Threat Type: Connection based, software based
Examples of Threats:
Unauthorized access to your home network or a computer on your home network through your Internet connection
Unauthorized installation of software programs onto a computer or device on your home network
Unauthorized access by a computer or software program to the Internet, exchanging unintended information
Using compromised computers on your home network as anonymous sources for launching attacks on others
Our Tips:
Install a stateful-packet-inspection firewall between your broadband Internet connection and home network.
Install personal firewall software on each of the computers in your home network.
Periodically monitor access logs and firewall rules to ensure continued protection.
The term firewall is borrowed from the construction industry, where a hardened fire-proof material, such as cinder block, is built between two sections of a building so that if one catches on fire, the other might not.
A firewall in computer terms provides similar protection, by shielding one part of a network (say, your home network) from another part (say, the Internet) that may be “on fire.” Now, the Internet is not exactly in flames, but it is a “dirty” network, meaning few rules and regulations apply, and those that do exist are often circumvented by some folks. You can view the Internet kind of like the Wild West of networks.
Firewalls are one of the most important lines of defense you need for your home network. You may ask yourself, “Why are firewalls so important? After all, I have been using the Internet for years with a dialup connection and never needed one before.”
The answer is simple. If you only have to go into a bad part of town occasionally, maybe you can just be careful. If you have to live in that part of town all the time, it is probably wise to lock the doors and carry some type of protection.
With high-speed broadband service, your Internet connection is always on, meaning as long as your broadband modem is connected to your home network and it is powered on, your home network and all the computers on it have a connection to the Internet. You are no longer just visiting the bad side of town; with broadband, you are now living there.
Unchecked, hackers, bored or mischievous neighbors (or their kids), or just other people with too much time on their hands can try to access your home network through your broadband connection from anywhere in the world. Broadband also provides hackers with high-speed connections to do a lot more hacking. Once hacked, you cannot undo what you may lose, such as personal data, access to financial accounts, and so on. So, the only real option is to prevent yourself from being hacked in the first place.
Firewalls provide a means to block unwanted visitors from gaining access to your home network, the computers on it, and the information those computers contain.
Why would someone want to access your home network? Well, for a lot of reasons, ranging from simple theft of the information on your computers to hijacking your computers and using the anonymity they can provide to conduct other illegal activities. It is impossible to list here all the examples, but let’s consider two common ones.
First, most people regularly store information, such as e-mail, spreadsheets, and even passwords to online accounts (eBay and PayPal, for example) on their computers. Figure 1-1 shows how a hacker can launch what is called a brute-force attack to gain access to one of your computers. Tools to perform such attacks, which are easily available on the Internet, use dictionary files to repeatedly attempt to guess your password to remotely log in to your computer or to access a shared drive.
If left unchecked, hackers can attempt thousands of times until they succeed. When into the computer, they can simply help themselves to whatever information you have stored there.
In the second example, it is not the information itself on the computers the hacker is interested in, but enlisting your computer (probably along with hundreds or thousands of others) into what is called a bot army. Bot armies are when a hacker has taken over control of many computers and then uses the computers for illicit means, such as to attack other computers or corporate websites. Figure 1-2 shows an example of using a bot army to conduct a distributed denial-of-service (DDoS) attack.
By exploiting a security flaw in the computer’s operating system, hackers can install a small program to take remote control of your computer. After doing so on hundreds or thousands of other computers, hackers can then go after their target with a DDoS attack by instructing all the remote-control computers in the bot army to start sending web page requests to a website such as Microsoft.com and repeat the requests as often as possible. If successful, the tens of thousands of requests can cause a spike in the web server and possibly cause it to fail because of overloading. If they cannot cause the server to fail entirely, it might be possible to disrupt or slow down the service to legitimate folks who are trying to access the website.
This is called a DDoS attack. If the attack were conducted from a single computer, the website owners might be able to recognize a pattern and simply block that computer from making future requests. However, if the attack is coming from thousands of people’s home computers, how can the website owner distinguish legitimate requests from an attack? That’s the point of a bot army: scale, anonymity, and stealth.
We do not pretend to have the answers to why people do such things. Quite frankly, many of them are highly intelligent folks, who for whatever reason have decided to run against society’s grain. Regardless of why, they do it; so, it is important for you not to be a victim.
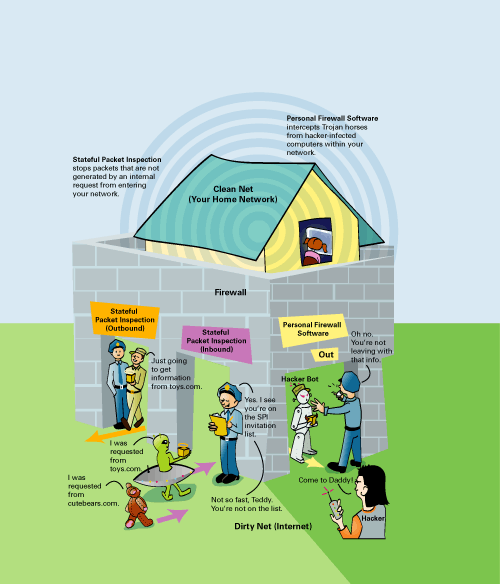
Firewalls can protect your home network by monitoring your broadband Internet connection and only permitting legitimate traffic (the data packets coming in and out of your network) to reach its destination. Firewalls come in two basic types: stateful packet inspection (SPI) firewalls and personal software firewalls (sometimes referred to as packet-filtering firewalls). The following two sections discuss and compare the different types.
Let’s examine what an SPI firewall is. Packets are messages containing pieces of data used to communicate between your computers or with the Internet. Inspecting those packets means we look at each one and check whether it is a legitimate message. Stateful means that not only are we going to check each message itself, but check that the message is sent or received at the right time in the conversation.
For example, suppose two people, Sally and Rick, are talking and the conversation goes something like this:
<dialog> <speaker>Rick</speaker>“Hi Sally.”
<speaker>Sally</speaker>“Hi Rick.”
<speaker>Rick</speaker>“’sup girl?”
<speaker>Sally</speaker>“Hi Rick.”
<speaker>Rick</speaker>“Did you hear me Sally? I asked, ‘sup girl?”
<speaker>Sally</speaker>“Hi Rick.”
</dialog>What can we learn? Well, after Rick asks, “’sup girl?” the first time, we expected Sally to say something witty, such as, “The sky and your cholesterol.” Instead, she repeats, “Hi Rick.” That sounds fishy because it is not what we expected Sally to say at that point in the conversation. Even fishier is she repeats it a third time. So we can conclude either that Sally has been taken over by an alien or replaced by a robot. Either way, we are probably done talking to her and politely smile as we walk away.
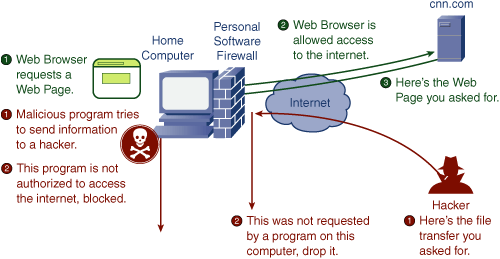
SPI works in a similar way. Figure 1-3 shows an example of an SPI firewall on a broadband Internet connection.
As shown in the green series of events in Figure 1-3, as a computer on the home network originates a request for a web page, the SPI firewall inspects the request as it passes and makes note of the request. Next, when the website responds with the web page, the SPI firewall inspects the response. It looks in its memory and realizes that, yes, this web page response was because of the computer on the home network asking for it, and the SPI firewall allows the web page through to the home network.
If a hacker or some other computer attempts to send a message to a computer in the home network, such as in the red series of events in Figure 1-3, the SPI firewall inspects the message again. This time, however, the firewall cannot make the connection between the message and a request from the home network because such a request did not occur. So, the firewall blocks the message.
Pretty neat. SPI firewalls are an effective way to keep out unwanted intrusions into your home network. They do not solve everything; after all, hackers are crafty and figure out ways around just about everything. However, SPI firewalls can at least dramatically increase the level of protection you have to start with.
If only we had SPI firewalls for our phone lines to keep telemarketers from calling us unless we called them first.
Personal software firewalls have a slightly different role in your home network security. Whereas SPI firewalls are usually meant as a barrier to what can come from the Internet, personal software firewalls act as a barrier to what can go to the Internet from your computers.
Figure 1-4 shows an example of a personal software firewall. A web browser, such as Internet Explorer, attempts to send a web page request to the Internet. The personal software firewall is set up to allow access for this program, so the request is allowed, and the web page is retrieved.
Suppose, however, that despite your best attempts, your computer becomes infected with a Trojan horse virus program (see Chapter 3, “Tip 3: Use Antivirus Protection,” for more information on viruses). Now the little devil attempts to send information back to the hackers who planted it, as depicted in Figure 1-4. This time, however, the personal software firewall intercepts the access attempt because that program is not set up to be permitted access to the Internet. The request is denied, and the hacker does not receive the information from your computer.
Just to confuse things a little, many personal software firewall programs also contain an SPI firewall for both outbound and inbound protection, as depicted in the lower right of Figure 1-4. Sweet.
Now that you understand a bit about how they work, let’s take a look at where you should place firewalls in your home network and then go ahead and turn them on. Keep in mind that even if your device comes with a built-in firewall, it may not be turned on by default.
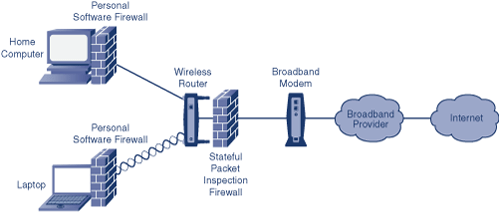
Figure 1-5 shows where firewalls are recommended in your home network. First, it is absolutely essential to place an SPI firewall between your high-speed broadband service and your home network. Fortunately, most home network routers now ship with a built-in SPI firewall, so it might require just turning it on.
Next, you need to install personal software firewalls on each of the computers in your network. As mentioned before, if the personal software firewalls on the computers also contain SPI firewall functions, all the better.
Each type of firewall presents several options. The next few sections explore the options, help you decide what is best for you, and help you install and turn them on.
As previously mentioned, you first need to place an SPI firewall between your home network and the Internet. You can do so either by installing a dedicated firewall device between your broadband cable or digital subscriber line (DSL) modem and your home network router or, if available, just turning the SPI firewall on inside your home router.
Very Important
We highly recommend you install a home network router between your high-speed broadband connection and the computers in your home. The router itself provides critical security functions such as Network Address Translation (NAT), providing a level of defense for your home network. For more information, see Home Networking Simplified, which contains a complete discussion on the importance of home routers.
To make it really easy, many home network routers are being shipped with built-in SPI firewalls, so all you have to do is turn it on. Nearly all new Linksys wired and wireless routers are equipped with a built-in SPI firewall. If your home router already has an SPI firewall, turn it on and you are done. If it does not, you need to make a decision about how to proceed.
Very Important
Make sure whatever you buy has an SPI firewall. Some products claim to include a firewall, but the term firewall can be interpreted several ways. Look on the box or ask a store professional to make sure what you are buying has SPI.
Because a home network router already has to handle all the messages between your computers and the Internet, it is also a convenient place to put an SPI firewall.
To activate it, you need to access the router’s administration function, usually with an Internet browser or a client on one of your computers. Figure 1-6 shows turning on the SPI firewall in a Linksys wireless router (model WRT54GS in this example).
The steps for turning on your firewall are as follows:
Access the router’s administration function. For Linksys routers, use Internet Explorer and enter the router’s IP address in your home network (usually 192.168.1.1).
When prompted, enter the administrator user ID and password.
Click the Security tab.
Click Enable for the firewall function.
Also checkmark the optional additional protection functions, including Block Anonymous Internet Requests, Filter Multicast, Filter Internet NAT Redirection, and Filter IDENT(Port 113). These are to detect and block several specific known hacking attacks.
Click Save Settings.
That’s it. Now your SPI firewall is running and protecting your home network from the Internet. You have just taken an extremely important step to protecting your home network.
You might ask, “How do I know it is working?” Great question. See you are already learning to become suspicious and think security. Read on and we will give you some tips to make sure what you think you have working really is protecting you like you think.
If your home network router does not offer a built-in SPI firewall, you must decide whether to replace your home network router with one that does or purchase and install a dedicated firewall device. A dedicated firewall device is essentially a box that you place between your broadband modem and your home router that acts 100 percent of the time as a firewall. It provides no other networking functions.
In corporate security circles, dedicated firewalls are preferred because security-minded folks argue that if you keep the software in the box simple, it will have fewer security holes, and as soon as you start adding other functions to it, you add complexity and open up the possibility for holes.
For your home network, dedicated firewalls are becoming extremely rare because it is much more economical and space efficient to have the home router provide the function.
If you decide to go with a dedicated firewall, be aware that each one differs according to the manufacturer. We suggest following the manufacturer’s installation instructions.
Very Important
If you already have an older home network router installed that does not have an SPI firewall—for example, an older Wireless-B standard router—you might want to kill two birds and consider upgrading to a faster Wireless-G or Wireless-N router and at the same time get the built-in SPI firewall. Chances are you can make both upgrades for the same or less than buying a dedicated firewall device to add to an existing older router.
Now that the SPI firewall is protecting the edge of your home network, it’s time to turn your attention to the computers on the home network. Each computer needs to have a personal software firewall installed. Unlike SPI firewalls, which usually come in physical devices, personal firewalls generally come in the form of software you install on the computer you want to protect.
Here again you have a choice of several options. The first option is Windows XP Service Pack 2 (SP2) and later offers a built-in software firewall. The second option is Zone Labs, which offers its basic ZoneAlarm software firewall for free. Finally, several software firewall programs are available for purchase.
Which you choose depends on your needs, but we try to highlight the advantages and disadvantages of each in the sections that follow.
Starting with Windows XP SP2, Windows offers a built-in personal firewall. If you have XP, but do not already have XP SP2 installed, you can obtain it here:
If you have an older version of Windows (including 98SE, ME, or 2000), you are out of luck until you upgrade to XP. See the next sections for other personal software firewall options.
The Windows XP firewall is a basic firewall with program access control (blocking computer to Internet) and SPI (blocking Internet to computer). It is a no-frills approach, but the price is right.
Figures 1-7 and 1-8 show how to enable the Windows XP built-in firewall.
The following are the steps to enable the Windows XP built-in firewall:
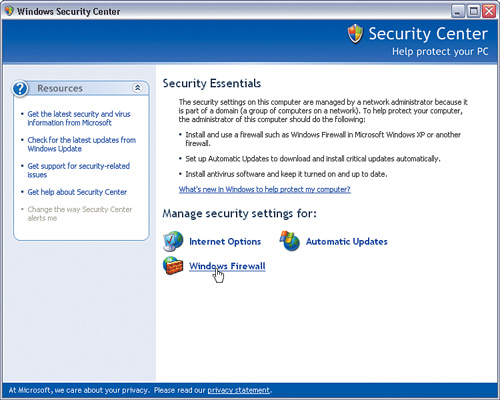
Click Start > Control Panel > Security Center. The main Security Center dialog will display, as shown in Figure 1-7.
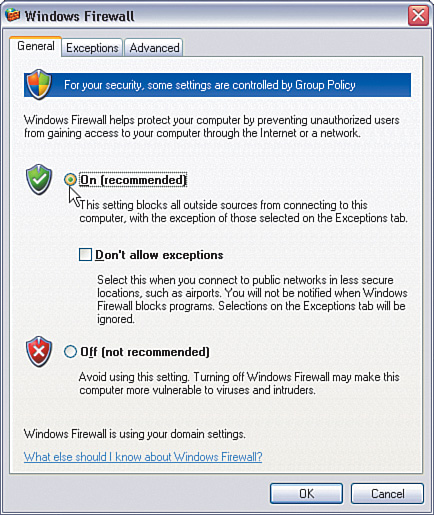
Click Windows Firewall. You will see the dialog shown in Figure 1-8.
Enable the On (recommended) button and click OK to save the setting.
The Windows XP built-in firewall is now enabled. There are not a lot of other things to configure, and the granularity of control you have is somewhat limited. But, all in all, it is an easy and cost-effective way to enable a personal software firewall on each of your computers. If you want a turn-it-on-and-forget-it firewall and you are running XP, this is a good option.
Very Important
Having the firewall program log interesting events (meaning when it detects unusual activity and takes an action such as dropping the packet) can prove useful for debugging. To enable logging with Windows Firewall, go to the Windows Security Center, click Windows Firewall, and go to the Advanced tab. In the Security Logging section, click Settings and then checkmark what you want to log and choose a location for the log file. To view the log, you must use Notepad to browse the file.
Another relatively easy and cost-effective option for a personal software firewall is ZoneAlarm. Zone Labs offers several versions of its firewall program, including a basic firewall program that is free and a couple more sophisticated versions for purchase.
Let’s look at the free version here. The for-purchase version is discussed in the next section. The free ZoneAlarm firewall is a fully functional, pretty good firewall program that includes the functionality you need to protect the computers in your home network. ZoneAlarm is somewhat more configurable than the Windows XP built-in firewall and provides more visibility into what is being blocked or allowed. This could be needed if you run into issues where certain programs you want to have access are being blocked for some reason. With ZoneAlarm, you can see what is being blocked and easily adjust the settings.
Very Important
Typically, only one personal software firewall program can be installed and active on a computer at a time. You generally cannot, for example, run both Windows XP Firewall and ZoneAlarm. Additional firewall programs do not offer any additional protection, and it could lead to complex problems. Pick one, not several. ZoneAlarm in particular disables Windows Firewall when it is installed to avoid such conflicts.
ZoneAlarm is available for download here:
Go to the download area and download the version that is just called ZoneAlarm for the free version.
The following covers some brief installation and setup steps that refer to Figures 1-9 and 1-10.
Download and install ZoneAlarm on your computer. You will need to then restart the computer to complete the install.
The main ZoneAlarm control dialog is shown in Figure 1-9. If you do not see it on your computer, double-click the yellow and red ZA icon that should be in your running tasks at the bottom right of your screen.
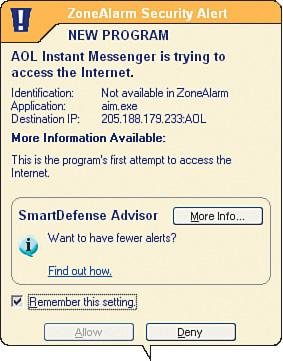
ZoneAlarm learns which programs you want to allow or block access to the Internet. When a program attempts access, you will see a popup box as in Figure 1-10.
Decide whether you want the program to have access. If yes, click the Allow button; if not, click Deny.
Check the Remember this setting box prior to clicking Allow or Deny if you want ZoneAlarm to grant or deny access to this program automatically in the future.
If you are not sure whether you want to allow or deny access, perhaps because you do not recognize the program, you can click on More Info to seek advice from Zone Labs.
The ZoneAlarm firewall is now enabled. It is a good idea at this point to try to use the programs you normally use, especially those that access the Internet, including Outlook Express (or the alternate e-mail program you use), instant messaging, Internet Explorer (or the alternate browser you use), and so on. Each time a new program tries to access the Internet, ZoneAlarm will prompt you to grant or deny access.
In general, ZoneAlarm initially blocks everything that automatically attempts to access the Internet, including things such as updates to your antivirus programs, which, of course, you want. You can usually read the popup warning and figure it out; if you are not sure what ZoneAlarm is attempting to block, choose the block function and then check the programs you use most often to make sure they are still operating correctly.
If one or more of the programs you used to use no longer works, or if a new program you install does not work properly, you might want to check the access settings in ZoneAlarm to make sure they are not incorrectly set:
Double-click the ZA icon on your taskbar, or click Start > Programs > Zone Labs > Zone Labs Security to launch the ZoneAlarm control dialog. You will see the main Security Center dialog shown previously in Figure 1-9.
Click Program Control on the left side of the dialog, and click the Programs tab at the top. You will see the dialog shown in Figure 1-11.
Find the program in the list you are trying to use and verify its access control settings. For example, you can see in this case that AOL Instant Messenger has green checkmarks next to it, meaning that it is always granted access. Red Xs mean the program is always blocked. Blue question marks indicate that there is no permanent setting and ZoneAlarm will prompt you each time the program runs.
To change the access setting, right-click the green check or red X beside the program and select the new setting.
Very Important
You will notice two sets of columns in the Program Control dialog: Access and Server. Access permissions apply to programs on your computer that need access to the Internet. In general, all programs that you want to allow to access the Internet need a minimum of Access permission. Server permission is an additional authorization needed by some programs that legitimately send unsolicited traffic to your computer, such as some e-mail and IM programs. Try allowing Access permissions first; if the program you are using still is not working correctly, try setting the Server permissions to Allow (green checks), too.
In summary, ZoneAlarm firewall is another relatively easy and cost-effective method for enabling a personal software firewall on each of your computers. If you want a firewall program that offers a bit more control and visibility, ZoneAlarm is a good option. If you are not running Windows XP and have no intention to upgrade, again ZoneAlarm is a good option for you.
Very Important
Having the firewall program log interesting events (meaning when it detects unusual activity and takes an action such as dropping the packet) can prove useful for debugging. Logging is enabled in ZoneAlarm by default. To view the log, bring up the ZoneAlarm main control dialog, click Alerts & Logs, and click the Log Viewer tab.
A third option for personal software firewall programs is to purchase one. You may ask, “Why buy one when there are two free options?” Two reasons. First, you get what you pay for, meaning the for-purchase firewall programs are typically going to be kept much more current and have features added to them (not to say that Windows XP Firewall or ZoneAlarm will not).
Second, when you purchase an antivirus software program (notice we said when, not if), you have the option of paying a little more money for an entire security bundle. We cover antivirus programs in Chapter 3. Security bundles are offered by the major security software vendors and include a whole suite of protection, including antivirus, firewall, spyware/adware blocking, parental control, antispam, and so on.
We recommend checking out the security bundles from the leading security software vendors in Table 1-1.
This book lacks space to show them all. Just to give you a feel for how the security packages look, however, the following discussion covers two of them. Keep in mind that you only need one of these firewall programs for your home network; adding a second will only disable the previously loaded firewall programs.
Figure 1-12 shows the main control panel for Symantec’s product, Norton Internet Security 200x. You can see that the Personal Firewall component that came included in the bundle is enabled.
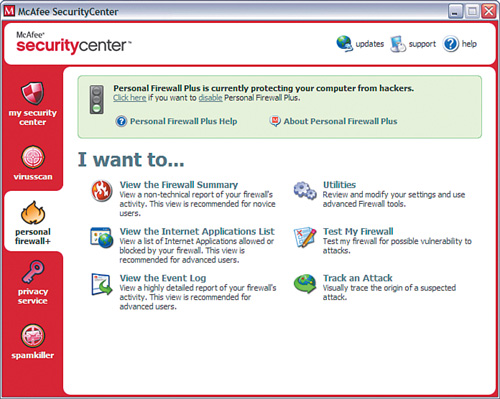
Figure 1-13 shows the main control panel for McAfee’s product, Internet Security Suite. Once again, you can see that the Personal Firewall component that came included in the bundle is enabled.
Both of these personal software firewalls operate similarly to ZoneAlarm. Each learns as new programs attempt to access the Internet, and you specify whether to grant or deny access. Both are also configurable and allow for relatively easy control and visibility.
If you decide to purchase a security bundle, the included personal firewall component is a good option. Also, if you need a fully functional firewall program with all the bells and whistles, one of these for-purchase programs is a good option for you. You should also check your Internet service provider’s security pages. They often offer bundles and good advice on firewalls and bundled security services.
After your new firewall protection is up and running (on both your router and your computers), and when you are comfortable that your programs are still working, it is worth a couple minutes to perform a quick test using an online tool to determine whether the firewalls are doing their job.
You can run a quick test using the port-scanning utility provided by a collection of broadband providers. You can access this here:
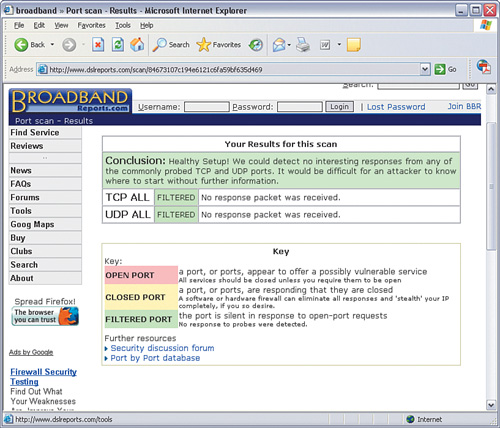
Click Probe, and when it finishes click Results. This utility attempts to get responses from your home network, which your SPI firewall should now block. Figure 1-14 shows a sample scan.
You should see all green indicators (not red or yellow), which means that your network is protected. Suggestions are offered if weaknesses in the network security are identified.
Another similar test is provided online by a group opposed to hacking, called Hacker Watch. You can find their test here:
Click Port Scan to start the test. This utility attempts to get responses from your home network, which your SPI firewall should now block. Figure 1-15 shows a sample result from this test.
When the test completes, you should again see green indicators, telling you the attempts to send messages into your home network from the Internet were appropriately blocked by your SPI firewall. If security weaknesses exist, some suggestions are made as to how to solve them.
Several other similar security scans are available online, such as the following:
Both of these programs (and several others) all work great. There is really no need to try them all out (but there’s nothing wrong with doing that). Just pick one that appeals to you and go with it.
Despite our best attempts, stuff happens. One of the most common ways you can get hacked today is by inadvertently unleashing a virus on your computer (see Chapter 3). Just opening an e-mail with a malicious program attached can wreak havoc on your computer, including setting up a Trojan horse program, whereby a hacker can take control of your computer.
Another less-invasive, but no-less-annoying intrusion, is spyware and adware (see Chapter 5, “Tip 5: Lock Out Spyware and Adware”). By installing a “free” program from the “who knows what” website, you can unleash an adware program on your computer that can annoy you with constant popup advertisements, or worse, start transmitting your Internet browsing habits over the Internet to someplace that wants to target you for direct marketing, or even log and report all your keystrokes (including passwords).
Sometimes, no easy way exists to tell whether you have been hijacked or infected. Sometimes, however, there are good ways to tell. One such way is to become familiar with which programs are installed on your computer. If you see a new program appear that you did not install or cause to install, it might be a malicious program.
You can take two steps to address the problem: Block the program’s access in the personal software firewall, and uninstall it. Make sure it is malicious before you take action.
Go to the program control screen in your personal software firewall program. For this example, we use ZoneAlarm. As shown in Figure 1-16, access the Program Control screen and select the Programs tab. Click the program in question (in this example, GAIN Application).
Down at the bottom of the window, you can see the filename of the program (in this case, GMT.exe). Doing a quick search online, we can find out that this is a common adware application from GAIN Publishing.
To block it, just right-click the program and select the red X. Now the program is blocked from accessing the Internet.
Blocking the program does nothing to solve the root cause of the problem, meaning the program is still sitting there running on your computer. Adware, and in general any needless program, can slow down performance of your computer dramatically. So, it is usually best to get rid of it.
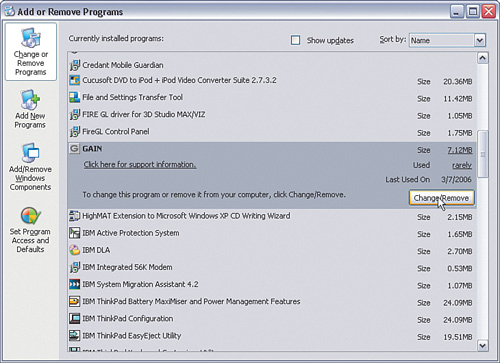
To do so, click Start > Control Panel > Add/Remove Programs. As shown in Figure 1-17, click the program you want to remove, and then click Change/Remove.
The adware program will be uninstalled. You can then either leave the access rule in ZoneAlarm (recommended) or delete it. If you leave it blocked and the same adware program should inadvertently be installed again, its access to the Internet will be blocked from the start. However, it does tend to produce some clutter in the program list.
In general, it is good practice to become familiar with the programs in the Windows Add/Remove Programs list and the Program Control list in your personal software firewall. That way, when a new entry unexpectedly appears, you can recognize it.
Although firewalls are intended to always block the bad stuff, while letting the good stuff through, it is not always that easy. Sometimes as a side effect of having a firewall, a program you want to access the Internet does not function properly.
The best approach if you suspect the firewall is causing the problem is to temporarily turn off the firewall and determine whether the program now functions. If it does, turn the firewall back on and adjust the access settings for the program. Peer-to-peer-sharing and file-transfer/FTP programs are the most common for this type of problem.
Firewalls do not solve every home network security issue. They are a critical step for security, but they need to be complemented with the other steps in this book (including antivirus and antispyware/adware).
Also, do not expect a firewall to catch every hack or intrusion attempt. Firewalls are pretty good at blocking today’s known hacks. However, crafty folks as the hackers are, they can find new ways around firewalls.
View having appropriate firewalls in your home network as significantly raising the barrier against intruders so that they move on to easier targets.
To find more information about firewalls, try these websites:
If you want something more technical, we recommend the following site: