Invalid Handle (Managed Space)
We recently encountered Invalid Handle (Volume 2, page 269) pattern in the context of .NET program execution. We decided to model it and wrote a small C# program:
namespace SafeHandle
{
class Program
{
static void Main(string[] args)
{
SafeFileHandle hFile =
new SafeFileHandle(new IntPtr(0xDEAD), true);
Console.WriteLine("About to close");
Console.ReadKey();
}
}
}
Of course, when we execute it nothing happens. Invalid handles are ignored by default. However, to change the behavior we enabled “Enable close exception” in glags.exe:
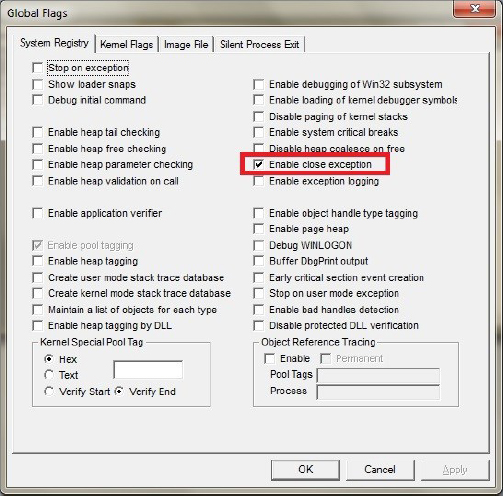
Moreover, if we run it we get this Managed Stack Trace (Volume 6, page 115):
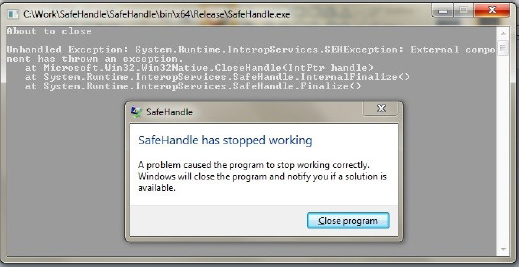
We could have detected invalid handle if we enabled Application Verifier but then we would not have Managed Code Exception (Volume 1, page 331).
So we load a crash dump (saved because we enabled LocalDumps10) and load SOS extension:
0:002> lmv m clr start end module name 000007fe`ed880000 000007fe`ee1eb000 clr (pdb symbols) Loaded symbol image file: clr.dll Image path: C:WindowsMicrosoft.NETFramework64v4.0.30319clr.dll [...] 0:002> .load C:WindowsMicrosoft.NETFramework64v4.0.30319sos 0:002> !pe Exception object: 0000000002ab5fe8 Exception type: System.Runtime.InteropServices.SEHException Message: External component has thrown an exception. InnerException: StackTrace (generated): SP IP Function 000000001B40EDD0 0000000000000000 mscorlib_ni!Microsoft.Win32.Win32Native.CloseHandle(IntPtr)+0×1 000000001B40F2F0 0000000000000000 mscorlib_ni!System.Runtime.InteropServices.SafeHandle.InternalFinalize()+0×1 000000001B40F2F0 000007FEEC62F7A6 mscorlib_ni!System.Runtime.InteropServices.SafeHandle.Finalize()+0×26 StackTraceString: HResult: 80004005
Our unmanaged CLR Thread (Volume 4, page 163) Exception Stack Trace (Volume 5, page 93) is quite simple:
0:002> k Child-SP RetAddr Call Site 00000000`1b40d6e8 000007fe`fd651430 ntdll!NtWaitForMultipleObjects+0xa 00000000`1b40d6f0 00000000`77621723 KERNELBASE!WaitForMultipleObjectsEx+0xe8 00000000`1b40d7f0 00000000`7769b5e5 kernel32!WaitForMultipleObjectsExImplementation+0xb3 00000000`1b40d880 00000000`7769b767 kernel32!WerpReportFaultInternal+0x215 00000000`1b40d920 00000000`7769b7bf kernel32!WerpReportFault+0x77 00000000`1b40d950 00000000`7769b9dc kernel32!BasepReportFault+0x1f 00000000`1b40d980 00000000`778b3398 kernel32!UnhandledExceptionFilter+0x1fc 00000000`1b40da60 00000000`778385c8 ntdll! ?? ::FNODOBFM::`string'+0x2365 00000000`1b40da90 00000000`77849d2d ntdll!_C_specific_handler+0x8c 00000000`1b40db00 00000000`778391cf ntdll!RtlpExecuteHandlerForException+0xd 00000000`1b40db30 00000000`778397c8 ntdll!RtlDispatchException+0x45a 00000000`1b40e210 00000000`778712c7 ntdll!RtlRaiseException+0x22f 00000000`1b40ebc0 000007fe`fd651873 ntdll!KiRaiseUserExceptionDispatcher+0×3a 00000000`1b40ec90 00000000`77621991 KERNELBASE!CloseHandle+0×13 00000000`1b40ecc0 000007fe`ec720418 kernel32!CloseHandleImplementation+0×3d 00000000`1b40edd0 000007fe`ed8e9e03 mscorlib_ni+0×580418 00000000`1b40eea0 000007fe`ed8e9e7e clr!CallDescrWorkerInternal+0×83 00000000`1b40eee0 000007fe`ed8ec860 clr!CallDescrWorkerWithHandler+0×4a 00000000`1b40ef20 000007fe`ed8f1a1d clr!DispatchCallSimple+0×85 00000000`1b40efb0 000007fe`ed8f19ac clr!SafeHandle::RunReleaseMethod+0×69 00000000`1b40f050 000007fe`ed8f180a clr!SafeHandle::Release+0×122 00000000`1b40f120 000007fe`eda4863e clr!SafeHandle::Dispose+0×36 00000000`1b40f190 000007fe`ec62f7a6 clr!SafeHandle::Finalize+0xa2 00000000`1b40f2f0 000007fe`ed8e9d56 mscorlib_ni+0×48f7a6 00000000`1b40f330 000007fe`eda83c4e clr!FastCallFinalizeWorker+0×6 00000000`1b40f360 000007fe`eda83bc3 clr!MethodDesc::RequiresFullSlotNumber+0×72 00000000`1b40f3a0 000007fe`eda83b0f clr!MethodTable::CallFinalizer+0xa3 00000000`1b40f3e0 000007fe`ed9fee46 clr!SVR::CallFinalizer+0×5f 00000000`1b40f420 000007fe`ed9aac5b clr!SVR::CallFinalizer+0×102 00000000`1b40f4e0 000007fe`ed8f458c clr!WKS::GCHeap::IsPromoted+0xee 00000000`1b40f520 000007fe`ed8f451a clr!Frame::Pop+0×50 00000000`1b40f560 000007fe`ed8f4491 clr!COMCustomAttribute::PopSecurityContextFrame+0×192 00000000`1b40f660 000007fe`ed9d1bfe clr!COMCustomAttribute::PopSecurityContextFrame+0xbd 00000000`1b40f6f0 000007fe`ed9d1e59 clr!ManagedThreadBase_NoADTransition+0×3f 00000000`1b40f750 000007fe`ed9533de clr!WKS::GCHeap::FinalizerThreadStart+0×193 00000000`1b40f790 00000000`776159ed clr!Thread::intermediateThreadProc+0×7d 00000000`1b40f850 00000000`7784c541 kernel32!BaseThreadInitThunk+0xd 00000000`1b40f880 00000000`00000000 ntdll!RtlUserThreadStart+0×1d
We see that exception processing happened during object finalization. We can infer the value of the handle (may be Small Value, Volume 7, page 191) via disassembly if this is possible:
0:002> kn # Child-SP RetAddr Call Site 00 00000000`1b40d6e8 000007fe`fd651430 ntdll!NtWaitForMultipleObjects+0xa 01 00000000`1b40d6f0 00000000`77621723 KERNELBASE!WaitForMultipleObjectsEx+0xe8 02 00000000`1b40d7f0 00000000`7769b5e5 kernel32!WaitForMultipleObjectsExImplementation+0xb3 03 00000000`1b40d880 00000000`7769b767 kernel32!WerpReportFaultInternal+0x215 04 00000000`1b40d920 00000000`7769b7bf kernel32!WerpReportFault+0x77 05 00000000`1b40d950 00000000`7769b9dc kernel32!BasepReportFault+0x1f 06 00000000`1b40d980 00000000`778b3398 kernel32!UnhandledExceptionFilter+0x1fc 07 00000000`1b40da60 00000000`778385c8 ntdll! ?? ::FNODOBFM::`string'+0x2365 08 00000000`1b40da90 00000000`77849d2d ntdll!_C_specific_handler+0x8c 09 00000000`1b40db00 00000000`778391cf ntdll!RtlpExecuteHandlerForException+0xd 0a 00000000`1b40db30 00000000`778397c8 ntdll!RtlDispatchException+0x45a 0b 00000000`1b40e210 00000000`778712c7 ntdll!RtlRaiseException+0x22f 0c 00000000`1b40ebc0 000007fe`fd651873 ntdll!KiRaiseUserExceptionDispatcher+0x3a 0d 00000000`1b40ec90 00000000`77621991 KERNELBASE!CloseHandle+0×13 0e 00000000`1b40ecc0 000007fe`ec720418 kernel32!CloseHandleImplementation+0×3d 0f 00000000`1b40edd0 000007fe`ed8e9e03 mscorlib_ni+0×580418 10 00000000`1b40eea0 000007fe`ed8e9e7e clr!CallDescrWorkerInternal+0×83 11 00000000`1b40eee0 000007fe`ed8ec860 clr!CallDescrWorkerWithHandler+0×4a 12 00000000`1b40ef20 000007fe`ed8f1a1d clr!DispatchCallSimple+0×85 13 00000000`1b40efb0 000007fe`ed8f19ac clr!SafeHandle::RunReleaseMethod+0×69 14 00000000`1b40f050 000007fe`ed8f180a clr!SafeHandle::Release+0×122 15 00000000`1b40f120 000007fe`eda4863e clr!SafeHandle::Dispose+0×36 16 00000000`1b40f190 000007fe`ec62f7a6 clr!SafeHandle::Finalize+0xa2 17 00000000`1b40f2f0 000007fe`ed8e9d56 mscorlib_ni+0×48f7a6 18 00000000`1b40f330 000007fe`eda83c4e clr!FastCallFinalizeWorker+0×6 19 00000000`1b40f360 000007fe`eda83bc3 clr!MethodDesc::RequiresFullSlotNumber+0×72 1a 00000000`1b40f3a0 000007fe`eda83b0f clr!MethodTable::CallFinalizer+0xa3 1b 00000000`1b40f3e0 000007fe`ed9fee46 clr!SVR::CallFinalizer+0×5f 1c 00000000`1b40f420 000007fe`ed9aac5b clr!SVR::CallFinalizer+0×102 1d 00000000`1b40f4e0 000007fe`ed8f458c clr!WKS::GCHeap::IsPromoted+0xee 1e 00000000`1b40f520 000007fe`ed8f451a clr!Frame::Pop+0×50 1f 00000000`1b40f560 000007fe`ed8f4491 clr!COMCustomAttribute::PopSecurityContextFrame+0×192 20 00000000`1b40f660 000007fe`ed9d1bfe clr!COMCustomAttribute::PopSecurityContextFrame+0xbd 21 00000000`1b40f6f0 000007fe`ed9d1e59 clr!ManagedThreadBase_NoADTransition+0×3f 22 00000000`1b40f750 000007fe`ed9533de clr!WKS::GCHeap::FinalizerThreadStart+0×193 23 00000000`1b40f790 00000000`776159ed clr!Thread::intermediateThreadProc+0×7d 24 00000000`1b40f850 00000000`7784c541 kernel32!BaseThreadInitThunk+0xd 25 00000000`1b40f880 00000000`00000000 ntdll!RtlUserThreadStart+0×1d 0:002> .frame /c d 0d 00000000`1b40ec90 00000000`77621991 KERNELBASE!CloseHandle+0x13 rax=00000000c0000001 rbx=000000000000dead rcx=00000000009a0000 rdx=0000000000000001 rsi=000000001b40efd0 rdi=000000001b40eff8 rip=000007fefd651873 rsp=000000001b40ec90 rbp=000000001b40edf0 r8=000000001b40ce08 r9=000000001b40cf70 r10=0000000000000000 r11=0000000000000246 r12=0000000000000001 r13=0000000040000000 r14=000000001b40ef40 r15=0000000000000000 iopl=0 nv up ei pl zr na po nc cs=0033 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246 KERNELBASE!CloseHandle+0×13: 000007fe`fd651873 85c0 test eax,eax 0:002> ub 00000000`77621991 kernel32!CloseHandleImplementation+0×1e: 00000000`7762196e 83f9f4 cmp ecx,0FFFFFFF4h 00000000`77621971 0f83952e0100 jae kernel32!TlsGetValue+0×3ef0 (00000000`7763480c) 00000000`77621977 488bc3 mov rax,rbx 00000000`7762197a 2503000010 and eax,10000003h 00000000`7762197f 4883f803 cmp rax,3 00000000`77621983 0f847f8dfeff je kernel32!CloseHandleImplementation+0×56 (00000000`7760a708) 00000000`77621989 488bcb mov rcx,rbx 00000000`7762198c e81f000000 call kernel32!CloseHandle (00000000`776219b0)
Here we also check the value from the managed stack trace or Execution Residue (Volume 2, page 239):
0:002> !CLRStack -a
OS Thread Id: 0x1390 (2)
Child SP IP Call Site
000000001b40edf8 000000007787186a [InlinedCallFrame: 000000001b40edf8]
Microsoft.Win32.Win32Native.CloseHandle(IntPtr)
000000001b40edf8 000007feec720418 [InlinedCallFrame: 000000001b40edf8]
Microsoft.Win32.Win32Native.CloseHandle(IntPtr)
000000001b40edd0 000007feec720418
DomainNeutralILStubClass.IL_STUB_PInvoke(IntPtr)
PARAMETERS:
<no data>
000000001b40eff8 000007feed8e9e03 [GCFrame: 000000001b40eff8]
000000001b40f148 000007feed8e9e03 [GCFrame: 000000001b40f148]
000000001b40f1f8 000007feed8e9e03 [HelperMethodFrame_1OBJ: 000000001b40f1f8]
System.Runtime.InteropServices.SafeHandle.InternalFinalize()
000000001b40f2f0 000007feec62f7a6
System.Runtime.InteropServices.SafeHandle.Finalize()
PARAMETERS:
this (0x000000001b40f330) = 0×0000000002ab2d78
000000001b40f6a8 000007feed8e9d56 [DebuggerU2MCatchHandlerFrame:
000000001b40f6a8]
0:002> !dso
OS Thread Id: 0x1390 (2)
RSP/REG Object Name
000000001B40EEA0 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40EFD0 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F038 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F050 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F090 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F120 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F190 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F1B8 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F240 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F2F8 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F330 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F360 0000000002ab5e10 System.Threading.Thread
000000001B40F390 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F3E0 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F3F0 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
000000001B40F430 0000000002ab58a8
Microsoft.Win32.SafeHandles.SafeViewOfFileHandle
000000001B40F4E0 0000000002ab2d78 Microsoft.Win32.SafeHandles.SafeFileHandle
0:002> !do 0000000002ab2d78
Name: Microsoft.Win32.SafeHandles.SafeFileHandle
MethodTable: 000007feec88a260
EEClass: 000007feec34d340
Size: 32(0x20) bytes
File:
C:windowsMicrosoft.NetassemblyGAC_64mscorlibv4.0_4.0.0.0__b77a5c561934e08
9mscorlib.dll
Fields:
MT Field Offset Type VT Attr Value Name
000007feec88a338 400060d 8 System.IntPtr 1 instance dead handle
000007feec8892b8 400060e 10 System.Int32 1 instance 3 _state
000007feec887de0 400060f 14 System.Boolean 1 instance 1 _ownsHandle
000007feec887de0 4000610 15 System.Boolean 1 instance 1
_fullyInitialized
Please note that we do not have global application flags:
0:002> !gflag Current NtGlobalFlag contents: 0x00000000
Here is the exception stack trace from a different crash dump when we enable Application Verifier:
0:002> !gflag Current NtGlobalFlag contents: 0x02000100 vrf - Enable application verifier hpa - Place heap allocations at ends of pages 0:002> k Child-SP RetAddr Call Site 00000000`24bac4a8 00000000`77cd3072 ntdll!NtWaitForSingleObject+0xa 00000000`24bac4b0 00000000`77cd32b5 ntdll!RtlReportExceptionEx+0x1d2 00000000`24bac5a0 000007fe`fa2c26fb ntdll!RtlReportException+0xb5 00000000`24bac620 00000000`77c2a5db verifier!AVrfpVectoredExceptionHandler+0x26b 00000000`24bac6b0 00000000`77c28e62 ntdll!RtlpCallVectoredHandlers+0xa8 00000000`24bac720 00000000`77c61248 ntdll!RtlDispatchException+0x22 00000000`24bace00 000007fe`fa2bae03 ntdll!KiUserExceptionDispatch+0x2e 00000000`24bad500 000007fe`fa2c268a verifier!VerifierStopMessageEx+0x6fb 00000000`24bad850 00000000`77c2a5db verifier!AVrfpVectoredExceptionHandler+0x1fa 00000000`24bad8e0 00000000`77c28e62 ntdll!RtlpCallVectoredHandlers+0xa8 00000000`24bad950 00000000`77c297c8 ntdll!RtlDispatchException+0x22 00000000`24bae030 00000000`77c612c7 ntdll!RtlRaiseException+0x22f 00000000`24bae9e0 000007fe`fa2d2386 ntdll!KiRaiseUserExceptionDispatcher+0x3a 00000000`24baeab0 000007fe`fdbd1873 verifier!AVrfpNtClose+0xbe 00000000`24baeae0 000007fe`fa2d4031 KERNELBASE!CloseHandle+0x13 00000000`24baeb10 000007fe`fa2d40cb verifier!AVrfpCloseHandleCommon+0x95 00000000`24baeb40 00000000`77a11991 verifier!AVrfpKernelbaseCloseHandle+0x23 00000000`24baeb80 000007fe`fa2d4031 kernel32!CloseHandleImplementation+0x3d 00000000`24baec90 000007fe`fa2d409c verifier!AVrfpCloseHandleCommon+0x95 *** WARNING: Unable to verify checksum for mscorlib.ni.dll 00000000`24baecc0 000007fe`e6a40418 verifier!AVrfpKernel32CloseHandle+0x2c 00000000`24baed00 000007fe`ec0e9e03 mscorlib_ni+0x580418 00000000`24baedd0 000007fe`ec0e9e7e clr!CallDescrWorkerInternal+0x83 00000000`24baee10 000007fe`ec0ec860 clr!CallDescrWorkerWithHandler+0x4a 00000000`24baee50 000007fe`ec0f1a1d clr!DispatchCallSimple+0x85 00000000`24baeee0 000007fe`ec0f19ac clr!SafeHandle::RunReleaseMethod+0x69 00000000`24baef80 000007fe`ec0f180a clr!SafeHandle::Release+0x122 00000000`24baf050 000007fe`ec24863e clr!SafeHandle::Dispose+0x36 00000000`24baf0c0 000007fe`e694f7a6 clr!SafeHandle::Finalize+0xa2 00000000`24baf220 000007fe`ec0e9d56 mscorlib_ni+0x48f7a6 00000000`24baf260 000007fe`ec283c4e clr!FastCallFinalizeWorker+0x6 00000000`24baf290 000007fe`ec283bc3 clr!MethodDesc::RequiresFullSlotNumber+0x72 00000000`24baf2d0 000007fe`ec283b0f clr!MethodTable::CallFinalizer+0xa3 00000000`24baf310 000007fe`ec1fee46 clr!SVR::CallFinalizer+0x5f 00000000`24baf350 000007fe`ec1aac5b clr!SVR::CallFinalizer+0x102 00000000`24baf410 000007fe`ec0f458c clr!WKS::GCHeap::IsPromoted+0xee 00000000`24baf450 000007fe`ec0f451a clr!Frame::Pop+0x50 00000000`24baf490 000007fe`ec0f4491 clr!COMCustomAttribute::PopSecurityContextFrame+0x192 00000000`24baf590 000007fe`ec1d1bfe clr!COMCustomAttribute::PopSecurityContextFrame+0xbd 00000000`24baf620 000007fe`ec1d1e59 clr!ManagedThreadBase_NoADTransition+0x3f 00000000`24baf680 000007fe`ec1533de clr!WKS::GCHeap::FinalizerThreadStart+0x193 00000000`24baf6c0 000007fe`fa2d4b87 clr!Thread::intermediateThreadProc+0x7d 00000000`24baf780 00000000`77a059ed verifier!AVrfpStandardThreadFunction+0x2b 00000000`24baf7c0 00000000`77c3c541 kernel32!BaseThreadInitThunk+0xd 00000000`24baf7f0 00000000`00000000 ntdll!RtlUserThreadStart+0x1d 0:002> !pe There is no current managed exception on this thread 0:002> !CLRStack OS Thread Id: 0x51e4 (2) Child SP IP Call Site 0000000024baed28 0000000077c612fa [InlinedCallFrame: 0000000024baed28] Microsoft.Win32.Win32Native.CloseHandle(IntPtr) 0000000024baed28 000007fee6a40418 [InlinedCallFrame: 0000000024baed28] Microsoft.Win32.Win32Native.CloseHandle(IntPtr) 0000000024baed00 000007fee6a40418 DomainNeutralILStubClass.IL_STUB_PInvoke(IntPtr) 0000000024baef28 000007feec0e9e03 [GCFrame: 0000000024baef28] 0000000024baf078 000007feec0e9e03 [GCFrame: 0000000024baf078] 0000000024baf128 000007feec0e9e03 [HelperMethodFrame_1OBJ: 0000000024baf128] System.Runtime.InteropServices.SafeHandle.InternalFinalize() 0000000024baf220 000007fee694f7a6 System.Runtime.InteropServices.SafeHandle.Finalize() 0000000024baf5d8 000007feec0e9d56 [DebuggerU2MCatchHandlerFrame: 0000000024baf5d8] 0:002> !dso OS Thread Id: 0x51e4 (2) RSP/REG Object Name 0000000024BAEDD0 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAEF00 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAEF68 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAEF80 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAEFC0 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAF050 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAF0C0 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAF0E8 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAF170 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAF228 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAF260 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAF290 000000000c285e10 System.Threading.Thread 0000000024BAF2C0 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAF310 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAF320 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0000000024BAF360 000000000c2858a8 Microsoft.Win32.SafeHandles.SafeViewOfFileHandle 0000000024BAF410 000000000c282d78 Microsoft.Win32.SafeHandles.SafeFileHandle 0:002> !CLRStack -a OS Thread Id: 0x51e4 (2) Child SP IP Call Site 0000000024baed28 0000000077c612fa [InlinedCallFrame: 0000000024baed28] Microsoft.Win32.Win32Native.CloseHandle(IntPtr) 0000000024baed28 000007fee6a40418 [InlinedCallFrame: 0000000024baed28] Microsoft.Win32.Win32Native.CloseHandle(IntPtr) 0000000024baed00 000007fee6a40418 DomainNeutralILStubClass.IL_STUB_PInvoke(IntPtr) PARAMETERS: <no data> 0000000024baef28 000007feec0e9e03 [GCFrame: 0000000024baef28] 0000000024baf078 000007feec0e9e03 [GCFrame: 0000000024baf078] 0000000024baf128 000007feec0e9e03 [HelperMethodFrame_1OBJ: 0000000024baf128] System.Runtime.InteropServices.SafeHandle.InternalFinalize() 0000000024baf220 000007fee694f7a6 System.Runtime.InteropServices.SafeHandle.Finalize() PARAMETERS: this (0x0000000024baf260) = 0×000000000c282d78 0000000024baf5d8 000007feec0e9d56 [DebuggerU2MCatchHandlerFrame: 0000000024baf5d8] 0:002> !do 0x000000000c282d78 Name: Microsoft.Win32.SafeHandles.SafeFileHandle MethodTable: 000007fee6baa260 EEClass: 000007fee666d340 Size: 32(0x20) bytes File: C:windowsMicrosoft.NetassemblyGAC_64mscorlibv4.0_4.0.0.0__b77a5c561934e089mscorlib.dll Fields: MT Field Offset Type VT Attr Value Name 000007fee6baa338 400060d 8 System.IntPtr 1 instance dead handle 000007fee6ba92b8 400060e 10 System.Int32 1 instance 3 _state 000007fee6ba7de0 400060f 14 System.Boolean 1 instance 1 _ownsHandle 000007fee6ba7de0 4000610 15 System.Boolean 1 instance 1 _fullyInitialized
