate to $APP_HOME/default and edit the workflow_actions.conf file. Insert the following content into this file as a new stanza:
[Google Search] display_location = event_menu fields = site, topic label = Google $topic$, restrict to $site$ link.method = get link.target = blank link.uri = https://www.google.com/?q=site:$site$+$topic$ type = link
This will do exactly what the DNS lookup workflow does, except that it is a Google search restricted to the $site$ website, as found in your sample data. This workflow will apply only to events that have the site and topic fields.
