Under certain circumstances, it is not possible to directly connect to an OpenVPN server. This happens most often when firewalls are restricting UDP-based traffic. In such cases, OpenVPN can connect to an OpenVPN server via an intermediary host known as a proxy. OpenVPN supports two types of proxies, SOCKS and HTTP-based, both of which work only using TCP-based configurations. This recipe will outline how to access an OpenVPN server via a SOCKS proxy, whereas the next two recipes will show how to use an HTTP proxy, both with and without authentication.
SOCKS proxies can very easily be set up using almost any SSH client. On Linux and Mac OS X, it can be done using the ssh or slogin commands, whereas, on Windows, the free SSH client PuTTY can be used. In this recipe, we will use SSH on a Linux client to set up a public SOCKS proxy. A Windows OpenVPN client will connect using this proxy.
We will use the following network layout:

Set up the client and server certificates using the first recipe from Chapter 2, Client-server IP-only Networks. For this recipe, the server computer was running CentOS 6 Linux and OpenVPN 2.3.12. The client was running Windows 7 64 bit and OpenVPN 2.3.10. Keep the configuration file, example8-9-server.conf, from the Tuning TCP-based connections recipe from Chapter 8, Performance Tuning at hand. For the client, keep the configuration file, basic-tcp-client.ovpn, from Using an ifconfig-pool block recipe from the Chapter 2, Client-server IP-only Networks at hand.
- Start the server:
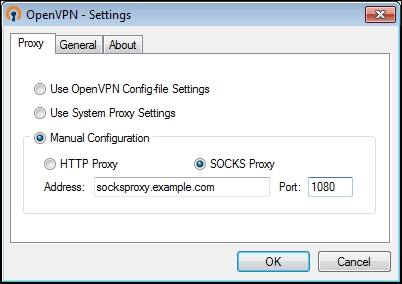
[root@server]# openvpn --config example8-9-server.conf - Right-click on the OpenVPN GUI tray icon and select Settings. Fill in the name or IP address of the SOCKS proxy host, and then click on OK:
- Set up a SOCKS proxy by setting up an SSH connection on the intermediary proxy host. The destination address for the SSH connection is a server which can reach the OpenVPN server:
[socks-proxy]$ ssh -g -D 1080 remote-host.example.com - Now start the OpenVPN client in another terminal window:


- The connection log will show that OpenVPN first connects to the remote proxy host (in this screenshot, the IP address
192.168.3.17was used). This connection is then forwarded to the OpenVPN server and the VPN is established:
A SOCKS proxy host acts as an intermediary between the (OpenVPN) client and the server. SOCKS proxies can also be configured in most web browsers and are often used to gain access through a hotel or corporate firewall. The client first connects to the SOCKS proxy host and then requests a new connection to the actual endpoint, which is the OpenVPN server in this case. If the connection is allowed by the SOCKS host, the connection is established and the VPN connection can be set up.
Before using a proxy host to set up a VPN connection, there are a few things to consider:
Proxy hosts tend to have a severe impact on the performance of a VPN setup. Both the bandwidth and the latency are usually affected when proxy hosts are used. This is mostly caused by having to connect to a separate host. There is little that can be done about this drop in performance.
SSH can be a very handy tool to set up a SOCKS proxy host, over which an OpenVPN connection can be set up. Apart from the drawback mentioned above, this introduces another penalty: both the SSH connection and the VPN connection will normally be encrypted. Thus, tunneling traffic over an encrypted VPN link, which in itself is tunneled over an encrypted SSH link, is double encrypted!
A question that you should ask yourself if you are tunneling VPN traffic over an SSH tunnel is: why? What type of traffic needs to be tunneled over a VPN link that cannot be tunneled via a SOCKS-over-SSH tunnel? Most modern web browsers and e-mail clients have built-in support for SOCKS hosts, eliminating the need for a full-blown VPN. File sharing protocols such as Windows file sharing (Common Internet File System (CIFS)) can also be tunneled over an SSH connection. In those cases, a VPN tunnel adds only extra complexity.
In OpenVPN 2.2 and higher, support is added to connect to a SOCKS proxy that required authentication. For OpenVPN 2.2, plain-text authentication support is added. Though the name "plain text" may suggest otherwise, the authentication mechanism is secure, as the connection to the SOCKS proxy host is encrypted first.
