When Linux is used as a desktop operating system, the network configuration is configured using the Linux NetworkManager in most of the cases. This package allows a non-root user to start and stop the network connections, connect and disconnect from wireless networks, and also to set up several types of VPN connections, including OpenVPN. In this recipe, we will show how to configure an OpenVPN connection using the GNOME variant of the NetworkManager.
Set up the client and server certificates using the first recipe from Chapter 2, Client-server IP-only Networks. For this recipe, the server computer was running CentOS 6 Linux and OpenVPN 2.3.11. The client was running Fedora 22 Linux and OpenVPN 2.3.11. This version of Linux comes with NetworkManager 1.0.8, including the NetworkManager-openvpn plugin. The NetworkManager-openvpn plugin is not installed by default and needs to be explicitly added to the system. Keep the configuration file, basic-udp-server.conf, in the Server-side routing recipe from Chapter 2, Client-server IP-only Networks, at hand.
- Start the NetworkManager configuration screen by right-clicking on the NetworkManager icon in the taskbar and selecting Edit Connections. A window will pop up.
- Choose the VPN tab to set up a new VPN connection:

- Click on the Add button to bring up the next screen:

- Select the OpenVPN as the VPN type and click on the Create... button. If the VPN connection type OpenVPN is not available, then the
NetworkManager-openvpnplugin is not installed. - Fill in the details of the VPN tab of the next window:

The Gateway is the hostname or IP address of the OpenVPN server. The Type of authentication is Certificates (TLS). Then, for the User Certificate, CA Certificate, and Private Key fields, browse to the directory where the client files
client1.crt,ca.crt, andclient1.keyare located, respectively. Fill in the Private Key Password fields, if required. Do not click on the Save button just yet, click on Advanced... instead. - In the next window, go to the Security tab:

- Select the encryption cipher and HMAC authentication protocol to use for the connection and then click on OK.
- Then, go to the TLS Authentication tab.

- Enable Verify peer (server) certificate usage signature, then select Use additional TLS authentication, and browse to the location of the
ta.keyfile. Choose 1 for the key direction. - Click on OK when done and then click on Apply to save the new VPN connection.
- Next, start the server:
[root@server]# openvpn --config basic-udp-server.conf - And finally, on the client, start the VPN connection by clicking on the NetworkManager icon, choosingVPN Connections and selecting Example 9-1:

You can verify whether the VPN connection is established correctly by pinging the VPN server IP.
The NetworkManager-openvpn plugin is a GUI for setting up an OpenVPN client configuration file. All the settings made are the equivalent of setting up the client configuration file as done in the Server-side routing recipe from Chapter 2, Client-server IP-only Networks.
The NetworkManager-openvpn plugin supports some advanced configuration settings:
The NetworkManager-openvpn plugin can also be used to set up VPN-specific routes. Open the main VPN configuration screen again and go to the IPv4 Settings tab. Click on the Routes... button on this screen:

A new window will appear:
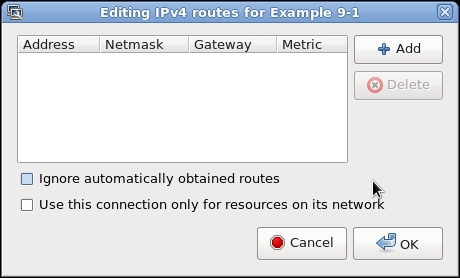
Routes pushed by the server can be overruled using the Ignore automatically obtained routes option. By default, the NetworkManager-openvpn plugin will enable redirect-gateway, even if it is not pushed by the server. This behavior can be overruled by checking the Use this connection only for resources on its network checkbox.
The NetworkManager-openvpn plugin also updates the /etc/resolv.conf file if the OpenVPN server pushes out DNS servers using the following directive:
push "dhcp-option DNS a.b.c.d"
