Managing and appropriately governing identities using an Identity Governance solution can make a big difference to the security posture of an organization.
To best understand how, we must first learn from our collective past mistakes and omissions. Looking back over recent data breach reports and examining the forensic and post-incident analysis, we notice two things relative to the discussion on identity management controls. The first is that threat sophistication is increasing at a furious rate. The adversary is persistent and well funded and knows where best to attack and pursue persistence. The second is that these forensic reports clearly show that identity management mistakes and weaknesses are the common faults in many breaches. These identity management mistakes and process weaknesses are things like poor account controls; weak passwords; orphan, dormant, and rogue accounts; weak inventory of entitlements; and the over-assignment of user privileges. These mistakes and management missteps tend to be spread across the Cyber Kill Chain.
The Cyber Kill Chain
The Cyber Kill Chain was introduced by Lockheed Martin in the late 1990s and documents the anatomy of a typical cyber breach by plotting the path of attack from start to finish. In many ways, it has become a reference model for cyber defense thinking for more than 20 years.
There are many derivatives of the Cyber Kill Chain approach. We introduced one earlier in this book with the privileged attack chain. We now want to take this concept further and use a view of the formal attack phases to help us better understand where identity attack vectors
are exposed and best mitigated.
Figure 11-1 shows this further adaptation of the formal Cyber Kill Chain model that we will use to highlight where weakness in the IAM system (and its controls) are often at fault. This goes beyond the formal list of identity attack vectors introduced in Chapter 4 and examines the flaws in the underlying systems and infrastructure that get exploited.

Figure 11-1
A summary view of the phases of a typical cyberattack
In the following text, we will use this fictional attack timeline to plot the details and actions of a real-world cyberattack. The details are, in fact, derived from several recent actual breach reports with all identifying information suitably removed. We will first draw out on this timeline how things went wrong. We then come back around and review the same timeline with an emphasis on how and where IAM could have helped prevent and detect the breach. This is set against an event timeline that started in 2016. Analysis of that event and others just like it shows that an average attack can last between 200 and 300 days. Here we see an extended period spanning nearly two years from April 2015 through January 2016.
Reconnaissance
For this breach, things start as they often do with active reconnaissance. The elements of this attack phase are summarized in Figure 11-2. The first phase of the Cyber Kill Chain is all about the adversary gaining knowledge on the target and how best to attack it. As a starting tactic, the attacker will often begin scanning all the externally facing web and network resources the target enterprise has available.
This phase is also when social engineering begins. Anyone and everyone connected with the company – employees, customers, vendors, partners, and so on – will be researched, and those with potential access into the enterprise will be sent blanket phishing emails. Executives and other high-value targets will usually be subject to these spear-phishing campaigns.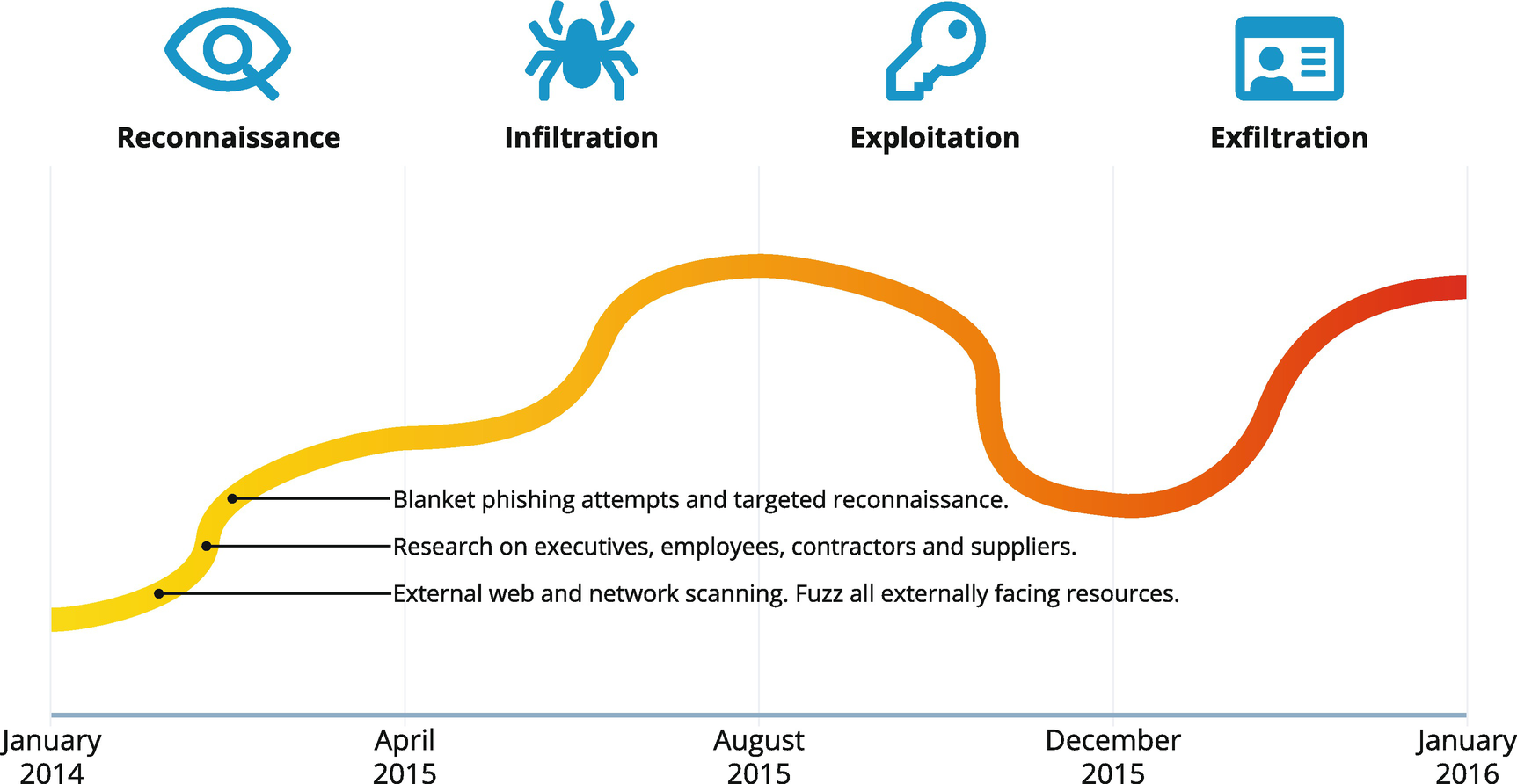

Figure 11-2
Reconnaissance Phase IAM weaknesses
Infiltration
The next phase of our Kill Chain is infiltration; this is summarized in Figure 11-3. With ever-increasing numbers of people accessing our systems and data, eventually someone always makes a mistake. Often that mistake is simply clicking the wrong link in the wrong email. Spear-phishing has become so sophisticated and so widespread that in our scenario, an executive clicked a link that downloaded a basic “drive-by” malware exploit onto their computer. With that exploit successfully executed, the local admin account could be compromised, and the bad guys have access to a wide range of enterprise network resources. With a local admin access, the attacker could move laterally with virtually no limits to attack the organization’s servers, install required attack tooling, and begin scanning the network for further weaknesses.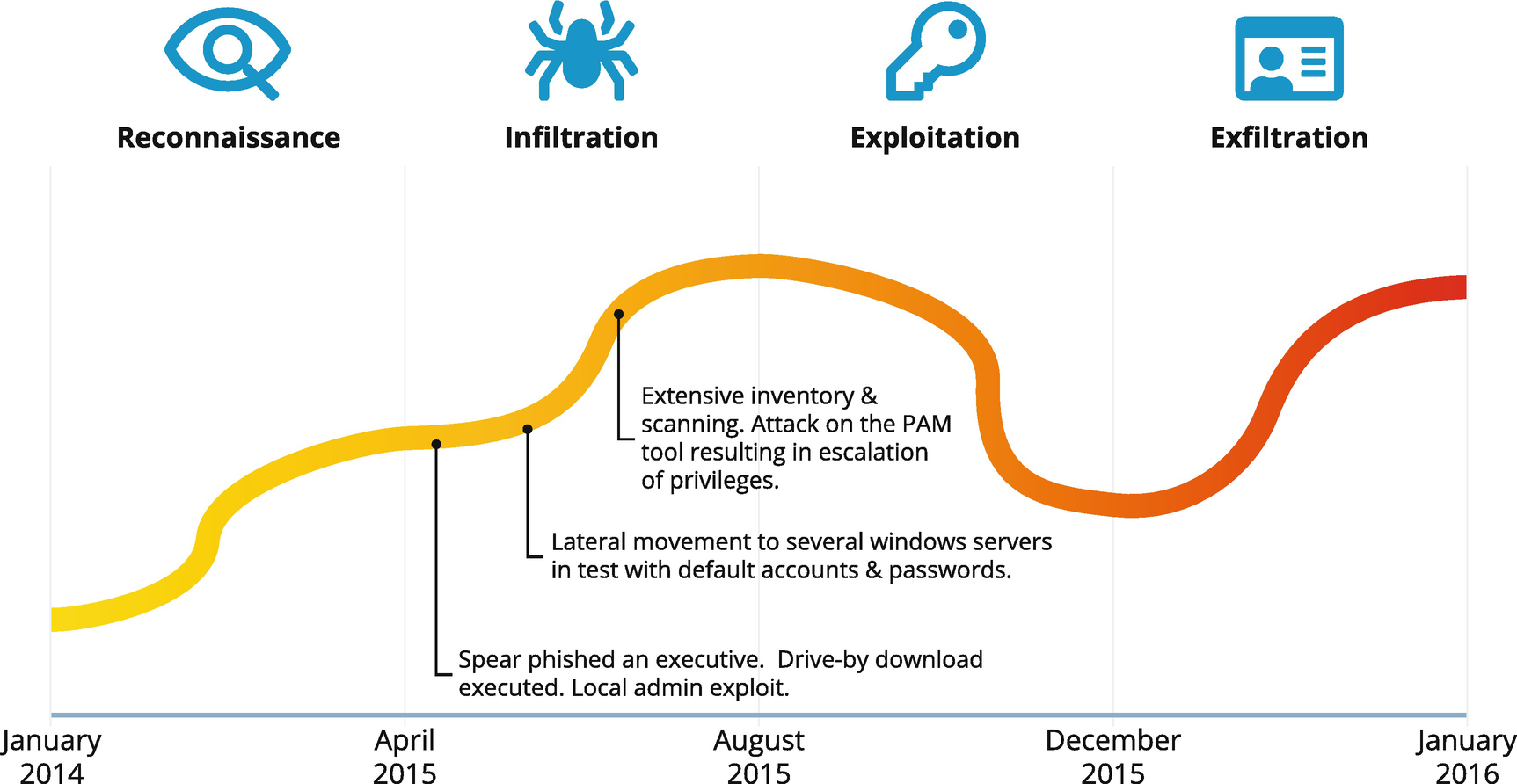

Figure 11-3
Infiltration Phase IAM weaknesses
Exploitation
During this phase of the attack, the attackers have found their way into several resources and are looking for the best ways to gain higher levels of privilege and access to the most valuable data resources. This phase of the attack is highlighted in Figure 11-4. We usually see brute force password attacks on administrative accounts as the most common identity attack vector here. The goal is to compromise more accounts and move laterally. We often see attacks on business processes such as manual access requests and end-user self-service capabilities. When a system of requesting and gaining access is executed over email, messages are easily spoofed, and incorrect access is often granted.

Figure 11-4
Exploitation Phase IAM weaknesses
Exfiltration
Once a good set of target systems are owned, the last phase of the Kill Chain is the exfiltration of data. This is shown in Figure 11-5. This usually involves downloading password databases for internal systems, the collection of customer data, and the theft of intellectual property. We also see archiving and removal of large number of files from internal and cloud file storage systems at this time. And lastly, in more recent attacks, we see the use of ransomware to hold the organization hostage after the adversary has “left the building.”

Figure 11-5
Exploitation Phase IAM weaknesses
Fixing IAM Gaps and Overlaying Governance Controls
With modern identity management software at hand, we can prevent many of the mistakes seen across the typical Cyber Kill Chain. Using IAM best practices, we can overlay governance controls to protect known weaknesses and set out additional detection capabilities that improve situational awareness.

Figure 11-6
Enhanced IAM protection and detection capabilities
In Figure 11-6, we show the array of enhanced IAM protection and detection capabilities available on the market today. These capabilities can be applied across the Cyber Kill Chain. We will now look at each of these capabilities in turn and show how they should be used to create a different outcome:
- Weak Inventory and Cataloging – Default accounts and passwords used during lateral movement can be aggregated, certified, and automatically remediated. Orphan account management can detect the creation of new admin accounts used by attackers. An automated recertification can also be used to highlight escalation of privileges that tends to happen over an extended period.
- Strong Authentication – Strong multifactor authentication and context aware login can prevent and detect lots of issues in the flow of the kill chain. With strong controls over sign-on, internal security teams can identify administrative access that happens at unusual times and from unusual locations. This is true for managing access to the IAM tools themselves. For example, strong authentication should always be used when logging into an Identity Governance system.
- Password Controls – Good password management controls play a significant part in preventing and slowing down the progress of an attack. Strong password policies make cracking and brute-force password attacks computationally time-consuming and costly for the attacker. Identity Governance lifecycle triggers can also be used to alert the security team that account passwords were changing outside of policy controls.
- Lifecycle Management – Account Lifecycle Management sets out an operational baseline for both prevention and detection of compromise. Implementing strong JML state transition controls can help detect out-of-policy changes to the overall assigned entitlement model. Embedded data triggers can easily be used to alert admins and security staff when entitlements are changing. And detective controls and policy checks can catch the escalation of privileges that inevitably happened during a successful attack.
- PAM Governance – The inventory and modeling of any deployed Privilege Account Management (PAM) infrastructure proves essential additional controls and governance. Applying the full suite of IGA best practices to the entitlements managed by the PAM tier is also essential to prevent and detect an attack. We must deliver visibility and certification for access to PAM systems as they are a focus point for attacks. Administrator and root accounts are the keys to the kingdom and the target goal of a threat actor when trying to infiltrate an environment. Inventorying and modeling PAM system assignment and usage, creation, and entitlements is key in preventing identity-based attack vectors.
- Request Controls – Approvals and audit for all new access changes stop the adversary from circumnavigating manual request and fulfillment systems. Preventive policy evaluation helps ensure that only the right people have access and allowing IT security staff to focus on the areas of highest risk.
- File Access Governance – Effective access modeling, data classification, and file access alerts are key controls available throughout the Cyber Kill Chain. During the ever-shortening exfiltration phase, file access governance techniques are an essential means of detecting the kinds of file access events typical to this phase.
