Identity Governance has emerged as a critical building block in enterprise Information Technology (IT) automation, in enterprise security, and in corporate compliance management. It provides a framework for controlling user access and ultimately helping to reduce overall operational risk. Fortunately, there is a good degree of industry consensus around what Identity Governance means, so for the purpose of this book, we offer the following summary definition:
Identity Governance is the technology and processes to ensure that people have appropriate access to applications and systems and that the organization always knows who has access to what, how that access can be used, and if that access conforms to policy.
Who Has Access to What?
Identity Governance is the process of managing who has access to what. Employees, contractors, and business partners all require access to enterprise systems and data. Understanding who does have access, who should have access, and how that access is being used is a critical business and IT security concern. Figure 6-1 helps illustrate this structure.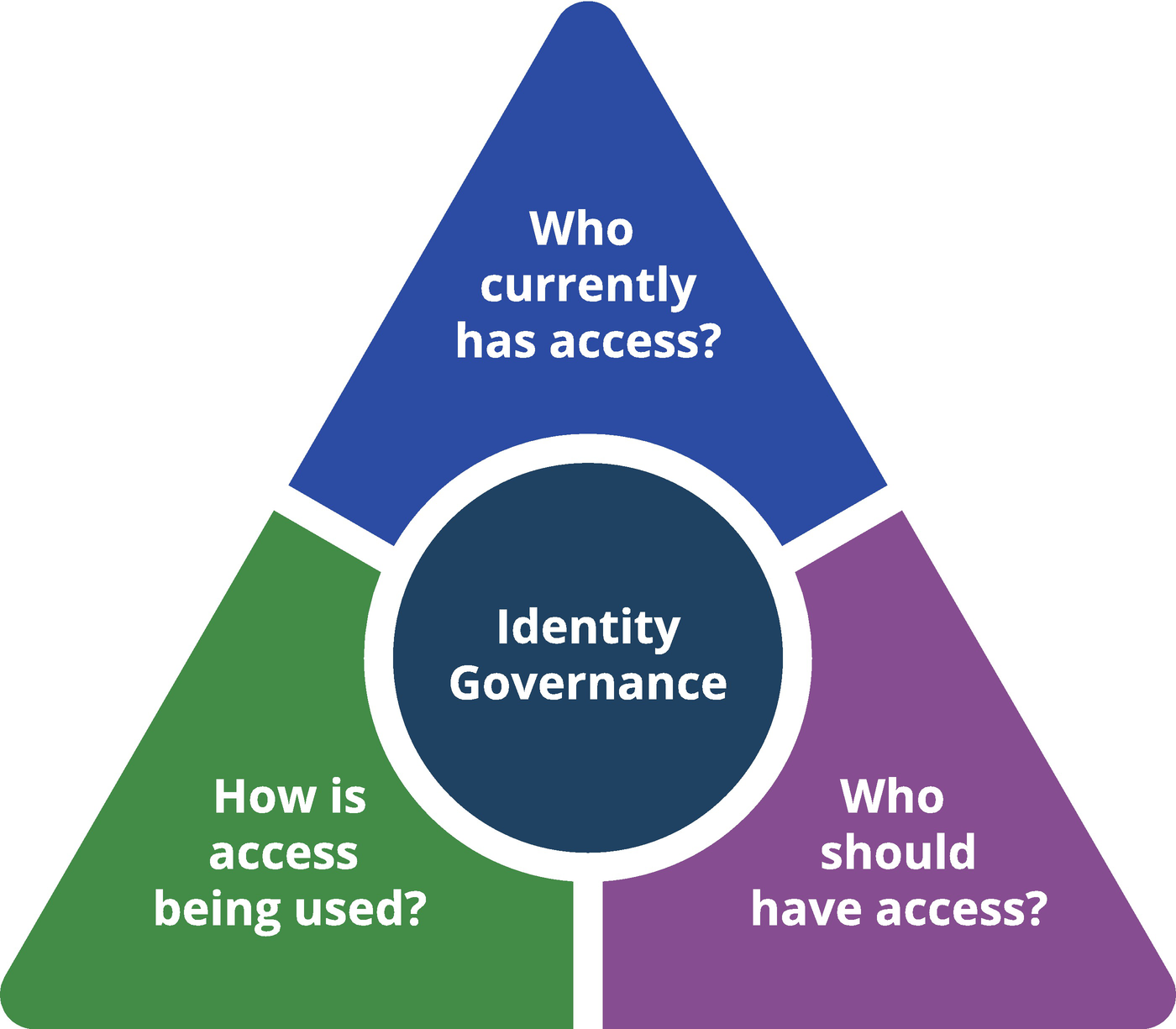

Figure 6-1
Identity Governance is the science of understanding and managing who has access to what across all enterprise data resources
Understanding who does have access is a critical first step in managing the “current state.” In order to manage user access, we have to understand how things are set up today. All IT systems have a history. User access comes and goes over time, and without a diligent system of administration and audit, these systems always trend toward entropy and invalid access. Before any level of validation or update can be made to these systems, we have to understand the current state. To provide a useful example, when using Google Maps on your mobile device, before you can get directions to your destination, their system has to know your current location, where you are – your current state.
Deciding who should have access is a more complex statement of business security policy, often referred to as the “desired state.” Even with an understanding of the current state, before we can update or change it in any way, we have to understand what the configuration should look like afterward. This means defining business rules and understanding appropriate levels of access in advance. Defining appropriate access is a topic we will come back to many times in this book. For now, simply think of this as your Google Maps destination. When the system knows where you are starting from, and where you want to go – your desired state – the system can provide a clear set of driving directions.
Tracking how access is actually being used provides critical input into the overall governance process. All too often, access is provided that is incorrect, unused, or used in an inappropriate manner, and so tracking actual systems usage is key. This process of usage tracking does not imply any breach of user privacy or egregious oversight. It can mean something as simple as monitoring and storing a “last login” date for a given application. Successful best practice shows us that, in order to ensure the ongoing integrity and refinement of the “desired state,” we need usage date. Coming back to the Google Maps example, driving directions are greatly enhanced by understanding current traffic flows. In today’s busy towns and cities, knowing where there is congestion allows mapping systems to provide alternative routes and update recommended directions and estimated time of arrival. The same is true for governance – understanding usage means better controls and more effective security.
Managing the Complexity of User Access
Most organizations today work with a mix of cloud, SaaS, and on-premise systems and applications. Services are delivered through multiple channels and by multiple service providers. Managing access control, regardless of how it is provided to the end user, is the remit of Identity Governance.
User access controls are embedded in our applications, systems, and infrastructure. Each system establishes an access control policy to protect its data. This process of access control often looks simple to those unfamiliar with the process of managing it. People – access – data, how hard can it be (see Figure 6-2)?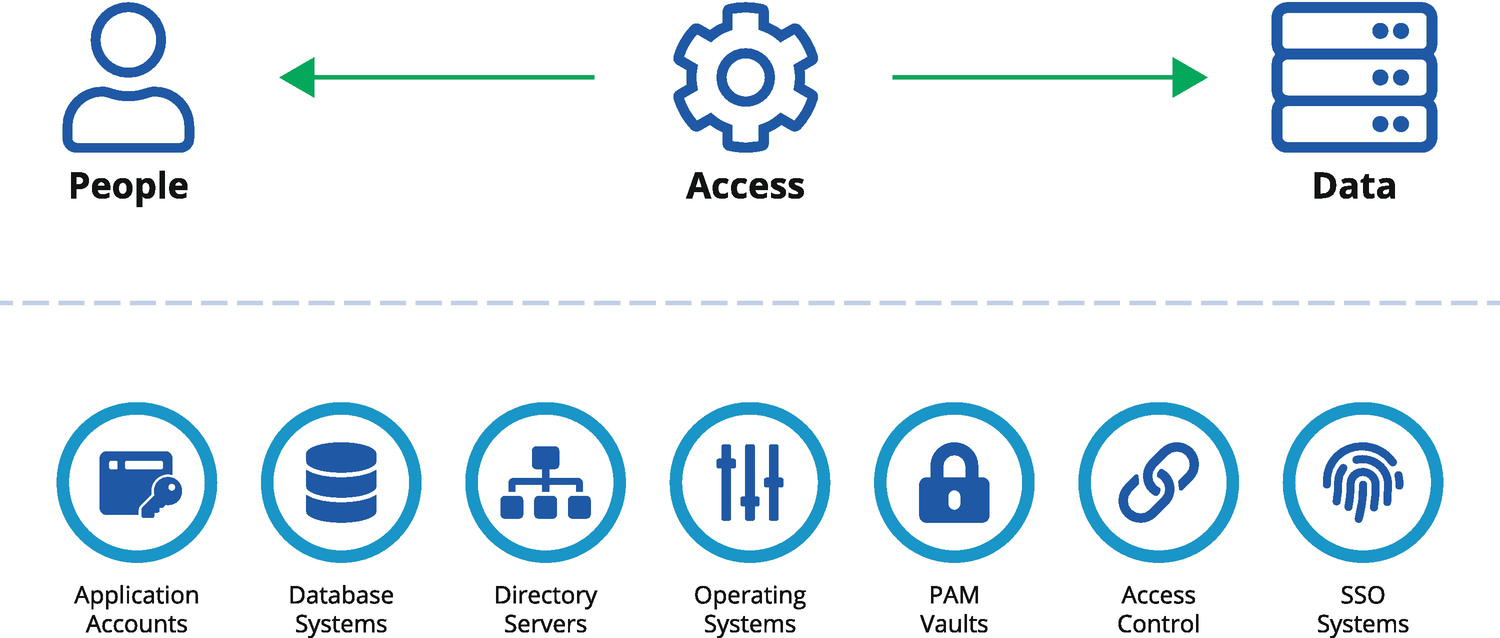

Figure 6-2
The complexity of user access control in enterprise systems spanning embedded and externalized methods of control
- It turns out that consistent, comprehensive, and sustainable management of these various forms of access control requires dedicated focus. For even the smallest organization, the implementation of access control ends up being embedded across application accounts, database systems, directories, operating systems, and a range of external access management solutions like Single Sign-On (SSO) and externalized Attribute-Based Access Control (ABAC) services.
Identity Governance solutions help an organization inventory and analyze and understand what access privileges are granted to employees, contractors, and business partners across these various systems. They deliver automation, controls, and governance for all systems of access wherever they reside. Identity Governance provides a high-level management overlay for identities, users, accounts, privileges, entitlement, and access however they are implemented.
The Scope of the Problem
The scope of control required for Identity Governance today is extensive. In cybersecurity, the phrase “you’re only as strong as the weakest link” is very relevant here. We have to deliver the right access to the right people across all systems, applications, and data. Automation, controls, and governance are required for cloud and on-premise systems and must span the divide between structured and unstructured data storage systems.
A good example of the importance of scope comes from managing financial data. If, for example, we provide amazing governance over access to our core on-premise SAP system (structured data), yet we allow unrestricted access to a spreadsheet of information (unstructured data), extracted from that system, we have a problem. Today, the adversary understands that file shares and unstructured data resources like SharePoint contain valuable enterprise information. It’s our responsibility in Identity Governance to help ensure that controls and oversight are available for these unstructured resources too. We’ll come back to the specific challenges around managing these unstructured systems in a later chapter.
Managing the Full Lifecycle of Access
And finally, a comprehensive approach to Identity Governance must address the full lifecycle of user access. We often use the term in Identity Governance “JML” – this stands for Joiners
, Movers
, and Leavers. This is a phrase taken from the realm of Human Resources and is used to capture the three major states that a typical user access process will go through. Identity Governance is responsible for providing visibility and controls for this full lifecycle.
At each phase of the user’s access lifecycle, Identity Governance is responsible for delivering automation and controls to ensure that the right access is maintained – especially when users move between states. We will address how to approach lifecycle management and provide insight into its best practices in the next chapter.
