There are a number of tools specific to testing Web sites. These tools look for vulnerabilities in Common Gateway Interface (CGI) scripts and other exploitable files, or you can use them for brute force attacks against authentication mechanisms. Many automated vulnerability scanners (see Chapter 11) can also be used for testing Web sites. We do not cover these automated vulnerability scanners again in this chapter. Instead, here we cover some of the Web-testing tools we have found useful in our engagements.
In addition to these tools, you should gather as much information about the Web server as possible and perform research for vulnerabilities. You can use many of the Web sites covered in Chapter 22 to help perform this research. You should search for Web-hosting software, software versions, CGIs identified by Whisker and other tools, and any other applications found running on the target servers. Many times there are published vulnerabilities that affect these areas. Some even include the exploit code, which you can use to test the vulnerability. You could also locate the patch information and apply it. However, using untested exploit code during penetration testing is dangerous. The code could contain Trojan horses, back doors, or bugs, and you will probably not know exactly what the exploit will do to the server. Always run the code in a test environment before using it against production systems.
URL: www.wiretrip.net
Client OS: UNIX
Target OS: Web sites
Price: Free
Description: Whisker is a Perl-based CGI scanner. The tool examines a target Web site against a database of known vulnerabilities, which is essentially a script file. Whisker is highly configurable. You can modify or create new script files to customize the database for each particular scan. Whisker comes with a default scan.db file, which is quite comprehensive.
Whisker is a very fast scanner, but it can be difficult to use and interpret if you are not familiar with Perl or CGI. If you are not comfortable creating your own scan databases, Whisker's default database is still useful for checking for CGI scripts, command interpreters, password files, and other Web application vulnerabilities. Whisker also has options for evading detection by IDSs, using output directly from Nmap, and other handy functions.
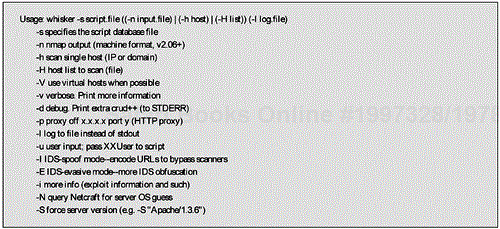
Use: Whisker requires a Perl interpreter to run. If you do not have a Perl interpreter on your system, you will need to install one. To use Whisker, simply execute it from the command line and give it the IP address or host name of the target Web server and a file containing the scan database. Whisker then searches the site for vulnerable CGI scripts and reports the names and locations of vulnerable files. The syntax and options that appear in Whisker's documentation are shown in Figure 17-1
Figure 17-2 contains a portion of Whisker output from a Whisker scan. As you can see, Whisker reports the location of a potentially vulnerable file but does not offer much amplifying information. If Whisker reports “OK,” it found the file, and you will have to perform some research to find out how to exploit it.
Benefits: Whisker is considered one of the best CGI vulnerability scanners available. It is highly customizable, and it is also free.
Cons: Whisker can be difficult to install, run, and interpret if you are not familiar with Perl or Web vulnerabilities. The tool does not offer much amplifying information other than whether or not the file is vulnerable. To find out how to repair or address the issue, you may need to perform some research on your own.
URL: www.hackers.com/html/archive.5.html
Client OS: Windows 9x/NT
Target OS: Web server
Price: Free
Description: Web servers have long been known to have more features than can be managed easily. SiteScan is a useful tool from Rhino9 for finding these exploitable features. It automates several exploits against Web servers. Although these attacks are a bit dated, it is surprising how many administrators fail to keep security patches up to date.
Use: SiteScan is easy to install and use. Figure 17-3 displays the SiteScan interface. Start by entering the IP address or URL for the target server in the Server window. Then simply click the button for the test you want to perform. The results of the test are displayed in the Results window. SiteScan includes options for checking for vulnerable test CGIs, service passwords, passwords embedded in HTML or Java code, vulnerable IIS admin, finger, and other weaknesses.
Benefits: The tool is easy to use and free. It automates many tests for Web servers.
Con: Many of the tests are dated and the servers may no longer be susceptible.
URL: www.pimmel.com/thcfiles.php3
Client OS: Windows NT
Target OS: Web servers
Price: Free
Description: This tool is currently in a beta version, but it promises to be useful for Web penetration testing. It automates many of the manual security testing functions and is scalable to large internal networks. Additionally, it looks for the pesky CGI scripts that often create holes in the system. It also performs banner grabbing. The tool has an easy-to-use GUI.
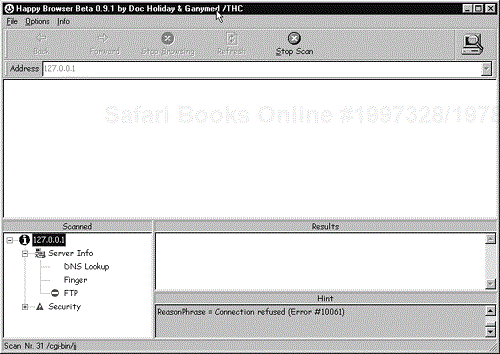
Use: THC Happy Browser is easy to use. Figure 17-4 displays the interface. Enter the IP address of the target server in the Address window and start the scan. The tool begins to collect the information from the scan and displays it in the Scanned window. Under the Server Info heading the tool lists DNS-related information, finger access, and FTP findings. The tool lists information concerning CGIs and other vulnerabilities under the Security heading. By expanding the Security group, you can see the checks the tool performed.
Benefits: THC Happy Browser is easy to use and performs many security checks for Web servers. The tool is also free.
Cons: The tool is not very configurable, and you cannot individually select the tests you want the tool to perform. In addition, it does not have regular updates for new vulnerabilities.
URL: www.packetstormsecurity.org
Client OS: Windows 9x/NT
Target OS: Web authentication
Price: Free
Description: wwwhack is a brute force tool for Web services authentication and other types of authenticated services such as FTP, POP3, and news servers. It cycles through a list of user names and passwords in an attempt to gain access. The tool comes with a default password file that can be modified for the particular site you are testing, or you can specify your own word lists. Be careful using this tool during penetration testing. If the Web site you are testing has account lockout enabled, you will probably lock out the accounts you test. In addition, if the site is logging failed login attempts or has intrusion detection in place, your activity will most likely be detected.
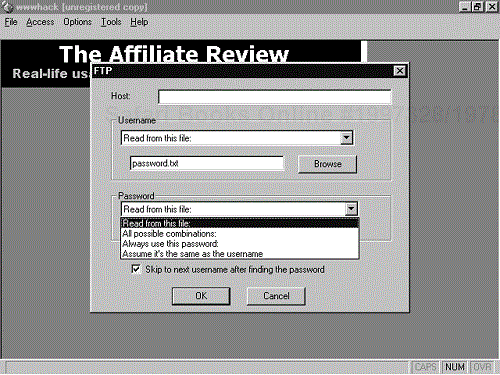
Use: After installing and launching wwwhack, use the Access menu to select the type of authentication you wish to test. Once you select the authentication type, another window appears in which you enter the host name or IP address of the target, the location of the user names for the test, and password options for the test. Specify the file that contains the user names for this test. Figure 17-5 shows the several options you can use for the passwords. You can either use the user name as the password or use a text file with passwords. Once you have entered this information, select OK and let the tool start cracking.
Benefits: The tool offers an easy way to try multiple user name and password combinations when testing Web security. Also, the tool is freeware.
Cons: You have to know a valid user name for the site, which may be difficult to obtain. Also, by using the tool you increase your chances of detection.
URL: www.packetstormsecurity.org
Client OS: Windows 9x/NT
Target OS: Web authentication
Price: Free
Description: Web Cracker is a brute force tool for Web authentication services. It is very fast because of its use of multithread processing, and it also has a nondefault URL format for testing certain types of sites that use CGI, ISAPI, and NSAPI scripts. Web Cracker uses a user ID and password file and goes one step further by translating the IDs and passwords into various forms, such as all upper- or lowercase letters. The tool also offers proxy server support.
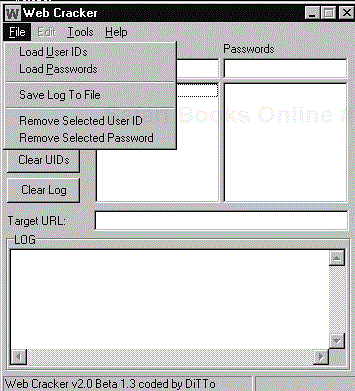
Use: The tool is simple to use. Once you have launched the interface, select Web Cracker Setup from the Tools menu. Figure 17-6 shows the Web Cracker Setup window where you set options for the user ID and password file such as case, whether to use the user ID as the password, and proxy settings. Once you have configured your settings, select the appropriate options from the File menu (see Figure 17-7 ) to load the user ID file and password file. Then simply click the Start button and the tool will start cracking.
Benefits: Web Cracker is a fast, effective brute force tool for HTTP basic authentication. In addition, the tool is free.
Con: The tool cannot support SSL authentication. You need to have some idea of the type of user IDs used for the site in order to be effective.
Client OS: Windows 9x/NT
Target OS: Authenticated services
Price: Free
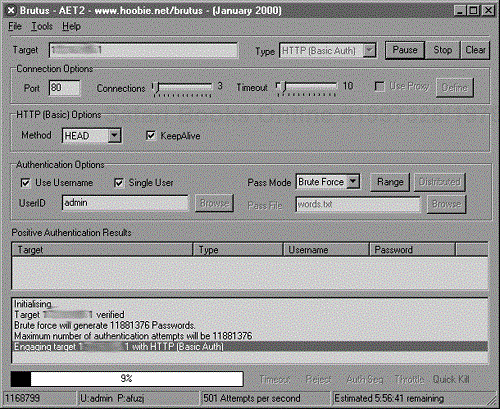
Description: Brutus is a brute force tool that can be used for HTTP authentication as well as other authenticated services such as FTP, telnet, POP3, and so on. You supply a user ID or IDs and a password file and launch the tool against the authentication server. The tool can perform multiple connections at the same time, and timeouts can be adjusted. As with other brute force tools, using it will set off IDSs if the target has them.
Use: Figure 17-8 displays Brutus's user interface. To use the tool, enter the target IP address in the Target window and select the type of authentication. The connections and timeouts can also be adjusted. Next, either supply a user name or a file containing a list of user names. Finally, specify a password file or select Brute Force in the Pass Mode window and start cracking.
Benefits: The tool provides an easy way to attempt to brute force different types of authentication mechanisms. It is easy to use and can use multiple connections to speed the operation.
Con: Brute force tools can be detected by IDSs and other monitoring systems if they are in use on the target.
On one engagement, we were given the client's IP address range and asked to attempt to penetrate the defenses. We started with the discovery phase and confirmed the client's IP address ranges and DNS information. Using Sam Spade (see Chapter 12) we performed whois queries on “client.com,” obtained DNS information, and confirmed the IP address range.
Next we used Pinger to identify live hosts within the IP address range. Pinger identified five hosts within the range. It appeared ICMP was allowed into the network, but we still used Nmap to perform a TCP ping using SYN packets just in case some hosts were not responding to ICMP. We used the following Nmap command for this purpose:
# nmap –PT80 ip_address_range
Nmap found only the same five hosts Pinger had identified.
Next we performed a stealth port scan against the five hosts using our list of favorite ports (we present this full list in Chapter 13). This list contains about 30 ports that either offer identifying information about the host or run a service that we can frequently use to compromise the system. By using a stealth port scan for just a few select ports, we improve our chances of avoiding detection. We used the following Nmap command:
# nmap -sS –O –p 7,21,23,25,80,135-139,2301 (etc.) IP_address_range
The Nmap results identified the systems as Windows NT systems. In addition to others, TCP port 2301 was open. We knew port 2301 supports the Compaq Insight Manager. We knew this service frequently contains vulnerabilities that enable us to compromise the host. (If we were not aware of the vulnerabilities we would have identified the service during our banner-grabbing step and identified the vulnerabilities through research.)
Such sites as www.packetstormsecurity.org, www.securityfocus.com, and others with vulnerability databases contain information concerning the Compaq vulnerabilities.
The Compaq Management Web Agent and the Compaq Survey Utility may be vulnerable to an access validation error. A remote user could exploit this vulnerability to access and download files. Compaq's Insight Manager is a management tool that can monitor and control the operation of Compaq clients. In order to communicate with its managed devices, it runs a Web server listening on TCP port 2301.
This particular version of Compaq Insight Manager was susceptible to a vulnerability that caused it to fail to check whether any requested files fell outside its document tree. This allowed attackers to retrieve files in the same drives as that on which the software resides if they knew the file name.
In addition, there are three default accounts (user name/password pairs) with access to the Insight Manager. These accounts are anonymous/(no password), user/public, and administrator/administrator. The first step we took to exploit this vulnerability was to attempt to log into the Compaq Insight Manager via a Web browser using the URL http://10.10.10.250:2301/cpqlogin.htm. This returned the login screen. We entered the default administrator user ID and password and were successful. The administrator had failed to change the default user ID and passwords. We frequently find these accounts still set to the defaults because system administrators may not even realize the service is installed.
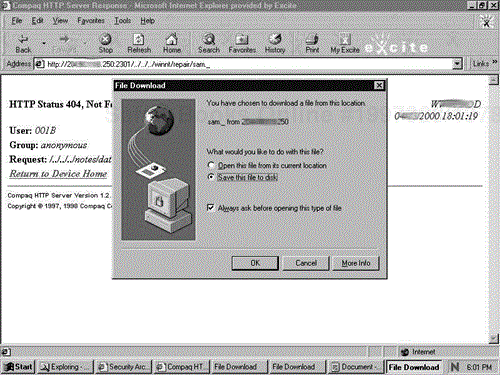
Next we attempted to access files on the system. We targeted the system's repair SAM database. We entered the URL http://10.10.10.250:2301/../../../winnt/repair/sam._ in the browser in an attempt to download the repair SAM file. The results are shown in Figure CS-1.
This successfully downloaded the SAM file to our machine. After downloading the SAM file, we used L0phtCrack to crack the passwords. Within an hour, L0phtCrack was able to crack the passwords for all three users in the SAM file, including that of the administrator's account. We had attained administrator-level access within a matter of hours.
Once we had accomplished this against one host, we could use Compaq's HTTP Auto-Discovery Device List (at http://10.10.10.250:2301/cpqdev.htm) to locate other vulnerable machines and further penetrate the client's network.
This was a fairly straightforward test. The basic steps are listed below.
Identify the target hosts.
Scan to find open ports.
Identify applications, servers, and so on that are running (based on the open ports).
Find exploits specific to those applications and servers.
Exploit.
This example illustrates the importance of knowing what services are running on your systems, changing all default passwords, and keeping up-to-date on all system patches. In addition, blocking all unnecessary ports and services at the firewall and border router would have prevented access to the vulnerability.