The correct answer is B. Standard Primary and Standard Secondary DNS zones are sometimes referred to as traditional DNS zone files. Both types are stored as text files on the DNS server’s hard drive. Active Directory–integrated zones and Standard Primary DNS zones are both read/write copies of the DNS zone; therefore, answers A and C are incorrect. Stub zones are read-only copies of a DNS zone that contain a subset of the records associated with that zone, but the scenario called for an entire copy of the zone data and interoperation of the DNS server and the zone with BIND-based DNS servers; therefore, answer C is incorrect.
The correct answer is C. An Active Directory–integrated zone is a type of DNS zone that allows for secure dynamic updates. Standard Primary and Standard Secondary DNS zones are sometimes referred to as traditional DNS zone files. Both types are stored as text files on the DNS server’s hard drive. These zone types do not allow for secure dynamic updates; therefore, answers A and B are incorrect. Stub zones are read-only copies of a DNS zone that contain a subset of the records associated with that zone. These zone types do not allow for secure dynamic updates; therefore, answer D is incorrect.
The correct answer is D. A DNS server configured with a stub zone is not authoritative for that zone. It identifies the DNS servers that are authoritative for the zone. Answers A and B are incorrect. These zone types are used to resolve all resource records within a zone. Answer C is incorrect because an Active-Directory integrated zone simply stores zone information within Active Directory.
The correct answer is D. The actual issue here is that no default gateway is configured for PSERVER1, so it has no way to communicate outside its own subnet, which makes answer D the best choice. The PING locahost command should return the result of 127.0.0.1. The subnet mask on the user’s workstation is fine, so this eliminates answer A, and answer B states that the default gateway on the user’s workstation is incorrect, when it’s actually missing, so this answer is not correct.
The correct answers are A and E. There is no way a workstation with an IP address of 199.254.15.35 can use a subnet mask of 255.255.255.240. Answer B is incorrect because the default gateway may be correct. It is the subnet mask that is not configured correctly. There is nothing wrong with the settings on PSERVER, so none of these selections is the correct answer; therefore, answers C, D, F, and G are incorrect.
The correct answer is D. The question stated that PSERVER1 is on the 10 network; that means its host ID should be 67.35.10 (with an IP address of 10.67.35.10). The question also mentioned that ROUTER1 has an IP address of 10.99.35.1. For these two systems to be on the same subnet, they both need to use the same subnet mask of 255.0.0.0. Although it might seem odd, the IP address of 10.67.35.10 using a subnet mask of 255.0.0.0 and a default gateway of 10.99.35.1 for PSERVER1 is fine. There are no incorrect settings on the workstation, and none of the other settings on PSERVER is incorrect; therefore, answers A, B, and C are incorrect.
The correct answers are A and D. Unless another mechanism is already installed to facilitate the connection, an RRAS server needs to be installed at the Hartford and Wallingford locations to secure the connection between the two locations. L2TP and IPSec are the only suitable protocols from the protocols listed; therefore, answers B and C are incorrect. Installing VPN servers does not secure all IP traffic between the Hartford and Wallingford locations; therefore, answers E and F are incorrect.
The correct answers are B, C, and E. The Microsoft L2TP/IPSec VPN client must be installed on systems running Windows 98, Windows Me, or Windows NT Workstation 4.0 because those legacy operating systems cannot support this client on their own. Windows 2000 supports these protocols. Implementing an L2TP and IPSec strategy running in Transport mode is necessary to set up secure traffic. The best way to implement it is by configuring a domain security policy instead of a local security policy. The security policy must also require security in order to meet the requirements of the scenario. Therefore, you should not use a policy that requests security.
The correct answers are B and F. The easiest way to configure and secure the IP traffic from the Hartford location to the remote office in Wallingford is to use the installed RRAS server and configure a local security policy to require security for all communications between them. Answer A is incorrect because you do not need to install the Microsoft L2TP/IPSec VPN client—the security association is made between the two RRAS servers, as this is the least amount of administrative effort. None of the other options completely addresses all the scenario’s needs and requirements better than these two choices; therefore, answers A, C, D, and E are incorrect.
The correct answer is E. Port 3389 must be opened for Remote Assistance traffic to be allowed through the Windows Firewall. Answer A is incorrect because port 25 is used for SMTP. Answer B is incorrect because port 110 is used for POP3. Answer C is incorrect because port 443 is used for HTTPs. Answer D is incorrect because port 993 is used for IMAPs (IMAP secure).
The correct answer is B. Using the Classless Inter-Domain Routing setup of 177.25.0.128/26 allows 6 bits of host addressing, which means 62 host addresses are available per subnet, so answer B is the only correct choice.
The correct answers are B and C. RIPv2 can use CIDR and VLSM. OSPF is a link-state protocol based on an algorithm that determines the shortest path between source and destination nodes on a routed network. OSPF is a better choice than either version of RIP when you are considering routing 17 hops between the farthest segments of a network. RIPv1 is difficult to deploy in larger environments because it supports the main classes of IP addresses only and cannot use CIDR or VLSM; therefore, answer A is incorrect. BGP uses TCP to send detected routing changes and updated router table information between gateway hosts on autonomous systems, such as gateway hosts on the Internet. The routing table contains a list of known routers, the IP addresses they can reach, and any cost metric associated with the routes; therefore, answer D is incorrect.
The correct answers are A and D. Bridges and switches operate at the Data Link layer (Layer 2 of the OSI model) and automatically forward all broadcast traffic received; therefore, Subnets 1 and 2 will be part of the same broadcast domain, making answer A correct. Although Layer 2 switches can be found at the borders of collision domains, they do not form a border of a broadcast domain. Because Layer 2 switches do form the borders of collision domains, Subnets 1 and 2 will be in different collision domains, making answer D correct. Because answers B and C state the opposite, they are incorrect.
The correct answer is C. You should execute the Tracert command from Computer A to a host on Subnet B. The results will indicate whether a router between the two subnets is not functioning. Answer A is incorrect. The default gateway for Subnet A is functioning because computers on this subnet can access resources on all other subnets, except Subnet F. Answer B is incorrect because reconfiguring the routing tables is at this point immature. Answer D is incorrect because the ARP cache is used to map NetBIOS names to IP addresses.
The correct answer is B. You should configure all client computers with the IP address of the WINS server. This can be done manually or using DHCP scope options. All client computers will then be able to resolve NetBIOS names using the WINS server. Answer A is incorrect because Windows 95 and Windows XP Professional both support WINS. Answer C is incorrect because BOOTP enabled routers affect whether or not a subnet requires a DHCP relay agent. Answer D is incorrect because WINS proxies are only required on those subnets that support non-WINS clients.
The correct answer is C. You must create static mappings for the UNIX servers. Without the Samba client installed, UNIX servers do not support WINS and can not register their names with a WINS server. Therefore, a static mapping must be created to allow WINS clients to resolve the NetBIOS names of the UNIX servers to IP addresses. Answers A and D are incorrect because these solutions will not facilitate name resolution of the UNIX servers. Answer B is incorrect. The UNIX servers do not support WINS and therefore can not register their names with a WINS server.
The correct answer is B. PPP logs provide control and error messages for a PPP connection and are one of the best resources available for troubleshooting PPP connectivity issues. When systems on your network are configured with RRAS enabled for network access by clients, you can use Windows Authentication or Windows Accounting to log authentication and accounting information for network access connections. This level of logging is in addition to any events recorded in the System log, but it does not give you the required information, so answer A is incorrect. The RRAS service supports logging authentication events and information for remote connections via the Remote Authentication Dial-In User Service (RADIUS) server when RADIUS authentication and accounting are enabled through the Internet Authentication Service. However, this does not give you the required information, so answer C is incorrect. You can use audit logging in Windows Server 2003 to monitor IPSec events to troubleshoot unsuccessful L2TP connections and IPSec encryption; therefore, answer D is incorrect.
The correct answer is D. You can use audit logging in Windows Server 2003 to monitor IPSec events to troubleshoot unsuccessful L2TP connections and IPSec encryption. When systems on your network are configured with RRAS enabled for network access by clients, you can use Windows Authentication or Windows Accounting to log authentication and accounting information for network access connections, but it does not give you the required information, so answer A is incorrect. PPP logs provide control and error messages for a PPP connection and are one of the best resources available for troubleshooting PPP connectivity issues, but they do not give you the required information, so answer B is incorrect. The RRAS service supports logging authentication events and information for remote connections via the RADIUS server when RADIUS authentication and accounting are enabled through the Internet Authentication Service, but it does not give you the information necessary, so answer C is incorrect.
The correct order is as follows:
B. Cache
F. WINS
C. Broadcast
A. LMHOSTS
E. HOSTS
D. DNS
When a client computer is configured to use the H-node type, it first checks the local NetBIOS name cache. If there is no mapping, the client will attempt to contact a WINS server followed by a broadcast. If these resolution methods fail, the client computer will check the LMHOSTS and HOSTS files, respectively. The last method the client computer will use is DNS.
The correct answer is B. The 003 Router option should always be configured at the scope level, if there are multiple subnets. Client computers will not be able to communicate outside their local subnet if the IP address of the default gateway is incorrect. Therefore, answers A, C, and D are incorrect.
The correct answer is B. The only correct choice is route delete 192.168.1.0 mask 255.255.255.0 203.11.4.225. Entering route delete -p 192.168.1.0 mask 255.255.255.0 203.11.4.225 throws an error; therefore, answer A is incorrect. Likewise, entering route delete -p 192.168.1.0/24 203.11.4.225 causes an error; therefore, answer C is incorrect. Entering route delete 192.168.1.0/24 203.11.4.225 deletes the persistent route from the external connection; therefore, answer D is incorrect.
The correct answer is A. You should implement the 80/20 rule between the DHCP servers. One DHCP server is configured with 80% of the IP address for the local subnet and 20% of the IP address for another subnet. If the local DHCP server is offline, IP addresses can be leased from the remote DHCP server. Answer B is incorrect because clustering will result in additional cost to purchase the specialized hardware. Answer C is incorrect because DHCP can not be used with Network Load Balancing. Answer D is incorrect because the routers are BOOTP enabled.
The correct answer is B. You should monitor network traffic to AppSRV using the Network Monitor tool. You can analyze the network traffic to see which client computer is causing the performance problem. Answer A is incorrect because the Performance console is used to monitor the performance of system components. The captured data will not provide the information required. Answer C is incorrect because Task Manager only provides basic network usage statistics. Answer D is incorrect. You can use the Computer Management console to identify the users who are connected to shares on the application server. However, it is not used to monitor network traffic.
The correct answer is B. By increasing the lease duration, clients will not have to renew their IP address leases with the DHCP server as often. Answer A is incorrect because although this would reduce the amount of DHCP traffic, it does not really address the problem at hand and decentralizes IP address administration. Answer C is incorrect because placing a second DHCP server on the network would provide load balancing but would not address the amount of traffic being generated. Answer D is incorrect because a DHCP Relay Agent is used to forward DHCP requests from one subnet to the DHCP server located on another subnet.
The correct answer is A. When your solution needs to allow client systems to resolve DNS queries as often as possible on a network with limited bandwidth and to make sure there is no single point of failure on this site for name resolution, your only option is installing two caching-only DNS servers locally. Forward-only DNS servers do not function if the external link to other DNS servers goes down. This is also true for nonrecursive DNS servers and conditional-forwarder DNS servers; therefore, answers B, C, and D are incorrect.
The correct answer is D. A conditional-forwarder DNS server forwards specific DNS queries according to the DNS domain name in the query. Because the question specified that client systems must always be able to resolve DNS queries for gunderville.com and have no single point of failure for name resolution, the best answer to this question is D. None of the other answers supplies the correct solution; therefore, answers A, B, and C are incorrect.
The correct answers are A, B, and E. Low-level security DNS deployments have little to no security configurations. They can be found in designs and deployments where an enterprise’s DNS infrastructure is fully exposed to the Internet and name resolution is performed by all DNS servers in the network. Often these DNS servers are configured with root hints pointing to root servers for the Internet, and all DNS servers have cache pollution prevention disabled. The DNS servers in a low-level security configuration have dynamic updating enabled on all DNS zones, and UDP and TCP port 53 traffic are allowed to pass at the network firewall. Only answers A, B, and E outline the parameters of a low-level security DNS deployment. All other options are for medium-level and high-level DNS security designs; therefore, answers C, D, F, and G are incorrect.
The correct answers are D, F, and G. A medium-level security configuration is usually deployed with security features that are available to the DNS service when servers are configured with Standard Primary DNS zones on member servers. This type of DNS configuration might have limited direct exposure to the Internet, so zone transfers are limited to only the servers listed in the name server (NS) resource records. The DNS servers can use other DNS servers as forwarders when they cannot resolve names locally, and proxy servers and gateways are used for name resolution for Internet systems. Dynamic updating is not configured for any DNS zones, and cache pollution prevention is enabled. Only answers D, F, and G outline the parameters of a medium-level security DNS deployment. All other options are for low-level and high-level DNS security designs; therefore, answers A, B, C, and E are incorrect.
The correct answers are B, C, and H. The usagunderville.com domain is not a child of gunderville.com because it is not part of the contiguous namespace. The usa_gunderville.com name uses a noncompliant underscore (_) character. The usa#1.gunderville.com name uses a # symbol, which is not RFC 1123 compliant. As defined in RFC 1123, you can use all uppercase letters (A–Z), lowercase letters (a–z), numbers (0–9), and the hyphen (-) for DNS namespaces on the Internet. The name u.s.a.gunderville.com is an acceptable child domain to gunderville.com; u would be a child of the s domain, which is a child of the a domain; therefore, answer A is incorrect. The names usa.internal.gunderville.com, usa.external.gunderville.com, usainternal.gunderville.com, u.s.a-one.gunderville.com, and usaone.gunderville.com all use RFC 1123–compliant characters and are part of the contiguous namespace, so they are correct.
The correct answer is D. Each site has two DNS servers for each DNS namespace. So, the Wallingford site has two DNS servers for gunderville.com, two DNS servers for usa.gunderville.com, and two DNS servers for connecticut.usa.gunderville.com—a total of six DNS servers in that site. Because there are six sites, there are 36 DNS servers total, making answers A, B, and C incorrect.
The correct answer is A. Each site has two DNS servers for each DNS namespace. So the Wallingford site has two DNS servers for gunderville.com, two DNS servers for usa.gunderville.com, and two DNS servers for connecticut.usa.gunderville.com—a total of six DNS servers in that site. Because there are six sites, there are 36 DNS servers total. There can be only one Standard Primary zone for any DNS namespace; there are three domain namespaces total, so answer A is the only correct answer.
The correct answer is D. Each site has two DNS servers for each DNS namespace. So, the Wallingford site has two DNS servers for gunderville.com, two DNS servers for usa.gunderville.com, and two DNS servers for connecticut.usa.gunderville.com—a total of six DNS servers in that site. Because there are six sites, there are 36 DNS servers total. There can be only one Standard Primary zone for any DNS namespace; there are three domain namespaces total, so there are three Standard Primary zones. That means the remaining 33 DNS servers have a total of 33 Standard Secondary DNS zones.
The correct answer is D. Each site has two DNS servers for each DNS namespace. So, the Wallingford site has two DNS servers for gunderville.com, two DNS servers for usa.gunderville.com, and two DNS servers for connecticut.usa.gunderville.com—a total of six DNS servers in that site. Because there are six sites, there are 36 DNS servers total.
There can be only one Standard Primary zone for any DNS namespace; there are three domain namespaces total, so there are three Standard Primary zones. That means the remaining 33 DNS servers have a total of 33 Standard Secondary DNS zones. All DNS servers store zone information. For gunderville.com, that means the Wallingford site has two DNS servers, the NH site has two DNS servers, the Connecticut site has two DNS servers, and the New England site has two DNS servers. The HQ site and the BU site for gunderville.com also have two DNS servers. Therefore, 12 DNS servers store zone information for gunderville.com, and one server is a Standard Primary DNS zone. That means 11 DNS servers are deployed across the sites with Standard Secondary DNS zones, so only answer D is correct.
The correct answer is D. Each site has two DNS servers for each DNS namespace. So the Wallingford site has two DNS servers for gunderville.com—a Windows Server 2003 DNS server and a BIND DNS server with a Standard Secondary zone. There are two DNS servers for usa.gunderville.com—a Windows Server 2003 DNS server and a BIND DNS server with a Standard Secondary zone. The connecticut.usa.gunderville.com domain has two DNS servers—a Windows Server 2003 DNS server and a BIND DNS server with a Standard Secondary zone. Therefore, this site has six DNS servers, three of which are Windows Server 2003 DNS servers with Active Directory–integrated zones and three BIND DNS servers with Standard Secondary zones. With six sites total, that means 18 DNS servers are running BIND and hosting Standard Secondary zones. Therefore, only answer D is correct.
The correct answers are A, C, and F. Both Standard Primary zones and Active Directory–integrated zones support standards outlined in the IETF specifications for domain namespaces. They also support incremental zone transfers and allow fault tolerance for name resolution, regardless of which DNS server fails, because Standard Secondary zones still resolve current DNS names if the Standard Primary DNS zone fails.
Only Active Directory–integrated DNS zones store zone information in Active Directory and allow read/write access to the DNS namespace for all DNS servers in a domain. Also, only Active Directory–integrated DNS zones allow fault tolerance for DNS updates, regardless of which DNS server fails, because these zones are multimaster copies of the zone information and can be updated on any DNS server. Answers B, D, and E are not examples of these features of Standard Primary zones and Active Directory–integrated zones.
The correct answers are A, B, and C. Standard dynamic updates of DNS consider only the client operating system and its innate ability to update DNS, not the client membership or lack thereof in the domain. Windows 98 and NT 4 systems cannot update DNS; the DHCP service needs to be enabled to perform this action. Windows 2000 Professional clients in the domain and the workgroup can update DNS dynamically, so answers D and E are incorrect. The same can be said for Windows XP clients, so answer F is incorrect.
The correct answer is A. The #pre directive defines which entries in the LMHOSTS file should be preloaded into the local NetBIOS name cache. Answer B is incorrect because the #include directive is used to specify another LMHOSTS file from which entries should be used. Answer C is incorrect because the #mh directive is used to add multiple entries for a multihomed computer. Answer D is incorrect because the #DOM directive is used to indicate that the record is for a domain controller.
The correct answers are A, B, and D. Dynamic updates require that DNS servers support that type of update. This support can be found in Windows Server 2003 DNS, Windows 2000 Server DNS, and BIND DNS version 8.2.1. Windows NT 4 DNS and BIND DNS version 4.9.7 servers do not support dynamic updates, so answers C and E are incorrect.
The correct answer is A. When clients are configured to use H-node, they contact a NetBIOS name server first. If the server does not respond, a local broadcast will be used to resolve the name. By configuring the 046 WINS/NBT Node Type on the DHCP server and setting the value to 8, client computers will be automatically configured to use H-node. Therefore, answers B, C, and D are incorrect.
The correct answer is E. UNIX servers do not use WINS for name resolution. Therefore, in order for the servers to resolve NetBIOS names, you must enable WINS lookup on the DNS servers. If the DNS servers can not resolve a query, they will then query a WINS server. Answer A and C are incorrect because DHCP servers can update host names, not NetBIOS names. The UNIX servers do not require their host names to be updated. This will not facilitate NetBIOS name resolution. Answer B is incorrect because a WINS Proxy Agent is used to facilitate NetBIOS name resolution for non-WINS clients in a subnetted network. The scenario does not indicate that multiple subnets exists. Answer D is incorrect because creating static mappings for the UNIX servers will not facilitate NetBIOS name resolution for these servers.
The correct answers are C and D. An iterative query is a DNS resolution query made from a client to a DNS server, in which the server returns the best answer possible based on its local cache or stored zone data. If the server performing the iterative query does not have an exact match for the name request, it returns an error message saying that the requested name cannot be found, or it supplies a pointer to an authoritative server in another level of the domain namespace or to the Internet to query an ISP DNS name server or the root DNS servers on the Internet. A recursive query is a DNS resolution query made from a client to a DNS server, in which the server assumes the full workload and responsibility for providing a complete answer to the query. The DNS server returns a name resolution to the client system, or returns a name not found error if the DNS server cannot locate the DNS server that is authoritative for the requested domain name or if a lookup timeout condition is met. Answers B and E describe different types of name resolution lookups.
The correct answer is D. You should configure conditional forwarding. This allows you to configure a DNS server to forward requests to specific DNS servers. In this case, DNS01 will forward all requests for hosts in zandri.com to the DNS server authoritative for the zone. Answer A is incorrect because a stub zone is used to identify which DNS servers are authoritative for a given zone. Answers B and D are incorrect. Neither of thses options will result in all requests for zandri.com being forwarded to a specific DNS server.
The correct answers are D, E, G, and H. To successfully configure your DNS servers so that they provide DNS resolutions and assume the full workload and responsibility for supplying complete answers to DNS queries, you must set up your DNS servers so that they perform recursive DNS lookups on behalf of DNS clients. You do not want any DNS servers in your enterprise (except for one designated DNS server, DNS1.gunderville.com) to contain any pointer information to root servers on the Internet, so you will need to remove root hints from DNS2.gunderville.com through DNS12.gunderville.com. Because all servers should forward DNS requests for Internet resources to the DNS1.gunderville.com DNS server, you must configure all DNS servers, DNS2.gunderville.com through DNS12.gunderville.com, as forwarders and configure them to forward to DNS1.gunderville.com. You must also allow only DNS1.gunderville.com to perform DNS queries from the internal network through the firewall to the Internet for DNS resolution. This configuration prevents client systems manually configured with IP addresses of other DNS servers on the Internet—for example, DNS servers that belong to an ISP—from being able to make DNS resolution requests to those Internet systems.
The correct answer is B. The zone transfer refresh interval on the Start of Authority (SOA) tab of the forward lookup zone is the best place to make changes if you want to adjust the time interval a secondary DNS server waits before querying for updated zone information. The default setting for the refresh interval is 15 minutes (900 seconds). When this threshold is met, the secondary DNS server requests a copy of the current SOA record and compares the serial number of the source server’s SOA record with the serial number in its own local SOA record. If they are different, the secondary DNS server requests a zone transfer from the primary DNS server to update its information. If the default setting is not sufficient, lower the value to initiate requests more often so that updates occur more frequently. The DNS information in this scenario is very dynamic, so you need to lower the refresh interval so that your DNS servers are updated more often. None of the other options offers a better solution.
The correct answer is E. The zone transfer expire interval is the best place to make changes if you want to adjust the amount of elapsed time that must occur before a secondary server stops responding to DNS queries because of failures for zone updates. After this threshold time has been exceeded, data in this replica of DNS information is assumed to be out of date because it has not been updated. The default value is 24 hours (86,400 seconds) and can be adjusted as necessary. If your environment is more sensitive to DNS changes and has a highly dynamic DNS configuration, you might need to shorten the expire interval so that these servers go offline sooner than 24 hours.
The correct answer is B. When you need to configure your DNS servers from communicating with other DNS servers to resolve queries outside your domain, you need to disable recursion on DNS servers. Configuring DNS servers as forwarders actually tells them which other DNS servers to communicate with. Updating root hints has the same result. Round-robin rotation has nothing to do with allowing or preventing the DNS server from communicating with other DNS servers to resolve queries outside the domain. Caching-only DNS servers are normally used to intentionally cache DNS lookup results gathered from other DNS servers.
The correct answers are C and D. In such a small environment, the best solution is to use LMHOSTS files and place them on all systems. Configuring DNS servers to resolve the WINS names does not work in this scenario because there is no NetBIOS (WINS) name resolution in place. You could configure one or both domain controllers with the additional role of a WINS server, but this method is not the simplest way to deploy a NetBIOS name resolution solution for your small Windows Server 2003 domain. Also, you need to consider the hardware of current domain controllers; they are already overloaded when you take their hardware configuration into account. In addition, no business growth is expected this year, and the number of clients and servers is almost always static.
The correct answers are B, C, and E. FTP runs on port 20 and 21. Because neither port is listed, clients will not be able to use this service or use LDAP, which runs on port 389. The other listed services would be allowed, as port filtering does not close out their default ports. DHCP on ports 67 and 68 would be permitted, as would HTTP and HTTPS traffic.
The correct answer is A. When the Password Must Meet Complexity Requirements policy is enabled, passwords must meet the minimum complexity requirements, such as being at least six characters long. Answer B is incorrect because when the minimum password length is set, the password needs to be at least the indicated number, not more than the indicated number. Answer C is incorrect because both policies can be linked at the domain level and not conflict with each other. Answer D is incorrect because computer policies do not conflict with user policies in this scenario.
The correct option to select is Enable Split Horizon Processing. Enabling this option prevents routing loops and ensures that any routes learned from a network are not sent as RIP announcements on the network. RIP v2 is prone to routing loops. When split-horizon is enabled, a router can not advertise a route on the same connection from which it was learned. This option is enabled by default in Microsoft Windows Server 2003.
The correct answers are A, B, and C. To configure the network to allow IP multicast traffic between the two locations, you need to create an IP-in-IP interface between the servers, assign the interface to the IGMP routing protocol, and run the interface in IGMP proxy mode. Multicasting is useful for point-to-multipoint delivery of information on a network. Multicast traffic hits only nodes that are specifically listening for it. IP multicast addresses are reserved and assigned from within the Class D address range of 224.0.0.0 through 239.255.255.255. IGMP is used to exchange membership status information between IP routers that support multicasting and members of multicast groups. IP-in-IP tunnels are often used for forwarding IP multicast traffic from one area of the intranet to another, across a portion of the intranet that does not support multicast forwarding or routing. IGMP router mode keeps track of multicast hosts on the network. IGMP proxy-mode interfaces are designed to work with IGMP router mode interfaces. The purpose of proxy mode is to connect the multicast router to a private network or the Internet.
The correct answers are A, D, and E. You open port 80 on the IIS server to allow HTTP traffic. You block port 119 on the IIS server, which denies newsgroup server traffic. You block port 110 on the IIS server, which denies POP3 traffic. You open port 25 on the IIS server to allow use of SMTP. You open port 443 on the IIS server, which allows secure HTTP connections. For this scenario, only answers A, D, and E describe the results of the actions taken if no default ports have been changed.
The correct answer is:
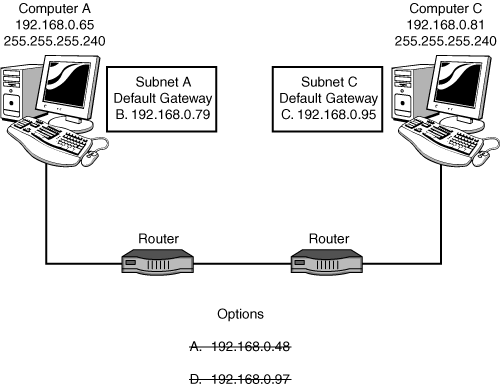
From the subnet masks shown in the exhibit, you can determine that subnetting is being used. Based on a subnet mask of 255.255.255.240, the valid subnet IDs are being incremented by 16. The six valid ranges of IP addresses per subnet are as follows:
192.168.0.16–192.168.0.31
192.168.0.32–192.168.0. 47
192.168.0.48–192.168.0.63
192.168.0.64–192.168.0.79
192.168.0.80–192.168.0.95
192.168.0.96–192.168.0.111
Computer A on subnet A is configured with an IP address of 192.168.0.64. Therefore, the default gateway must be an IP address in the range of 192.168.0.64–192.168.0.79. From the available IP addresses, you should choose the default gateway of 192.168.0.79.
Computer C on subnet C is configured with an IP address of 192.168.0.81. Therefore, the default gateway must be an IP address in the range of 192.168.0.80–192.168.0.95. From the available IP addresses, you should choose the default gateway of 192.168.0.95.
The correct answer is D. You should create a template using the Security Templates snap-in and configure the required settings. The template can be imported into a GPO that is linked to the OU containing the servers. This way all servers in the OU will be configured with the same settings. Answers A and B are incorrect because they require more administrative effort. Answer C is incorrect because the security settings will be applied to all computers in the domain. The settings should only be applied to the new servers.
The correct answers are B and C. By configuring the day and time restrictions, users can dial in during the weekdays. Because the RRAS server is configured with a range of IP addresses, all clients will lease an IP address when they establish a connection. Answer A is incorrect because you must configure the Windows Groups condition to limit access to a specific group of users. Answer D is incorrect. The RRAS server must be configured to use DHCP and the relay agent must be configured on the RRAS for clients to be assigned optional parameters.
The correct answers are B, C, and F. Because you have decided to deploy automated updates via the Windows Update site, using the Automatic Update client, the solution does not allow administrative approval of all updates before they are deployed to systems because clients simply download all available updates posted to the public Microsoft website. Although this solution allows you to schedule the installation of downloaded content, it cannot be used on all clients in your environment. For these reasons, answers A, D, and E are not correct.
The correct answers are B, C, F, and G. Because you have decided to deploy automated updates via the Windows Update site, using the Automatic Update client, the solution does not allow administrative approval of all updates before they are deployed to systems because clients simply download all available updates posted to the public Microsoft website. Although this solution does allow you to schedule the installation of downloaded content, it cannot be used on all clients in your environment. The clients allow downloading of the latest Windows operating system and IE service packs via the Windows Update site. For these reasons, answers A, D, E, and H are not correct.
The correct answers are A, C, E, and G. When your setup uses Tunnel mode, the two RRAS servers negotiate all security for the traffic, so the Microsoft L2TP/IPSec VPN client does not need to be installed on legacy systems. All IP traffic traveling from your network over an untrusted network will be secured and support all clients in the environment. Addressing requirements for header encryption, tunnel authentication, and encryption are met by using L2TP and IPSec, as L2TP can be used on IP, frame relay, X.25, or ATM-based networks.
The correct answers are C, D, E, and F. Usually when systems need to be manually configured, a shared secret is being used. Kerberos is usually the authentication method when all subject systems are members of the same Active Directory domain. A public key certificate is often used in Internet settings, such as e-commerce, or when computer systems are not members of the local domain. Public key certificates are also used with legacy systems that cannot use Kerberos or when you have customers using an extranet, as these systems are not normally domain members and have no way to use Kerberos.
The correct answers are B, D, and E. IPSec Transport mode authenticates and encrypts data flowing between any two computers running Windows 2000 Server or Windows Server 2003. It provides security for the network and can potentially support a secure connection with multiple computers at a time. Transport mode is the default IPSec mode.
Using IPSec in Tunnel mode authenticates and encrypts data flowing within an IP tunnel created between two routers. Windows 2000 Server and Window Server 2003 require RRAS to implement Tunnel mode for IPSec. You enable Tunnel mode in the IPSec Management console and configure Tunnel mode settings by supplying an IP address for each end of the tunnel. This encrypts all data sent between systems from one location to another via the two RRAS servers.
You need to provide a secure connection for all systems between your main office and your branch offices. This requirement has not been met because IPSec Transport mode does not cover all traffic from all systems. The solution also needs to be “always” available for all systems, but the NT 4 systems cannot use this solution.
Forcing all communications to “require” security encrypts all data transferred between all hosts. With this deployment, the NT 4 systems cannot communicate with other systems. “Request” security is less secure than “require” security because “request” security still allows unsecured network connections between systems. For those NT 4 systems to be able to use L2TP/IPSec, the Microsoft L2TP/IPSec VPN client needs to be installed.
