CHAPTER 19
How to Plan and Run a Risk Management Workshop
ROB QUAIL, BASc
Principal, Robert Quail Consulting
INTRODUCTION
The guidelines and advice in this chapter are based on the author's experience facilitating more than 250 risk workshops of various forms, with the number of participants ranging from 8 to 800. It is not intended to be a comprehensive guide to facilitation techniques, but assumes the reader has some basic understanding of how to facilitate a management meeting.
WHAT IS A RISK WORKSHOP?
A risk workshop is a structured, large-group conversation about future uncertainties.
- The workshop is structured to yield specific results. Therefore, there is a set agenda and a facilitator, whose responsibility is to ensure that the conversation takes a specific form aligned with the workshop's objectives. Depending on the ultimate purpose of the workshop, these desired results may include some mixture of learning, decision making, and commitment to action.
- The workshop involves a large group. Large, in this sense, means more than seven or eight participants—more people than could normally have a satisfactory, efficient conversation about a complex topic on their own in a single pass and achieve an effective outcome or result, without structured facilitation. On the other hand, groups of more than 25 participants can be unwieldy and difficult to manage. Therefore, it is best to keep an upper limit on the number of participants at about 25.
- The workshop is a conversation. The emphasis in a risk workshop is on enabling an open and frank discussion among people with knowledge or authority over the subject risks, and on encouraging contrary views and perspectives.
- The workshop is about the future. It concerns future events and uncertainty; it attempts to gather all the known, relevant facts, assumptions, suppositions, and uncertainties about a future set of events or situations, predict how those events or situations might affect the organization's shared goals, and predict how the organization would or should handle that scenario.
WHY USE WORKSHOPS?
It is tempting to think of workshops as merely a data-gathering exercise; after all, from the risk manager's perspective, the workshop provides access to a whole roomful of experts and decision makers for a specified period of time. It gets results much more quickly than data mining of similar scope, and certainly is much quicker than surveys or individual interviews. However, the benefits of risk management workshops go far beyond the convenience for the risk manager:
- Learning opportunity: A well-structured workshop allows participants to examine risks from a range of perspectives and learn from other experts and leaders. Participants will inevitably emerge from the workshop understanding their business better and with a heightened awareness of corporate objectives and the landscape of internal and external risk environments. If the workshop agenda includes discussions of current, committed, and contemplated mitigants, they will also gain a greater understanding of how other parts of the organization are managing the risks, and how these mitigants might fit together.
- Overcoming cognitive bias: Risk workshop techniques and processes require that participants break down elements of a risk or decision into discrete elements and apply established criteria in evaluating these elements. This can be helpful in reducing the effect of cognitive, statistical, and social biases that otherwise can interfere with effective decision making under uncertainty.
- Team building: Risk workshops are an excellent tool for promoting team building. A risk workshop provides a “safe” environment to share perspectives and ideas and ensures equal opportunity for participation. It is a great “get to know you” exercise for a recently established management team.
- Efficient use of time: Risk workshops can be an effective way for a management team to cover a large amount of ground very quickly. The focus on a defined agenda and use of facilitation techniques and risk management tools ensure that the discussion is targeted on the highest-priority issues.
- Risk management education: Risk workshops provide a “live” demonstration of risk management techniques and approaches. As such, they are an excellent vehicle for educating participants on the theory and application of risk management to specific business problems.
- Continuous improvement: Risk workshops provide the risk manager with an environment for continuously improving the quality of tools and techniques. By repeated exposure and use by managers from a variety of levels and backgrounds, a program of workshops will effectively validate such tools as risk tolerances and voting guides.
HOW TO CONDUCT A RISK WORKSHOP
The following sections provide a general approach for planning and executing a typical risk workshop. The entire process is depicted in Exhibit 19.1.
Preparation
A smoothly run and successful workshop that results in usable outcomes depends on adequate preparation; an effective workshop on risks is never the result of “winging it.” Regardless of the objectives and nature of the workshop, the greater the extent of preparation, the greater the likelihood there will be of a successful outcome.
Identify the Sponsor
Given the use of tools such as “anonymous” voting and facilitated discussion, a risk workshop has the appearance of being a democratic process. It is not. It is a consultation, conducted in the context of an organizational hierarchy, and should be conducted under the leadership of a specific decision maker. Therefore, all risk workshops must have an executive sponsor who is functionally accountable for the scope of the objectives and risks under discussion; someone who is “in charge”; someone who ultimately “owns” the risks. This person is not normally the risk manager. The role of the sponsor for a risk workshop is to set the context for the workshop, provide a view of their tolerance for risk taking, pass ultimate judgment on behalf of the broader organization and on the tolerability of risk exposures, and ultimately be able to present the results to those to whom the sponsor is accountable.
Exhibit 19.1 How to Conduct a Risk Workshop
| Step | |
|---|---|
| Workshop Preparation | Identify the sponsor |
| Set the workshop objectives | |
Set the scope:
| |
Assemble risk criteria:
| |
| Set the agenda | |
| Decide on attendees | |
| Assemble reference materials | |
| Arrange venue | |
| Workshop Execution | Facilitate the workshop For each risk:
|
| Record the results |
As described throughout the following sections, the sponsor will make decisions concerning the planning and design of the workshop, will play a critical role in setting the context and tone of the workshop itself, and will ultimately assume responsibility for the outputs of the workshop and ensuring that agreed-to actions are completed. Although the risk manager will do all the “heavy lifting” in terms of planning and executing the workshop, the sponsor will need to make key decisions before, during, and after the workshop, and together these decisions will be the ultimate determinant of the workshop's success.
Set the Objectives of the Workshop
It is imperative, in designing a risk workshop, that the facilitator gets a clear understanding of the sponsor's objectives for the workshop, as this will have implications for most other aspects of workshop design. A useful model for understanding these objectives is illustrated in Exhibit 19.2.
The vertical axis of this figure represents the desired discipline of the workshop. Learning Discipline workshops, at the bottom of this scale, place the emphasis on discussion and casual discourse on the subject risk areas, to enhance individual and collective understanding of the risks, rather than driving toward decision making. The process is loosely defined, there is a lot of scheduled “slack” time in the agenda, and the facilitator is relatively hands-off in allowing the discussion to follow the apparent interest of the participants. Learning workshops are well suited to new problems and new risk areas, with relatively cohesive management teams and no real imperative for immediate decision making. Because workshops can be excellent team-building forums, they can also be well-suited to new teams, so long as the goals of the workshop do not include driving to immediate decision making on a specified list of risks and issues.
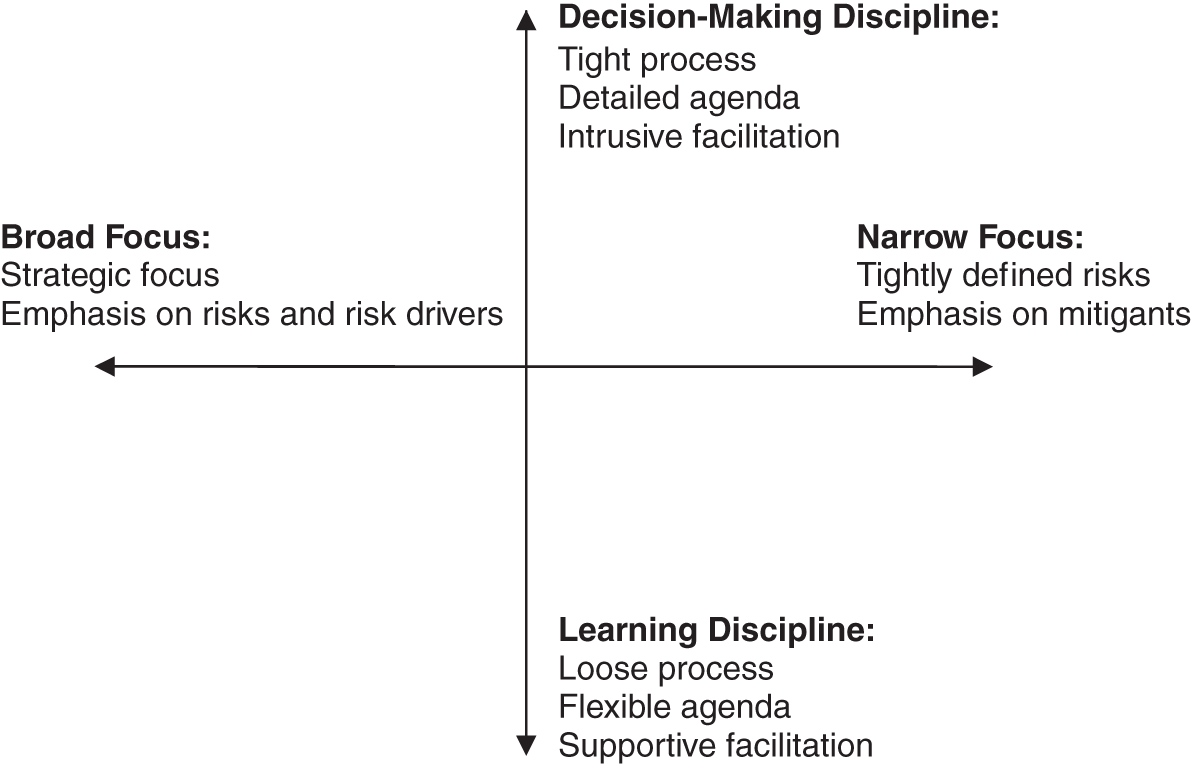
Exhibit 19.2 Setting Workshop Objectives
At the opposite extreme of the vertical axis, Decision-Making Discipline workshops are results-oriented. Decision-making workshops are, as the name implies, called for when a management team must make a decision immediately on the significance of risks and the adequacy of controls. A high degree of trust in the facilitator is required, because the facilitator will play a highly intrusive role in managing the discussions. The agenda is highly prescriptive right down to the minute, the process is highly scripted, and the facilitator keeps the process strictly on-topic and on-schedule.
The horizontal axis of Exhibit 19.2 depicts the focus of the workshop. Broad Focus risk workshops explore arrays or groups of risks at the strategic level. The emphasis is on identifying, understanding, and measuring risks, rather than evaluating the adequacy of mitigants, as the high-level depiction of risks may not lend itself to the discrete evaluation of mitigants to the point where a judgment of adequacy is possible. The agenda of these workshops will allow for greater understanding of the risk environment and the interplay of internal and external factors on the risks. Such workshops are useful for executive teams at the start of a strategic planning exercise. They are also useful at the commencement of large projects or programs (the so-called “storming” stage).
At the opposite end of the horizontal scale in Exhibit 19.2, Narrow Focus risk workshops are targeted at risks that are defined and understood to a high degree of specificity. Such workshops will normally make use of performance or other indicator data and may require the participation of functional or technical experts. Narrow focus workshops also allow for a greater emphasis on the evaluation of controls and mitigants for each risk. These workshops are best suited for technical groups and detailed planning exercises, such as annual departmental business planning.
Note that the choice of workshop type is not an either-or decision. The facilitator must get an understanding of where among these four extremes the sponsor's requirements lie. This can be gleaned by asking questions such as:
- How essential is it that we get through all of the risks on the agenda?
- Do you expect that decisions will be made in the room?
- What is the participants' level of understanding of the risks that are on the agenda? How important is it to you that they understand them all?
- Do you need to develop a detailed understanding of specific elements of these risks and how we are mitigating them, or are you looking for more of a high level of understanding of the risks as a suite?
- What is the level of trust and cohesiveness of this group?
Set the Scope
The scope of the risk workshop will consist of three elements: (1) the organizational objectives, (2) the risk universe, and (3) the time horizon.
- Organizational Objectives. Specifying the organizational objectives is an important activity because it helps define the scope of the session, it will assist in clarifying which risks will be selected for detailed scrutiny during the workshop, and it forms the basis of reference materials to be used by participants in evaluating risk magnitude. What are the stated objectives of the broader organization, and, more specifically, the objectives or results for which the sponsor is accountable? Depending on the emphasis on formal objective setting in the organization, these may be readily obtained (for example, from a Balanced Scorecard or some other formal statement of goals) or may need to be articulated as a step in workshop preparation. Objectives might be defined in areas such as financial results, reputation, customer relationship, operational efficiency, corporate stewardship, safety, and so on.
- Risk Universe. The risks selected for discussion at a workshop should be drawn from a broader “risk universe.” The facilitator should help the sponsor select the list of risks in the “universe” that are relevant to the sponsor's organizational objectives and known to be of possible concern. A risk may be selected for the universe because either it is considered to be a serious threat to one or more of the organizational objectives, or because it is the responsibility of the sponsor to mitigate that risk on behalf of the broader organization.
- Time Horizon. The sponsor and facilitator set a limit for how far into the future the workshop will look in examining risks. The horizon will be a function of the scope of the organization (more senior-level workshops will tend to have longer horizons), the timeline of the organizational objectives (if the objectives are expressed relative to a specific time horizon, that might be a useful reference point), and the volatility of the business (if the business environment is extremely uncertain, then looking forward more than a few years may not yield very reliable results). Ordinarily, risk workshops will have a horizon of somewhere between two and five years.
Assemble Risk Criteria
In order to have an efficient workshop and ensure that risks are assessed in a manner consistent with the overall risk appetite and tolerance of the broader organization, relevant risk criteria, of the type described in ISO 31000:2018, are essential.
- Impact Scale. An essential tool for any risk workshop is a set of common criteria that participants will use to gauge the potential impact of the risk. Impact should always be expressed relative to the organizational objectives. Thus, an impact scale will consist of a matrix very much like the one depicted in Exhibit 19.3, with the objectives listed down the left-hand column and a range of potential outcomes laid out under a numerical scale that represents varying degrees of deviation from expected goals or targets. Experience has shown that a 1–5 scale provides enough gradations for most workshops. In the example shown in Exhibit 19.3, the scales are calibrated such that events with a worst-credible impact of less than 3—Major are generally tolerable, and events with a worst-credible impact of 3—Major or greater may be intolerable.
Exhibit 19.3 Sample Impact Scale
Objective
Attribute
Event5
Catastrophic4
Severe3
Major2
Moderate1
MinorFinancial Net Income Net income shortfall (in one year, after tax) >$100M $50M–$100M $25M–$50M $5M–$25M <$5M Creditworthiness Change in financial ratios or risk Event of default; unable to raise any capital due to credit rating Credit rating downgrade to below “investment grade”; unable to raise required amount of capital Credit rating downgrade Put on credit “watch” Credit-rating agencies and bondholders express concern Reputation Public profile Negative media or opinion-leader attention Negative national media attention; opinion leaders nearly unanimous in criticism Regional negative media attention; many opinion leaders publicly critical Significant negative local media attention; customers publicly critical Letter to board of directors and CEO Letter to member of management Employee confidence Employee dissatisfaction Widespread departures of key staff with scarce skills or knowledge Sharp, sustained drop in employee survey results; departures of key staff Sharp decline in employee survey results Moderate decline in employee survey results Less than planned improvement in employee survey results Competitiveness Unit-cost reduction Failure to reduce unit costs Unit labor costs increase by > 15% Unit labor costs increase by 10–15% Unit labor costs increase by 5–10% Unit labor costs increase by 3–5% Unit labor costs not reduced Work program accomplishment Work program shortfall > 50% of critical projects late; or <50% of total work programs completed > 3 critical projects late; or 50–69% of total work programs completed 2 or 3 critical projects late; or 70–84% of total work programs completed 1 critical project late; or 85–94% of total work programs completed No critical projects late; or >95% of total work programs completed Safety and environment Employee availability and safety Employee injury Employee fatality or major permanent disability Employee critical injury Deterioration in safety targets No improvement in safety targets Less than planned improvement in safety record Environmental performance Adverse environmental impact Widespread offsite impacts (e.g., regional or municipal water supply) Multiple local offsite impacts (e.g., multiple residential properties or private water supplies) Significant local offsite impact (e.g., a public thoroughfare) Minor local offsite impact (e.g., a single residential property or private water supply) Minor impact on our property only - Strength of Mitigants Scale. One step in the process is to allow participants to express their degree of confidence in the mitigants and internal controls in place or committed to manage the risk. Once again, a 1–5 scale provides a reasonable degree of granularity. A sample Mitigants Strength scale (in this case with a strong emphasis on internal controls) is shown in Exhibit 19.4.
- Probability Scale. Participants will also need a reference to allow consistent ratings of probabilities. Again, a 1–5 scale is recommended, with the midpoint representing a 50/50 chance of occurring at least once over the workshop time horizon. An example is shown in Exhibit 19.5.
Set the Agenda
Once the objectives and criteria for the workshop have been set, the next task is to set the agenda. An obvious question is how much time is available and how many risks can be covered in the available time? There are no hard-and-fast rules, but as general guidelines:
- An entire day of risk discussions can be exhausting, and after working through eight or so risks, the process will start to seem stilted and formulaic to the participants. Allow adequate time for breaks and do not try to extend a risk workshop beyond eight hours in total. Half-day workshops are more likely to yield a positive experience for participants, even if it means breaking up the workshop over two or more days. Remember, a risk workshop should seem to participants like a stimulating and efficient conversation, not drudgery.
- For a typical workshop with a reasonable balance between learning and decision-making objectives, 30 minutes per risk is the minimum time that should be allotted.
- Some extra time should be allowed for the first few risks until the participants get familiar with the workshop process and tools.
The method for choosing (from the risk universe) the risks for discussion is another decision that is primarily up to the sponsor. Alternatives include:
- The sponsor chooses the risks alone. Although this approach is simple and quickly done, it does not allow consultation beyond whatever awareness of the risk profile the sponsor has already. This may cause key or emerging risks to go undiscussed.
Exhibit 19.4 Sample “Strength of Mitigants” Scale
Score Rating Description 5 Full controls; prescriptive; senior management/CEO oversight Full controls established (see “Full Controls” description), plus: - Objectives, policies, plans, and measures all formally approved by senior management/CEO and clearly documented.
- Authorities, responsibilities, and accountabilities tightly defined.
- Formal coordination of decisions of different parts of the organization through steering committees or other mechanisms.
- Prescriptive/detailed procedures exist.
- Close, frequent monitoring of performance; results are reported regularly to senior management/CEO and required improvements are closely followed up.
- Overall controls are subject to formal and/or independent review.
4 Full controls All elements are fully implemented and complete. 3 Substantial controls Only one or two elements are missing or incomplete. 2 Partial controls A significant number of elements are missing or incomplete. 1 Few controls Almost no elements are in place. Full Controls consist of: Purpose - Business objectives are communicated to all levels.
- Policies are established and communicated so that people understand expectations.
- Plans have been established and communicated.
- Measurable performance targets have been set.
- Risks are understood and accepted on a cost-benefit basis.
Commitment - Authorities, responsibilities, and accountabilities have been established.
Capability - People have necessary knowledge and skills.
- People have necessary resources and tools, including appropriate computer systems and data.
- Adequate, timely communication and coordination are in place to allow people to perform their responsibilities.
- Control activities, such as procedures, are in place and appropriately scaled to risk.
Monitoring and learning - Performance is monitored against targets; assumptions are challenged periodically.
- Follow-up takes place to ensure effective change.
- Overall control is periodically assessed
Exhibit 19.5 Sample Likelihood Scale.
Score Rating Probability in Planning Period (5 years) Expectation of Event Frequency (in years) 5 Very Likely > 95% >1 in 2 4 Likely 75% 1 in 4 3 Even Odds 50% 1 in 10 2 Unlikely 25% 1 in 20 1 Remote < 5% <1 in 100 - Advance polling, using e-mail, interviews, and so on, to involve the participants in choosing the risks from the risk universe in advance of the workshop date. This approach has the principal advantage of broad involvement in the process and a sense of ownership in the agenda among participants. However, it can be more costly and requires considerably more lead time.
- The sponsor and facilitator together arrive at a “best-efforts” list of risks and the participants modify and choose from that list as an early item on the workshop agenda. Anonymous voting techniques may be employed to involve the group in the selection of the risks for discussion at the beginning of the workshop. This approach represents a reasonable compromise between the above approaches.
Decide on Attendees
For most risk workshops, as a general rule, the target number of active participants should range from about 8 to about 25. Smaller groups usually do not offer the variety of perspectives or require formalized facilitation of the type described in this chapter. Larger groups can be unwieldy and there are special challenges in controlling group dynamics and giving everyone a sense that they have had a reasonable amount of “air time.” Large groups can be accommodated but require additional detailed planning and more experienced facilitators; see the section “Tough Spots.”
The decision on who attends will ultimately be left to the sponsor. The list of attendees will depend on which risks are on the agenda for discussion, assuming these are known in advance: the attendee list should allow for full exploration of the risks on the agenda, and, if applicable, decision making on the actions to be taken. This means that the workshop should include functional or technical subject-matter experts and key management stakeholders and decision makers. Another useful rule is to ensure that any person or group that might reasonably be expected to carry an action item out of the workshop is represented.
Other considerations:
- If the workshop concerns the key risks to the success of a department or business unit within an organization, ensure that all the key groups within that unit are represented.
- If the workshop concerns key risks to a large project, in addition to the technical experts or “leads” for various facets of the project plan, ensure that the project management office or people in other key project governance roles (such as audit) are represented.
- If a purpose of the workshop is “team building,” this will be a factor in selecting attendees as well; excluding members of the “team” could have negative consequences on team cohesion and compromise “team building.” Consider inviting attendees from other organizations or companies, such as partners or service providers, where the objectives or mitigants are shared or jointly resourced.
To facilitate a risk workshop, the author recommends a two-person facilitation “team.” One person, the “facilitator,” will focus on running the meeting and guiding the discussion. The other person, the “record keeper,” will ensure that what is said or decided at the meeting is recorded. Although it is possible for the facilitator to assume both roles, experience has shown that the workshop can be run more efficiently and produce better documented results if there is a separate record keeper assisting the facilitator. Note: The record keeper role is not just a “recording” function. The record keeper must have the ability to listen to and understand the discussion and boil it all down to a few key points to be recorded and simultaneously displayed to participants.
Assemble Reference Materials
Often, especially for risk workshops with narrow focus and decision-making discipline, there may be a need to assemble background or reference materials on the risks to be discussed. This may include:
- Detailed definitions or descriptions of the risks, risk sources, or potential impacts
- Results of past risk assessments or studies
- Relevant reports such as audit reports
- Operational or other data
Depending on the amount of material included, it may be preferable to circulate these reference materials to workshop attendees for review beforehand.
Arrange Venue
Normally a U-shaped seating configuration is preferred as it allows for face-to-face contact, simultaneous reading of displayed materials, and a central position from which the facilitator can direct the discussion and keep everyone engaged. The ideal layout for the room will have two computers and two display screens set up at the front of the room where all participants can see them: one screen for displaying context information and/or voting results (assuming anonymous voting technology is used) and the other screen for recording the key discussion points. It is also useful to have one or more flipcharts for recording “parked items” and other “side” items that may come up but are not central to the agenda.
Often it can be helpful to hold the workshop away from the normal place of business, to avoid the temptation for people to return to their desks during breaks.
EXECUTION
Assuming the preparation is complete and thorough, the execution of the workshop is focused mostly on maintaining or controlling the discussion, properly recording what is said and decided, and reporting the results.
Facilitate the Workshop
The purpose of this section is to describe the basic elements common to most or all risk workshops, not to provide a detailed explanation of meeting facilitation techniques. More facilitation “tips and tricks” are provided in the next section. (Note: This section assumes the use of anonymous voting, which the author considers an essential tool for efficient risk workshop execution.)
Although the workshop will be customized based on its specific objectives and focus, each risk discussion will have the following components. For each risk:
- Introduce the risk. Ensure that all participants have a common understanding of what is meant by the subject risk.
In addition to a simple definition of the risk, an effective way to build a common understanding is to ask participants to briefly describe, as a simple “mini-scenario,” how this risk might come to pass; what triggering event or condition would signify that the risk has occurred; and what might credibly be experienced by the organization as a result. Sometimes this brainstorming technique of developing mini-scenarios is termed back-casting. Ask the group something like this question: “Imagine it is several years from now and this risk has come to pass in what you would consider to be the worst-credible way. What happened?”
Record and display the key discussion points. Have the group brainstorm several of these brief scenarios; record them all.
- Impact. Have the participants individually vote on what they regard to be the magnitude of the “worst credible” impact of the risk using the Risk Impact Scale.
Introduce the vote with an instruction like this: “Review the scenarios that have just been described, and decide in your own mind which of these represents a credible scenario that is the most harmful. Then decide which of the objectives is most threatened by this scenario and find a point on the Risk Impact Scale corresponding to that objective that most closely resembles this impact. The risk score associated with that impact will be your vote.”
The voting is followed by a conversation to explore the rationale behind responses and probe into the reasons behind diversity of opinion. To encourage a complete discussion, the facilitator should ask questions like, “Which objective did you feel was most threatened by this risk?” and “Please describe the mental journey you took in evaluating the risk and deciding how to vote.” The note taker should record the key perspectives of participants.
The primary objective of this discussion is not necessarily to force consensus on the impact of the risk (although this is of course preferable), but to ensure that all perspectives get communicated and are understood by all participants, especially the sponsor.
This portion of the workshop can involve one or more revotes and rounds of discussion. The facilitator should introduce a revote by saying something like: “Now we have heard a range of perspectives and arguments on the potential magnitude of this risk. Let's see how many of you have changed your minds as a result.” It may take multiple iterations of “vote—discuss—vote—discuss” to complete this part of the agenda. It is important to remember that the role of the facilitator is to get all views on the table and encourage constructive debate.
- Strength of Mitigants. Using the Strength of Mitigants Scale, have participants assign an overall rating to the current and committed mitigants of the risk. This can be introduced by saying, “Consider all the activities that you are aware of to prevent this risk from occurring or hurting our organization. Decide for yourself how complete this set of activities is, relative to the kinds of things described in the voting guide.” Once the vote is complete, the facilitator should then ask participants to share with the rest of the group the mitigants they were considering in their vote and describe and record the key strengths and gaps/weaknesses in current mitigants. If the discussion is lively and results in significant learning by participants, have a revote following the discussion.
- Probability. Using the Probability Scale, have participants assign a probability of the risk coming to pass with an impact as large as was assigned in the second step above, in light of their view of the likelihood of the initiating events or conditions and their degree of confidence in the mitigants. Discuss the results and accompanying rationale and, if necessary, revote if there was significant deviation on the initial vote.
- Tolerability. At this point the facilitator should summarize the results of the discussion, including the voted scores and the discussion notes. In consultation with participants, the sponsor should then declare whether in their view the current level of risk exposure is tolerable to the organization. If the answer is that the risk is tolerable, no more discussion is required. If the answer is that it is intolerable, then normally the group will review the control gaps identified during the “controls” discussion and identify focus areas for improvement to mitigate the risk down to a tolerable level and discuss and assign additional actions needed.
It is important that the discussion on actions not become too detailed, or it will derail the discussion and put the agenda at risk. The author has found it useful to categorize actions into two types:
- Quick hits, which are relatively simple, well understood actions that can be implemented with minimal resources and planning. Quick hits can be assigned to an individual to ensure they are done by a specific date.
- Big ideas, which are expressions of potential actions that require more thought and analysis. Big ideas are best assigned to a “Champion,” who will take responsibility for further evaluation and consultation and bring a more fully formed action plan back to the sponsor or group at a later, specified date for approval.
Record the Results
As mentioned in an earlier section, it is best to have a dedicated record keeper, recording what gets said and displaying it for all to see. This can be most conveniently done by typing key points into a computer and simultaneously projecting them on a screen so that all participants can refer to what was said and know that the key points are being properly recorded. The intent is not to record every word that gets said, but the highlights of the discussion in point form. Also, any decisions, conclusions, or actions need to be clearly noted. It is recommended that the record keeper prepare a template in advance (see Exhibit 19.6) that follows the workshop agenda. Throughout the workshop, the facilitator must keep an eye on the note-taking screen to ensure that the record keeper is able to keep up with the discussion and capture the key aspects of what is said.
Exhibit 19.6 Sample Record-Keeping Template
| Risk Title: Cyber-Breach | Risk Score: 2.80 | |
| Description: The risk of a cyber-breach involving or affecting customer operations | ||
| Scenarios: | ||
| ||
| Magnitude Discussion: | Score: 3.8 | |
| ||
| Controls Discussion: | Score: 3.5 | |
| Strengths: | Gaps: | |
|
| |
| Probability Discussion: | Score: 1.8 | |
| ||
| Tolerability (Yes or No) : No | ||
| Actions: | Champion | Due Date |
| Complete privacy audit | Joe Smith | Q4 2019 |
| Continue to verify compliance with OEB and internal requirements | Alf Jones | Q4 2020 |
Prepare the Final Report
One of the advantages of having a real-time record keeper is that a report of the workshop, showing the risk map and discussion points and actions, can be finalized and distributed to the sponsor and participants as required within a matter of hours. The report should include as a minimum:
- A graphical or tabular summary of the results of the workshop (e.g., a risk map), showing the results of the voting and the conclusions on which risks are considered tolerable or intolerable with current mitigants.
- A summary of committed actions, in a “who-what-by-when” format.
It is best to schedule a debrief meeting with the sponsor to walk through the highlights of the report and make sure they are clear on the next steps for following up on assigned actions.
TECHNIQUES FOR PLANNING AND FACILITATING EFFECTIVE RISK WORKSHOPS
The facilitator of a risk workshop is responsible for guiding the workshop participants through the process and ensuring effective and efficient discussions on the subject risks. This section provides some useful general advice and tips for workshop facilitators.
“Anonymous” Voting
The author has used so-called “anonymous” voting tools (wireless keypad transmitters and receivers) for more than 250 risk workshops over a 19-year period, to great effect. These systems allow the facilitator to pose a question, displayed for the group to see, along with a range of numerical responses (corresponding to the scales described in the previous section), and obtain and feed back to participants a quick, real-time poll of the views of participants. These systems have the following advantages:
- They ensure full participation. Every participant is forced to go through the mental exercise of thinking individually through the question posed by the facilitator and deciding for themselves on an appropriate response. This enables subsequent full participation in the discussion.
- They are efficient. In a matter of seconds, the entire room can get feedback on the views of all participants concerning the question being posed, and get an instant read of the degree of consensus or disagreement. If, in the initial round, there is a narrow distribution of votes, indicating that consensus already exists, this is a signal to the facilitator that the discussion can be short and merely focused on quickly obtaining the “reasons why.” This can save time in a tight agenda and leave more time for topics where there is a broader range of views.
- They stimulate discussion. The facilitator can probe for arguments supporting each response. If there is broad disagreement (shown by a broad distribution of votes), the facilitator can immediately probe into the reasons why for each and stimulate a healthy debate.
- They reduce the opportunity for individuals to dominate the discussion. In the absence of the voting tools, more senior people in the room can (often unwittingly) influence others' views and dominate the discussion. Several years ago, the author sat in on a two-day workshop where anonymous voting was not employed, and instead participants held up cards indicating their own vote. In this session, participants fell into a pattern of waiting to see how the “boss” voted before holding up their cards. Obviously, such a dynamic is not conducive to thorough discussion of all critical aspects of an issue on its own merits.
Note that there are alternatives to dedicated keypads and receivers to support group voting exercises, where participants enter their responses on laptop computers, tablets, or smartphones. While these systems are convenient, they have the principal disadvantage of allowing participants to be distracted by other things on their tablets, phones, or computers. Single-purpose keypads are useful facilitation tools specifically because they can only be used for one thing: voting on questions posed by a facilitator in the workshop (and not for checking e-mail, messages, the stock market, or the latest news).
Useful Facilitation Tips
What follows are some useful ideas to help ensure successful, stimulating risk workshops.
- Get permission. Ask the sponsor to communicate to all workshop attendees that the facilitator is being given authority over the meeting agenda and process, and that the facilitator will direct the conversation and can intervene to keep the discussions on track and moving forward.
- Inquire. Ask open-ended questions, such as “Why?” Ask participants to speak not just on behalf of themselves but what they think others might be thinking. Ask for the contrary view: “What are some of the arguments against this?” Ask for evidence: “How do you know?”
- Restate. Summarize or paraphrase what you have just heard. Summarize the key points and then ask someone to add to them or comment on them or contradict them.
- Provoke. State extreme views that you might have heard or imagined on the subject of discussion. Encourage healthy debate.
- Use silence. After asking a question that gets no immediate response, it is extremely tempting to fill the silence by talking more or restating the question. Don't. Wait through the silence. If you wait long enough, someone will speak.
- Get out of the way. If a good animated discussion starts to happen that is directly on topic, and there is available time, try to “blend in with the furniture.” Walk to the side of the room or sit down. Let them run with it. Wait for the discussion to peter out or drift off topic before again making your presence felt.
- Don't overexplain. The author's experience is that the more participation (and less explanation or lecturing) there is in a workshop agenda, the more engaged the participants will be. Avoid lengthy descriptions of the steps to be taken or the underlying theory. Tell them the bare bones of what they need to do for the next step in the process, and then let them learn by doing.
Tough Spots
- Nonparticipation. It is the author's opinion that the duty of the facilitator is to create the conditions for an open discussion, and the duty of the attendees at a workshop is to actually participate. Therefore, the author does not believe that the facilitator should go to greater lengths (beyond the provision of anonymous voting systems) to ensure that all attendees fulfill their duty to participate. That being said, if an attendee is not participating in the discussion, there are options to encourage that person to speak up, such as making a point of asking them by name for their viewpoint when there is a pause in the discussion. Care must be taken not to intervene in this fashion too often, however, or the facilitator will start to assume the “crutch” role of drawing out all silent attendees. It is better to make it clear at the start of the workshop that all attendees are expected to contribute to the best of their ability.
- Dominators. If a member is dominating the discussion, say, “Let's find out what other people think on this. Anyone else?” If the dominator is also the sponsor, the best approach is to call a brief recess and take the sponsor aside and discreetly coach them to withhold their views to allow them to gain the benefit of others' perspectives.
- Large groups. If you are successful in building enthusiasm for risk workshops, you may be asked to try to do something with a much larger group. (Note: The author's largest group was 800 participants.) Obviously, the goals in large group sessions are different than those for smaller groups. It is a practical impossibility to make everyone feel like a full participant in the entire discussion. Instead you may choose to have the discussion in subgroups, and then have each subgroup appoint a spokesperson to summarize the discussion and share it with the larger group. Or, if interactive discussion is not a key objective of the meeting you may use anonymous voting to gather the entire group's views on the risks or issues and then have “experts” or people in a position of authority stand up and provide commentary on or reactions to the voted results.
CONCLUSION
We have shown how to plan, organize, and facilitate a risk workshop. Risk workshops play a vital role in ERM by helping engage executive managers and staff in understanding the corporate objectives and the risks to achieving these within given tolerances. As such, not only do workshops help identify and address critical risks, they also provide excellent opportunities for participants to learn about organizational objectives, risks, and mitigants.
APPENDIX 19.A: FACILITATING ONLINE WORKSHOPS
Many organizations are increasingly moving toward virtual, online meetings, using videoconferencing resources rather than meeting in person. The COVID-19 pandemic accelerated this trend. Therefore, from time to time, risk workshops need to be held virtually. The purpose of this appendix is to provide general advice for facilitating online risk workshops.
The principal challenges in facilitating a workshop online lie in the difficulty of effectively monitoring and maintaining participant engagement throughout the session. In a physical meeting room, the facilitator can watch body language and look for visual cues that show attention, engagement, frustration, and so on, among attendees, and make adjustments; call on particular individuals, or adjust the pace and focus of the discussion. This becomes much more difficult in an online setting. Therefore, the following adjustments are recommended.
Shorter-Duration, More Narrowly Focused Workshops
Due to the difficulty in maintaining participant attention, and the tendency for the process in a virtual setting to devolve from a series of conversations among attendees to a mechanical routine, online workshops are best parsed into short meetings of one- or (at most) two-hour duration, perhaps exploring only one or two risks at a time. The facilitator should expect that the process for assessing each risk will take considerably longer than at an in-person workshop; between 50 and 100 percent longer would be a good planning assumption.
Fewer Attendees
Large groups quicky become unwieldy in a virtual session. Monitoring levels of participation and effectively directing the traffic of conversation in a large group are much more difficult online. For this reason, smaller groups are preferred.
As a rough rule of thumb, the ideal range in terms of number of workshop attendees should be cut by one-third: in the body of this chapter, the ideal range is given as 8 to 25, but for online workshops, a better range is 5 to 16 participants. Note that a tighter, more narrowly focused agenda per the previous point above may allow the attendee list to be reduced without losing out on access to subject-matter experts and stakeholders who might enrich the discussion.
Cameras-On
If possible, it is recommended that all attendees be instructed to leave their videocameras on for the duration of the discussion; the video image of each attendee is the only cue available to the facilitator on the level of engagement. Further, having all cameras on is more likely to support spontaneous participant-to-participant conversational dialogue.
Screen Use
As was mentioned earlier this chapter, in an in-person workshop, two screens are recommended: one screen for displaying context information and/or voting results (assuming anonymous voting technology is used) and the other for recording the key discussion points. This is not easily accomplished with most videoconferencing solutions. This necessitates frequent back-and-forth movement between context/voting screens and note taking. Some planning will be necessary to decide how to manage screen-sharing; it may be necessary for the note-taking facilitator to have full control of what is displayed, or for the two facilitators to pass control back and forth.
Facilitation Tools and Techniques
Some videoconferencing solutions have embedded participant-polling capability, but these normally do not include the ability to consolidate multiple votes, do calculations across results, or display tables of an entire workshop's results. However, there are browser-based audience-response tools that are suitable for risk workshops. Using these tools would normally require that participants have a separate browser window open on their computer, or use a second device such as a smartphone, in order to enter their votes.
Videoconferencing solutions often have features not available in in-person forums, such as chat capability, providing a second channel for participants to provide comments or ideas, and the ability to set up spontaneous breakout groups for subgroup exploration of topics. Many videoconferencing solutions also have whiteboard-sketch capability, which can take the place of flipcharts in the more conventional in-person workshop setting.
Most of the facilitation tips in the chapter still apply. One thing that is worth noting is the “use silence” suggestion; after asking a question that gets no immediate response, it is extremely tempting to fill the silence by talking more or restating the question. Don't. Wait through the silence. Note that this may be a longer silence than in an in-person workshop.
▪ ▪ ▪
Other than the above recommendations, virtual workshops are identical to in-person ones, including the importance of the sponsor, setting objectives, planning the agenda, the use of criteria, the recording of the discussion, and the basic process to be followed for each risk.
APPENDIX 19.B: “BLACK SWAN” WORKSHOPS
In his landmark 2007 book The Black Swan: The Impact of the Highly Improbable, Nassim Nicholas Taleb introduced the concept of the black swan. Simply put, a black swan is an event that is extreme in terms of its impact, seemed highly unlikely before its occurrence, but is often rationalized as foreseeable in hindsight. The book argues that extreme events such as these have had disproportionately high, sometimes transformational, impacts on history, society, and industry. Examples of black swan events include World War I, the terrorist attacks on the World Trade Center in New York on September 11, 2001, the emergence of the Internet, the fall of the Soviet Union, and the 2008 financial crisis.
One of the challenges for the risk manager in dealing with black swan events is that, because they are by definition individually unpredictable and unforeseen, they usually do not find their way onto traditional risk profiles, and do not lend themselves to impact-controls-likelihood evaluations in conventional risk workshops. However, black swans do occur and can and do have a huge impact on the ability for an organization to achieve its business objectives. Therefore, much can be learned by examining them, and the ability of the organization to detect and cope with them should they occur.
One way to deal with this challenge is to approach black swan workshops as a thought experiment. The objective of a black swan workshop is not to anticipate the most impactful, most likely events and plan for the mitigation of those occurrences, as is the case in a conventional risk workshop. Instead, it is to postulate examples or classifications of black swans, and then ask the following questions:
- How quickly would the event or this type of event occur? For example, a computer crash or electrical blackout can be instantaneous, whereas the effects of a shift in weather patterns could take much longer, even though the ultimate impact could be devastating.
- Could we cope with this type of event by detecting that the event has occurred or is occurring and taking steps to adapt to the new circumstance?
To aid in brainstorming imagined black swan events, it may be helpful to identify categories of black swan sources or types, using a taxonomy like the following:
- Technological (e.g., technology breakthrough, collapse of technology infrastructure)
- Environmental/weather/cosmic (e.g., unprecedented storm, solar event, earthquake)
- Security (e.g., novel terrorist attack)
- Local/political (e.g., local political unrest)
- Global/political (e.g., global conflict)
- Economic (e.g., major unexpected economic shock or crisis, or new competitive force)
Ahead of the workshop, compile a list of possible black swan events, and obtain executive input as to which they wish to discuss. Then, in a workshop setting, the management team can explore each chosen black swan by following the following steps:
- Black Swan Identification/Definition: Select and briefly define the imagined black swan event.
- Velocity Assessment: Semiquantitatively assess the potential speed of onset of the black swan, that is, the interval between the initiating event or condition (which is the point at which the risk becomes inevitable) and its peak impact on our objectives (see Exhibit 19.7).
Exhibit 19.7 Velocity Criteria
5 Instantaneous Less than 1 day 4 Immediate 1 day to 1 month 3 Rapid 1 month to 1 year 2 Gradual 1 to 5 years 1 Slow More than 5 years - Organizational Resilience Assessment: Semiquantitatively assess the organization's ability to detect and respond to the black swan event before and after the event, that is, the ability to detect and deploy (plans, organizations, structure) and the availability of resources (people, knowledge, liquidity, equipment, etc.) (see Exhibit 19.8).
- Lessons Learned/Actions: Decide whether the organization's resilience is adequate for black swan events of that type, or whether additional detection or response capability is required.
Just as was the case in conventional risk workshops, anonymous voting technology is recommended to elicit answers to steps 2 and 3 in the list above, using the same vote/discuss/revote process as described in the chapter. The results can be displayed on a velocity-versus-resilience graph for easy reference and comparison.
Black swan workshops do not replace conventional risk workshops. What they do is look at the risk-event-response capability of the organization with a different lens.
Note: At the time of writing of this chapter, the world is in the midst of responding to the COVID-19 pandemic. Whether this event is truly a black swan could be debatable, since pandemics do occur from time to time. But certainly, the impact on many countries, industries, and organizations has been extreme, and has tested their ability to understand the extent of the threat and be agile and responsive as events have unfolded. It would be prudent for many organizations to conduct a “lessons learned” exercise once these events, and other similar future major transformative occurrences, have concluded, to examine their resiliency in terms of dealing not just with pandemics, but with other such extreme events. A series of black swan workshops is an ideal process for this.
Exhibit 19.8 Resilience Criteria
| 5 | Immediate | Appropriate resources and plans are accessible or in place, are regularly tested, and could be deployed immediately. |
| 4 | Full | Resources are accessible or in place, and could be deployed with some effort. Responsibility for development of plans is clear. |
| 3 | Substantial | Resources are accessible for large aspects of the risk and its impact, but there are significant gaps, where we would have to organize ourselves, procure resources, and develop and deploy plans on the fly. |
| 2 | Partial | No resources exist for significant aspects of the risk or its impact; coping with the risk would take years of planning and resource redeployment. |
| 1 | Minimal | Plans and resources are unavailable. |
REFERENCE
- Taleb, Nassim Nicholas. 2007. The Black Swan: The Impact of the Highly Improbable. Random House.
ABOUT THE AUTHOR
Rob Quail, BASc (Industrial Engineering, University of Toronto) was part of the team that established the enterprise risk management processes, tools, and methodologies at Hydro One Networks Inc. that are widely regarded as best practice. He has successfully applied ERM methodologies to a broad range of business problems and challenges, including acquisitions, outsourcing, downsizing, large-scale IT projects, labor disruption, regulatory compliance management, major construction project management, strategic planning, and capital investment.
Rob has lectured on ERM techniques at the York University Schulich School of Business since 2010. In addition to his ERM roles, Rob has held key executive leadership roles in the areas of business technology, outsourcing, and customer service.
Today, Rob provides independent consulting services in enterprise risk management, business process and technology outsourcing, and customer care to clients in a variety of industry sectors, including energy, health care, technology, financial services, and government agencies.
