CHAPTER 7: DATA MANAGEMENT
“As a general rule the most successful man in life is the man who has the best information.” Benjamin Disraeli
Data Protection for Cutting Edge IT
At the end of the first half of 2012, there were 562,854,336 records disclosed to unauthorized parties from 3,190 reported incidents across all industries since the Choice Point incident in 2005. It is not unusual for an individual to have multiple records breached, multiple credit cards reset on account of fraud, and to have multiple offers of credit monitoring services. Thirty-seven percent of those records were because of:
- Unintended disclosure – Sensitive information posted publicly on a website, mishandled, or sent to the wrong party via e-mail, fax, or mail.
- Physical loss – Lost, discarded, or stolen non-electronic records, such as paper documents.
- Portable device – Lost, discarded, or stolen laptop, PDA, Smartphone, portable memory device, CD, hard drive, data tape, etc.
- Stationary device – Lost, discarded, or stolen stationary electronic device such as a computer or server not designed for mobility.
Fifty-six percent of these losses involved malware or hacking, that is electronic entry by an outside party, malware, and spyware. Less than one percent were on account of payment card fraud.
This is significant. It is evidence that the PCI DSS requirements are successful in decreasing the volume of fraud, evidence that controls do work. According to the website, the data chain, payment card fraud losses in 2010 reached their lowest levels since 2000. That is the good news. The bad news is that over 90 percent of the losses involved some combination of hacking through unprotected systems, unintended disclosures (mistakes), lost mobile devices, theft, or improper disposal of media. This is only the tip of the iceberg as it pertains only to those losses that are reportable under statutory requirements, and it only reflects the breaches that are actually discovered.
What the 90 percent problem is telling us, in part, is that the vast number of reported losses involves media that was not erased prior to release – improper disposal of electronic and paper records. It hints at mobile devices containing sensitive information that are easily lost and are not encrypted properly, and the ease of electronic transmission of files containing information that should have been removed, encrypted, or obfuscated. These are basic fundamental control issues across people, process, and technology aspects. The larger part of the loss is more difficult; it means that we are deploying or acquiring infrastructure and applications that are prone to malware and mobile software attack, that we continue to be vulnerable to “click and own” threats via poor browsing practices by users, and that our systems are improperly hardened against both insider and outsider attacks. This was nowhere more clear than with sophisticated breaches in 2010–2011. A few notable examples are included in the following table:
Table 1: Examples of security breaches
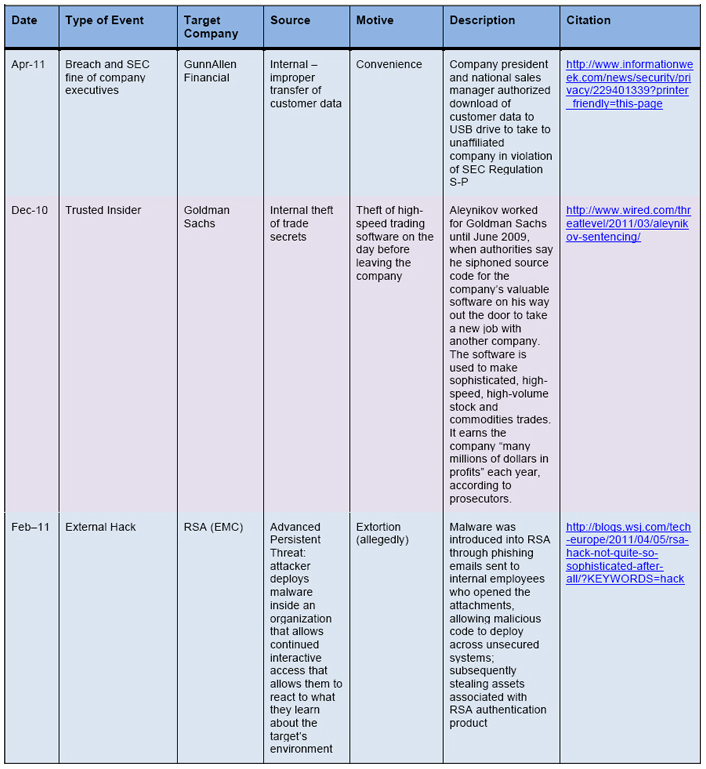

The adoption of cutting edge IT involves more and more third parties, and fewer “in-house” implementations. IT departments in some companies are becoming less technical and more focused on service management of third-party contracts and relationships. The accountability for preventing data loss of all kinds still rests with the contracting organization. Detailed responsibilities for control can only extend to the contractor from the contracting organization via contract. It is essential that the security organization and legal support work closely with supply chain management to ensure that end-to-end holistic processes and controls are in place at the service provider, and that these controls are auditable by the contracting organization or its designated representative. Such demands are likely to affect the cost of services delivered by the third party and could even be rejected by the third party, leaving the contracting organization unable to comply with baseline security policies ipso facto. The desire to adopt a particular vendor or technology can lead to negotiations and agreements with controls that are less than those required to address the exploding data loss problem.
There are three primary actions necessary for due diligence by an organization that is adopting cutting edge IT through third-party services, and two are relatively new to the IT controls catalog:
- Conduct a data inventory. Know where data stores are located logically and physically. Understand which data stores contain regulated or sensitive information, and understand how aggregations of data through data warehouses and mash ups can reveal knowledge that may be sensitive. Know where the access points are for end users to access data and how it can be downloaded, stored, and transmitted by end user action. Understand who is accountable for the data within the organization and how decisions about its usage are made.
- Draft IT control requirements for all third-party providers to be agreed to in the earliest stage of contract negotiations. Indicate which terms are non-negotiable (keep in mind the security hierarchy and attributes discussed in Chapter 6). Be sure to collaborate with the legal counsel that supports contract negotiation, and with supply chain management leadership. Build these controls, and the monitoring of them, into the cost model used for business case evaluation. Pay particular attention to controls that affect the 90 percent of breaches and that are difficult to monitor in third-party environments.
- Understand legal, regulatory, and statutory requirements affecting data. Translate these requirements into actionable controls that must be addressed, and assess gaps and remediation plans. An organization that adopts a control framework based on COBIT 5, ISO27001/2, ITIL®, and GAPP will meet most requirements, even in international settings. A particular concern will be trans-border data flow and the restrictions on sensitive information. Privacy professionals should be consulted on this to ensure the proper requirements are addressed.
