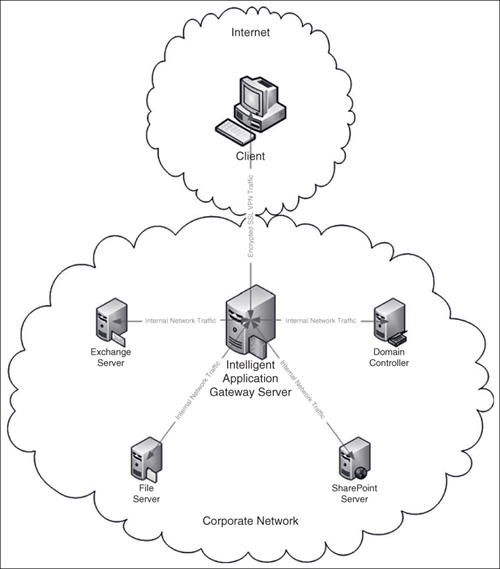
As part of the Forefront infrastructure, virtual private network (VPN) traffic can be configured to pass through the Intelligent Application Gateway (IAG) using a Secure Sockets Layer (SSL) connection. VPNs allow remote users to securely connect to internal networks to gain access to resources. Previously, VPN traffic was encrypted using Layer 2 tunneling protocol (L2TP) or point-to-point tunneling protocols (PPTP), resulting in support problems such as problems with application compatibility, setup complications, and difficulty when being used over networks that use Network Address Translation (NAT).
Using encrypted VPN traffic to connect to the application gateway will help prevent data from being compromised. Using IAG 2007 Network Connector SSL VPN, this traffic is tunneled using a SSL connection. Company employees will establish connections from remote locations, such as their home or a branch office. Client computers will install a Network Connector Client application when they reach the Whale Communication IAG 2007 Portal, allowing them to connect to the internal network using SSL, and eliminate the usability problems that were previously caused by L2TP or PPTP connections.
A large number of companies are allowing employees to do work from home. Allowing employees to access the internal resources of the company’s infrastructure can benefit the productivity of a company. When users connect to the internal network using an insecure network (the Internet), there are security risks involved. In addition, the client’s computer may be in an unknown security state creating additional security risks. Using VPN, which encrypt the traffic, has helped to reduce the vulnerabilities associated with remote connection. Network administrators can use Microsoft Forefront to provide this functionality in environments and for applications for which it was previously unavailable using tunneling SSL connections through the Whale Communication IAG. Administrators can also require compliance with Windows updates, antivirus, anti-spyware, and/or other applications prior to allowing a client VPN access to the corporate network. Figure 10.1 shows the network path for a client connected using the IAG 2007 Network Connector SSL VPN.
The IAG Network Connector SSL VPN would be used for clients that you want to have full network-level access to the corporate network from remote clients. Similar to how LT2P and PPTP VPNs worked in the past but it will allow you to connect from network locations that were not previously possible. Some of these environments include connecting from a client that is behind a router using NAT or in environments with highly restrictive firewalls. The Network Connector also allows you to specify networking parameters including Domain Name System (DNS), WINS, Gateway, and Domain Name for clients after they connect.
Another benefit of the IAG Network Connector SSL VPN is that it supports IAG Access Policies prior to connection. This allows you to confirm compliance with important security measures, such as Windows updates, antivirus, or other software applications prior to the client being allowed to connect to the corporate network. This is a dramatic security improvement over L2TP and PPTP VPNs of the path. To begin configuring the IAG 2007 Network Connector SSL VPN, you would open the IAG Configuration Console and select Admin | Network Connector Server. The following tabs are displayed that allow you to configure the Network Connector to your specific needs.
The Network Segment tab is where you would go to define the network interface connector (NIC) for use by IAG. This dialog will display all of the server’s network interface connections and allows you to select the one that will be used to access the corporate network. This NIC should be the one that is connected to the internal corporate network and it will display the current networking parameters that are active for this NIC on the server. Figure 10.2 shows this configuration page and the different options.
This tab also included a Complementary Data area, which allows you to define networking parameters including DNS, WINS, and the network gateway. You can specify that these settings override the server’s own settings, or have them only apply to the server that doesn’t have these settings configured. These are the settings that will be provided to clients after they connect using the Network Connector. This might be needed if you want to provide your client different settings, such as a specialized WINS server or a special remote client DNS server that only includes name resolution for specific computers and applications.
The IP Provisioning tab is where you would go to define the different Internet Protocol (IP) ranges that will be given to clients when they connect using the Network Connector. All of the address ranges listed will need to be either corporate IP Addresses or private IP Addresses as a mixture of addresses is not supported. If your corporate network uses 10.1.0.0/255.255.0.0 as its corporate IP address space, you may decide to dedicate 10.1.254.2-10.1.254.254 as the corporate address pool for use by the Network Connector SSL VPN. For a private address pool, you may choose to use 192.168.254.2-192.168.254.254. If you specify corporate addresses, you will need to exclude these addresses from your corporate Dynamic Host Configuration Protocol (DHCP) server; otherwise, you could cause IP conflicts. If you select Private IP addresses you will also need to ensure that the address pools specified are properly routed through your network gateway to the IAG server and properly configured in your corporate firewalls. With both corporate and private addresses, the DHCP service needs to be installed and running on the IAG server in order to assign IP addresses to remote clients (see Figure 10.3).
The Access Control tab allows you to set the access restrictions that will apply to the clients that are connected via the Network Connector. The Internet Access section allows you to define how a client will connect to the Internet. This can be either Split Tunneling Mode, where Internet Traffic bypasses the VPN, Non-Split Mode, where Internet traffic is routed through the corporate connection, or No Internet Access, where the client allows access to only resources defined on the Network Connector server (see Figure 10.4).
The Additional Networks tab is where you would select any other networks that should be available to the Network Connector clients when they connect to the Network Connector SSL VPN. In addition, you will need to determine how client IP conflicts are handled. The choices are Fail, Prompt, and Skip. These options determine if a client is open on a Network Connector SSL VPN connection even if they are presently on one of the additional networks. The IP Pool does not need to be included, as that is done automatically. Take special care to include any addresses that your users may need to be able to contact, including infrastructure servers such as DCS, WINS, and DNS, in addition to any application server that they may need to access such as file, print, e-mail, and the location of their desktops for Remote Desktop Protocol (RDP) access. You should also take care to not be overly broad when you define your additional networks, since unmanaged clients may be able to access them and perhaps launch attacks against them. Only seven IP address ranges can be specified as additional networks (see Figure 10.5).
The Advanced tab allows you to set three groups of settings (see Figure 10.6). The first is the Network Connector Listener protocol and port. The default is Transmission Control Protocol (TCP) and Port 6003. The second group of settings is related to the log settings including the log level and location. The log levels range from 1 (minimal) to 5 (verbose). Be careful when increasing the log level as the logs can be extremely large when in verbose mode and affect system performance. The third group of settings allows you to modify the number of threads per central processing unit (CPU), buffer levels, and timeouts.
After the Network Connector server has been configured and activated, you will need to add the application as an option in the IAG 2007 Portal. You can add the application by opening the IAG Configuration Console and running the Add Application Wizard, selecting Client/Server and Legacy Applications and the Network Connector. On the next screen you would give the Network Connector an application name in the portal, and define who is authorized to use the application and the access policy. The next screen displays the settings configured under the Network Connector server configuration and it also allows you to select Launch Automatically on Start, which launches the Network Connector Client upon login to the Portal. The final wizard screen allows you to organize the application in a folder and provide a short and full description for the application.
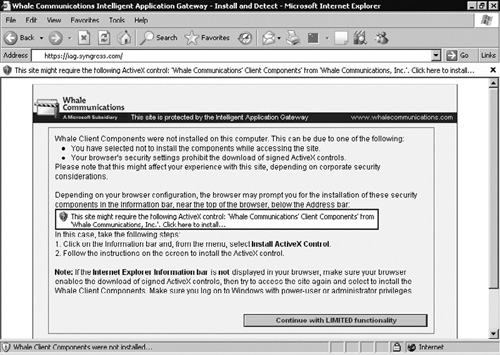
When clients first connect to the IAG 2007 Server Portal, they will be asked to download the Whale Communications’ Client Components v3.7 if they are on machines that support ActiveX (see Figure 10.7).
After installation of this ActiveX software package, the IAG portal will run a client compliance check against the connecting client. This compliance check will determine if your client has the software components required to access the portal. These components may include the presence of Windows updates, anti-spyware, antivirus software, and/or any other compliance requirement that is specified by the administrator of the IAG server. Once this compliance check has completed successfully, the logon screen will be displayed. If the client does not support ActiveX, the user will be taken directly to the login screen and no compliance check will be performed. After successfully logging into the server, you will be presented with a list of applications that are available for your use. One of these applications may be the Network Connector, which is the SSL VPN that operates at the network layer. Depending on the configuration, this Network Connector could also be automatically activated when you login to the portal. If the client supports ActiveX, a second installation will occur for the Network Connector client components. If the client does not support ActiveX but does support Java, a Java install of the Network Client will begin. You can determine the status of the Network Connector by selecting its icon in the system tray for the ActiveX version or a second Web page for the Java version. You can see the icon for the network connector and the status screen in Figure 10.8.
Once the Network Connector has successfully connected, you will be able to access your private corporate resources just as if you were located at the network. If you are using the ActiveX version, all internal and SSL wrapper-based applications will be tunneled through the network connector. If you are using the Java version, only Internet applications will be tunneled through the network connector. SSL Wrapper applications launched through the portal will use a separate SSL connection and not be tunneled over the Network Connector.
The Network Connection server provides your users with a new option for secure remote connectivity. The SSL VPN improves upon LT2P and PPTP by allowing connectivity in network environments where it was not previously possible, such as homes, hotels, or sites with highly restrictive firewalls. It will also allow you to access your clients as if it were on the local network, which can be useful for things such as software distribution and remote control. Unlike LT2P and PTPP connections, the SSL VPN can be configured to confirm client compliance prior to allowing a connection. This ensures that the client meets a minimum security standard prior to being allowed to connect to the corporate network. This is extremely important with the increased utilization of remote access on unknown computers of questionable security.
The following network diagrams will show how data is transmitted by the client, over the Internet, and into the corporate network when the network connector is connected.
| The IAG Network Connector SSL VPN would be used for clients that you want to have full network-level access to the corporate network from remote clients. |
| The Network Segment tab is where you would go to define the network interface connector for use by IAG. |
| The IP Provisioning tab is where you would go to define the different IP ranges that will be given to clients when they connect using the Network Connector. |
| IAG 2007 supports the option of a Network Connector Java client in addition to the Network Connector ActiveX client. |
| If you are using the ActiveX version, all internal and SSL wrapper-based applications will be tunneled through the network connector. |
| SSL wrapper applications launched through the portal will use a separate SSL connection and not be tunneled over the Network Connector. |