Chapter 11
Cisco Forensic Capabilities
“Any product that needs a manual to work is broken.”
—Elon Musk
The focus of this book has been providing readily available tools such as open source applications for the average network engineer. This chapter addresses what is available using open source tools supported by Cisco and tools from the Cisco enterprise security catalog. This includes technology that generates logs, solutions that can be leveraged during an incident response situation, and ways to access data in general using Cisco products such as routers and switches. We highlight each product’s security features but do not go into great detail because you can find that information on the Cisco website.
We first touch on Cisco’s history and how Cisco security products fit within various types of architectures.
Cisco Security Architecture
The Cisco foundational technology is networking. Most networks have or at some point have used Cisco technology for general routing and switching. As business grew, Cisco expanded into different markets, including security; today it is seen as a market leader in this space. The current Cisco catalog targets capabilities that address different parts of cyberattacks. Cisco calls this approach the Before, During, and After (BDA) strategy, which is a summarized version of the Cyber Kill Chain Model originally developed by Lockheed Martin. Cisco inherited the BDA strategy from the Sourcefire acquisition and continues to focus on a threat focus message. The message is broken down into the concepts shown in Figure 11-1.

Figure 11-1 The Cisco Before, During, and After Summary of the Cyber Kill Chain
![]() Before the Attack: Limiting communication to trusted parties to reduce the risk of attacks before they happen. For example, if an attacker builds a web server disguised as a bank to remotely attack you, would you be able to determine the difference between a real bank and this potentially malicious website? By blocking the malicious website, you prevent the attacker from being able to attempt an attack against you. This example showcases the concept of reputation security, which is giving a website a reputation or credit score that is adjusted as traffic from the source is seen as safe or malicious. We cover this topic in more detail shortly.
Before the Attack: Limiting communication to trusted parties to reduce the risk of attacks before they happen. For example, if an attacker builds a web server disguised as a bank to remotely attack you, would you be able to determine the difference between a real bank and this potentially malicious website? By blocking the malicious website, you prevent the attacker from being able to attempt an attack against you. This example showcases the concept of reputation security, which is giving a website a reputation or credit score that is adjusted as traffic from the source is seen as safe or malicious. We cover this topic in more detail shortly.
Another Before technology example is access control, sometimes called network access control or NAC. NAC technologies are designed to prevent any random system from being offered full network access upon plugging in to a network. The idea is that an attacker would have to be viewed as an approved system to gain access; thus, it is unable to plug in to a system and launch an attack.
It is important to point out that Before technology isn’t typically 100 percent effective, but it makes it harder for attackers to execute an attack. If we look back at our web server example, an attacker could compromise a trusted website such as a school’s homepage and launch attacks from there. Doing so, however, would require more effort, reducing the likelihood that an attacker will go through the trouble of attacking this sample school just so it could attack another target. It is also important to point out that the goal of a security operations practice is to prevent any threat at this stage of the attack. The main reason for this is to block attacks before they happen to prevent the attack from having a chance to exploit a vulnerability by blocking the malicious party from being able to attempt an attack. The attacker could have an unknown exploit known as a day zero, but there isn’t an established channel for it to be delivered.
Technology Examples: Firewalls, VPN, Access Control, Content Filters
![]() During the Attack: Detecting and preventing attack behavior. This capability is typical of technologies leveraging attack and behavior signatures or looking for known threats. These technologies are not 100 percent effective due to the limitations on the number of signatures that can be enabled and the pure number of potential vulnerabilities that exist in the average network environment. Best practice is to continuously tune this technology so that it protects the vulnerabilities that exist within your network. Continuously tuning is important because a vendor can’t autoprovide this data without knowing where you are vulnerable. Usually, informing security products about local vulnerabilities is a manual process known as tuning the security solution, but some vendors such as Cisco offer vulnerability data scanning that automatically tunes detection capabilities. Other capabilities that can enhance detection seen in the During phase can come from features such as machine learning and behavior analysis techniques, which typically are a focus of After technologies.
During the Attack: Detecting and preventing attack behavior. This capability is typical of technologies leveraging attack and behavior signatures or looking for known threats. These technologies are not 100 percent effective due to the limitations on the number of signatures that can be enabled and the pure number of potential vulnerabilities that exist in the average network environment. Best practice is to continuously tune this technology so that it protects the vulnerabilities that exist within your network. Continuously tuning is important because a vendor can’t autoprovide this data without knowing where you are vulnerable. Usually, informing security products about local vulnerabilities is a manual process known as tuning the security solution, but some vendors such as Cisco offer vulnerability data scanning that automatically tunes detection capabilities. Other capabilities that can enhance detection seen in the During phase can come from features such as machine learning and behavior analysis techniques, which typically are a focus of After technologies.
Technology Examples: Antivirus, Antimalware, Intrusion Detection, Intrusion Prevention, Email/Web security detection solutions
![]() After the Attack: Handling post-compromise security. This means anything that has bypassed the Before and During phases and is typically handled during the incident response plan. After technology is critical for validating how the other phases are functioning. Without After technology, it is pretty much impossible to know what has bypassed the existing Before and During technologies. Forensics typically is heavily involved in After technology.
After the Attack: Handling post-compromise security. This means anything that has bypassed the Before and During phases and is typically handled during the incident response plan. After technology is critical for validating how the other phases are functioning. Without After technology, it is pretty much impossible to know what has bypassed the existing Before and During technologies. Forensics typically is heavily involved in After technology.
Technology Examples: NetFlow, Honeypots, Behavior-based Technology/Baselining, File Analytics
The BDA could be used, for example, against an exploit kit delivering ransomware. For example, an attacker sends an email with the goal of having the victim click a link within the email to send him to an attack server. That server identifies a vulnerability on the victim’s computer and pushes ransomware to the system. Ransomware then launches and encrypts the files. Figure 11-2 shows the basic architecture of an exploit kit delivering ransomware.

Figure 11-2 Exploit Kit Delivering Ransomware
The BDA approach works like this: the Before stage blocks the email or user request to access the website when he clicks the malicious link. The During stage identifies that the malicious website is attempting to abuse a vulnerability and prevents exploitation and delivery of the ransomware. The After stage identifies that the malicious payload installed on the victim’s system is attempting to encrypt the hard drive and prevent the malware from executing. In Figure 11-3, security technology is used to address this attack example.

Figure 11-3 Technology Defending Exploit Kits
The goal for a defender is to stop the attack as early as possible in the BDA strategy. For example, if the After technology catches a threat, the focus is to enhance the During and Before stages to block this attack. In this example, the IPS needs to be updated via signature and behavior to identify the attack that was missed. The email and web security solutions need to add the malicious web source to a blacklist to prevent future users from accessing that source or receiving email from associated domains.
We cover Cisco technology from a BDA viewpoint throughout this chapter. Before going into enterprise solutions from Cisco, let’s start with what open source solutions are available.
Cisco Open Source
Cisco has acquired many companies over the years, but one in particular was built on a revolutionary open source technology. In 2001, Martin Roesch developed the Snort intrusion detection and prevention software, which various organizations use widely today. Martin later started Sourcefire, which over the years offered a handful of open source as well as enterprise solutions. Some open source options created by Sourcefire and now supported by Cisco include but are not limited to the following:
![]() Snort: Free network intrusion detection system (NIDS) software for Linux and Windows.
Snort: Free network intrusion detection system (NIDS) software for Linux and Windows.
![]() Forensics Value: Snort is a customizable IDS and IPS. Examples of its value were discussed earlier in this book.
Forensics Value: Snort is a customizable IDS and IPS. Examples of its value were discussed earlier in this book.
![]() ClaimAV: Antivirus engine for detecting Trojans, viruses, malware, and other malicious threats.
ClaimAV: Antivirus engine for detecting Trojans, viruses, malware, and other malicious threats.
![]() Forensic Value: Host security tool that can prevent malicious files from executing and generate valuable log data. If you don’t want to pay for an antivirus, consider ClaimAV.
Forensic Value: Host security tool that can prevent malicious files from executing and generate valuable log data. If you don’t want to pay for an antivirus, consider ClaimAV.
![]() Razorback: Framework that provides advanced processing of multitiered data and detection of client-side threat events.
Razorback: Framework that provides advanced processing of multitiered data and detection of client-side threat events.
![]() Forensic Value: Razorback is made of a dispatcher surrounded by nuggets. Each nugget performs discrete tasks including data collection, detection and analysis, output, intelligence, correlation, and defense updates.
Forensic Value: Razorback is made of a dispatcher surrounded by nuggets. Each nugget performs discrete tasks including data collection, detection and analysis, output, intelligence, correlation, and defense updates.
![]() Daemonlogger: Fast packet logger designed specifically for use in NSM environments.
Daemonlogger: Fast packet logger designed specifically for use in NSM environments.
![]() Moflow Framework: Framework that provides tools for vulnerability discovery and triage.
Moflow Framework: Framework that provides tools for vulnerability discovery and triage.
![]() Joy: Tool used for capturing and analyzing NetFlow and intraflow data.
Joy: Tool used for capturing and analyzing NetFlow and intraflow data.
Enterprise technology focuses on simplifying and enhancing capabilities of tools available in the open source community. This is why people pay for such tools rather than building and supporting technology using tools that are free and widely available. For example, Firepower was developed as an enterprise application layer firewall, IPS, and breach detection technology. Building it with open source tools would require managing multiple applications, developing thousands of attack signatures, and investing hundreds of expert-level hours to manage and interoperate the data. Even with that effort, it probably wouldn’t be close to what can be purchased. I’ve worked on developing tools like this, and there are experts on very specific things like the quality of the user experience, graphic design, and so on that only a larger organization can invest in, hence “enterprise-level technology.”
Enterprise offerings also offer various threat intelligence and attack signature feeds that utilize data available only to paying customers. When somebody asks me to explain the difference between an open source IPS and enterprise offering, I give the analogy of a car engine versus the entire car. Someone could turn a car engine into a car with a lot of work, but it most likely will not be as effective as something professionally built and maintained. Most administrators are busy maintaining security for their organization, so they would rather pay for the right technology versus building it themselves. Plus, what happens when the smart person leaves the company and something new or a bug patch is needed?
Speaking of enterprise technology, let’s switch gears and look at Cisco’s popular enterprise threat management platform. We start here because it offers licensing for Before, During, and After defense features.
Cisco Firepower
The foundation of Cisco Firepower started with technology associated with the Sourcefire acquisition. That foundation technology offered a handful of capabilities, including application layer firewall, intrusion detection/prevention, and advanced malware detection. Once acquired by Cisco, the Firepower technology has enhanced the platform with Cisco’s Adaptive Security Appliance (ASA) firewall and other technology developments. Today, both the ASA platform and Firepower platform are seen as one solution called Cisco Firepower. The Before capabilities for Cisco Firepower are the application visibility and controls as well as URL security feeds; some URL capabilities require a license, whereas the remaining features come with the standard solution. The During capabilities are made up of the intrusion detection and prevention features. The After capabilities include network and endpoint Advanced Malware Protection (AMP).
What is the forensic value? Firepower can provide various levels of details regarding security and network incidents. The firewall data covers all ports and protocols regardless of the license purchased, so any user has access to application firewall capabilities. The URL feed license option can be used to control website content and prevent web sources considered malicious based on various ranking factors. This tool can help develop detailed reports on user activity within the network and how they access the Internet. Figure 11-4 shows a summary page that provides details such as device types on the network, what websites people are accessing, and what applications are installed. There are many built-in reports, so everything can be exported as a report.

Figure 11-4 Cisco Firepower Summary Dashboard
Firepower IPS data is based on an impact ranking system. An impact of zero means the event has occurred outside the profiled network. It is important to validate any of these events that occur within a fully profiled network. An impact four event represents a known host showing acceptable behavior. Impact three means an event may have occurred, such as a relevant port is not open or a protocol is not in use. Impact two is something worth investigating, and impact one is something you would want to act upon immediately. Impact data is based on various data sources, such as protocols, IP, ports, and services. Figure 11-5 shows a Cisco Firepower impact one event, showcasing a web application exploitation potentially providing access to a remote attacker. It is likely important for the investigation of a cyberattack to know details of the attack, such as the parties involved and protocols used. Firepower IPS data can answer those questions with great detail.

Figure 11-5 Cisco Firepower Impact One Event
The final license option for Cisco Firepower is Advanced Malware Protection. This capability is also offered in most of Cisco’s other security technology, such as email, web, and endpoint options. For that reason, we focus on the AMP technology next.
Cisco Advanced Malware Protection (AMP)
Part of the Firepower offering is breach detection, which means looking for threats that bypass common perimeter and signature-based solutions like firewalls and intrusion prevention. Breach detection tends to leverage behavior and anomaly capabilities in regard to questioning unusual and malicious behavior versus looking for known behavior tagged as malicious. Cisco AMP is focused on file behavior because most attackers use files (exploits, malware, ransomware, rootkits, and so on). For example, a PDF file should act like a PDF document file. If that document acts like a malicious file, or it attempts to spread to other systems or encrypt parts of the hard drive, Cisco AMP flags this behavior even if it doesn’t know what the threat is from an attack signature viewpoint. That malicious file has a hash value created and flagged, so any sign of that file can be identified and removed across the network. This includes going back in time, which is also known as retrospective security. This means the file may have been flagged at 5 p.m., but it potentially could have been on the network or another system prior to that time. By continuously monitoring all files at all times, AMP is able to map the entire time that file has been seen on the network. This capability is critical for a forensics investigation into the spreading of malicious software. Figure 11-6 shows file mapping from a Firepower viewpoint.

Figure 11-6 Cisco Firepower File Mapping
Cisco AMP offers multiple options. One option is a network-focused connector that can look at files as they traverse the network. This permits the Cisco AMP technology to monitor files crossing the network. For example, in Figure 11-7, Cisco Firepower has identified a malicious file and created a timeline chart showing when the file first appeared on the network as well as any associated systems that were infected as the threat spread laterally. Figure 11-7 shows how a threat has hit systems represented on the left. By clicking the red bang sign across from those systems, an administrator can get details of the infection at that point in time as well as a map of movement. Most Cisco network security offerings have an AMP license option.
In this example, a file called FedexInvoice_EE776129.exe with the hash value b8d4d6b3…703c5de7 could have been identified at the highlighted point in time by Cisco AMP as being malicious for various reasons. For one thing, a FedEx invoice file should not be an executable, but many users may not understand this concept and click it anyway. After this incident is identified, the hash file could be used to check the rest of the network for any other signs of that file. By using retrospective tagging, Cisco AMP could map all versions of the file regardless of its name because a hash is used to accurately identify the file (we discussed this concept earlier in this book). This capability also enables us to find the true first person who obtained the malicious file, known as patient zero.
It’s critical to understand how the malicious file found its way onto the network. It was probably brought on by a user clicking the wrong thing because it’s obvious that the file is designed to trick people into believing it is a FedEx invoice. Regardless of how it was done, the reason usually comes down to some type of vulnerability being exploited. If the vulnerability isn’t secured, this attack vector is likely to be used again in the future to deliver another malicious file. This is why it is a bad practice to wipe systems that are infected with malicious software without first discovering how that software got installed. Figure 11-8 shows details on patient zero to better understand what happened at the time of infection. Cisco Firepower could now blacklist the source that delivered the file and prevent any movement of that file if it is ever seen on the network moving forward. Here, user Carlota Fontenot was the person who brought this file on the network from 10.131.13.15 using a Firefox browser. This feature can save a ton of time during an investigation of a network breach because most paying customers are going to ask, “How did we get infected?” This report gives you those details in a simple-to-follow method.
There are some limitations of Cisco AMP for Network running on a platform like Cisco Firepower. In this case, it runs from a network, so it does not have visibility or access to the actual hosts that are using the files. Cisco AMP running on a network solution can protect only what it sees; in other words, if a host leaves a network, that host essentially is not protected. Regarding remediation, Cisco AMP for Network can impact only what it can touch, so it can block files from crossing the network but cannot remove files from infected endpoints or see beyond endpoint firewalls.
Cisco AMP for Endpoint solves this concern by offering a lightweight agent that continuously evaluates files seen on the host where it is installed. Cisco AMP for Endpoint also looks for other things such as potential vulnerabilities, which are used to inform Cisco Firepower. Therefore, Firepower IPS settings can adjust detection capabilities based on what is seen by Cisco AMP for Endpoint. In Figure 11-9, Cisco AMP for Endpoint points out vulnerabilities on an asset owned by user Ning. This capability is critical for keeping network detection up to date with the types of hosts that are accessing the network. This example shows five critical vulnerabilities that an attacker could use to exploit this system. Cisco Firepower could enable signatures to prevent exploitation of these vulnerabilities and inform the administrator that she should address this host’s vulnerabilities.

Figure 11-9 Vulnerabilities Found on a Host by Cisco AMP for Endpoint
The CVE values for any identified threats are included and can be clicked to look up more details about why this is considered a high risk to the associated asset. Figure 11-10 shows the details brought up when the administrator clicks CVE-2013-5907. This information is useful when you are providing a digital forensics report explaining how the attacker got in as well as what improvements you would suggest.

Figure 11-10 Details on CVE-2013-5907
Cisco AMP for Endpoint gives the administrator a deep look at all files on all systems, regardless of where they are in the world. An administrator can quickly identify top risks, as in Figure 11-11 showing the top vulnerable software found on all corporate-monitored assets. In this example, the top risk is Adobe Flash Player. Again, this is useful data for a delivery report providing recommendations to reduce risk.

Figure 11-11 Top Vulnerable Software
A similar search can be done for top vulnerable applications. Figure 11-12 shows a pie-chart version of this data.
If Cisco AMP for Endpoint sees a file as malicious, it removes that file, as shown in Figure 11-13. AMP also can provide detailed reports explaining why something was considered malicious. This information can be extremely detailed using the built-in Cisco Threat Grid reporting system. These details are extremely useful when you’re creating digital forensics reports as well as validating whether other versions of the threat still exist within the customer’s environment. Many incident response service teams leverage Cisco AMP to map out the files on the network and quickly zero in on malicious software that is typically extremely difficult to detect with other tools.

Figure 11-13 File Removed by Cisco AMP
Cisco Threat Grid also has a standalone offering that complements Cisco AMP. Because Threat Grid is available in different Cisco products and offers a lot of forensic value, we focus on that next.
Cisco Threat Grid
Cisco Threat Grid offers a combination of advanced sandboxing with threat intelligence to identify advanced malicious artifacts. This capability is critical for identifying files that are seen as suspicious even if they are not identified as a threat by other technologies. Artifacts can be identified by having Threat Grid automatically monitor files that cross a specific platform like Cisco Firepower as well as manually sending any questionable file to a Threat Grid solution to be evaluated. The key value is that you can learn why a file is considered malicious and provide a thorough test of a potentially malicious artifact using this technology. This test is extremely important for any legal or forensic matter not only to identify all malicious elements but also to back up what you claim is a threat. Figure 11-14 showcases an example of a file flagged as malicious. This example includes different hash values of the threat to accurately locate it even if the attacker attempts to change the name of the file. This tool is also useful for threat feeds because other networks may experience this threat.

Figure 11-14 Malicious File Identified
The key data that many administrators want to know is why a file is considered malicious. Figure 11-15 provides a list of behavior-based indicators that explain why a file is a threat. This example shows various ransomware behavior triggers such as TOR communication and data deletion. These details are great for a forensics report post-incident response.
Other helpful details provided in a Threat Grid report include registry activity, process details, and TCP/IP data and DNS details. Figure 11-16 shows examples of this type of data.

Figure 11-16 Examples of Data in Threat Grid Reports
Cisco AMP can also provide videos showing the malicious file running in a Threat Grid sandbox environment. This demonstrates why the file was flagged using a view of what the file would look like if it infected the targeted endpoint. Figure 11-17 shows a video showcasing a malicious file encrypting the host and presenting a ransomware warning. This is a great way to capture people’s attention regardless of their technical knowledge.

Figure 11-17 Cisco Threat Grid Video of Malicious File
Evaluation can be automated or manual using features such as the Glovebox that let administrators execute and interact with the file in question in a controlled environment during the evaluation process. Using these features helps administrators understand the true nature of a file faster and helps them more accurately respond to potential threats. From a forensics viewpoint, being able to respond to threats is critical because most investigations require the details around any identified malicious artifacts. To summarize the forensics value, Cisco Threat Grid dramatically simplifies the process of evaluating potential malicious artifacts and likely provides more accurate details than what could be determined using manual efforts. This includes identifying various characteristics of the malware, such as which URLs it attempts to access, how it changes files during operation (known as polymorphism), and what exploits it uses to spread to other systems. This information is all automatically recorded as the malicious file runs in a contained environment. It is likely investigators would not see all these details because they do not see the malicious file execute from start to finish in a real environment. Typically, investigators react to the results of a compromise and therefore see only part of the malicious file’s characteristics.
One final value of Cisco Threat Grid is the sheer number of threat samples seen by the Cisco Talos research team. No other vendor sees the same level of threats, so it is likely that anything found within your environment likely has been seen somewhere else, speeding up detection through threat intelligence.
Cisco Threat Grid is part of many Cisco security offerings, such as Cisco AMP, Next Generation IPS, and email, but also can be a dedicated appliance or cloud offering. The Threat Grid on-premise appliance options are 5004 and 5504 appliances, which provide local malware analysis and sandboxing. This option is popular for those with requirements to keep all files local. The cloud Threat Grid option comes as a subscription giving access to APIs and additional threat intelligence feeds beyond what is standard with the Threat Grid capabilities included with other Cisco security technologies. The following Cisco technologies leverage Threat Grid at the time of this writing:
![]() Cisco Advanced Malware Protection AMP for Networks
Cisco Advanced Malware Protection AMP for Networks
![]() Cisco Advanced Malware Protection for Endpoints
Cisco Advanced Malware Protection for Endpoints
![]() Cisco Advanced Malware Protection Private Cloud
Cisco Advanced Malware Protection Private Cloud
![]() NGFW and ASA with Firepower Services
NGFW and ASA with Firepower Services
![]() Cisco Intrusion Prevention System (NGIPS)
Cisco Intrusion Prevention System (NGIPS)
![]() Cisco Web (WSA) and Email (ESA) Security Solutions
Cisco Web (WSA) and Email (ESA) Security Solutions
![]() Cisco Meraki MX
Cisco Meraki MX
![]() Cisco Umbrella
Cisco Umbrella
Many non-Cisco vendors leverage Threat Grid in various fashions. Learn more at www.cisco.com/c/en/us/products/security/threat-grid/integrations.html.
Cisco Web Security Appliance
We covered the difference between web proxies and application layer firewalls in Chapter 8, “Network Forensics.” Cisco Firepower is an application layer firewall, and Cisco Web Security Appliance (WSA) is a proxy. This means WSA focuses only on Internet-based traffic. The strengths of this approach are based on performance, deployment strategies that can leverage redirection through Web Cache Communications Protocol (WCCP), caching of website data, and some other features that are not available in many application firewall solutions such as data loss prevention (DLP).
Cisco WSA offers similar Before security features to Cisco Firepower by leveraging reputation and content-filtering capabilities. To be clear on the difference between these two features, content means material that your organization wants to control but doesn’t necessarily have to do with security risk. For example, playboy.com is probably safe for your computer to access but not an appropriate use of time for most users during work hours. Security filtering based on reputation and other big data trends targets threats. For example, most companies permit banking websites, but administrators want to prevent a fake bank that pushes malware to systems that connect to it.
Cisco WSA takes a slightly different approach for the During and After defenses. The During detection is not an intrusion detection or prevention system like what is offered in Cisco Firepower. Instead, WSA offers license options for antivirus and malware scanners from Sophos, Webroot, McAfee, and Cisco. The After features not only include Cisco Advanced Malware Protection (AMP), but also can leverage a cloud-based breach detection feature known as Cisco Cognitive Threat Analytics (CTA). CTA came to Cisco through acquisition and dramatically improves incident response to breaches. We look more at CTA in the next section.
The forensics value of Cisco WSA is similar to Cisco Firepower in that you can understand how users interact with the Internet. The challenges with results are, unlike with an application layer firewall, a proxy can view only the traffic that crosses the platform, so internal lateral traffic is not seen. Application layer firewalls can create internal network objects and be aware of different network segments. Cisco Firepower tries to identify internal devices using discovery protocols, so you specify what is considered inside and outside the network as well as what IP ranges should be part of which network segment. Cisco WSA does not do this; it has limited internal visibility. This design does not take away the value of its internal visibility, however, because many internal systems need to access the Internet. For example, the claim from CTA is that 90 percent of internal threats phone out, which means they will eventually cross the path of a proxy if one is in place. Let’s look at how this type of technology works to help assist tools like Cisco WSA with detecting internal threats.
Cisco CTA
Cisco Cognitive Threat Analytics (CTA) analyzes anomalous web traffic with the goal of flagging malicious sources. Unlike edge defense technologies such as content filters and Cisco Umbrella, Cisco CTA looks for insider threats such as rootkits, botnets, and malvertising other pieces of malware. Even though many of these threats are based on being inside the network, the majority of them use the web for command-and-control communication. Cisco CTA can pick up on this behavior as well as other threats such as preventing data exfiltration, which is typically the result of a threat successfully breaching a network.
To be clear on the Cisco CTA solution, it is not a standalone product you buy. CTA is a feature that is enabled on web security proxies such as Cisco Web Security Appliance (WSA) or Blue Coat ProxySG. Traffic is analyzed to gather user and device behavior. Using machine learning and anomaly detection from a cloud-based software as a service (SaaS), CTA flags behavior that is suspicious and requires attention. Cisco CTA can also be used by other solutions leveraging the Structured Threat Information eXpression (STIX) and Trusted Automated eXchange of Indicator Information (TAXII). Figure 11-18 presents the basic concept behind Cisco CTA.

Figure 11-18 Overview of Cisco Cognitive Threat Analytics
Meraki
One final Cisco security platform that covers the Before, During, and After approach to consider is the Meraki security product line. Meraki is different from other Cisco offerings because it is a hybrid cloud and physical offering. Meraki security appliances are managed from the cloud. The focus for Meraki is simplicity, which means making deployment, scalability, and management easy. An administrator can purchase hardware and have it completely configured prior to it showing up at a branch location. To complete the deployment, the local staff just needs to plug it in, and the Cisco Meraki solution downloads all its required configuration.
Meraki’s capabilities are similar to Firepower, but it has some limitations. The Before capabilities are similar at a high level; for example, you can control content and block malicious websites. Cisco Firepower is an enterprise application layer firewall, so it offers more granular controls for those features. Meraki’s IPS is a light version of what is offered in Cisco Firepower, so you can’t tune or select specific signatures to enable or disable. You can only select a general security setting and hope the right signatures are enabled. Cisco Meraki offers AMP for the After phase, but as with Cisco WSA, it detects only what crosses the Cisco Meraki appliance. Figure 11-19 show the configuration screen for enabling Cisco AMP with Meraki as well as the limited IPS security settings available.

Figure 11-19 Cisco Cognitive Threat Analytics in Action
Note One common question is when to select Meraki, WSA, or Firepower because all three seem to offer similar features from a high level. There is no absolute answer, but the general recommendation is to select Firepower when security is the top desire. If simplicity and scalability, such as deploying security across hundreds of locations, are the goals, Meraki is probably the best fit. If user performance with the Internet is critical, a proxy is likely the best, hence Cisco WSA.
To summarize Meraki’s forensic value, an administrator can export details to back up any findings. This information can be useful for any legal cases involving web usage. The data is stored in a secured cloud, but some legal teams may question the chain of custody because this is a hybrid deployment. Our thoughts for proving that proper chain of custody was enforced are to treat the evidence as if it’s your private cloud and secure what you download. Cisco has many documents backing up the quality of security of its cloud infrastructure, so most courts should trust evidence found within a cloud-managed solution like Cisco Meraki. Figure 11-20 shows a Cisco Meraki summary report screen.

Figure 11-20 Cisco Meraki Summary Report Screen
All these Cisco technologies target web usage, but what about security email? Could these solutions provide enterprise-level security against sophisticated email attacks? The answer is no. Yes, solutions like WSA, Firepower, and Meraki can block malicious web sources and block attacks, but email attacks can be very specific to that method of communication, requiring dedicated technology. So let’s take a closer look at Cisco’s enterprise email security offering.
Email Security Appliance
Email traffic and attacks can be a lot different from network-based attacks. For example, spam is an email problem in that it’s about receiving content that is probably fine but undesired. Also, the format of email messages can be modified to bypass detection tools. An example is putting white spaces that users wouldn’t notice but would make the email seem different to generic spam detection tools. Packets can be seen differently, such as the use of Base64 for content transfer encoding. For these and many other reasons, it makes sense to have a dedicated email security solution designed to defend against email-based threats.
Cisco Email Security Appliance (ESA) can be a physical, virtual, or cloud option for securing email. Just as with web security solutions, there are the BDA security features. Before features include reputation and Big Data type security as well as content controls, so this means filtering out things like foul language found within emails. During features are similar to Cisco WSA in that they are based on enabling antivirus and antispam capabilities from Sophos, McAfee, and Cisco. For the After phase, once again the Cisco AMP option is available, as well as other security features like data loss prevention. Figure 11-21 shows the Security Services tab option, giving a view of some of the security features that can be enabled within Cisco ESA.

Figure 11-21 Cisco ESA Security Services Tab
The forensics value of Cisco ESA is knowing all the details associated with email entering and leaving the organization. Any legal matters involving people sending out confidential information, statements that were made, and many other situations could be proved via email. For most legal matters, email is treated as a record of statement, which means whatever is said in an email could end up in court and used as evidence. When doing this within Cisco ESA, you need to first identify the email(s) of interest by searching using many filter options such as user, destination, and source. Cisco ESA offers various options to accomplish this. You can export emails or reports of email behavior, which include details needed for legal matters, such as time of day and parties involved.
One final security concept for email is how many attacks are delivered via the web but use email as a method to get users to access their website. For example, it is common for a phishing attack email to pretend to be something like a postal service and say “click here” to get some data. The goal is to have users click the link, which takes them to a malicious landing page that delivers web-based exploitation. The email is essentially safe because it is only text. Cisco ESA can work with web security solutions and evaluate links included in emails before they permit users who receive the email to click them. This is best practice because attackers hit you both through email and web sources.
Cisco Identity Services Engine
If we look back at the BDA concept, it is critical for any mature security operation center staff to know who and what is on their network. By doing this, you prevent attacks before they can occur and limit the spread of threats by breaching the perimeter. You can control access by using manual efforts such as port security or simply walking around looking for or scanning for devices. However, these approaches are difficult to maintain and not absolute in coverage. A better approach—one that is not only industry best practice but also required by many compliancy standards for security—is to use automated access control. Typically, this type of control is achieved using 802.1x, but some solutions leverage other protocols such as SNMP. Cisco ISE follows industry best practices using 802.1x, which can enforce access control using VLANs, ACLs, dynamic ACLs, or TrustSec policies; in other words, devices are provisioned with specific network access based on the policies created within Cisco ISE. The goal of a Cisco ISE solution is to know who and what are accessing the network and provisioning the right access even if they are connecting using the LAN, VPN, or wireless resources. Figure 11-22 summarizes this concept.

Figure 11-22 Cisco ISE High-level Overview
Key features of Cisco ISE include profiling and posture. Profiling is the ability to identify devices based on how they use the network. Cisco ISE uses various probes that include SNMP, DHCP, DHCPSPAN, HTTP, RADIUS, and DNS to accurately identify a device. The concept is based on profile buckets, which means a device at first will fall in the unknown bucket. When the link-up trap information is seen, Cisco ISE can typically determine the basic device type using MAC details. For example, an Apple device is identified, but this limited layer 2 data is likely not enough to determine what type of Apple device is being seen. As more data is collected using different probes, such as DHCP and DNS, Cisco ISE can continue to learn and associate specific characteristics about the device to move it to a more detailed classification bucket. For example, the Apple device example could move to an iPhone or iPad after the DHCP and DNS level information is seen. Figure 11-23 shows the main policy buckets available in Cisco ISE.

Figure 11-23 Cisco ISE Profiles
Posture is the ability to ensure devices meet specific criteria before being permitted access to specified ISE policies. For example, an administrator could require that anybody granted Employee access must have the latest Windows or Apple updates as well as a specific vendor antivirus installed and up-to-date. Posture can also be used to validate that certain settings or certificates exist to match a device to something customized, such as a corporate-issued asset. This is a much more accurate and secure method to validate an asset versus the traditional approach of checking against a MAC address because it can be easily spoofed.
The forensics value of a Cisco ISE solution is the ability to gather exactly who and what accessed a specific part of the network as well as potentially know what was installed at the time of access. This information can be exported to another source or as a report for legal purposes. Timing and integration are critical for these reports, so the Cisco ISE system should be synchronized properly with an approved centralized time server, and the account storage system such as Active Directory should be verified as being secured to ensure that the Cisco ISE system is working with valid data. In regard to posture, it is important to note that Cisco ISE can be configured to periodically revalidate an endpoint against a policy, but once the system is granted access to part of a network, Cisco ISE doesn’t continually monitor that asset’s posture state. For example, a policy could check to see if an asset has antivirus installed, but when the user is approved access, she could turn off antivirus. Ideally, Cisco ISE would periodically check that asset’s policy state and reenable antivirus, but this is an unknown because Cisco ISE targets access control versus monitoring internal user and device actions.
Speaking of the concept of internal monitoring and digital forensics, one extremely important concept is, in general, all access control technology focusing on what comes onto the network. Vendors can include some capabilities that monitor what takes place on the network, such as continuously profiling devices, but that is typically not the focus of NAC technology. This is where integration with other technologies is critical because a lot of value can be leveraged with an access control technology. It is also important to understand this because this gap in time would mean anything that occurs after a system accesses a network would not be useful for legal matters. That’s okay because it isn’t a focus of NAC technology.
A lot of value can be achieved by integrating an access control technology like Cisco ISE with other solutions. Here are some popular examples:
![]() Access control knows who and what connects to the network, which can be called “context,” meaning details on devices on the network. This information can be exported to other security solutions, so any IP address that is seen can be renamed to a more detailed context provided by the NAC technology. For example, a SIEM may see an IP address and have it renamed to user jmuniz’s iPad.
Access control knows who and what connects to the network, which can be called “context,” meaning details on devices on the network. This information can be exported to other security solutions, so any IP address that is seen can be renamed to a more detailed context provided by the NAC technology. For example, a SIEM may see an IP address and have it renamed to user jmuniz’s iPad.
![]() Access control can change the connection state of a device. This can range from limiting access with changes in VLAN, ACL, or other enforcement methods as well as completely removing the device from the network. Essentially, a NAC technology can be a bouncer. Other technologies could use this NAC bouncer when they believe a device is a high risk to the network. For example, a SIEM may get an alert that jmuniz’s iPad contains malicious software and automatically signal the NAC technology to remove the iPad from the network. This capability can be critical for situations when a network is vulnerable to a threat spreading or when administrators are unable to quickly react to a threat. Think about a situation in which ransomware has infected an endpoint and is seeking to move laterally and infect the rest of the network. What if this happened at 3 a.m.? Who would be around to see and react to it?
Access control can change the connection state of a device. This can range from limiting access with changes in VLAN, ACL, or other enforcement methods as well as completely removing the device from the network. Essentially, a NAC technology can be a bouncer. Other technologies could use this NAC bouncer when they believe a device is a high risk to the network. For example, a SIEM may get an alert that jmuniz’s iPad contains malicious software and automatically signal the NAC technology to remove the iPad from the network. This capability can be critical for situations when a network is vulnerable to a threat spreading or when administrators are unable to quickly react to a threat. Think about a situation in which ransomware has infected an endpoint and is seeking to move laterally and infect the rest of the network. What if this happened at 3 a.m.? Who would be around to see and react to it?
![]() NAC technology can be used to enforce compliance for devices and network standards. I have deployed NAC technology that is customized to mirror requirements for corporate-issued assets to help automate provisioning policy. For example, I worked with a hospital that had an orchestration system that automated the provisioning of doctors’ and nurses’ handheld devices. When a new device was provided to an employee, that employee was instructed to connect the device to the corporate network and let the NAC technology push down required software and settings; this process is known as device onboarding. This policy was part of a customized integration with the NAC and orchestration software.
NAC technology can be used to enforce compliance for devices and network standards. I have deployed NAC technology that is customized to mirror requirements for corporate-issued assets to help automate provisioning policy. For example, I worked with a hospital that had an orchestration system that automated the provisioning of doctors’ and nurses’ handheld devices. When a new device was provided to an employee, that employee was instructed to connect the device to the corporate network and let the NAC technology push down required software and settings; this process is known as device onboarding. This policy was part of a customized integration with the NAC and orchestration software.
Many other valuable integrations are potentially available depending on the vendor of the access control technology and skills of the team deploying and managing the technology. The preceding examples are the most common ones I have seen and found officially supported by vendors such as Cisco. For example, the sharing of context and auto removal of devices is supported with Cisco ISE 2.1 with many other vendors, ranging from SIEMs like Splunk to vulnerability scanners like Tenable and Rapid 7. Our recommendation is to stick with integrations that are officially supported by the vendor and tread lightly with autoremediation because not tuning these settings could remove devices that are critical to the business. For example, a business using access control technology could get a false positive alert by another security technology against a critical asset and direct the NAC technology to remove that technology from the network, causing an undesired interruption of service. I recommend starting with noninterruptive integrations such as sharing of context to prove a successful integration before considering autoremediation features.
Next, we look at Cisco’s premier network monitoring security technology, which also leverages the existing infrastructure—Stealthwatch. To be clear, Cisco ISE uses 802.1x, while Stealthwatch uses NetFlow. Both 802.1x and NetFlow are available in most modern network equipment, turning the network into a detection and enforcement point. I call this pre- and post-access control, whereas Cisco coins this “Network as a sensor, Network as an enforcer.”
Cisco Stealthwatch
Stealthwatch came from the Cisco acquisition of Lancope. This technology is built on NetFlow, which records network traffic. Many devices support NetFlow, which was covered in Chapter 8, “Network Forensics.” Stealthwatch supports all forms of NetFlow and sFlow with the goal of turning the entire network into a giant detection grid. This includes physical, virtual, and cloud technology. Physical devices include routers, switches, wireless access points, and firewalls. For virtual devices, it is common to deploy Cisco Stealthwatch within a virtual network to monitor east-west lateral traffic, which is typically not accessible by security solutions that sit on the edge of the data center. Cloud environments can even be monitored using an agent that translates traffic within the cloud into NetFlow that is sent back to the Cisco Stealthwatch solution. When NetFlow isn’t available, a Stealthwatch Sensor can convert raw data into NetFlow and add additional value such as application layer data. Figure 11-24 shows a breakdown of the Stealthwatch solution offering.

Figure 11-24 Cisco Stealthwatch Offering
![]() Stealthwatch Management Center (SMC): SMC provides administration of the solution, which means that system administrators log in to the SMC to configure, monitor, and report on the network.
Stealthwatch Management Center (SMC): SMC provides administration of the solution, which means that system administrators log in to the SMC to configure, monitor, and report on the network.
![]() Stealthwatch Collector: The Stealthwatch Collector is the place where flow is sent to be processed by the Stealthwatch solution. Network devices such as routers, switches, and wireless access points are configured to send NetFlow at the IP address of the collector unless another tool is used to copy the flow data for centralizing purposes, such as the Stealthwatch UDP Director.
Stealthwatch Collector: The Stealthwatch Collector is the place where flow is sent to be processed by the Stealthwatch solution. Network devices such as routers, switches, and wireless access points are configured to send NetFlow at the IP address of the collector unless another tool is used to copy the flow data for centralizing purposes, such as the Stealthwatch UDP Director.
![]() Stealthwatch Sensor: Many devices support some form of NetFlow, but for situations when NetFlow isn’t available, a Stealthwatch Sensor can be used to convert raw network traffic into flow. The Stealthwatch Sensor also offers additional value, such as adding application layer details to the records because native NetFlow doesn’t contain this level of detail. This is accomplished using deep packet inspection (DPI) and behavior analysis to identify applications and protocols in use across the network no matter whether they are in plain text or use advanced encryption and obfuscation techniques. Stealthwatch sensors are extremely useful in virtual environments when NetFlow is not supported, providing valuable east-west visibility, which is typically a blind spot for data center administrators.
Stealthwatch Sensor: Many devices support some form of NetFlow, but for situations when NetFlow isn’t available, a Stealthwatch Sensor can be used to convert raw network traffic into flow. The Stealthwatch Sensor also offers additional value, such as adding application layer details to the records because native NetFlow doesn’t contain this level of detail. This is accomplished using deep packet inspection (DPI) and behavior analysis to identify applications and protocols in use across the network no matter whether they are in plain text or use advanced encryption and obfuscation techniques. Stealthwatch sensors are extremely useful in virtual environments when NetFlow is not supported, providing valuable east-west visibility, which is typically a blind spot for data center administrators.
![]() Stealthwatch UDP Director: NetFlow must be enabled on devices, which includes configuring where the NetFlow should be sent. This potentially cumbersome process must be repeated any time a new device needs to receive NetFlow. The Cisco Stealthwatch UDP Director can be a centralized repository of NetFlow, so all devices need to be enabled one time and pointed at the UDP Director. The UDP Director can be configured to forward all NetFlow to any device, providing the ability to increase the number of devices that can receive NetFlow as well as quickly adapt to changes in where NetFlow needs to be sent. For large networkers, this is a critical tool to remain productive.
Stealthwatch UDP Director: NetFlow must be enabled on devices, which includes configuring where the NetFlow should be sent. This potentially cumbersome process must be repeated any time a new device needs to receive NetFlow. The Cisco Stealthwatch UDP Director can be a centralized repository of NetFlow, so all devices need to be enabled one time and pointed at the UDP Director. The UDP Director can be configured to forward all NetFlow to any device, providing the ability to increase the number of devices that can receive NetFlow as well as quickly adapt to changes in where NetFlow needs to be sent. For large networkers, this is a critical tool to remain productive.
![]() Stealthwatch Cloud: Another popular feature can be enabled—that is, adding a cloud license to gain visibility into public and private cloud environments. Think of this as a tap into the cloud via a software agent that can send NetFlow back to the Cisco Stealthwatch Collector.
Stealthwatch Cloud: Another popular feature can be enabled—that is, adding a cloud license to gain visibility into public and private cloud environments. Think of this as a tap into the cloud via a software agent that can send NetFlow back to the Cisco Stealthwatch Collector.
There is a lot of forensic value from the Stealthwatch offering. An administrator can identify unusual behavior and quickly prioritize where to start investigating for potential compromises. This is different from how many network-focused NetFlow tools function. Common NetFlow solutions look only at network trends and can effectively identify spikes and valleys, or situations involving systems being overutilized, network congestion, and so on. NetFlow technologies that include security capabilities can combine behavior algorithms with network trends to pinpoint malicious activity. For example, systems doing port scans give off a behavior signature that can be identified and labeled as unauthorized scanning, which typically represents malware or insiders looking for systems to attack. If a system is infected, that lateral movement between systems can be identified as a potential worm. It is common for infected systems to beacon out of the network, and that traffic tends to look different from a user accessing Internet resources. Those behaviors alone should represent a threat, but Cisco Stealthwatch considers each device based on a baseline of what is considered usual behavior. If a device has never scanned the network before or performed lateral movement, it is quickly escalated as being a high priority threat. This anomaly detection is key for identifying stealthy threats. Figure 11-25 shows the Cisco Stealthwatch Cybersecurity Dashboard that monitors for common malicious behavior. This tool can not only be useful for targeting where to spend time during a forensics investigation but also for helping to speed up the incident response process.

Figure 11-25 The Cisco Stealthwatch Security Dashboard
One interesting concept is how a NetFlow-based technology can address data loss. Traditionally, data loss is enforced by either detecting data in motion using specific triggers such as a Social Security number, or through labeling and encrypting data known as data at rest. This approach can be effective but extremely time consuming and costly to implement and enforce. Baselining data trends can be an interesting way to monitor data movement; this process involves identifying usual amounts and transfer methods of data as well as other aspects such as frequency and time. For example, Cisco Stealthwatch could set off an alarm when somebody in the sales department sends data that is larger than normal, at an unusual time of day, or in an unusual manner. This tactic isn’t 100 percent accurate, but it helps identify things that should be investigated because this type of behavior could indicate a breach. Combine this with triggered packet capturing, and you have a very effective solution for recording unusual data loss. This could be helpful to answer the question, “What was stolen from our network?”
There are some challenges in using NetFlow for forensics. First, NetFlow is just network records, so the actual associated packets are not included. Also, using NetFlow requires time to truly understand and baseline a network. This means a solution would have to already exist to leverage baseline data, but Cisco Stealthwatch can still effectively identify all devices on the network and identify threats using other measurements and triggers. Lastly, many NetFlow solutions include modification of data such as deduplication and record consolidation (sometimes called stitching) to help with performance and to simplify results. This modification arguably could contaminate evidence if findings were to be used in a court of law. Cisco Stealthwatch has options to work around these challenges by offering a packet capture solution that can be triggered upon alerts of interest or run on parts of the network with sensitive data monitoring needs. Having the packet capture details back up NetFlow logs should hold up as legitimate evidence for any legal matter even though NetFlow could be used alone for many use cases.
One final NetFlow concept is how NetFlow is natively unaware of application data. Cisco Stealthwatch offers the NetFlow sensor, which can not only convert raw traffic to NetFlow but also tag on application layer data. This capability provides a richer view of context associated with data, such as what websites are being accessed by the IP address. Figure 11-26 shows a high-level graph of application data identified by the Cisco Stealthwatch sensor.
Cisco Tetration
NetFlow can be really helpful on networks and in the data center. Cisco’s Tetration Analytics platform is designed to provide visibility into everything running within a data center in a real-time manner that is deeper than other tools, including Cisco Stealthwatch. Stealthwatch is based on NetFlow, whereas Tetration sees every packet and every flow at the line rate (about 1.5 terabytes per second). Tetration processes this data using machine learning and intelligent algorithms to enforce policy and deliver visible insight to the data center within minutes. We are talking about a ton of data and details, so you can map all applications and their dependencies. Details include what’s talking, its service name, what time it was kicked off, and so on. In Figure 11-27, Cisco Tetration maps an application’s dependencies.

Figure 11-27 Cisco Tetration Application Dependencies
The solution is made up of servers and software sensors, so it is a major commitment in price and infrastructure but is based on automatically learning the environment, thus making deployment easy. Other tools like Cisco Nexus 9000 switches can also provide Tetration visibility into the environment. The focus of this solution is for those looking for deep data center visibility to solve challenges such as learning the impact of migrating application, disaster recovery planning, application optimization, unusual application usage, and so on. One major security value is for those looking to enforce zero trust white list policies, which are extremely hard to enforce without this level of automated learning and enforcement. For example, enforcing very strict security policies has a high risk of breaking things. This chance of causing complications tends to slow down or even prohibit enforcing security due to the risk of impacting business operations. Cisco Tetration can do a logical test of what a security implantation change would do and its effectiveness on your current environment. It does this using historical data to accurately provide an understanding of all associated risk without touching a live system.
The forensics value of this type of solution should be pretty obvious. This level of detail could prove any case involving how people or systems interact with the data center being monitored. You could easily zero in on data of interest and provide the court very granular details to prove your point. Cisco Tetration stores all the flows or network activity since the deployment of Cisco Tetration. This capability lets you go back to the time of an incident and replay the entire event to learn how the threat executed as well as how the team and system reacted to the threat. You can show with specific details what was touched, who accessed the system during the incident response, and even older related information such as who potentially made a configuration mistake prior to the event that led to the identified breach. Future threats can be seen, including unknown threats and anomalies, because the entire data center is continuously monitored down to the process level.
Cisco Umbrella
The first thing that happens when a system attempts to access a website is that it looks up the site using a Domain Name Server (DNS). DNS is like a phone book for the Internet, translating domain names into their actual location (IP address). Because this lookup happens first, it would be ideal to prevent threats at this point since it limits system exposure to attacks before they can occur. So essentially, DNS-based security is like a first line of defense against remote threats. To be clear, this does not refer to protecting the authenticity of DNS records, which is important for security to avoid DNS-based attacks. DNS as a first line of defense means using various forms of threat intelligence to determine if a website being requested is potentially malicious.
Cisco Umbrella, at its core, is a secure Internet gateway in the cloud. It works as your DNS service provider so it can filter what is and is not permitted, essentially working like a traditional security content filter does. You can create content policies, which are things you want to filter but are not necessarily a security risk. An example is adult material or gambling websites, which are common to deny to employees on a corporate-sponsored network. Playboy.com is probably safe for your computer to access but is not an appropriate use of time for most organizations, as explained earlier in “Cisco Web Security Appliance (WSA).” Figure 11-28 shows an example of some content options.

Figure 11-28 Some Cisco Umbrella Content Options
The other type of filtering is security related, which means threats. Unlike the pure reputation concept covered during the WSA overview, Cisco Umbrella looks at various Domain Name Servers and associations. This means Umbrella considers things like all websites registered by the party responsible for a website, the common websites that send traffic to a website, and where people go from a website. This information is critical for catching large-scale attacks, such as websites used as landing or redirection pages for other malicious websites. Figure 11-29 shows some of the security categories you can enable for blocking.

Figure 11-29 Some Cisco Umbrella Security Options
What does it mean to be malicious from a DNS viewpoint? If the website is flagged for malicious behavior, its trust level is reduced until it breaks a threshold that moves it to a blacklist, just like other content security-related tools. Cisco Umbrella sees more than just specific website data. First, Cisco sees over 80 billion DNS requests a day, giving it a nice size sample pool of data. Umbrella therefore can compare requests it sees from a website to what the rest of the world sees. For example, if your website makes up the majority of traffic to or from a website, it is likely your site is being targeted or being used to attack another website. Imagine if a so-called bank has 95 percent of its traffic hitting your organization. That site, then, is likely not a bank because it should have users from all over the place, unless it’s your organization’s private bank.
Domains may also be linked to malicious sites providing details that could reveal a potential threat before it has a chance to launch an attack. Cisco Umbrella considers website associations; in other words, if a website is malicious and always comes from another website, all websites associated with the threat actor are viewed as a potential threat. You can see many of these deeper DNS details by using the Cisco Investigate features within Umbrella. Investigate is essentially a DNS forensics tool. Figure 11-30 shows some basic details pulled up on www.thesecurityblogger.com.
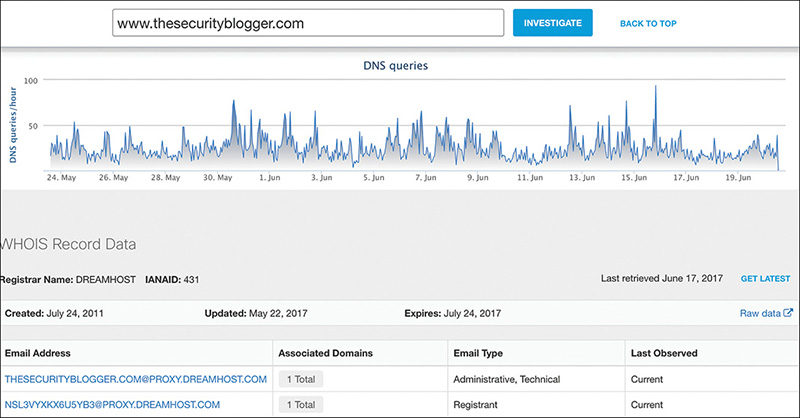
Figure 11-30 Cisco Investigate Looking at www.thesecurityblogger
Details that you can pull up include WHOIS records, timing, security scores, global geography access distribution, all associated IP addresses, name servers, co-occurrences on other websites, and related domains. Figure 11-31 shows the many co-occurrences and related websites for www.cisco.com.

Figure 11-31 Cisco Investigate Looking at www.cisco.com
Note Forensic value can be a big deal in cases that deal with understanding website activity and associations. I was involved in a case that questioned whether a blog post was costing a company millions of dollars in brand damage. Using DNS records, I was able to show the actual potential human activity versus botnet and other nonrelated activity, dramatically reducing the real-world value of the damage that could be claimed. Potential damage went from millions to under a thousand dollars!
Let’s say you search a website like www.movies123.com because you heard that it advertises free movie streaming. The first thing you see, as shown in Figure 11-32, is that Cisco Umbrella blocked some of its associated IP addresses for malicious activity.

Figure 11-32 Cisco Investigate Looking at www.movies123.com
If you click that IP address to see the details on the website, Cisco Umbrella shows this malicious website is associated with various Trojans. Cisco AMP Threat Grid tested these Trojans by using tactics discussed earlier in this chapter to validate whether they are true threats, as shown in Figure 11-33.

Figure 11-33 Threats Associated with 208.73.210.200
When I scrolled down to see the known domains using this IP address, I found that hundreds of websites are associated with this malware. Figure 11-34 shows a portion of these websites. Hundreds are identified, which shows how DNS can link together malicious websites to other domains, providing a more granular first line of security defense.

Figure 11-34 Websites Associated with 208.73.210.200
One cool Cisco Umbrella API integration is the ability to send malicious website data to Cisco Umbrella and have that website blocked globally at the gateway. For example, if a SIEM flags attacks coming from different security products, it would be great to ensure that those sources are blacklisted. Rather than blacklisting only at the network edge, Cisco Umbrella can block this website for any user protected by DNS security, including mobile phones, laptops, and all branches along with the edge. This capability dramatically simplifies and speeds up enforcement.
To summarize Cisco Umbrella’s forensics value, you can quickly identify all websites accessed by anybody protected by the solution and pull up details on the DNS records and associated web sources. These capabilities can simplify website reconnaissance, developing a case that includes web use behavior and helping justify actions taken by a web resource.
Using DNS for a first line of defense is great, but the cloud can also be a place where visibility and policy enforcement are lost. More and more companies are moving to cloud services, which is why Cisco recently acquired Cloudlock. Next, we check out what Cloudlock has to offer.
Cisco Cloudlock
One trend that is taking place is how companies are migrating services to the cloud. Services include file sharing like Dropbox and Box, monitoring services such as Salesforce, and email such as Gmail. As data leaves the network, in many cases, visibility and controls leave as well. Cisco Cloudlock acts as a cloud access security broker (CASB), protecting cloud users, data, and applications. For example, what happens if an access account is compromised by a malicious party? Cisco Cloudlock can identify that my account has logged in to the cloud from two different locations across the globe, representing a potential data breach. The same goes for users sharing data; a major fear would be an internal user posting a sensitive document in a cloud service that isn’t monitored or a person leaving the company but before doing so downloading sensitive data such as sales contacts. Mobile device permissions can also be a challenge. What happens when an application requests access to the entire mobile device, including applications containing sensitive data such as your email? Cloudlock can handle these and other cloud security use cases.
The forensics value from Cisco Cloudlock is being able to view details on how monitored cloud services are being leveraged. This includes who accesses what with granular details that are perfect for any legal matters requiring such data. For example, if a case involves lost credit card numbers, Cloudlock DLP (Data Loss Prevention) can provide those details, as shown in Figure 11-35. The idea is that a user shares a document containing credit card records using something like Dropbox. Cloudlock can prevent this sharing and flag when sensitive data such as credit card data is present where it shouldn’t be.

Figure 11-35 Cisco Cloudlock Data Loss Prevention
Cisco Network Technology
The final technology to consider is the general network equipment from Cisco. Hundreds of commands are available within Cisco networking equipment, such as routers and switches. We covered a lot of these commands in Chapter 8 on network forensics. Commands include showing running configurations, details about systems on the network, types of data being sent, and so on. From a digital forensics viewpoint, the key is to be able to gather details that you can use to identify content around the event you are trying to prove. This includes proving that the data is not contaminated by following the procedures covered in this book as well as ensuring that the hardware or timing server the hardware relates to is secure. See Chapter 8 to learn more about the value from networking technology. Most examples cover the general concepts seen within Cisco network-based technology.
Summary
In this chapter, we touched on many of the security solutions and capabilities available from Cisco. Each product could be described in its own book, and many are; they’re available on the Cisco Press website. Because this is a Cisco Press book, this chapter answers questions around what Cisco offers in the realm of security from a very high level. We also included nuggets on how these technologies could be used for digital forensics, but due to the massive catalog, we could provide only limited details. We highly suggest that you check out www.cisco.com/go/security to learn more about these and other security solutions offered by Cisco.
In the next chapter, we challenge you with a handful of investigation scenarios. The goal is to test your knowledge of the topics covered in this book through these challenges.





