Chapter 11: Monitoring Enterprise Apps with Microsoft Defender for Cloud Apps
The previous chapter covered how we can implement enterprise applications into Azure Active Directory (AD) for use with single sign-on (SSO). This included utilizing Microsoft Defender for Cloud Apps (formerly Microsoft Cloud App Security) to discover applications that are being used on your company network. In this chapter, we will look at the advanced tools and capabilities of Microsoft Defender for Cloud Apps to monitor and manage the use of cloud applications in your company.
In this chapter, we're going to cover the following main topics:
- Planning your cloud application strategy
- Implementing cloud app security policies
- Planning and configuring cloud application permissions
- Discovering apps by using a Microsoft Defender for Cloud Apps or an Active Directory Federated Services (ADFS) app report
- Using Microsoft Defender for Cloud Apps to manage application access
Technical requirements
In this chapter, we will continue to explore configuring a tenant for the use of Microsoft 365 and Azure. There will be exercises that will require access to Azure AD. If you have not yet created the trial licenses for Microsoft 365, please follow the directions provided within Chapter 1, Preparing for Your Microsoft Exam.
Planning your cloud application strategy
In Chapter 10, Planning and Implementing Enterprise Apps for Single Sign-On (SSO), we discussed how Microsoft Defender for Cloud Apps can help to discover the applications being accessed by users and how we can manage the applications that we want them to use. This included on-premises and cloud applications that we registered for SSO. This chapter will focus more on how to develop a cloud application strategy and the reasons why we would allow or deny certain applications. Let's start by reviewing what Microsoft Defender for Cloud Apps is and how it is used to discover apps being accessed by our users and registered devices.
Discovering apps with Microsoft Defender for Cloud Apps
As mentioned in Chapter 10, Planning and Implementing Enterprise Apps for Single Sign-On (SSO), Microsoft Defender for Cloud Apps is a cloud service with Microsoft 365 that provides cloud access security broker services. A cloud access security broker is used as a policy enforcement point between the consumers and the providers so that applications adhere to the baseline security requirements of the company. Microsoft Defender for Cloud Apps provides these capabilities for Microsoft, third-party cloud, and registered on-premises applications.
Microsoft Defender for Cloud Apps is a helpful solution to aid in the discovery of applications that are being used within your company to help you control shadow IT. Shadow IT is the use of applications that are not approved by the company for use on the company network or on devices that also access company data. Microsoft Defender for Cloud Apps will identify all applications that are being accessed through managed users and devices. These applications are then reported on the discovery dashboard. Knowing the applications that are being used and accessed allows us to plan for the use of authorized applications and block unauthorized applications.
For companies that have users in office locations with a firewall or a device that is able to log network traffic, Microsoft Defender for Cloud Apps' discovery capabilities allow you to connect these logs and it will create a discovery report that lists the applications that are being accessed. The workflow and architecture of Microsoft Defender for Cloud Apps are shown in Figure 11.1:
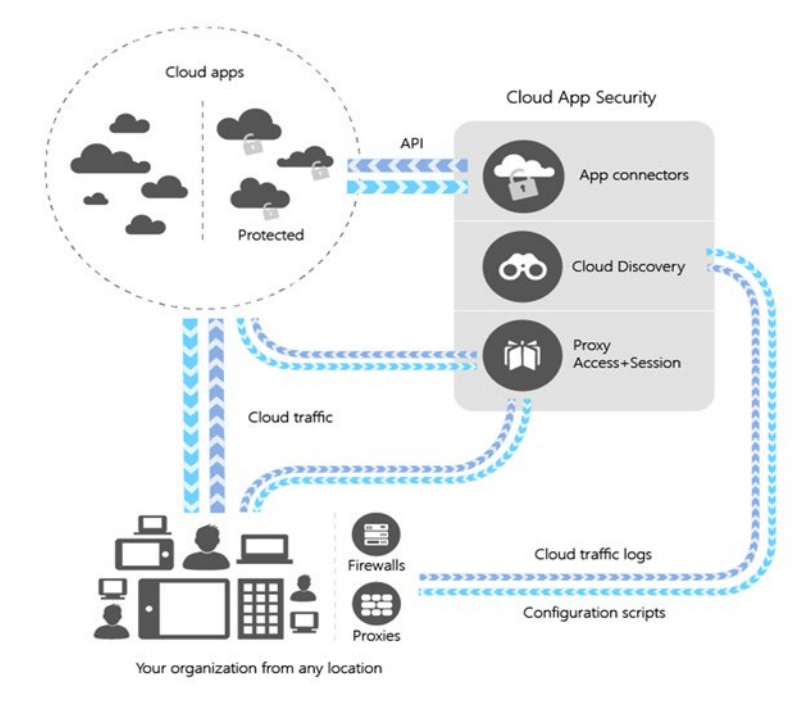
Figure 11.1 – Microsoft Defender for Cloud Apps architecture
The next sections will discuss the use of cloud app discovery for identifying application use and the next steps to take with those applications.
Cloud app discovery
As stated in the previous section, Microsoft Defender for Cloud Apps utilizes logs from network traffic to identify the applications that users are accessing. Traffic logs from on-premises firewalls will provide a snapshot report on the most common applications and the users that are accessing these apps. Traffic from devices managed with Microsoft Intune will be fed into the Microsoft Defender for Cloud Apps discovery overview dashboard, as shown in Figure 11.2:
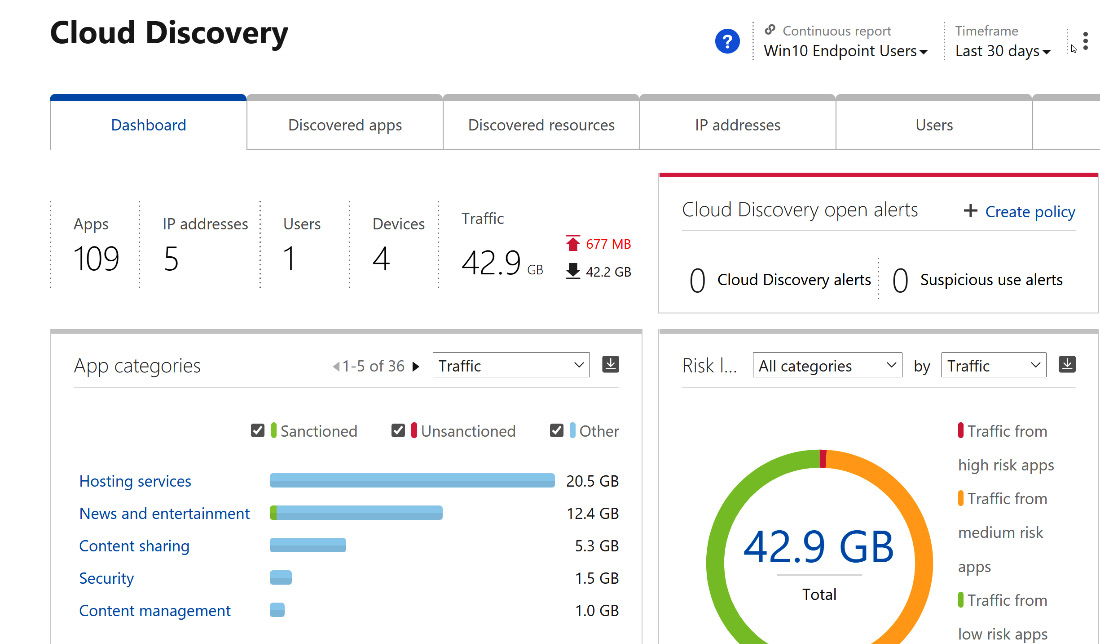
Figure 11.2 – Microsoft Defender for Cloud Apps Cloud Discovery dashboard
This information is the basis for planning and monitoring application use within your organization. You can build documentation on user usage and habits, and then evaluate the legitimate need for various applications to be used on company resources. In the Using Microsoft Defender for Cloud Apps to manage application access section, we will discuss more about evaluating the app score to determine whether to sanction or un-sanction apps. For additional information on the discovery of cloud apps, please visit this link: https://docs.microsoft.com/en-us/cloud-app-security/set-up-cloud-discovery.
Once we have determined the applications that we are going to allow as a company, we can create a plan and enforce policies utilizing Microsoft Defender for Cloud Apps. Figure 11.3 shows the architecture of monitoring applications within Azure AD. This architecture simplifies the management and monitoring of applications through Microsoft Defender for Cloud Apps:
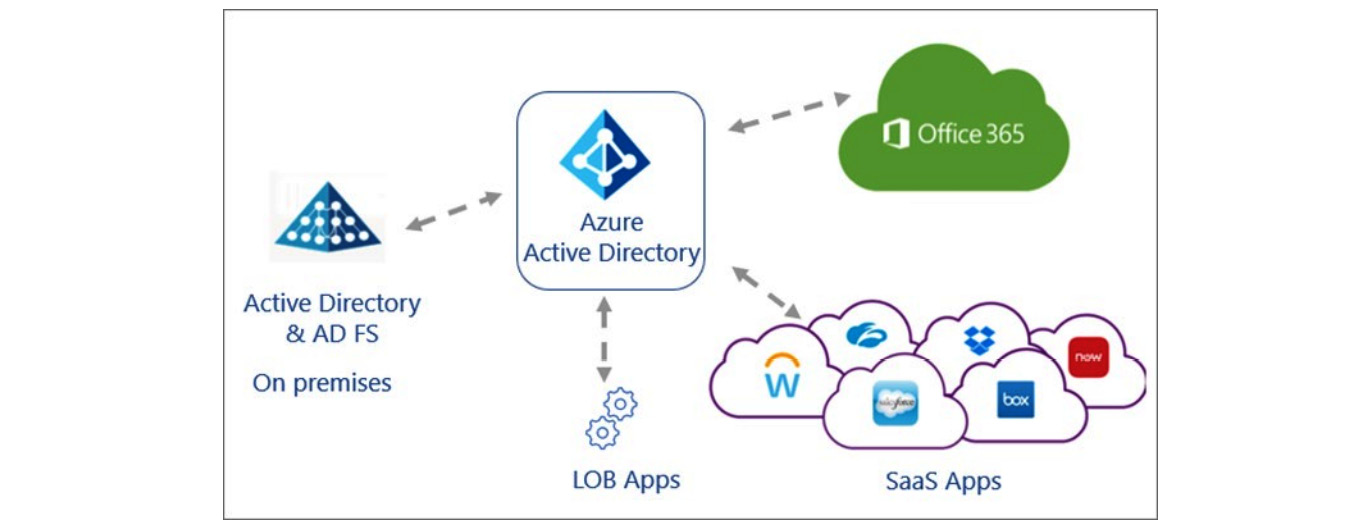
Figure 11.3 – AD and cloud apps managed by Microsoft Defender for Cloud Apps
When this architecture is utilized, the company can take advantage of the various security, compliance, and governance tools available within Azure AD, Microsoft 365, and Azure for the cloud and on-premises line of business applications, such as Microsoft Defender for Cloud Apps, Conditional Access policies, and Azure AD Identity Protection.
The next section will go through the process of creating security policies for cloud apps within Microsoft Defender for Cloud Apps.
Implementing cloud app security policies
In the previous sections, we went through the planning process of discovering and identifying applications that can be migrated to Azure AD for SSO. This section goes through the process of configuring an Azure AD application proxy to migrate on-premises applications to Azure AD for authentication and SSO.
Conditional Access policies in Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps allows us to create additional control for cloud apps through policies specific to the cloud apps that we are monitoring. Creating these policies can be done from within the Control menu within the Microsoft Defender for Cloud Apps portal, as shown in Figure 11.4. There are also a number of built-in templates, which can be found under Templates in the Control menu:
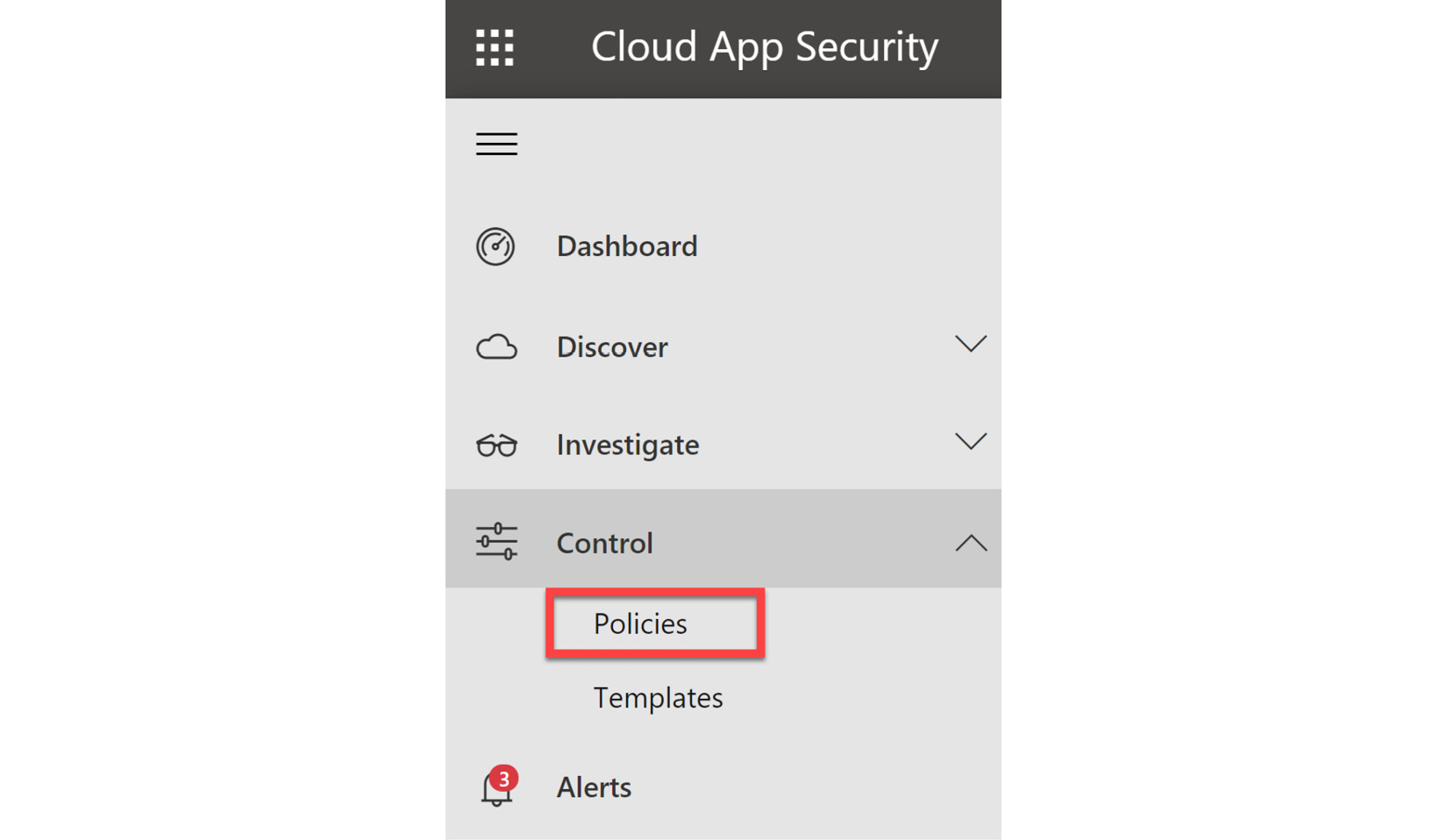
Figure 11.4 – Conditional Access policies in Cloud App Security
For more on the use case for creating a Conditional Access policy, please review Chapter 9, Planning, Implementing, and Administering Conditional Access and Azure Identity Protection, of this book. Let's go through the process of creating a new policy within the Microsoft Defender for Cloud Apps portal. We will then look at how to utilize one of the templates to create a new policy:
- The first step is to navigate to Control on the Microsoft Defender for Cloud Apps menu and select Policies, as shown in Figure 11.4.
- Note that within the policy dashboard there are several threat-detection policies that are already enabled within Microsoft Defender for Cloud Apps. These policies are used to alert and protect our environment from known malicious activity. We will discuss these alerts later in the Policy alerts and response in Microsoft Defender for Cloud Apps section. Figure 11.5 shows this dashboard. To create a new policy, select the + Create policy dropdown:
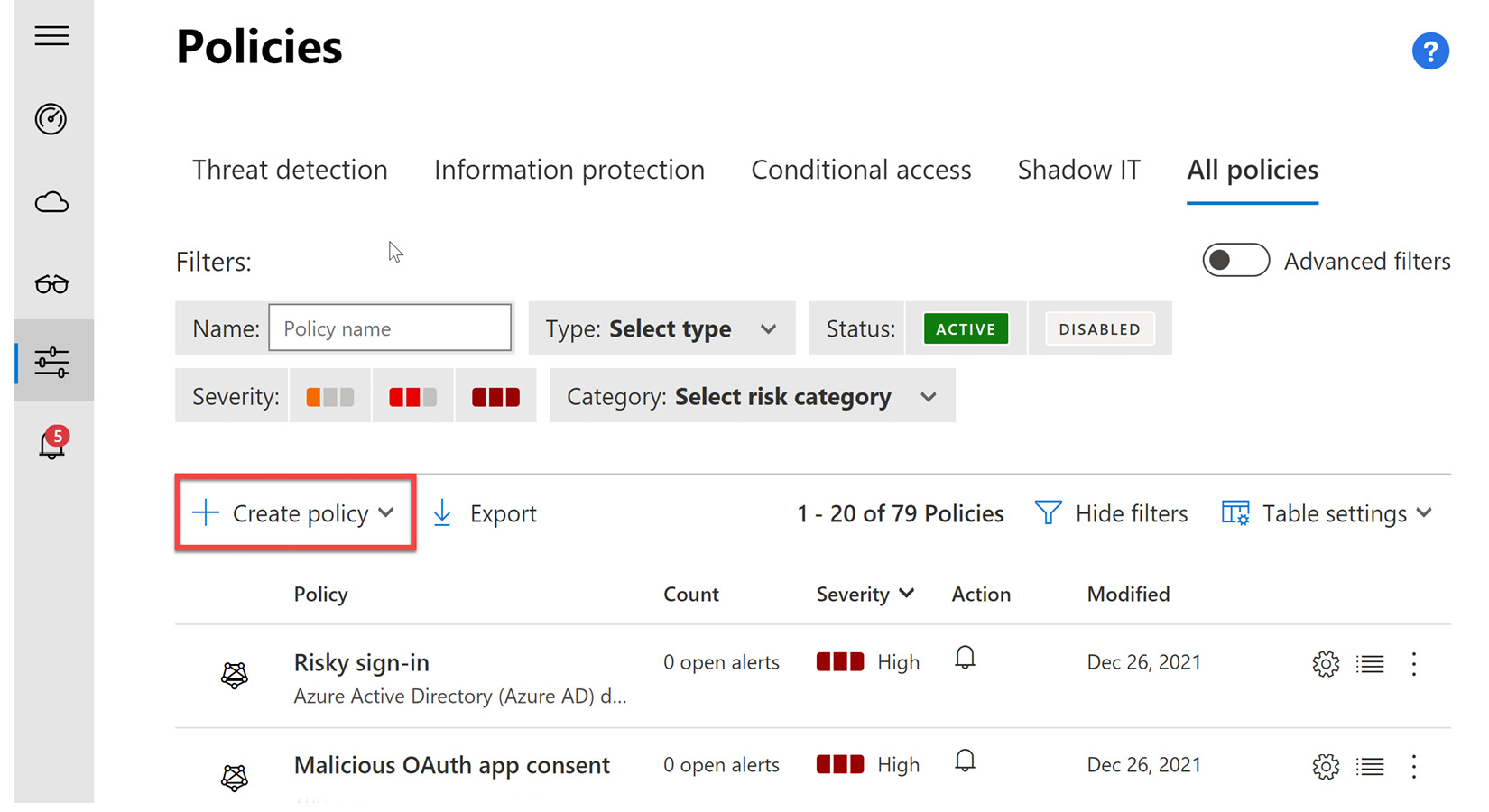
Figure 11.5 – Policies dashboard and the + Create policy option
- Within the + Create policy dropdown are several selections to determine the type of policy that you would like to create. We will discuss the use of each of these in the Types of Microsoft Defender for Cloud Apps app policies section. For this exercise, select File policy from the list:
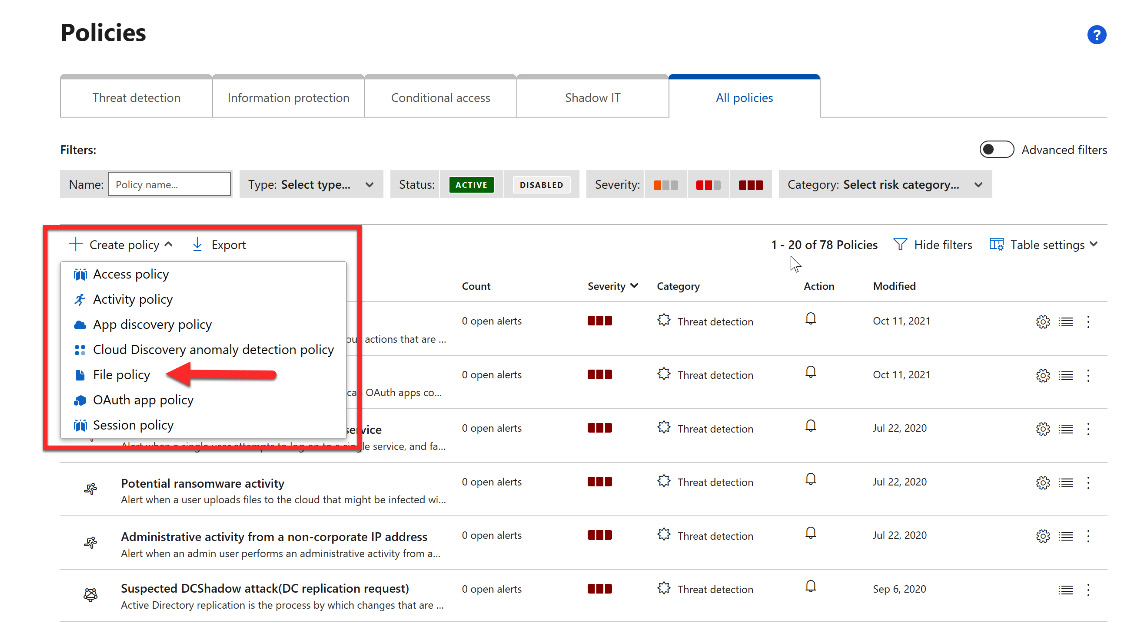
Figure 11.6 – Types of Microsoft Defender for Cloud Apps app policies
- Unlike a Conditional Access policy within Azure AD, Microsoft Defender for Cloud Apps policies provide templates that you can utilize to create your policy and provide several preconfigured filters, as shown in Figure 11.7. For this exercise, we will select the File shared with personal email addresses template:
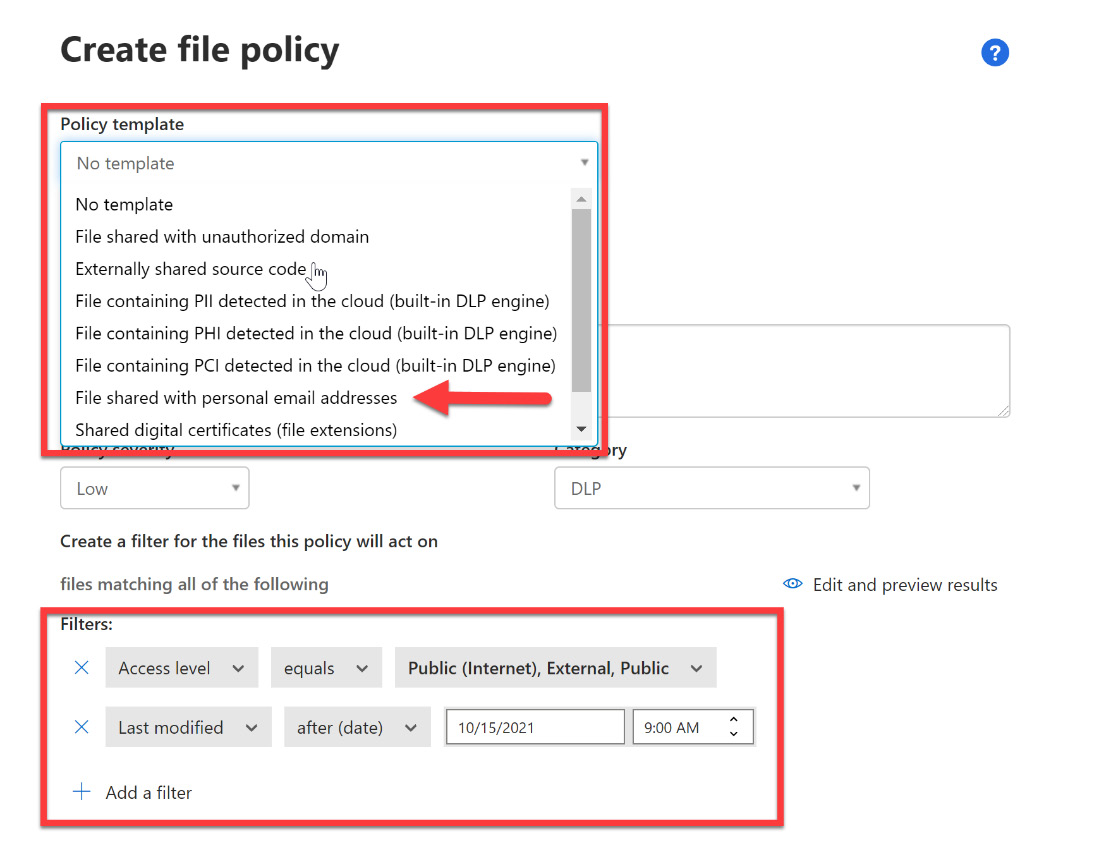
Figure 11.7 – Creating a file policy from a template
- When asked to confirm that this will overwrite all existing values, select Apply template, as shown in Figure 11.8:
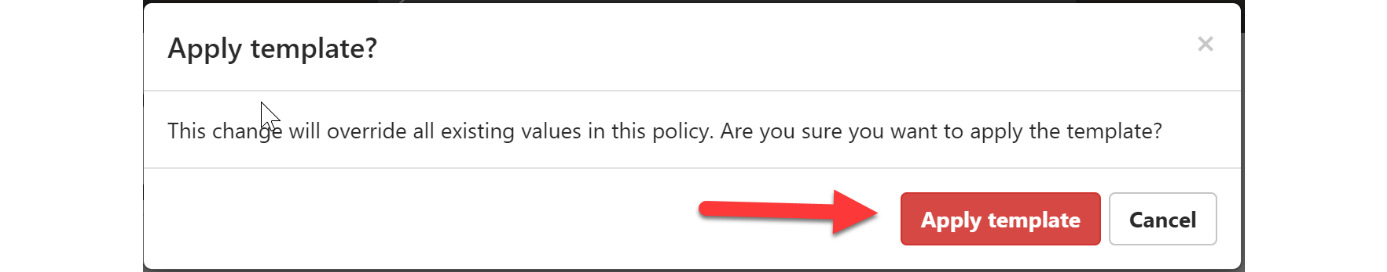
Figure 11.8 – Confirming that you want to apply template
- The template completes the required fields, but you have the option to change these as needed for your company policy. For example, you may want this policy to be of medium or high severity instead of the default low, as shown in Figure 11.9. Change Policy severity to Medium for this exercise:
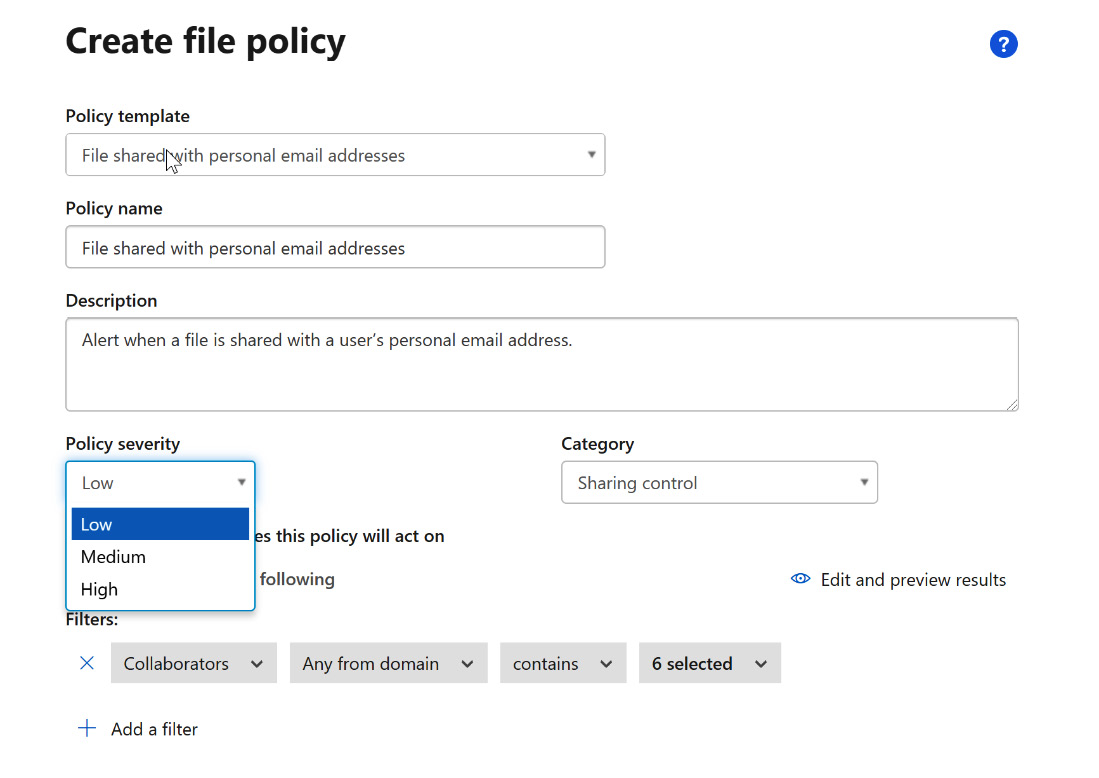
Figure 11.9 – Changing Policy severity
- Scrolling down on the Create file policy tile, you will find additional configurable drop-down selections and checkboxes to customize your policy, as shown in Figure 11.10:
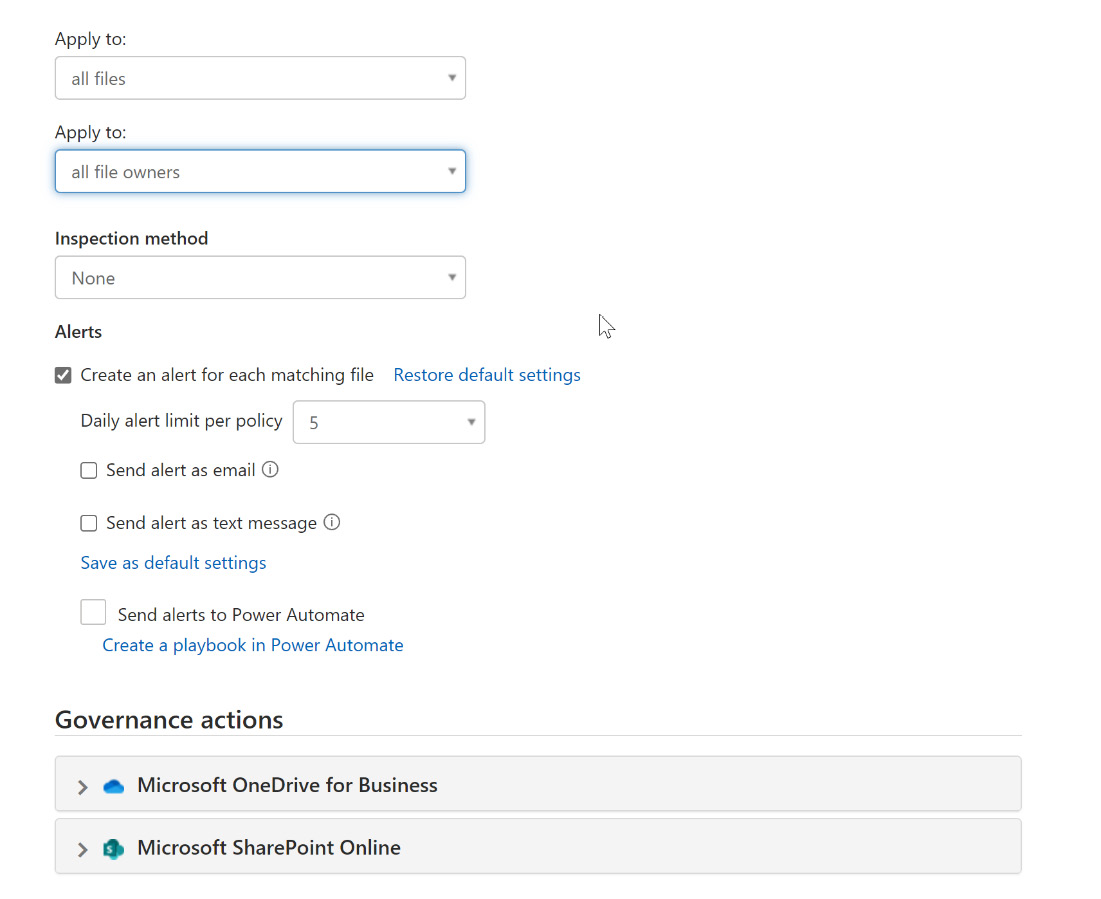
Figure 11.10 – Customizing the file policy
- The next step is to configure the files to apply the policy within OneDrive for Business and SharePoint. This can be all files, selected folders, or all files excluding selected folders. Figure 11.11 shows these selections; we will select all files for this exercise:
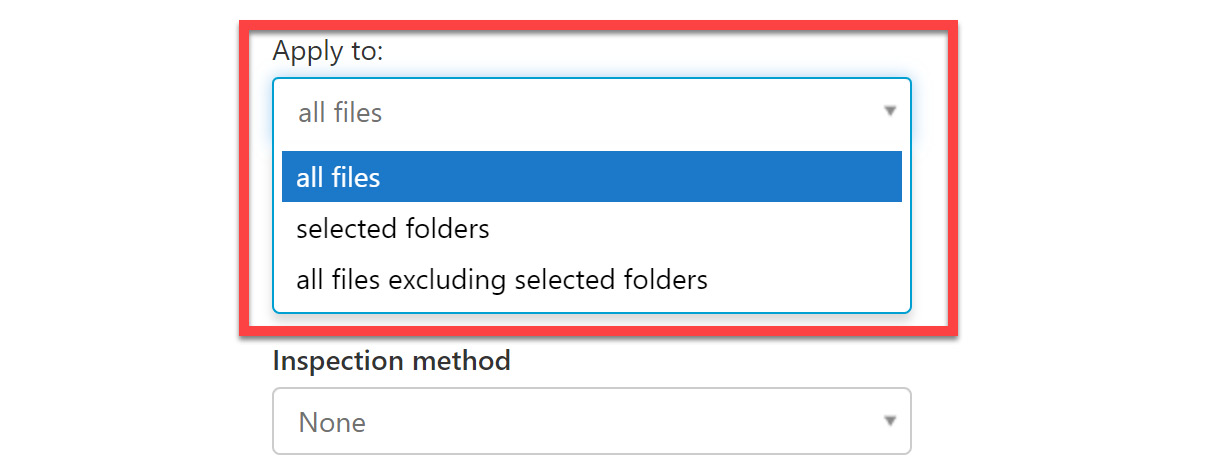
Figure 11.11 – Applying to all files
- After selecting the scope of the files, we now set Apply to: to owners to determine the files that are in scope, based on the owners of the files. This includes all file owners within the scope, a user group, or an excluded group. If you have a sales group created in your Azure AD, select that group for this exercise. If not, select all file owners, as shown in Figure 11.12:
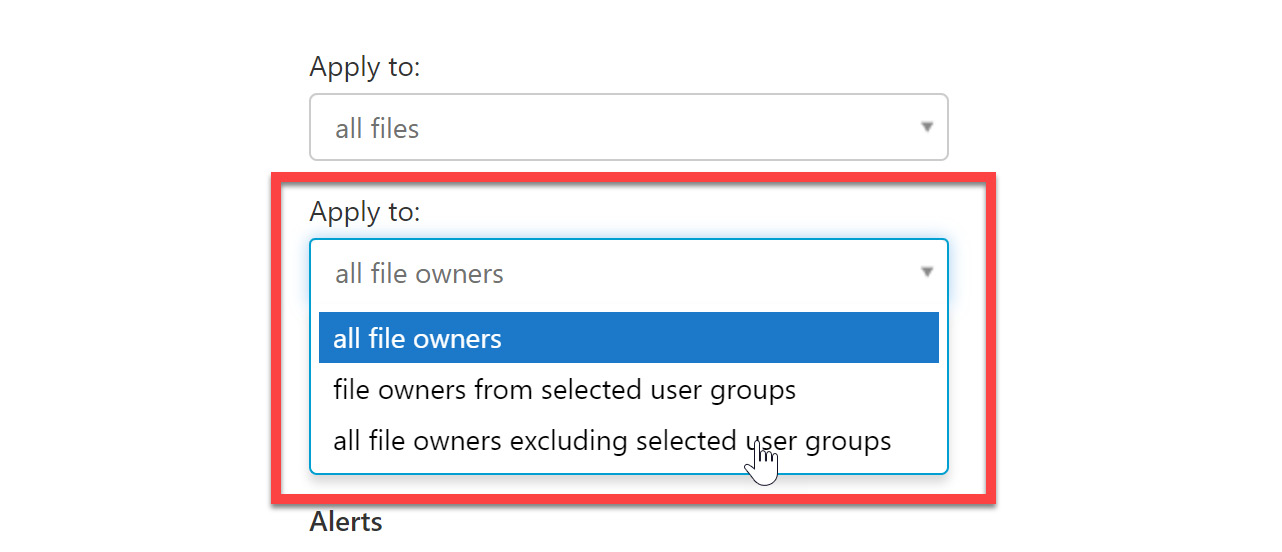
Figure 11.12 – Applying to all file owners
- The next option is Inspection method. Since the file policy is a threat protection policy, we can configure Inspection method to utilize an existing data loss prevention policy and also data classification services that are configured within Microsoft 365. Data Loss Prevention (DLP) is out of scope for this exam, so we will choose None for this exercise, as shown in Figure 11.13:
Figure 11.13 – Inspection method
- The next section to configure is Alerts. These alerts are typical for policy templates. You have the ability here to set an alert limit, specify the alert to be sent as an email or text message, and utilize a pre-created Power Automate workflow. Select Send alert as email and enter your email address for this exercise:
Figure 11.14 – Configuring Alerts
- The next two sections are Governance actions. The first is for Microsoft OneDrive for Business. These include several options, as shown in Figure 11.15. We will leave these unselected for this exercise:
Figure 11.15 – OneDrive for Business governance actions
- The Governance actions options for Microsoft SharePoint Online are the same as Microsoft OneDrive for Business. Again, leave these as the defaults:
Figure 11.16 – SharePoint Online governance actions
- The final action is to create the policy. There is a note in the portal that clarifies that this policy will only scan online files and folders and nothing external, per Microsoft privacy standards:
Figure 11.17 – Creating the policy
Those were the steps to create a file policy within Microsoft Defender for Cloud Apps. The next section will provide an additional definition of the other optional policy types within Microsoft Defender for Cloud Apps.
Types of Microsoft Defender for Cloud Apps app policies
When you navigate to the policy tile within Microsoft Defender for Cloud Apps, there are several different policies and templates that you can utilize. Each of these policies is categorized by the area of protection that the policy governs and the type of policy that will be implemented. The following are the types of policies that are available. More information can be found here: https://docs.microsoft.com/en-us/cloud-app-security/control-cloud-apps-with-policies.
The access policy is in the Conditional Access category. These policies work in the same way as Azure AD Conditional Access policies. They monitor the users and devices that have access to applications in Microsoft Defender for Cloud Apps in real-time.
The activity policy is in the threat detection category. These policies monitor particular activities from various users that take place across different apps and resources. These policies require the configuration of monitoring APIs to be connected to Microsoft Defender for Cloud Apps.
The app discovery policy is a shadow IT policy. Shadow IT is those applications that may not be on the list of allowed applications within the company policy. App discovery policies can monitor applications being accessed outside of these policies and report through alerts and notifications when unsanctioned apps are accessed by users and devices.
The Cloud Discovery anomaly detection policy is another shadow IT policy. These policies look for unusual activity on discovered apps. These may be on sanctioned and unsanctioned apps. An example would be a large amount of data being downloaded suddenly or impossible travel with a login event from two different countries within a short period of time.
The file policy is an information protection policy. These policies allow you to scan files within the policy scope and to verify that proper data protection is in place for potentially sensitive information within those files. Refer to Figure 11.7 on how to filter these templates for customized alerts.
The OAuth app policy is a threat protection policy. These policies investigate permissions and whether they are enabled on the app. The policy can then approve or revoke that permission. These policies are built-in.
The session policy is a Conditional Access policy. These policies monitor the activity on apps in real time and control the activity on those apps as allowed through the policy.
Now that we know the different policy types and categories, we will look at the policy alert and response dashboard in Microsoft Defender for Cloud Apps.
Policy alerts and response in Microsoft Defender for Cloud Apps
Once you have created policies to govern your cloud and enterprise apps, you need to make sure that you are monitoring and responding to these alerts. The Microsoft Defender for Cloud Apps Policies dashboard provides access to this information for policy alert and response. Figure 11.18 shows this dashboard and the built-in policies that are in place, along with alerts on those policies:
Figure 11.18 – Built-in policies and open alerts
If you look on the left-hand side menu, there is a bell icon that will show whether there are any active alert notifications that you need to review. Figure 11.19 shows the active alerts and where to find these notifications:
Figure 11.19 – Alert notification and active alerts
From this dashboard, you can review and respond to these alerts, and add governance actions based on policy alerts.
In the next section, we will discuss the planning and configuring of cloud application permissions.
Planning and configuring cloud application permissions
The permissions for enterprise applications were discussed in Chapter 10, Planning and Implementing Enterprise Apps for Single Sign-On (SSO), but we will review them again here. There are two primary roles to consider for cloud applications, application administrator and cloud application administrator:
- The application administrator role, which allows users to create and manage enterprise applications, application registrations, and application proxy settings. These administrators can also grant application permissions and delegated permissions.
- The cloud application administrator role can still manage enterprise applications and application registrations, but since this designation is for cloud applications, they do not have the ability to manage application proxies.
When determining the role to assign to an administrator, you should determine whether that administrator is going to be required to manage on-premises enterprise applications that are registered with an application proxy. If so, they should be assigned the application administrator role. If they are only managing cloud-native applications, then the cloud application administrator will be the proper permission needed to adhere to the principle of least privilege.
The next section will go through the steps to discover apps in Microsoft Defender for Cloud Apps and ADFS app reports.
Discovering apps by using Microsoft Defender for Cloud Apps or an ADFS app report
In this section, we show how to discover third-party applications through Cloud App Security with Microsoft Defender for Cloud Apps reporting and ADFS app reports.
Discovering apps with Microsoft Defender for Cloud Apps app report
Microsoft Defender for Cloud Apps utilizes logs from network traffic to identify the applications that users are accessing. Traffic logs from on-premises firewalls will provide a snapshot report on the most common applications and the users that are accessing these apps. Additional information on app discovery can be found at this link: https://docs.microsoft.com/en-us/cloud-app-security/set-up-cloud-discovery. Traffic from managed devices will be fed into the Microsoft Defender for Cloud Apps Cloud Discovery overview dashboard, as shown in Figure 11.20:
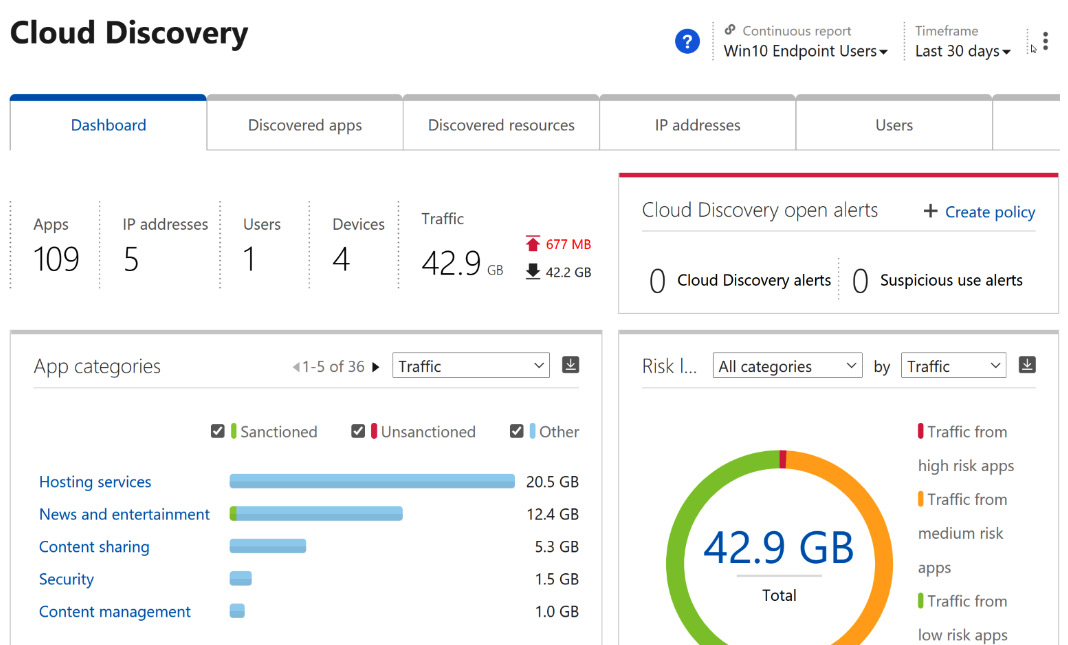
Figure 11.20 – Microsoft Defender for Cloud Apps Cloud Discovery dashboard
This information is the basis for planning and monitoring application use within your organization. In addition, you can review the Discovered apps tab within the Cloud Discovery menu to identify apps based on configured user groups, as shown in Figure 11.21:
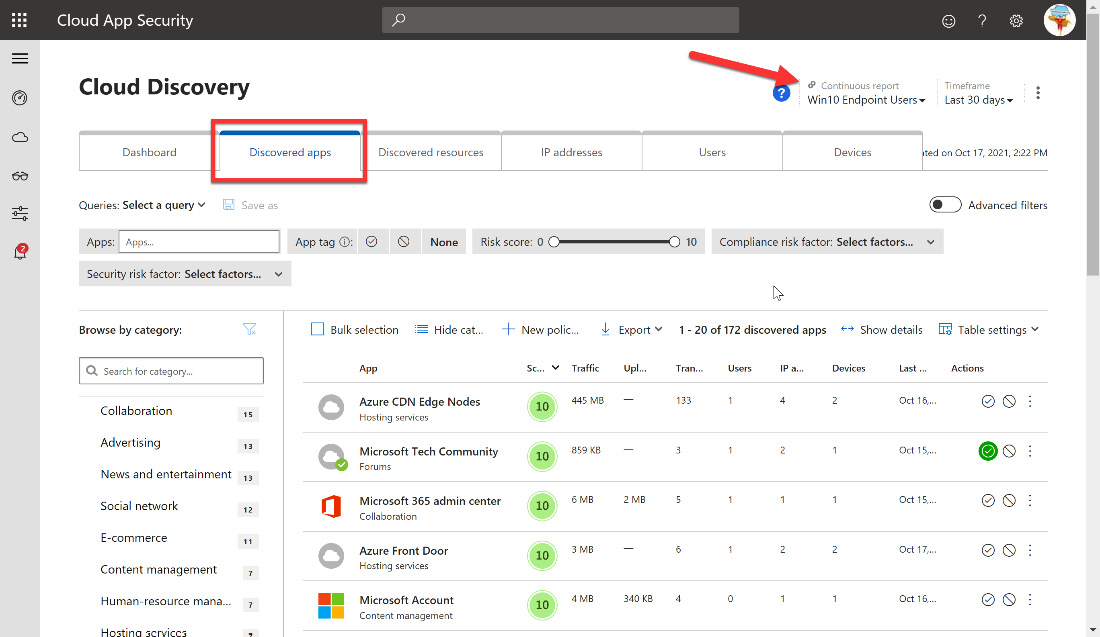
Figure 11.21 – Discovered apps dashboard
The next sections will discuss the use of Cloud App Discovery for identifying application use through on-premises resources.
Discovering apps with an ADFS app report
As stated in the previous section, Microsoft Defender for Cloud Apps utilizes logs from network traffic to identify the applications that users are accessing. Traffic logs from on-premises firewalls will provide a snapshot report on the most common applications and the users that are accessing these apps. The report can be initiated through the home dashboard of Microsoft Defender for Cloud Apps. You will need access to your firewall to generate this report. Figure 11.22 shows where you initiate the creation of this report:
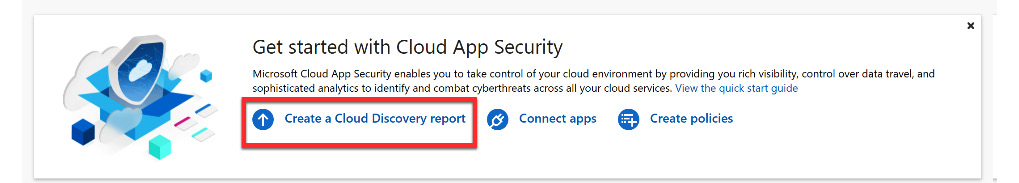
Figure 11.22 – Creating a Cloud Discovery report
This information is the basis for planning and monitoring your application use within your organization. The next section will discuss how to manage these applications and protect against shadow IT.
Using Microsoft Defender for Cloud Apps to manage application access
The final area that we need to consider for our application strategy is securing the applications and determining which applications will be allowed or denied access by our users and registered devices.
Discovered app scoring
As a company, you have a responsibility to protect against the sharing of personally identifiable information and company data by users. This includes the potential exposure of this data through unsanctioned cloud applications that are being accessed from devices. Cloud App Security provides an easy-to-follow scoring system for cloud applications, where the level of protection that each app provides has a score based on GENERAL, SECURITY, COMPLIANCE, and LEGAL criteria. Figure 11.23 shows the scoring for Microsoft Office Online:
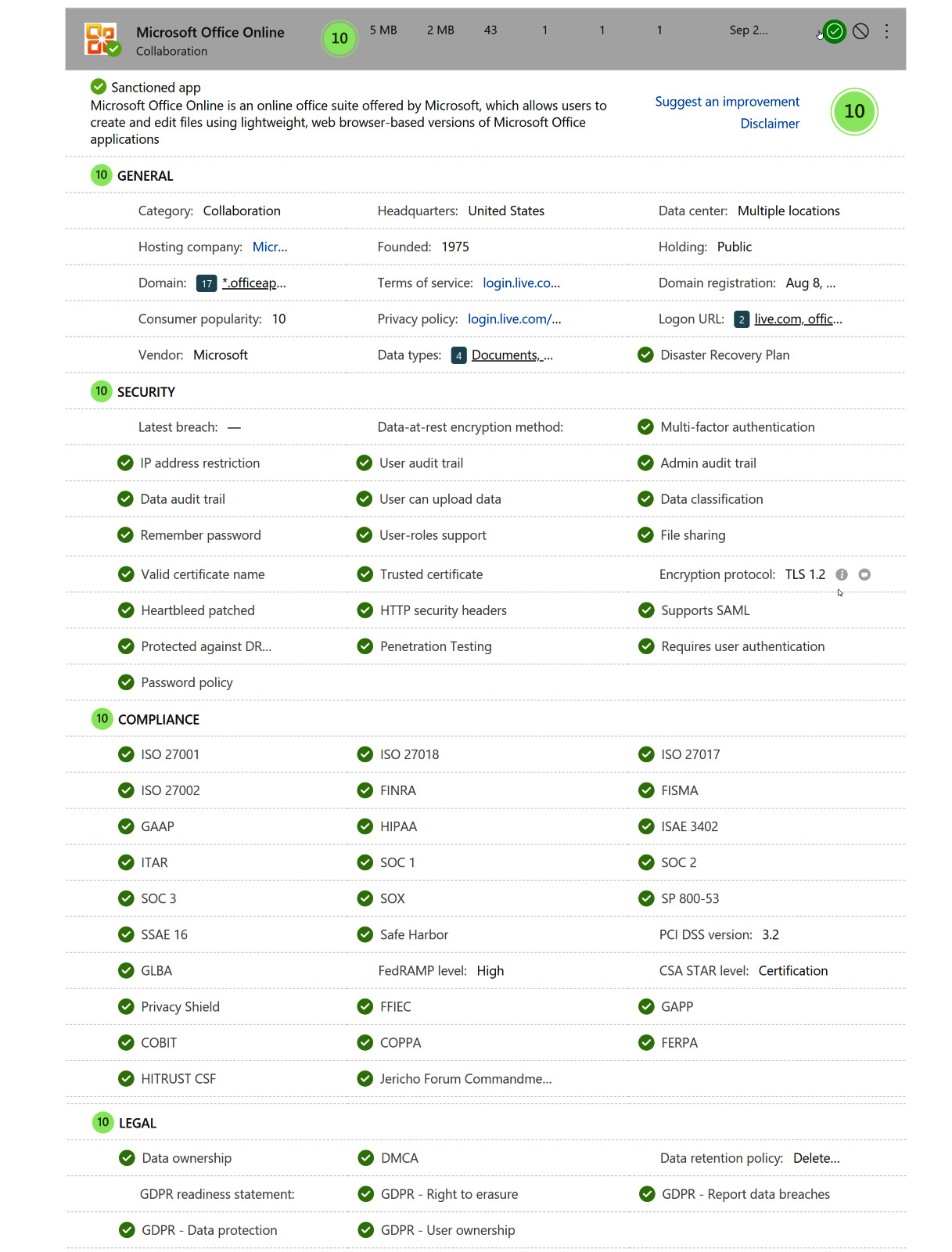
Figure 11.23 – Microsoft Office Online score
Sanctioning and unsanctioning apps
Once you have evaluated the applications that are discovered as being accessed by your company users and devices, you can review their scores and determine whether these will be sanctioned or unsanctioned for use. Sanctioned apps will continue to be allowed for use by users and devices. Unsanctioned apps will be blocked on registered devices or devices that registered users are logged into. This includes apps that are installed locally, accessed on a web browser, and accessed on a private browser session. Figure 11.24 shows the sanctioned and unsanctioned selection area for an app:
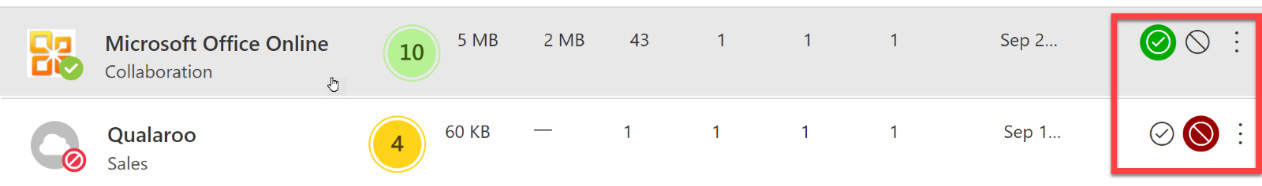
Figure 11.24 – Sanctioned and unsanctioned apps
When unsanctioning an app in Microsoft Defender for Cloud Apps, the access to the application is blocked on devices that are registered to Azure AD and/or users that are logged into Azure AD on those devices. This includes blocking access to installing these applications on these devices or access through web browsers, both public and private sessions.
Next, we will provide a summary of what was discussed in this chapter.
Summary
In this chapter, we covered the use of third-party cloud applications within our organization, and how to manage, monitor, and control them with Cloud App Security. This included how to create app policies and discover apps to sanction or unsanction on a Microsoft tenant. In the next chapter, we will discuss entitlement management and managing the terms of use for users.
