In this chapter we’ll explore more of some of the most essential components of quantum-based cryptography, including the grandparent of quantum key distribution protocols, the formidable BB84. You’ll see some familiar concepts and names, but you will probably also encounter several new ideas.
On Quantum Key Distribution (QKD)
We’ll now probe into some of the most important concepts related to quantum cryptography, including quantum key distribution (QKD). Do note that QKD is not the same as quantum encryption; it is instead a very effective auxiliary technique for securing keys/passwords. Current implementations of QKD are to be used in tandem with well-established classical algorithms, such as the AES.
A number of transmission protocols exist for QKD. We’ll next discuss some of these protocols in detail.
Let’s Go with Light
Quantum communications can be implemented using several varieties of quantum particles, including ions, atoms, and light (i.e., photons). Out of these, unit light tends to interact with matter to the smallest degree as photons are massless. This makes photons the optimal choice of transfer unit when it comes to tackling the issue of decoherence (as discussed in Chapter 10). Light, however, does sometimes disperse over time; a few of those important photons may never arrive at their intended destination. How these losses affect quantum communications is largely dependent on which protocol is being used (Scarani et al. 2009).
BB84
Developed all the way back in 1984 by Charles Bennett and Gilles Brassard, the BB84 was the first cryptographic protocol that allowed legitimate parties to detect eavesdropping during message transmission. It uses Heisenberg’s uncertainty principle, which as you might remember from Chapter 9 states that quantum-based data can’t be measured without disturbing it.
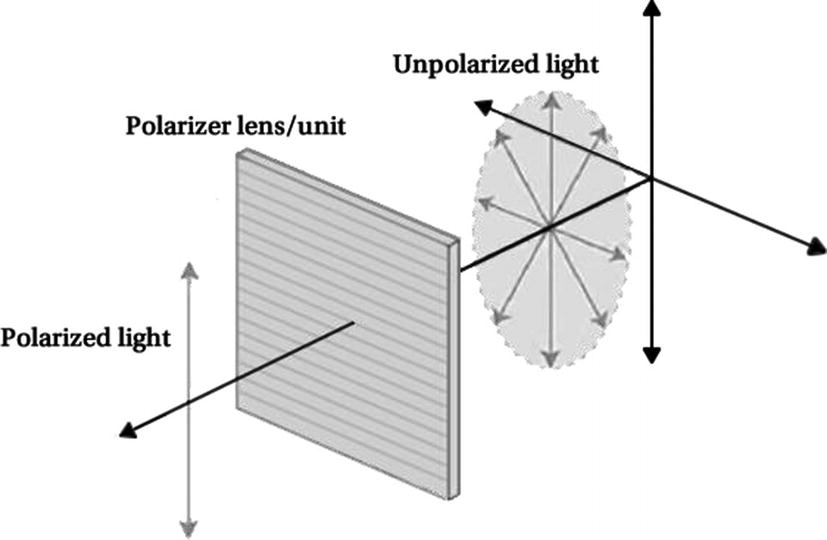
The oscillation patterns of photons can be altered using polarizer devices

Bits can be encoded in the polarization states of a photon in the BB84 protocol. The black arrows denote the rectilinear basis
A small sifted key. The plus sign denotes a rectilinear basis, while X refers to the diagonal one
Adramicia-Alphonsine’s bit | 1 | 1 | 0 | 0 | 0 | 1 | 1 | 1 |
Adramicia-Alphonsine’s basis | + | X | + | X | X | + | X | + |
Adramicia-Alphonsine’s polarization | 90° | 45° | 0° | 135° | 45° | 90° | 45° | 0° |
Biniyaamzawed’s basis | + | X | + | X | + | X | + | + |
Biniyaamzawed’s measurement | 90° | 45° | 90° | 135° | 90° | 45° | 0° | 0° |
Shared bits (i.e., the secret password/key) | 1 | 1 | 0 | 1 |
Key sifting is often performed on a more or less open channel such as the Internet. Although it might sound risky, malicious actors cannot often use sifting-related communications to gain information on any keys/passwords transmitted using QKD.
The no-cloning theorem (see Chapter 10) guarantees information can’t be duplicated in this realm. Also, any eavesdropping on channels using the BB84 protocol will result in an increased rate of quantum errors; this will let the legitimate parties know they are being spied upon.
B92
Developed by Charles Bennett of BB84 fame, the B92 is basically an optimized version of his previous protocol. Instead of four polarized states, the B92 offers just two (Ouchao, Jakimi 2018). Transmission of the basis (i.e., rectilinear or diagonal) used in the sifting stage is also not needed in B92. While easier to implement than the BB84, the newer protocol is thought to be less secure.
The Six-State Protocol (SSP)
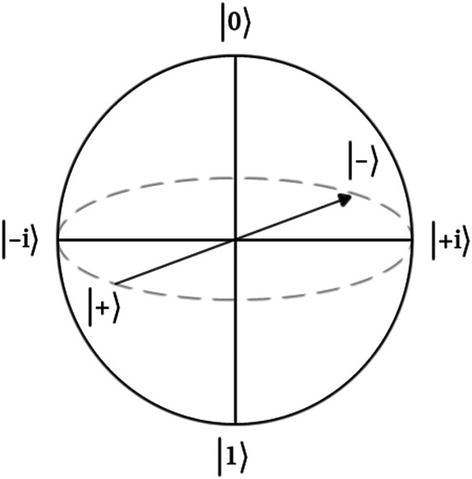
The three bases and six states of polarization of the SSP represented with a Bloch sphere
The Ekert Protocol (E91)
The Ekert protocol uses quantum entanglement with a central source between two parties to transmit messages simultaneously; a currently known practical source could be a satellite in orbit. The photons used in the protocol are entangled and assigned with randomized polarization.
The Einstein–Podolsky–Rosen paradox (EPR paradox) is a thought experiment devised in 1935 basically stating that quantum mechanics were in fact considered an incomplete paradigm. The quantum properties of entanglement and superposition in particular were thought to be in conflict with classical physics . The Ekert protocol actually provides a functional framework for putting the theoretical physics outlined in the EPR paradox into practice (Ilic 2007).
Continuous-Variable (CV) Protocols
The previously introduced protocols have been discrete variable in nature in which information is carried by single, or entangled, photons. A continuous-variable (CV) protocol is a different approach in which amplitudes, instead of individual photons, are measured. The photon counter units in discrete-variable protocols slow down the proceedings a tad and are not needed with continuous-variable protocols. Although generally faster during operation, CV protocols tend to produce more errors (Scarani et al. 2009).
Shor’s (Factoring) Algorithm
Some encryption schemes previously thought of as impenetrable are meeting their matches. One such scenario unfolded when Peter Shor’s factoring algorithm emerged in 1994, which is bad news for public-key cryptographic approaches such as the RSA. Shor’s algorithm was devised to discover prime factors of arbitrary numbers.
In practice, Shor’s algorithm consists of two phases; the first of which may be performed on a classical computer. In 2001 IBM built a seven-qubit quantum computer and with it successfully demonstrated the second part of Shor’s algorithm.
Now, are algorithms like the RSA in peril? Not really. For its 2048-bit variety at least, we would need a quantum computer of several hundred qubits to make the wait palatable. In addition, even if we managed to create such a computer, the issue of decoherence remains; as discussed in the previous chapter, qubits eventually lose their luster with their quantum properties. And we can forget about a classical supercomputer working on cracking the RSA with its several trillion year time frame.
Quantum Coin Flipping
Sometimes you can’t be sure that the receiving end of quantum communications is the intended one. Quantum coin flipping is a protocol for two parties who do not trust each other. The technique is being researched for secure authentication (i.e., fingerprinting) purposes as some stages in a typical QKD process involve nonsecure channels of communication. An approach where quantum coin flipping is executed after QKD is performed has been proposed; this would thwart most attempts at a man-in-the-middle attack (Rass et al. 2009).
In Closing
Which established protocols exist for quantum key distribution (QKD) , in particular the BB84 and the basics of its workings
What key sifting means
The significance of Shor’s algorithm and quantum coin flipping
In the next chapter we’ll delve much deeper into the fascinating theme of quantum-based cryptography. There are still many concepts left to unearth in quantum key distribution alone, for one.
References
B. Ouchao, A. Jakimi. International Journal of Advanced Engineering, Management and Science, June 2018. Performance Evaluation of Secure Key Distribution Based on the B92 Protocol.
Scarani, Bechmann-Pasquinucci et al. Rev.Mod.Phys. 81, 2009. The Security of Practical Quantum Key Distribution.
Ilic, Nikolina J. Phy 334, 2007. The Ekert Protocol.
S. Rass, P. Schartner, M. Greiler. 2009 IEEE International Conference on Communications. Quantum Coin-Flipping-Based Authentication.
