In a large infrastructure environment, capturing, extracting, and storing data becomes a bottleneck at times. In such cases, we can use Moloch, which is a free, open source, large-scale packet-capturing system that allows us to draw intelligence while effectively managing and storing the data:

From the preceding screenshot, we can see various stats with respect to the source IP and destination. Expanding the first entry (192.168.0.109 -> 172.217.7,4), we can see plenty of detailed information:
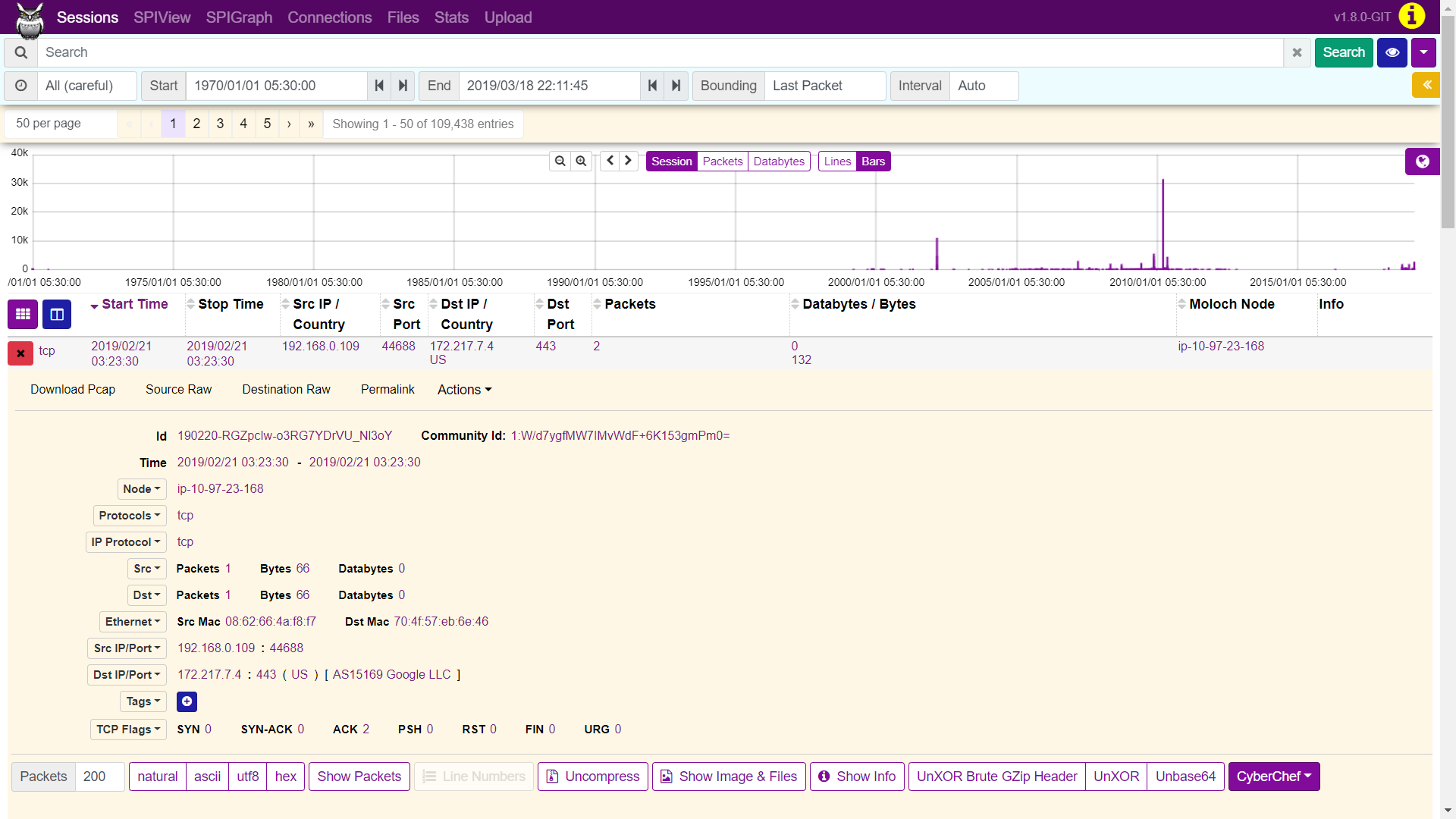
We can see we have a much wider view of the details now. Moloch also provides stateful packet inspection view and graph as shown in the following screenshot:

We can see that we have data in a segregated view of the protocol, which is DHCP in our case. We can select other protocols, such as DNS, from SPIView and can see the various details such as hosts, IP addresses resolved, ASN, and much more as shown in the following screenshot:

Next, let's see the SPIGraph that contains the source and destination nodes:

The connections graph gives us a nice view of the nodes and lists the source and destination IPs. We can see that we have chosen weight as packets so that links become thicker where large packets are transferred. Doing this, we will have a clear understanding of where most of the packets are flowing.
Covering all the features of Moloch is outside the scope of this book. I suggest that you install Moloch and work with it. Moloch can be downloaded from https://molo.ch/. Moloch is available to download in the binary format for CentOS 6 and 7, Ubuntu 14.04/16.04/18.04 LTS releases. The reason we covered Moloch as a part of network forensics is that most of you might be working in an environment where there is no, or limited, packet-capturing done. The idea of implementing Moloch is to reduce costs by implementing a cost-effective solution and to cut down on forensic investigations through third-party vendors. It is one tool that offers many features and next-level packet inspection. Hence, it helps in-house forensic investigators and incident responders.
More information on tools, plugins, scripts, and dissectors for Wireshark can be found at https://wiki.wireshark.org/Tools.
Tools for malware analysis on the network end can be found at https://github.com/rshipp/awesome-malware-analysis#network.
For tools related to wireless forensics, check out https://github.com/nipunjaswal/Wireless-forensics-framework.
