The easiest way to detect a SQL injection, and any vulnerability using Burp Suite, is through a scanner. To use a scanner, you do the following:
- Open Burp Suite to view the main Dashboard, as shown in the following screenshot. Note that this is only available in the Professional Edition; the Community Edition does not have Scanner as an option. If you use the Community Edition, then use the scanner included in ZAP Proxy (which can be found here: https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project):
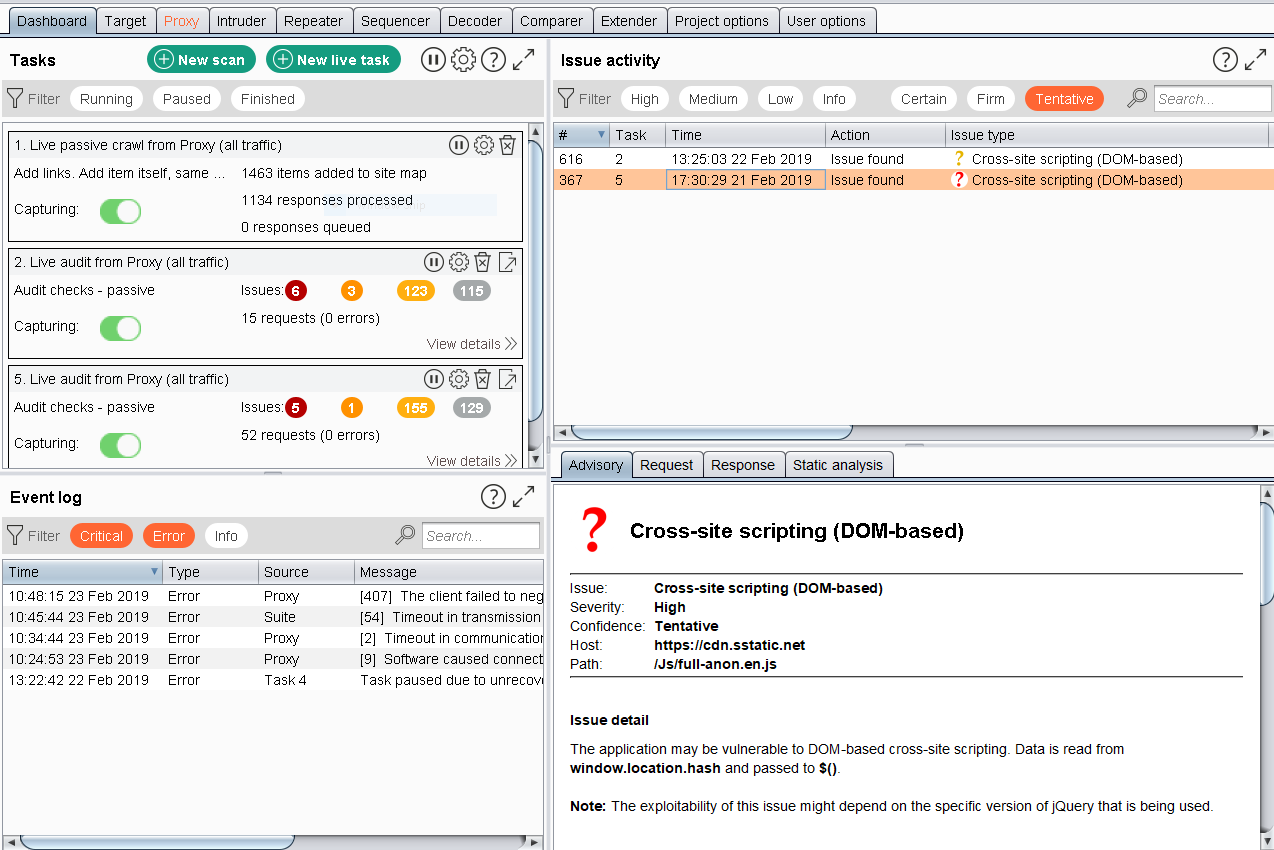
- In this screen, click on New scan. This button will launch the wizard to configure the scan; here, you can add all the URLs that you want to scan, limit the scope of the scan, set credentials for authenticated scans, and create specific tasks, such as filters. To perform an application scan, enter the URL you want to scan, as shown in the following screenshot:

- Next, click on Application Login and add credentials for the application. In this case, we add the user for the website, as demonstrated in the following screenshot:

- Click on the OK button and the scanner will start the detection, as shown in the following screenshot. Burp Suite will ask you whether it needs more information to perform the scan:

Now, let's move on to the next detection method, which is CO2 detection.
