
Virtualization and Cloud Computing
Domain Objectives
• 4.1 Summarize cloud-computing concepts.
• 4.2 Summarize aspects of client-side virtualization.
 Summarize cloud-computing concepts
Summarize cloud-computing concepts
Cloud computing has become omnipresent, from online storage services and e-mail providers to integrated business apps. In this section, you learn about the different types of cloud services and how to choose the most appropriate cloud model for the work your client or organization needs to do.
Common Cloud Models
It wasn’t that very long ago that the “cloud” wasn’t much more than a few friendly file-storage services, such as OneDrive, Dropbox, and Google Drive. Today, the cloud offers virtually any service users and enterprises require for infrastructure and applications. The cloud offers a vast array of on-demand computing resources and services from providers such as Amazon, Microsoft, Google, Carbonite, IBM, and myriad others, all on the open Internet.
Cloud Deployment Models
The cloud is conceptually and physically made up of layers of overlapping models. Some models relate to how the cloud is accessed or provided, and others are defined by the type of service or content offered. These models are grouped into two general categories: deployment models and service models. For the A+ Core 1 exam, you need to know what each of these various models defines and understand the services it provides.
Let’s start with the deployment models. In simple terms, a cloud deployment model defines who has access to the cloud and its construction. The A+ Core 1 objectives focus on four primary cloud deployment models: public, private, community, and hybrid.
Public Cloud
On the open, public Internet, almost any service anyone who can access and use the resources available is in the public cloud. When we talk about the cloud in general terms, we are most likely referring to the public cloud. The resources available in the public cloud are owned by the providers and offered to the public, without cost, restriction, or authorization. Search engines, reference sites, and information and entertainment portals are examples of public clouds.
Private Cloud
A private cloud, which is also referred to as an internal cloud, is the opposite of a public cloud. Whereas the public cloud is open to all, a private cloud is closed to the public and open to only the members of a select group. The group is typically a company, school, social or political organization, or another type of membership group or organization. Private clouds offer access control, security, and specialization, which are typically minimal in a public cloud.
Community Cloud
A community can be made up of the students and parents of a school district, citizens of a region, the members of an exclusive organization, the businesses in a chamber of commerce, corporations in the same industry, and the like. A community cloud is a form of a private cloud, paid for by a community, that allows its members to share information and resources. A community cloud can be likened to a community bulletin board or forum.
Hybrid Cloud
A hybrid anything is made up of parts, usually the best parts, of related elements. A hybrid cloud is a conglomeration of structure, access, and content of public and private clouds (a community cloud is essentially a hybrid cloud to begin with). A hybrid cloud is made up of differing amounts of public cloud, private cloud, and onsite resources to create a custom environment.

EXAM TIP You need to understand who can access each type of cloud deployment model and who controls them.
Cloud Service Models
When the cloud was first defined by the National Institute of Standards and Technology (NIST) in 2011, it had three service delivery models: Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS). Since then, there has been an explosion of “aaS” services defined, each with a narrower scope than the last.

EXAM TIP You need to know the common cloud model acronyms—IaaS, SaaS, and PaaS—and associated delivery models for the CompTIA A+ 220-1101 exam.
Infrastructure as a Service
Pronounced as “eye-a-a-ess,” IaaS is a cloud service that provides service subscribers with a combination of virtualization, protection against data loss and downtime, and the scalability to respond to spikes in demand. Cloud service providers (CSPs) enable anyone from individuals to large multinational corporations to launch new virtual servers using a given operating system (OS), on demand, at very low cost. CSPs provide flexible virtualized environments that are capable of driving popular, complex web applications, development environments, and customized operations, including unlimited data storage, database servers, caching, media hosting, and more, all billed by usage. IaaS frees subscribers from managing hardware and operating environments.
Software as a Service
SaaS, which is pronounced as “sass,” is the general term for software applications offered on a cloud-based delivery model to the general public by developers and providers. Access to SaaS offerings can be free (with registration), subscribed to via a time-based agreement, subscribed to on a pay-as-you-go basis, or included as part of a membership package. The benefit to the user or subscriber is that the provider has the responsibility for maintaining and updating its SaaS offerings, along with supplying hardware, installation, and access control, thus relieving the user of these responsibilities.
Examples of SaaS model software and applications include word processing, presentations, spreadsheets, e-mail, flowcharting, and audio/video teleconferencing. SaaS offerings are available anywhere there is an Internet connection. However, one of the major tradeoffs of using SaaS applications is that you may need to give up control of your data to the SaaS provider and trust in its security.
Platform as a Service
PaaS, pronounced as “pass,” is a cloud service model that provides subscribers with access to a customized bundle of hardware and software resources over the Internet. One of the more common uses for PaaS services is for software development and testing. A PaaS environment can give software developers the tools needed for developing, deploying, administering, and maintaining applications and other software products.
The PaaS CSP constructs an infrastructure, which could be an IaaS, and builds a platform. The platform can even be a complete deployment and management system. A PaaS subscription saves the user acquisition and maintenance costs as well as the cost and time of setup, configuration, and maintenance (commonly at the expense of flexibility).
Cloud Characteristics
Cloud computing is in many ways similar to the time-sharing practices of the early days of computing. Time-sharing allowed companies to “rent” time on a centralized computer and to avoid the expense of purchasing computing equipment, which at the time was primarily mainframes. In many ways, the cloud permits a company to “rent” services from a service provider over the Internet, rather than over dial-up lines as before, and not have to bring all of the required hardware and software, and people, in-house. The following sections provide descriptions of some of the features and characteristics of cloud computing.
Shared Resources
One of the benefits of cloud computing is how it enhances the concept of shared resources. All networks feature shared resources, such as storage and servers connected to the same LAN. With cloud computing, these and other resources are accessed on the Internet.
When you consider that even a moderately successful CSP may have dozens, if not hundreds or thousands, of subscribers to it services, providing access to its resources must be on a shared basis. Depending on the service model offered, hardware, software, data storage, and other services must be leveraged to provide each of the service subscribers with the resources and access defined in each service level agreement (SLA). To accomplish this, the CSP must implement a virtualized environment.
System, network, and storage virtualizations are essential elements of resource sharing in cloud computing. On the subscriber side, the CSP’s virtualized environment is transparent, and each individual or corporate subscriber operates in a “dedicated” space that provides all of the resources required for their needs.
Metered Utilization
A metered utilization model is a measured activity method that some CSPs use to track the activities of a subscriber on a cloud service. The metrics show the amount of resource usage, in appropriate units of measure, and provide the CSP with a basis for monitoring, controlling, throttling (limiting), scaling, and, of course, billing the subscriber for that usage.
The service agreement between the CSP and the subscriber defines the rate per unit for the various measures of time (minutes), data transfer amounts (MB or GB), scalability (service levels), data storage space (MB/GB), and other resources and related measurements. For example, should a company need extra servers during the work week only, it can subscribe for the use of IaaS servers and pay for the time, capacity, or data transfer metrics it uses. The company avoids purchasing physical servers that may sit idle nearly 30 percent of the time. Metered utilization services are also known as measured services or “pay-per-use” services.
Resource control and billing are the two primary reasons CSPs use metering. Metering captures a subscriber’s use of shared resources, such as bandwidth or data storage, as they are consumed. The captured data can then be used for analysis, summarization, scaling or throttling, and billing.
Scaling is the expansion or reduction of the usage thresholds or amounts of a subscribed service based on demand, usage, or isolated events. For example, if a subscriber is constantly at or over their subscribed disk storage limit, they can agree to scaling the disk storage limit to a new higher level. The same scenario could also apply should the subscriber need to reduce their resource requirements. Scalability of resources can also be a standby or as-needed service that is applied on the fly.
Throttling isn’t exactly the opposite of scaling, but if scaling is considered to be an expansion, then throttling is a contraction. However, throttling is based on an agreed-to ruleset that defines resource access and usage. A subscriber’s actual usage is measured against the throttling rules, which typically define the upper limit of a resource’s usage. Throttling is normally used to prevent unlimited use of a resource that is scarce or in high demand.
Billing is based on the actual utilization of resources by a subscriber. The metered usage metrics are used to generate the billing, which is commonly monthly.
Elasticity/Scalability
One of the more sought-after characteristics of the cloud is flexibility, which is expressed as elasticity in the A+ Core 1 objectives and scalability in many service descriptions. Expanding the capabilities of an in-house system can take more time than is usually available and cost more than it should. A cloud service such as IaaS or PaaS can provide subscribers with the capability of expanding resources as they become required. This elasticity can be instantaneous, with the subscriber unaware of the changes, or the subscriber can be notified for approval before the service increase is applied. Flexibility provides the subscriber with the capability of adding cloud resources and services on demand, which empowers the subscriber to scale up or down rapidly to manage spikes or lulls in resource demand. This is known as rapid elasticity.

EXAM TIP Rapid elasticity allows a customer to use more, or fewer, cloud resources, as needed. On demand means that a customer can access cloud resources 24/7, as needed.
High Availability
Some companies and organizations must have access to their data and systems at (or very nearly at) all times, 24/7 and 365. Ensuring this capability can be extremely expensive considering the equipment and personnel required. Subscribing to a cloud service that promises this level of support, called high availability, involves transferring both the responsibility and trust to a CSP.
Data stored in the cloud, regardless of it being a ready source for interactive commerce or as a backup, is an essential asset that must retain its integrity and be immediately available when needed. The services and security measures of a CSP offering data storage must provide for the high availability, confidentiality, and integrity of its subscribers.
High availability is an umbrella term that is defined by the terms of an SLA between the CSP and the subscriber. Suppose the subscriber needs its data to be instantly available only certain hours and days, such as 7 a.m. to 10 p.m., Monday through Friday, but no less than 99.9 percent of the time during those hours. This, then, is the high availability required by the subscriber. An online shopping website that supports real-time ordering around the clock, seven days a week and 52 weeks a year, could require the same percentage of high availability (99.9 percent), which results in a much higher commitment from the CSP. In comparing these two examples, we can see that the former requires a commitment from the CSP that, during the contracted hours, the SaaS and the subscriber’s data cannot be unavailable for any more than one minute per daily session. In the second example, the CSP commits to ensuring that its services cannot be unavailable more than 8.78 minutes per year. Table 4.1-1 provides the upper limits of downtime in the “five-nines” chart for high availability commitments.
TABLE 4.1-1 Downtime Limits by Time Period in the Five-Nines Schedule
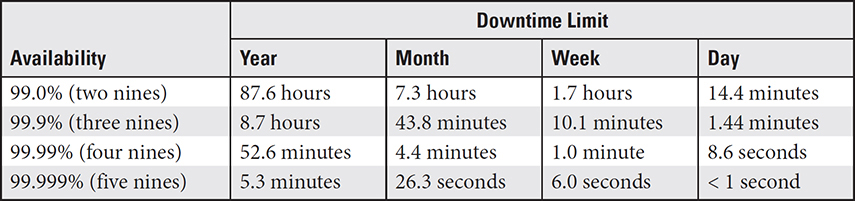

EXAM TIP You don’t need to memorize the information in Table 4.1-1. It’s provided only as an illustration for high availability. However, the five-nines approach is commonly used to define availability terms in SLAs.
File Synchronization
File synchronization is fundamentally a form of file backup, where a data file or object is replicated to one or more different storage media. File synchronization differs from just making a copy periodically in that it’s designed to keep copies of files and objects coordinated, regardless of their locations. A backup copy of a file is a snapshot taken at a point in time. Until a backup is replaced by a later snapshot of the same file, it remains the same. A synchronized file remains constant to its source, meaning that any change made to the source file is automatically made (on demand) to the synchronized file as well. Backup files are normally stored on a separate medium or device and placed offline in a secured location. A set of synchronized files can be stored on the same device or even on different types of storage media on the same device, attached to its network, or even in the cloud. Typically, though, synchronized files are stored on different devices and usually different media.
A set of synchronized files may have copies on a desktop PC, a mobile PC, and a smartphone, and perhaps other devices as well. On these devices, the files may be on a hard disk, a USB device, and on the Universal Flash Storage (UFS) of a cell phone. If a modification is made to any one of a file’s copies, a file synchronization application or service will follow predefined rules and settings to apply the modification to all other versions of the file, regardless of on which device the change was made and on which devices the synchronized files copies are stored. The configuration and settings of the file synchronization software determines its actions: for example, not all copies are updated for any change; some copies are updated only periodically; all synchronized copies are refreshed periodically—plus a variety of other synchronization actions.
File synchronization can be a one-way or two-way process. One-way synchronization is also referred to as mirroring (in RAID). When a change is made to a base copy of a file, copies of the revised file are sent to designated locations in storage. Only changes to the base file are mirrored. Two-way synchronization, which is actually what file synchronization is, applies any modifications to all copies of a file, often by copying the entire file to all the synchronized copies.
Desktop Virtualization
Virtualization, in the context of computing, is a process that simulates hardware elements that exist only as creations of the virtualization software. Although virtual, the simulated hardware is able to function as if it were an actual device. Virtual devices can be computers, network adapters, internetworking devices, and many others, including what you’ll likely see on the A+ Core 1 exam: virtual desktops.
Virtual desktops are created in one of two models: hosted desktop infrastructure (HDI) and client virtualization or virtual desktop infrastructure (VDI). The hosted desktop model defines virtualized machines and desktops created directly on physical hardware, or what is called “bare metal.” Client virtualization, or VDI, can create desktop environments on the premises, on a remote workstation on a local network, or in the cloud.
Desktop virtualization creates (and in many cases, stores) multiple simulated user desktops, all running on a single computer. The host device, the computer on which the virtualization software (called a hypervisor) is running, could be a physical computer in an organization or a virtual computer in the cloud. Most of the virtualization systems create persistent virtual desktops, which means that the system saves the entire virtual desktop’s environment so that its user can store it and then later recall it to continue exactly at the point where it was stored. A nonpersistent virtual desktop cannot be saved and is completely new each time it’s started.
Virtualization systems support three types of desktop virtualizations:
• Virtual desktop infrastructure (VDI) In this type of desktop virtualization, the hypervisor creates virtual machines (VMs), each with its own desktop image, on a data center or cloud server. Users access the virtual desktops remotely from endpoint devices. VDI creates a dedicated VM that creates its own unique operating environment.
• Remote desktop services (RDS) Using RDS, users can access a remote desktop that shares hardware resources as well as system and application software.
• Desktop as a Service (DaaS) DaaS (pronounced as “dass”) is very much like VDI, with the major exception that the user’s organization doesn’t supply the hardware or software on which the virtual desktop is generated, only the endpoint device used to access the DaaS service in the cloud.
REVIEW
Objective 4.1: Summarize cloud-computing concepts
• The major types of cloud services are Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS).
• The public cloud provides cloud services to anyone.
• A private cloud limits access to authorized internal users.
• A community cloud is a private cloud with access limited to a specific group of organizations or individuals.
• A hybrid cloud blends features of public and private cloud resources.
• Resources such as VMs, cloud storage, and others can be shared via LANs (internally) or cloud computing (externally).
• Metered utilization tracks computing resource usage via measurements of bandwidth, time, and/or capacity for billing and analysis purposes.
• The ability to add or drop cloud services as needed (on-demand self-service) enables organizations to have rapid elasticity.
• Popular cloud-based services include e-mail, file storage, and file synchronization.
• Virtual desktop infrastructure (VDI) creates a virtual environment that can be accessed locally or on the cloud as a stored, persistent, or renewed standard or nonpersistent desktop image.
• File synchronization is used to keep multiple copies of a file or object in sync, commonly on diverse devices.
4.1 QUESTIONS
1. Company A uses several SaaS products such as Gmail and Google Docs, along with a customized private cloud for its proprietary apps. Which of the following best describes Company A’s cloud computing strategy?
A. Public cloud
B. Hybrid cloud
C. Community cloud
D. VMM
2. Company B operates an around-the-clock real-time sales operation that supports both telephone and online orders. When an order is accepted, the inventory is updated in real time to avoid oversales. What element of the company’s SLA with a CSP covers the requirements of this area of its operations?
A. Bandwidth
B. Backups and archives
C. High availability
D. Metered utilization
3. Your company is going to use cloud services to develop software, and the software will then be available as a cloud service. Which pairing accurately reflects what services will be used, in the correct order?
A. IaaS, PaaS
B. PaaS, SaaS
C. SaaS, IaaS
D. SaaS, PaaS
4. What is the term for the capability of a cloud service to expand or contract its resources, as required, to serve a subscriber’s needs?
A. DaaS
B. Synchronization
C. Rapid elasticity
D. Metered utilization
5. Your company needs access to unlimited resources to support on-demand swings in resource requirements but wants to pay only for the resources actually used. What service arrangement is your company looking for?
A. VDI
B. IaaS
C. Hybrid cloud
D. Metered utilization
4.1 ANSWERS
1. B A hybrid cloud combines public cloud (in this case, SaaS) and private cloud solutions.
2. C High availability is a critical element of Company B’s operations.
3. B Platform as a Service (PaaS) is the use of a complete cloud-based software development environment. Software as a Service (SaaS) makes the software available for use via the cloud.
4. C Rapid elasticity in a cloud environment is the ability to increase or decrease committed resources, as needed, to meet a subscriber’s processing or storage requirements.
5. D Metered utilization provides unlimited access to resources on a pay-for-what-you-use basis.
 Summarize aspects of client-side virtualization
Summarize aspects of client-side virtualization
Virtualization enables a single physical host computer running specialized software to create virtual machines (saved in separate files), also known as guests, which replicate other computers, each with its own operating system, settings, apps, and data. Client-side virtualization refers to running a virtual machine (VM) on your local system (in contrast to VMs run elsewhere) regardless of whether the VM file itself might be stored locally or on a central server accessed via the network. The software used to create and manage VMs is known as a hypervisor.
Purpose of Virtual Machines
If you aren’t familiar with virtualization, the idea can seem a little pointless at first. Why would you need to run an OS inside an OS? Here are a few of the biggest benefits:
• Going virtual enables companies to combine multiple servers onto fewer machines than in traditional computing. This offers tremendous savings on hardware purchases, electricity use, and the space used for computing.
• Because a VM is only a single file or two, a hacked system can rapidly be replaced with a snapshot (a backup) taken of the properly working VM. This is especially useful for getting critical servers back up quickly. Likewise, the minimal file numbers make it easy to duplicate a VM.
• The capability to run many operating systems on a single physical machine makes multiplatform testing and research easier and cheaper than with traditional setups.
Sandboxing
Sandboxing is a virtualization concept in which a newly developed or a suspicious program can be executed as a test or a trial on a virtualized computer. The program running in the sandbox has the resources it needs to completely simulate that it’s running in a production environment without any of the risk that might mean.
Another virtual concept that is an extension of a sandbox is the container. Sandboxes are created in essentially the same size and with the same resources, which is often more than what’s actually needed for its purpose. A container is a sandbox that is fitted to its task.
Another, perhaps lesser known, fact about sandboxes is that a virtual machine is essentially a sandbox, which is something you should know.

EXAM TIP You should know about sandboxes, containers, and VMs for the A+ Core 1 exam.
Test-Driven Development
Test-driven development (or test development) is a rapid application development (RAD) technique commonly performed on a VM, which is a perfectly safe environment for the development and testing of apps. In test development, small blocks of programming are tested against an environment that simulates the problem to be solved or an objective to be achieved. The short version of the test development process goes something like this: create a test, write a program, test the program, adapt the programming, and then repeat.
Application Virtualization
Application virtualization is a term that describes one of the major purposes and uses of virtualization in general. Application virtualization describes the interaction of a thin network client running in an application environment on a VM. The virtual environment hosting the virtual application could be a local or remote physical or virtual server. Application virtualization is able to overcome any environment conflicts on a local machine.
Virtual applications are optimized to run in virtual desktop environments on a local machine or in the cloud. A virtual application actually runs on a server but appears to be running on the VM. Another form of application virtualization is application streaming. In this method, only portions of an application, its code, configuration, and data are delivered to the VM and then only when they are needed.
Application virtualization managers can streamline the use of virtualized applications. For example, the Microsoft Application Virtualization (App-V) for Windows product manages the delivery of virtual applications to user environments. The virtual applications are stored on central servers and delivered in real time using the as-needed method described earlier. On the virtual desktop, a user accesses the virtual application in the same way as a locally installed application.

NOTE Other available virtual application managers include Citrix Virtual Apps, Parallels Remote Application Server, and the Microsoft Azure Virtual Desktop.
Many companies and organizations cling to older, “legacy” software (most likely with the claim that if it’s still working, there’s no reason to replace it), despite the fact that the hardware and software environments on which it was originally developed to run may no longer be available. Cross-platform virtualization, which is a software-based system emulator, allows these systems to run on a virtual machine configured to provide the required environment. Virtualization provides the capability for legacy operating systems and applications to continue to be used until newer software can be developed or the processes are brought up to date.

EXAM TIP For the A+ Core 1 exam, know and understand the purpose and use of VMs and their relationships with virtual apps, including sandboxes, application and test development, and VDI.
Resource Requirements
The latest versions of Windows, Linux, and macOS will support a hypervisor or a virtual machine manager (VMM). However, a hypervisor or VMM runs better on a computer with hardware virtualization support. If your computer’s CPU and BIOS UEFI include hardware virtualization, it can be enabled or disabled in the system setup utility (see Figure 4.2-1).

FIGURE 4.2-1 UEFI firmware settings for CPU virtualization support on AMD (top) and Intel (bottom) CPUs
Cross-Reference
Hardware virtualization is also covered in Domain 3.0, Objective 3.4.

NOTE AMD and Intel include hardware virtualization to provide better performance when the CPU is supporting multiple VMs and operating systems. AMD’s hardware virtualization features are Secure Virtual Machine (SVM) mode and AMD-V. Intel provides VT-x and Intel VT-d. VT-d is separate from VT-x and provides directed I/O (input/ output) virtualization for better performance.
In addition to hardware virtualization, two other hardware requirements for efficient virtualization support are RAM and storage space. Each VM requires just as much RAM as the physical machine it’s emulating. Even though the RAM assigned to a VM is allocated as needed, the host machine may need sufficient RAM itself to run the hypervisor and, in some cases, the host operating system and perhaps other software. Just how much RAM is needed in total typically requires a bit of research.
A VM can also take up a lot of storage space. A VM’s files can consume a considerable amount of storage space because they include everything installed on the VM, which can amount to anywhere from a few megabytes to as much as dozens of gigabytes. Online calculators can be used to help you calculate the space requirements for configuring a VM in a variety of hypervisors or VMMs.

ADDITIONAL RESOURCES One virtualization calculator you could use is the “Virtualization Calculator” provided by WintelGuy.com at https://wintelguy.com/vmcalc.pl.
Emulator Requirements
In the virtualized world, some hardware is emulated and some is virtualized. Often emulation and virtualization are confused and thought to be the same thing. Although they have many similarities, emulation and virtualization have some differences in how they operate.
When a system imitates the actions of another, it is emulating that system. For example, suppose you have an old game such as Duke Nukem that you’d like to play again. Windows 11 won’t run the software, but you can access an OS emulator, like OnWorks.com, that emulates a Windows 95 environment through your browser so you can play the game. Your system is still Windows 11, but you’re running a browser that is running an emulator on a web application. Emulation is performed by software running on a native environment that mimics another environment. The difference is basically that virtualization runs independent of the base system whereas emulation runs on the base system.
Hypervisors emulate hardware to allow a guest OS to be able to access and use the hardware devices available on a host system. Otherwise, the hypervisor would need to include a device driver for any and all devices a guest OS supports. Emulating a generic version of a device driver allows the guest operating system and any application it runs to use the virtual hardware. The types of hardware being emulated are typically those that are widely supported and those for which the guest OS includes a driver.
In the emulation performed by a hypervisor, the commands given to the virtual desktop hardware device are converted into the appropriate commands used by the physical device.

EXAM TIP Understand that emulating another platform (using a laptop to run Sony PlayStation 5 games, for example) requires hardware several times more powerful than the platform being emulated.
Security Requirements
A virtual machine should be kept as secure as a physical computer. After all, with network and Internet connections present on almost any VM, it can be used (or misused) in the same way as a physical computer. Different users with different levels of access should be set up on a VM that will be used by multiple users. Strong passwords should be implemented. Antivirus and anti-malware apps should be deployed and kept updated. OS updates should be performed as needed.

EXAM TIP Virtualized operating systems use the same security features as real ones. You still need to keep track of user names, passwords, permissions, and so on, just like on a normal system.
Network Requirements
The easiest way to network a computer that will be hosting one or more VMs is with the fastest wired Ethernet supported. If you want a wireless connection, you could use a wireless NIC that uses a PCIe slot. Using a USB network adapter is not recommended because of the limited support that USB devices have on most VM software.
Hypervisor
A hypervisor, also known as a virtual machine manager (VMM), creates, runs, and manages VMs. There are two types of hypervisors: Type 1 and Type 2.

EXAM TIP Be sure to know the differences between Type 1 and Type 2 hypervisors.
A Type 1 hypervisor such as Hyper-V, VMware ESXi, or Citrix Hypervisor (formerly known as Citrix XenServer) runs directly on computer hardware in place of a standard operating system. A Type 1 hypervisor is also known as a “bare-metal” hypervisor because there’s no other software between it and the hardware. VMs running server operating systems are run on Type 1 hypervisors.
A Type 2 hypervisor such as Oracle VM VirtualBox or VMware Workstation is run on a standard operating system (Linux, Windows, or macOS). Thus, Type 2 hypervisors have an additional layer of software compared to Type 1 hypervisors (see Figure 4.2-2 for an example). Most types of client-side virtualization use Type 2 hypervisors.
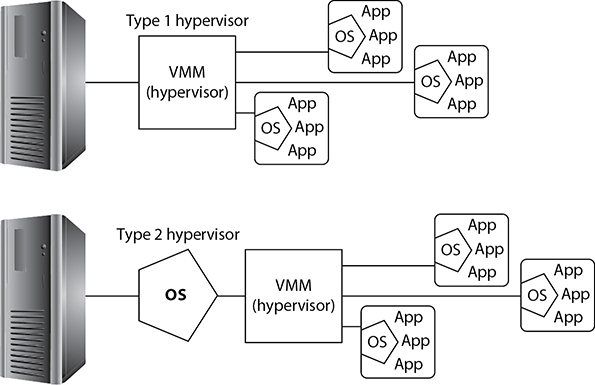
FIGURE 4.2-2 Type 1 hypervisor (top) compared to Type 2 hypervisor (bottom)

NOTE Although you install Hyper-V after installing Windows Server or enable it after installing a Windows 10 or Windows 11 edition that includes it, it is considered a Type 1 hypervisor. Here’s why: after Hyper-V is installed/enabled, it turns the Windows edition that was installed first into a VM running under Hyper-V, and additional VMs can be created. To learn more about the differences between Hyper-V running on Windows versus Hyper-V running on Windows Server, see https://docs.microsoft.com and search for “Hyper-V.”
Installing a Hypervisor and Creating a Virtual Machine
Installing a third-party hypervisor is like installing any other software—download and execute the hypervisor software and follow its setup wizard. On a Windows system that includes Hyper-V, you can enable it in the Windows Features dialog box (see Figure 4.2-3), which you reach via Control Panel | Programs and Features applet | Turn Windows Features On or Off. After enabling Hyper-V, reboot the system.
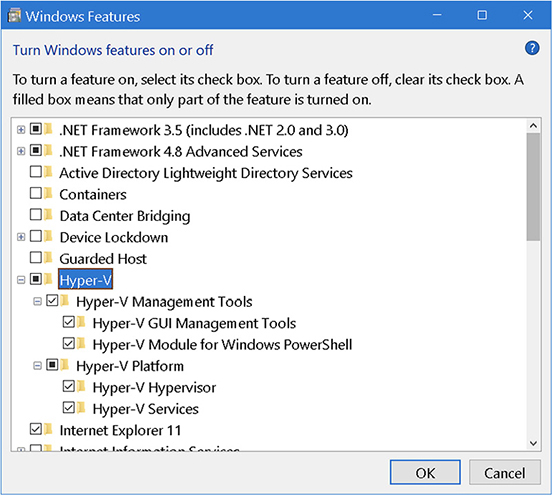
FIGURE 4.2-3 Enabling Hyper-V in Windows
After you’ve installed your hypervisor of choice, you’ll have a virtual machine manager that acts as the primary place to create, start, stop, save, and delete guest virtual machines. On pretty much any VMM, you create a new VM by clicking New | Virtual Machine and completing the wizard that opens (see Figure 4.2-4). Most hypervisors have presets to ensure your guest OS has the virtual hardware it needs.
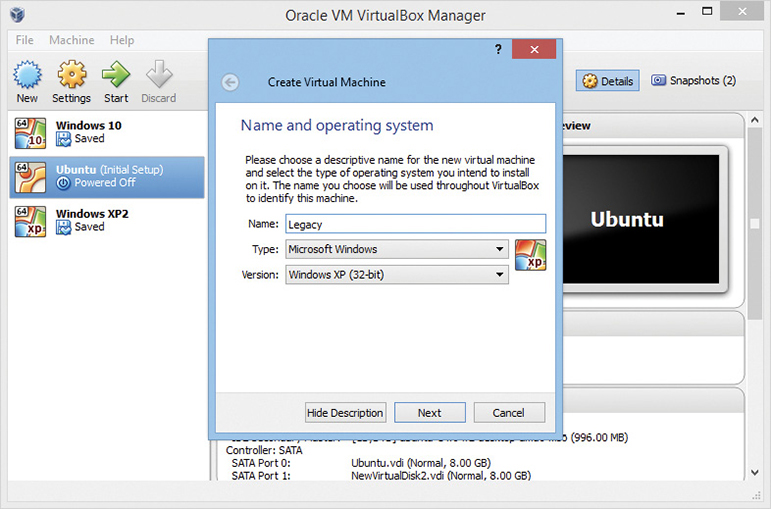
FIGURE 4.2-4 Creating a new VM in Oracle VirtualBox
Installing the Guest Operating System
Once you’ve created the new guest VM, it’s time to install a guest operating system. Would you like to use Microsoft Windows in your virtual machine? No problem, but know that Windows (and any other licensed software you install) requires a valid license.
If you don’t already have installation media, most VMMs can just treat any ISO file (such as the one you’d use to make your own installation media) as the virtual machine’s optical drive. If the VMM recognizes your installation media (see Figure 4.2-5), it may configure the virtual hardware settings (amount of RAM, virtual hard drive size, and so on) automatically; otherwise, you need to set sensible values for these (you can still change them after the VM is created). Next, set the size of the virtual drive (see Figure 4.2-6).
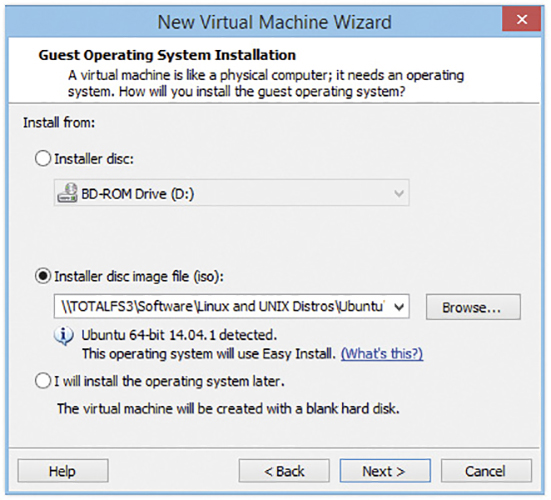
FIGURE 4.2-5 Installer recognizing selected installation media
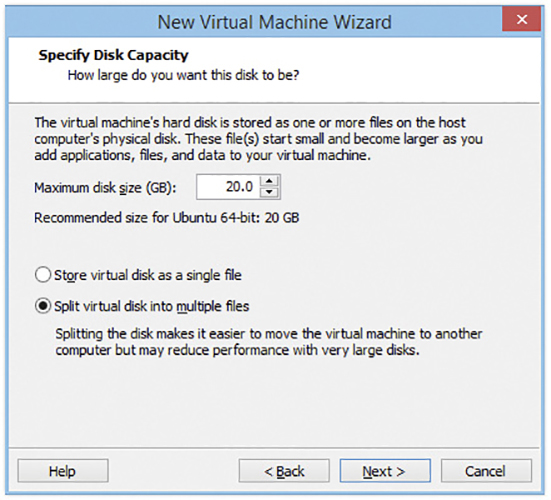
FIGURE 4.2-6 Setting the virtual drive size

EXAM TIP After you have set up a VM, installing an operating system into it is just like installing an OS on a normal computer.
You’ll also be prompted to name the VM and indicate where to store its data files. If you specified installation media, you’ll also have some time to burn while the OS installs. After configuration and installation, you can stop, start, pause, or delete the VM, add or remove virtual hardware, or just interact with the OS and other software inside it.

NOTE Use descriptive names for virtual machines, such as “64-Win10-Mark.” This will save you a lot of confusion when you have multiple VMs on a single host.
Using a VM is almost exactly like using a real system, except it’s contained in a window and some hotkeys differ. VMware Workstation, for example, replaces CTRL-ALT-DELETE with CTRL-ALT-INSERT by default (so you can still use CTRL-ALT-DELETE on your desktop). That, and you can adapt your virtual desktop to changing needs without a trip to the store: a good hypervisor can add and remove virtual hard drives, virtual network cards, virtual RAM, and so on. Keep in mind that USB drive support varies between hypervisors and may require special settings or have limited support for USB 3.0 and faster versions.
REVIEW
Objective 4.2: Summarize aspects of client-side virtualization
• Virtualization enables companies to use fewer servers to perform tasks, provides for faster backup, and enables multiplatform testing on a single computer.
• Virtual machines (VMs) can provide for sandboxes and development and testing environments.
• Intel and AMD processors support hardware virtualization with VT-x and AMD-v, which is enabled or disable in BIOS/UEFI setup.
• Virtualization requires sufficient RAM and disk space for each VM as well as for the host OS or hypervisor.
• Hypervisors emulate a wide range of hardware without specific drivers.
• VMs require exactly the same levels of security (passwords, updates, and so on) as the physical computers they replace.
• Application virtualization provides support for legacy applications and cross-platform compatibilities.
• Type 1 hypervisors (a.k.a. bare-metal hypervisors) are installed directly on the hardware and are typically used for VMs in production applications.
• Type 2 hypervisors are installed on an operating system and are typically used for experimenting and educational purposes.
• Hyper-V is a Type 1 hypervisor available on Windows 10 and later that is enabled through the Turn Windows Features On or Off option in the Programs and Features Control Panel applet.
4.2 QUESTIONS
1. What is the term for a virtual machine (VM) environment used to test out new programs in an isolated area away from critical servers and resources?
A. Type 1 virtualization
B. Sandbox
C. VMM
D. Type 2 virtualization
2. Which of the following statements are true?
A. A virtual machine is a computer that is walled off from the physical computer on which the virtual machine is running.
B. Virtual machines provide the capability of running multiple machine instances, each with its own operating system.
C. The downside of virtual machine technologies is that having resources indirectly addressed means there is some level of overhead.
D. A and B.
E. All of the above.
3. Company D has set up virtualization on several late-model Intel and AMD systems running high-performance processors using the recommended settings in the hypervisor for each VM, but the VMs are running very slowly. Which of the following is the most likely cause?
A. Hardware virtualization support is not enabled in the UEFI firmware.
B. VMs are using too much RAM.
C. Hardware virtualization support is not enabled in the OS.
D. VMs are using too much disk space.
4. Customer E is running Windows 10 Pro and wants to install a Linux-based VM in Hyper-V. Which of the following must the customer do for this to work? (Choose two.)
A. Turn on Hyper-V in Windows Features.
B. Run Windows Update.
C. Scan the host system for viruses.
D. Restart the system.
5. What operating system can be installed as a VM guest OS?
A. Windows 10
B. Linux distro
C. Windows 11
D. macOS
E. All of the above
4.2 ANSWERS
1. D Type 2 virtualization runs within an installed operating system and relays requests to the hardware to the host operating system, whereas Type 1 virtualization directly interfaces with the computer’s hardware.
2. E A VM is segregated from the physical computer, can be one of many instances running on a physical computer with its own OS, and can generate additional operational overhead.
3. A High-end Intel and AMD processors have support for hardware virtualization. However, if it is not enabled in the firmware, virtualization would run very slowly.
4. A D For this to work, hardware virtualization support must first be enabled in the UEFI/BIOS. Second, Hyper-V needs to be turned on in Windows Features. Finally, enabling Hyper-V requires the system to be restarted.
5. E Any of these OSs can be installed in a VM.
