Chapter 3. Intercloud IT Management Strategy
This chapter covers the following topics:
![]() IT Service Management Guiding Principles: This section explains how companies become successful by making their customers successful and meeting their business objectives. You will also learn how B2B (business-to-business) companies are shifting to B4B (business for business) in order to meet customer business goals and stay ahead of competitors.
IT Service Management Guiding Principles: This section explains how companies become successful by making their customers successful and meeting their business objectives. You will also learn how B2B (business-to-business) companies are shifting to B4B (business for business) in order to meet customer business goals and stay ahead of competitors.
![]() Technology Business Management (TBM): This section uses the TBM Framework to discuss business transformation, IT transformation, and technology transformation as well as the relationship among these transformations to realize the customer business outcomes. In addition, some of the new IT technology transformations and their impact on businesses are provided.
Technology Business Management (TBM): This section uses the TBM Framework to discuss business transformation, IT transformation, and technology transformation as well as the relationship among these transformations to realize the customer business outcomes. In addition, some of the new IT technology transformations and their impact on businesses are provided.
![]() Cisco Lifecycle for IT Services and Management: This section discusses the ITIL framework and how ITIL can be used within cloud for services delivery. Some of the Cisco best practices for Plan, Build, and Manage that align with the ITIL lifecycle are also provided.
Cisco Lifecycle for IT Services and Management: This section discusses the ITIL framework and how ITIL can be used within cloud for services delivery. Some of the Cisco best practices for Plan, Build, and Manage that align with the ITIL lifecycle are also provided.
![]() Fundamental Services Building Blocks for Cloud: This section provides customer service ingredients, the fundamental cloud service building blocks. Also, cloud/Intercloud service challenges, the services catalog, and service portals are discussed.
Fundamental Services Building Blocks for Cloud: This section provides customer service ingredients, the fundamental cloud service building blocks. Also, cloud/Intercloud service challenges, the services catalog, and service portals are discussed.
![]() Use Case for Intercloud Management Strategy—Shadow IT: The use case describes the shadow IT that exists in most customers’ IT cloud/Intercloud environments, and how IT investments can be monitored and controlled so that IT departments and CIOs become more relevant and manage IT as a business to meet the needs of their organization.
Use Case for Intercloud Management Strategy—Shadow IT: The use case describes the shadow IT that exists in most customers’ IT cloud/Intercloud environments, and how IT investments can be monitored and controlled so that IT departments and CIOs become more relevant and manage IT as a business to meet the needs of their organization.
This chapter describes details of cloud/Intercloud IT service management. At the heart of IT service management is the ability to achieve the business outcomes of customers. The technology has a huge impact on the way services are delivered and consumed by customers. The technology transitions create opportunities to make IT transformations and to meet the required customer business objectives. The world and customers are moving away from legacy IT transactional services to consumption-type (pay based on use) services using cloud and Intercloud technologies. This chapter explains how technology changes such as cloud and the Intercloud have created opportunities for service providers to make adjustments in their IT operations to realize the new customer business outcomes.
IT Service Management Guiding Principles
Businesses that thrive are businesses that understand customer needs and deliver what is needed seamlessly while meeting the quality-of-service (QoS) requirements and SLAs. Services are the building blocks for IT service management (ITSM), but how do you determine which services are the “right” services to develop and deliver to customers? ITSM generally refers to the practice of aligning the delivery of IT services with the needs of the enterprise while strongly emphasizing customers and users.
The new technologies of cloud, IoT, IoE, big data, mobility, SDN, and analytics are changing the way IT organizations strategize and implement technology. You can be the best technologist in the world, but if you cannot effectively leverage technology and lead initiatives that deploy the technology, it just doesn’t matter. The big bucks always go to those who can work with business executives in leveraging technology to provide business outcomes.
In old-world business (B2B), the product vendors, especially software companies, loaded up on features so they could charge customers by feature and also compete with other vendors based on features. It made for good advertising. Let’s face it; most people even in product companies do not understand how all these features work and whether they are even useful for consumers. The corporate buyers buy these products based on their experience and judgment and evaluate several bidders to see if the products meet their needs. Many times even the engineers who make the buying decisions are not the ones who operate the products and are not sure how the products fit into their environments. Thus the buyers are totally dependent on the vendors, and in most cases the buyers never realize more than 50% of the value of the software. Figure 3-1 shows the consumption/adoption gap.1
As shown in Figure 3-1, increased complexity makes it harder for customers to achieve full value. Most customers prefer (or should prefer) the features required for mission-critical applications and then additional sophisticated features as they become more familiar with the product and features. The majority of executives, 88%, expect process alignment from their vendor to achieve better adoption.2 Cloud technology is transforming IT suppliers from B2B-type product sellers to sellers that embrace XaaS (anything as a service) models as shown in Figure 3-2.
Cloud-enabled services benefit customers most since they buy only what they need initially and depend on external clouds for items such as testing, R&D, disaster recovery, and so forth. Once customers are comfortable, they can add more features as needed. In XaaS, unlike B2B, the customers are not paying for the features or buying the equipment. They are buying only the services that are required to meet all of their business goals. In this case, the burden has shifted from the customer to the vendor to make sure all the infrastructure works the way it is supposed to and produces the business outcomes the client requires. The client pays only for what is used. The client does not have to learn all the intricacies of equipment, interfaces, and other technology aspects; this burden has shifted to the vendor.
Users of IT are being transformed as well. In a dramatic change from just a couple of years ago, the role of CIO has changed from someone who keeps the lights on to a strategic thinker who transforms the IT department from a cost center into a strategic value provider. The CIOs are being invited into boardrooms for strategic planning, and with the increased visibility comes increased responsibility to bring both top-line and bottom-line business value. When CIOs lack a voice in the boardroom, they become more like keep-the-lights-on people and eventually become victims to budget cuts and outsourcing of many of the IT functions. IT governance can help CIOs to become agents of change and be active partners in laying out the company’s strategy. An IT organization’s success factors include
![]() Technology decisions driven by business strategy (not the other way around)
Technology decisions driven by business strategy (not the other way around)
![]() Sustaining the IT activities as efficiently as possible
Sustaining the IT activities as efficiently as possible
![]() Speed to market (agile transformation)
Speed to market (agile transformation)
![]() Technology architecture aligning with business initiatives and technology at the heart of the value proposition
Technology architecture aligning with business initiatives and technology at the heart of the value proposition
Technology Business Management (TBM)
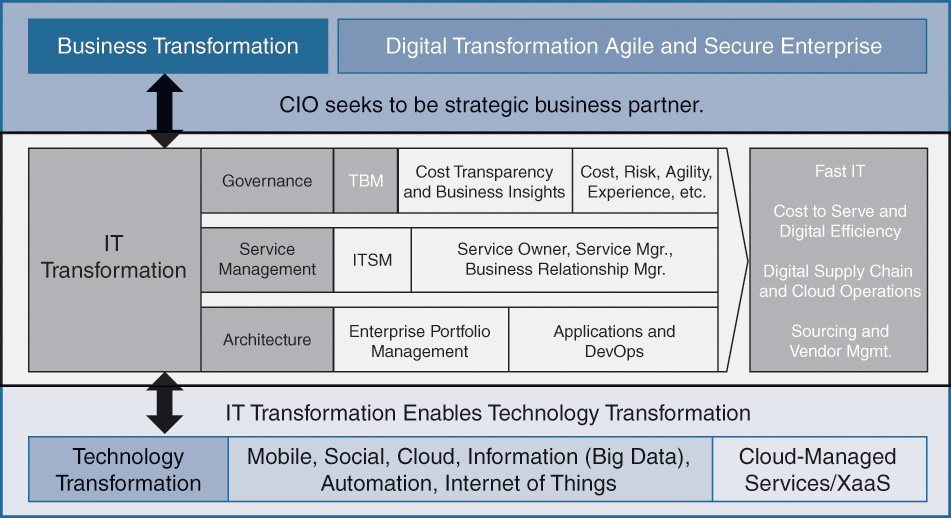
Transformation of IT occurs along several dimensions or tracks, each one undergoing its own transformation. It requires modern governance where every dollar counts, between running the business and changing the business. It requires a “services everything” approach and a modern enterprise architecture focused on capability-led planning and project and portfolio management of investments (change the business).
Figure 3-3 shows the TBM Framework, which has three important layers:
![]() Business transformation
Business transformation
![]() IT transformation
IT transformation
![]() Technology transformation
Technology transformation
The following subsections discuss these three areas in detail.
Business Transformation
It is not the strongest of the species that survive, nor the most intelligent, but the one most responsive to change.
—Charles Darwin
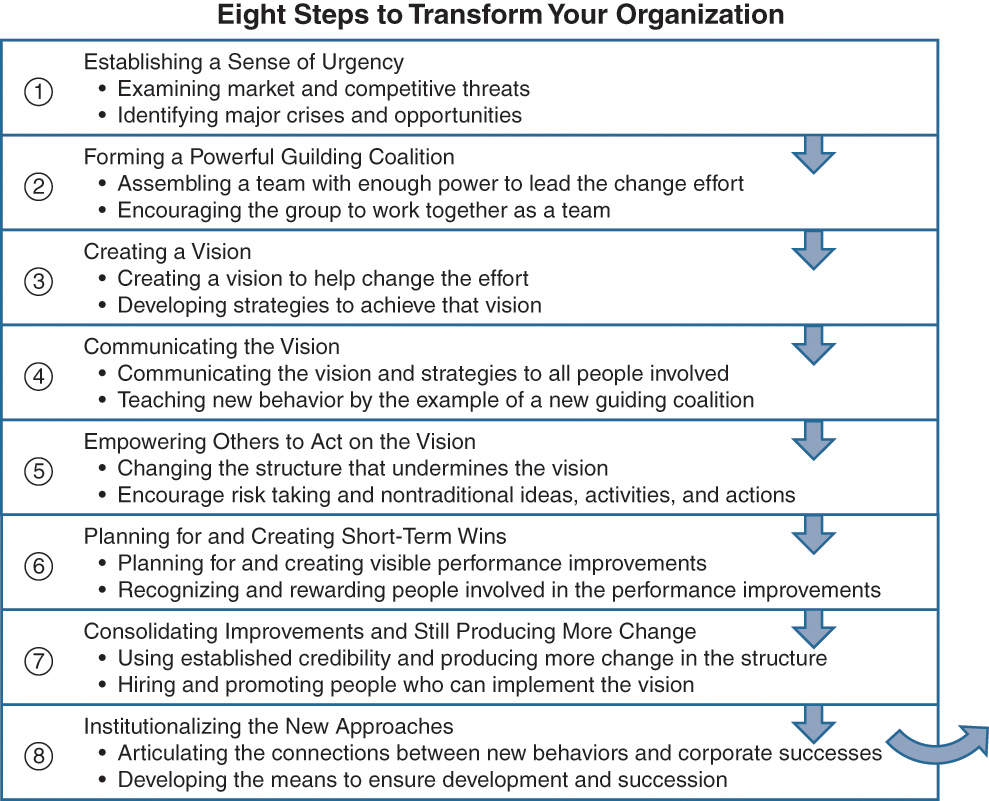
The need for business transformation may be caused by external changes in the market such as technology changes, regulations coming into force, or market competition becoming more intense. Business transformation is achieved by realigning the way staff works, how the organization is structured, and how technology is used. Typically organizations go through several stages in transforming themselves, as shown in Figure 3-4.3
IT Transformation
What is IT transformation? Ask 10 people in IT and you will get 10 different answers. Is it IT going from a cost center to operating as a business, moving from centralized operations to decentralized operations? It seems these answers are agreeable to many CIOs. Dan Roberts, president of Ouellette & Associates, a Bedford, New Hampshire, consulting firm that focuses on IT transformation, believes part of the problem is the inability of CIOs to communicate their vision. Roberts says, “You have to think about it as looking from the outside in. People in IT work their tails off trying to hit the bull’s-eye on customer value, business value, and being more strategic. They’re hitting the bull’s-eye every time, but it’s their bull’s-eye, not their clients’ bull’s-eye.”4
Cisco Systems CEO John Chambers, in an interview with the Wall Street Journal, said that the digital disruption facing companies is so intense that one-third of corporate leadership teams will not make the transition over the next three years. For CIOs, though, it’s an opportunity to elevate their roles. “It’s a chance for IT to be back in vogue.”5
In any case, irrespective of the beliefs, IT transformation needs to take place when
![]() The IT infrastructure can’t keep up with the business needs
The IT infrastructure can’t keep up with the business needs
![]() The CIOs are out of touch with their customers’ experience
The CIOs are out of touch with their customers’ experience
![]() The IT systems and technologies are outdated
The IT systems and technologies are outdated
![]() Shadow IT is prevalent and siphoning off resources
Shadow IT is prevalent and siphoning off resources
![]() Employees are not using the company assets
Employees are not using the company assets
![]() The IT departments are not considering and using open-source technology
The IT departments are not considering and using open-source technology
Technology Transformation
Technology has the potential to change the structure of existing industries and to create new industries. It is also a great equalizer, undermining the competitive advantages of market leaders and enabling new companies to take leadership away from existing firms. Since technology is such a vital force, the field of technology management has emerged to address the particular ways in which companies should approach the use of technology in business strategies and operations. Technology management is the set of policies and practices that leverage technologies to build, maintain, and enhance the competitive advantage of the firm.
The world is moving from hardware centricity to a world of software, services, data, and analytics. In addition, there is an even bigger change as the business model moves from transaction- to consumption-based services. These changes include extreme automation of manual operations, a shift from PDI (Prepare, Design, Implement) selling to business outcome selling. The selling of services will need to transition from the traditional role of following the product sales rep to leading the sale. In the future, services will own the revenue quota and the overall customer P&L. This represents both an opportunity and a challenge for all services sales leaders and IT vendor management, and the change management process will be critical for future success.6
The underlying benefit of cloud computing is shared resources, supported by the underlying nature of a shared infrastructure environment. Thus, SLAs span clouds and are offered by service providers as service-based agreements rather than customer-based agreements. Measuring, monitoring, and reporting on cloud performance is based upon an end user experience or the end users’ ability to consume resources. The downside of cloud computing, relative to SLAs, is the difficultly in determining a root cause for service interruptions due to the complex nature of the environment.7
In the context of a business and operations, technology has a wide range of potential effects on management:
![]() Reduced costs of operations: For example, manufacturing companies use technology to lower manufacturing and administrative costs, enabling the company to make and sell more manufactured products.
Reduced costs of operations: For example, manufacturing companies use technology to lower manufacturing and administrative costs, enabling the company to make and sell more manufactured products.
![]() New product and new market creation: For example, Apple Computer miniaturized music devices and telephone/mobile phones to create a huge market worldwide and became one of the biggest companies in the world.
New product and new market creation: For example, Apple Computer miniaturized music devices and telephone/mobile phones to create a huge market worldwide and became one of the biggest companies in the world.
![]() Adaptation to changes in scale and format: In the early part of the twenty-first century, companies addressed how small devices such as cell phones, personal digital assistants (PDAs), and MP3 players supported various features and functions. For example, cell phones began to support email, web browsing, text messaging, and even picture taking as well as phone calls.
Adaptation to changes in scale and format: In the early part of the twenty-first century, companies addressed how small devices such as cell phones, personal digital assistants (PDAs), and MP3 players supported various features and functions. For example, cell phones began to support email, web browsing, text messaging, and even picture taking as well as phone calls.
![]() Improved customer service: Cisco collects data in a sophisticated way from enterprise devices and provides messaged information in the form of analytics to help enterprise customers manage their networks.
Improved customer service: Cisco collects data in a sophisticated way from enterprise devices and provides messaged information in the form of analytics to help enterprise customers manage their networks.
![]() Big data and analytics: Many companies have started collecting data from various sources, virtualizing the data, and messaging the data to create analytics/applications to help consumers in their daily life. Based on the data collected through WiFi devices, retailers can determine what consumers are looking for and provide the information through displays and targeted advertisements.
Big data and analytics: Many companies have started collecting data from various sources, virtualizing the data, and messaging the data to create analytics/applications to help consumers in their daily life. Based on the data collected through WiFi devices, retailers can determine what consumers are looking for and provide the information through displays and targeted advertisements.
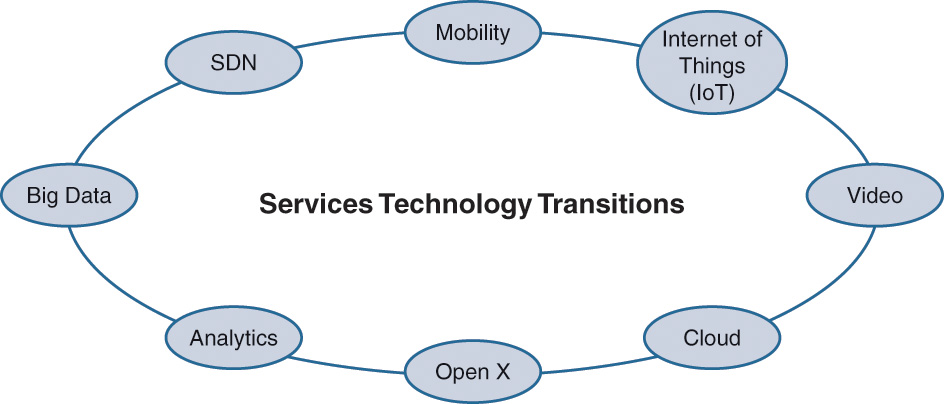
Figure 3-5 shows some of the latest technologies that play a role in the transformation of services. These technology transitions drive enterprise and service provider IT investment decisions across both services and products.
Table 3-1 describes at a high level some of the impacts of the latest technologies shown in Figure 3-5 on the business and IT operations.
Aligning IT and Business
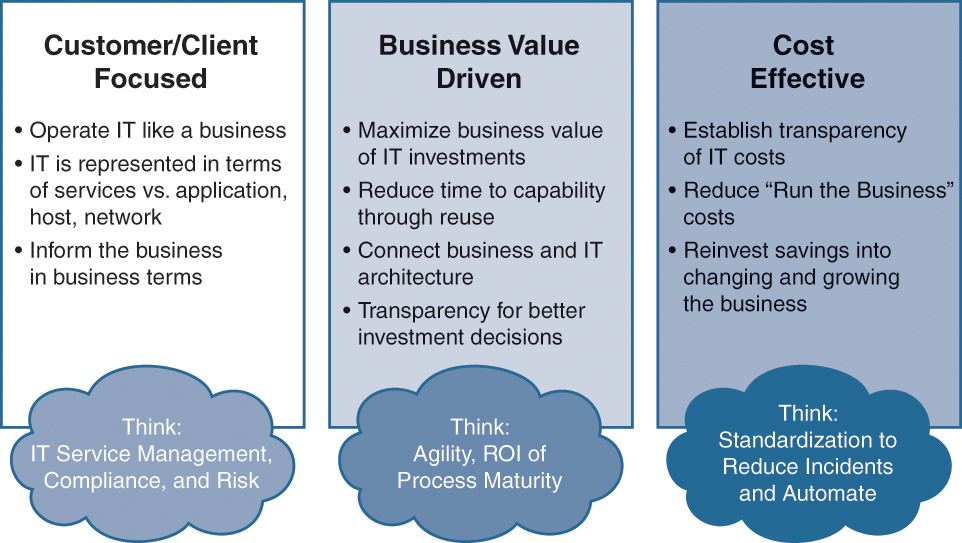
Figure 3-6 shows the IT and business need to operate together in order to be cost-effective. Many of these functions are possible using cloud and other technologies highlighted before. Business management and IT need to use the capabilities of cloud to align with each other.
Cloud computing is growing at a rate of 30% each year and drives a major portion of IT spending. To meet business demands without losing control or compromising security, businesses need an agile IT model. Cloud computing provides this agility with a fast, flexible way to use the most advanced technology possible, when and where it is needed. Cloud computing also lets businesses pay for technology only when they use it. Because public cloud computing removes the need for organizations to make large initial capital investments for hardware and facilities, it is also very cost-effective and adaptable.
Best Practice
In the development and testing use case, enterprise customers develop workloads in service provider clouds and bring the workloads back to their private clouds after the workloads are promoted to the production environment in order to address any critical security and compliance concerns for IT departments.
Most important, cloud computing frees valuable IT staff from routine IT operations and maintenance so they can create new services and revenue streams. This speed, effectiveness, flexibility, and innovation are the basis of the IoE economy.
Aligning Software Management to ITIL Processes
Formerly known as the Information Technology Infrastructure Library, ITIL is a set of practices for ITSM that focuses on aligning IT services with the needs of business. In its current form (known as ITIL 2011 edition), ITIL is published as a series of five core volumes, each of which covers a different ITSM lifecycle stage. It brings together a comprehensive set of service and lifecycle products designed to improve service levels and productivity, deliver best practices and standardization, and align IT to the delivery of business value.
Figure 3-7 shows the ITIL lifecycle (Service Strategy, Service Design, Service Transition, Service Operation, and Continual Service Improvement), with software service components mapped to it. Cisco uses Plan, Build, and Manage phases that align with the ITSM ITIL lifecycle.
Cisco Lifecycle for IT Services and Management
Consumable IT services are the focus of ITIL, whereas Cisco Services is concerned with services offered around projects and delivering services based on an agreed-upon statement of work (SOW) or contract, and it aligns with ITIL. Figure 3-8 shows the Cisco Services lifecycle, a three-phase effort that maps to ITIL’s five-phase lifecycle. Cisco has some 400-plus services that map around the Plan-Build-Manage Cisco lifecycle. The following subsections briefly describe the Cisco Services lifecycle and how it maps to ITIL.
Plan (Service Strategy and Service Design Phases)
In a dramatic change from just a few years ago, the role of CIO has gone from someone who keeps the lights on to a strategic thinker who transforms the IT department from a cost center or a commodity center to a strategic value provider. The IT organization’s (CIO’s) success factors in the strategy phase include
![]() Technology architecture aligning with the business initiatives
Technology architecture aligning with the business initiatives
![]() Speed to market
Speed to market
![]() Sustaining the IT activities as efficiently as possible
Sustaining the IT activities as efficiently as possible
Service Design is about defining the standards for things like operating systems, for example, designing the manageability of the service, the capacity model, and so on. In this phase vendors design the solutions based on the strategy phase.
Build (Service Transition Phase)
The Service Transition phase implements the Service Design that was built in the design phase into production at the service provider location. Typically, service delivery teams work with the operations teams and implement the services that the provider will offer to end users. Here, the vendor (such as Cisco or a partner) implements orchestration tools to automate the provisioning, stage all of the equipment, validate, and hand off all of the equipment and products to the service providers. Also, depending on the complexity, training is provided to the operations staff for smooth transition of the technology/solutions.
Manage (Service Operation and Continual Service Improvement Phases)
The Service Operation phase is when the service provider takes over the management of the cloud operations from the equipment vendors, system integrators, and partners; from that point the provider will take service orders from its end customers. All service phases are important, but the Service Operation phase draws the most attention because 60% to 70% of IT budgets are spent in dealing with day-to-day operations. In the Service Operation phase, the service provider not only takes the service orders for service fulfillment but also monitors and audits the service using the monitoring systems to ensure that the SLAs are met.
Service Optimization (Continual Service Improvement), as the name implies, is an ongoing practice to improve the IT organization’s activities using best practices, as opposed to a reactive response to a specific situation or a temporary crisis.
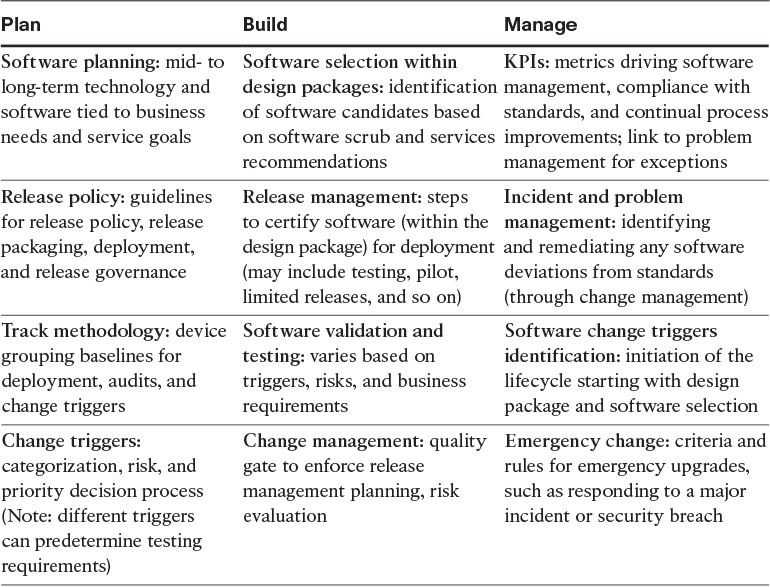
Best Practices in Software Management Services in the Cisco Lifecycle
Table 3-2 shows some of the Cisco leading/best practices within the Plan-Build-Manage lifecycle.
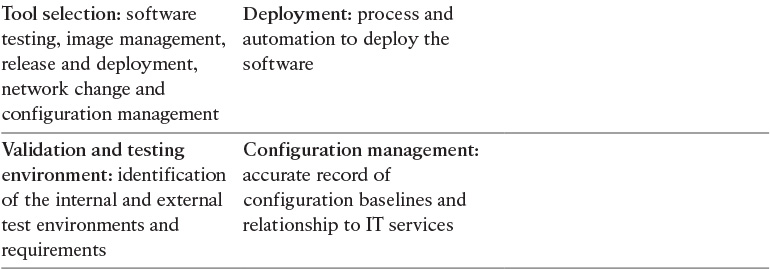
Cisco Lifecycle Services for Cloud
Table 3-3 shows some of the tasks performed under the Cisco Plan-Build-Manage lifecycle, which aligns with the ITIL lifecycle.
Is ITIL Still Relevant When Delivering Services via Cloud?
Yes, it is true, ITIL started long before these new technologies such as cloud, big data, and analytics. However, that does not necessarily make ITIL irrelevant. In fact, it is more important than ever to ensure that businesses follow the structure laid out in ITIL. Cloud computing enables new IT architecture, altering the way services are sourced and delivered. Software is delivered to consumers based on pay per use, like utilities such as electricity, water, and telephone. These new technologies and new capabilities enable IT to bring services to consumers much more efficiently and at a reduced cost so that they can meet their business goals.
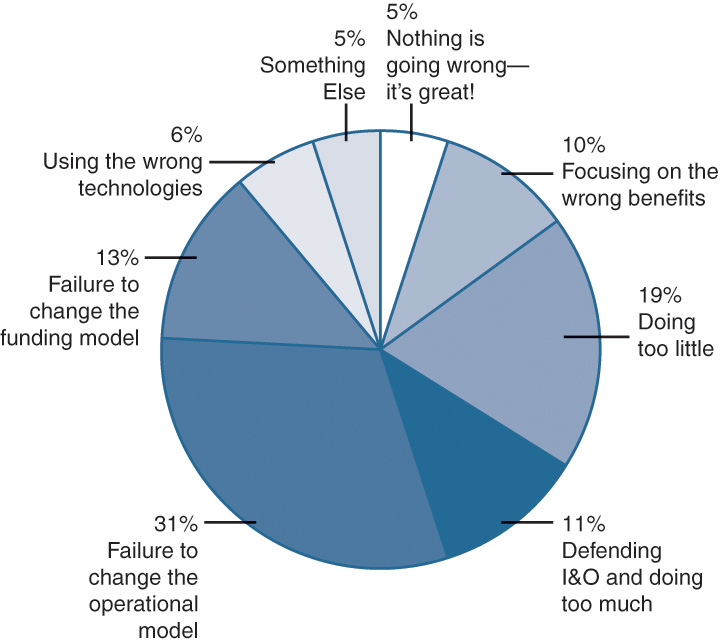
A recent survey at a Gartner conference showed that 95% of private clouds are failing. Why? Figure 3-9 shows some of the reasons quoted by the survey respondents for the failure of private clouds.8 This is exactly the reason IT services need proper planning and business alignment in order to make any clouds successful. Most importantly, the automation of processes and systems must follow ITIL practices.
The following ITIL phases briefly highlight some of the tasks that can be done in order to incorporate new technologies such as cloud so that IT services are successful:
![]() Service Strategy: Cloud does not change the marketplace for services. It only provides a new way to achieve the service objectives. This means it is more relevant during Service Strategy that we define the technology strategic objectives and how the current-state legacy architecture needs to migrate to cloud and other technologies to provide the services to customers. The business case should also be done in this phase.
Service Strategy: Cloud does not change the marketplace for services. It only provides a new way to achieve the service objectives. This means it is more relevant during Service Strategy that we define the technology strategic objectives and how the current-state legacy architecture needs to migrate to cloud and other technologies to provide the services to customers. The business case should also be done in this phase.
![]() Service Design: The design of cloud should be done such that the cloud technology aligns and integrates with the rest of the technologies that are already in place, and it is aligned with the business objectives so that the IT services enable the business outcomes. The alignment between technology and business was described previously in this chapter. (Figure 3-9 shows that 10% of respondents in the Gartner survey stated private clouds failed due to focusing on the wrong benefits and 6% stated the failure was because of using the wrong technologies.)
Service Design: The design of cloud should be done such that the cloud technology aligns and integrates with the rest of the technologies that are already in place, and it is aligned with the business objectives so that the IT services enable the business outcomes. The alignment between technology and business was described previously in this chapter. (Figure 3-9 shows that 10% of respondents in the Gartner survey stated private clouds failed due to focusing on the wrong benefits and 6% stated the failure was because of using the wrong technologies.)
![]() Service Transition: The cloud vendor should ensure during Service Transition to the customer that all the required tests are done in the customer environment, and the cloud technologies delivered will enable the business to achieve its objectives.
Service Transition: The cloud vendor should ensure during Service Transition to the customer that all the required tests are done in the customer environment, and the cloud technologies delivered will enable the business to achieve its objectives.
![]() Service Operation: The traditional operations need to go through the change, and operations staff should get appropriate training in order to make cloud technologies successful. The service operations are the lifeline for any IT services, and it is IT staff who would be monitoring the services, troubleshooting in case of any issues, and providing support to end users. (Figure 3-9 shows that 31% of survey respondents say private clouds failed due to operations.)
Service Operation: The traditional operations need to go through the change, and operations staff should get appropriate training in order to make cloud technologies successful. The service operations are the lifeline for any IT services, and it is IT staff who would be monitoring the services, troubleshooting in case of any issues, and providing support to end users. (Figure 3-9 shows that 31% of survey respondents say private clouds failed due to operations.)
![]() Continual Service Improvement (CSI): During the CSI or Service Optimization phase it is very important to fine-tune and adjust all of the other phases based on the lessons learned, especially with the addition of any changes in technology or business processes.
Continual Service Improvement (CSI): During the CSI or Service Optimization phase it is very important to fine-tune and adjust all of the other phases based on the lessons learned, especially with the addition of any changes in technology or business processes.
Best Practice
Follow structured models like ITIL to ensure that services proposed and developed meet customer business goals. Also, audit the services to fine-tune systems for improvements and business alignment.
Fundamental Services Building Blocks for Cloud
So what is cloud computing? From a “utility” perspective, cloud could be considered as the fourth utility (after water, electricity, and telephony), which, as we and many others believe, is the ultimate goal of cloud.
The National Institute of Standards and Technology (NIST) provided the simplest definition for cloud: “Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.”9 Gartner defines cloud computing as “a style of computing where massively scalable IT-related capabilities are provided ‘as a service’ using Internet technologies to multiple external customers.”10
Typical Cloud Services
There are typically three major offerings that sum up cloud computing services: SaaS, PaaS, and IaaS. In most cases, the “layers” of cloud computing are represented as a pyramid with IaaS at the bottom, PaaS in the middle, and SaaS at the top. Table 3-4 provides a brief description of the service models.
Though IT foundation is not a service, it would be appropriate to include it because services require IT hardware and software resources such as a network comprising switches, routers, firewalls, load balancers, and so on; server and storage farms; and the software. Typically, IT foundation is composed of multivendor devices and software. Some of the major players that supply IT foundation include Cisco, Hewlett-Packard, IBM, VMware, Red Hat, Microsoft, and others.
Architecture Considerations for IT Services in Cloud
Many considerations may come from customers, partners, and internally from systems engineers and developers. From an IT services and business perspective, the following are some key considerations for IT services in cloud.
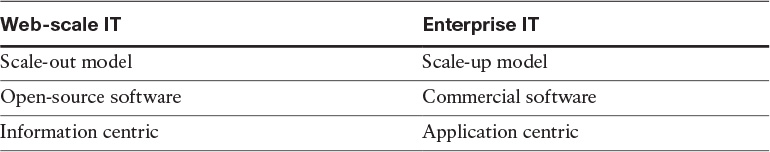
Web-scale IT
Web-scale IT, a term coined by Gartner, alludes to the fact that enterprise IT departments can become service providers by simulating how they design and operate technology architectures. Doing so requires a reexamination of IT conventional wisdom in several areas, including how to build clouds and develop applications so that they are scalable and delivered quickly to the market, as well as being resilient in the case of failure, and how to develop operational processes that are complementary to a more agile environment.
Table 3-5 lists some of the features of Web-scale IT versus enterprise IT.
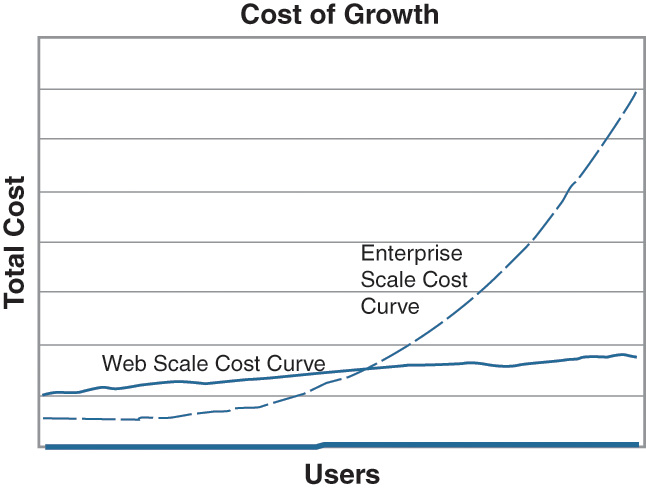
Applying the Web-scale architectural principle reduces costs as demand increases, as shown in Figure 3-10. As demand increases, commodity servers are added, and with variable costs being linear, fixed costs are diluted over a growing number of users.1
OpenStack
OpenStack is an open-source cloud operating system developed by a community of open-source developers and participating organizations.11 This initiative aims to deliver solutions for all types of clouds, whether public, private, or hybrid. The solutions are designed to be easy to implement, massively scalable, and comprehensive in features.
An open-source platform means the business is never locked into a proprietary vendor. It also provides tremendous choice from an ecosystem of industry-leading technologies (see Chapter 4, “Intercloud Architecture(s) and Provisioning”).
Cisco and OpenStack
Cisco is fully committed to OpenStack and has invested over US$1 billion to build the Intercloud using OpenStack. In addition, Cisco has purchased Metacloud, which is completely built on OpenStack for supporting private clouds. Figure 3-11 shows the Cisco commitment to OpenStack. Also, the Cisco connected cloud, cloud services, WebEx, WebEx Square, and VideoScape are built based on OpenStack.
Agility and Flexibility
Orchestration and automated flow through provisioning for compute, network, and storage are keys to agility. New users should be provisioned rapidly, and changes can be quick and across large groups of users. Web-scale architecture integrates and automates storage and networking provisioning in addition to compute, allowing full-service provisioning in seconds.
Software-Defined Networks and Network Simplification
Software-defined networks and NFV simplify service provisioning in enterprise and service provider networks. In SDNs, control is decoupled from the network infrastructure, allowing the service operations to manage a multivendor infrastructure fabric from a centralized location.
Network functions virtualization basically eliminates network function dependency on the hardware, which results in sharing of the physical hardware by multiple VNFs.
The majority of IT service providers’ complaints are that there are way too many appliances for Level 4 through Level 7 along with their element managers and network management tools. This creates a major operating expense and capital expense burden for providers and requires technical skills to manage this equipment. Some of the devices that can be virtualized include
![]() Firewalls, load balancers, DNS, Dynamic Host Configuration Protocol (DHCP), and packet gateways
Firewalls, load balancers, DNS, Dynamic Host Configuration Protocol (DHCP), and packet gateways
![]() CDN
CDN
![]() Radio Access Network (RAN), including base stations, 2G, 3G, 4G LTE
Radio Access Network (RAN), including base stations, 2G, 3G, 4G LTE
![]() Broadband Remote Access Server (BRAS) and QoE testing equipment
Broadband Remote Access Server (BRAS) and QoE testing equipment
![]() Set-top boxes (STBs) and regional gateways
Set-top boxes (STBs) and regional gateways
Automated Operations, Orchestration, and Management
An automated and orchestrated operations environment is essential in order to achieve a Web-scale IT environment of reliability, availability, and scalability. Intercloud operations, including fulfillment, assurance, and billing (FAB), are discussed later in the book.
Data Management
The key to operations applications and analytics is data. Data is key for everything. With cloud and the explosion of mobile devices, data is getting very large, and it is necessary to manage all of the data coming from various sources.
The need for applications to obtain information (data) from a single query is driving the demand more than ever due to the explosion of business applications from cloud and IoT/IoE technologies. These business applications need processed data (shown as analytics) from heterogeneous systems in near real time for business agility.
Here are a few insights for strategic architectural decisions:
![]() The traditional data warehouse has been overwhelmed by analytics demands, giving rise to the logical data warehouse (LDW) as a best-in-class architecture.
The traditional data warehouse has been overwhelmed by analytics demands, giving rise to the logical data warehouse (LDW) as a best-in-class architecture.
![]() Leading-edge enterprises are starting to leverage a hybrid integration platform to take advantage of the best cloud-based and on-premises integration approaches.
Leading-edge enterprises are starting to leverage a hybrid integration platform to take advantage of the best cloud-based and on-premises integration approaches.
![]() Greater visibility of application, server, and service-level data is pushing network operations staff to provide similar contextual insight into their domains.
Greater visibility of application, server, and service-level data is pushing network operations staff to provide similar contextual insight into their domains.
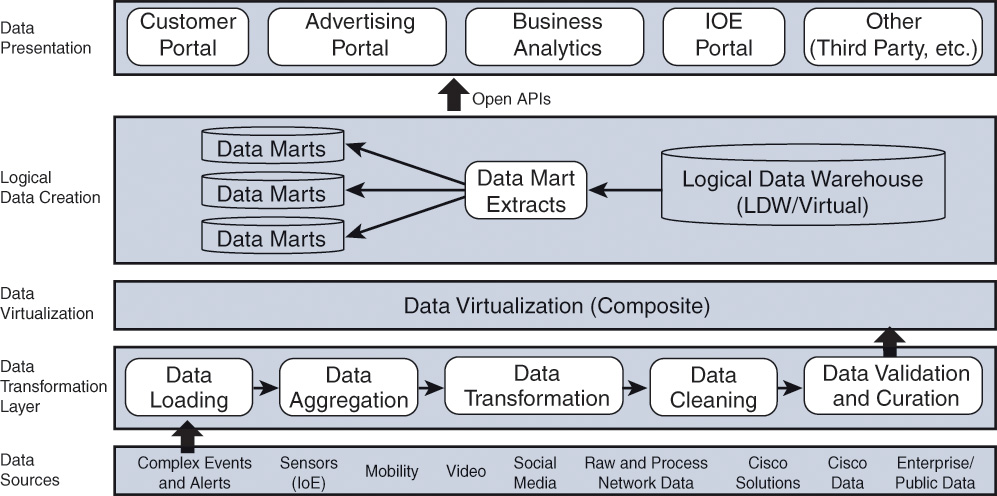
Figure 3-12 shows the architecture for managing the data so that Web-scale IT operations can be achieved. The list that follows briefly explains the layers in Figure 3-12.
![]() Data sources: Data sources include network, compute, storage, mobile devices, video, sensor data for IoT and IoE applications, and social networks.
Data sources: Data sources include network, compute, storage, mobile devices, video, sensor data for IoT and IoE applications, and social networks.
![]() Data transformation layer: The data that arrives into the transformation layer needs to be aggregated, transformed, cleansed, and curated before being sent up the stack to higher data layers.
Data transformation layer: The data that arrives into the transformation layer needs to be aggregated, transformed, cleansed, and curated before being sent up the stack to higher data layers.
![]() Data virtualization: The data that arrives at this layer may be structured or unstructured, and some data may be static and some may be in real time from streaming devices. The data is virtualized and sent up the stack for storing in an LDW.
Data virtualization: The data that arrives at this layer may be structured or unstructured, and some data may be static and some may be in real time from streaming devices. The data is virtualized and sent up the stack for storing in an LDW.
![]() Logical data creation: The data is stored in an LDW and may also be stored in data marts for specialized applications and for use by third parties.
Logical data creation: The data is stored in an LDW and may also be stored in data marts for specialized applications and for use by third parties.
![]() Data presentation: The data at the presentation layer is for consumption by various users. Users typically query for certain business outcomes, and the required data comes from data layers below.
Data presentation: The data at the presentation layer is for consumption by various users. Users typically query for certain business outcomes, and the required data comes from data layers below.
Best Practice
With judicious use of virtualization, changes at lower levels are transparent to higher levels of the infrastructure such as applications; therefore the changes can be made freely without impact. Virtualization makes scaling the infrastructure possible because it makes scaling manageable.
Challenges in IT Services
Based on many discussions with customers and surveys, the following security and integration issues seem to be on many customers’ minds:
![]() How cloud will keep data secure and available
How cloud will keep data secure and available
![]() How to comply with current and future security and risk management requirements
How to comply with current and future security and risk management requirements
![]() What type of security services are available through cloud
What type of security services are available through cloud
![]() How to perform internal and external audits of cloud security
How to perform internal and external audits of cloud security
![]() How to automate network, compute, and storage provisioning
How to automate network, compute, and storage provisioning
![]() How to do on-demand provisioning in near real time from a customer portal to all the infrastructure devices
How to do on-demand provisioning in near real time from a customer portal to all the infrastructure devices
![]() How to orchestrate between many new cloud tools and existing legacy tools
How to orchestrate between many new cloud tools and existing legacy tools
Though most of the surveys show that over 80% of customers are concerned about security and integration, most successful organizations are taking a calculated risk and implementing cloud with appropriate security measures. As many of you know, nothing can be 100% secure, but by knowing the current state, one can apply appropriate security measures to mitigate the risk and grow the business. Security and integration are discussed further in later chapters.
The Cloud Adoption Journey
Cloud adoption is a journey. The journey starts with increasingly capable pubic cloud services and private cloud platforms for the enterprise. From there, new APIs and protocols, virtual private cloud services, hybrid cloud capabilities, and open standards for cloud will appear and evolve over time. The eventual goal is an open, public cloud networking infrastructure, which we call the Intercloud. Figure 3-13 shows a typical cloud adoption journey, and the list that follows describes what happens during the journey.
![]() Consolidation: Every company has its own pace for cloud adoption. Each business line will need to analyze and decide the correct roadmap for this change. The benefits of the consolidation process will push companies in the correct way toward cloud.
Consolidation: Every company has its own pace for cloud adoption. Each business line will need to analyze and decide the correct roadmap for this change. The benefits of the consolidation process will push companies in the correct way toward cloud.
![]() Virtualization: Virtualization provides a logical representation of physical resources and enables flexible configuration and management of all infrastructure resources, and it reduces costs and increases agility.
Virtualization: Virtualization provides a logical representation of physical resources and enables flexible configuration and management of all infrastructure resources, and it reduces costs and increases agility.
![]() Public clouds: These are what most people think of when someone says “cloud.” They are hosted by service providers. They can host multiple users (tenants) at any time, who pay for the services they use just like other utility bills such as electricity, water, and telephone. They are managed by the service provider, and the user uses the applications such as CRM, email, collaboration, and other web applications. Public clouds are attractive since the users do not have to lay out any capital investment, which is provided by the service provider. Service providers provide security as they see fit and may charge extra for additional security, availability, and support.
Public clouds: These are what most people think of when someone says “cloud.” They are hosted by service providers. They can host multiple users (tenants) at any time, who pay for the services they use just like other utility bills such as electricity, water, and telephone. They are managed by the service provider, and the user uses the applications such as CRM, email, collaboration, and other web applications. Public clouds are attractive since the users do not have to lay out any capital investment, which is provided by the service provider. Service providers provide security as they see fit and may charge extra for additional security, availability, and support.
![]() Private clouds: Private clouds are private because they have only one tenant (a company or an enterprise). Private clouds serve their enterprise employees only and do not engage in providing services for external customers. The capital is invested and controlled by the enterprise. Enterprise companies migrate their data centers to a private cloud to run their business applications such as R&D, business intelligence (BI), supply-chain management, and so forth to maintain competitive advantage. Also, private clouds may have better security since the enterprise strictly controls it. Also, in private clouds services can be standardized as the enterprise sees fit.
Private clouds: Private clouds are private because they have only one tenant (a company or an enterprise). Private clouds serve their enterprise employees only and do not engage in providing services for external customers. The capital is invested and controlled by the enterprise. Enterprise companies migrate their data centers to a private cloud to run their business applications such as R&D, business intelligence (BI), supply-chain management, and so forth to maintain competitive advantage. Also, private clouds may have better security since the enterprise strictly controls it. Also, in private clouds services can be standardized as the enterprise sees fit.
![]() Hybrid clouds: Hybrid clouds are a combination of private and public clouds and they enjoy the benefits of both. Businesses can put their own innovative applications in private clouds during nonpeak times and move them to a public cloud during peak times. Also, businesses may use certain applications from public clouds and certain of their own applications from their private clouds.
Hybrid clouds: Hybrid clouds are a combination of private and public clouds and they enjoy the benefits of both. Businesses can put their own innovative applications in private clouds during nonpeak times and move them to a public cloud during peak times. Also, businesses may use certain applications from public clouds and certain of their own applications from their private clouds.
![]() Intercloud: The vision and topology for the Intercloud we will refer to is an analogy with the Internet itself: in a world of TCP/IP and the World Wide Web, data is ubiquitous and interoperable in a network of networks known as the “Internet”; in the world of cloud computing, content, storage, and computing are ubiquitous and interoperable in a network of clouds known as the “Intercloud.” This gives the flexibility for a service provider or an enterprise to stitch together a service seamlessly using services from multiple clouds.
Intercloud: The vision and topology for the Intercloud we will refer to is an analogy with the Internet itself: in a world of TCP/IP and the World Wide Web, data is ubiquitous and interoperable in a network of networks known as the “Internet”; in the world of cloud computing, content, storage, and computing are ubiquitous and interoperable in a network of clouds known as the “Intercloud.” This gives the flexibility for a service provider or an enterprise to stitch together a service seamlessly using services from multiple clouds.
IT Services Catalog
An IT services catalog, also referred to as an IT services portfolio, contains a list of technology resources an IT organization provides. IT services catalogs typically have two parts: a customer-facing part where business users can browse and select services, and a technical part, accessible only to IT administrators, that documents exactly what is required to deliver each service in the catalog. IT organizations maintain these services catalogs by upgrading the software, setting permissions for who can access what items, and adding new services and removing services that are no long required.
Version 3 of ITIL introduced IT services catalogs as a best practice for IT service management. User portals contain a menu of services offered by an IT organization. An effective services catalog enables IT to deliver business services that are more customer and service focused, which results in higher customer satisfaction, provides standardization and consistency, and increases IT visibility across the organization.
For the Intercloud, customers should be able to access services catalogs with services offered by multiple providers through self-service portals and select services that meet their SLAs and business objectives. For the Intercloud, it is most likely that the services catalog will be federated, and it is essential that to make the service deployment easier, service definitions and terminology need to be standardized. Based on the customer request, the service provider will combine services from multiple providers using the federated services catalogs. Service brokering, orchestration, and automation will be a big part of the services catalog for Intercloud services, enabling cloud users to obtain services from multiple providers on demand.
Cisco offers customers a broad portfolio of Cisco Powered Cloud Services, including
![]() Shadow IT solution (see the use cases in the next section)
Shadow IT solution (see the use cases in the next section)
![]() IaaS
IaaS
![]() Unified Communications (UC) as a service based on Hosted Collaboration Service (HCS)
Unified Communications (UC) as a service based on Hosted Collaboration Service (HCS)
![]() Contact center as a service based on HCS
Contact center as a service based on HCS
![]() Video and telepresence as a service
Video and telepresence as a service
![]() Desktop as a service
Desktop as a service
![]() Disaster recovery as a service
Disaster recovery as a service
Use Case for Intercloud Management Strategy—Shadow IT
This section presents a definition of the shadow IT problem, common software usage, issues, a recommended solution, and solution architecture.
The Shadow IT Problem
“Shadow IT” refers to unauthorized IT operating in an enterprise network without the knowledge of the enterprise IT department. Shadow IT is a security risk and can be detrimental to the enterprise IT as unauthorized IT resources are being siphoned off to outside. The capabilities of cloud increase the risk of shadow IT since cloud or the Intercloud makes it easier for employees to go outside their normal channels of approval to gain quick access to resources from outside their IT organization. In most cases, IT organizations, though they are aware, are not able to control such behavior since they have no mechanism to determine the extent of shadow IT within their enterprise.
Shadow IT Common Usage Software
Table 3-6 shows shadow IT software used by people in enterprise organizations.
Shadow IT Issues
The following represent some of the key shadow IT issues for an organization:
![]() Company employees bypass IT and set up their own clouds.
Company employees bypass IT and set up their own clouds.
![]() Employees may be taking IT into their own hands. Maybe that is the wave of the future; however, from a CIO and business perspective, it can be a nightmare.
Employees may be taking IT into their own hands. Maybe that is the wave of the future; however, from a CIO and business perspective, it can be a nightmare.
![]() The CIOs and the company lose their grip on the IT organization.
The CIOs and the company lose their grip on the IT organization.
![]() Employees may store company data outside the company (in Dropbox and other places) against the organization’s policies, leading to increased risk of data and company liability.
Employees may store company data outside the company (in Dropbox and other places) against the organization’s policies, leading to increased risk of data and company liability.
![]() Moving the data and accessing unauthorized sites for company business put the company and its customers at risk.
Moving the data and accessing unauthorized sites for company business put the company and its customers at risk.
![]() Company IT resources are wasted as employees seek tools outside their own organization because of simplicity and less bureaucracy.
Company IT resources are wasted as employees seek tools outside their own organization because of simplicity and less bureaucracy.
![]() Shadow IT can create a dysfunctional IT environment between the IT organization and business groups.
Shadow IT can create a dysfunctional IT environment between the IT organization and business groups.
![]() Shadow IT can create inefficiencies and can be a barrier to innovation by blocking the establishment of more efficient work processes.
Shadow IT can create inefficiencies and can be a barrier to innovation by blocking the establishment of more efficient work processes.
Industry surveys also support this trend. A recent survey conducted by advisory firm CEB shows that CIOs of 165 organizations (representing more than US$47 billion in IT spending) estimate shadow IT to be 40% beyond the official IT budget. One company survey showed that one in four admits to purchasing and/or deploying a cloud application such as Salesforce.com, Concur, Workday, or Dropbox. Close to 72% of executives in a recent survey admit they don’t know how many shadow IT applications are being used within their enterprises. Gartner predictions show that IT budgets are moving out of the control of IT departments.
Shadow IT causes many compliance issues since the IT department does not have a clue regarding the sites employees visit and how they are used. Regulations that require business compliance include the following:12
![]() SOX (Sarbanes-Oxley Act)
SOX (Sarbanes-Oxley Act)
![]() Basel II (international standards for banking)
Basel II (international standards for banking)
![]() COBIT (Control Objectives for Information and Related Technology)
COBIT (Control Objectives for Information and Related Technology)
![]() FISMA (Federal Information Security Management Act of 2002)
FISMA (Federal Information Security Management Act of 2002)
![]() GAAP (generally accepted accounting principles)
GAAP (generally accepted accounting principles)
![]() HIPAA (Health Insurance Portability and Accountability Act)
HIPAA (Health Insurance Portability and Accountability Act)
![]() IFRS (International Financial Reporting Standards)
IFRS (International Financial Reporting Standards)
![]() ITIL (Information Technology Infrastructure Library)
ITIL (Information Technology Infrastructure Library)
![]() PCI DSS (Payment Card Industry Data Security Standard)
PCI DSS (Payment Card Industry Data Security Standard)
![]() TQM (Total Quality Management)
TQM (Total Quality Management)
In summary, shadow IT presents a new set of challenges for business and IT leaders, including how to manage the costs and risks associated with cloud adoption and how to establish effective cloud management processes.
Shadow IT: Is This a Necessary Evil?
Why is shadow IT used in organizations in spite of all the risks? The main reason is that IT departments with a legacy infrastructure are slow to react to the needs of the people in the organization. Here are some additional reasons:
![]() The IT departments fail to keep up with employees’ technology needs.
The IT departments fail to keep up with employees’ technology needs.
![]() The IT departments have legacy systems and work processes are slow to react.
The IT departments have legacy systems and work processes are slow to react.
![]() The IT departments do not have the budget to meet the demands of employees.
The IT departments do not have the budget to meet the demands of employees.
![]() The IT departments are not innovative and not able to keep up with technology transformations.
The IT departments are not innovative and not able to keep up with technology transformations.
Creating a Shadow IT Solution
One of the ways to solve the problem just described is to create a shadow IT solution that will provide the answers to the following questions:
![]() How much shadow IT is a problem? In other words, what is the extent of the shadow IT in the organization?
How much shadow IT is a problem? In other words, what is the extent of the shadow IT in the organization?
![]() What cloud providers are employees reaching out to?
What cloud providers are employees reaching out to?
![]() Is there a way to monitor the network and determine communications service providers that are being used and the extent of usage?
Is there a way to monitor the network and determine communications service providers that are being used and the extent of usage?
![]() Can the solution provide the IT department a way to remediate the situation (that is, provide the same capabilities as the shadow IT)?
Can the solution provide the IT department a way to remediate the situation (that is, provide the same capabilities as the shadow IT)?
![]() Can the solution be automated with certain policies?
Can the solution be automated with certain policies?
![]() Can there be an Intercloud hybrid solution to remediate shadow IT?
Can there be an Intercloud hybrid solution to remediate shadow IT?
Shadow IT Solution Architecture: Traffic Data Collection, Analysis, and Consumption Analytics
Public cloud services are being adopted rapidly because they make good business sense. Why? Because they help businesses become more agile and reduce costs and complexity. However, the transition to cloud has led to shadow IT, or rogue cloud services used without the knowledge of IT. Cisco has found that there are typically 5 to 10 times more cloud services being used than are known to IT. The increase of shadow IT cloud services presents new trials for leaders, including greater risks, increased costs, and challenges in governing new cloud vendors.
With the Cisco Data Center Assessment for Cloud Consumption service, you can know which public cloud services your business uses and become more agile, reduce risks, and optimize your public cloud costs.
Figure 3-14 shows the traffic data collection and analysis to determine shadow IT providers. The cloud usage collector is placed at the customer’s premises to collect the traffic data. The collected data is forwarded to the Cisco cloud, where analysis is performed. The data is benchmarked to determine which cloud providers are accessed, and consumption analytics are displayed on a web portal.
With collection tools in the network, this tool can help you find out what cloud services employees are using across your entire organization. Using this information, the Cisco cloud experts will help you identify and manage cloud security risks and compliance issues. They will also determine what you’re really spending on cloud and find ways to save money. Finally, they will provide suggestions for new processes for managing cloud vendors, enabling you to launch new services faster and be more responsive to business needs. This service will help you track how cloud services are being used and help you collaborate with business leaders on how to take advantage of cloud to improve results.
Further details and data sheets can be found in references 13–15 at the end of the chapter.
Customer Benefits of Cisco Data Center Assessment for Cloud Consumption Service
With the Cisco Data Center Assessment for Cloud Consumption service, you can
![]() Understand how cloud is being used in your organization by discovering unknown cloud services
Understand how cloud is being used in your organization by discovering unknown cloud services
![]() Manage risks by finding cloud security risks and compliance issues
Manage risks by finding cloud security risks and compliance issues
![]() Reduce costs by determining what you’re really spending on cloud, and discover ways to save money by consolidating or discontinuing services
Reduce costs by determining what you’re really spending on cloud, and discover ways to save money by consolidating or discontinuing services
![]() Become more agile with improved processes for governing cloud service providers and establish faster ways to select and deploy cloud services to meet the needs of your business
Become more agile with improved processes for governing cloud service providers and establish faster ways to select and deploy cloud services to meet the needs of your business
![]() Work better with lines of business by understanding public cloud needs and responding faster to new requests
Work better with lines of business by understanding public cloud needs and responding faster to new requests
Summary
This chapter described how businesses are changing to take advantage of the new technologies and moving from B2B business models to B4B business models. In the cloud economy, businesses are reducing their capital expense and buying the services that are required to meet all of their business goals. In this case, the burden has shifted from the customer to the vendor to make sure all the infrastructure works the way it is supposed to and produces the business outcomes required by the client. The shift from B2B to B4B makes operating expenses more important. Operating expenses are everyday expenses, unlike capital expenditures, so it is essential to automate operations and processes to reduce them.
We also presented the TBM Framework, which ties together business management, IT, and technology management. Some of the new technologies and their impact on the business and operations were presented, as well as some best practices for aligning IT with the business. This chapter also described some of the key features required for achieving Web-scale IT services operations.
Shadow IT exists in all IT departments, and the chapter included a use case showing why it exists and how it can be avoided using some of the technologies available. Cisco can help alleviate the situation and help IT operate as a business to meet its clients’ needs.
Key Messages
![]() Businesses are being transformed from B2B to B4B, and vendors need to change their business practices in order to stay competitive and stay in business. Smaller vendors can provide the same services as large vendors with the advent of cloud technology.
Businesses are being transformed from B2B to B4B, and vendors need to change their business practices in order to stay competitive and stay in business. Smaller vendors can provide the same services as large vendors with the advent of cloud technology.
![]() Business transformation, IT transformation, and technology transformation are all tied together as shown in the TBM Framework. Technologies have wide implications for business models. For example, Apple’s miniaturization of the mobile device created one of the biggest consumer product companies in the world and brought about many changes in the way people work, communicate, and live.
Business transformation, IT transformation, and technology transformation are all tied together as shown in the TBM Framework. Technologies have wide implications for business models. For example, Apple’s miniaturization of the mobile device created one of the biggest consumer product companies in the world and brought about many changes in the way people work, communicate, and live.
![]() IT transformation needs to take place along the lines of technology and business transformation, and IT departments and CIOs need to act like service providers meeting the needs of their customers. The digital disruption facing companies is so intense that one-third of corporate leadership teams will not make the transition over the next three years. For CIOs, though, it’s an opportunity to elevate their roles.
IT transformation needs to take place along the lines of technology and business transformation, and IT departments and CIOs need to act like service providers meeting the needs of their customers. The digital disruption facing companies is so intense that one-third of corporate leadership teams will not make the transition over the next three years. For CIOs, though, it’s an opportunity to elevate their roles.
![]() It is important to make sure Web-scale IT service operations are included in the design and operation of clouds that include new technologies such as cloud, SDN/NFV, automating the operations, and data management for analytics.
It is important to make sure Web-scale IT service operations are included in the design and operation of clouds that include new technologies such as cloud, SDN/NFV, automating the operations, and data management for analytics.
![]() Shadow IT is inevitable in most enterprises. It is caused by the inefficiencies and ineffectiveness of IT departments. It should be managed through some of the techniques proposed in this chapter, so that IT departments in the enterprise do not get outsourced, stay in business, and operate as a business.
Shadow IT is inevitable in most enterprises. It is caused by the inefficiencies and ineffectiveness of IT departments. It should be managed through some of the techniques proposed in this chapter, so that IT departments in the enterprise do not get outsourced, stay in business, and operate as a business.
References
1. J. B. Wood, Todd Hewlin, and Thomas Lah, B4B: How Technology and Big Data Are Reinventing the Customer Supplier Relationship (Point B Inc., 2013).
2. Dr. Vasudeva Akula, Director, Global Business Enablement, NICE Systems, “Closing the Consumption Gap with Insights from Value Realization Scorecards,” presentation at TSIA conference, 2012.
3. John P. Kotter, “Leading Change: Why Transformation Efforts Fail,” Harvard Business Review, January 2007, https://cb.hbsp.harvard.edu/resources/marketing/docs/95204f2.pdf.
4. www.cioinsight.com/c/a/Foreward/What-Is-IT-Transformation-Really.
5. Rachael King, “Cisco’s John Chambers: Digital Disruption Is an Opportunity for CIOs,” Wall Street Journal, February 3, 2013, blogs.wsj.com/cio/tag/wsj-cio-network.
6. Nick Earle, Cisco SVP in services, “The Future of Service Sales,” TSIA conference, Las Vegas, 2013, www.youtube.com/watch?v=4l-UUQfulQc.
7. www.referenceforbusiness.com/management/Str-Ti/Technology-Management.html.
8. http://blogs.gartner.com/thomas_bittman/2015/02/05/why-are-95-of-private-clouds-failing/.
9. http://csrc.nist.gov/groups/SNS/cloud-computing.
10. “Gartner Says Cloud Computing Will Be as Influential as E-business,” June 26, 2008, www.gartner.com/it/page.jsp?id=707508.
11. http://opensource.com/resources/what-is-openstack.
12. https://en.wikipedia.org/wiki/Shadow_IT.
13. Cisco Data Center for Cloud Consumption Services Overview: Bringing Cloud Services Out of the Shadows.
14. Cisco Data Center Assessment for Cloud Consumption Service: Data Sheet.
15. Cisco Data Center Optimization for Cloud Consumption Service: Data Sheet.