1
The IoT: Intrusive or Indispensable Objects?
1.1. Introduction
Following Bill Gates’ famous statement in the 1970s, “A computer on every desk and in every home,” the world entered the era of computer science during the 1980s. This democratization became reality in developed countries, although not as much in third-world countries, which is a state of affairs identified by a digital and technological divide. New technological advances (computer science, telecommunications, miniaturization of electronics, etc.), led to the emergence of other solutions, new chips and electronic circuits, new computer systems and communication protocols, whose successful realization is the spread of mobile telephony and access to new compact and portable products. The smartphone is the prime example of this change; it now integrates all of the functions and services of a computer, making exchanges and communication accessible to a very large number of people. Moreover, with the connected watches that have appeared in the last few years, we are truly in the middle of the era of connected and portable devices.
Contrary to the development of computers and mobiles, whose concepts do not differ very much from one manufacturer to another (Apple, Windows, IBM, Dell, HP, etc.), the concept of the Internet of Things is broader and refers to a new way of living and managing current and professional affairs via the Internet. The environment is now more open for businesses and start-ups to innovate and offer new services and technologies. Nevertheless, the major players already have a head start in the area: like Cisco for networks, Google for the management of big data, Microsoft for Cloud Computing, Intel for micro-processors, etc. It is clear that development and investment in the IoT, the businesses mentioned above, promising a future that is radiant but which remains nevertheless to be discovered and which will reveal whether this was a revolution or a passing technological fad. One of the goals of these objects is the transformation of uses or even creating new ones.
1.2. The age of miniaturization and technological progress
The development of computers and mobile telephony has been the technological duo of choice for several years. This has allowed the arrival in the markets of innovative projects, amazing and increasingly spectacular miniatureization. The ENIAC1 was the first electronic computer, occupying an area of a hundred square meters made to imitate a mechanical calculator2. An ultra-miniature version of the ENIAC computer, which is the size of a single integrated circuit chip, was developed by a research team from the University of Pennsylvania (Figure 1.1).

Figure 1.1. The miniature version of the ENIAC
The appearance of smartphones has been accompanied by enormous technological progress in the last decades, from the testing of the first mobile telephone, the Motorola DynaTAC 8000X3 in 1973, to Samsung’s most recent ultra-comprehensive and light smartphone4, progress is exponential at different levels (Figure 1.2), computation power, design and ergonomics, energy consumption, etc. These advances have brought about a considerably profound change in the nature of the relationship humanity has with the objects and environment that surround it and a change to every person’s everyday life and lifestyle.

Figure 1.2. The evolution of mobile telephony
1.3. The history of a digital ecosystem
The history of the Internet is enthralling and rich through its path of developing as an open system that is in perpetual motion. Despite its young age (it has been 25 years since the web was launched), the network has not stopped surprising us, thanks primarily to the work of communities of engineers and developers coming from different areas of study such as computer science, telecommunications and above all electronics. These are communities that connect to innovate and to respond to user needs in a collaborative and participatory spirit. Even if the origins and ideas of this network date back more than 50 years, a real enthusiasm was witnessed with the arrival of its best-known service, the web, which was put into operation back in the beginning of the 1990s. The revolution was provided by a multimedia navigation system with the development of the HTML language5 that could integrate text, images and above all links between documents and fragments of documents. This extension of the Internet has taken on a new dimension, offering new experiences and new uses, as well as new difficulties, for navigation and tracking in a space of very dynamic and occasionally extensible links [BAL 96].
Since its conception, several layers have been added to the first version of the web. We can distinguish three essential steps in its development:
- – the web 1.0: represented by the debut of the static and above all passive web of the 1990s, it offered basic navigation between pages of information whose purpose was documentary reference. This step was marked by the simplicity of the language used: HTML6;
- – the web 2.0, called the collaborative web, of the 2000s was the web of blogs, forums and CMS, with the web passing into active mode, with the users becoming actors and producers of content they played a contributing role and took forceful ownership of its new digital tools;
- – the web 3.0: represents the current web of which semantics and connected objects are the two principle technologies.
From the web 1.0 to the web 3.0, to hypermedia [BAL 96] to the hyperobject7, the Internet has gone from being based on information to being based on objects, from an Internet of links between documents, to one linking physical or digital objects (documents and information). It is a communicating and autonomous ecosystem, whose different objects are easily identified, and secure exchanges according to standardized protocols. These networks of objects8 already pose the problem of traces of data generated by the activities and exchanges of connected objects. Data to be exploited from the perspective of digital processing, according to approaches of knowledge engineering, another area concerned with the large masses of data otherwise known as Big Data.
1.4. Internet of Things, which definition?
The term Internet of Things (IoT) refers to a network that is more and more spread out, one of material objects connected to the Internet, identified and recognized, like all other traditional devices that we use every day, such as computers, tablets, smartphones, etc. Perceived these days as a new technological revolution, the Internet of Things is defined, according to Weil and Souissi [WEI 10], simply as:
“The extension of the current Internet to all objects able to communicate, directly or indirectly, with electronic devices that are themselves connected to the Internet.”
An official definition of the IoT remains to be found, a job for the actors in the domain, even if the overall concept and its components are wellknown, such as the communication of data streams and associated protocols which remain a large open workshop.
Recently, tech giant Google has developed “Brillo”, a platform for peripheral devices which handle the Internet of Things. It will be able to work with a very large optimization of the memory and processer, Wi-Fi and Bluetooth, it is derived from the “Android” operating system. Other companies have invested in the area, with Samsung’s Artik, the Agile IoT platform from the manufacturer Huawei, intended for the IoT. Microsoft is not excluded, with a new version of its Windows 10. This shows the interest that large technology companies have in this new extension of the Internet.
1.5. The security of connected objects: the risks and the challenges
Data security is a crucial point and one of the greatest obstacles to the development of the IoT on a large scale. As with the Internet, security is a workshop in perpetual evolution, the problem is posed and is transposed logically onto the protection of data sent and/or received by a connected object and becomes a great technological challenge for the different actors in this new ecosystem.
We regularly see that digital insecurity is a recurring question, especially on the Internet network, affecting the hacking of websites, message servers, e-mail accounts and this is often done with a remote takeover of machines. This insecurity logically extends to the IoT. Like a connected computer, any connected object could be subject to hacking, a takeover, the installation of spyware, etc. With the impossibility of controlling and limiting the development of this ecosystem, it is necessary to look for and suggest security strategies for protecting the networks of these objects and to fill in the gaps in security detected.
The role of the telecommunications sector was and remains primordial for safeguarding the communication of these objects (object-object or object-person), as for the Internet, it is their responsibility to make as big an effort as possible to put in place solutions in the areas of security. A role that is just as important as that of software developers.
1.6. Protocols, standards and compatibility: toward a technological convergence
In this emerging market, a long-awaited consensus between the industrial actors in the domain is yet to arrive. It would make many products compatible with each other for the purposes of communication and the exchange of data. Currently each business uses its own technological solutions, a product manufactured by Samsung cannot exchange with one from LG, such as the automatic display of information from a television of one brand to a television from another brand. Task forces from several manufacturers9 have recently discussed standards for objects connected to the Internet, to allow devices to mutually understand each other and determine the requirements regarding connectivity and interoperability between multiple devices. The question of norms and standards is central in the case of a need for technological convergence:
“Normalization (and/or standardization) are notions which have become unavoidable with cultural, industrial, economic and especially digital globalization” [FAB 13].
The notions of norms and standards are present in Europe, and in America under the same name. It is understood that a norm is a frame of reference published by an official international organization for standardization such as the ISO10, ECS11, AFNOR12 or the IEEE13. A standard can be described as a group of recommendations advocated by a group of representatives and informed users that is widely disseminated and used. HTML (W3C) format14 for the web is the prime example of this type of procedure.
1.6.1. The origins of some norms and standards
Because the world of the IoT is obscured by a multitude of protocols, it is difficult to make an exhaustive list of them. A significant number of diverse solutions are ready to be developed quickly once norms or standards are integrated into future projects on a large scale. There are still many hypotheses to be confirmed in this rapidly expanding market. Some solutions are already on the market and others are in the process of development and validation, with the goal of standing out with their effectiveness and how simple they are to implement, an important point for small businesses and start-ups joining the IoT market, looking for communications solutions at the lowest cost until an agreement at this level has been reached. The goal will be to show the interest and usefulness of their products and to create a place and a name within the booming market15.
In terms of communication, wireless is the best adapted to connected, and often portable, products. WiFi16 and its variants are technologies that are increasingly popular at the moment, for short-/medium-distance communication17 indoors and, with Bluetooth, as a short-distance18 communication technology. Numerous protocols19 supplement these two technologies, or even compete with them. Some have advantages such as a reduction in energy consumption20:
- – WiFi direct21: unlike WiFi, which makes it possible to connect objects via an access point (an Internet box, for example), WiFi direct provides direct connectivity between two objects;
- – Bluetooth LE/Smart22: considered complementary in relation to Bluetooth, it has low energy consumption, reduced coverage and a lower output. It is a solution for some types of connected objects;
- – the Bluetooth aptx: a means of communication intended for audio broadcast by transcoding flows at a rate higher than 350 Kbit/s. A codec is used for the compression and diffusion of sound where the transmitter and the receiver must be compatible;
- – the ZigBee23: this solution24 offers connectivity with low energy consumption that is easy to embed within various connectable products, with a low bit rate that goes up to 250 Kbit, and a short coverage of around 100 meters;
- – Near Field Communication (NFC)25: a solution for proximity communication (for a distance of a few centimeters). This protocol has its advantages: a miniature chip and the possibility of securing exchanges via an embedded encryption. Numerous uses, contactless payment, etc.;
- – the Z-Wave26: this wireless protocol solution makes it possible to link several devices, it goes both ways, sending and receiving data. Its use is adequate for home automation, with a coverage of 30 meters inside, to 100 meters outside;
- – the Thread: established by Samsung and Nest Labs, is a competitor of the technologies mentioned previously, and consumes very little energy. It is a solution for home automation connectivity, to link different objects and devices in a network and to Internet. An alliance of several partners including Silicon Labs and Google gives it significant weight in the creation of future norms and standards.
1.7. Humanity, intelligence and technologies
1.7.1. Crowdfunding as an aid to innovation
Securing funding for making an innovative project a reality, especially for a young business without a history of activity and the multiplication of ideas and projects in the era of globalization, is not an easy thing. With the arrival of the IoT, the enthusiasm for this type of financing is without precedent27. Crowdfunding is an original principle (and an innovative approach), a fashionable solution for launching innovative projects with strong technological potential and for raising funds without too many constraints. The start-up Looksee28, for example, is working on the Eyecatcher project, a smart bracelet that combines design, fashion and technological innovation (Figures 1.3 and 1.4).

Figure 1.3. The Eyecatcher bracelet, display of notifications and messages in real time

Figure 1.4. The Eyecatcher in fashion mode
The project’s originality and innovation have already attracted more than 400 participants on the participatory platform Kickstarter, who have supported the project by raising hundreds of thousands of dollars, even though the creators of the project asked for only two thirds of this amount. Innovation lies at the level of low energy consumption thanks to its e-ink (digital ink) screen. Communication is done via Bluetooth with a smartphone application and makes it possible to send photos, designs and above all be programmed to send notifications such as e-mail, scheduling, etc.
1.7.2. Participatory environmental sensors and citizens
The Green Watch Project is a pioneering project in the field of connected objects and the result of research and development between an academic institution and industrialists. This project, of which the Paragraphe laboratory was one of the key elements for its realization, can be summarized as a group of participatory citizen sensors to measure the levels of ozone and noise in an urban environment. This project is part of an effort in the participatory and experimental sciences to rethink the relationship of the individual with his or her environment.
The technological and experimental aspect of the Green Watch Project consists of using two sensors: one for ozone and the second for noise. Geographic localization, necessary for getting the user’s coordinates, is done with a GPS chip. The data is communicated via a mobile terminal (a telephone) with a Bluetooth chip.
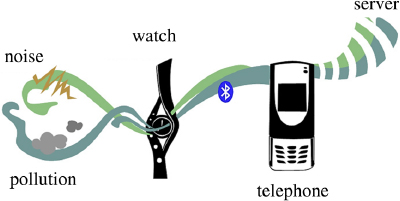
Figure 1.5. Architecture of the Green Watch

Figure 1.6. Map of the data from Green Watch sensors
This architecture29 (Figure 1.5) provides the possibility of measuring, recording and communicating the data to an online processing and visualization mapping platform (Figure 1.6)30.
Connected objects for the environment have shown their effectiveness in many contexts, the automation of sampling in high-risk places, such as during nuclear disasters, as was the case in Fukushima. This was an example where citizens searched on the Internet and social networks in order to understand the dangers of the situation and act accordingly. Radiometers had been installed in the area of the accident to measure radiation in real time and were connected to the Internet network, and the results were published on social media [SEG 15].
1.7.3. When digital art goes into connected mode
Fictions d’Issy31 is a generative and interactive novel developed at Paragraphe and presented during the Cube Festival, which was dedicated to digital creation, in 2005. The originality of the project’s approach consisted of combining communication tools by connecting a text generator [BAL 06] to readers by means of a mobile telephone and displaying the texts generated on electronic information signs in the urban space of the town of Issy-les-Moulineaux (Figure 1.7), a first for this type of digital installation. This connected artistic work project was a pioneer in the field of living art32. The love story it tells is generated continuously by fragments of text of two characters who are evolving in the town’s urban landscape.

Figure 1.7. A display panel participating in the Fictions d’Issy installation33
The principle of this connected work consists of the successive demands for the generation of fragments of texts (Figure 1.8) by readers via mobile phone calls using the keys on the keypad, with each one of the keys chosen influencing how the story unfolds and transforming the reader into an active participant in the story.
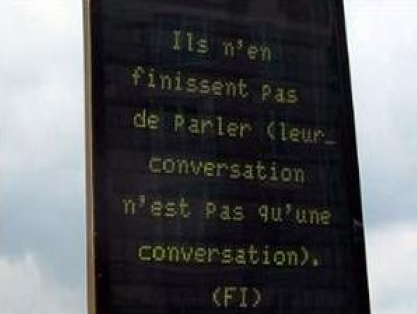
Figure 1.8. Example of a fragment of the story displayed on an information panel in the town34
1.7.4. Home automation for a connected and communicating habitat
In the past, the costs of constructing smart urban places were too high, and only accessible to a minority. The solution required the intervention of a specialized company, with a cumbersome process of integration and adaptation of devices. With the emergence of the IoT, home automation has made huge progress and has now become easy and inexpensive. You simply choose a central control device (Home Hub) compatible with a maximum of home automation objects35. Home automation is the field which has put the most items on the market, and it has not stopped developing since the first days of the Internet, the evolution of networks and video surveillance. We now have a connected and communicating habitat, if not to say intelligent without exaggeration, because several areas36 are involved in this revolution: security, energy, lighting, health, etc.
The smartphone has become the interface and the means of access and control for home automation. It is a simple and easy application interface available for the management of components. One pertinent example would be controlling entrance to and exit from the house, without the need for door keys, after the emergence of smart locks, such as the “Kevo” lock from the American company Kwikset37 which makes it possible to order the opening or closing of a door remotely and without a key (Figure 1.9). The contribution of this type of object to everyday life is undeniable. If someone rings the doorbell, you are alerted via smartphone and it is no longer necessary to stay at home to let in a visitor (or a repairman, for example). Combined with a connected camera, it will be possible to hear and speak to him remotely.

Figure 1.9. The Kevo smart lock from the American company Kwikset
Smart cameras are part of the array of connected objects created in order to address the undeniable security needs of private individuals as well as professionals. They take up the torch of traditional video surveillance which consisted of setting up an IP camera and accessing it remotely. The new generation is clearly evolving: the HD Home from Withings38 is a camera that integrates video recognition algorithms and night vision (Figure 1.10). Another function is audio analysis, which makes it possible to understand specific sounds such as the crying of children.

Figure 1.10. The Withings HD Home intelligent video surveillance
The interaction of these connected objects with the user allows object ↔ user communication via a smartphone, and an exchange of the data issued from the objects’ environment by sensors, such as temperature, humidity, continuous measurement of the ambient air quality, and possibly allows other actions via communication with other objects.
1.7.5. Connected objects, a step toward the enhanced human
In Sweden, the use of local currency for payment has become almost obsolete. Donating to the church during mass or paying for a baguette or coffee is now done with ultra-modern methods, a smartphone in most cases, and, surprisingly, contactless payment by chips implanted under the skin of the hand (Figure 1.11). To make a payment, you just have to present your hand at payment terminal. Solutions are being tested by businesses for payments limited to cafeterias. A Canadian sports club now allows its members to be implanted with a chip with limited data to access the stadium39, an experiment which says a lot about the concept of the augmented individual and which provides a glimpse of a future that is closer than we think. Other possibilities are being considered, since personal, financial and other data is loaded onto the electronic chip.

Figure 1.11. Chip implanted under the skin of the hand40
With the connected bracelets, activity sensors and the implant of a micro-chip for (auto-)surveillance, human beings are increasingly hyperconnected. The field of the “Quantified-Self” and the example of Chris Dancy41 say a lot. This individu-Data [MER 13] shows the complexity that humanity could maintain with the masses of data that come from connected objects, and the way to interpret and use them in a healthy way.
This raises myriad questions about the connected human and questions about this way of life: security, private life, embedded personal data, etc. Social divisions are omnipresent when speaking about technological innovation, since older people who do not follow these technological changes very closely often find themselves on the fringes of these new uses and in difficulties socially, simply due to the fact that that societal evolution follows the majority and not the minority, which is the case in the digital society in which we have been living for some time now.
Another possibility for connected objects is to become a method of payment like any other. The company MasterCard, is working on ways to transform different fashion or other objects such as bracelets, rings, and smart watches42 (Figure 1.12).

Figure 1.12. Payment via a smart watch
1.8. Conclusion
The technological revolution which has taken place over the course of recent years has totally changed the concept of computing. Previously, efforts were concentrated mostly on the development of office computers, smartphones, portable computers, tablets and other similar products. The change now operates on another level, with products that increasingly respond to consumer needs in daily life; products that are less bulky and with a refined design, with shapes that integrate logically into the user’s environment, or physically in them or on them. This period was accompanied by advances in the area of the technology industry such as flexible touch screens, now used in smart watches, available on the market recently. Another dimension of use has been crossed, between computer products and these new miniature intelligent devices. It is no longer only a user-centered usage but one extended to his or her personal and professional environment. More and more objects make it possible to control the different elements of a habitat, a car, urban spaces, etc.
The rush toward the IoT bubble will continue, as with the first rush toward the Internet bubble, without worry about the medium- and long-term problems and risks that this provokes. The user’s private life will be at the center of these preoccupations, increased control of the environment by various objects leaves a very small margin for freedom. Used to making choices himself, the user will see himself overtaken by some decisions whose consequences could be difficult to manage and correct. Hacking is another problem which raises a number of questions and leaves experts and users skeptical about the future. These products could easily be targeted by hacking with Ransomware43 hacking, and put many people in extremely serious situations, whether through control of health devices or the control of private data.
The society of connected objects, via its experts, its users and its businesses, must reconsider and reflect on its future, to provide a perspective that is expert and reassuring at every level, especially security. This was the case with the Internet and its web service, which after several years of development had no real security vision set up. The IoT must find actors44 from the same category as the Internet, to give users a display of confidence, and allow trouble-free development in this environment whose horizon remains to be examined with close attention by experts and researchers in different areas such as computer science, sociology, psychology, etc.
The users are the real actors and decision-makers in the market. Some see connected objects as a new fashion, a trend, which is just temporary for many of the objects already on the market or those to come, and which will fade away with time and combined with an abandoning of media interest in the subject, for others, it is really everyday objects which have a bright future in front of them. Between true innovations and illusory progress, the question will remain open for a long time as long as scientific and economic studies do not validate the economic, social and technological reality of this market.
1.9. Bibliography
[BAL 86] BALPE J.-P., Initiation à la génération de textes en langue naturelle, Exemples de programmes en Basic, Eyrolles, Paris, 1986.
[BAL 96] BALPE J.-P. et al., Techniques avancées pour l’hypertext, Hermes, Paris, 1996.
[FAB 13] FABRE R., HUDRISIER H., PERRIAULT J., “Normes et standards: un programme de travail pour les SIC”, Revue française des sciences de l’information and de la communication, no. 2/2013, available at: http://rfsic.revues.org/ 351, consulted June 15, 2016, made available online January 1, 2013.
[MER 13] MERZEAU L., “L’intelligence des traces”, Intellectica, no. 59, pp. 115–135, 2013.
[SEG 15] SEGAULT A., TAJARIOL F., ROXIN I., “Tweets de Fukushima: Capteurs connectés et médias sociaux pour la diffusion de l’information après un accident radiologique”, Actes du colloque H2PTM’15, ISTE Editions, London, 2015.
[WEI 10] WEIL M., SOUISSI M., “L’Internet des objets: concept ou réalité?”, Annales des Mines – Réalités industrielles, no. 4, pp. 90–96, 2010.
Chapter written by Nasreddine BOUHAÏ.
