


Enterprise solutions
In this chapter, we describe the major solutions that can help enterprises achieve their business goals and the reasons on why IBM Power10 processor-based mid-range servers provide a significant contribution to that end.
5.1 PowerVM virtualization
The PowerVM platform is the family of technologies, capabilities, and offerings that delivers industry-leading virtualization for enterprises. It is the umbrella branding term for IBM Power processor-based server virtualization:
•IBM Power Hypervisor
•Logical partitioning
•IBM Micro-Partitioning®
•Virtual I/O Server (VIOS)
•Live Partition Mobility (LPM)
PowerVM is a combination of hardware and software enablement.
|
Note: PowerVM Enterprise Edition License Entitlement is included with each Power10 processor-based mid-range server. PowerVM Enterprise Edition is available as a hardware feature (#EPVV); supports up to 20 partitions per core, VIOS, multiple shared processor pools (MSPPs); and also offers LPM.
|
5.1.1 IBM Power Hypervisor
IBM Power processor-based servers are combined with PowerVM technology and offer the following key capabilities that can help to consolidate and simplify IT environments:
•Improve server usage and share I/O resources to reduce the total cost of ownership (TCO) and better use IT assets.
•Improve business responsiveness and operational speed by dynamically reallocating resources to applications as needed to better match changing business needs or handle unexpected changes in demand.
•Simplify IT infrastructure management by making workloads independent of hardware resources so that business-driven policies can be used to deliver resources that are based on time, cost, and service-level requirements.
Combined with features in the Power10 processor-based mid-range servers, the Power Hypervisor delivers functions that enable other system technologies, including logical partitioning technology, virtualized processors, IEEE virtual local area network (VLAN)-compatible virtual switches, virtual Small Computer Serial Interface (SCSI) adapters, virtual Fibre Channel (FC) adapters, and virtual consoles.
The Power Hypervisor is a basic component of the system’s firmware and offers the following functions:
•Provides an abstraction between the physical hardware resources and the LPARs that use them.
•Enforces partition integrity by providing a security layer between LPARs.
•Controls the dispatch of virtual processors to physical processors.
•Saves and restores all processor state information during a logical processor context switch.
•Controls hardware I/O interrupt management facilities for LPARs.
•Provides VLAN channels between LPARs that help reduce the need for physical Ethernet adapters for inter-partition communication.
•Monitors the enterprise Baseboard Management Controller (eBMC) and performs a reset or reload if needed, notifying the operating system (OS) if the problem is not corrected.
The Power Hypervisor is always active, regardless of the system configuration or whether it is connected to the managed console. It requires memory to support the resource assignment of the LPARs on the server. The amount of memory that is required by the Power Hypervisor firmware varies according to several factors:
•Memory usage for hardware page tables (HPTs)
•Memory usage to support I/O devices
•Memory usage for virtualization
Memory usage for hardware page tables
Each partition on the system includes its own HPT that contributes to hypervisor memory usage. The HPT is used by the OS to translate from effective addresses to physical real addresses in the hardware. This translation from effective to real addresses allows multiple OSs to run simultaneously in their own logical address space. Whenever a virtual processor for a partition is dispatched on a physical processor, the hypervisor indicates to the hardware the location of the partition HPT that can be used when translating addresses.
The amount of memory for the HPT is based on the maximum memory size of the partition and the HPT ratio. The default HPT ratio is 1/128th (for AIX, VIOS, and Linux partitions) of the maximum memory size of the partition. AIX, VIOS, and Linux use larger page sizes (16 and 64 KB) instead of using 4 KB pages. The use of larger page sizes reduces the overall number of pages that must be tracked; therefore, the overall size of the HPT can be reduced. For example, the HPT is 2 GB for an AIX partition with a maximum memory size of 256 GB.
When defining a partition, the maximum memory size that is specified is based on the amount of memory that can be dynamically added to the dynamic logical partition (DLPAR) without changing the configuration and restarting the partition.
In addition to setting the maximum memory size, the HPT ratio can be configured. The hpt_ratio parameter for the chsyscfg Hardware Management Console (HMC) command can be issued to define the HPT ratio that is used for a partition profile. The valid values are 1:32, 1:64, 1:128, 1:256, or 1:512.
Specifying a smaller absolute ratio (1/512 is the smallest value) decreases the overall memory that is assigned to the HPT. Testing is required when changing the HPT ratio because a smaller HPT might incur more CPU consumption because the OS might need to reload the entries in the HPT more frequently. Most customers choose to use the IBM provided default values for the HPT ratios.
Memory usage for I/O devices
In support of I/O operations, the hypervisor maintains structures that are called the translation control entities (TCEs), which provide an information path between I/O devices and partitions. The TCEs provide the address of the I/O buffer, indications of read versus write requests, and other I/O-related attributes. Many TCEs are used per I/O device, so multiple requests can be active simultaneously to the same physical device. To provide better affinity, the TCEs are spread across multiple processor chips or drawers to improve performance while accessing the TCEs.
For physical I/O devices, the base amount of space for the TCEs is defined by the hypervisor that is based on the number of I/O devices that are supported. A system that supports high-speed adapters also can be configured to allocate more memory to improve I/O performance. Linux is the only OS that uses these extra TCEs so that the memory can be freed for use by partitions if the system uses only AIX.
Memory usage for virtualization features
Virtualization requires more memory to be allocated by the Power Hypervisor for hardware statesave areas and various virtualization technologies. For example, on Power10 processor-based systems, each processor core supports up to eight simultaneous multithreading (SMT) threads of execution, and each thread contains over 80 different registers.
The Power Hypervisor must set aside save areas for the register contents for the maximum number of virtual processors that are configured. The greater the number of physical hardware devices, the greater the number of virtual devices, the greater the amount of virtualization, and the more hypervisor memory is required. For efficient memory consumption, wanted and maximum values for various attributes (processors, memory, and virtual adapters) must be based on business needs, and not set to values that are significantly higher than actual requirements.
Predicting memory that is used by the Power Hypervisor
The IBM System Planning Tool (SPT) is a resource that can be used to estimate the amount of hypervisor memory that is required for a specific server configuration. After the SPT executable file is downloaded and installed, you can define a configuration by selecting the correct hardware platform and the installed processors and memory, and defining partitions and partition attributes. SPT can estimate the amount of memory that is assigned to the hypervisor, which helps you when you change a configuration or deploy new servers.
The Power Hypervisor provides the following types of virtual I/O adapters:
•Virtual SCSI
The Power Hypervisor provides a virtual SCSI mechanism for the virtualization of storage devices. The storage virtualization is accomplished by using two paired adapters: a virtual SCSI server adapter and a virtual SCSI customer adapter.
•Virtual Ethernet
The Power Hypervisor provides a virtual Ethernet switch function that allows partitions fast and secure communication on the same server without any need for physical interconnection or connectivity outside of the server if a Layer 2 bridge to a physical Ethernet adapter is set in one VIOS partition, also known as Shared Ethernet Adapter (SEA).
•Virtual FC
A virtual FC adapter is a virtual adapter that provides customer LPARs with an FC connection to a storage area network (SAN) through the VIOS partition. The VIOS partition provides the connection between the virtual FC adapters on the VIOS partition and the physical FC adapters on the managed system.
•Virtual (tty) console
Each partition must have access to a system console. Tasks such as OS installation, network setup, and various problem analysis activities require a dedicated system console. The Power Hypervisor provides the virtual console by using a virtual tty or serial adapter and a set of hypervisor calls to operate on them. Virtual tty does not require the purchase of any other features or software, such as the PowerVM Edition features.
Logical partitions
Logical partitions (LPARs) and virtualization increase the usage of system resources and add a level of configuration possibilities.
Logical partitioning is the ability to make a server run as though it were two or more independent servers. When you logically partition a server, you divide the resources on the server into subsets, which are called LPARs. You can install software on an LPAR, and the LPAR runs as an independent logical server with the resources that you allocated to the LPAR.
LPAR also is referred to in some documentation as a virtual machine (VM), which makes it look like what other hypervisors offer. However, LPARs provide a higher level of security and isolation and other features that are described in this chapter.
Processors, memory, and I/O devices can be assigned to LPARs. AIX, IBM i, Linux, and VIOS can run on LPARs. VIOS provides virtual I/O resources to other LPARs with general-purpose OSs.
|
Note: The Power E 1050 server does not support IBM i.
|
LPARs share a few system attributes, such as the system serial number, system model, and processor FCs. All other system attributes can vary from one LPAR to another.
Micro-Partitioning
When you use the Micro-Partitioning technology, you can allocate fractions of processors to an LPAR. An LPAR that uses fractions of processors is also known as a shared processor partition or micropartition. Micropartitions run over a set of processors that is called a shared processor pool (SPP), and virtual processors are used to enable the OS manage the fractions of processing power that are assigned to the LPAR.
From an OS perspective, a virtual processor cannot be distinguished from a physical processor unless the OS is enhanced to determine the difference. Physical processors are abstracted into virtual processors that are available to partitions.
On a Power10 processor-based server, a partition can be defined with a processor capacity as small as 0.05processing units. This number represents 0.05 of a physical core. Each physical core can be shared by up to 20 shared processor partitions, and the partition’s entitlement can be incremented fractionally by as little as 0.05 of the processor. The shared processor partitions are dispatched and time-sliced on the physical processors under the control of the Power Hypervisor. The shared processor partitions are created and managed by the HMC.
|
Note: Although the Power10 processor-based mid-range server supports up to 20 shared processor partitions, the real limit depends on application workload demands in use on the server.
|
Processing mode
When you create an LPAR, you can assign entire processors for dedicated use, or you can assign partial processing units from an SPP. This setting defines the processing mode of the LPAR.
Dedicated mode
In dedicated mode, physical processors are assigned as a whole to partitions. The SMT feature in the Power10 processor core allows the core to run instructions from two, four, or eight independent software threads simultaneously.
Shared dedicated mode
On Power10 processor-based servers, you can configure dedicated partitions to become processor donors for idle processors that they own, which allows for the donation of spare CPU cycles from dedicated processor partitions to an SPP. The dedicated partition maintains absolute priority for dedicated CPU cycles. Enabling this feature can help increase system usage without compromising the computing power for critical workloads in a dedicated processor mode LPAR.
Shared mode
In shared mode, LPARs use virtual processors to access fractions of physical processors. Shared partitions can define any number of virtual processors (the maximum number is 20 times the number of processing units that are assigned to the partition). The Power Hypervisor dispatches virtual processors to physical processors according to the partition’s processing units entitlement. One processing unit represents one physical processor’s processing capacity. All partitions receive a total CPU time equal to their processing unit’s entitlement. The logical processors are defined on top of virtual processors. Therefore, even with a virtual processor, the concept of a logical processor exists, and the number of logical processors depends on whether SMT is turned on or off.
5.1.2 Multiple shared processor pools
MSPPs are supported on Power10 processor-based servers. This capability allows a system administrator to create a set of micropartitions with the purpose of controlling the processor capacity that can be used from the physical SPP.
Micropartitions are created and then identified as members of the default processor pool or a user-defined SPP. The virtual processors that exist within the set of micropartitions are monitored by the Power Hypervisor. Processor capacity is managed according to user-defined attributes.
If the IBM Power server is under heavy load, each micropartition within an SPP is assured of its processor entitlement, plus any capacity that might be allocated from the reserved pool capacity if the micropartition is uncapped.
If specific micropartitions in an SPP do not use their processing capacity entitlement, the unused capacity is ceded, and other uncapped micropartitions within the same SPP can use the extra capacity according to their uncapped weighting. In this way, the entitled pool capacity of an SPP is distributed to the set of micropartitions within that SPP.
All IBM Power servers that support the MSPP capability have a minimum of one (the default) SPP and up to a maximum of 64 SPPs.
This capability helps customers reduce total cost of ownership (TCO) when the cost of software or database licenses depends on the number of assigned processor cores.
5.1.3 Virtual I/O Server
The VIOS is part of PowerVM. It is the specific appliance that allows the sharing of physical resources among LPARs to allow more efficient usage (for example, consolidation). In this case, the VIOS owns the physical I/O resources (SCSI, FC, network adapters, or optical devices) and allows customer partitions to share access to them, which minimizes and optimizes the number of physical adapters in the system.
The VIOS eliminates the requirement that every partition owns a dedicated network adapter, disk adapter, and disk drive. The VIOS supports OpenSSH for secure remote logins. It also provides a firewall for limiting access by ports, network services, and IP addresses.
Figure 5-1 shows an overview of a VIOS configuration.
Figure 5-1 Architectural view of the VIOS
It is a best practice to run dual VIOSs per physical server.
Shared Ethernet Adapter
A SEA can be used to connect a physical Ethernet network to a virtual Ethernet network. The SEA provides this access by connecting the Power Hypervisor VLANs to the VLANs on the external switches. Because the SEA processes packets at Layer 2, the original MAC address and VLAN tags of the packet are visible to other systems on the physical network. IEEE 802.1 VLAN tagging is supported.
By using the SEA, several customer partitions can share one physical adapter. You also can connect internal and external VLANs by using a physical adapter. The SEA service can be hosted only in the VIOS (not in a general-purpose AIX or Linux partition) and acts as a Layer 2 network bridge to securely transport network traffic between virtual Ethernet networks (internal) and one or more (Etherchannel) physical network adapters (external). These virtual Ethernet network adapters are defined by the Power Hypervisor on the VIOS.
Virtual SCSI
Virtual SCSI is used to view a virtualized implementation of the SCSI protocol. Virtual SCSI is based on a client/server relationship. The VIOS LPAR owns the physical I/O resources and acts as a server or in SCSI terms a target device. The client LPARs access the virtual SCSI backing storage devices that are provided by the VIOS as clients.
The virtual I/O adapters (a virtual SCSI server adapter and a virtual SCSI client adapter) are configured by using an HMC. The virtual SCSI server (target) adapter is responsible for running any SCSI commands that it receives, and it is owned by the VIOS partition. The virtual SCSI client adapter allows a client partition to access physical SCSI and SAN-attached devices and LUNs that are mapped to be used by the client partitions. The provisioning of virtual disk resources is provided by the VIOS.
N_Port ID Virtualization
N_Port ID Virtualization (NPIV) is a technology that allows multiple LPARs to access one or more external physical storage devices through the same physical FC adapter. This adapter is attached to a VIOS partition that acts only as a pass-through that manages the data transfer through the Power Hypervisor.
Each partition features one or more virtual FC adapters, each with their own pair of unique worldwide port names. This configuration enables you to connect each partition to independent physical storage on a SAN. Unlike virtual SCSI, only the client partitions see the disk.
For more information and requirements for NPIV, see IBM PowerVM Virtualization Managing and Monitoring, SG24-7590.
5.1.4 Live Partition Mobility
With LPM, you can move a running LPAR from one system to another one without disruption. Inactive partition mobility allows you to move a powered-off LPAR from one system to another one.
LPM provides systems management flexibility and improves system availability by avoiding the following situations:
•Planned outages for hardware upgrade or firmware maintenance.
•Unplanned downtime. With preventive failure management, if a server indicates a potential failure, you can move its LPARs to another server before the failure occurs.
For more information and requirements for LPM, see IBM PowerVM Live Partition Mobility, SG24-7460.
HMC 10.1.1020.0 and VIOS 3.1.3.21 or later provide the following enhancements to the LPM feature:
•Automatically choose fastest network for LPM memory transfer.
•Allow LPM when a virtual optical device is assigned to a partition.
5.1.5 Active Memory Mirroring
Active Memory Mirroring (AMM) for Hypervisor is available as an option (#EM8G) to enhance resilience by mirroring critical memory that is used by the PowerVM hypervisor so that it can continue operating in a memory failure.
A portion of available memory can be proactively partitioned such that a duplicate set can be used on non-correctable memory errors. This partition can be implemented at the granularity of DIMMs or logical memory blocks.
5.1.6 Remote Restart
Remote Restart is a high availability (HA) option for partitions. If an error occurs that causes a server outage, a partition that is configured for Remote Restart can be restarted on a different physical server. At times, it might take longer to start the server, in which case the Remote Restart function can be used for faster reprovisioning of the partition. Typically, this task can be done faster than restarting the server that stopped and then restarting the partitions. The Remote Restart function relies on technology that is like LPM, where a partition is configured with storage on a SAN that is shared (accessible) by the server that hosts the partition.
HMC 10R1 provides an enhancement to the Remote Restart feature that enables remote restart when a virtual optical device is assigned to a partition.
5.1.7 IBM Power processor modes
Although they are not virtualization features, the IBM Power processor modes are described here because they affect various virtualization features.
On IBM Power servers, partitions can be configured to run in several modes, including the following modes:
•Power8
This native mode for Power8 processors implements version 2.07 of the IBM Power instruction set architecture (ISA). For more information, see Processor compatibility mode definitions.
•Power9
This native mode for Power9 processors implements version 3.0 of the IBM Power ISA. For more information, see Processor compatibility mode definitions.
•Power10
This native mode for Power10 processors implements version 3.1 of the IBM Power ISA. For more information, see Processor compatibility mode definitions.
Figure 5-2 shows the available processor modes on a Power10 processor-based mid-range server.

Figure 5-2 Processor modes
Processor compatibility mode is important when LPM migration is planned between different generation of servers. An LPAR that might be migrated to a machine that is managed by a processor from another generation must be activated in a specific compatibility mode.
|
Note: Migrating an LPAR from a Power7 processor-based server to a Power10 processor-based mid-range server by using LPM is not supported; however, the following steps can be completed to accomplish this task:
1. Migrate LPAR from a Power7 processor-based server to a Power8 or Power9 processor-based server by using LPM.
2. Migrate the LPAR from the Power8 or Power9 processor-based server to a Power10 processor-based mid-range server.
The OS running on the Power7 processor-based server must be supported on the Power10 processor-based mid-range server or must be upgraded to a supported level before completing these steps.
|
5.1.8 Single-root I/O virtualization
Single-root I/O virtualization (SR-IOV) is an extension to the Peripheral Component Interconnect Express (PCIe) specification that allows multiple OSs to simultaneously share a PCIe adapter with little or no runtime involvement from a hypervisor or other virtualization intermediary.
SR-IOV is PCI standard architecture that enables PCIe adapters to become self-virtualizing. It enables adapter consolidation through sharing, much like logical partitioning enables server consolidation. With an adapter capable of SR-IOV, you can assign virtual slices of a single physical adapter to multiple partitions through logical ports, which is done without a VIOS.
5.1.9 More information about virtualization features
The following IBM Redbooks publications provide more information about the virtualization features:
•IBM PowerVM Best Practices, SG24-8062
•IBM PowerVM Virtualization Introduction and Configuration, SG24-7940
•IBM PowerVM Virtualization Managing and Monitoring, SG24-7590
•IBM Power Systems SR-IOV: Technical Overview and Introduction, REDP-5065
5.2 IBM PowerVC overview
IBM Power Virtualization Center (PowerVC) is an advanced virtualization and cloud management offering (that is built on OpenStack) that provides simplified virtualization management and cloud deployments for IBM AIX and Linux VMs, including Red Hat OpenShift (CoreOS) running on IBM Power. PowerVC is designed to improve administrator productivity and simplify the cloud management of VMs on IBM Power servers.
By using PowerVC, you can perform the following tasks:
•Create VMs and resize the VMs CPU and memory.
•Attach disk volumes or other networks to those VMs.
•Import VMs and volumes so that they can be managed by IBM PowerVC.
•Deploy new VMs with storage and network from an image in a few minutes.
•Monitor the usage of resources in your environment.
•Take snapshots of a VM or clone a VM.
•Migrate VMs while they are running (live migration between physical servers).
•Automated Remote Restart VMs in a server failure.
•Automatically balance cloud workloads by using the Dynamic Resource Optimizer (DRO).
•Use advanced storage technologies, such as VDisk mirroring, IBM HyperSwap, and
IBM Global Mirror.
IBM Global Mirror.
•Put a server into maintenance mode with automatic distribution of LPARs to other servers and back by using LPM.
•Create a private cloud with different projects/tenants that are independent from each other but use the same resources.
•Create a self-service portal with an approval workflow.
•Meter resource usage as a basis for cost allocation.
•Improve resource usage to reduce capital expenses and power consumption.
•Increase agility and execution to respond quickly to changing business requirements.
•Increase IT productivity and responsiveness.
•Simplify IBM Power virtualization management.
•Accelerate repeatable, error-free virtualization deployments.
IBM PowerVC can manage AIX and Linux based VMs that are running under PowerVM virtualization that are connected to an HMC or that use NovaLink. This release supports the scale-out and the enterprise IBM Power servers that are built on IBM Power8, IBM Power9, and Power10 servers.
|
Note: The Power E1050 server is supported by PowerVC 2.0.3 or later. If an additional fix is needed, see IBM Fix Central.
|
5.2.1 IBM PowerVC functions and advantages
When more than 70% of IT budgets are spent on operations and maintenance, IT customers legitimately expect vendors to focus their new development efforts to reduce IT costs and foster innovation within IT departments.
IBM PowerVC gives IBM Power customers the following advantages:
•It is deeply integrated with IBM Power.
•It provides virtualization management tools.
•It eases the integration of servers that are managed by PowerVM in automated IT environments, such as clouds.
•It is a building block of IBM Infrastructure as a Service (IaaS), which is based on
IBM Power.
IBM Power.
•PowerVC integrated with other cloud management tools, such as Ansible, Terraform, or Red Hat OpenShift, can be integrated into orchestration tools, such as the IBM Cloud Automation Manager, VMware vRealize, or SAP Landscape Management (LaMa).
•PowerVC also provides an easy exchange of VM images between private and public clouds by using the integration of IBM Cloud Object Storage into PowerVC.
IBM PowerVC is an addition to the PowerVM set of enterprise virtualization technologies that provide virtualization management. It is based on open standards and integrates server management with storage and network management.
Because IBM PowerVC is based on the OpenStack initiative, IBM Power can be managed by tools that are compatible with OpenStack standards. When a system is controlled by
IBM PowerVC, it can be managed in one of three ways:
IBM PowerVC, it can be managed in one of three ways:
•By a system administrator by using the IBM PowerVC GUI
•By a system administrator that uses scripts that contain the IBM PowerVC Representational State Transfer (REST) application programming interfaces (APIs)
•By higher-level tools that call IBM PowerVC by using standard OpenStack API
The following PowerVC offerings are positioned within the available solutions for IBM Power cloud:
•IBM PowerVC: Advanced Virtualization Management
•IBM PowerVC for Private Cloud: Basic Cloud
•IBM Cloud Automation Manager: Advanced Cloud
•VMware vRealize: Advanced Cloud
PowerVC provides a systems management product that enterprise customers require to manage effectively the advanced features that are offered by IBM premium hardware. It reduces resource use and manages workloads for performance and availability.
For more information about PowerVC, see IBM PowerVC Version 2.0 Introduction and Configuration, SG24-8477.
5.3 Digital transformation and IT modernization
Digital transformation is the process of using digital technologies to create business processes or modify existing ones.
It also means changing the culture and experiences to meet the changing needs of the business and the market. This reimaging of business in the digital age is digital transformation.
For IBM, digital transformation takes a customer-centric and digital-centric approach to all aspects of a business, from business models to customer experiences, processes, and operations. It uses artificial intelligence (AI), automation, hybrid cloud, and other digital technologies to leverage data and drive intelligent workflows, faster and smarter decision-making, and a real-time response to market disruptions. Ultimately, it changes customer expectations and creates business opportunities.
To date, one of the main technologies that is recognized to enable the digital transformation and the path to application modernization is Red Hat OpenShift. There are advantages to associate Red Hat OpenShift with the IBM Power processor-based platform.
5.3.1 Application and services modernization
Modernizing applications and services (both legacy and cloud-native) on containers that are deployed through a platform that is designed with Kubernetes orchestration at its core is arguably the most forward-looking strategy any business will benefit from. Unsurprisingly, it is also at the heart of the IBM and Red Hat strategy for the hybrid multicloud reality of tomorrow's digital landscape.
Red Hat OpenShift is a container orchestration platform that is based on Kubernetes that helps develop containerized applications with open-source technology. It facilitates management and deployments in hybrid and multicloud environments by using full-stack automated operations.
Containers are key elements of the IT transformation and journey toward modernization. Containers are software executable units in which the application code is packaged, along with its libraries and dependencies, in common ways so that it can be run anywhere, both on desktop and on any type of server or on the cloud. To do this task, containers take advantage of a form of OS virtualization in which OS functions are used effectively both to isolate processes and to control the amount of CPU, memory, and disk that those processes have access to.
Containers are small, fast, and portable because unlike a VM, they do not need to include a guest OS in every instance, and can instead simply leverage the functions and resources of the host OS.
Containers first appeared decades ago with releases such as FreeBSD jails and
AIX Workload Partitions (WPARs), but most modern developers remember 2013 as the beginning of the modern container era with the introduction of Docker.
AIX Workload Partitions (WPARs), but most modern developers remember 2013 as the beginning of the modern container era with the introduction of Docker.
One way to better understand a container is to understand how it differs from a traditional VM. In traditional virtualization (both on-premises and in the cloud), a hypervisor is used to virtualize the physical hardware. Each VM contains a guest OS, a virtual copy of the hardware that the OS requires to run, with an application and its associated libraries and dependencies.
Instead of virtualizing the underlying hardware, containers virtualize the OS (usually Linux) so that each individual container includes only the application and its libraries and dependencies. The absence of the guest OS is the reason why containers are so light, fast, and portable.
With IBM Power, you enable the possibility of having a high container ratio per core with multiple CPU threads and co-localized cloud-native applications and applications that are related to AIX, which use API connections to business-critical data for higher bandwidth and lower latency than other technologies. Only with IBM Power do you have a flexible and efficient usage of resources, manage peaks, and support both traditional and modern workloads with the eventual support of Capacity on Demand (CoD) or sharing processor pools.
The Red Hat Ansible product complements the solution with best-in-class automation.
5.3.2 System automation with Ansible
Enterprises can spend much precious administrative time performing repetitive tasks and using manual processes. Tasks such as updating, patching, compliance checks, provisioning new VMs or LPARs, and ensuring that the correct security updates are in place, are taking time away from more valuable business activities.
The ability to automate by using Ansible returns valuable time to the system administrators.
Red Hat Ansible Automation Platform for IBM Power is fully enabled, so enterprises can automate several tasks within AIX and Linux that include deploying applications. Ansible also can be combined with HMC, PowerVC, and Power Virtual Server to provision infrastructure anywhere you need, including cloud solutions from other IBM Business Partners or third-party providers based on IBM Power processor-based servers.
A first task after the initial installation or setup of a new LPAR is to ensure that the correct patches are installed. Also, extra software (whether it is open-source software, independent software vendor (ISV) software, or perhaps the business’ own enterprise software) must be installed. Ansible features a set of capabilities to roll out new software, which makes it popular in Continuous Delivery/Continuous Integration (CD/CI) environments. Orchestration and integration of automation with security products represent other ways in which Ansible can be applied within the data center.
Despite the wide adoption of AIX in many different business sectors by different types of customers, Ansible can help introduce IBM Power processor-based technology to customers who believe that AIX skills are a rare commodity that is difficult to find in the marketplace but want to take advantage of all the features of the hardware platform. The Ansible experience is identical across IBM Power or x86 processor-based technology, and the same steps can be repeated in IBM Cloud.
AIX skilled customers also can benefit from the extreme automation solutions that are provided by Ansible.
The IBM Power processor-based architecture features unique advantages over commodity server platforms such as x86 because the engineering teams that are working on the processor, system boards, virtualization. and management appliances collaborate closely to ensure an integrated stack that works seamlessly. This approach is in stark contrast to the multivendor x86 processor-based technology approach, in which the processor, server, management, and virtualization must be purchased from different (and sometimes competing) vendors.
The IBM Power stack engineering teams work closely to deliver an enterprise server platform, which results in an IT architecture with industry-leading performance, scalability, and security (see Figure 5-3).
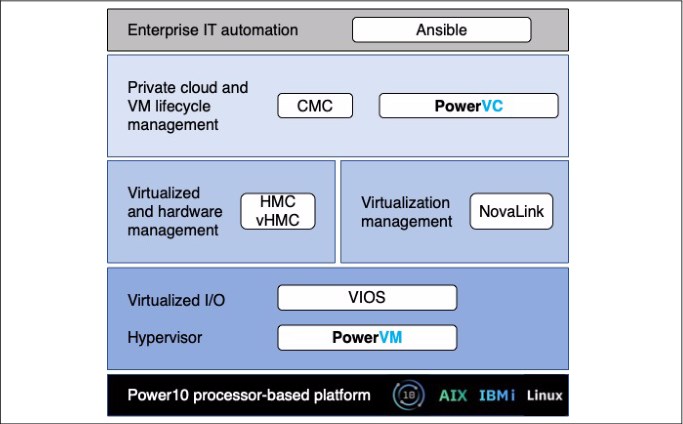
Figure 5-3 IBM Power stack
Every layer in the IBM Power stack is optimized to make the Power10 processor-based technology the platform of choice for mission-critical enterprise workloads. This stack includes the Ansible Automation Platform, which is described next.
Ansible Automation Platform
Ansible Automation Platform integrates with IBM Power processor-based technology, which is included in the Certified Integrations section of the Red Hat Ansible website.
The various Ansible collections for IBM Power processor-based technology, which (at the time of writing) were downloaded more than 25,000 times by customers, are now included in the Red Hat Ansible Automation Platform. As a result, these modules are covered by the Red Hat 24x7 enterprise support team, which collaborates with the respective IBM Power processor-based technology development teams.
IBM Power in the Ansible ecosystem
A series of Ansible collections is available for the IBM Power processor-based platform. A collection is a group of modules, playbooks, and roles. By embracing Ansible in the
IBM Power community, the AIX and IBM i communities have the right set of modules that are available. Some examples are development of tools to manage AIX logical volumes, which put module interfaces over the installation key command, or managing the AIX init tab entries.
IBM Power community, the AIX and IBM i communities have the right set of modules that are available. Some examples are development of tools to manage AIX logical volumes, which put module interfaces over the installation key command, or managing the AIX init tab entries.
|
Note: The Power E 1050 server does not support IBM i.
|
Our OS teams develop modules that are sent to the Ansible open-source community (named Ansible Galaxy). Every developer can post any object that can be a candidate for a collection in the open Ansible Galaxy community and possibly certified to be supported by IBM with a subscription to Red Hat Ansible Automation Platform (see Figure 5-4).

Figure 5-4 IBM Power content in the Ansible ecosystem
Ansible modules for AIX
The IBM Power AIX collection, as part of the broader offering of Ansible Content for
IBM Power, is available from Ansible Galaxy and has community support.
IBM Power, is available from Ansible Galaxy and has community support.
The collection includes modules and sample playbooks that help to automate tasks. You can find it at this web page.
Ansible modules for HMC
IBM Power HMC collection provides modules that can be used to manage configurations and deployments of HMC systems. The collection content helps to include workloads on
IBM Power processor-based platforms as part of an enterprise automation strategy through the Ansible ecosystem.
IBM Power processor-based platforms as part of an enterprise automation strategy through the Ansible ecosystem.
For more information about this collection, see this web page.
Ansible modules for VIOS
The IBM Power VIOS collection provides modules that can be used to manage configurations and deployments of IBM Power VIOS systems. The collection content helps to include workloads on IBM Power processor-based platforms as part of an enterprise automation strategy through the Ansible system.
For more information, see this web page.
Ansible modules for Oracle on AIX
This repository contains a collection that can be used to install an Oracle single instance database 19c on AIX OS and that creates a test database on an AIX file system and on Oracle ASM. This collection automates the Oracle 19c database installation and creation steps.
For more information, see this web page.
Ansible modules for Oracle RAC on AIX
This collection provides modules that can be used to install Oracle 19c RAC on AIX OS. This collection also automates the Oracle 19c RAC installation and creation steps.
For more information, see this web page.
Ansible modules for SAP on AIX
The Ansible Content for SAP Software on AIX provides roles to automate administrator tasks for SAP installations on AIX, such installing the SAP Host Agent, starting and stopping SAP instances, and upgrading the SAP kernel.
For more information, see this web page.
5.4 Protecting trust from core to cloud
The IT industry has long relied on perimeter security strategies to protect its most valuable assets, such as user data and intellectual property. Using firewalls and other network-based tools to inspect and validate users entering and leaving the network is no longer enough because digital transformation and the shift to a hybrid cloud infrastructure are changing the way industries do business.
Many organizations also are adapting their business models, and many organizations have thousands of people connecting from home computers outside the control of an IT department. Users, data, and resources are scattered worldwide, making it difficult to connect them quickly and securely. Without a traditional local infrastructure for security, employees' homes are more vulnerable to compromise, putting the business at risk.
Many companies are operating with a set of security solutions and tools even without them being fully integrated. As a result, security teams spend more time on manual tasks. They lack the context and information that are needed to effectively reduce their organization's attack surface. Rising data breaches and rising global regulations have made securing networks difficult.
Applications, users, and devices need fast and secure access to data, so much so that an entire industry of security tools and architectures was created to protect them.
Although enforcing a data encryption policy is an effective way to minimize the risk of a data breach that, in turn, minimizes costs, only a few enterprises at the worldwide level have an encryption strategy that is applied consistently across the entire organization, largely because it adds complexity, costs, and negatively affects performance, which means missed service-level agreements (SLAs) to the business.
The rapidly evolving cyberthreat landscape requires focus on cyber-resilience. Persistent and end-to-end security is the only way to reduce exposure to threats.
Prevention is the best protection
Since prevention is the best protection, Power10 processor-based servers provide industry leading isolation, and integrity that help prevent ransomware from being installed. The following features and implementation help customers protect their businesses:
•Host/firmware secure and trusted boot.
•Guest OS secure boot (AIX now, and Linux upcoming).
•Built-in OS runtime integrity: AIX Trusted Execution, and Linux IMA.
•Most secure multi-tenant environment with orders of magnitude lower Common Vulnerabilities and Exposures (CVEs) versus x86 hypervisors.
•Orders of magnitude lower CVEs for AIX.
•Simplified patching with PowerSC.
•Multi-factor authentication (MFA) with PowerSC MFA.
Early detection is critical
Integrated security and compliance management with PowerSC makes it harder to misconfigure and easier to detect anomalies. Offerings such as IBM Security QRadar® enhance inherent security with early anomaly detection.
Fast and efficient recovery
It is easier to deploy resiliency strategies with IBM PowerHA and IBM Storage Safeguarded Copy, and by leveraging IBM Storage and security services for fast detection and automated recovery of affected data.
5.4.1 Power10 processor-based technology integrated security ecosystem
IBM Power processor-based platforms always offer the most secure and reliable servers in their class. Introducing Power10 processor-based technology in 2021, IBM further extended the industry-leading security and reliability of the IBM Power processor-based platform with a focus on protecting applications and data across all the hybrid cloud environments. IBM also introduced significant innovations along the following major dimensions:
•Advanced data protection that offers simple to use and efficient capabilities to protect sensitive data through mechanisms such as encryption and MFA.
•Platform security ensures that the server is hardened against tampering, continuously protects its integrity, and ensures strong isolation among multi-tenant workloads. Without strong platform security, all other system security measures are at risk.
•Security innovation for modern threats helps you stay ahead of new types of cybersecurity threats by using emerging technologies.
•Integrated security management addresses the key challenge of ensuring correct configuration of the many security features across the stack, monitoring them, and reacting if unexpected changes are detected.
The Power10 processor-based servers are enhanced to simplify and integrate security management across the stack, which reduces the likelihood of administrator errors.
In the Power10 processor-based scale-out servers, all data is protected by a greatly simplified end-to-end encryption that extends across the hybrid cloud without detectable performance impact and prepares for future cyberthreats.
Power10 processor-core technology features built-in security integration:
•Stay ahead of current and future data threats with better cryptographic performance and support for quantum-safe cryptography and fully homomorphic encryption (FHE).
•Enhance the security of applications with more hardened defense against return-oriented programming (ROP) attacks.
•Simplified single-interface hybrid cloud security management without any required setup.
•Protect your applications and data with the most secure VM isolation in the industry with orders of magnitude lower CVEs than hypervisors that are related to x86 processor-based servers.
Also, workloads on the Power10 processor-based scale-out servers benefit from cryptographic algorithm acceleration, which allows algorithms, such as Advanced Encryption Standard (AES), SHA2, and SHA3 to run significantly faster than Power9 processor-based servers on a per core basis. This performance acceleration allows features, such as AIX Logical Volume Encryption, to be enabled with low performance overhead.
5.4.2 Crypto engines and transparent memory encryption
Power10 processor-based technology is engineered to achieve faster encryption performance compared to IBM Power9 processor-based servers. Power10 processor-based scale-out servers are updated for today’s most demanding standards and anticipated future cryptographic standards, such as post-quantum and FHE, and brings new enhancements to container security.
Transparent memory encryption is designed to simplify encryption and support end-to-end security without affecting performance by using hardware features for a seamless user experience. The protection that is introduced in all layers of an infrastructure is shown in Figure 5-5.

Figure 5-5 Protecting data in memory with transparent memory encryption
5.4.3 Quantum-safe cryptography support
To be prepared for the quantum era, the Power10 processor-based server is built to efficiently support future cryptography, such as quantum-safe cryptography and FHE. The software libraries for these solutions are optimized for the Power10 processor-based chip ISA, and they are or will be available in the respective open source communities.
Quantum-safe cryptography refers to the efforts to identify algorithms that are resistant to attacks by classical and quantum computers in preparation for the time when large-scale quantum computers are built.
Homomorphic encryption refers to encryption techniques that permit systems to perform computations on encrypted data without decrypting the data first. The software libraries for these solutions are optimized for the IBM Power processor-based chip ISA.
5.4.4 IBM PCIe3 Crypto Coprocessor BSC-Gen3 4769
IBM PCIe3 Crypto Coprocessor BSC-Gen3 4769 (#EJ37) provides hardware security protection for the most sensitive secrets. It supports IBM AIX, IBM i without VIOS, or supported distributions of Linux OSs.
|
Note: The Power E 1050 server does not support IBM i.
|
IBM PCIe3 Crypto Coprocessor BSC-Gen3 4769 provides a comprehensive set of cryptographic functions, including the common AES, Triple Data Encryption Standard (TDES), Rivest-Shamir-Adleman (RSA), and error correction code (ECC) functions for data confidentiality and data integrity support. In addition, IBM Common Cryptographic Architecture (CCA) features extensive functions for key management and many functions of special interest to the banking and finance industry.
The co-processor holds a security-enabled subsystem module and batteries for backup power. The hardened encapsulated subsystem contains two sets of two 32-bit PowerPC 476FP reduced-instruction-set-computer (RISC) processors running in lockstep with cross-checking to detect soft errors in the hardware.
It also contains a separate service processor that is used to manage:
•Self-test and firmware updates.
•RAM, flash memory, and battery-powered memory.
•Secure time-of-day.
•Cryptographic quality random number generator.
•AES, Data Encryption Standard (DES), TDES, Hash-Based Message Authentication Code (HMAC), Cipher-based Message Authentication Code (CMAC), MD5, and multiple Secure Hash Algorithm (SHA) hashing methods.
•Modular-exponentiation hardware, such as RSA and ECC.
•Full-duplex direct memory access (DMA) communications.
A security-enabled code-loading arrangement allows control program and application program loading and refreshes after co-processor installation in your server.
IBM offers an embedded subsystem control program and a cryptographic API that implements the CCA Support Program that can be accessed from the internet at no charge to the user.
The 4769 PCIe Cryptographic Coprocessor is designed to deliver the following functions:
•X.509 certificate services support.
•American National Standards Institute (ANSI) X9 TR34-2019 key exchange services that use the public key infrastructure (PKI).
•Elliptic Curve Digital Signature Algorithm (ECDSA) secp256k1.
•CRYSTALS-Dilithium, a quantum-safe algorithm for digital signature generation and verification.
•An RSA algorithm for digital signature generation and verification with keys up to 4096 bits.
•High-throughput SHA, MD5 message digest algorithm, HMAC, CMAC, DES, TDES, and AES-based encryption for data integrity assurance and confidentiality, including AES Key Wrap (AESKW) that conforms to ANSI X9.102.
•Elliptic-curve cryptography for digital signature and key agreement.
•Support for smart card applications and personal identification number (PIN) processing.
•Secure time-of-day.
•Visa Data Secure Platform (DSP) point-to-point encryption (P2PE) with standard Visa format-preserving encryption (FPE) and format-preserving, Feistel-based Format Preserving Encryption (FF1, FF2, and FF2.1). Format Preserving Counter Mode (FPCM) is defined in ANSI x9.24 Part 2.
5.4.5 IBM PowerSC support
Power10 processor-based scale-out servers benefit from the integrated security management capabilities that are offered by:
•IBM PowerSC.
•The IBM Power software portfolio for managing security and compliance on every
IBM Power processor-based platform that is running AIX.
IBM Power processor-based platform that is running AIX.
•The supported distributions and versions of Linux.
•PowerSC is introducing more features to help customers manage security end-to-end across the stack to stay ahead of various threats. Specifically, PowerSC 2.0 adds support for Endpoint Detection and Response (EDR), host-based intrusion detection, block listing, and Linux.
Security features are beneficial only if they can be easily and accurately managed. Power10 processor-based scale-out servers benefit from the integrated security management capabilities that are offered by IBM PowerSC, and the IBM Power software portfolio for managing security and compliance on IBM Power processor-based platforms (AIX and Linux on IBM Power).
PowerSC is sitting on top of the Power solution stack, and it provides features such as compliance automation to help with various industry standards, real-time file integrity monitoring, reporting to support security audits, patch management, and trusted logging.
By providing all these capabilities through a web-based user interface (UI), PowerSC simplifies management of security and compliance.
PowerSC MFA provides additional assurance that only authorized people access the environments by requiring at least one additional authentication factor to prove you are the person that you say that you are. MFA is included in PowerSC 2.0. Because stolen or guessed passwords are still one of the most common ways for hackers to get into systems, having an MFA solution in place allows you to prevent a high percentage of potential breaches.
PowerSC 2.0 also includes EDR. It provides:
•Intrusion Detection and Prevention (IDP)
•Log Inspection and Analysis
•Anomaly detection, correlation, and incident response
•Response triggers
•Event context and filtering
5.4.6 Secure Boot and Trusted Boot
IBM Power servers provide a highly secure server platform. IBM Power10 processor-based hardware and firmware includes PowerVM features to provide a more secure platform for cloud deployment.
The key PowerVM features include:
•A secure initial program load (IPL) process or the Secure Boot feature allows only correctly signed firmware components to run on the system processors. Each component of the firmware stack, including hostboot, the Power Hypervisor, and partition firmware (PFW), is signed by the platform manufacturer and verified as part of the IPL process.
•A framework to support remote attestation of the system firmware stack through a hardware trusted platform module (TPM).
The terms Secure Boot and Trusted Boot have specific connotations. The terms are used as distinct yet complementary concepts.
Secure Boot
The Secure Boot feature protects system integrity by using digital signatures to perform a hardware-protected verification of all firmware components. It also distinguishes between the host system trust domain and the Flexible Service Processor (FSP) trust domain by controlling service processor and service interface access to sensitive system memory regions.
Trusted Boot
The Trusted Boot feature creates cryptographically strong and protected platform measurements that prove that particular firmware components have run on the system. You can assess the measurements by using trusted protocols to determine the state of the system and use that information for security decisions.
5.4.7 Enhanced CPU: baseboard management controller isolation
Separating CPU and service processor trust domains in Power10 processor-based scale-out servers improves protection from external attacks.
Power10 processor-based technology introduces innovations to address emerging threats, specifically with additional features and enhancements to defend against application domain vulnerabilities such as ROP attacks (a security exploit technique that is used by attackers to run code on a target system). This capability uses a new in-core hardware architecture that imparts minimal performance overhead (approximately only 1 - 2% for some sample workloads tested).
The baseboard management controller (BMC) chip is connected to the two network interface cards through Network Connectivity Status Indicator (NCSI) (to support the connection to HMCs) and also have a PCIe x1 connection that connects to the backplane. This connection is used by PowerVM for partition management traffic, but it cannot be used for Guest LPAR traffic. A Guest LPAR needs its physical or virtual network interface PCIe card (or cards) for an external connection.
Hardware assist is necessary to avoid tampering with the stack. The IBM Power platform added four instructions (hashst, hashchk, hashstp, and hashchkp) to handle ROP in
IBM Power ISA 3.1B.
IBM Power ISA 3.1B.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
