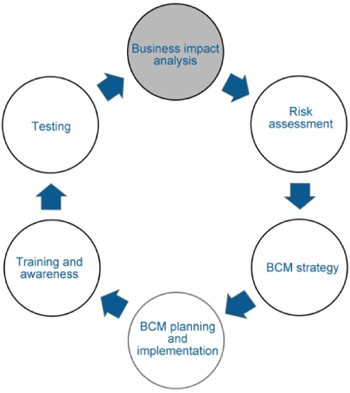
CHAPTER 3: RUNNING THE BCM LIFE CYCLE
BCM implementations follow a logical sequence of activities by which information flow and analysis are conducted. These activities and implementations are grouped in phases or stages, where each phase or stage makes use of the others. The progressive, continuous sequence of these phases or stages is called the BCM life cycle.
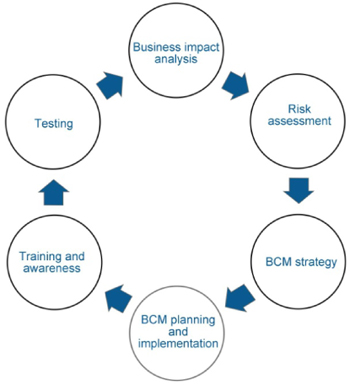
I find the term “life cycle” very descriptive and fit for the overall BCM purpose and concept. The first word “life” indicates progression, development, growth, and maturity.
The second word “cycle” indicates continuity, iteration, and persistence. Both provide strong indicators to many of the features that successful BCM programs should possess.
Running the BCM life cycle for the first time
Now we have finished the setup of the different elements of the BCM governance model, we can move on to the implementation of the BCM model, or the BCM life cycle.
The BCM program will include a set of initiatives, projects, and task packages that achieve certain goals. There are two main approaches that can be followed here:
- Implement the different phases and stages of the BCM life cycle as separate tasks, or small projects.
- Implement the complete life cycle as a dedicated project.
The first approach is useful when the organization has already implemented some phases or stages in previous projects, sometimes through different specialties, like information security or IT disaster recovery. What will be needed is to complement and build upon the other stages or phases to complete the life cycle.
The second approach is preferred when the organization has not implemented the BCM life cycle before. It is more beneficial when an experienced consultant is recruited to implement the life cycle. With such an approach, effort and resources are more dedicated and more attention is given to the project than the regular tasks being executed on a daily basis.
The focus here will be on using the second approach. The reason for this selection is to show the integration and sequence features of the BCM life cycle. Nevertheless, different phases or stages of the BCM life cycle can still be implemented separately.
Launching the first BCM project
The BCM project will include all the BCM life cycle phases or stages. The project will lay the foundations for the BCM program and implementations in the organization along with the BCM governance setup. As with all projects, launching the BCM project will require a set of components. Of particular importance among these components are the following:
- business case
- terms of reference
- communication plan
- risk register.
These components include vital and critical information for initiating the project.
Business case
The business case answers the very fundamental question of why the organization should undertake the BCM project. It includes all the rationale and drivers behind performing the project.
For BCM projects, the business case may not be so easy to define. However, there are some common drivers and needs that can significantly help in defining it:
- recent failures which the organization experienced
- regulatory, legal, or legislative requirements
- gaining competitive advantage
- enhancing operational and organizational performance
- protection of the organization’s assets.
The most important features of your business case should be relevance, flexibility, and practicality. Asking for too much might prematurely kill the effort. On the other hand, promising too much will very probably damage the program’s credibility and put the whole BCM program at risk.
Terms of reference
The terms of reference (ToR) of a project define the scope, deliverables, project structure, project roles and responsibilities, resources and budgets, and timelines. In the case where an external consultant is hired, the ToR provide the basis for their contract.
For the scope, you should identify what the scope of the project activities will be for:
- products and services
- geographical locations
- organizational units
- assets
- activities related to stages and phases of the BCM life cycle.
Such scoping of the project may be the same as for the BCM program or could be a subset of it.
For the deliverables, the BCM project should include the following deliverables. Please note that these deliverables are delivered through different phases of the BCM life cycle:
- BIM and risk assessment documentation
- BCM strategy documentation
- BCM framework (if included within the scope of the project)
- BCM plans and procedures
- BCM knowledge documentation and resources
- BCM testing documentation and resources
- BCM awareness and training material, documentation, and resources.
As with the business case, the golden rule is to be relevant, flexible, and practical.
Roles and responsibilities list the various stakeholders of the BCM project and what their roles are. A good place to start is the list of roles and responsibilities defined within the BCM governance model. Make sure that you have all the various roles assigned to their owners.
Resources and budgets need to be defined here. Seek help to design your budget requirements from professional bodies, consultants, and peer organizations. Add a margin as a cushion for expected delays or scope changes. Make sure you challenge your budgeting assumptions carefully as you will need to defend your requirements in the face of budget cuts and shrinkages. It’s also beneficial to have the stakeholders review and communicate their views on the budgets and resources as this can help rationalize the decisions and make them more relevant to the organization. The same applies for the timeline. The golden rule of being relevant, practical, and flexible should always be considered in this area.
The communication plan
The communication plan controls what messages and reports are to be communicated between the project’s stakeholders. It also defines how these messages and reports are delivered.
For a BCM project, it is very useful to draft the communication plan to ensure all the stakeholders are involved. A proper communication plan will enable progress, risks, and issues to be correctly communicated and addressed.
Risk register
The project risk register documents the identified threats to the project and how to manage them. For a BCM project, some of the risks can be:
- improper or inadequate involvement from the top management;
- poor contributions and commitment across the organization;
- poor data, feedback, and requirements communicated from stakeholders;
- improper budgeting;
- unrealistic deadlines;
- insufficient scoping.
It is worth noting here that the types of risk facing the project are highly dependent on the dynamics of your organization. Seek help from your project management office (PMO) or similar functions, peer organizations, industry forums, or consultants to define your risks and establish your risk register. Risk registers are living documents. They should be periodically reviewed before, throughout, and after the completion of the project.
BCM project hierarchy and structure
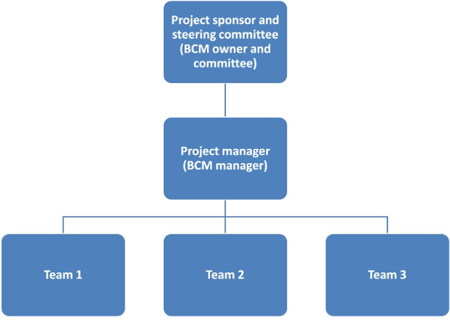
Figure 8: BCM project hierarchy
Now all the start-up documentation is ready, we can define the BCM project hierarchy:
- project sponsor: BCM owner
- project advisors: BCM committee
- project manager: BCM manager
- assistant project manager: qualified BCM officer/analyst
- business/support team: BCM coordinators and other specialized teams.
It is clear now that the previously established governance model becomes more consistent and integrated throughout the implementation of the BCM life cycle.
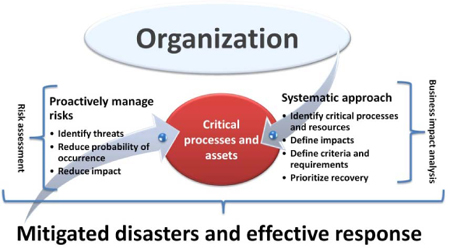
Business impact analysis
Business impact analysis is the most important phase within the BCM life cycle. It constitutes the foundation or basis upon which all later stages and phases depend. The objectives of BIA are to identify:
- the environment in which the organization exists;
- what the stakeholders’ requirements are;
- what the regulatory or statutory/legal requirements are;
- what the key, or core, activities within the organization are;
- what assets or resources, internal and external, support key activities;
- what impacts there would be on the organization in the case of a failure of key, or core, activities over time;
- the interdependencies between internal and external resources and assets;
- the organization’s obligations towards external entities.
Identifying the above would allow the BCM program to be built to “serve and protect” the most critical aspects of the organization, thus ensuring the survival of the organization should disasters and crises occur.
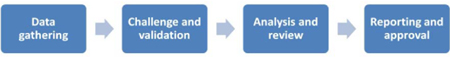
The BIA process needs careful planning, follow-up, and coordination to succeed. It also requires relatively extensive resources to complete it. The BIA process would follow the logical sequence of:
1 gathering data and requirements;
2 challenging, validating, and signing off data and requirements;
3 analyzing and reviewing;
4 reporting and approving BIA results.
The scope of the BIA should be same as that of the BCM program. Nevertheless, if the BIA is expected to take a very long time or needs extensive unavailable resources, then the BCM project manager can start with a BIA limited to certain parts of the original scope and then cover the other parts in later BIA implementations. Naturally, the BCM owner’s approval is essential for following such approach.
Gathering data and requirements
Gathering data and requirements starts with selection of the right tools to use, which are mainly summarized within three tools:
- workshops
- questionnaires
- interviews.
For successful data and requirements gathering, the BCM manager should use all three tools. Workshops generate results of good quality, but they are relatively difficult to conduct. Questionnaires generate large amounts of data in a short time, but the quality is not that good. Interviews are useful when there are some specific questions that need answering. Knowing that, your data gathering may be something like:
- Use questionnaires to collect the data and requirements from stakeholders within the scope.
- Conduct interviews to answer specific questions that may arise when analyzing data from questionnaires.
- Hold workshops to filter and link the gathered data and requirements.
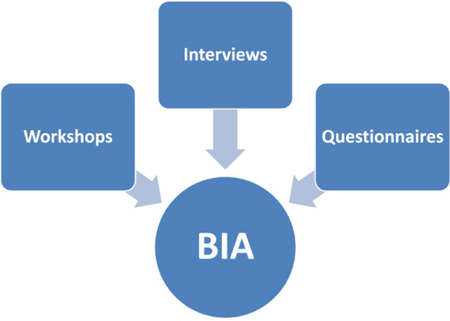
Figure 11: Data gathering approaches
When designing the questionnaires, you may use whatever methods are appropriate for your organization, from paper questionnaires to spreadsheet or word-processing software to specialized software designed especially for business continuity. Whatever the method selected, the questionnaire should gather details about:
- processes and activities within the scope;
- resources required for conducting processes and activities;
- internal and external dependencies between processes and activities;
- impacts over time when not performing the processes and activities;
- the maximum time that can be tolerated without performing the processes and activities;
- the maximum data loss tolerated for the processes and activities;
- technology used to conduct the processes and activities;
- the key people, staff availability and succession planning;
- resources required for recovering processes and activities in alternative working locations.
There are some specifications that are globally adopted in BCM programs and are identified within the BIA:
- Critical: Using the word critical to label certain processes/activities indicates there are severe impacts for not performing them and there is a higher level of priority for managing these processes/activities. The definition of critical is highly dependent on the organization and its environment. It should be understood and communicated that labeling a certain process/activity as critical does not indicate that the others are luxury or cosmetic processes/activities. It just highlights that it has higher a priority for recovery. In the event of disaster, the recovery process should be flexible enough to allow for the recovery of less critical processes/activities, when needed.
- Recovery time objective (RTO): The RTO is the time objective or goal for restoring the processes/activities. Recovery point objective (RPO): The RPO defines the currency level of data, and electronic and hard copies, needed to properly perform the process/activity. It defines the maximum data loss acceptable and is one of the major inputs to the organization’s backup and archiving processes.
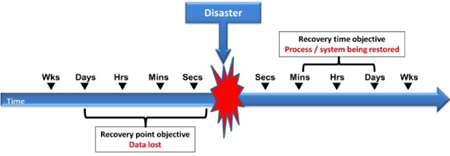
Figure 12: Continuity specifications
When specifying impacts, there is a set of common areas of impact to investigate and identify. While the set of impact areas varies from one organization to another, there are some principal areas to consider.
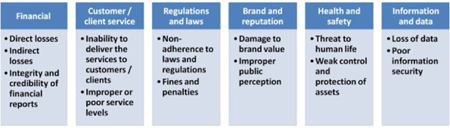
Figure 13: Common areas of impact
On another level, when investigating specific impacts, the impact measurement and rating scheme should be established: qualitatively or quantitatively. If numbers are available and accessible, quantitative impacts are more accurate, yet at the end there should be some lines drawn to determine criticalities and priorities; that’s when we go back to the qualitative approach. Otherwise, the qualitative approach seems more usable and applicable.
Now, once the questionnaires have been designed, they should be reviewed with the BCM owner to get endorsement and capture other requirements that might be needed in later phases or stages of the BCM life cycle.
After obtaining the BCM owner’s approval of the questionnaires, they should be distributed to the BCM coordinators. Group workshops or one-to-one meetings are conducted to introduce the BCM coordinators to the questionnaires and explain how the BIA process will be performed. It is important here to highlight and stress the importance of the deadlines set for completing the BIA. This step is important since it will help the BCM coordinators plan how best to contribute to the BIA process.
Now the BCM coordinators have the BIA questionnaires, there should be constant follow-ups with the BCM coordinators to check on their progress and whether they have inquiries or questions that need answers. There may also be a need to hold workshops or meetings for coordinators, especially to resolve dependency issues.
Challenge, validate, and sign off data and requirements
The information provided from the first phase of data and requirements gathering should be put through several challenge and validation cycles at different levels. The main reason for this is to ensure that correct data are provided and requirements documentation is properly produced. The main concerns about the provided data are incompleteness, inaccuracy, and unfair (overestimation or underestimation) ratings of requirements.
The first challenge and validation level is with the process/activity owner and BCM coordinator. For this level, all sections of the BIA should be visited, making sure that all data and ratings are provided and are justifiable. If there are noticeable points or concerns to highlight, they need to be brought up for discussion in order to be resolved.
If they are not resolved, these concerns need to be raised to the next validation level: the business unit head. For this, a one-to-one meeting between the business unit head and the BCM coordinator should be held. Within that meeting, the questionnaire should be introduced and its various sections walked through. This meeting is the right place to raise any unresolved issues or noticeable points that require clarification and decisions to be made. Once finalized, the business unit should sign off the questionnaire for completeness and accuracy of data provided.
There’s one guideline to follow here; the data contained within the BIA questionnaire is owned by the business unit. The people at the various business units are the experts in their areas and they are responsible for the validity of the information they provide. The BCM team’s role is to help them follow the process properly. The more the BCM team follows this guideline, the more successful it is in the BCM program.
Analyze, report, and approve BIA results
The analysis of data and requirements provided through the BIA questionnaire focuses on defining the RTO, RPO, and criticality of processes/activities within the scope. It also defines the resources required to continue working and recover the processes/activities at alternative work locations. Achieving such a results is not easy and it involves many variables. Impacts related to staff well-being, adherence to regulations and laws, financial implications, reputation and image, and other impacts should be investigated taking into consideration the dependency map of the processes/activities.
There’s also the concept of “seasonality” of processes. The season of a process/activity is when the criticality of this process/activity becomes higher due to more severe impacts being expected. Examples of seasonal processes/activities are payroll, regulatory reporting, stock inventories, etc.
When defining the BIA results, there should be room for scenarios where some processes/activities may be highly utilized in disasters or crises while they enjoy moderate utilization in normal working conditions. For example, the organization’s website or portal may not be critical to the operations and business but during a disaster it could be very helpful for internal and external communications. Thus its criticality is upgraded and a more demanding RTO and RPO are required.
Once all the requirements have been defined, a report should be produced for the BCM owner and committee containing all of the BIA results. A typical BIA report would include:
- an introduction explaining its purpose and methodology;
- an executive summary highlighting the most important results and issues;
- consolidated BIA results for all the processes/activities within the scope;
- detailed BIA results for individual business units;
- concerns and issues highlighted within the BIA process;
- recommendations.
Approval of the BIA results is the responsibility of the BCM owner and committee. Their approval should be documented for audit purposes.
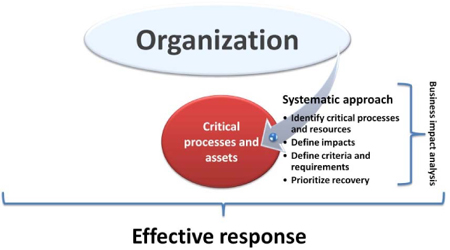
Figure 14: BIA process outcomes
Risk and threat assessment
Now that the critical aspects of the organization have been identified, we should start our proactive approach towards protecting them. BCM is not only about reacting to and recovering from disasters; it is also about mitigating the probability of their occurrence and their impacts when they do occur.
A comprehensive look at the critical aspects of an organization would identify the main components of these. In almost all organizations, these components are:
Having this component breakdown should make the process of threat identification easier and more focused. The list of threats facing the above components of critical aspects of an organization is highly dependent on the organization’s environment and nature. But the main point here is to keep an open mind, not only about external threats but also any internal weaknesses that may introduce high impacts.
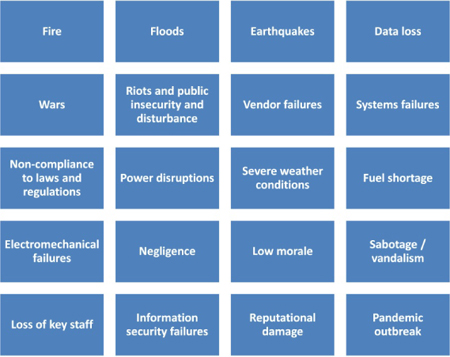
Figure 16: Common threats and risks
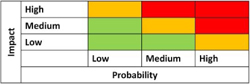
External threats and internal weaknesses are translated into risks by defining probabilities and impacts where:
Risk = probability x impact
Graphically, a matrix is used to illustrate the various ratings of risks. A selection should be made here between using a quantitative approach or a qualitative approach for defining probabilities and impacts. It is suggested that it is kept simple and consistent with the approach used in the BIA.
Risk treatment options
Identifying external threats and internal weaknesses is only one step; deciding how to treat them comes next. Risk treatment should be in line with the organization’s risk appetite and risk tolerance. Risk appetite is simply how much risk the organization is willing to take, or manage. Related to risk appetite is risk tolerance, which defines the amount of risk the organization is willing to accept. It is the organization’s pain threshold for risk.
There are common risk and threat treatment options to select from:
- Accept or tolerate: Risk is usually accepted when the impact is low, regardless of the probability. In the worst cases, high-probability, low-impact risks are annoyances to normal operations and working conditions.
- Transfer or share: Transferring or sharing risks is widely used for low-probability, high-impact risks. Usually, this type of risk is very hard to justify in terms of cost. Common implementations of risk transfer are using insurance and outsourcing. The tricky part is keeping an eye on how the third party (insurance company or outsourcing company) is managing the risk.
- Terminate or avoid: When possible and cost-effective, organizations aim to eliminate the source of the risk, thus moving the probability to a minimal value.
- Treat or mitigate: Mitigation of risks is the option chosen when the probability cannot be minimized effectively but the impact can be. To minimize the impact, the organization implements certain measures to control the risk.
As a rule, managing certain risks requires a mix of treatment options, for example managing risks to continuity and protecting your organization’s critical aspects in a cost-effective manner.
Process of threat and risk assessment
The process of threat and risk assessment starts with looking at the components forming the critical aspects of the organization and trying to identify the threats that face them and which could affect their operations. There are suggested sources that can help you identify the threats and risks:
- risk registers maintained at your organization
- recent incidents that have occurred
- internal and external audit reports
- industry studies
- insurance studies and reports
- interviews with stakeholders and staff.
After defining the risk and threat sources, define what will be used for the scoring methods for both probability and impact. Then obtain approval from the BCM owner and committee on the list of identified threats and the scoring methods.
The next step is to decide how to treat identified threats and risks, bearing in mind both applicability and cost. Obtain approval from the BCM owner and committee on these decisions.
The final step in this process is to document your selected options to treat threats and risks along with the estimated costs in a risk treatment plan. The BCM owner and committee should approve this document.
Figure 18: Business impact analysis and risk assessment
Strategies and risk treatment plans
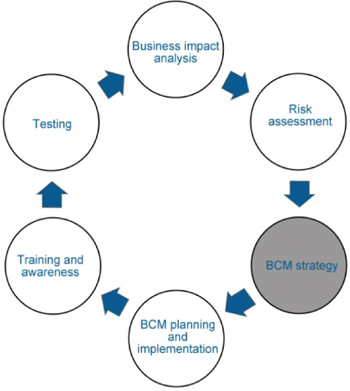
We now move to the next stage of the BCM life cycle; strategies and risk treatment plans (RTPs). The BIA defined the critical aspects and the continuity requirements of the organization. Threat and risk assessment defined the threats and risks for those critical aspects and what the management actions would be for those risks and threats. What we need to do now is to decide what strategies should be selected to satisfy the continuity requirements and how the threat and risk assessment management actions will be translated into practical and applicable plans. This phase in the BCM life cycle is called determining the BCM strategy. In this context, the BCM strategy may be referred to as the
BCM continuity options. The two terms are used interchangeably.
The main outcomes of the strategies selected will be:
- the minimization of probabilities and impacts of threats and risks facing the organization;
- ensuring continuity and protection of critical aspects of the organization;
- the introduction of higher levels of redundancy and resilience to the organization;
- the introduction of flexibility for recovery of non-critical aspects of the organization.
The guidelines for choosing the right BCM strategies and RTPs are:
- Effectiveness: How effective is the selected strategy and RTP in minimizing the probability and impact of threats and risks, protecting the critical aspects defined, and meeting continuity requirements (RTO, RPO, etc.)?
- Cost-benefit analysis: The selected strategy and RTP should have a strong cost-benefit case and analysis. As a guideline, the cost of implementing the strategy and RTP should not exceed the financial cost of the aspect being protected or the loss resulting from a threat or disaster happening.
- Applicability: The selected strategy and RTP should be practical and possible to implement. There’s not much use in designing ideal strategies and RTPs that only work in an ideal world.
The scope of the strategies and RTPs is mapped to the organizational components listed previously:
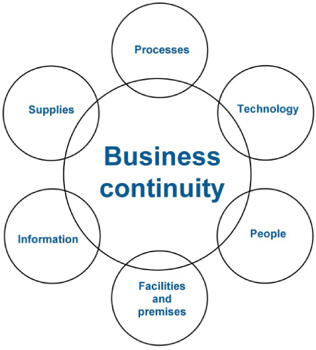
People
People are the core BCM objective and ensuring their protection and continuity is not an easy thing to build in and establish. The strategies and RTPs for the people component should serve four main goals:
- protection of their safety and well-being;
- minimizing threats and risks arising from people and staff;
- ensuring their availability as appropriate for recovery and continuity;
- maintaining sufficient levels of core knowledge, skills, and competencies throughout recovery and continuity phases.
To achieve these goals, there are suggested continuity strategies:
- Maintain sufficient and distributed documentation of critical processes, procedures, and activities.
- Implement multi-skill and knowledge transfer activities and training programs.
- Implement succession planning and job rotation programs for critical people working in critical processes and activities.
- Maintain an inventory of qualified contractors ready to join the organization. You may want to consider using recruiting agencies or headhunters to help you.
- Implement talent management to minimize talent and skill concentration in one group or in one location.
- Consider outsourcing some of your critical processes to an external party while maintaining sufficient controls and measures to protect the organization against relevant risks.
The RTPs should focus on the following techniques:
- strictly implementing health and safety processes;
- maintaining strict information security controls for people and staff.
Premises
Strategies and RTPs focusing on premises ideally concentrate on scenarios resulting in the non-usability of the sites and locations of the organization.
The most common approach for BCM strategies for premises is the use of alternative locations if disasters or incidents occur. There are, however, other BCM strategies that may be useful to the organization such as:
- using alternative locations provided by professional hosting service providers;
- having reciprocal agreements with other organizations that share an industry, geography, or infrastructure;
- using remote working solutions (whether from home or other locations);
- using ad-hoc locations as required in times of disaster;
- outsourcing disrupted services to professional providers.
There are several points that need an extra degree of focus and attention. The first of these is that when selecting alternative locations, the risks and threats that surround the primary location should be minimized as much as possible in the alternative one. Some of the preferable features that alternative locations should have are as follows:
- They are sufficiently distant from primary locations.
- They have ease of access and use.
- They are easy to activate and deactivate.
- They can accommodate extra staff and workloads.
- They have minimized risks by nature.
- They possess sufficient infrastructure.
The definition of each of the above features is left to the organization and how much they are willing to invest in their alternative locations. Alternative locations may be left unused except for times of testing and invocation or may be locations that are already active and in use.
The second point is that when selecting professional hosting service providers, extra care should be given to the contractual terms covering the type and length of use, invocation, testing, and security, and the privacy issues of both parties and the information situated at those sites. The same concepts apply for reciprocal agreements.
As for the RTP focusing on premises, the range of options should focus on:
- implementing strict physical security and environmental preparations to protect the facilities and premises from incidents and disruptions;
- considering extra protection measures in terms of insurance and maintaining sufficient coverage for protecting facilities and premises.
Technology
Technology plays a very important role in an organization, where it is now considered the backbone of operations and information usage. When designing and selecting BCM strategies to deal with technology, the restricting factors are:
- continuity specifications (RTO, RPO, criticality, recovery requirements);
- candidate locations to host technology services;
- distance between technology locations;
- connectivity readiness and deployment;
- capability to outsource technology infrastructure and services to professional service providers.
The selected BCM strategies list can contain:
- deploying redundant infrastructure, systems, and technology services at different locations either inside the organization or externally by utilizing professional hosting service providers;
- preparing locations for providing technology services while deploying and activating technology services at times of disaster.
The selected strategy should be flexible enough for update and enhancement due to the evolving nature of technology in terms of complexity and advancement.
There’s a chapter later in the book dedicated to the technological aspects of BCM.
The RTPs covering technology are highly integrated with the continuity strategy as they should focus on introducing more resilience to technology. Resilience means the ability and capability of the organization to recover from incidents in a rapid manner without the organization being affected.
The integration between BCM and information security is highly visible in this context. Most of the RTPs handling technology are within the domain of information security where the above-mentioned four main requirements are met in a cost-effective and practical manner.
Information
Information is the lifeblood of an organization. Interactions of the various types of information define many of the organizational components. Strategies selected for information should satisfy four main requirements:
- Confidentiality: Services and information should be available only to relevant stakeholders.
- Integrity: Relevant services and information should be reliable, consistent, and meaningful as required.
- Availability: Services and information should be available to relevant stakeholders when needed without significant, unacceptable delays.
- Currency or freshness: Services and information should be up to date and current as required by the stakeholders.
The strategies should also cover all types of information: electronic and hard copy:
- Hard copies: Consider using document management and archiving solutions for keeping electronic copies of originals. You may also want to distribute your vital records over multiple locations and sites. Some organizations dedicate specific sites and locations for the storage of documentation, filing, and archiving. You may want to make copies of those hard copies and store them off site.
- Electronic data: The most common strategy is using backup tapes and/or replication to redundant environments, on site and off site. The main inputs for this strategy are the RPO and retention policy, which contain the backup/replication and information storage policies.
RTPs for information are shared with the technology RTPs and are covered through a robust information security program. RTPs should meet the four main requirements mentioned earlier:
- Storage locations for hard copies and electronic data media should be protected against external and internal factors that can jeopardize the information for any of the four requirements.
- Tapes should be tested regularly to make sure they are usable and data residing on them is usable.
- Disposal of information should also be done in a way that protects the organization from unauthorized access to information.
Supplies
Organizations today exist in a world of interactions and interdependencies. An organization’s products serve as inputs and supplies to other organizations. Therefore, it is critical for an organization not only to look after its internal operations and environments, but also to consider its reliance on others to maintain its operations and environment.
The BCM strategies for supplies should focus on:
- maintaining additional levels of critical supplies at various locations;
- diversifying sources of critical supplies;
- developing contractual agreements with vendors for consistent, just-in-time deliveries of critical supplies.
RTPs for supplies should also cater for:
- regular delivery of critical supplies;
- making sure suppliers and vendors have validated business continuity plans or alternative procedures that are reliable and auditable;
- enforcing agreements and contracts with vendors and suppliers against bad performance, and poor delivery or non-delivery of supplies.
Stakeholders
Internal and external stakeholders are those who are linked to the organization and have an interest in it. They are consequently affected when disasters and incidents affect the organization. Different types of stakeholder require different needs to be met. It is difficult to identify the appropriate BCM strategies for all stakeholders. The main point here is to identify the organization’s key stakeholders, discover their requirements, and design your strategies to meet such requirements. In particular, stakeholders with special needs should be catered for with regard to their welfare and protection.
Once the strategies and RTPs are selected, the BCM owner and committee should sign them off in order to mandate other stakeholders within the organization to start implementation and execution of the selected set of strategies and RTPs.
Planning and implementation
Now that we have defined the continuity specifications for the organization and decided the strategy to follow to meet such specifications, we get into the phase of documenting the continuity plans and implementing selected strategies and RTPs.
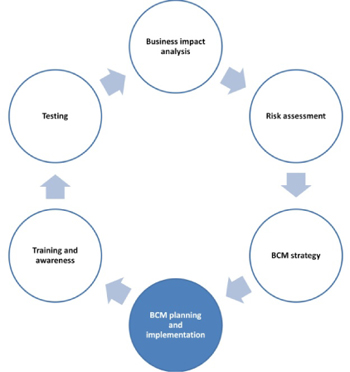
Starting with BCM planning, let’s consider the situation when a disaster hits. Most probably there will be some chaos. There might also be some haphazard decisions made that make the situation even worse. If we want to plan for managing disasters and crises, then we should be focusing on two main plans:
- The crisis management plan (CMP): The CMP should be a well-structured yet simple plan to allow the organization to manage the early stages of the disaster in the most appropriate way.
- The business continuity plan (BCP): Once the situation comes under control, a typical BCP would allow the organization to recover its functions, processes, and assets to be operational again. Furthermore, the BCP should allow the organization to fully recover itself to the status it had before the disaster occurrence.
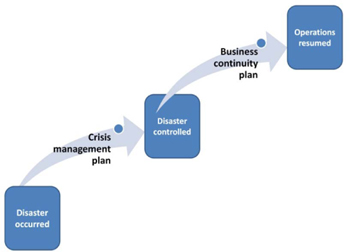
Figure 22: Crisis management plan and business continuity plan
Crisis management plan
The main purposes of the CMP are to:
- perform proper situation assessments;
- initiate communication channels with all required stakeholders;
- control the situation and limit the impacts.
The main features of the CMP are simplicity and effectiveness and it should meet the continuity specifications set earlier. The CMP should also be linkable to the BCPs that may be invoked in later stages.
There are two main approaches to follow when developing the organization’s CMP:
- The first approach is developing CMPs according to specific scenarios. The “scenario-based” CMP is fit only to handle those scenarios that it is created for. Thus its effectiveness is relatively limited.
- The second approach is developing CMPs according to impacts. CMPs that are based on impacts are highly effective in all situations sharing same impacts. Yet they require more maturity of the organization in defining the impacts of the disaster and selecting an appropriate CMP afterwards.
Contents of the crisis management plan
A typical CMP should contain the following sections:
- Purpose and scope: The plan should identify what services/processes/activities are included within the plan and their relevant continuity specifications.
- Roles and responsibilities: Specific responsibilities, roles, and authorities are documented within the plan.
- Invocation process: This describes how the plan will be invoked based on the situational assessment in the early stages of the disaster. The invocation of the plan may also include how people will be relocated and relevant logistics of such invocation and relocation.
- Document ownership and maintenance: The plan should identify the owner of the CMP, who is usually the BCM owner. It should also identify how the plan will be maintained through version control and record management processes.
- Contact information/emergency contacts: The plan should include all required contact information for the CMP to be effective.
- Tasks and actions: The plan should detail what tasks are to be performed and who will perform them. It should also identify the success criteria of those tasks and actions. In particular, people-related tasks are the most important of these. Since protecting people is the core objective of BCM, the CMP should have specific actions to protect, evacuate, and maintain the welfare and safety of the people.
- Internal and external communications and responses: The CMP should activate the communication channels, internally and externally. This part is vital for the success of the organization in managing disasters and crises.
- Command centers and locations: It is very probable that primary work locations will be unusable or unfit to work in at times of disaster. If this is the case, the CMP should identify the immediate alternative locations from which the organization will be managing the disaster and the crisis.
- Appendices: There might be some specific additional information required for effective management of the crisis. The CMP should include all the required information as it will be the main reference for the organization in time of disaster and crisis.
Business continuity plan
CMPs are for managing the disaster at the organization level. They are responsible for ensuring that the organization, as one entity, goes through the disaster safely and with minimum losses and impacts. CMPs provide the basis from which more specific plans are created and used.
BCPs, on the other hand, are those plans developed to recover specific functions, processes, activities, or assets from disasters and ensure they provide their services internally within the organization and externally to clients, vendors, and other stakeholders within acceptable levels and specifications. Within BCPs fall the IT disaster recovery plans (DRPs), which we will cover in more detail later in the book.
Contents of the BCP
A typical BCP’s contents should allow the recovery of specific functions according to approved continuity specifications. These contents include:
- Purpose and scope: The plan should identify what services/processes/activities are included within the plan and their relevant continuity specifications.
- Roles and responsibilities: Specific responsibilities, roles, and authorities are documented within the plan.
- Invocation process: This is how the plan will be invoked based on the situational assessment in the early stages of a disaster. The invocation of the plan may also include how people will be relocated and relevant logistics of such invocation and relocation.
- Document ownership and maintenance: The plan should identify the owner of the BCP, who is usually the process owner or department head. It should also identify how the plan will be maintained through version control and records management processes.
- Contact information/emergency contacts: The plan should include all required contact information for the BCP to be effective. These contacts may be internal ones within the organization or external ones like vendors, regulators, public authorities, insurers, etc.
- Tasks and actions: The plan should detail what tasks are to be performed and who will perform them. It should also identify the success criteria of those tasks and actions.
- Assets and resources required for recovery: The plan should identify the assets and resources required to perform successful recovery. These requirements are to be specified over time in order to cater for the logistics related to provision of these assets and resources. The assets/resources categories may include people, locations and workspaces, technology and networking, data and information relevant to the function, necessary supplies, and stakeholder communications.
- Restoration process: There should be detailed information on how to get back to normal conditions once the disaster situation ends.
- Appendices: There might be some specific additional information required for effective management of the crisis. Such additional information may cover the testing history of the plan, major results of the BIA and risk assessment, physical security aspects, and the maintenance procedure and history of the plan.
Awareness and training
We have now progressed a good way into the BCM life cycle, from initiating the life cycle to BIA, risk and threat assessment, BCM strategies and RTPs, and planning. Now we need to communicate all of this progress to the relevant stakeholders for the organization. This communication has two main processes:
- BCM awareness: BCM awareness creates an acceptable level of knowledge and understanding of the BCM program within the organization and is targeted towards all of the organization’s stakeholders.
- BCM training: The training stream aims to give specific skills and advanced knowledge to particular stakeholders related to the BCM plans. BCM training builds upon the awareness process as stakeholders need to be introduced to the program before advanced knowledge is transferred to them.
The BCM training and awareness processes start with the training needs analysis (TNA). Within the TNA, you can identify the existing level of BCM knowledge and skills within the organization. Once existing levels are defined, you need to define the desired levels of BCM knowledge and skills needed for the organization and how these will be delivered. As well as delivering BCM training and awareness, we need to measure the effectiveness of these processes. Useful tools for this may be:
- the number of employees and relevant stakeholders who attended the training and awareness programs;
- a review of the training and awareness material by peers or training professionals;
- a diversity of methods and tools to deliver training and awareness material;
- feedback, surveys, and comments received from recipients of the training and awareness material.
When delivering the training and awareness messages, make sure that the language used is relevant to the recipients’ levels of knowledge and interest. The methods used to deliver the training and awareness messages vary from one organization to another. Common methods may include:
- internal and external portals and websites;
- sessions and workshops;
- orientation and induction programs for new staff;
- electronic education solutions;
- e-mails and newsletters;
- contests and quizzes;
- tours and road shows for important BCM initiatives and projects.
Training and awareness programs should be consistent and continuous, without burdening the recipients or diluting the importance of the messages.
BCM awareness
As mentioned above, BCM awareness aims to create a sufficient level of knowledge across the organization relevant to the BCM program, its components, and deliverables. The BCM awareness process should trigger the organization stakeholders to:
- appreciate the need for BCM and the benefits that it brings for them and for the organization;
- know the form of the BCM program within the organization and its progress.
BCM training
The BCM training process builds advanced knowledge and skills within specific stakeholders to ensure that their contribution to the BCM program, both in normal business conditions and in disruptions, is up to the level required. The BCM training process splits into two main streams:
- BCM training for the BCM team: BCM life cycle, BCM program management, crisis management, and BCM technical issues.
- BCM training for other stakeholders: the training necessary for CMPs and BCPs.
Testing
The testing phase of the BCM life cycle aims mainly to validate the plans and documentation against recovery objectives and continuity specifications. There are, however, other goals that testing serves. Testing is a very good tool to leverage the awareness and training levels of the relevant stakeholders, since active participation and the iteration of tests and exercises instill good levels of knowledge and skills. It also increases the level of confidence in the BCM program both inside and outside the organization as people see that the plans they participated in developing are actually working and come into action when they are needed. Overall, improving the testing processes increases the level of BCM program maturity for the organization. Proven evidence of testing is now a regular internal and external audit area as well as a regulatory requirement.
There are some guidelines that the BCM professional should follow when developing the testing and exercising process. Certain types of test need careful planning as they themselves can turn into disasters to the organization. Every test should serve a certain goal and have a specific objective. Doing haphazard tests serves no one and will waste resources. They can easily make you lose support and momentum inside the organization for the BCM program.
The testing process
The BCM testing process starts with a testing plan. The testing plan is prepared at the beginning of each year and it identifies the scope, types, dates, resources, and objectives of all tests. At a minimum, the scope of the testing plan should cover the critical aspects of the organization at least once a year. Make sure to consult the BCM owner and committee, process owners, auditors, and other stakeholders when preparing the testing plan. The plan should be reviewed and approved by the BCM owner and committee.
Before the planned test date, the BCM professional should introduce the test to the participants and obtain their sign-off on the test scope, type, date and time, and steps.
After that, the tests are conducted and after execution the results reported to the BCM owner and committee with observations and recommendations.
Test types
BCM tests and exercises vary in terms of resource requirements and complexity:
- Desk check: The desk-check test is the simplest of the BCM tests. Its main aim is to make sure that the contents of the plans pass audit and challenge reviews.
- Walk-through: Walk-through tests incorporate different participants who are relevant to the plans being tested to make sure that all areas are covered within the plans and no gaps exist.
- Simulation: Simulation tests provide an environment similar to a disaster and put several plans into action to make sure plans that are linked to each other are working properly.
- Alternative site test: A partial or complete test of the alternative site defined in the plans may be done to ensure its readiness to be activated in disasters. This type of test includes relocation of people, activation of the site, invocation of the plan, and returning back to normal. It is important to make sure that no interruption to the normal business operations occurs during these tests.
- Full test: A full test activates all CMPs and BCPs that have been developed and demonstrates the capability of the organization to manage disasters. However, this type of testing is the most complicated and requires a high level of BCM maturity and planning to make sure that the test is doable. Usually, organizations bring in experts in crisis management and BCM testing when they do this type of test for the first few times until they possess the necessary knowledge, skills, and resources to implement such tests.
Rerunning the cycle
A BCM program is continuous and ongoing by nature. BCM is not a project; neither is it a set of templates and documents developed two years ago. The BCM life cycle is iterative by nature and the phases are rerun either periodically or when needed to keep the BCM program fit for purpose and relevant.
The need to rerun the BCM life cycle
Organizations are dynamic entities which are continuously in a state of change and evolution. The BCM program should be kept up to date, current, and relevant to the organization. Not doing this would jeopardize an organization’s readiness to manage disasters and can increase the probability and impact of threats facing the organization.
Triggers for rerunning the BCM life cycle
The BCM life cycle rerun is triggered by two types of triggers.
Time triggers
Most standards and best practices suggest reviewing the BCM life cycle phases and components at least once a year. Best practices suggest that critical aspects of the organization and their relevant documentation and preparations should be revisited twice or more a year.
Change triggers
There are triggers other than time for rerunning the BCM life cycle, such as:
- considerable staff turnover, especially for key staff;
- new products and services;
- considerable change in technology services and infrastructure;
- new locations and premises;
- considerable change in the organization’s strategy and direction;
- new regulations and laws affecting BCM;
- the occurrence of incidents or disasters.
Successful BCM programs incorporate both triggers for rerunning the BCM life cycle.
Nature of rerunning the BCM life cycle
Rerunning the BCM life cycle does not necessarily require the same resources and time required in the first run. The BCM manager and his/her team should plan the life cycle rerun carefully with the best utilization of resources and the achievement of the required goals.
We need to define the scope of rerunning the life cycle. This means defining the aspects to be reviewed and updated organizationally (departments, processes, etc.) and functionally (locations, technology, products and services, etc.).
Once the scope is defined, you need to plan for the rerun and get approval from the relevant stakeholders, including the BCM owner and committee, department heads, and process owners. The planning should be flexible in order to get the buy-in from them. Departments and process owners in particular have a lot more to do than updating the BCM life cycle. The rerun can be in a small area that only needs a work package or an agreed task list. It can also be a big rerun affecting a large part of the organization and so needs to be delivered through a dedicated project.
Once buy-ins and approvals are there, we can start the rerun activities. Periodic and as-needed reporting should be made available to the BCM owner and committee as well as relevant stakeholders. The result will be an up-to-date and current BCM program that effectively minimizes threats and manages disasters.