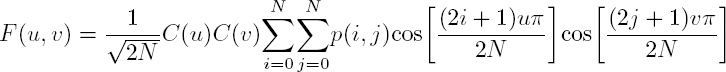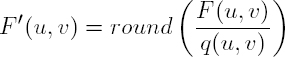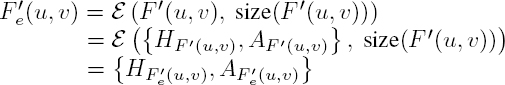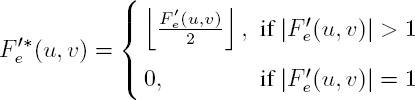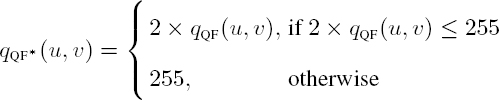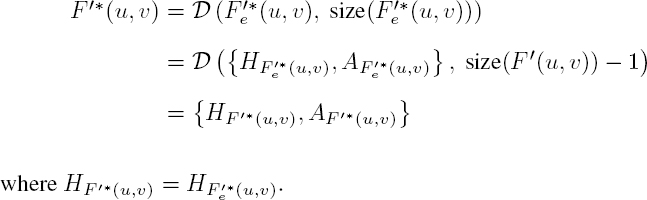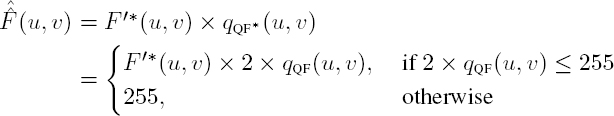4
Image Crypto-Compression
Vincent ITIER1, Pauline PUTEAUX2 and William PUECH2
1CRIStAL, University of Lille, CNRS, IMT Lille Douai, France
2LIRMM, Université de Montpellier, CNRS, France
The growing popularity of social networks and cloud computing has greatly increased the number of Joint Photographic Experts Group (JPEG)-compressed image exchanges. In this context, the security of the transmission channel and/or online storage can be sensitive to privacy leaks. Selective encryption is an effective tool for masking image content and protecting privacy while remaining consistent with the image encoding format. JPEG image encryption, also known as JPEG image crypto-compression, defines methods for encrypting a portion of the image content while still respecting the JPEG format. These methods provide a level of visual privacy while attempting to limit the file size expansion compared to classic JPEG compression. This type of method, which appeared in the early 2000s, relies on different approaches to implement the basic principles of cryptography. More recently, the question of security against decryption attacks has been the subject of increasing attention. Image processing in the crypto-compressed domain, that is, without decryption, is another new area of work.
4.1. Introduction
Over the past decade, increasing use of online storage (the cloud) and the sharing of data over networks has led to a growing demand for security and privacy with respect to personal data; the EU’s General Data Protection Regulation (GDPR)1 is a clear illustration of this increased concern. In practice, confidentiality, authentication and integrity are under constant threat when multimedia data are transmitted and/or stored, due to hacking, copying and attempts to make malicious use of information. It is not enough to simply secure access to the file: the content itself must be protected. This can be done by encryption or data hiding.
Image encryption is an effective method of ensuring the visual privacy of image content while preserving its format and size. Unauthorized individuals are prevented from accessing the original clear image content by the introduction of randomness. Encryption may be full, where the original data are encrypted in their entirety, or selective, where only a portion of the data are protected; the choice of approach depends on the application and on the desired level of security.
The rapid growth of network usage means that bandwidth requirements are constantly increasing. Limiting bandwidth usage is an important challenge for digital productivity and environmental reasons. JPEG compression has been the most widely used compression format for storing and sharing digital images for over 25 years, since its last ISO/IEC 10918-1 ITU-T Recommendation T.81. standard was published in 1993 (Wallace 1992). JPEG is still widely used, essentially as a result of its history, alongside the fact that this format is still preferred in many applications. The vast majority of display systems, including web browsers, are compatible with the different versions and extensions of JPEG (XR, XT, etc.). Furthermore, the Independent JPEG Group (IJG)2 produces a powerful, regularly-updated free library, libjpeg, which is widely used. The efficiency of JPEG is a result of lossy compression and the use of minimum redundancy codes. However, the quality degradation associated with JPEG compression limits its use in high-precision areas such as medical, satellite and military imagery. Hierarchical and lossless coding techniques are less commonly used, and will not be discussed here.
Format-compliant encryption methods are designed to combine efficient compression and encryption to produce encrypted content that is compatible with the format specifications. These methods are known as crypto-compression methods. The first JPEG crypto-compression methods were developed in the early 2000s, based on classic image encryption methods. However, direct application to the case of JPEG-compressed images is not trivial, as the JPEG format does not permit simple manipulation of the pixels in an image. The specificities of the format must be taken into account when applying cryptographic processes.
In section 4.2, we present an overview of the preliminary notions inherent in JPEG crypto-compression. The JPEG format, its properties and the notations used in this chapter are presented in section 4.2.1. Section 4.2.2 is devoted to the basics of cryptography, while a description of image encryption is given in section 4.3; we also present the problems involved in compressing encrypted images. Section 4.4 provides a survey of the state of the art in JPEG crypto-compression, designed as a solution to this problem. Section 4.5 illustrates the challenge of image processing in the crypto-compressed domain, notably with respect to one of the first proposed methods, involving the recompression of crypto-compressed images. Our conclusions are presented in section 4.6.
4.2. Preliminary notions
4.2.1. The JPEG image format
The compression and decompression steps used in the JPEG format, set out in the JPEG standard, are shown in Figure 4.1. Compression involves six main steps. First, the color space of the image is transformed from the RGB (red, green and codecolorBlue) space into another color space where luminance and chrominance are decorrelated, such as YCbCr. Monochrome planes may be downsampled (vertically, horizontally or in both directions, for chrominance and/or luminance). Each plane is then divided into non-overlapping blocks of size N × N (typically N = 8), and each block is projected in a frequency space using the DCT (discrete cosine transform). Taking a block B of size N × N from an image I, the DCT is:
with p(i, j), 0 ≤ i, j < N the pixels in block B, F (u, v), 0 ≤ u, v < N the frequency coefficients and ![]() and 1 otherwise.
and 1 otherwise.
In practice, DCT computation is optimized using intermediate results and can be carried out at faster or slower speeds with more or less approximation (see the fast, slow, float modes in libjpeg3). Each block of frequency coefficients is then quantized using a quantization table Q of size N × N containing the quantization coefficients q(u, v). The quantization operation involves dividing the coefficients F (u, v) of the block B by the elements in the quantization matrix Q:
where round(·) represents the rounding operator to the nearest integer.
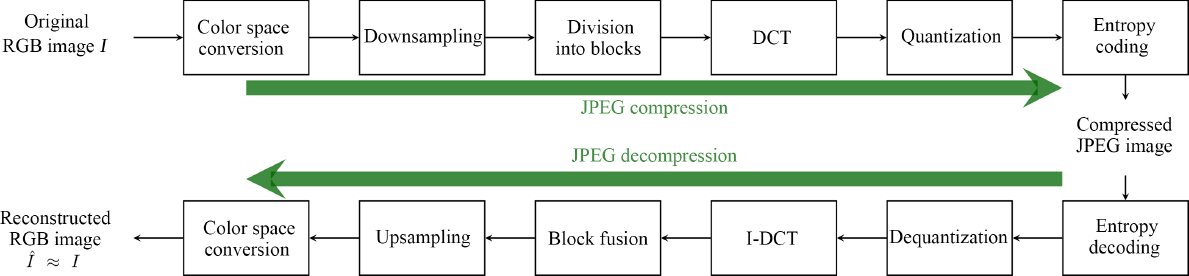
Figure 4.1. JPEG compression and decompression steps
This step encodes the quantized DCT coefficients F′(u, v) onto 8-bit integers. Finally, the blocks are compressed, either sequentially or incrementally, using one of two specified entropy encodings, a Huffman encoding or an arithmetic encoding. The bitstream produced by the codec is usually encapsulated in EXIF (Exchangeable Image File Format) or JFIF (ISO/IEC 10918-5:2013 2013) (JPEG File Interchange Format), which establishes the form of the header and the binary markers delimiting the parameter fields.
Decompression is carried out by reversing the operations performed during compression. Since subsampling and quantization operations are not reversible, these are the two main causes of information loss during JPEG compression. Inverse quantization consists of inverting equation [4.2], multiplying the quantized DCT coefficients F′(u, v) by their corresponding frequency quantizers q(u, v):
The inverse cosine transform, noted I-DCT, makes it possible to return to the spatial domain from the frequency domain.
The downsampling and quantization operations draw on studies of the capabilities of the human visual system (HVS). Channels are often downsampled due to the low sensitivity of the HVS to chrominance. Additionally, the DCT decomposes the signal into N × N frequencies, from lowest to highest: the HVS is more sensitive to low frequencies, which provide an overview of image content, and less sensitive to high frequencies, describing details, which can thus be quantized to a greater extent. Based on this principle, the IJG proposes standard quantization tables QQF, calculated from a reference table QQREF and an integer quality factor noted QF | QF ∈ [1, 100], where QREF = 50. For QF = 100%, all of the coefficients in the Q100 table are set at 1. In practice, some applications, such as Adobe Photoshop or GIMP, use their own tables. Since the tables are included in the JPEG header, they do not need to be transmitted to the decoder in advance.
Figure 4.2 shows images obtained after JPEG compression with different QF, applied to an image from the UCID database (Schaefer and Stich 2003) (Figure 4.2(a)). Note that with a high QF, the compression rate τ is already significant, but the quality of the original image is still high (Figure 4.2(b), τ = 12.96 and PSNR = 41.46 dB and Figure 4.2(c), τ = 23.35 and PSNR = 38.78 dB). The main problem in cases of JPEG compression with a low QF concerns degradations in texture, the appearance of granularity and block artifacts (Chan 1992), as shown in Figure 4.2(d), with QF = 25 % (τ = 71.18 and PSNR = 32.82 dB).
In this chapter, we shall consider the most usual choice for JPEG options, which consists of encoding a 24-bit RGB image in a sequentially ordered bitstream, derived from a Huffman encoding. The block size is 8 × 8 pixels (N = 8). The luminance/chrominance color space (YCbCr: Y is the luminance component; Cb and Cr are the chrominance components) is used, with a standard downsampling of the chrominance channels (4:2:0) or (4:2:2): the size of the blocks is divided by two or four, respectively, by averaging the value of the neighboring pixels. The quantized frequency coefficients of each block are coded in a zigzag order on an MCU (minimum coded unit). The coefficients are then ordered by increasing frequency; since the high frequencies are quantized more strongly, the blocks tend to end in zeros, allowing for more efficient coding. The block encoding step is illustrated using an example in Figure 4.3. More generally, the coding of the DC coefficient F′(0, 0), proportional to the mean value, corresponds to a pair (HF′(0,0), AF′(0,0)). The amplitude parameter AF′(0,0) encodes the prediction error, while the header parameter HF′(0,0) indicates the number of bits needed to encode it. The AC coefficients F′(u, v), such that (u, v) ≠ (0, 0), are encoded by a pair (HF′(u,v), AF′(u,v)). AF′(u,v) encodes the amplitude of the coefficient, and the header HF′(u,v) is composed of the range of zeros – the run-length – computed earlier, alongside a parameter stating the number of bits required to encode the amplitude. When the last non-zero coefficient of the block has been encoded, an EOB (End Of Block) indicator symbol is added to the MCU. The MCU sequence is placed after the header. In the remainder of this chapter, for ease of reading, the code associated with a coefficient will be noted as the coefficient.

Figure 4.2. Illustration of JPEG compression: a) uncompressed image (590.8 Ko) from the UCID database (Schaefer and Stich 2003), b) image compressed using JPEG at QF = 90% (45.6 Ko), c) image compressed using JPEG at QF = 75% (25.3 Ko), d) image compressed using JPEG at QF = 25% (8.3 Ko)
4.2.2. Introduction to cryptography
Cryptography is one of the disciplines of cryptology – etymologically the science of secrecy – which relates to protecting messages, using one or more keys. Unlike steganography or data hiding, which consists of embedding a message within other content, cryptography makes a message unintelligible to anyone other than the intended recipient.
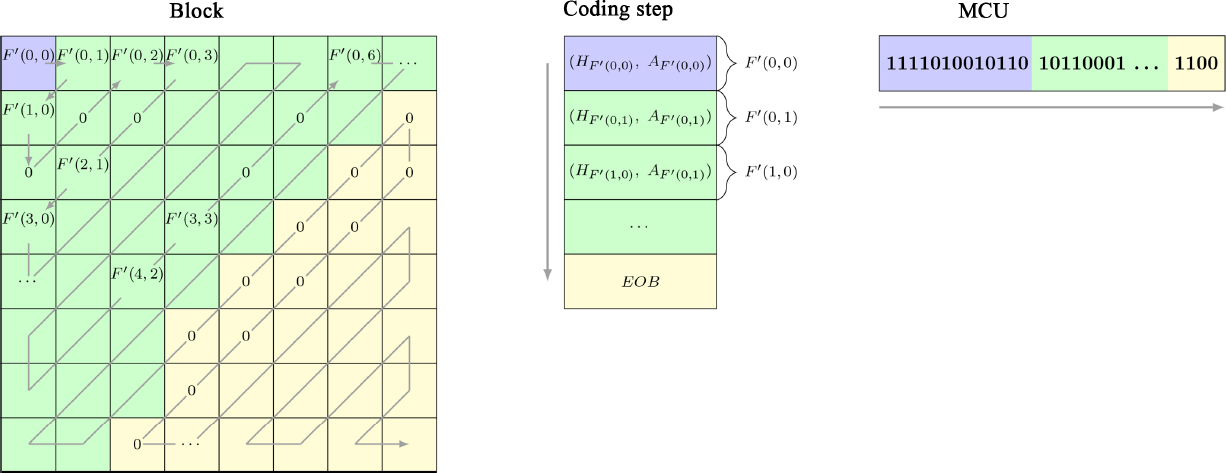
Figure 4.3. Illustration of block code construction on an MCU (minimum coded unit)
COMMENT ON FIGURE 4.3.– The block is zigzagged for run-length encoding, then the coefficients are coded using Huffman tables. The DC coefficient is shown in purple, and the AC coefficients quantized in green. Starting from the position where all quantized AC coefficients are zero in the zigzag order, they are coded by an EOB signal.
Although cryptography has been used since ancient times, it only truly took off at the end of the 20th century, notably with the development of computer science. The principles of modern cryptography are laid out by Kerckhoffs in the article La cryptographie militaire in the Journal des sciences militaires (Journal of Military Sciences) published in 1883 (Kerckhoffs 1883):
- – security relies on the secrecy of the key, not the method;
- – it should be materially, if not mathematically, impossible to decode an encrypted message without the key;
- – it should not be possible to determine the key using the clear and encrypted texts.
Thus, it is assumed that all parameters of the cryptosystem other than the key must be public and universally known. Shannon, in 1949, stated the need to “assume the enemy knows the system” (Shannon 1949). The principles established by Kerckhoffs and Shannon are now considered fundamental in the implementation of any cryptosystem. This approach contrasts with that of security by obscurity, which relies on the non-disclosure of information about the structure, operation and implementation of an algorithm to be protected (e.g. by code obfuscation or remote code execution).
Two broad classes of cryptographic algorithms can be defined: symmetric cryptography – also known as secret key cryptography – and asymmetric cryptography – also known as public key cryptography.
In symmetric cryptography, the same key, called the secret key, is used to encrypt and decrypt a message. Thus, the security of the cryptosystem relies on the secure exchange of the key; only the sender and the recipient of the message must know the secret key. In addition, the key must be large enough to protect against brute-force attacks, in which all possible combinations are tested in order to find the correct key to decrypt the message. There are two categories of symmetric cryptosystems: stream ciphers and block ciphers. Stream ciphers treat the clear message as a stream of data (bits or bytes). During encryption, each character is encrypted independently, meaning that the algorithm is very fast to execute. Stream encryption can be performed in real time, without needing to wait for all of the data for encryption to be received. The stream cipher principle, also known as a disposable mask or Vernam cipher, was first defined in Vernam (1926). A secret key is used as the initialization seed for a cryptographically secure pseudo-random number generator (PRNG) to generate a pseudo-random binary sequence, called the encryption stream, of the same size as the message to be encrypted. Messages are then encrypted by performing an exclusive-or between the data to be encrypted and the generated pseudo-random binary sequence. In block cipher algorithms, on the other hand, clear data are split into blocks of fixed size (often 64, 128 or 256 bits); blocks are then encrypted one by one. There are several different block cipher methods (Dworkin 2001), such as ECB (electronic code book), CBC (cipher block chaining), CFB (cipher feedback), OFB (output feedback) or CTR (counter-based cipher). The best-known block encryption algorithms include the Data Encryption Standard (DES), published in 1976 (Davis 1978), the Triple DES (3DES) (Karn et al. 1995), derived from the DES, and the Advanced Encryption Standard (AES) (Daemen and Rijmen 1999), which is currently the benchmark standard for block encryption. Note that the DES algorithm uses a single 56-bit key, while 3DES uses two or three keys of the same size. AES encryption traditionally uses a key of between 128 and 192 bits, and recent cases have extended to 256 bits (Singh 2013).
In asymmetric cryptography, two keys are used: a public key and a private key. These keys are generated by the user who wishes to receive the messages. They are mathematically related insofar as the decryption operation is the inverse of the encryption operation. For this purpose, one-way functions, which are easy to evaluate but difficult to reverse, are used. The public key is generated by computing the image of the private key via the chosen one-way function. In other words, even if the public key is known, it is very difficult to retrieve the associated private key (which is impossible to compute in polynomial time). Thus, the public key can be transmitted openly, but the private key must remain secret and is never transmitted. Asymmetric encryption algorithms can be used for two purposes:
- – to encrypt the message before sending to guarantee its confidentiality: the sender uses the recipient’s public key to encrypt the message and the recipient uses their private key to decrypt it;
- – to digitally sign a message to guarantee its authenticity: the sender uses their own private key to encrypt the message, and the recipient uses the sender’s public key to decrypt it, thus authenticating the sender.
The first asymmetric protocol was described by Merkle in a paper written in 1975 (Merkle 1978); however, due to a 3-year publication delay, the concept of secure cryptographic key exchange over a public channel is generally attributed to Diffie and Hellman (1976). Using their method, two people who do not know each other can jointly establish a shared secret key over a non-secure channel. This key can then be used to encrypt subsequent communications between these two people. The first asymmetric encryption method, named RSA, was developed by Rivest et al. (1978). This approach is based on the problem of factorizing large numbers as a product of two prime numbers. Other methods used other difficult problems, such as the discrete logarithm (El Gamal 1985) or quadratic residuality (Paillier 1999). Note that the size of the keys used in asymmetric cryptosystems varies from 1,024 to 4,096 bits.
There are advantages and disadvantages to both symmetric and asymmetric algorithms. One notable difference is that symmetric cryptography requires key exchange, which is not necessary in asymmetric cryptography. Asymmetric algorithms are more complicated to implement, slower and require greater hardware resources than symmetric algorithms. PGP software aims to combine the advantages of these two classes of cryptographic algorithms by offering a hybrid system. A secret one-time key is generated in order to send messages securely, encrypting the message using a symmetric algorithm. The key itself is then encrypted using an asymmetric encryption algorithm such as RSA. The sender then transmits both the encrypted message and key to the recipient. The time needed to execute the asymmetric algorithm is considerably reduced as only the key is encrypted in this manner.
The latest developments in cryptology research relate to quantum and post-quantum cryptography. Quantum cryptography draws on the properties of quantum physics – notably the Heisenberg principle – and of information theory in order to develop cryptographic algorithms, resulting in proven or conjecturally unattainable levels of security. For example, in quantum key distribution, a key can be transmitted between two remote parties on demand with demonstrable security. If the information is intercepted and read by a third party, errors will be introduced so that the attack is detected. The aim of post-quantum cryptography is to create cryptographic methods that are resistant to an attacker using a quantum computer. Cryptographic algorithms that rely on the discrete logarithm problem or on the product of two integers problem for security are no longer guaranteed to be secure when faced with quantum computing power. Nevertheless, since quantum technology is not yet operational, this theoretical research has very few practical applications at present.
4.3. Image encryption
The purpose of image encryption is to ensure visual privacy of the clear content of an image. Encryption is said to be “full” when the original content of the image is protected in its entirety: in this case, no information about the clear image can be extracted from the encrypted image. In contrast, “selective” encryption conceals only part of the data. Finally, in “partial” encryption, only a specific area of the image is encrypted, and pixels outside of this area are clearly visible. The difference between these three types of encryption is illustrated in Figure 4.4.

Figure 4.4. Illustration of the difference between three types of encryption: a) original image, b) full encryption, c) selective encryption and d) partial encryption
Image encryption methods must verify two properties:
- – format conformity: the encrypted image must have the same format as the original image;
- – size preservation: the encrypted and original images must be the same size.
The first property implies that data must be structured in the same way before and after encryption. This means that classic cryptographic methods cannot be directly applied to images without being adapted to take account of the specificities of image formats. Furthermore, the format conformity property implies that encrypted data can be viewed using the same image editing software as the original data.
In terms of the second property, note that a limited increase in data size after encryption can be acceptable in certain applications.
Moreover, following Shannon (1949), an encryption method must result in confusion and diffusion. In the case of images, the confusion principle implies that the relationship between the encryption key and the encrypted image must be as complex as possible. The diffusion property indicates that the statistical redundancy between pixels in a clear image must be dissipated in the statistics of the encrypted image. In other words, the correlation between pixels in the clear image should not be reflected in the encrypted image. Pixel permutation and substitution operations are used to introduce confusion and increase diffusion.
While the classical cryptographic algorithms described in section 4.2.2 have been adapted for image formats, specific algorithms have also been developed. Note that these algorithms are generally based on a symmetric encryption method; asymmetric encryption is less widespread due to the large volume of data to process. Asymmetric encryption is much more costly in terms of computing time and results in an increase in the size of the original data.
In the following section, we shall describe naive approaches to image encryption, based on the use of a PRNG and on the substitution or permutation principle (section 4.3.1). We will then explain how chaos theory has been applied to image encryption (section 4.3.2). Finally, we will briefly touch on encryption-then-compression approaches, in which images are encrypted before being compressed (section 4.3.3).
4.3.1. Naive methods
Image encryption approaches based on substitution and/or permutation operations involve the use of cryptographically secure PRNGs, as described in section 4.2.2. As input, these generators rely on a secret key, K, the type of elements and the length of the sequence to be generated.
The objective of shuffle encryption methods, which are efficient and easy to implement, is to transform a clear image into an unintelligible one by permuting the positions of pixels. Take an image ![]() of m × n pixels. I is shuffle-encrypted as follows. A PRNG is used with a secret key K to define the new pixel positions of I. A sequence
of m × n pixels. I is shuffle-encrypted as follows. A PRNG is used with a secret key K to define the new pixel positions of I. A sequence ![]() of m × n pseudo-random positions s(i) such that 0 ≤ s(i) < m × n and ∀ i, ∀ j, 0 ≤ j < m × n, i ≠ j ⇒ s(i) ≠ s(j) (in order to avoid collisions) is generated. The encrypted image
of m × n pseudo-random positions s(i) such that 0 ≤ s(i) < m × n and ∀ i, ∀ j, 0 ≤ j < m × n, i ≠ j ⇒ s(i) ≠ s(j) (in order to avoid collisions) is generated. The encrypted image ![]() is obtained by copying the pixel values of I at pseudo-random positions given by the sequence S:
is obtained by copying the pixel values of I at pseudo-random positions given by the sequence S:
Certain authors have suggested random permutations of rows and columns in an image (Usman et al. 2007; Premaratne and Premaratne 2012) or pixel blocks (Wright et al. 2015), rather than switching the locations of all of the pixels.
Substitution-based encryption methods have also been developed. These use an exclusive-or operation between the generated pseudo-random sequence and the content of a clear image. The operation can be performed in two different ways. The image can be encrypted pixel by pixel, bit by bit (e.g. from the least significant bit to the most significant bit), or bit-plane by bit-plane (e.g. from the least significant plane to the most significant plane). Consider an image ![]() of m × n pixels. The pixel-by-pixel encryption of I is performed as follows. A pseudo-random binary sequence
of m × n pixels. The pixel-by-pixel encryption of I is performed as follows. A pseudo-random binary sequence ![]() of m × n bytes s(i), is generated using a secret key K and a PRNG. The encrypted image
of m × n bytes s(i), is generated using a secret key K and a PRNG. The encrypted image ![]() is then obtained by performing an exclusive-or between each pixel p(i) in the image I and the associated byte s(i) in the pseudo-random sequence S:
is then obtained by performing an exclusive-or between each pixel p(i) in the image I and the associated byte s(i) in the pseudo-random sequence S:
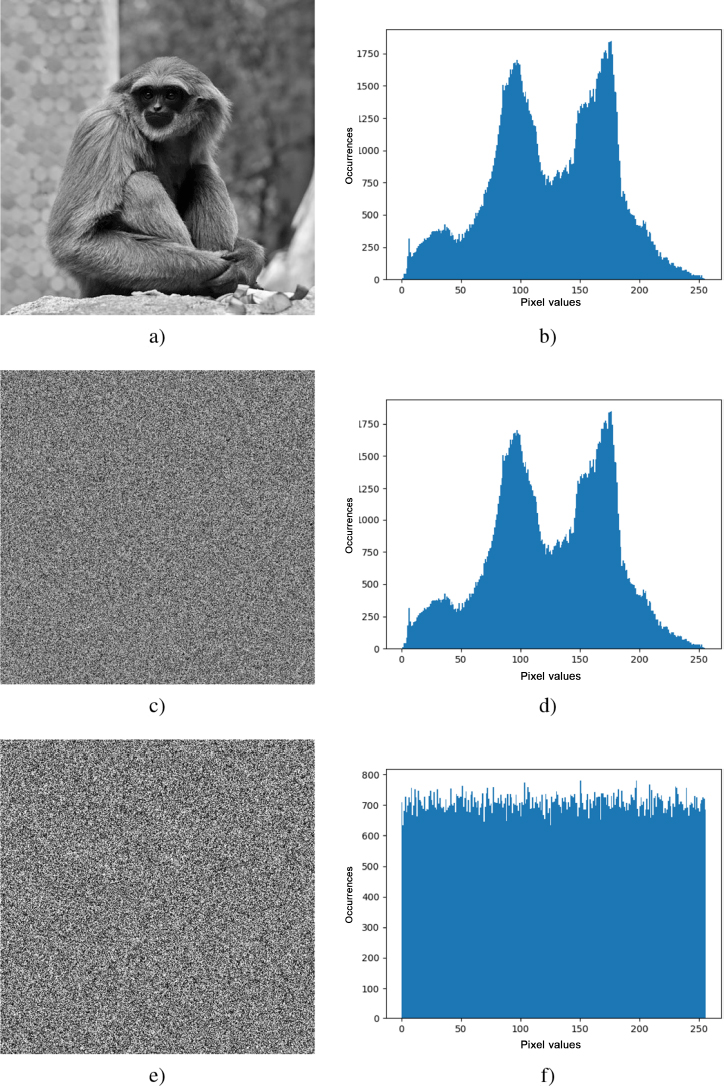
Figure 4.5. Illustration of image encryption by shuffling and substitution. a) original image, b) histogram associated with (a), c) image (a) encrypted by pixel shuffling, d) histogram associated with (c), e) image (a) encrypted by substitution, pixel by pixel, and f) histogram associated with (e)
Figure 4.5 shows a clear image, encrypted versions using shuffling and substitution, and the associated histograms. We see from Figure 4.5(b) that the distribution of pixels in the clear image includes a certain number of modes relating to the content. Furthermore, as we see from Figure 4.5(d), the histograms of pixels in the encrypted and clear images are identical. While this encryption method is easy to apply, certain statistical properties of the original image are preserved. In the case of pixel substitution (Figure 4.5(f)), on the other hand, the pixel distribution is almost uniform. While neighboring pixels have similar values and are strongly correlated in the clear domain, these relationships are removed by this form of encryption. Thus, analysis of an image encrypted using substitution methods – unlike shuffling methods – does not give any information about the original content of the clear image.
4.3.2. Chaos-based methods
The rapid development of chaos theory and associated applications has resulted in the creation of a variety of encryption techniques. The first method using chaos was published by Arnold and Avez in 1967 and is known as Arnold’s cat map (Arnold and Avez 1967). Later, Scharinger and Pichler applied the baker’s map to image encryption (Scharinger and Pichler 1996). These two well-known methods are illustrated in Figure 4.6.
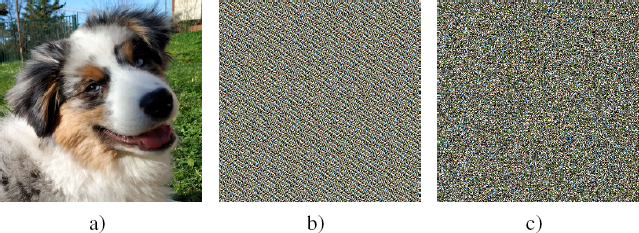
Figure 4.6. Illustration of two image encryption methods using chaos theory: a) original image, b) Arnold’s cat map (Arnold and Avez 1967) and c) baker’s map (Scharinger and Pichler 1996)
Fridrich extended the discretized version of this map into three dimensions (3D) and combined it with a scattering mechanism (Fridrich 1997, 1998). In most cases, later encryption algorithms incorporate both permutation and substitution mechanisms and use a combination of several chaotic maps. Chaos-based cryptosystems can be divided into two distinct classes. In the first class, a pixel is considered to be the smallest element (Chen et al. 2004; Mao et al. 2004; Guan et al. 2005), while in the second class, binary operations are applied to the bits making up a pixel (Xiang et al. 2007; Zhu et al. 2011). In Chen et al. (2004), the authors applied Arnold’s cat map in three dimensions, while in Mao et al. (2004), baker’s map is used in three dimensions to swap pixel positions during the substitution phase. Guan et al. (2005) applied Arnold’s cat map to shuffle the pixel positions of an image in the spatial domain, before using the chaotic system defined in Chen and Ueta (1999) to change the pixel values. To reduce the execution time, Xiang et al. (2007) defined a chaotic selective encryption method, encrypting only the four most significant bits of each pixel and leaving the four least significant bits clear. In 2011, Zhu et al. (2011) proposed a cryptosystem in which Arnold’s cat map is used to perform permutations at the binary level, allowing both the location and values of pixels in the image to be changed. A logistic map is then used to introduce diffusion.
4.3.3. Encryption-then-compression
Encryption-then-compression methods, as their name suggests, work by encrypting then compressing an image. The challenge with this type of method is that compression must be carried out in the encrypted domain, without access to the secret key or the original, clear image. At first glance, the compression of encrypted data appears impossible since the redundancies between pixels are removed by the encryption operation. However, in 2004, Johnson et al. (2004) showed that stream-encrypted data can be compressed without altering its security level. Following on from these theoretical results, practical algorithms for lossless compression of encrypted binary images have been developed. Kumar and Makur (2008) applied this method to prediction errors computed in the encrypted domain, improving the compression rate. Lazzeretti and Barni (2008) have presented several methods for lossless compression of grayscale and color encrypted images. The authors divided images into binary planes before exploiting intra- and inter-plane correlation. Other encryption-then-compression methods rely on shuffling blocks in an image (Kurihara et al. 2015, 2017). The original image is divided into blocks of 16 × 16 pixels, which are then pseudo-randomly swapped using a first secret key. A second secret key is used to perform rotations and/or inversions on the blocks. A transformation is also applied to the pixels of each block: the highest order bit of some pixels is modified using a third secret key. Finally, in the case of color images, the three components are permutated using a fourth secret key. The resulting encrypted image is robust to conventional JPEG compression.
Despite considerable efforts made in recent years, encryption-then-compression systems still perform poorly in terms of compression performance, compared to lossy or lossless image and video encoders using clear data input. Moreover, many of these approaches are vulnerable to puzzle attacks (Cho et al. 2010). Given that JPEG is the most widely used compressed image format, many methods rely on joint encryption and JPEG compression together. The challenges and operation of these image crypto-compression approaches will be described in section 4.4.
4.4. Different classes of crypto-compression for images
In this section, we shall present a state of the art of the broad categories of crypto-compression methods that are compatible with JPEG format, with examples selected on the basis of performance and diversity. These methods may be extended to other formats.
Encryption and compression steps were carried out separately in early crypto-compression methods. The main problem with this strategy is that encryption significantly alters the statistical characteristics of the image: efficient substitution-based encryption methods tend to result in a distribution of the encrypted image which is close to a uniform distribution of random variables. Furthermore, shuffling-based encryption methods remove spatial coherences. This means that compression efficiency is greatly reduced if encryption is performed first. In this context, interest in JPEG-compressed image encryption has increased in recent years. The main aim is to encrypt images in such a way that the encrypted data can always be represented in a meaningful format (i.e. preserving format conformity). In the JPEG format, not all binary data need to be encrypted: encryption methods can thus focus on image-specific data rather than format. When decompressing without the encryption key, the image in pixel form is selectively encrypted since not all of the information is encrypted, unlike full pixel encryption methods (used in a non-compressed format). A visual security level (transparent, sufficient or confidential) must be defined in accordance with the application. Keyless decryption must, by definition, be very complex. In methods of this new type, compression and JPEG encryption are either performed together or after compression. There are three main categories of methods: sign bit encryption, DCT coefficient encryption and methods based on shuffling DCT coefficients or JPEG blocks. Shi and Bhargava designed one of the first crypto-compression approaches to directly encrypt the binary JPEG stream (Shi and Bhargava 1998). The authors suggest encrypting the sign bit of the AC and DC coefficients (the sign of the difference in the case of DC coefficients). A binary pseudo-random sequence is generated based on a secret key and encryption is performed by an exclusive-or operation on this sequence with the sequence of all sign bits. This method preserves the JPEG structure of the image, which can be viewed using standard image editing software. Furthermore, the compression ratio is hardly (if at all) changed, since the number of bits remains the same. Nevertheless, Said (2005) was able to demonstrate weaknesses in this method. Given that the image respects the JPEG format, the majority of the bitstream remains unchanged even if the clear image seems to be encrypted. It is therefore easy to guess the original value of the encrypted bits. Recent methods have attempted to increase security and visual privacy, focusing on increasing the confusion and diffusion properties using substitution and/or shuffling-based crypto-compression techniques.
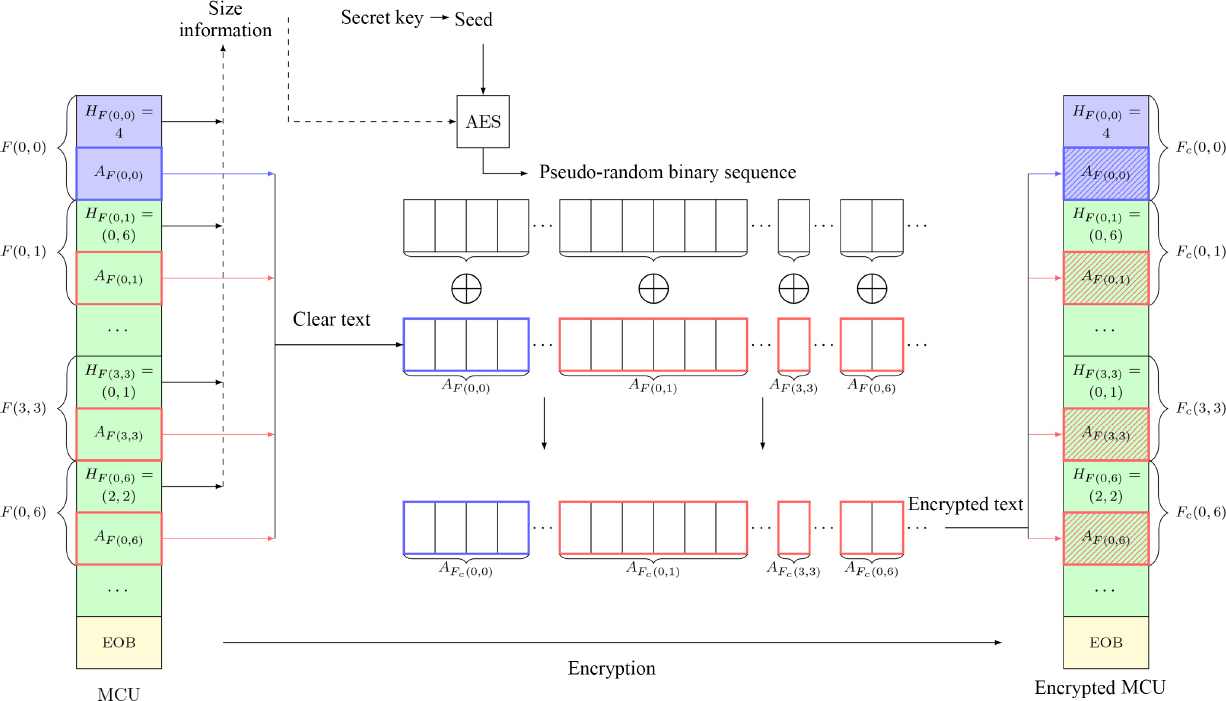
Figure 4.7. Illustration of the substitution-based crypto-compression approach designed by Puech and Rodrigues (2005). ⊕ represents the exclusive-or operator
4.4.1. Substitution-based crypto-compression
Methods in the substitution-based crypto-compression class operate by replacing clear values with encrypted values. In general, values are encrypted using the exclusive-or operator between the clear values and a pseudo-random sequence generated using a secret key. This operation maintains format compatibility and limits file size inflation. Van Droogenbroeck and Benedett (2002) suggest encrypting AC coefficients after the DCT transformation, but not the DC coefficients, since they contain important visible information and are predictable. Building on this idea, Puech and Rodrigues have proposed a selective encryption method for JPEG images that encrypts both DC and AC coefficients (Puech and Rodrigues 2005).
In this method, shown in Figure 4.7, all the DC coefficient codes (optional) and the non-AC coefficients are concatenated to form a 128-bit bitstream. This bitstream is then encrypted using the AES algorithm (Daemen and Rijmen 1999) in OFB mode. Finally, the JPEG image is constructed using the encrypted coefficient values. Since the size of the coefficients, alongside the zero-range encoding, remains unchanged, the Huffman encoding is also unchanged and the resulting JPEG file has the same size as if it had been compressed without encryption, using the same parameters. When decoded without decryption, the image is not easily understandable by the HVS. If the DC coefficients are encrypted, then the image is incomprehensible. If the AC coefficients alone are encrypted, however, then the low-resolution image will be accessible. Rodrigues et al. (2006) extended this concept to protect individual anonymity, rather than the entire image: in this case, encryption is performed on regions of interest, such as human skin, detected automatically. These regions are detected using the clear DC coefficients of the Cb and Cr color components. Selective encryption is applied to blocks of the luminance component Y during the entropy coding phase. As the HVS has relatively low sensitivity to chrominance information, it is usually highly quantized and downsampled. The impact of encrypting the corresponding channel coefficients is only minor. The quantized AC coefficients of the region of interest are encrypted using the CFB mode of the AES algorithm. This method respects the JPEG format, and the resulting crypto-compressed JPEG image is the same size as that obtained using the standard JPEG algorithm. Furthermore, partial encryption is sufficient to hide sensitive information, such as text (Pinto et al. 2013). The advantage of these encryption methods is that the compression ratio is the same as that of a conventional JPEG compression using the same parameters. However, information is not shuffled during transmission, meaning that the resulting crypto-compressed images are more vulnerable to brute force attacks.
4.4.2. Shuffle-based crypto-compression
Just like shuffle encryption, shuffle crypto-compression consists of rearranging the elements of an image using a PRNG. In the case of JPEG compression, the most obvious elements to shuffle are the JPEG blocks. This introduces distortion into the image at the decoding stage due to the predictive coding of the DC coefficients, but does not change the size of the image, since the blocks (except the DC coefficients) are independently coded.
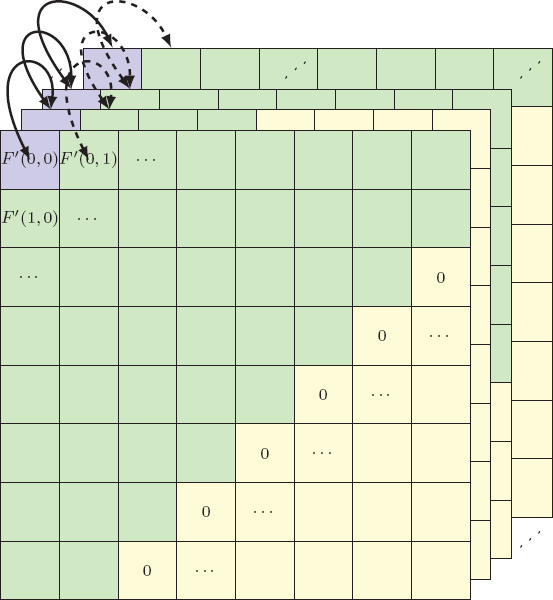
Figure 4.8. Illustration of the full inter-block shuffle method (FIBS) for frequency coefficients, proposed by Li and Yuan (2007)
However, the blocks remain clear, and security is not guaranteed. Kurihara et al. (2017) designed an encryption-then-compression approach in which blocks are permuted in the spatial domain. This approach is vulnerable to puzzle solver attacks, as demonstrated by Chuman et al. (2017). The method has been further developed to use other elements of the compressed JPEG image, which permit efficient and secure information transmission while limiting the inflation of the JPEG file size. In natural images, the distribution of coefficients of the same frequency follows a Laplacian distribution (Lam and Goodman 2000). Shuffling non-zero coefficients of the same frequencies seems to give good security while preserving the overall file size. The run-length coding is identical, but the value of the coefficient can be changed, resulting in a change in the Huffman code. However, Li and Yuan (2007) have shown that this approach can be attacked to generate a sketch of the image, and visual privacy is therefore not guaranteed. The authors suggested a solution to this problem in the form of the FIBS (Full Inter-Block Shuffle) method, which consists of shuffling coefficients of the same frequency between blocks, as shown in Figure 4.8. The decoded image is then unintelligible (if the DC coefficients are encrypted); however, since the coefficients are mixed, the entropy coding step is less efficient than with standard JPEG compression. This is due to the fact that the zero-range coding is less efficient, since successive zeros in the blocks are scattered. This may lead to a change in the position of the end-of-block code, so that the MCUs require more bits. Furthermore, the header of the code for a coefficient may be modified according to the size of the zero range preceding it. Note that non-textured areas are affected by the encryption due to the shuffling of zeros. Shuffling methods do not permit the introduction of confusion: the distribution of DCT coefficients always follows the same frequency distribution after naive shuffling (Reininger and Gibson 1983).
Figure 4.9 shows the results obtained after applying three different crypto-compression methods with QF = 90% to the UCID database image (Schaefer and Stich 2003) shown in Figure 4.2(a). The crypto-compressed images in the first line were obtained by encrypting the AC coefficients of the three YCbCr components alone. The images in the second line were obtained by encrypting both AC and DC coefficients. Figures 4.9(a) and (d) are obtained by applying Puech and Rodrigues’ substitution method (Puech and Rodrigues 2005). The crypto-compressed images in Figures 4.9(b) and (e) are obtained by shuffling. Note that, for both methods, when only the AC coefficients are encrypted, the crypto-compressed images are the same size as the JPEG image with QF = 90% (Figure 4.2(b)). Finally, the size inflation observed in Li and Yuan’s FIBS method (Li and Yuan 2007) results from the loss of efficiency of zero-range coding (59.5 KB in the case of Figure 4.9(c) and 63.3 KB in the case of Figure 4.9(f)).
4.4.3. Hybrid crypto-compression
Certain authors have turned to hybrid approaches in order to benefit from the advantages of both confusion and diffusion properties. The encryption capacity of the methods presented earlier is only low if the quality factor is low, since there are few non-zero coefficients. The advantage of hybrid approaches is that an accumulation of different steps with a low impact on file size results in a low overall size increase, but with higher visual privacy and security. Minemura et al. (2012) took this approach in shuffling JPEG blocks. Within each block, the AC coefficients with a null zero range are shuffled then the sign bits are encrypted using a pseudo-random sequence and the XOR operation to increase perturbations. These three steps do not increase file size. DC coefficients are then grouped by close values using frequency-domain edge detection for processing; this may result in a small increase in the number of bits. In concrete terms, if only the AC coefficients are shuffled then the edges of the image will still be perceptible. Taking a similar approach, Unterweger and Uhl (2012) described a three-step crypto-compression method. The first step is to shuffle the order of the code coefficients (of the form ![]() in an MCU using the AES algorithm (Daemen and Rijmen 1999) in OFB mode, as shown in Figure 4.10. Non-zero coefficients and the zero coefficients coded together are shuffled: this operation does not increase the size of the code, but changes the position of the frequency coefficients. The bits of the coefficient values
in an MCU using the AES algorithm (Daemen and Rijmen 1999) in OFB mode, as shown in Figure 4.10. Non-zero coefficients and the zero coefficients coded together are shuffled: this operation does not increase the size of the code, but changes the position of the frequency coefficients. The bits of the coefficient values ![]() are then inverted as a function of the output (binary, 0 or 1) of the AES-based PRNG used in the previous step. Finally, a pseudo-random approach is used to modify the order of MCUs sharing the same Huffman tables, which gives additional security to an extent dependent on the number of Huffman tables. This method is secure in the sense that a brute force attack on the AES key will be more effective than trying all possible combinations.
are then inverted as a function of the output (binary, 0 or 1) of the AES-based PRNG used in the previous step. Finally, a pseudo-random approach is used to modify the order of MCUs sharing the same Huffman tables, which gives additional security to an extent dependent on the number of Huffman tables. This method is secure in the sense that a brute force attack on the AES key will be more effective than trying all possible combinations.
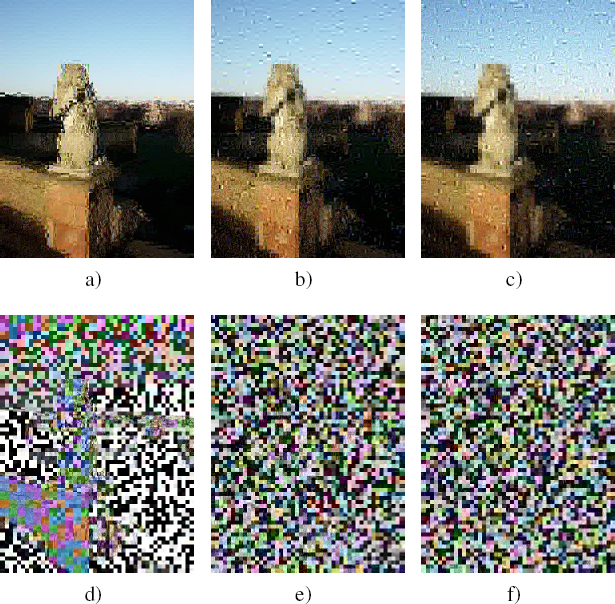
Figure 4.9. Crypto-compressed images with QF = 90%, with encrypted AC coefficients (first line) and encrypted DC and AC coefficients (second line) for the three YCbCr components of the image shown in Figure 4.2(a)
COMMENT ON FIGURE 4.9.– (a) and (d) obtained using Puech and Rodrigues’ method (Puech and Rodrigues 2005) (45.6 KB and 48.9 KB); (b) and (e) obtained by shuffling non-zero coefficients (45.9 KB and 49.5 KB); (c) and (f) obtained using Li and Yuan’s FIBS method (Li and Yuan 2007) (59.5 KB and 63.3 KB).
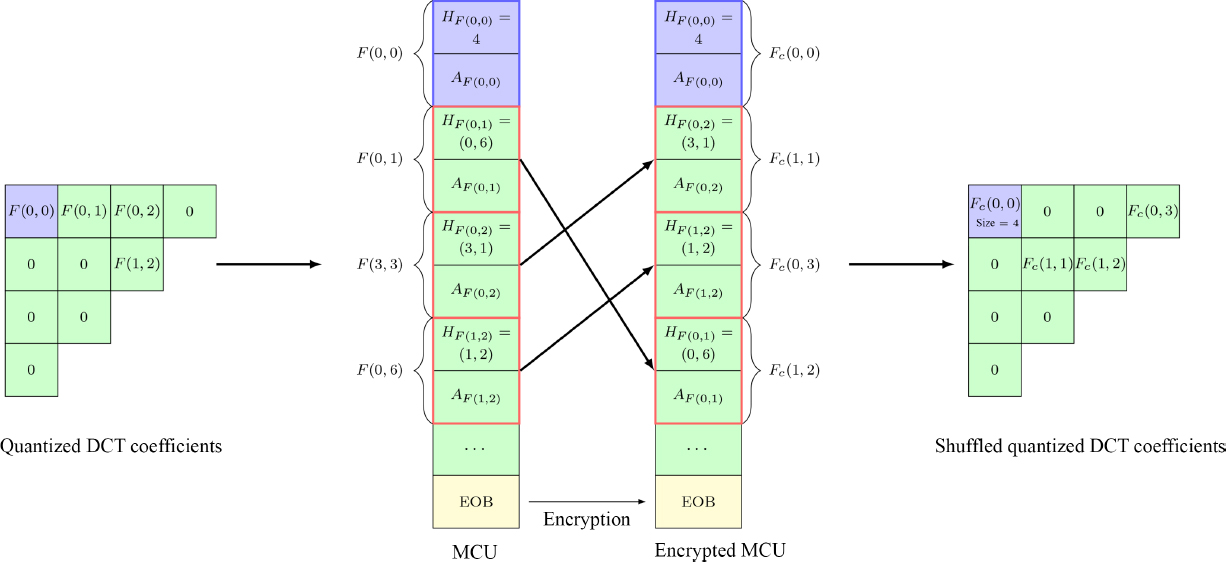
Figure 4.10. Illustration of Unterweger and Uhl’s intrablock coefficient code shuffling method (Unterweger and Uhl 2012)
The methods presented here can be used to encrypt JPEG images in an efficient and effective manner, both in terms of visual privacy and file size limitation. Security analysis of crypto-compression methods, as found in Unterweger and Uhl (2012), is currently lacking, but current trends point toward this analysis becoming increasingly systematic. Although most methods are based on the JPEG format, and thus on the discrete cosine transform (DCT), other schemes exist and have been popularized in recent years. A variety of JPEG2000 compatible image crypto-compression methods are presented in Engel et al. (2009). Other methods work by encrypting the sign of wavelet coefficients (Dufaux et al. 2004), on permutations (Norcen and Uhl 2004; Lian et al. 2004) or on randomized arithmetic coding (Grangetto et al. 2006). Shahid et al. (2011) adapted these methods for video by designing a selective encryption technique for the H.264/AVC video codec for the CAVLC and CABAC standards. Encryption is performed during the entropy coding phase using the AES algorithm in CFB mode. To conserve file size and preserve the H.264/AVC format, encryption is only applied to CAVLC keywords and CABAC bitstreams. An in-depth study of HEVC crypto-compression methods has recently been published (Hamidouche et al. 2017). Crypto-compression methods for video files will be discussed in greater depth in Chapter 5.
The advantage of crypto-compression methods is that crypto-compressed images can be handled in the same way as conventional JPEG images in terms of sharing, storage or viewing. However, some tasks can no longer be carried out using these files, such as computer visualization algorithms, quality enhancement or the application of a second compression; these operations all require decryption. In this context, homomorphic encryption methods have been designed to allow operations to be performed directly in the encrypted domain (see Chapter 6).
4.5. Recompressing crypto-compressed JPEG images
Let us suppose that an individual – let us call her Alice – wishes to use a JPEG crypto-compression system to prevent malicious use of her images and to use as little space as possible. Alice wants to store her images in the Cloud in order to back up her data and access her files from anywhere. JPEG crypto-compression is a suitable solution in this case, as it offers a degree of confidentiality with respect to attacks on the platform, or to data analysis by the web host. Most cloud services impose limitations on image submission (in terms of either size or format) in order to optimize storage and bandwidth usage. If Alice crypto-compresses her images with a quality factor QF, the network administrator may want to recompress them. Recompression is usually carried out by applying a new JPEG compression with a specific quantization table. However, while simple recompression of a crypto-compressed image is possible, Alice will no longer be able to decrypt her images using her secret key: the content of the original image is lost. Crypto-compression methods are not robust to simple recompression. Alice could, theoretically, transit her secret key to the host to permit crypto-compression with a lower quality factor, but this solution is not secure. Ideally, a method is needed to permit recompression of crypto-compressed JPEG images without using the secret key. In this case, the images transferred by Alice would be recompressed directly on the cloud server, with a new quality factor QF* such that QF*< QF.
In this section, we present a method for recompressing crypto-compressed JPEG images without knowing the secret key used during encryption (Itier et al. 2020). We shall begin by describing the different steps of the proposed new crypto-compression method, which is based on the study of Puech et al. (2013). As we shall see, JPEG compression and encryption are performed jointly during Huffman coding. We then describe an efficient method to recompress crypto-compressed JPEG images directly in the encrypted domain. Note that this approach preserves the security level of the crypto-compression method. The general scheme of this method for recompressing crypto-compressed JPEG images is shown in Figure 4.11.
4.5.1. A crypto-compression approach robust to recompression
The crypto-compression method used here draws on the work of Puech et al. (2013). Our aim is to adapt this approach in order to make it robust to the application of one or more recompression operations following the initial crypto-compression. If an image is crypto-compressed using the approach described in Puech et al. (2013) then recompressed without adaptation, then desynchronization with the pseudo-random binary sequence used for decryption will occur during the decoding phase, and it will be impossible to reconstruct the content of the original image. To solve this problem, we propose a reordering of the JPEG coefficients during the encryption phase. Figure 4.11 shows a general overview of the crypto-compression method is presented.
The standard JPEG compression steps are applied to the original image I up to quantization of the frequency coefficients. Encryption is then carried out during the Huffman coding phase. At the very least, the luminance component Y must be encrypted to preserve the confidentiality of the original image. We recall that the two chrominance components, Cb and Cr, can also be encrypted; however, as we see from Figure 4.12, this is not crucial, since the HVS is not particularly sensitive to them. All coefficients in each MCU which are non-zero F′(u, v) after quantization are encrypted. The non-zero AC F′(u, v) coefficients are then reordered according to their size in descending order. The recompression step described in section 4.5.2 corresponds to dividing all non-zero AC coefficients F′(u, v) by two. Note that reordering of the coefficients makes it possible to resynchronize the PRNG, even for a coefficient F′(u, v) with a coded amplitude of one bit, reduced to zero after recompression. Without the reordering step, it would be impossible to differentiate between these coefficients and those that were already zero before the recompression, resulting in desynchronization with the pseudo-random binary sequence.
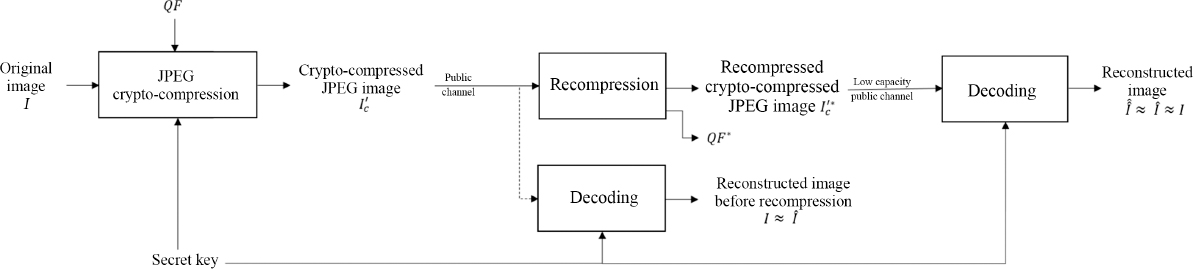
Figure 4.11. General scheme of the recompression method for crypto-compressed JPEG images
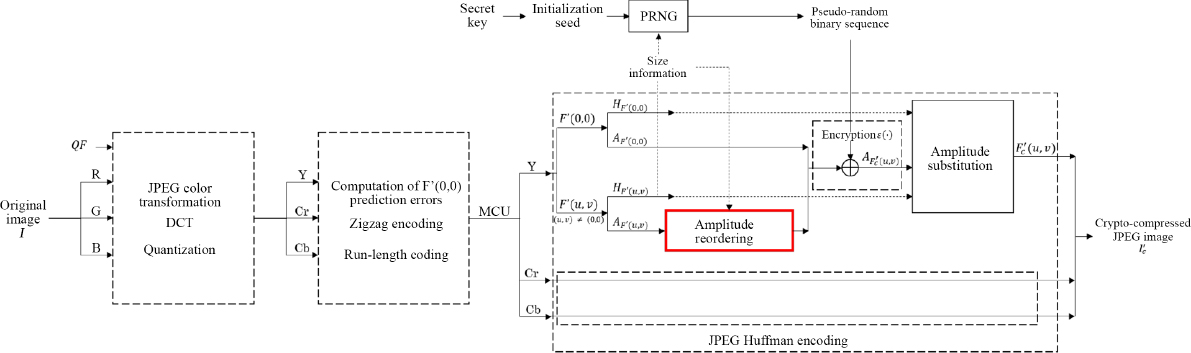
Figure 4.12. Crypto-compression method, designed to be robust to recompression
Once the non-zero AC coefficients F′(u, v) have been selected and re-ordered, a secret key is used to generate a different seed for each MCU. This seed is used to initialize a PRNG to obtain a pseudo-random binary sequence. The size of this sequence is computed by adding the sizes of each non-zero AC coefficient F ′(u, v), giving a number of bits which is sufficient to encrypt all of their amplitudes. Thus, the value of an encrypted coefficient ![]() is:
is:
Where ![]() .
.
As we see from Figure 4.12, the encryption function ![]() consists of applying an exclusive-or operation between the amplitude value of a clear coefficient F′(u, v) and the corresponding part of the pseudo-random binary sequence, according to its size and position in the MCU. The amplitude values
consists of applying an exclusive-or operation between the amplitude value of a clear coefficient F′(u, v) and the corresponding part of the pseudo-random binary sequence, according to its size and position in the MCU. The amplitude values ![]() of the original binary stream are replaced with the encrypted values
of the original binary stream are replaced with the encrypted values ![]() to obtain the encrypted MCU. In this sequence, the encrypted equivalent of a coefficient F′(u, v), coded by a pair
to obtain the encrypted MCU. In this sequence, the encrypted equivalent of a coefficient F′(u, v), coded by a pair ![]() , is
, is ![]() coded by a pair
coded by a pair ![]() of which the header remains unchanged. Note that the encrypted coefficient is coded on the same number of bits as the original version, since only an exclusive-or is applied. Finally, the crypto-compressed JPEG image
of which the header remains unchanged. Note that the encrypted coefficient is coded on the same number of bits as the original version, since only an exclusive-or is applied. Finally, the crypto-compressed JPEG image ![]() is obtained.
is obtained.
4.5.2. Recompression of a crypto-compressed image
As we see from Figure 4.13, recompression is applied directly to the encrypted JPEG bitstream for each component. Following crypto-compression, each MCU is made up of one or more coefficients, encoded by ![]() pairs. The first step in recompression is to remove the least significant bit from the amplitude parameter of each coefficient
pairs. The first step in recompression is to remove the least significant bit from the amplitude parameter of each coefficient ![]() The recompressed coefficients
The recompressed coefficients ![]() are calculated as follows:
are calculated as follows:
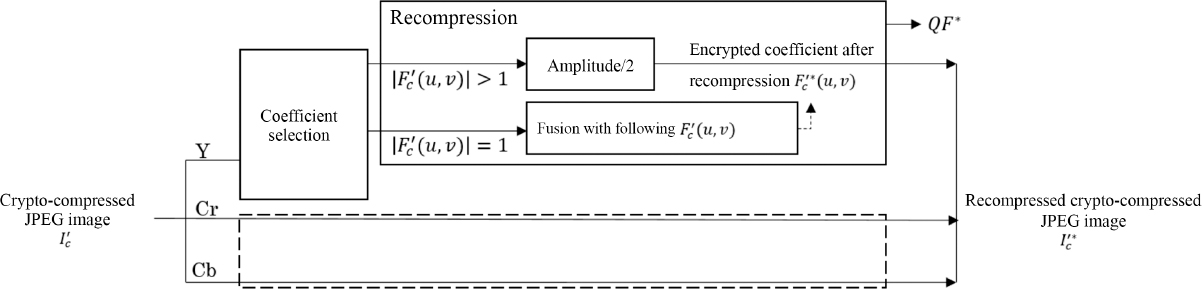
Figure 4.13. Recompression of a crypto-compressed image
Removing the last bit of each non-zero coefficient causes a one-bit reduction in the size of their binary code. The size parameter in the header should therefore be adjusted accordingly. Moreover, if the amplitude of a coefficient ![]() is encoded on one bit before recompression, its recompressed version
is encoded on one bit before recompression, its recompressed version ![]() will be a null coefficient. Thus, this coefficient must be encoded in the zero range of the next coefficient
will be a null coefficient. Thus, this coefficient must be encoded in the zero range of the next coefficient ![]() which must be non-zero by construction. The value of the zero range of its header
which must be non-zero by construction. The value of the zero range of its header ![]() is adjusted by taking account of the number of preceding coefficients, which are equal to zero. The new value of the zero range is equal to the initial value of the zero range, plus that of the previous coefficient, plus one:
is adjusted by taking account of the number of preceding coefficients, which are equal to zero. The new value of the zero range is equal to the initial value of the zero range, plus that of the previous coefficient, plus one:
Finally, the recompressed encrypted coefficients in each MCU are coded by the pair ![]() . The coefficients qQF* (u, v) in the updated quantization table QQF* are:
. The coefficients qQF* (u, v) in the updated quantization table QQF* are:
The main advantage of the proposed method is that it is easy to locate the deleted bits after recompression. This means that synchronization with the pseudo-random binary sequence remains possible, enabling error-free decryption. The fact that non-zero coefficients are reordered by amplitude means that those that become zero after recompression are located at the end of the MCU.
The format preservation property of our method means that the recompressed crypto-compressed image ![]() remains in JPEG format. The image may be decrypted using the secret key used for encryption, but only if the image is known to have been recompressed. A flag may be added to the comment section of the JFIF file to indicate the number of recompressions that have been performed.
remains in JPEG format. The image may be decrypted using the secret key used for encryption, but only if the image is known to have been recompressed. A flag may be added to the comment section of the JFIF file to indicate the number of recompressions that have been performed.
4.5.3. Decoding a recompressed version of a crypto-compressed JPEG image
As we see from Figure 4.14, the decoding phase consists of four main steps: decrypting the JPEG binary flow encrypted during Huffman decoding, inverse quantization, the I-DCT transform and inversion of the color space change (from YCbCr back to RGB).
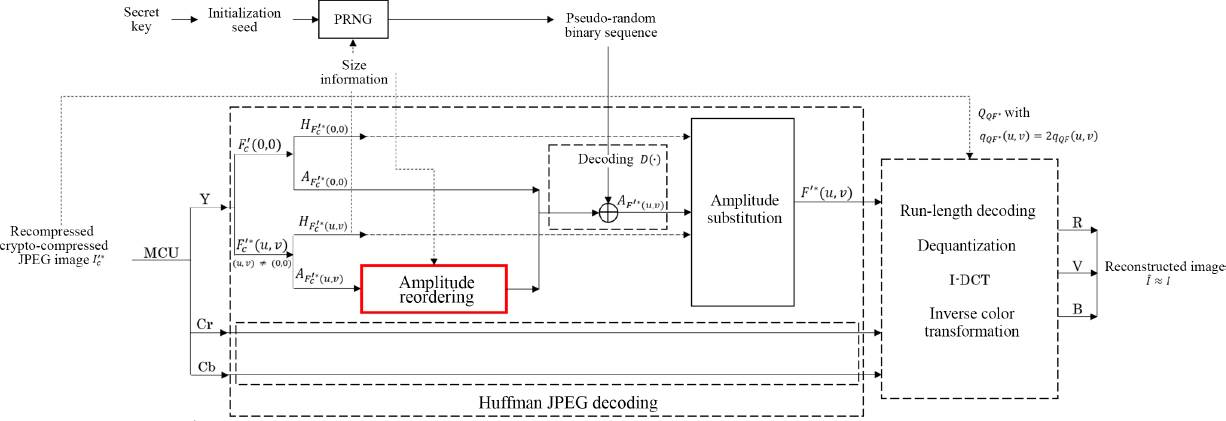
Figure 4.14. Decoding a recompressed version of a crypto-compressed JPEG image
The decryption operation can be carried out by anyone with access to the secret key used during encryption. By referring to the comment part of the JFIF file, it is possible to know whether the encrypted image has been recompressed. The first step of decryption is to use the secret key as an initialization seed for the PRNG in order to generate the pseudo-random binary sequence required for decryption. The decryption process thus takes account of the fact that the encrypted binary sequence must be shifted in order to decrypt each coefficient; remember that these coefficients were divided by two during the recompression phase. As the last bit of each code is removed during recompression, the last bit of each part of the pseudo-random binary sequence associated with a coefficient must also be ignored. The decryption function ![]() is similar to the encryption function. It requires two input parameters: a recompressed encrypted coefficient
is similar to the encryption function. It requires two input parameters: a recompressed encrypted coefficient ![]() and its size, which is specified in the header. The associated clear coefficient is obtained by applying an exclusive-or between the magnitude of the encrypted coefficient and the associated part in the pseudorandom binary sequence:
and its size, which is specified in the header. The associated clear coefficient is obtained by applying an exclusive-or between the magnitude of the encrypted coefficient and the associated part in the pseudorandom binary sequence:
Note that applying the proposed recompression method to the clear JPEG image I′, we obtain exactly the same coefficients ![]() as after decrypting the coefficients
as after decrypting the coefficients ![]() . The encryption/decryption method is commutative with the recompression method, since the exclusive-or operation is commutative with the floor function:
. The encryption/decryption method is commutative with the recompression method, since the exclusive-or operation is commutative with the floor function:
After decryption, Huffman decoding is applied and the quantized DCT coefficients are reconstructed. The inverse quantization operation is then performed in order to obtain the dequantized values ![]() As we have seen, the decrypted image corresponds to the recompressed compressed image
As we have seen, the decrypted image corresponds to the recompressed compressed image ![]() . Its quantization table QQF∗ is derived from the quantization table QQF of the compressed image I′, of which the coefficients have been multiplied by two:
. Its quantization table QQF∗ is derived from the quantization table QQF of the compressed image I′, of which the coefficients have been multiplied by two:
Finally, the decompressed RGB image ![]() image is obtained by applying the I-DCT transformation to convert the frequency coefficients into pixels, then the inverse color space change to convert the YCbCr image into RGB. As in the case of a standard JPEG compression, depending on the quality factor QF, the content of the reconstructed image
image is obtained by applying the I-DCT transformation to convert the frequency coefficients into pixels, then the inverse color space change to convert the YCbCr image into RGB. As in the case of a standard JPEG compression, depending on the quality factor QF, the content of the reconstructed image ![]() will be more or less faithful to the original image I.
will be more or less faithful to the original image I.
4.5.4. Illustration of the method
Figure 4.15 was obtained by applying the crypto-compressed JPEG image recompression method to the Peppers image (321 × 481 pixels) using a quality factor of QF = 75% for the first JPEG compression. The first step in the method is to crypto-compress the original image. In this example, the AC and DC coefficients of the three components (Y, Cb and Cr) are encrypted to preserve the visual privacy of the original image content. We see that it is difficult to distinguish details, and that the value of the color PSNR is very low (11.74 dB). After the decoding phase, we see that the decrypted crypto-compressed JPEG image is very similar to the original image (PSNR = 38.59 dB). Note that this image is identical to the one obtained after a classic non-encrypted JPEG compression with QF = 75%. The obtained crypto-compressed image is then recompressed directly in the encrypted domain (i.e. without decrypting the crypto-compressed image). By analyzing the quantization table, we can estimate the quality factor after recompression as EQF∗ = 50% (Itier et al. 2020). Finally, the recompressed crypto-compressed JPEG image can be perfectly decrypted with the secret key used for crypto-compression. The PSNR value is high (35.21 dB), indicating strong similarity between the resulting image and the original Peppers image.
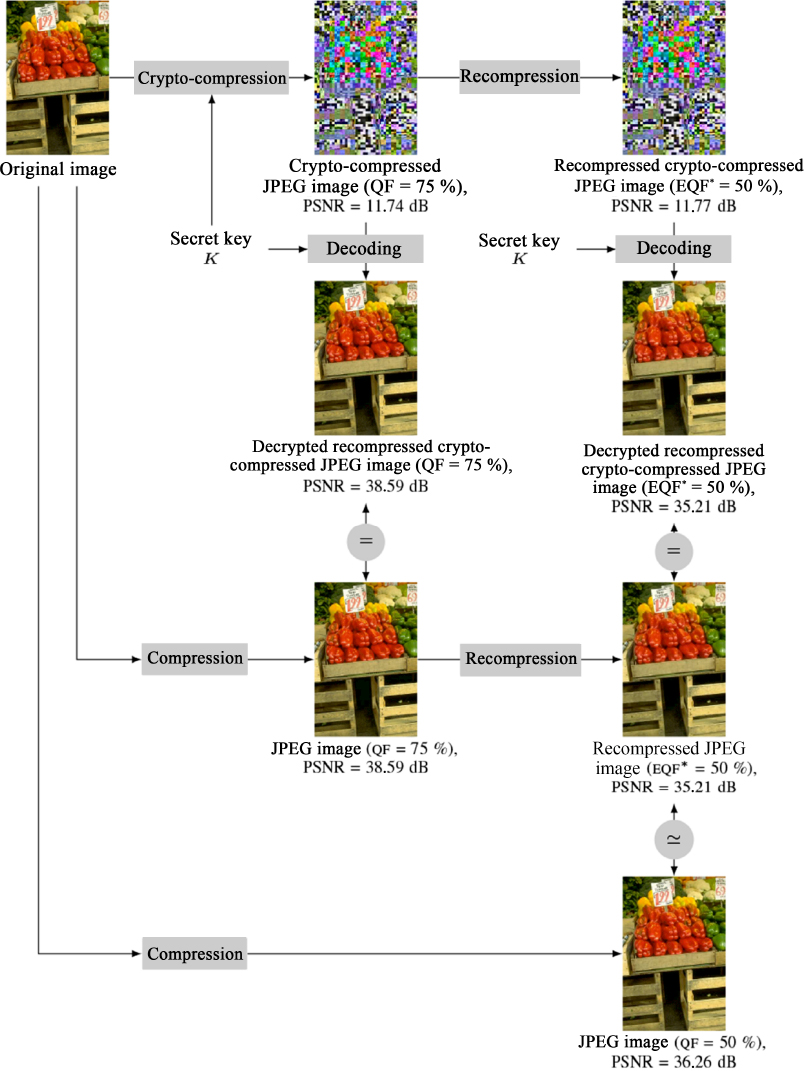
Figure 4.15. Application of our method: crypto-compression of the Peppers image (QF = 75%, encryption of the AC and DC luminance coefficients and the two chrominance components) and recompression of the crypto-compressed image
4.6. Conclusion
In this chapter, we have described the development of JPEG crypto-compression methods over the last two decades. State-of-the-art methods draw on essential encryption concepts alongside in-depth knowledge of the JPEG compression format. Crypto-compression operations are not limited to the JPEG format; however, the widespread use of this format for sharing and viewing images makes it particularly suitable for a presentation of this type. Generally speaking, image crypto-compression methods aim to fulfill three aims: providing a satisfactory compression ratio (which must be comparable to conventional compression), visual privacy, and encryption security (vs. brute force attacks, key estimation, etc.). As we have seen, systematic security analysis of these methods is a growing area of research. These methods are designed to provide a certain level of visual security (via selective encryption), which can be estimated based on the encryption parameters. However, there is no guarantee of a fixed privacy level, and two images encrypted in the same way may present significant differences in visual privacy levels as perceived by an observer. Visual privacy is often evaluated using conventional image quality metrics such as PSNR or SSIM. Since these methods are designed to compare “high”-quality images, however, their effectiveness in estimating the “badness” of an image is limited. In this context, new methods have recently been proposed for assessing visual privacy assessment. These methods or principles may be used to design crypto-compression methods to meet user-imposed levels of visual privacy.
Images can be processed within the JPEG crypto-compressed domain, permitting applications such as the recompression of crypto-compressed images described above. The field of image encryption is currently evolving due to the development of homomorphic encryption methods, which offer a level of security comparable with that of conventional methods while still permitting data processing. The use of these methods in the context of crypto-compression presents a significant challenge due to the need to respect the size constraints of compressed files.
4.7. References
Arnold, V.I. and Avez, A. (1967). Problèmes ergodiques de la mécanique classique. Gauthier-Villars, France.
Chan, S. (1992). Recompression of still images. Report, University of Kent, Canterbury.
Chen, G. and Ueta, T. (1999). Yet another chaotic attractor. International Journal of Bifurcation and Chaos, 9(7), 1465–1466.
Chen, G., Mao, Y., Chui, C.K. (2004). A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos, Solitons & Fractals, 21(3), 749–761.
Cho, T.S., Avidan, S., Freeman, W.T. (2010). A probabilistic image jigsaw puzzle solver. In Conference on Computer Vision and Pattern Recognition (CVPR). IEEE, San Francisco.
Chuman, T., Kurihara, K., Kiya, H. (2017). On the security of block scrambling-based ETC systems against jigsaw puzzle solver attacks. In International Conference on Acoustics, Speech and Signal Processing (ICASSP). IEEE, New Orleans.
Daemen, J. and Rijmen, V. (2002). The Design of Rijndael: AES, the Advanced Encryption Standard. Springer, Berlin.
Davis, R. (1978). The data encryption standard in perspective. IEEE Communications Society Magazine, 16(6), 5–9.
Diffie, W. and Hellman, M. (1976). New directions in cryptography. IEEE Transactions on Information Theory, 22(6), 644–654.
Dufaux, F., Wee, S., Apostolopoulos, J., Ebrahimi, T. (2004). JPSEC for secure imaging in JPEG 2000. In Electronic Imaging, Applications of Digital Image Processing, Tescher, A. (ed). The International Society for Optical Engineering, Bellingham.
Dworkin, M. (2001). Recommendation for block cipher modes of operation: Methods and techniques. Report, National Institute of Standards and Technology, Computer Security Division, Gaithersburg.
El Gamal, T. (1985). A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Transactions on Information Theory, 31(4), 469–472.
Engel, D., Stütz, T., Uhl, A. (2009). A survey on JPEG2000 encryption. Multimedia Systems, 15(4), 243–270.
Fridrich, J. (1997). Image encryption based on chaotic maps. In International Conference on Systems, Man, and Cybernetics (SMC). IEEE, Orlando.
Fridrich, J. (1998). Symmetric ciphers based on two-dimensional chaotic maps. International Journal of Bifurcation and Chaos, 8(6), 1259–1284.
Grangetto, M., Magli, E., Olmo, G. (2006). Multimedia selective encryption by means of randomized arithmetic coding. IEEE Transactions on Multimedia, 8(5), 905–917.
Guan, Z.-H., Huang, F., Guan, W. (2005). Chaos-based image encryption algorithm. Physics Letters A, 346(1), 153–157.
Hamidouche, W., Farajallah, M., Sidaty, N., El Assad, S., Deforges, O. (2017). Real-time selective video encryption based on the chaos system in scalable HEVC extension. Signal Processing: Image Communication, 58, 73–86.
ISO/IEC 10918-5:2013 (2013). Information technology – Digital compression and coding of continuous-tone still images: JPEG File Interchange Format (JFIF) – Part 5. Report, International Organization for Standardization.
Itier, V., Puteaux, P., Puech, W. (2020). Recompression of JPEG crypto-compressed images without a key. IEEE Transactions on Circuits and Systems for Video Technology, 30(3), 646–660.
JEITA CP-3451E (2002). Exchangeable image file format for digital still cameras: Exif Version 2.32. Report, Japan Electronics and Information Technology Industries Association.
Johnson, M., Ishwar, P., Prabhakaran, V., Schonberg, D., Ramchandran, K. (2004). On compressing encrypted data. IEEE Transactions on Signal Processing, 52(10), 2992–3006.
Karn, P., Metzger, P., Simpson, W. (1995). The ESP triple DES transform. RFC, 1851, 1–11.
Kerckhoffs, A. (1883). La cryptographie militaire. Journal des sciences militaires, IX, 5–38, 161–191.
Kumar, A.A. and Makur, A. (2008). Distributed source coding based encryption and lossless compression of gray scale and color images. In Workshop on Multimedia Signal Processing (MMSP). IEEE, Cairns.
Kurihara, K., Shiota, S., Kiya, H. (2015). An encryption-then-compression system for JPEG standard. In Picture Coding Symposium (PCS). IEEE, Cairns.
Kurihara, K., Imaizumi, S., Shiota, S., Kiya, H. (2017). An encryption-then-compression system for lossless image compression standards. IEICE Transactions on Information and Systems, 100(1), 52–56.
Lam, E.Y. and Goodman, J.W. (2000). A mathematical analysis of the DCT coefficient distributions for images. IEEE Transactions on Image Processing, 9(10), 1661–1666.
Lazzeretti, R. and Barni, M. (2008). Lossless compression of encrypted grey-level and color images. In European Signal Processing Conference. EUSIPCO, Lausanne.
Li, W. and Yuan, Y. (2007). A leak and its remedy in JPEG image encryption. International Journal of Computer Mathematics, 84(9), 1367–1378.
Lian, S., Sun, J., Wang, Z. (2004). Perceptual cryptography on JPEG2000 compressed images or videos. In International Conference on Computer and Information Technology (CIT). IEEE, Wuhan.
Mao, Y., Chen, G., Lian, S. (2004). A novel fast image encryption scheme based on 3D chaotic baker maps. International Journal of Bifurcation and Chaos, 14(10), 3613–3624.
Merkle, R.C. (1978). Secure communications over insecure channels. Communications of the ACM, 21(4), 294–299.
Minemura, K., Moayed, Z., Wong, K., Qi, X., Tanaka, K. (2012). JPEG image scrambling without expansion in bitstream size. In International Conference on Image Processing (ICIP). IEEE, Orlando.
Norcen, R. and Uhl, A. (2004). Encryption of wavelet-coded imagery using random permutations. In International Conference on Image Processing (ICIP). IEEE, Singapore.
Paillier, P. (1999). Public-key cryptosystems based on composite degree residuosity classes. In International Conference on the Theory and Applications of Cryptographic Techniques. EUROCRYPT, Prague.
Pinto, M., Puech, W., Subsol, G. (2013). Protection of JPEG compressed e-comics by selective encryption. In International Conference on Image Processing (ICIP). IEEE, Melbourne.
Premaratne, P. and Premaratne, M. (2012). Key-based scrambling for secure image communication. In International Conference on Intelligent Computing. ICIC, Huangshan.
Puech, W. and Rodrigues, J.M. (2005). Crypto-compression of medical images by selective encryption of DCT. In European Signal Processing Conference. EUSIPCO, Antalya.
Puech, W., Bors, A.G., Rodrigues, J.M. (2013). Protection of colour images by selective encryption. In Advanced Color Image Processing and Analysis, Fernandez-Maloigne, C. (ed.). Springer, New York.
Reininger, R. and Gibson, J. (1983). Distributions of the two-dimensional DCT coefficients for images. IEEE Transactions on Communications, 31(6), 835–839.
Rivest, R.L., Shamir, A., Adleman, L. (1978). A method for obtaining digital signatures and public-key cryptosystems. Communications of the ACM, 21(2), 120–126.
Rodrigues, J.M., Puech, W., Bors, A.G. (2006). Selective encryption of human skin in JPEG images. In International Conference on Image Processing (ICIP). IEEE, Atlanta.
Said, A. (2005). Measuring the strength of partial encryption schemes. In International Conference on Image Processing (ICIP). IEEE, Genoa.
Schaefer, G. and Stich, M. (2003). UCID: An uncompressed color image database. In Electronic Imaging: Storage and Retrieval Methods and Applications for Multimedia. SPIE, San Jose.
Scharinger, J. and Pichler, F. (1996). Efficient image encryption based on chaotic maps. In Proceedings of the 20th Workshop of the Austrian Association for Pattern Recognition (OAGM/AAPR) on Pattern Recognition, Pinz, A. (ed.). R. Oldenbourg Verlag GmbH, Munich.
Shahid, Z., Chaumont, M., Puech, W. (2011). Fast protection of H. 264/AVC by selective encryption of CAVLC and CABAC for I and P frames. IEEE Transactions on Circuits and Systems for Video Technology, 21(5), 565–576.
Shannon, C.E. (1949). Communication theory of secrecy systems. Bell System Technical Journal, 28(4), 656–715.
Shi, C. and Bhargava, B. (1998). A fast MPEG video encryption algorithm. In International Conference on Multimedia (MM). ACM, Bristol.
Singh, G. (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for information security. International Journal of Computer Applications, 67(19), 33–38.
Unterweger, A. and Uhl, A. (2012). Length-preserving bit-stream-based JPEG encryption. In Workshop on Multimedia and Security (MMSec). ACM, Warwick.
Usman, K., Juzoji, H., Nakajima, I., Soegidjoko, S., Ramdhani, M., Hori, T., Igi, S. (2007). Medical image encryption based on pixel arrangement and random permutation for transmission security. In International Conference on e-Health Networking, Application and Services (Healthcom). IEEE, Taipei.
Van Droogenbroeck, M. and Benedett, R. (2002). Techniques for a selective encryption of uncompressed and compressed images. In Advanced Concepts for Intelligent Vision Systems (ACIVS), Springer, Ghent.
Vernam, G.S. (1926). Cipher printing telegraph systems: For secret wire and radio telegraphic communications. Journal of the AIEE, 45(2), 109–115.
Wallace, G.K. (1992). The JPEG still picture compression standard. IEEE Transactions on Consumer Electronics, 38(1), XVIII–XXXIV.
Wright, C.V., Feng, W.-C., Liu, F. (2015). Thumbnail-preserving encryption for JPEG. In Workshop on Information Hiding and Multimedia Security (IH&MMSec). ACM, Portland.
Xiang, T., Wong, K.-W., Liao, X. (2007). Selective image encryption using a spatiotemporal chaotic system. Chaos: An Interdisciplinary Journal of Nonlinear Science, 17(2), 023115.
Zhu, Z.-L., Zhang, W., Wong, K.-W., Yu, H. (2011). A chaos-based symmetric image encryption scheme using a bit-level permutation. Information Sciences, 181(6), 1171–1186.
Zimmermann, P.R. (1995). The Official PGP User’s Guide, Volume 5. MIT Press, Cambridge.
- 1 Available at: https://eur-lex.europa.eu/legal-content/FR/TXT/?uri=CELEX%3A32016R0679.
- 2 Available at: https://www.ijg.org/.
- 3 Independent JPEG Group; available at: https://www.ijg.org/.