Since the inception of networked computing, technologies have increasingly been created with network capabilities allowing them to communicate and exchange data much like the traditional client-server model. Today, technology is being embedded in almost everything that is manufactured, from smartphones, coffee makers, and televisions to automobiles, wearable devices, and more.
The modern development of technology has brought about a new era and there are now millions of devices connected to and that communicate through the Internet. While this development has made our personal and business lives more comfortable and convenient, the Internet of Things (IoT) era raises concerns of security and privacy while presenting challenges of applying existing principles, methodologies, and techniques to gather and process potential evidence when needed.
Brief History of the Internet of Things (IoT)
Ever since the inception of technology, visionaries have imagined a day when machines can communicate with one another without human intervention. Like cloud computing, discussed in Chapter 18, “Forensics Readiness in Cloud Environments,” there were several technological advancements that created the concept of the Internet of Things (IoT) and that have made it what it is today.
One of the first examples of the IoT concept being actualized was in the early 1980s. Developers at Carnegie Melon University developed a program that allowed them to connect—over the Internet—to a refrigerated Coca Cola machine. The software checked the inventory of the appliance to see if there was a drink available and if it was cold.
What could be considered the starting point for IoT dates to the 1830s, when machines were developed for direct communication (i.e., telegraphy). Subsequently, the development and advancement of both computer systems and networking capabilities throughout the 1900s was a major evolution towards the concept of IoT. Formally, the Internet of Things (IoT) as a concept was officially named in 1999 when Kevin Ashton, who was the executive director of Auto-ID Labs at the Massachusetts Institute of Technology (MIT), in a presentation given for Proctor & Gamble, stated that:
Today computers, and, therefore, the Internet, are almost wholly dependent on human beings for information… If we had computer[s] that knew everything there was to know about things, using data they gathered without any help from us, we would be able to t[r]ack and count everything and greatly reduce waste, loss and cost.
By the year 2013, the IoT concept had evolved into a revolutionary concept that enabled most any device with an on/off switch to operate and communicate intelligently with other devices. Now, IoT applies the concept of being always connected, from anywhere and at any time, which has now allowed for people-people, people-things, and things-things connections. These potential relationships introduce new avenues by which personal and business information can be exchanged, new attack vectors (i.e., hacking a toaster to gain access into a network environment), and how or where digital evidence can persist.
What Is the Internet of Things (IoT)?
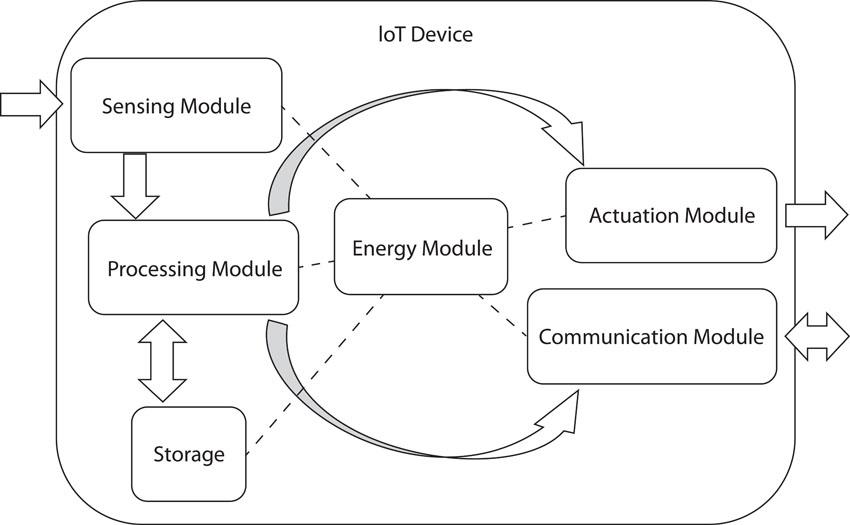
Smart devices falling within the concept of IoT have been in use for some time now in areas such as healthcare, transportation, and home automation. Knowing what classifies any technology device as an IoT device requires understanding the distinguishing characteristic that these technologies possess in comparison to traditional technologies. Illustrated in Figure 20.1, all IoT devices have the following five main modules:
1. Sensor module detects and reacts to:
a. Requests made by a user or other sensor (controlled sensors); or
b. Changes in the local environment (event-driven sensors).
2. Processing module processes information received from sensors and transmits it as needed.
3. Actuation module triggers the physical device to execute the processed results.
4. Communication module transmits data to other devices across networked environments.
5. Energy module manages the availability of power and its consumption for all other IoT modules.
Figure 20.1 IoT module relationships.
Additionally, all IoT devices have the following five main characteristics:
1. Existence: Physical things can be embedded with specific (IoT) technology.
2. Sense of self: Physical things have a sense of identity and can handle data, make decisions, and act autonomously.
3. Connectivity: Physical things can connect openly with other things.
4. Interactivity: Physical things can interoperate and work together regardless of whether human intervention is present.
5. Dynamicity: Physical things can communicate with different things at any time, in any place, and in any capacity.
6. Scalability: Physical things can be expanding and associated across a global network.
7. Computational limitations: The processing unit is not designed to perform specific functions or to perform complex operations.
8. Resource limitations: There is limited onboard capacity to provide an operating environment (i.e., storage, power).
Challenges with the Internet of Things (IoT)
Generally, the goal of IoT is to make our lives more convenient and dynamic by allowing disparate devices to exchange information with each other to provide useful services to the owner. However, it was not necessarily designed with concerns of security or privacy in mind. As result, IoT has created new opportunities for cybercrime to capitalize on these devices as new attack vectors.
Predominantly, IoT devices come in many different form factors that offer varying amounts of onboard storage, primarily only for its operating system (OS). Because of storage limitations, IoT devices are exceptionally volatile in the lifespan to which they keep information, resulting in potential evidence being overwritten quickly. While a simple solution would be to leverage remote logging capabilities for IoT devices, concerns arise about guaranteeing the integrity and authenticity of evidence. Additionally, because IoT devices may not come in the form of traditional computer systems, digital forensics practitioners are faced with complexities of having to gather and process evidence from unusual sources where existing techniques are difficult to apply, such as coffee makers or televisions.
With traditional computer systems, security controls are implemented as a means of safeguarding informational assets. As stated previously, the growth of IoT has raised significant concerns of security because any device can be interconnected and their form factors aren’t designed for security capabilities. For example, IoT introduces new attack vectors whereby threat actors could use an IoT device (e.g., light bulb). Considering this, businesses are faced with storing massive amounts of technology-generated data, and they need to develop strategies for securely storing it to serve as potential digital evidence if (or when) required.
Sensors and camera have become quite commonplace, allowing for information to be gathered and in some cases, without knowledge or ways to avoid it. This makes people uncomfortable knowing that information about them is being collected and, once it’s been collected, they have little to no control over who has access to it.
Evidence Gathering and Processing
With IoT, devices can be widespread and located outside the organization’s span of control, such as in the cloud, in a third-party facility, or at a person’s residence. Because of this, the collection and preservation of IoT evidence can prove challenging when digital content is created, transferred, stored, and accessed across an interconnected and geographically distributed network of devices.
Technology-generated data generated from one IoT device or another may not be created or stored in a consistent structure or format. As result, digital forensics practitioners are experiencing difficulties when using existing digital forensics equipment and tools to gather and process digital evidence from IoT devices.
Forensics Readiness Methodology
Digital forensics investigations involving IoT devices require organizations to be proactive and develop strategies so that they are prepared to respond when required to. Pre-investigative readiness components are essential to ensure investigative techniques are prepared before an incident involving IoT devices occurs.
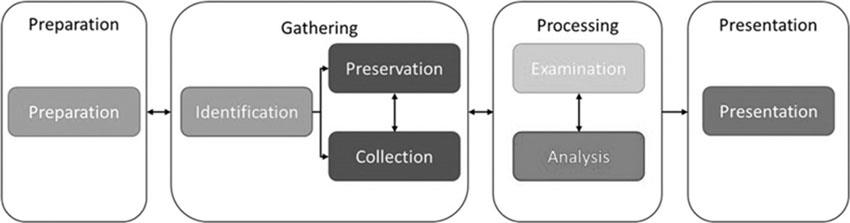
Following traditional methodologies, as illustrated in Figure 20.2 and discussed further in Chapter 2, “Investigative Process Methodology,” digital forensics investigations normally follow an approach whereby evidence is searched for (identified), seized (collected and preserved), and analyzed (processed). However, traditional investigative methodologies were not designed with IoT in mind and, given the variety and (potential) location of these devices, following this traditional approach to digital forensics investigations may not be suitable.
Alternatively, organizations need to optimize their investigative process by taking proactive steps to guarantee that evidence will be readily available if (and when) needed from IoT devices. Throughout the sections below, each step outlined for implementing digital forensics readiness will be discussed as it relates to improving investigative capabilities with IoT devices.
Figure 20.2 High-level digital forensics process model.
Step #1: Define Business Risk Scenarios
Digital forensics investigations involving IoT devices require organizations to follow a proactive approach whereby controls and measures have been implemented to guarantee digital evidence will be available if (and when) needed.
However, IoT devices are equipped with limited onboard hardware and scoped user interfaces such that technology-stored data cannot exist. Because technology-stored data is not created or stored on IoT devices, it is likely that all six business risk scenarios will not apply. For example, civil litigation matters are primarily concerned with producing electronically stored information (ESI) in the form of technology-stored data, with the understanding that some litigation matters will require technology-generated data to be produced.
Rather than assuming the use of IoT devices will limit the span of business risk scenarios, it is recommended to ensure all six scenarios are included right from the outset of enabling mobile device technologies. By doing so, organizations establish a wide scope of risk that allows them to be better positioned for focusing on specifics rather than establishing a narrow scope and having to expand after having identified missed evidence.
1. Reducing the impact of cybercrime
2. Validating the impact of cybercrime
3. Producing evidence to support organizational disciplinary issues
4. Demonstrating compliance with regulatory or legal requirements
5. Effectively managing the release of court-ordered data
6. Supporting contractual and commercial agreements
Refer to Chapter 7, “Defining Business Risk Scenarios,” for further discussion on the six business risk scenarios as they apply to digital forensics readiness.
Step #2: Identify Potential Data Sources
Knowing that IoT devices differ from traditional computer systems in design and capabilities, the potential for evidence to exist from one device to the next can vary. However, it is still important to keep in mind that evidence can exist on these devices, and it could be relevant to an investigation.
Generally, there are two classifications of IoT devices in use today: informational and special-purpose. Interactive devices—such as vehicle consoles and smart watches—are primarily considered informational devices because, from a systems perspective, they act as proxies for humans to suggest actions and provide sensors for input. Special-purpose devices have scoped interfaces to provide specific functionality, such as temperature sensors. When an informational device is identified as an evidential data source, there is potential for both technology-stored and technology-generated data to exist. However, when a special-purpose device is identified as an evidential data source, there is no capability for human interactions that allow for data to be created, thus limiting the potential that technology-generated data will exist and that only technology-generated will be available.
With both classifications of IoT devices, the following are three types of data that can be sourced from IoT devices:
• Passive data is any technology-generated data that requires IoT sensors to be activated, such as through an application programming interface (API), before the data is created.
• Active data is any technology-generated data that is created by persistently active IoT sensors in real time.
• Dynamic data is any technology-generated data that is created by IoT sensors, in real time, as result of communications with other modules or IoT applications and devices.
It is common to encounter any combination of data types (passive, active, or dynamic) from one classification of IoT device to the next. Understanding what evidence can be gathered from IoT devices requires the organization to (1) have control over what IoT devices can exist within their environment and (2) be able to routinely and proactively discover IoT devices.
Step #3: Determine Collection Requirements
With IoT devices, gathering and processing evidence is not as straightforward as it is with ESI located within an organization’s traditional computer systems and technologies. For example, because IoT devices have limited onboard storage, cloud computing environments are used to store data. This means that with IoT forensics, organizations need to consider the collection of digital evidence from one of the following three generic groups where ESI is located on:
• IoT devices and sensors
• Hardware and software that connect IoT devices within the scope of the organization’s control
• Hardware and software that connect IoT devices outside the scope of the organization’s control
With each of the above generic groups, there are three requirements that organizations should adopt to ensure digital evidence being gathered is done in a way that guarantees legal admissibility:
• Time synchronization is a big concern given the potential for latency or jitter than can result from the network connectivity and communications provided in most IoT devices today. Where technology permits, and the IoT device is under the organization’s span of control, it is recommended that a managed and centralized time service solution be used (e.g., network time protocol [NTP]).
• Memory and storage resources must be available for digital forensics practitioners to gather and process the potentially large volumes of technology-generated data created by IoT devices. Careful planning of storage and processing requirements for IoT forensics must be done to accommodate both short-term and long-term storage requirements.
• Communication within the organization’s networked environment is critical to ensure that potential evidence from technology-generated data being created by IoT devices can be extracted quickly. Organizations should develop a centralized storage facility, such as an enterprise data warehouse (EDW), as a solution for storing IoT device data.
Refer to Chapter 9, “Determine Collection Requirements,” for further discussion about requirements for gathering digital evidence.
Step #4: Establish Legal Admissibility
As discussed previously throughout this book, we know that evidence, whether physical or digital, is fragile and is subject to tampering, modification, or erasure. With all (physical or digital) evidence, maintaining a chain of custody is required to guarantee authenticity and integrity as a means of establishing legal admissibility.
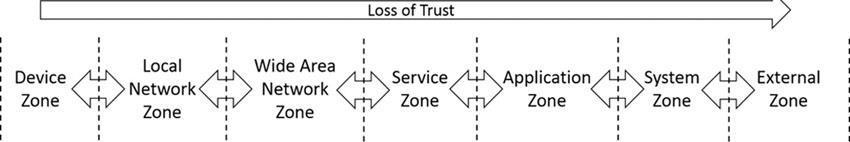
Like the layers of trust with cloud computing environments, as discussed in Chapter 18, “Forensics Readiness in Cloud Environments,” there are several technology zones where digital evidence can exist for IoT. Each of these trust zones was designed to provide a broad segmentation of its own data, along with its own authentication and authorization requirements, that can be used to isolate damage and restrict impact to lower trust zones. Generally, zones of trust found within IoT include the following:
• Device zone is the immediate physical space located around the device where access can be gained.
• Local network zone is any system that enables and controls communication to directly connected devices in a private network environment.
• Wide area network zone is any system that enables and controls communication to devices located across public network environments.
• Service zone is any software component or module that interfaces with devices through a networked environment.
• Application zone is any software component or module that provisions, develops, stores, or manages service and associated datasets.
• System zone is any technology infrastructure used to support the software components or modules.
• External zone is any subject or object that remotely interacts with the system but is not under the control of the application.
Because each zone is logically separated by a trust boundary, as illustrated in Figure 20.3, information transitioning between neighboring adjoining zones can be susceptible to malicious or unwanted access, interference, or disclosure. Understanding these risks and developing appropriate countermeasures requires completing both a threat model and risk assessment following proven and documented frameworks.
Where concerns about trust do exist with IoT devices, it is important that organizations have developed solutions to identify and secure IoT located throughout their (managed) network environment so that when an incident involving IoT does occur, required evidence will be available. Like the multiple layers of interactions found throughout enterprise technology stacks where security controls can be deployed and implemented, as illustrated in Figure 20.3, these security controls can also be leveraged to enhance forensics capabilities with IoT devices by placing controls closer to the actual data as a means of protection.
Refer to Chapter 3, “Digital Evidence Management,” for further discussion about data-centric security.
Refer to Chapter 10, “Establishing Legal Admissibility,” for further discussion about strategies for establishing and maintaining legal admissibility.
Refer to Addendums E and F, “Risk Assessment” and “Threat Modeling,” for further discussion on the framework and methodologies to follow.
Step #5: Establish Secure Storage and Handling
Generally, IoT devices are extremely volatile by design, largely due to the dynamic nature of the technologies and the varying levels of trust that exist. Considering the zones of trust illustrated previously in Figure 20.3, there can be concerns about the integrity of information at any layer, requiring organizations to implement strategies for addressing these potential issues. Because of this, unlike traditional computing environments, all ESI deemed relevant and meaningful as potential digital evidence needs to have an elevated degree of security controls implemented to safeguard its integrity and authenticity.
Figure 20.3 IoT trust zones.
For example, considering that IoT devices have limited onboard resources (i.e., storage capacity), the technology-generated data they create is often only available for short-lived periods. Given the potential volatile conditions of these devices, it is important that ESI serving as relevant digital evidence be secured while in use, in transit, and at rest. At a minimum, the following control mechanisms should be implemented (where possible) to guarantee the secure storage and handling of potential evidence in a cloud environment:
• Real-time logging of technology-generated data (i.e., log files) to a remote and centralized repository, such as an enterprise data warehouse (EDW), to address concerns of data volatility on IoT devices
• One-way cryptographic hash algorithm, such as the Message Digest Algorithm family (i.e., MD5, MD6)or the Secure Hashing Algorithm family (i.e., SHA-1, SHA-2, SHA-3), to establish and maintain both the integrity and authenticity of ESI
Refer to Chapter 3, “Digital Evidence Management,” for further discussion about data-centric security, technology-generated data, and technology-stored data.
Refer to Chapter 11, “Establish Secure Storage and Handling,” for further discussion about strategies for establishing and maintaining evidence integrity during handling and storage.
Step #6: Enable Targeted Monitoring
IoT devices are increasing being targeted by threat actors in large part because these technologies have weak or no security features or controls. As result, IoT devices can be a significant risk to organizations because of the increased attack surface that can be compromised as a means of gaining access to a controlled and secure network environment.
As with any traditional computer system, enabling an appropriate level of monitoring and detection is necessary for targeting (potentially) malicious activity on IoT devices. Achieving a state of digital forensics readiness within a corporate environment by enabling continuous security monitoring of IoT devices can be achieved through a variety of techniques, such as:
• Asset management and discovery to identify and inventory the presence of IoT devices located through the corporate network environment
• Intrusion detection and prevention systems (IDS/IPS) to inspect and provide alerts about potentially unwanted or malicious network communications associated with IoT devices
• Analytical techniques are approaches to continuous monitoring of an IoT device’s use and operation, such as anomaly detection or machine learning
• Remote logging of technology-generated data to a centralized data repository, such as an EDW, for correlation with other events for improved security intelligence
• Orchestration and automation solutions to programmatically execute playbooks and workflows required to alert and notify of potentially unwanted or malicious activity with IoT devices
Refer to Addendum G, “Data Warehousing Introduction,” for further discussions on the unique designs, capabilities, and purposes of these eco-systems.
Refer to Chapter 12, “Enabling Targeted Monitoring,” for further discussion about analytical techniques that can be utilized for continuous security monitoring.
Step #7: Map Investigative Workflows
With existing digital forensics methodologies, as discussed in Chapter 2, “Investigative Process Methodology,” the devices that can be encountered cannot be switched off at the risk of losing critical volatile data that could be used as evidence. However, following the traditional methodology with IoT devices may not be applicable because of how the unique characteristics (i.e., formats, protocols, interfaces) can complicate the techniques applied for gathering and processing evidence.
Knowing that there are additional considerations in conducting IoT forensics, it is necessary to implement guidelines and processes by which the digital forensics practitioner can gather and process potential digital evidence. The high-level digital forensics process model, as illustrated previously in Figure 20.1, will be applied to the activities and tasks involved in conducting IoT forensics.
As discussed in Chapter 2, ”Investigative Process Methodology,” the activities and tasks performed in this first phase are essential in successfully executing all subsequent phases of the investigative workflow. As a component of the preparation phase, organizations can proactively align their people, processes, and technologies to support their IoT forensics capabilities.
Steps taken to prepare for IoT device are essential for every organization. This requires support from (top-level) management so that appropriate controls can be implemented to ensure the investigative process is holistic and well thought out. For example, the following administrative, physical, and technical controls contribute to an organization’s ability to conduct IoT forensics:
• Establishing which IoT devices are approved to be connected throughout the organization’s network
• Developing a strategy for what standard operating procedures (SOP) are required to gather and process evidence
• Validating that the tools and techniques used are forensically sound and can support investigative requirements
• Maturing digital forensics practitioners who can appropriately gather and process evidence from IoT devices
Refer to Addendum A, “Tool and Equipment Validation Program,” for further discussion on the methodology required for validating and verifying the forensics readiness of digital forensics tools and technologies.
As discussed in Chapter 2, “Investigative Process Methodology,” the second phase of the investigative workflow consists of the activities and tasks involved in the identification, collection, and preservation of digital evidence. The same requirement for establishing the meaningfulness, relevancy, and legal admissibility of digital evidence applies for IoT devices; however, given the unique characteristics of each type of IoT technology, there are additional activities and tasks that need to be performed.
Identification Regardless of the evidence that has been identified, both physical and logical, digital forensics practitioners must follow consistent and repeatable processes to secure, document, and search a crime scene. Sample templates that can be used in the process of securing, documenting, and searching crime scenes have been provided in the Templates section of this book.
Within the vast IoT marketplace, new types of devices are being created with multiple form factors, operating systems (OS), and (wired and wireless) networking capabilities. Because IoT devices can be found in a variety of technologies (e.g., televisions, light bulbs, and heating, ventilation, and air conditioning [HVAC] systems), it is important that organizations have the technical capabilities to scan their entire network environment to detect the presence of IoT devices so that appropriate administrative, physical, and technical controls can be implemented.
The following approaches can be used to identify IoT devices:
• Network discovery to identify the presence of IoT devices located throughout the corporate network environment
• Asset management to maintain an accurate inventory of IoT devices connected to the corporate network environment
• Network access control to isolate connected IoT devices in specific areas of the corporate network environment
• Firewalls and proxies to control how IoT devices connect to the corporate network environment
As discussed previously, IoT devices are not designed with reduced form factors where technology-generated data is extremely volatile, requiring it to be stored in a remote facility to facilitate investigations. By documenting and amalgamating all technical specifications about IoT devices, organizations will be better positioned to answer questions about associated technology-generated data, such as “Where has the ESI come from?” “Where is the ESI stored?” and “What format is the ESI forwarded and stored in?” By building a profile of identified IoT devices, organizations are better equipped to substantiate the authenticity of the ESI and to also narrow the scope of an investigation when IoT devices are involved.
Collection and Preservation IoT devices are different from traditional computer systems because they typically have a limited power supply, lightweight computational resources, minimal storage capability, and extensive networking functionality. When encountering an IoT device, digital forensics practitioners must think about how leaving the device running at the crime scene can risk a potential loss of power or loss of potential evidence.
As a first responder, and considering the order of volatility, a decision needs to be made about whether to leave the device running—and allow data transfers from the scene to continue—or to power it off—and sever existing connections. From previous sections in this chapter we know that evidence volatility with IoT devices is more complex because the lifespan of data is extremely short. Facilitating this decision-making process requires referring to the previous phase of the investigative workflow whereby the technical specifications of the IoT device are documented and relevance can be established. Once relevance has been established via the phases outlined in the overall forensics investigation workflow, the device can be seized and secured as evidence.
Additionally, knowing that IoT devices are resource limited and need to leverage remote repositories for long-term storage of technology-generated data, there is the potential that relevant evidence will need to be sourced from cloud service providers (CSP). This presents challenges when gathering relevant evidence, as organizations may not have established contractual terms and conditions for the CSP to comply with investigative needs, and such situations may require the involvement of law enforcement.
Refer to for further discussion on this phase of the investigation workflow.
Refer to Chapter 18, “Forensics Readiness in Cloud Environments,” for further discussion on gathering evidence from cloud computing environments.
The forensics analysis and examination of IoT devices continues to be a challenge for the digital forensics community. Generally, these challenges are the result of several barriers associated with IoT devices, such as reduced form factors and the absence of available interfaces. Technically, current digital forensics techniques and tools have not reached a level of maturity within the IoT domain that allows for forensics acquisitions to be performed.
However, the digital forensics community continues to invest efforts in developing methodologies and techniques for processing evidence from IoT environments to address the current state of maturity. Refer to Chapter 1, “Understanding Digital Forensics,” for further discussion on the evolutionary cycle of digital forensics.
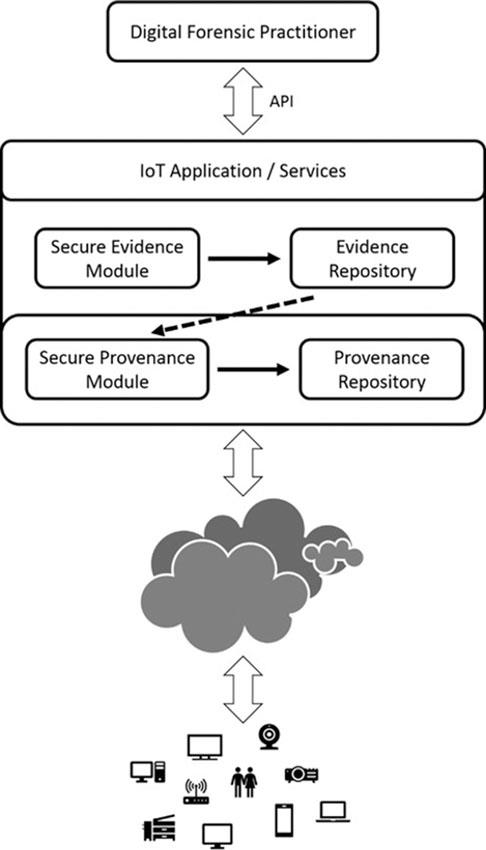
From this research, the proposed forensics-aware IoT (FAIoT) model has been drafted to reduce the challenges in IoT forensics capabilities by providing methodologies and techniques for securing volatile data and establishing higher levels of evidence-based trust. Illustrated in Figure 20.4, the FAIoT model consists of the following three parts:
• The secure evidence preservation module monitors known IoT devices and stores associated ESI in a secure repository.
• The secure provenance module guarantees a complete chain of custody of IoT evidence by maintaining records of access.
• Access to evidence through API provides a secure and read-only connection to IoT devices to gather evidence and access information.
In addition to the FAIoT model, new techniques and methodologies have been proposed to conduct digital forensics investigations in IoT environments. Notably, the following approaches have been proposed for IoT forensics.
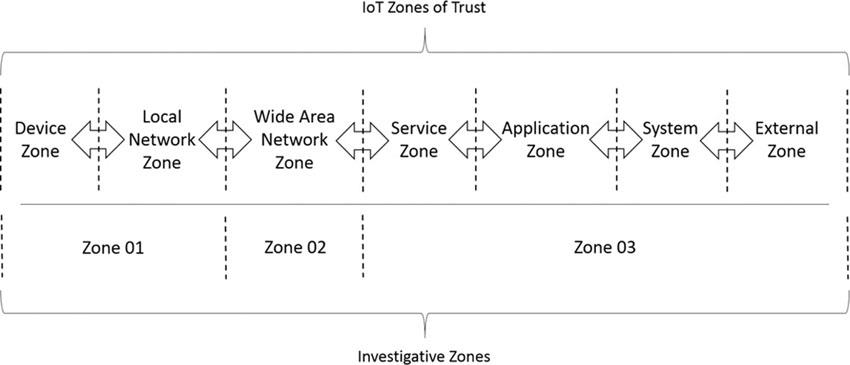
1-2-3 Zones 1-2-3 zones is an approach that segregates IoT environments into the following three zones to reduce challenges and to help digital forensics practitioners focus on clearly identified areas when executing their investigative process methodology:
• Zone 01 includes all IoT devices that can contain potential evidence.
• Zone 02 includes all intermediate components located between internal and external networks that support IoT communications.
• Zone 03 includes all hardware and software components that reside beyond the external networks, such as CSPs.
Figure 20.4 Forensics-aware IoT (FAIoT) model.
Illustrated in Figure 20.5, the three investigative zones above have been mapped against the seven trust zones discussed previously.
Next-Best-Thing (NBT) Triage Next-best-thing (NBT) triage is an approach used to identify an alternative source of evidence, within the crime scene, if the original IoT source is unavailable. In conjunction with the 1-2-3 zones approach, the NBT approach can be used to determine what other devices were connected to the device of interest, and subsequently identify any evidence left behind after being removed from the IoT environment.
Figure 20.5 Investigative zones versus trust zones.
Therefore, in such situations, digital forensics practitioners have the option of identifying and considering the next best source of relevant evidence for seizure. However, the NBT approach does not establish a systematic means by which digital forensics practitioners decide what the next best thing might be in different scenarios and situations, which can raise concerns when it comes to the relevance and meaningfulness of next best evidence sources.
While there may be constraints related to gaining access to and processing of physical IoT devices as evidence, as was discussed previously, the technology-generated data on these technologies is short lived and for investigative needs must be sent to a remote repository for long-term retention. The analysis and examination of evidence gathered from IoT devices, as with other technology-generated data, must consider the data source to effectively demonstrate authenticity and integrity.
From what has been previously covered in this chapter, it can be seen that IoT devices can transmit potentially relevant evidence to CSP environments. It is important that organizations consider the totality of potential evidence that can exist in these locations within the scope of an IoT investigation. Refer to Chapter 18, “Forensics Readiness in Cloud Environments,” for further discussion on processing evidence from cloud computing environments.
As discussed in Chapter 2, “Investigative Process Methodology,” documentation is a critical element of every investigation that needs to start at the beginning of an investigation and be carried out to the end. In this last phase of the investigative workflow, the final investigative report will be created to communicate factual conclusions by demonstrating the processes, techniques, tools, equipment, and interactions used to maintain the authenticity, reliability, and trustworthiness of digital evidence. Some things to consider when writing a final investigative report include the following:
• Structure and layout should flow naturally and logically; like how we speak.
• Content should be clear and concise to accurately demonstrate a chronology of events.
• Use of jargon, slang, and technical terminology should be limited or avoided, and where used, a glossary should be included to define terms in natural language.
• Where acronyms and abbreviations are used, they must be written out in full expression on first use.
• Because final reports are written after the fact, that is, after an investigation, content should be communicated in the past tense; but tenses can change where conclusions or recommendations are being made.
• Format the final report not only for distribution within the organization, but also with the mindset that it may be used as testimony in a court of law.
A template for creating written formal reports has been provided as a reference in the Templates section of this book.
Step #8: Establish Continuing Education
Like digital forensics, depending on an individual’s role with respect to IoT forensics determines the level of knowledge they are provided. Detailed discussion about the diverse levels of education, training, and awareness an organization should require of their people in support of digital forensics can be found in Chapter 14, “Establish Continuing Education.”
As the lowest type of education, this is a generalized level of training and awareness that is intended to provide people with foundational knowledge without getting too specialized vis a vis IoT forensics. Leveraging the education and training that has already been put in place for digital forensics, this education provides people with the competencies they need related to organizational policies, standards, and guidelines so that they indirectly contribute, through some form of behavior or action, to the organization’s digital forensics program.
Examples of topics and subjects that should be included as part of a mobile device forensics awareness program include the following:
• Business code of conduct
• Data protection and privacy
Essentially, the difference between this training and the previous awareness is that the knowledge gained here is intended to teach people the skills necessary to directly support the organization’s digital forensics program vis a vis how, where, and to what extent IoT devices are used for business purposes.
Information communicated at this level is more detailed than the previous type of education because it must provide people with the knowledge required to support a specific role or function, such as managing IoT device sensors.
For example, as part of basic IoT forensics training, information about audit logging and retention should be covered. Generally, this topic relates to the practice of recording events and preserving them, as per the organizational governance framework, to facilitate digital forensics investigations.
A working and practical knowledge of IoT forensics requires people to first and foremost have the skills and competencies necessary to ensure that all digital forensics principles, methodologies, and techniques are understood. Once the fundamental knowledge is gained, practitioners can then start pursuing a specialization into mobile device forensics.
However, unlike digital forensics education programs, the availability of curriculum dedicated entirely to IoT devices is still limited. Most commonly, IoT forensics is taught as a specific course in higher/post-secondary institutions or as a professional education module led by an industry-recognized training institute.
Refer to the appendix Education and Professional Certifications for a list of higher/post-secondary institutions that offer formal education programs.
Step #9: Maintain Evidence-Based Presentation
Regardless of how mobile devices are deployed in an enterprise, the systems and ESI present can be used to commit or be the target of criminal activity. However, perhaps the biggest challenge to a digital forensics investigation where mobile device technologies are within scope is the dynamic nature of determining the “who, where, what, when, why, and how” of criminal activity. Some things to consider when writing a final investigative report include:
• Structure and layout should flow naturally and logically; like how we speak.
• Content should be clear and concise to accurately demonstrate a chronology of events.
• Use of jargon, slang, and technical terminology should be limited or avoided, and where used, a glossary should be included to define terms in natural language.
• Where acronyms and abbreviations are used, they must be written out in full expression on first use.
• Because final reports are written after the fact, that is, after an investigation, content should be communicated in the past tense; but tenses can change where conclusions or recommendations are being made.
• Format the final report not only for distribution within the organization, but also with the mindset that it may be used as testimony in a court of law.
A template for creating written formal reports has been provided as a reference in the Templates section of this book.
Presently, there are few government or other regulatory bodies that have implemented legislation and requirements over the use of IoT devices. In large part, IoT devices continue to fall within the applicability of existing laws, standards, and regulations pertaining to the use of technology. As with other technologies, and discussed previously in this chapter, there continue to be key challenges involving the privacy of both information and users, the security of IoT devices, and the protection of ESI created, transmitted, and accessed.
Additionally, with respect to legal jurisdiction or ownership (i.e., custody, control, or possession), there is no difference between IoT devices and traditional computer systems when other organizations, service providers, etc. could be involved. In situations involving IoT devices and third parties, it is necessary to have contractual agreements in place (between all parties) to guarantee cooperation in the event of an incident or investigation involving an IoT environment.
While it is evident that IoT devices have generated significant value, in both business and personal contexts, the fact remains that legal and regulatory governance of IoT devices requires additional focus to address key problem areas. While challenges were identified previously in this chapter, the following are four key legal problem faced today:
While the widespread deployment of IoT devices, sensors can be used beneficially, but they also allow data to be used by organizations for discriminatory purposes, such as to draw inferences about misconduct or establish guilt. Although conclusions derived from fact-based evidence can establish guilt or innocence, the use of IoT data raises concerns about the possibility of indiscriminate exposure of information, for example, will IoT devices lead to new forms of discrimination against protected information classes such as race, age, or gender?
Generally, the concept of privacy is invoked to respect personally identifiable information (PII) and the right to determine how such data is used. However, IoT devices generate enormous amounts of data that can be used to learn about people’s activities, habits, personalities, preferences, and attributes. Accountability, a key principle of privacy, is difficult to maintain with IoT data because multiple third-party entities (i.e., organizations, vendors, service providers) collect, use, and (potentially) expose PII. Although IoT devices can be beneficial in providing relevant evidence, they can also be used in a manner that exploits or violates privacy rights.
Aside from the security challenges expressed previously in this chapter, IoT devices create liabilities related to cross-border data flows. Depending on the designed purpose and functionality, IoT devices can collect data that is private or sensitive and is subject to legal or regulatory scrutiny. This can raise concerns, as the data created by IoT devices may not be restricted from being transmitted across jurisdictional boundaries where different data protection laws, standards, and regulations are enacted. Uncontrolled data flows between IoT devices raise questions about legal scope, and it can be difficult to isolate which governing body the device collecting the data falls under. Generally, this becomes a matter of whether a jurisdiction with greater data protection laws can enforce increased protection requirements on other jurisdictions.
Further complicating matters of privacy, IoT device sensors also raise concerns about whether data was collected, transmitted, and accessed with the consent of its user(s). Furthermore, IoT devices complicate matters of consent largely because protection laws are not equipped to address matters of how such data can be shared with or sold to third parties. Additionally, where organizations have deployed IoT devices that can collect data that includes PII, access to and storage of this data can bring about legal and regulatory concerns related to whether employees have agreed.
Refer to Chapter 18, “Forensics Readiness in Cloud Environments,” for further discussion on legal considerations related to cloud computing environments.
Refer to Chapter 16, “Ensuring Legal Review,” for further discussion about laws, standards, regulations, jurisdiction, and ownership.
Although IoT devices continue to proliferate, there is currently little research focused on incorporating digital forensics readiness into IoT environments.