While crafting the namespace structure is critical to the directory administrator, the LDAP operations are at the heart of the client-to-server interaction. The LDAP operations are therefore what the typical user of your directory needs to know about, although good client software abstracts even this interaction from view. Users probably need only the search operation, which happens to be the most detailed operation. There are ten primary operations defined by the LDAP standard. Administrators and programmers use this full set as they manage directory information and create special business processes that interact with the directory information. This chapter describes the purpose of each of the ten operations, and along the way I discuss issues that relate to the client-server interaction.
The LDAP client is what a user sees of a directory
One of the most obvious topics involved in the client-server interaction is the LDAP client itself. The client software is the key to people finding the LDAP directory useful and easy to use. If the client software requires people to understand this book, or even a fraction of this chapter, they won't use the directory. Therefore, well-designed applications that hide LDAP from users are important. Because the search operation is the most prominent operation, it is addressed early in the chapter. You can explore how to create complex searches, how to use comparison operators, and what client options affect the search operation. By understanding how the client should work and what the common client configuration options are, you can educate users even if the client software isn't friendly.
LDAP operations, extensions, client services, and APIs are examined
After addressing the topics of immediate concern to users, I turn next to other standard operations and technical topics connected with the LDAP operations. In addition, I examine some extended operations and controls that can make an LDAP directory more valuable. The chapter ends with a look at the details of using an LDAP API. An organization that is developing a directory-enabled application or service needs to look at these details. Directory users will employ LDAP client software that was written using these underlying APIs, but typical users won't need to know about the API. For example, a programmer might design a program that automatically fills out all the paper forms needed when a new employee joins the organization. The new executive at Mycompany that was introduced in Chapter 1 would have a less painful first day with such a program in place. These standard APIs are the primary reason why LDAP is such a popular choice, because they work regardless of the client's operating system, making a multiplatform implementation possible. Appendix A summarizes the standard C version of the API, as defined in RFC 1823. In addition, this chapter takes a brief look at some of the functions in the C version of the API.
Many applications benefit from being able to interact with the directory to find information. An application or service that is capable of being an LDAP client is called directory-enabled.
Applications that can interact with a directory are called directory-enabled
Many e-mail services are directory-enabled
Among the most common directory-enabled applications are e-mail services. When an e-mail server receives an e-mail, it can query the directory to find out whether the e-mail address recipient resides at the local site and what e-mail server that person's mailbox resides on. Centralizing this information in the directory simplifies the administration of the e-mail servers by eliminating the need for a synchronized copy of this information on each e-mail server. For example, sendmail is a common UNIX mail server that can be directory-enabled (for more details, see Appendix C). Microsoft recognized the importance of directory-enabling their mail server, Microsoft Exchange 2000, and has integrated it with Active Directory (see Chapter 7).
E-mail clients can also be directory-enabled
Similarly, e-mail clients can be directory-enabled, and they provide a valuable service by looking up a destination e-mail address given a person's name. Several e-mail clients allow the user to browse a directory via an interface within the e-mail application and pick out recipients for an e-mail.
The limits of directory-enabled services haven't been reached yet
Directory-enabled services have few boundaries. For example, you could use an LDAP directory
As a certificate authority store associated with public-private certificate technology. This also allows you to provide a service to verify the validity of those certificates.
To catalog the location of HTML and other types of electronic documents. You could then query and return a list of appropriate documents, just as a library catalog would do.
Microsoft's Active Directory LDAP implementation is a good example of how a variety of directory-enabled services can be integrated. Via Microsoft's Active Directory, software can be distributed to computers, user and computer configurations can be set, printers can be advertised to clients, and so on. Clearly, there are significant benefits to centralizing information in a directory, especially information that helps manage resources.
Mycompany simply needs creativity and integrated services that take advantage of the directory to realize this potential.
An LDAP operation consists of a client request, server work, and the results
All the LDAP operations consist of the client sending the operation request along with parameters to the server. The server then performs the operation and sends a result code back to the client. The result code indicates the success or failure of the operation. When the operation is a search operation, the server sends all the entries that match the search parameters prior to sending the result code. There is no read operation, so if a directory user wants to read a specific entry, she must perform a search operation specifying the entry.
Search parameters define what entries the server returns to the client and how it finds those entries
The search operation has many parameters that modify how the server performs the operation. There are mandatory parameters that are required or the search will fail, and there are optional parameters that have default values if not set otherwise. The search parameters affect only the single search operation for which they are set. Should you want to modify all LDAP operations for a session, you must use an LDAP option, if there is an appropriate one. LDAP options are discussed a little later in this chapter. Do not confuse LDAP options with optional search parameters or the attribute options introduced in Chapter 4.
Where does the server begin looking?
The mandatory search parameters are
A base DN to begin your search—. An idea of how the directory is structured is helpful here. In other words, if you want to look up person entries, are they all in a common container? The base DN is sometimes also called the baseObject. If I didn't know where to begin, I could start at the root of the directory. In Mycompany's directory, this would be
dc=mycompany,dc=com. So at a minimum, I must know the naming contexts of the directory.How far does the server look?
The scope of the search—. There are three options for the scope. A
basescope means to search only the single entry at the base DN. Aonescope means to search all entries at the same level in the hierarchy within the container of the base DN. Asubtreescope means to search the base DN and all entries beneath the base DN, regardless of their level in the hierarchy.What special characteristics do the entries have?
A search filter—. Search filters are composed of an attribute type, a comparison operator, and an attribute value. These three components are surrounded by parentheses and form a search filter item. The simple syntax of the search filter item is
"("attributetype operator attributevalue")"with no spaces between any of these mandatory elements. The quotation marks enclose text that is constant in the syntax. For example,(objectclass=person)would be a valid search filter item. One or more search filter items can be combined with filter operators to form the search filter, so the example is also a valid search filter. Filter operators are introduced shortly.
To illustrate the use of a search filter, if I wanted to find my entry as shown in Figure 3-1, I might use the following search parameters:
Base DN: |
|
Scope: |
|
Search Filter: |
|
You can use filter operators to combine filters
You can combine filter items within the search filter parameter by using filter operators. Filter operators can modify a filter item specified within the search filter parameter, and they can be used to combine multiple filters to designate intricate sets of entries.
The filter operators available are
& AND
| OR
! NOT
These operators should precede the filter they modify. This precession is very similar to how functions in the LISP language or operations in reverse polish calculators are represented. The following filters illustrate the use of the filter operators with the directory shown in Figure 3-2. All the examples provided assume a base DN at the root of the directory, along with a subtree scope.
The filter
(|(cn=Brian Arkills)(cn=Chewbacca))
returns the entries of Chewbacca and me.
The filter
(!(|(cn=Brian Arkills)(cn= Chewbacca)))
returns all entries in the entire directory except Chewbacca or my entry, so it would return the entries of cn=Princess Leia, cn=Han Solo, uid=barkills, upn=441276, upn=239316, as well as the ten ou entries pictured. Containers are still entries.
The filter
(&(!(|(cn=Brian Arkills)(cn=Chewbacca)))(objectclass=inetOrgPerson))
finds all the inetOrgPerson entries except Chewbacca's or my entry, so it would return the entries of Princess Leia and Han Solo.
Search filters are the most dynamic and interesting parameter in the LDAP search operation. For more details on search filters, see the following section, Search Filters.
Should the server return the entire entry or just some of the attributes?
The optional search parameters are
What attribute information to return—. If you don't specify what you want, all the attributes of the entries the server finds will be returned. You can list the attribute types you want in a list separated by commas. The operational attributes, which are the attributes that the directory uses for its own purposes, are never returned unless explicitly specified. You can also specify that no attributes should be returned by denoting the attribute 1.1. This designation holds significance as a special OID number that is not associated with any attribute type. See Chapter 4 for more information on both operational attributes and OID numbers.
How should the server treat alias entries?
derefAliases—. Denotes how to deal with alias entries. An alias entry is a dummy entry that references or points to another entry. Dereferencing an alias simply instructs the server to go to the object that the alias references, and for the purposes of the search, treat the referenced object as if it were the alias object. The following options are available (for more information on alias entries, see Chapter 5):neverDerefAliasesDon't look up any alias reference.derefInSearchingLook up all alias references except on the baseObject.derefFindingBaseObjLook up alias references only on the baseObject.derefAlwaysLook up all alias references.
How many entries should the server return?
sizeLimit—. Limits the number of entries to return on the search. The default value of 0 denotes no limit. If a search finds more entries than what is specified as the limit, only the first set number is returned. In this case, a result code ofLDAP_SIZELIMIT_EXCEEDEDis returned to indicate that more results were available.Settings in other places can modify the effects of this parameter
Many LDAP server implementations allow the directory administrator to set a mandatory upper
sizeLimitfor all client operations. In this case, the client can set a limit with a lower value, but limits greater than the server limit are disregarded. Some LDAP servers have a special user that can override the size limit. Another modifier called an LDAP control can be used to tell the server to send the results back to the client in pages. For example, the directory might have asizeLimitof 50, and a search that yields 100 entries normally only returns the first 50. But if I ask for a page size of 50, the server would send the first 50 entries to my client, then the second 50, and I'd see all the entries. LDAP controls are modifiers that apply to a single LDAP operation. LDAP controls, including this one, are discussed later in this chapter.How long should the server work on this request?
timeLimit—. Limits the time in seconds allowed to complete the search. The default value of 0 denotes no limit. If a search operation takes longer to complete than the specified limit, the operation will finish at the time limit. Only the entries found in this time period are returned. In this case, a result code ofLDAP_TIMELIMIT_EXCEEDEDis returned to indicate that more results were available. Some LDAP server implementations allow the directory administrator to set a mandatory uppertimeLimitfor all client operations. Some LDAP servers have a special user that can override the server time limit. The client can set a limit with a lower value, but limits greater than the server limit are disregarded.Does the client want the attribute pair or just the type?
typesOnly—. If set totrue, the results will list only the attribute types, not the values. The default value offalsedenotes that both the attribute types and values should be returned.
You use match operators to limit the attribute values specified in the search filter
In addition to the filter operators, other operators, called match operators or comparison operators, can modify the search filter. Most documentation on the subject confuses match operators with filter operators. But match operators do not operate on the entire filter expression, only on the attribute value. The match operators are usually common mathematical operators, such as equality or greater than or equal. You use match operators to help designate the entries that match the attribute value parameters desired. The operations used to match vary depending on the specific type of data stored in the attribute. Most attributes store some type of string value, in other words, text. Therefore, the most common match operators you will use are string match operators. Here are the string match operators:
= Equality—. We have already looked at a few examples together.
<= Less than or equal to—.
(sn<=Arkills)would return entries alphabetically prior to Arkills in addition to Arkills, for examplesn=Adams. Note that in combination with the not filter operator, you can create a greater-than operation that doesn't include the entry that is equal.>= Greater than or equal to—.
(sn>=Arkills)would return entries after Arkills in addition to Arkills, for examplesn=Chewbacca. Note that in combination with the not filter operator, you can create a less than operation.~= Approximate—.
(sn~=Cat)would return entries likesn=Scat,sn=Cast,sn=Hat, andsn=Mat. The algorithm employed for the approximate match filter varies depending on the implementation, so these examples may not work in your environment. Usually a single character wildcard is permitted in any position, but this is not standardized, and the approximate match operator isn't always implemented.
You can use a wildcard to match substring values
Finally, you use the asterisk (*) as a wildcard for zero or more characters in the values of strings. You can use the wildcard by itself to detect the presence of an attribute or in combination with other characters to find substrings. In the example directory shown in Figure 3-3, a search filter of (cn=*Skywalker) would return the entries of both Luke and Anakin Skywalker. Both the presence and substring capabilities that the wildcard provides are very useful.
The available match operators are linked to the type of the attribute
As noted already, the list contains only the match operators for the string type. There are other match operators for other types of data. However, most of these operators work with other data types because these operators are fairly common across all the syntaxes.
New match operators can be defined with LDAP v3
LDAP v3 lets you define additional match operators and rules in the schema for specific data types. How you define these match operators for data and attribute types is covered in Chapter 4, in the section on attribute-matching rules. You can specify these extended match operators in the search filter by using an extended match filter syntax, which is slightly different from the simple search filter syntax already described. The extended syntax of the search filter is
"(" attributetype [":dn"] [":" extendedoperator] ":=" attributevalue ")"
The optional elements are in [brackets]. The extended operator is usually an OID, but a descriptive name can also be assigned in the schema and used here in the filter.
The filter (cn:1.2.3.4.987:=Brian Arkills) would match any entry by comparing “Brian Arkills” with the values in their cn attributes, using the matching logic defined by the matching rule denoted by OID 1.2.3.4.987. Should this OID not denote a matching rule that the directory supports (and in this case the OID is a fabrication of the author), the directory will return an error code.
The DN of entries can be searched with an extended match filter
Extended match filters also let you search the DN of an entry for value matches. This may be a bit confusing at first. An entry's DN contains all the RDNs of the object above it in the directory structure. These RDNs may or may not be attributes of the entry. So if you wanted to find all the entries with ou=People in the DN, you would need to use an extended match filter. Now you may be thinking, “Why wouldn't you use a search with a base DN at the People OU, and a one-level scope?” This seems to accomplish the same thing. But consider the possibility that a referral might reside in the People OU. The more simple search would return records via this referral that technically do not have ou=People in their DN. Also consider the possibility that there might be more than one container with an RDN of ou=People in the directory. In this case, a single search without extended match filters would fail to capture all the entries. Multiple searches would work, but that approach might be inconvenient. Not all LDAP servers support extended match filter searching for DNs.
You must treat special characters differently when they are used in the attribute value portion of an LDAP search filter
There are several special characters that must be treated differently when used in the attribute value portion of a search filter. You must escape these characters just as you had to escape the special characters in the DN or LDAP URL format. Table 3-1 lists the special search filter characters along with the escaped character sequence.
You must use the hexadecimal value of the character, which is different from quoting the special characters in DNs.
The server does most of the work
The LDAP client-server session minimizes client processing overhead. The server is responsible for performing the operations requested and bears the processing load, while satisfying the client request. In the client-server model, the server is designed to handle large computing loads, with larger processing and memory capacity, while the client may have little to no computing power. After the server performs the requested operation, the client receives a response or error from the server. The client does little work other than sending the request and receiving the answer.
Table 3-1. Special search filter characters
Character Desired in Attribute Value | Escaped Character |
|---|---|
* | 2A |
( | 28 |
) | 29 |
5C | |
NUL | �0 |
The client can make multiple requests to multiple servers
LDAP is message based, so the client can make multiple requests with a single session. These multiple operations from the same session each receive server attention at the same time, and therefore a great deal of work can be performed in parallel. Multiple sessions from the same client are also possible at the same time, so a single client can interact with more than a single LDAP server.
The result code indicates the end of the client operation
If the client submits a search request that returns several entries, several messages are returned to the client. Each returned entry is enclosed in a separate message to the client; and when all the entries are returned, a final result code message is sent to the client. Should a referral be returned, then, depending on the applicable settings, additional client or server traffic may result prior to the final result code indicating completion of the operation. Asynchronous LDAP APIs change this behavior; for more details, see the following section, APIs.
LDAP uses TCP/IP and is a very efficient communicator
The LDAP transport makes very efficient use of network traffic. LDAP uses TCP/IP for network communication. TCP/IP is processor and memory intensive, with error checking built into the protocol, and it is most efficient for sessions of more than trivial length. Startup and shutdown of TCP sessions can be a costly use of computer and network resources. The ability to perform multiple operations makes LDAP capable of making good use of communication resources.
The client-server interaction usually follows this pattern:
Client connects to server and requests a bind operation.
Server returns bind operation result code (success or the process ends here).
Client requests a search operation (or some other operation).
Server returns message with located entry or entries from search operation. If no entries are found, no entry messages will be sent.
Server sends search operation result code to client.
Client requests an unbind operation.
Server sends unbind result code and closes connection.
Note that result codes are important, in that they signal the completion of an operation as far as the server is concerned.
CLDAP uses UDP instead of TCP and uses considerably fewer resources than LDAP
There is a form of interaction with an LDAP directory that uses even less communication overhead than the traditional LDAP protocol based on TCP interaction. This form is called connectionless LDAP, sometimes abbreviated as CLDAP. RFC 1798 defines CLDAP, which uses UDP instead of TCP. A CLDAP transaction can use up to a third fewer network packets than LDAP. CLDAP further simplifies the directory model by restricting the number of operations available. CLDAP is primarily intended for use by very simple clients that need to quickly look up information in a directory. The low overhead and even more simplified operations available may be appropriate for some uses at your organization. Very few LDAP servers or client APIs support CLDAP yet. Messaging Direct is an example of one product that supports CLDAP to enable a high volume of messaging service queries.
The ten operations that LDAP defines cover the necessary interaction with a directory. The limited number of operations means that both the client and server are simple to implement and require limited resources.
Bind establishes the identity of the client
The bind operation is the first request a client sends to the server. Binding is the same task as authenticating to the directory. The client is verifying its identity to the directory, so all future operations can be performed in the context of that identity. A client that doesn't bind, or that binds with an empty string as the identity, is said to be anonymous. One identity may be allowed to view directory information that another identity can't. Binding to the directory provides an authorization context for allowing or denying the subsequent operations. The bind operation has two parameters: a DN and a set of credentials. Some LDAP directories are configured to support anonymous binding, and others are designed to allow no requests from anonymous clients. This design choice is typically linked to the sensitivity of the data in the directory.
Compare verifies that an attribute value is known
The compare operation simply verifies whether the information passed by the client matches the information stored in the directory. The compare operation is less useful than the search operation, except for one key situation in which it works differently from the search operation. If you ask to compare an attribute of an entry, but the attribute isn't present on the entry, a special result code is returned. A search operation for an attribute that isn't there returns no entries but a success result code. The compare operation has three parameters: a DN, an attribute type, and an attribute value.
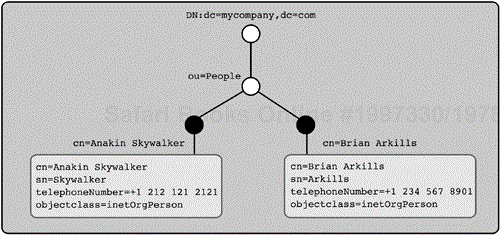
For example, a compare operation request with the following parameters, against the directory pictured in Figure 3-1, would return a TRUE response.
DN: |
|
Attribute: |
|
Value: | + |
Add creates new entries
The add operation allows the client to create a new entry. For it to be successful, the add operation requires that the client specify what object class(es) the new entry will contain, and that all mandatory attributes of that object class be supplied with values. The schema-checking process on the server enforces these requirements. Additionally, the container object of the new entry must already exist, and no existing entry can have the same DN. If there are structure rules for the entry's object class, they also must be met. Finally, the DN (and any RDNs) must be in the proper form with any illegal, special characters escaped. The add operation has primarily two parameters: a DN (of the new entry) and the attribute pairs (type and value) that you want to include on the entry. You can specify as many attribute pairs as you want (or as many as are required by the object class).
As an example, an add operation request to the Mycompany directory with the following parameters would be successful. I've denoted the list of attributes with semicolons delimiting the attribute pairs and with an equal sign connecting each pair. The actual syntax would depend on the API used.
DN: |
|
Attributes: |
|
Delete removes entries
The delete operation removes an entry from the directory. All information associated with that entry (the values of the entry's attributes) is removed. Of course, for the operation to succeed, the entry specified must exist. Additionally, that entry cannot be a container with child entries. A delete operation has a single parameter: the DN of the entry.
A delete operation request with the following parameter would delete the entry we just created in the previous Add section.
DN: |
|
Modify changes the attribute values of an entry
The modify operation allows the client to modify existing attributes of an entry, delete attribute values, or add a value to one or more attributes. The entry designated must exist for the operation to succeed. All the attribute modifications must succeed or the entire operation will fail. This condition avoids an inconsistent entry state in which the operation only partially succeeds. It also avoids the need for the client to order the attribute modifications in a least-to-highest risk order. The modify operation has two parameters: a DN and the set of attribute modifications desired.
Anakin's phone number has changed, and he is anxious to make sure the directory reflects his new number so he doesn't miss any calls from any ladies. He would also like to update his homePostalAddress so the Jedi Academy knows about his new home. A modify request with the following parameters will get the job done:
DN: |
|
Attributes: |
telephoneNumber=+1 212 121 2121; homePostalAddress=31580749 Sith Way $ Jedi Academy $ Coruscant; |
ModifyRDN renames the entry or moves the entry within the directory
The modifyRDN operation allows the client to rename the directory entry. The existing DN is specified, and the new RDN is supplied. The rename operation has four parameters: the DN to be renamed, the new RDN for the entry, a flag to tell the server whether to keep or delete the old RDN as an attribute of the entry, and an optional parameter for specifying a new parent container DN. This last optional parameter is important; it doesn't exist in the LDAP v2 standard. It lets you move an entry anywhere in the directory. The entry being moved can be a container with child entries beneath it. If the entry (or entries) being moved is being relocated to a DN on another server, the operation may fail depending on the vendor implementation. In this case, the client should be prepared to receive an affectsMultipleDSAs error in the result code. Even though the ability to specify a new parent DN is an essential requirement of meeting the LDAP v3 standard, some LDAP servers that advertise themselves as LDAP v3 compliant do not support this functionality.
The modifyRDN operation's ability to move an entry or even an entire portion of the directory tree can be confusing. The following examples should help to illustrate how this operation can be used. Each example is accompanied with a figure that shows how the directory looks before and after the operation.
Leia's name must be updated to reflect her marriage to Han Solo. The following modifyRDN operation parameters are used.
Original DN: |
|
New RDN: |
|
Delete-Old-RDN: |
|
New Parent DN: |
Figure 3-4 shows how the directory looks before and after the operation.
Mycompany's Sales department manages the Customers container in which all customer contact information is kept. The Sales department is now a division of the HR department. Because the HR department manages the People container, the HR department wants the Customers container moved under the People container to reflect the organizational change. The HR department also wants to rename the Customers container to Customer Contacts. The following modifyRDN operation parameters are used.
Original DN: |
|
New RDN: |
|
Delete-Old-RDN: |
|
New Parent DN: |
|
Figure 3-5 shows how the directory looks before and after the operation.
Many people know Chewbacca by his nickname Chewie. His name must be updated to include both his formal name and nickname. The following modifyRDN operation parameters are used. After this operation, the original RDN will no longer be a valid DN, but it will remain as an attribute of the entry.
Original DN: |
|
New RDN: |
|
Delete-Old-RDN: |
|
New Parent DN: |
Figure 3-6 shows how the directory looks before and after the operation.
You may have expected to see both “Chewie” and “Chewbacca” in the second tree. But because of space restrictions, I can't list all the attributes of each entry … so pretend you can see the additional attributes associated with all these entries.
Unbind cleanly ends the client session
The unbind operation allows the client to close its existing session with the directory. The directory obliges by discarding any client credentials it is holding, and it ceases any work on behalf of the client session, effectively terminating the session. Note that the connection, in other words, the TCP session between the client and server, isn't necessarily terminated. After an unbind operation, if the client requests a new operation without binding, the new operation will be evaluated in the context of an anonymous client. The unbind operation has no parameters. If the client terminates the session without issuing an unbind operation, most LDAP implementations use a session timeout parameter to accomplish the same end. The directory administrator can set this directory-wide timeout parameter.
Abandon cancels a specific client operation request
The abandon operation allows the client to tell the directory to cancel a specific previous operation it requested. This eliminates the need to unbind and rebind, should the client not want to wait for the results of a lengthy operation. This operation improves the potential efficiency of the client and server. The abandon operation has a single parameter: the message ID of the operation the client wishes to cancel. Note that a timing issue is possible with this operation. The client could send an abandon request that arrives at the server after the server has sent the complete result code (and entries) from the operation the client is canceling.
Extended operations allow new operations to be defined and used
The extended operation is a placeholder for specific directory implementations to extend the functionality of the directory but still have a predefined syntax for doing so. Additional security functionality such as session encryption is a good example of an extended operation. An extended operation can have parameters just as any other LDAP operation does. An LDAP directory must advertise what extended operations are available in the root DSE object in the supportedExtension attribute. The root DSE object is a special directory entry with an empty DN: “”.
RFC 3062 defines an extended operation to modify passwords
An example of an extended operation that has reached RFC status is the password modify extended operation as defined in RFC 3062. This operation addresses a common need of organizations. Traditionally, LDAP directories stored authentication information internal to the directory so each authentication identity had its own DN. In other words, the username and password were integrated with the LDAP namespace. Now, however, many LDAP directories use primarily SASL as the means of authentication. This allows for an external store of authentication information, using a non-LDAP namespace. Therefore, the traditional method of changing a password using the modify operation won't work in this instance. This extended operation provides a way to modify a password external to the directory.
LDAP controls allow a client to ask the server to perform a standard operation in a slightly different way
LDAP controls constitute an extra parameter that alters the behavior of one of the standard LDAP operations. A control allows an LDAP client to take advantage of a special feature that an LDAP server supports. An LDAP directory must advertise what controls are available in the root DSE object in the supportedControl attribute. The special feature provided by the control can affect how results are returned, allow the client to access entries that are usually ignored, perform a task that is normally impossible with a single operation, or other added functionality that could accompany one of the standard LDAP operations. LDAP controls are designated with an OID and are used in the extended versions of the client API functions.
The paged search control modifies the search operation by asking the server to return entries in pages
A common example of an LDAP control is the paged search control. This control supports a way to retrieve search results from the server a few at a time, instead of all at the same time. This capability is helpful when there is low bandwidth between the client and server, or when the expected number of entries is large. The client specifies a desired page size (in other words, the number of entries per LDAPMessage), and the server returns the smaller set along with a message that the results are paged and the expected number of entries so the client can request the rest by asking for the next paged set. This control provides the only way to circumvent a mandatory upper sizeLimit that is set at the server and affects all sessions. For example, if a directory administrator set a server mandatory sizeLimit of 500 entries, a normal client search would return only the first 500 entries and not reveal any other matching entries. But a search using the paged search control would allow the client to see all the matching entries in pages of 500 at a time. The limit of 500 due to the sizeLimit is still enforced, but the client can still accomplish its task.
The server-side sort control returns sorted search results
Another well-known LDAP control is the server-side sort control defined in RFC 2891. This control works in conjunction with the search operation and asks the LDAP server to sort the entries it returns based on the parameters the client requests. The parameters can include one or more attribute types, matching rules, and ascending or descending order. This control is intended to save the client processing time and resources.
Persistent search control continues to return results indefinitely
Another extended search control is the persistent search control. This control allows a client to receive constant updates on entries that fit the search profile submitted, in other words, the base DN, scope, and filter. When the specified entries change, the client is notified. This type of functionality is extremely useful, especially in a context in which you'd like the directory to feed information to a program or other directory. Unfortunately, this control is not documented in an RFC, but several vendors, including Netscape and Microsoft, have implemented it. Three different designs of this control have been submitted to the IETF for comment: PSEARCH, TSEARCH, and DIRSYNC. These nicknames represent so-called Internet-drafts, which are proposals that were submitted but didn't make it to Internet standard. To make matters worse, vendors have begun implementing slight variations of these three. For example, Microsoft's Active Directory implements a version of PSEARCH with a different OID than that specified in the Internet-draft: 1.2.840.113556.1.4.528. Fortunately, an effort known as LDAP Client Update Protocol (LCUP) is seeking to bring these three different implementations together in an RFC. For your reference, you can find information about these draft controls and LCUP in Appendix A.
LDAP controls are constantly in development to extend the functionality of LDAP
There are many other controls under development. For example, one draft control allows the client to direct the directory server how to handle referrals when chaining is supported. Another draft control called virtual list view lets the client specify that the server return search results in a special order and number designated by the client. This draft control is designed to replace the existing paged search control and will help e-mail clients more fully integrate with LDAP, so long lists of e-mail addresses can be browsed in a list by a specified number of entries. Clearly LDAP controls are an area in which considerable development is under way, and the functionality of LDAP is being extended to meet many needs. You'll see more examples of LDAP controls in Part II, when we look at several LDAP server products.
The LDAP API is an important component of the LDAP framework
LDAP client options allow the LDAP client to specify standard settings for the duration of an LDAP client session, as opposed to a single operation. LDAP client options apply to a server session; so if a client has a session open to two different servers, the options set on one session do not apply to the other server session. LDAP client options are different from LDAP attribute options (for more detail on these, see Chapter 4). The LDAP C API designates several standard client options, and any LDAP implementation can define new ones. The following list comprises some of the options listed in the API RFC:
LDAP_OPT_DEREFThis option allows the client to control how aliases are handled. The valid values are
LDAP_DEREF_NEVER: Never dereference aliases.LDAP_DEREF_SEARCHING: Don't dereference an alias at the base DN, but dereference otherwise.LDAP_DEREF_FINDING: Dereference an alias at the base DN, but don't dereference otherwise.LDAP_DEREF_ALWAYS: Always dereference.
LDAP_OPT_SIZELIMITThis option controls the maximum number of entries that can be returned.
LDAP_OPT_TIMELIMITThis option controls the maximum amount of time the server spends completing an operation.
LDAP_OPT_REFERRALSThis option controls whether the client chases referrals. The valid values are
LDAP_OPT_ON: Chase all referrals.LDAP_OPT_SUBORDINATE_REFERRALS: Chase only subordinate referrals.LDAP_OPT_EXTERNAL_REFERRALS: Chase only external referrals.
Significant options not defined in the API RFC that Mycompany may want its vendor to support include:
LDAP_OPT_SSLThis option directs the client to use SSL on client connections.
LDAP_OPT_REFERRAL_HOP_LIMITThis option sets the maximum number of referrals a client will chase on a single operation.
LDAP client options set parameters for an entire session
The C language LDAP application program interface (API) specified in RFC 1823 is not part of the LDAP standard. However, it is critically important because it helps to define a base framework for programmatically interacting with an LDAP server. Even though this RFC is not part of the standard, almost all vendors implement it. This RFC is an unofficial part of the standard by sheer use and implementation. This RFC is based on the LDAP v2 standard. There is work in progress to produce a replacement RFC that covers LDAP v3.
API calls mostly map to the standard server operations
The function calls specified in RFC 1823 mostly map to the basic LDAP operations. For example, consider the server operation used to add entries. There is a standard API function called ldap_add() that a client program would use to ask the server to perform the add operation.
Each function has a real-time version and a version that combines results into a single response
For each function, there are usually two versions. A synchronous version blocks until all results are available. The program calling a synchronous version doesn't get control until the server finishes replying to the request. The asynchronous version immediately returns a message ID. The program can then use other functions (supplying the message ID) to determine when the server has returned results for the operation. The synchronous versions are easier to use, but the asynchronous versions give your program greater efficiency and freedom at the cost of managing multiple requests/replies. The synchronous versions have a “_s” appended to the end of the function name, while the asynchronous versions do not. For example the synchronous version of the add operation is ldap_add_s(), whereas the asynchronous version is ldap_add().
Additional versions of functions offer other functionality
Several of the functions have more than just the synchronous and asynchronous versions. Some of the functions support slightly different functionality. Each set of versions of a function is loosely called a family, or friends of the primary function.
The LDAPMessage structure holds the results of the client's request, and it can be manipulated by functions
Results or errors from the primary operation function calls are returned via a special data structure called the LDAPMessage. The results in this structure can then be accessed by function calls that do not map to the primary LDAP operations. These other functions allow you to step through results or errors as you see fit. For example, one such function, ldap_first_entry(), calls the first entry returned in the LDAPMessage. This entry can then be stepped through with functions like ldap_first_attribute(). The functions ldap_next_entry() and ldap_next_attribute() allow you to step to the next entry and attribute, respectively.
LDAP API functions are flexible and easy to use
For a list of the functions defined in the LDAP API, see Appendix A. All the functions are included to highlight the flexibility available, should your organization want to develop applications that use their LDAP directory. In addition, the complete listing serves as a quick reference for developers getting started with the LDAP API. Each function is accompanied by a short description. More details on these functions can be found in the RFC, and programmers will want to consult vendor-specific API implementations for differences or significant additional functions.
API libraries in almost every language and platform are available
There are many different implementations of LDAP APIs in a multitude of languages. Netscape's LDAP SDK provides APIs in C, perl, and Java. Sun provides JNDI, a Java API. The PerLDAP SDK uses the perl language. Microsoft provides the ADSI SDK, which can be used with any COM-compliant language, such as C, C+, Visual Basic, Java, and VBScript. Many other APIs exist, including ones for PHP, ODBC, server-side JavaScript, ColdFusion, and others. Books on using the APIs and online resources should make it easy for a programmer to locate and learn whatever is needed.
LDAP operational functionality benefits from a unique blend of standardization and entrepreneurship
The client-server operational functionality of LDAP directories is largely standardized across every vendor's product. This provides a baseline of interoperability that is critical to LDAP's success. You will find this baseline invaluable when you want to centralize directory information. However, the operational functionality is not fixed or limited by the standards. Both the extended operation and LDAP controls provide a means for operational extension. This allows vendors to create unique and powerful enhancements that advance the usefulness of LDAP directories. Not all the operational functionality of LDAP directories is tied to the client-server interaction. In fact, the standard is largely silent about server-to-server interactions. For more detail on this topic, see Chapter 5.
Appendix A contains reference information on the LDAP API functions, as well as the draft controls mentioned.